Search the Community
Showing results for tags 'TPM and BitLocker'.
-
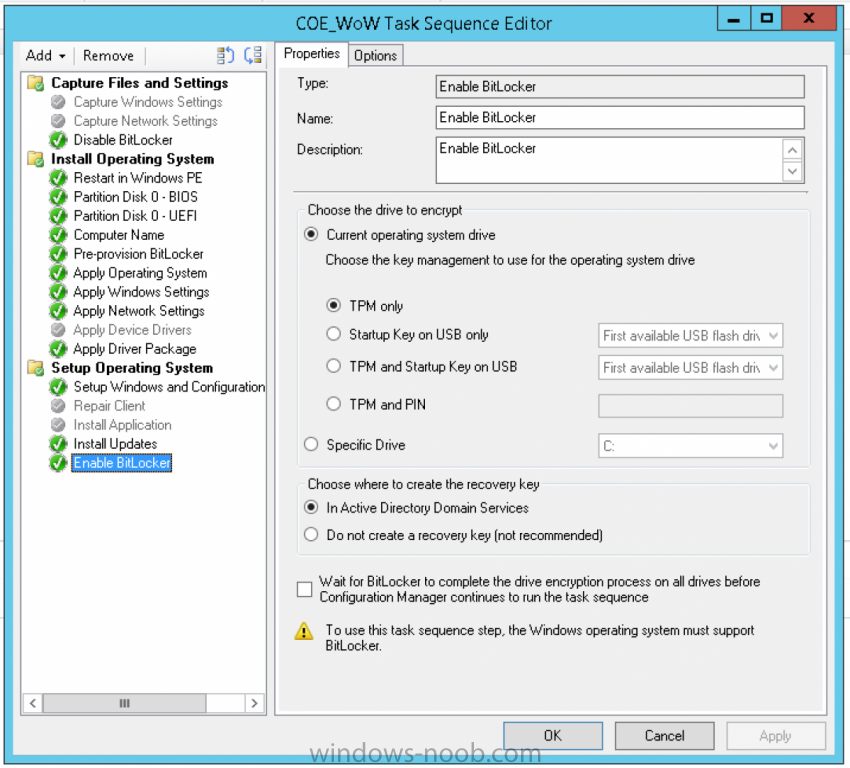
Hello, I'm having a problem enabling BitLocker on Windows 10 v1607 during the task sequence for one model laptop: Dell Latitude E5450 -- except that it does work about 10% of the time. I haven't been able to narrow it down to a specific hardware problem and different BIOS update versions and drivers also result in mixed successes (even on the same exactly laptop). Strangely, the E5450 model has worked historically with the Windows 10 LTSB 2015 version and BitLocker. Models in our environment that work 100% off the time (with the same exactly task sequence) include Latitude E6430, E5440, and E5470. We're using SCCM Current Branch and PXE boot for OS deployment. We do not have any integration with MDT or MBAM. With the E5450s, when it fails it does so at the default Enable BitLocker step. The Enable BitLocker step is configured for TPM Only, create recovery key in Active Directory, and Wait for BitLocker to complete. Also, prior to being built, the computers will have the TPM manually cleared in the BIOS (if previously BitLockered) and the disks formatted at the beginning of the build. Here's a snippet from the smsts logs for the Enable BitLocker step on a failed build: Command line: "OSDBitLocker.exe" /enable /wait:True /mode:TPM /pwd:AD Initialized COM Command line for extension .exe is "%1" %* Set command line: "OSDBitLocker.exe" /enable /wait:True /mode:TPM /pwd:AD Target volume not specified, using current OS volume Current OS volume is 'C:' Succeeded loading resource DLL 'C:\WINDOWS\CCM\1033\TSRES.DLL' Protection is OFF Volume is fully decrypted Tpm is enabled Tpm is activated Tpm is owned Tpm ownership is allowed Tpm has compatible SRK Tpm has EK pair Initial TPM state: 63 TPM is already owned. Creating recovery password and escrowing to Active Directory Set FVE group policy registry keys to escrow recovery password Set FVE group policy registry key in Windows 7 Set FVE OSV group policy registry keys to escrow recovery password Using random recovery password Protecting key with TPM only uStatus == 0, HRESULT=8028005a (e:\qfe\nts\sms\framework\tscore\encryptablevolume.cpp,1304) 'ProtectKeyWithTPM' failed (2150105178) hrProtectors, HRESULT=8028005a (e:\nts_sccm_release\sms\client\osdeployment\bitlocker\bitlocker.cpp,1252) Failed to enable key protectors (0x8028005A) CreateKeyProtectors( keyMode, pszStartupKeyVolume ), HRESULT=8028005a (e:\nts_sccm_release\sms\client\osdeployment\bitlocker\bitlocker.cpp,1322) ConfigureKeyProtection( keyMode, pwdMode, pszStartupKeyVolume ), HRESULT=8028005a (e:\nts_sccm_release\sms\client\osdeployment\bitlocker\bitlocker.cpp,1517) pBitLocker->Enable( argInfo.keyMode, argInfo.passwordMode, argInfo.sStartupKeyVolume, argInfo.bWait ), HRESULT=8028005a (e:\nts_sccm_release\sms\client\osdeployment\bitlocker\main.cpp,382) Process completed with exit code 2150105178 Failed to run the action: Enable BitLocker. The context blob is invalid. (Error: 8028005A; Source: Windows) On successful builds, the snippet is the exact same up to the "Protecting key with TPM only" line. At that point, it continues with the following before moving on to the next step: Protecting key with TPM only Encrypting volume 'C:' Reset FVE group policy registery key Reset FVE group policy registry key in Windows 7 Reset FVE OSV group policy registery key I'm mostly wondering if anyone has seen the errors "Failed to enable key protectors (0x8028005A)" or "The context blob is invalid. (Error: 8028005A; Source: Windows)" -- or has any idea of what could cause this issue. Thank for you any help you can provide!
- 1 reply
-
- Windows 10
- TPM and BitLocker
-
(and 4 more)
Tagged with:
-
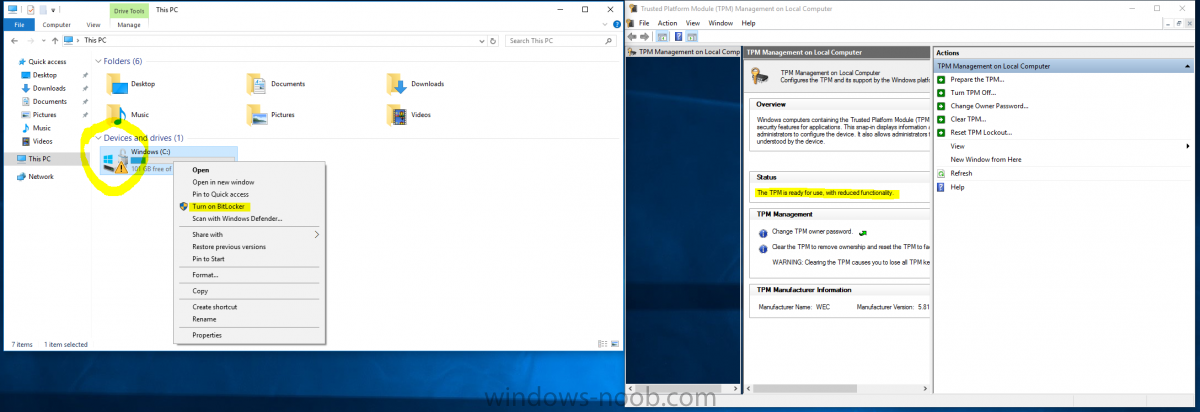
Hello, I am new here but I have been following windows-noob.com for a very long time. You have amazing content. I am Running SCCM 2012 R2 SP1 CU2 environment with MDT 2012 SP1 integrated plus I have WADK 10.0.10240.16384. I have build a Task Sequence below which works flawless on Dell OptiPlex 7040 and E5450. The only issue I have is when the deployment is completed. The bitlocker is not enabled and TPM says " tpm is ready for use with reduced functionality". TPM is enabled in BIOS, UEFI is selected, Secure Boot is enabled as well. Any help is appreciated on how to initiate TPM during OSD and enable bitlocker. Thanks for all the help
- 6 replies
-
- SCCM 2012 R2 SP1
- Windows 10
-
(and 4 more)
Tagged with: