
TR-909
-
Posts
2 -
Joined
-
Last visited
Posts posted by TR-909
-
-
Hello,
hoping for some help from with a strange issue I have on a customer site
I am currently unable to build Dell Optiplex 5040 devices with Windows 10 1909 x64 Enterprise from an Endpoint manager 1910 MDT integrated task sequence. The task sequence fails when trying to execute the Invoke-MbamClientDeployment.ps1 script.
I have detailed the high level tasks below and attached the SMSTS.log.
- BIOS upgraded to latest version
- BIOS Reset to factory settings
- BIOS Password Set
- BIOS Standard config applied
- UEFI Boot enabled
- TPM Cleared & activated
- TPM Converted from 1.2 to 2.0
- TPM Cleared again and reactivated
- OS Deployed
- Drivers deployed
- MBAM TPMPassTheHash step completed
- DOTNET Enabled
- C++ Redists applied
- Security Patches Applied
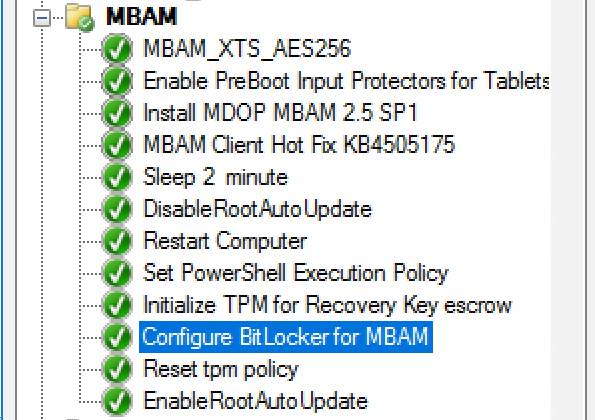
The MBAM Group
MBAM_XTS_AES256 applied to reg
PreBoot Input Protectors for Tablets applied to reg
MDOP MBAM 2.5 SP1 Installed
MBAM Client Hot Fix KB4505175 Applied
Sleep 2 mins
DisableRootAutoUpdate (Certificate applied)
Restart
Set PowerShell Execution Policy Set to bypass
Set PowerShell Execution Policy
powershell.exe -command Initialize-TPM Is run
**THE STEP THAT FAILS**
Invoke-MbamClientDeployment.ps1 with the below parameters
Parameters - -RecoveryServiceEndpoint "https://MBAM:443/MBAMRecoveryAndHardwareService/CoreService.svc" -StatusReportingServiceEndpoint "https://MBAM:443/MBAMComplianceStatusService/StatusReportingService.svc" –IgnoreEscrowOwnerAuthFailure -EncryptionMethod "XTSAES256"
**The Post Steps**
Reset TPM Policy
EnableRootAutoUpdate
The TPM status is
Enabled, Activate & NOT owned
The above works on all other models tested but fails on the 5040
The actual error message received is contained in the smsts.log file attached and the extract is below.
The device is also in a staging OU that receives no Group Policy. The device does register in MBAM if continue on error is checked on the offending task and the computer object moved to the correct OU but will not encrypt. The same task sequence works on the other Dell models tested e.g. 5050
I have logged in after and BitLocker throws a internal error if you try to run it manually.
**THE ENVIRONMENT****
A single site deployment of Endpoint Manager 1910 with two distribution points deploying Windows 10 1909 x64 enterprise with a MDT Integrated task sequence. The Dell command tool kit has been integrated into End Point Manager and drives the BIOS/TPM config steps in the task sequence. The Dell TPM conversion tool is used to convert the TPM to 2.0. The devices been build are production Windows 7 and are been repurposed as Windows 10 x64 Enterprise 1909


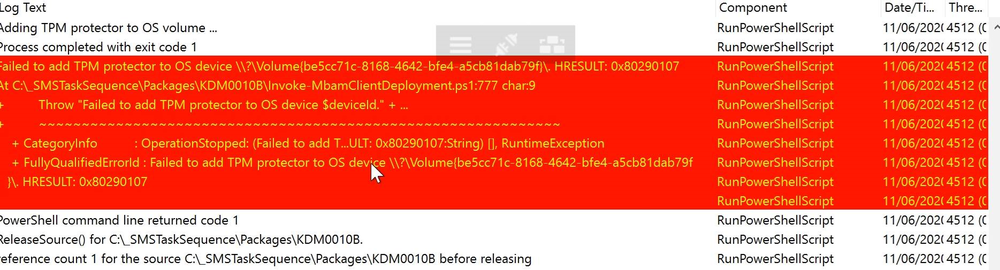
Failed to add TPM protector to OS device exit code 1
in System Center Configuration Manager (Current Branch)
Posted
Thank you for the quick reply, yes its less than helpful and also exactly what you get if you try to turn BitLocker on manually if you allow the TS to complete
The WIM has been offline serviced to the April Cumulative update and then patched as part of the task sequence using the method attached.
I have also had to add the cumulative update to the Boot image as the Dell TPM Conversion tool breaks with out it post 1903
https://www.dell.com/community/Microsoft-SCCM-SCOM-OpenManage/TPM-1-2-to-2-0-updater-in-WinPE-1903/td-p/7341321