Introduction
Microsoft added an ability to configure Alerts (preview) in Intune back in October 2022 and I’ve been using them since then, however I never got around to blogging about it as other things took priority.
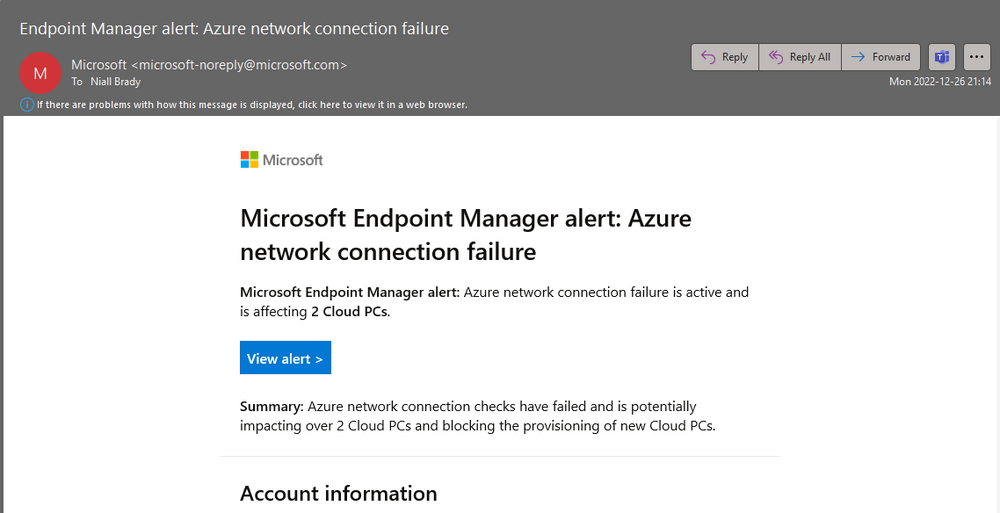
I was reminded that the alerts feature was configured by an email I received yesterday.
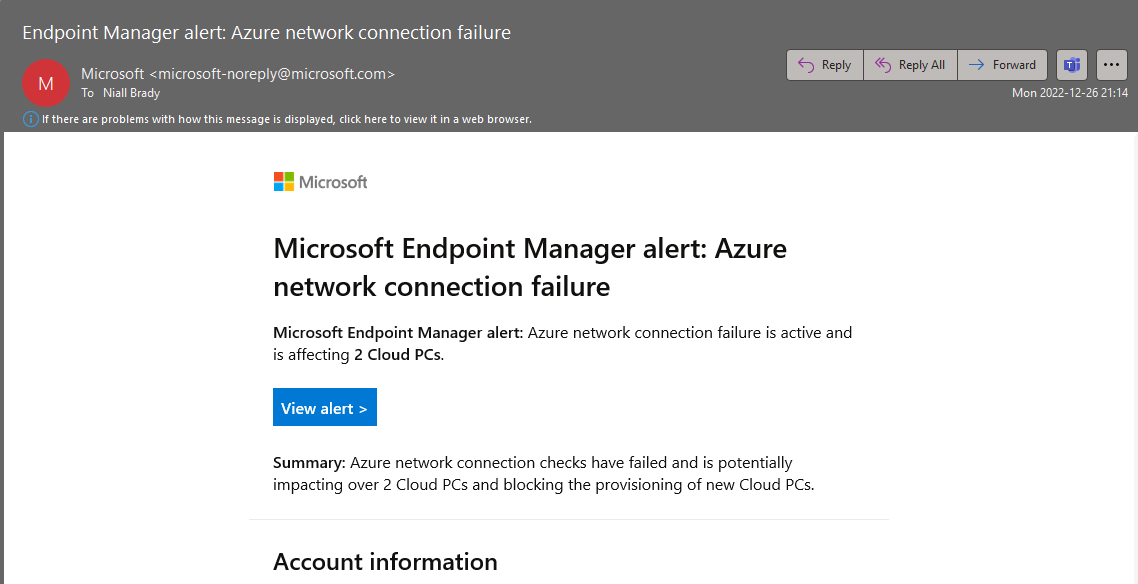
clicking on the View alert link in the email brings you to the associated alert info in Intune as shown here.
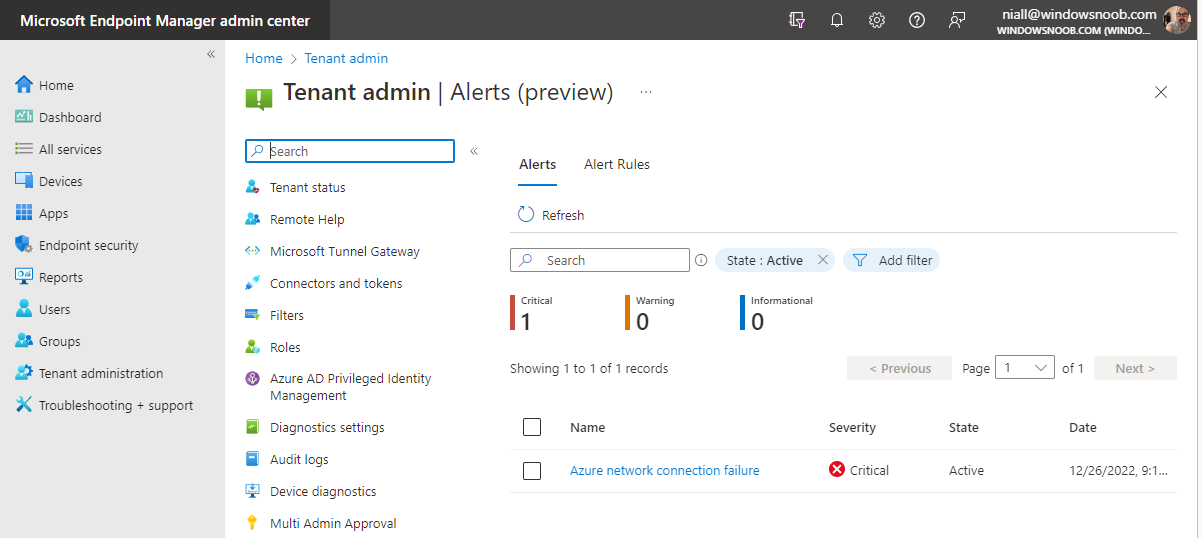
And clicking on the Azure network connection failure alert gives more data.
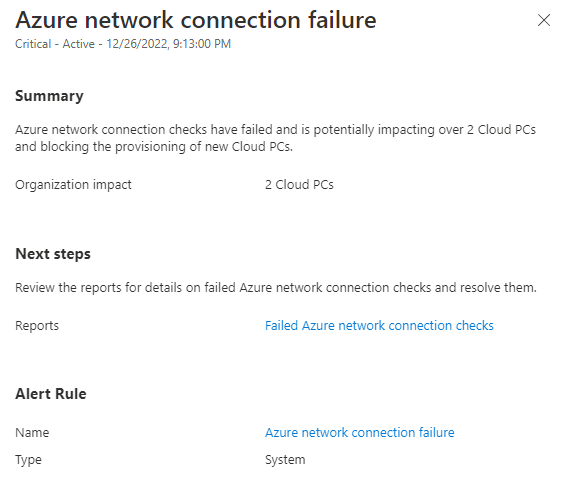
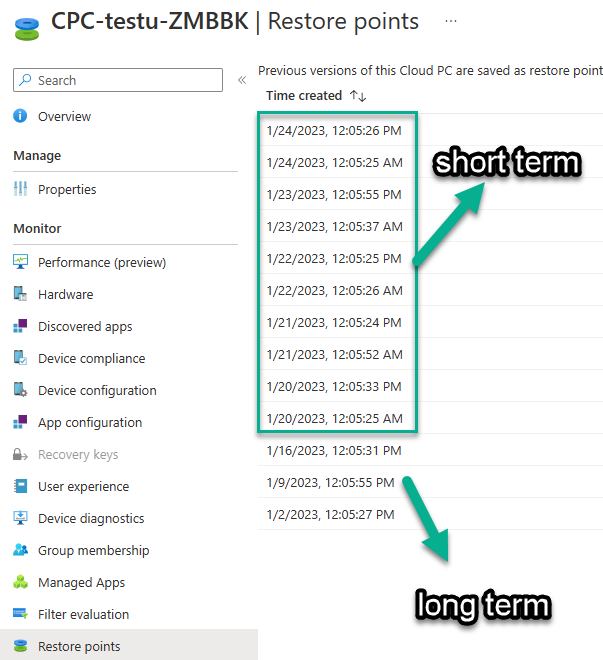
Note: You can further drill down into the details to get more data, and if you click on the linked reports it'll show your fail(ed) Azure Network Connections.
So why is this useful ?
Well in my particular case I caused the issue by shutting down the Routing and Remote Access (RRAS) server. I was doing some hyper-v maintenance and shut down the RRAS server before exporting it, and i never resumed the virtual machine, meaning that the Azure Network Connection check (ANC) would fail.
But let’s imagine that the RRAS server had an issue causing it to fail to start the service(s) or taking it offline. The email alert is yet another way of alerting admins that something is not right.
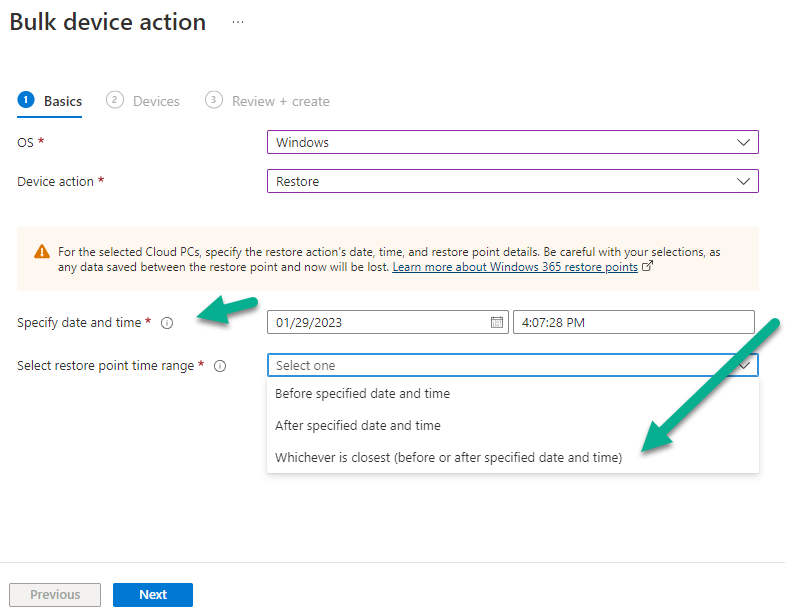
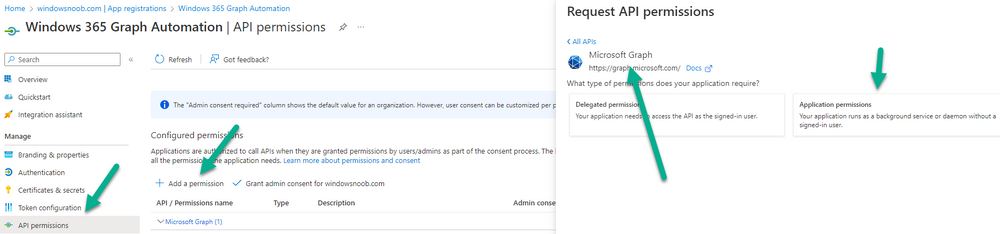
How to configure Windows 365 Alerts
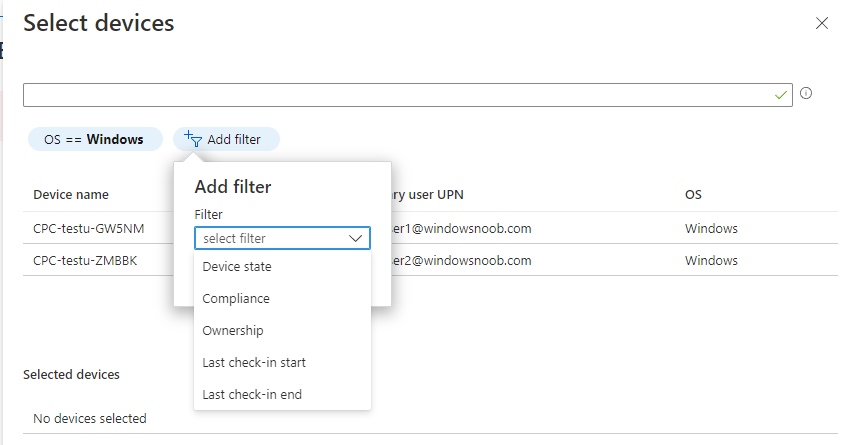
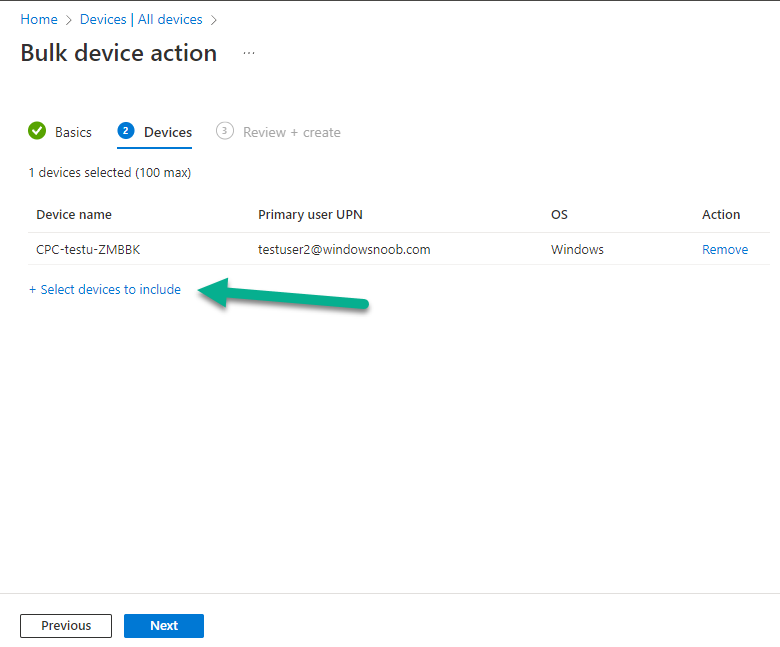
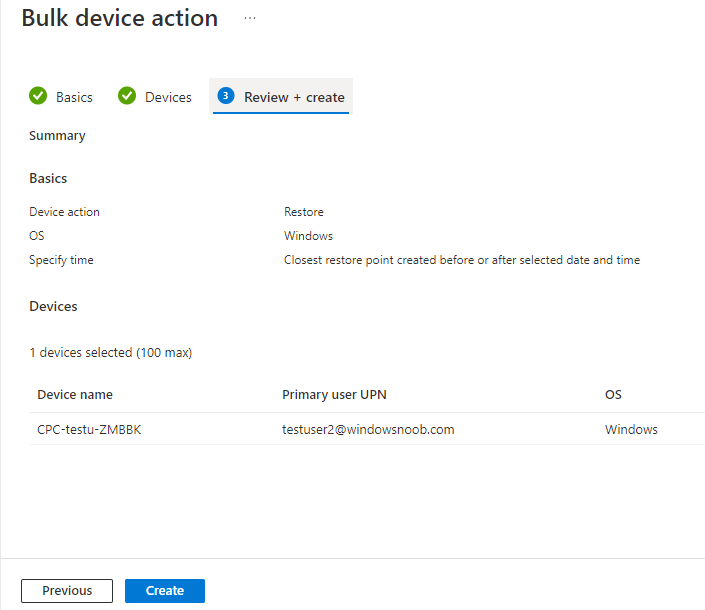
In the Intune portal select Tenant admin (1), select Alerts (preview) (2) and finally select Alert Rules (3) as shown in the screenshot below.
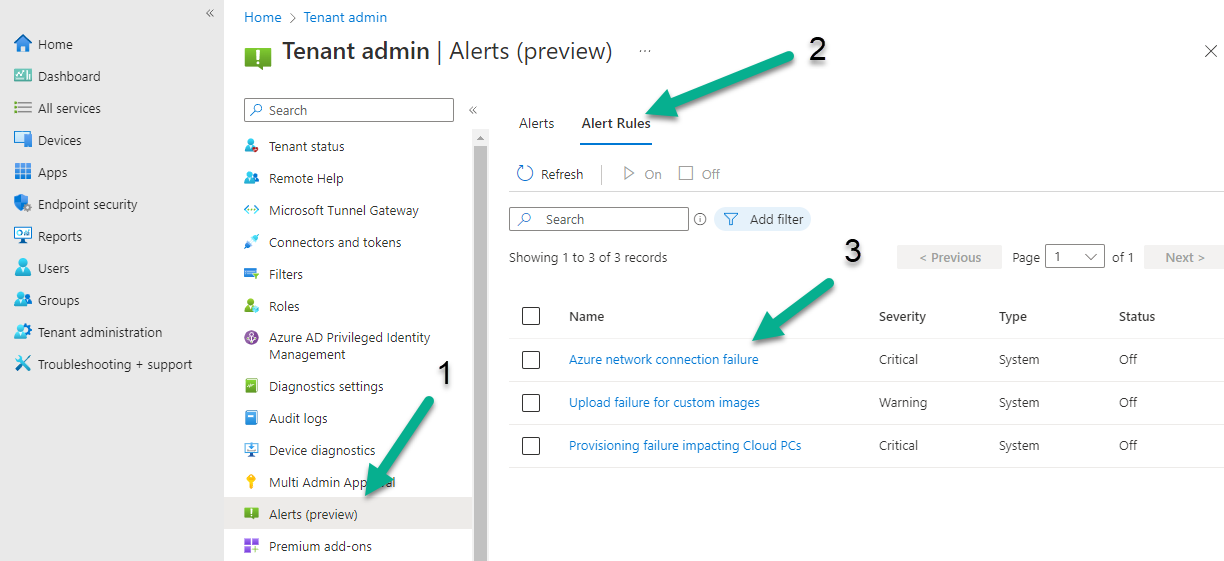
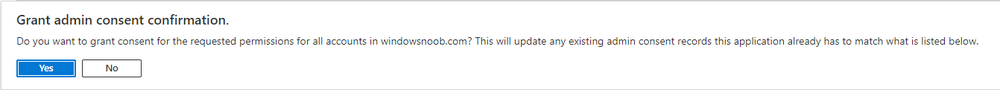
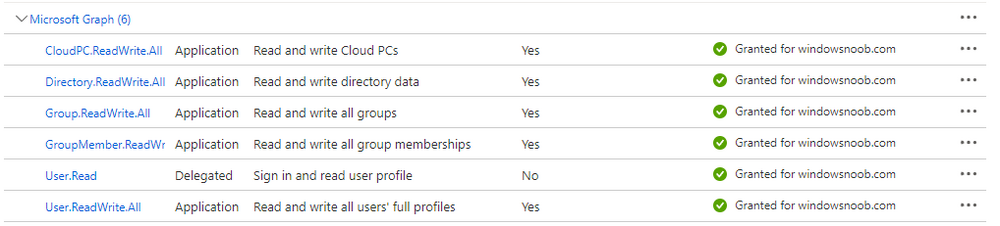
next, configure the alert making sure to select On for Status and add one or more email addresses. Finally, click on Apply.
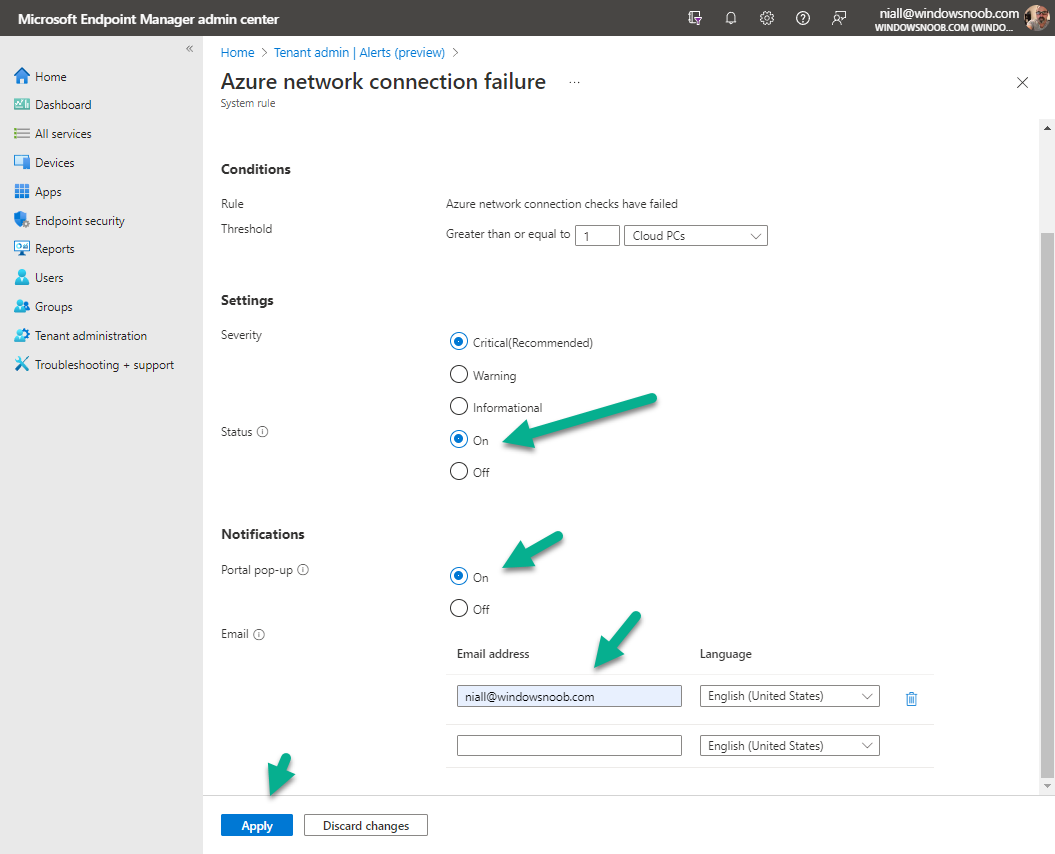
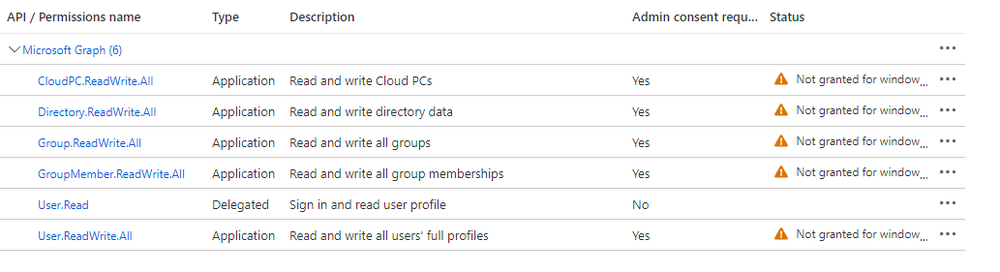
The following Windows 365 based alert rules are currently available at the time of writing (December 2022)
- Azure network connection failure
- Upload failure for custom images
- Provisioning failure impacting Cloud PCs
Currently it seems that the Alert rules are only available for failures or problems. Hopefully we’ll get more alert rules types such as the successful provisioning of a Cloud PC as I requested here. What else do you think we should be alerted about ?
until next time, adios !









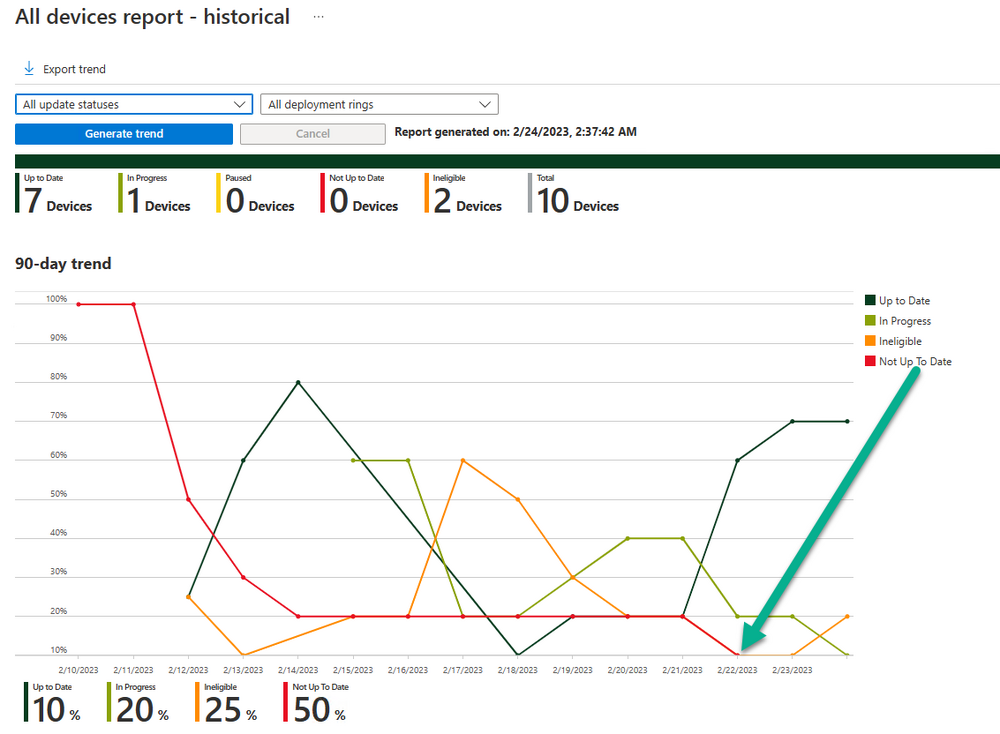

How can I use multiple monitors with Windows 365
in Windows 365
Posted
did you read the post above it at all ?