Search the Community
Showing results for tags 'bitlocker'.
-
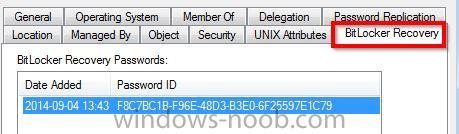
The writing of the Bitlocker key to AD has been working flawlessly... until we started to receiving machines with SSD drives in them. The task sequence works flawlessly with no errors. The problem is the bitocker recovery tab within AD is empty. I can run the manual way (https://blogs.technet.microsoft.com/askcore/2010/04/06/how-to-backup-recovery-information-in-ad-after-bitlocker-is-turned-on-in-windows-7/ ) and it will input the data in to ad, but I do not want to have to do this . The real strange thing is if I remove the machine from AD, and reimage it, the key properly registers itself within AD. Only on the second pass will it work?
-
Greetings good people of the interweb I am currently working on a project that i could use some help on, i along with a colleague have been scouring the internet trying to find any answer we can but have come up short which brings me here: The project in question involves Bit Locker on our Microsoft Surface devices; we currently utilize SCCM 2012 R2 to handle our windows updates (this is working fine); however due to the surface devices regularly having firmware updates that bit locker will prevent from installing, we are trying to identify a way to use SCCM to disable(suspend) bit locker before the updates are installed, then re-enable it once the updates are completed. We have tried the built in task sequence of disable bit locker, but once the device restarts it re-enables again. This can be a problem if the updates go through a series of restarts as part of the installation. We have tried using a CLI task sequence, but i am unsure if we have set it correctly as we are not getting any activity on our test devices. Any information, or walk-through or a general direction you can point me would be greatly appreciated. Thank you in advance!
-
I've been using MDT for a few years now, up to and including MDT 2012 update 1. Now we've purchased SC2012, and I'm trying to rebuild the deployment setup in SCCM to do the same things I did before in MDT. It looks like there are several areas where things might work in a different way. Rather than trying to manually recreate the exact steps I had in MDT, I wanted to check first to see if there's a better way to accomplish the same goals in SCCM. The question of the moment is regarding bitlocker. In MDT, I had set customsettings.ini up with different sections for laptops and desktops, and depending on the IsLaptop variable, it would jump to whichever was appropriate. For laptops, I enabled bitlocker. For Desktops, I didn't. I created a new mdt task sequence in SCCM (sp1 beta), and I see that it has steps included for pre-provisioning bitlocker and enabling bitlocker, both are conditional on the existence of an OSDBitlockerMode variable. I don't know how that variable is set, but I'd like the same setup I had with MDT, such that bitlocker is only enabled on laptops. What's the best way to do this?
- 5 replies
-
- bitlocker
- sccm2012sp1
-
(and 4 more)
Tagged with:
-
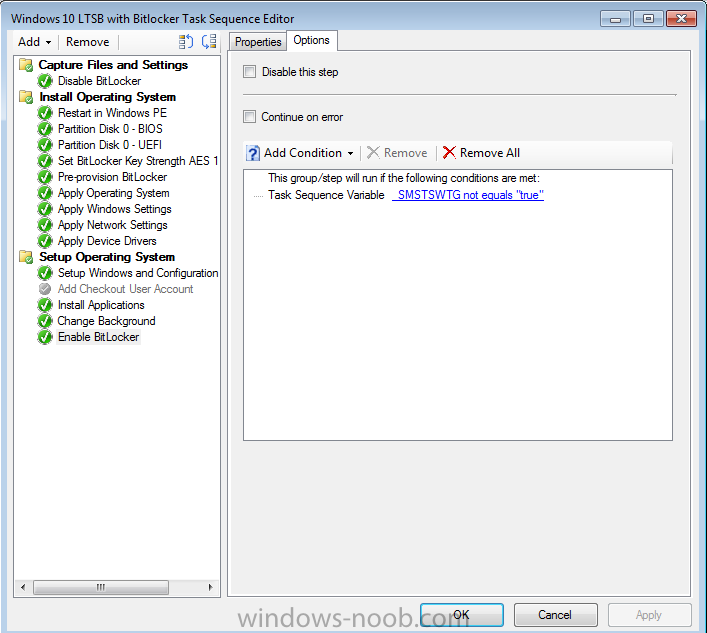
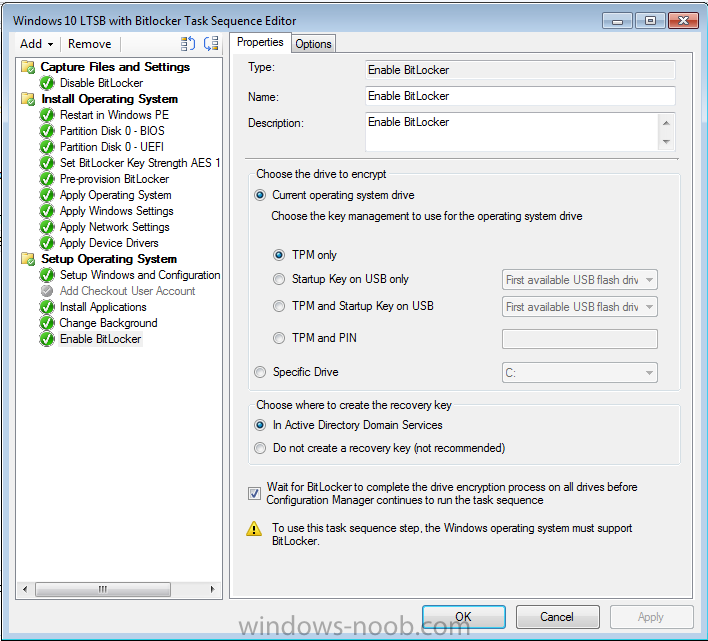
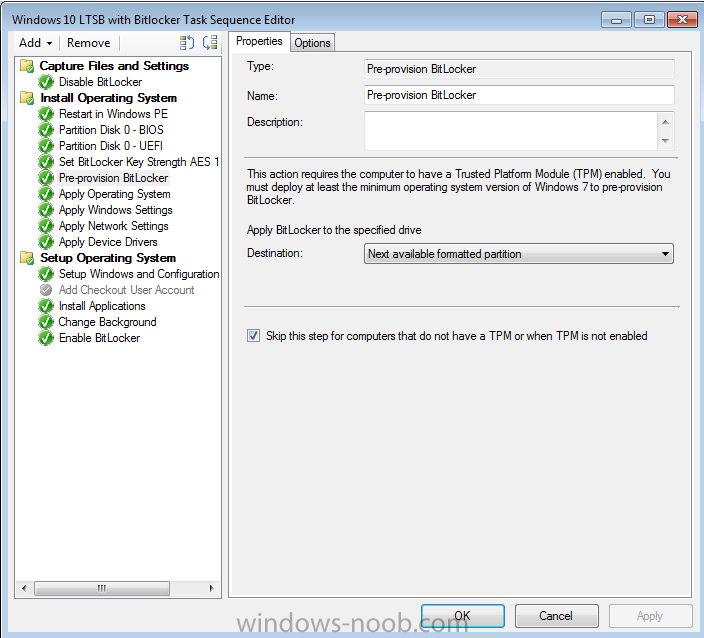
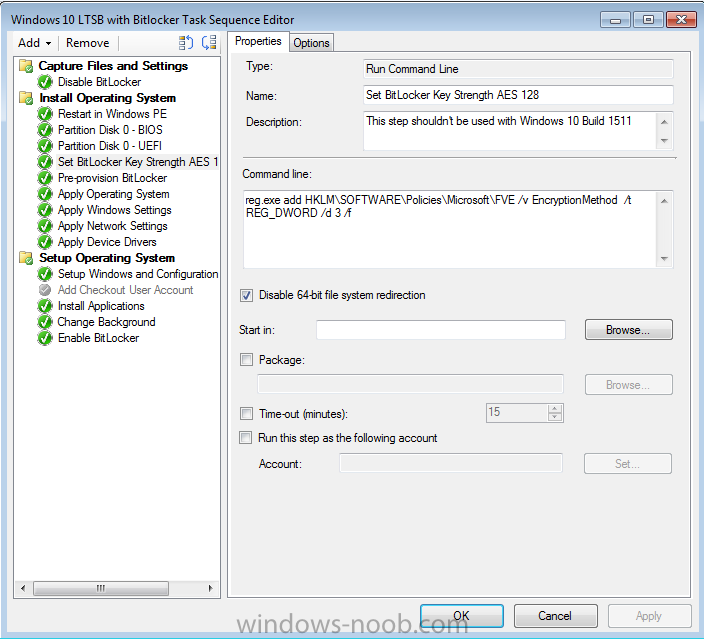
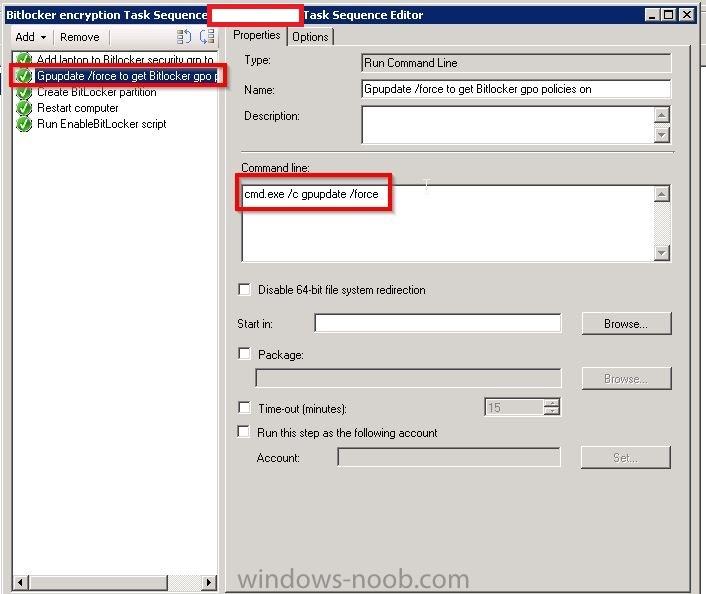
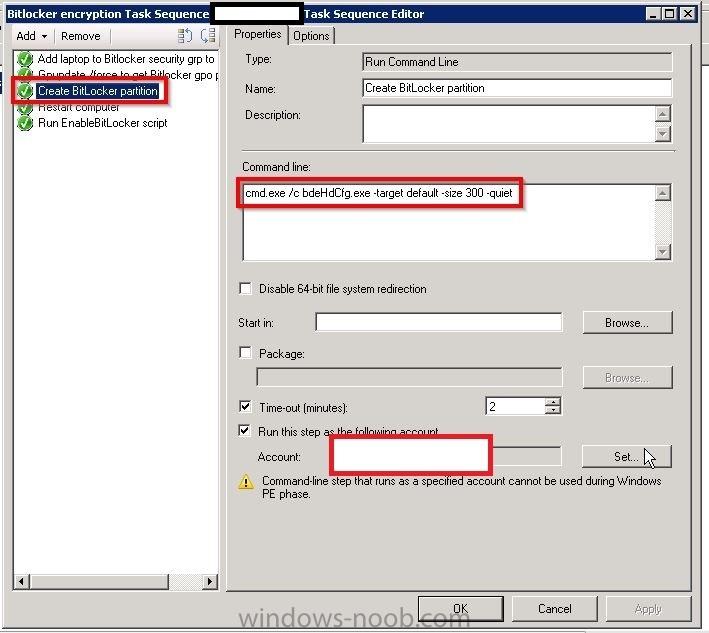
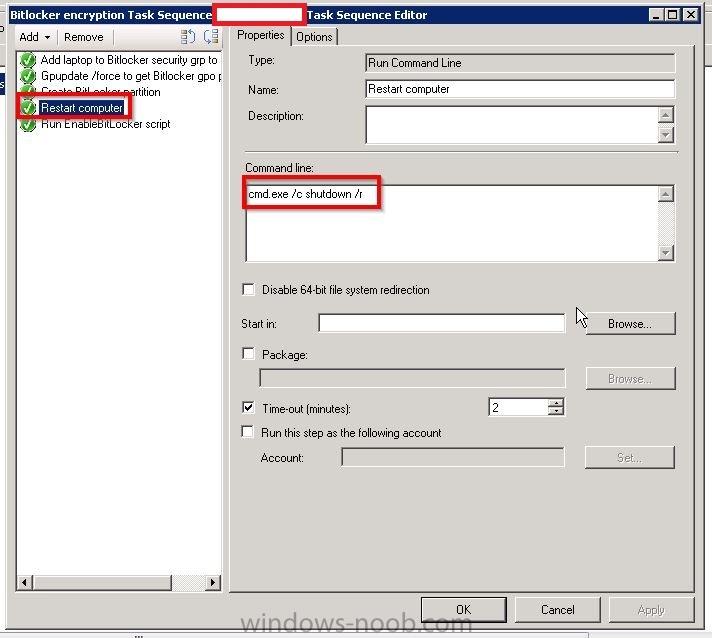
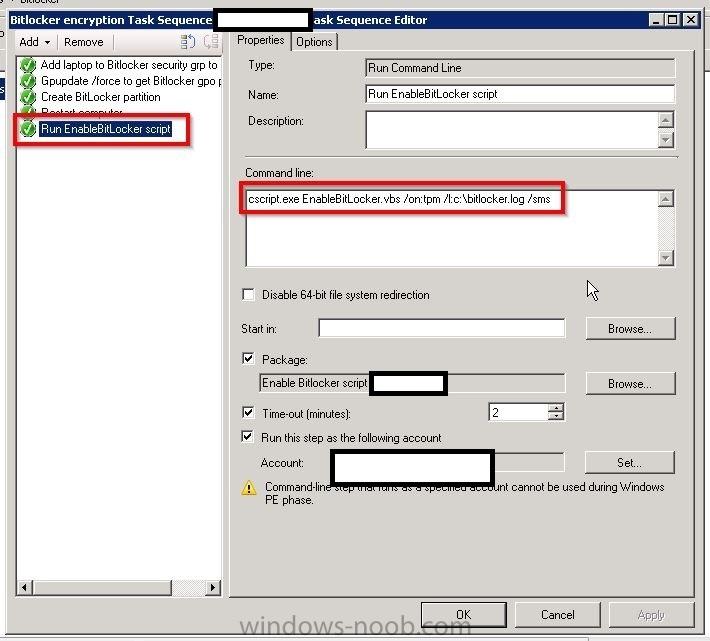
Hello, I am an SCCM new comer, but a long time reader of topics on this blog. This is my first post here. I have recently been appointed to take care of our new SCCM 2012 SP1 environment. I have a task sequence I am using to deploy Windows 10 LTSB with BitLocker to all laptops and mobile devices that pass through our department for imaging. I am experiencing something strange. I am noticing that around 98% of computers that receive the BitLocker enabled image do not "enable" BitLocker on an initial imaging of the computer. What is strange is that BitLocker DOES get enabled successfully once the computer is imaged a second time. I think what is confusing me the most is the fact that rarely the computer will get imaged with BitLocker enabled the first time running the task sequence, and this is inconsistent behavior. I am attaching screenshots of my task sequence steps for BitLocker, but I am unsure of what log to attach if any, and also where to find it. Sorry I'm still quite new to everything. Thank you in advance for any clues or help you can provide. Please let me know what else I can provide to help you guide me. Wardo
-
Hello I currently have a working task sequence for non UEFI machines it currently provisions a bitlocker space and depending if its a laptop or desktop enables either bitlocker with pin or just bitlocker No matter what I do I cannot seem to get a UEFI version to work in the task sequence. I have copied various settings from a MDT task sequence that cater for the UEFI sequence. I seem to be able to format based on the items I have copied but cannot get the bitlocker part to work. No errors as it seems to go through the sequence ok so I am guessing its not picking up correct variables to do the task Does someone have a working task sequence for UEFI machines I can look at I am currently trying to install a windows 7 x64 OS Any help Cheers
-
I'm enabling BitLocker on enterprise Dell laptops and that is working fine. I'm now testing BitLocker To Go and have spotted a permissions issue. It appears that users can control their own BitLocker To Go settings. It is possible, via Group Policy, to enforce passwords on USB drives and the user can then use this to unlock the drive. They can even change the password if required (the Recovery Key is still stored in AD using a GPO if they forget their password). But there is still the ability in 'Manage BitLocker' to turn off BitLocker To Go completely. This seems absurd! The idea of having BitLocker To Go on USB drives is to stop the theft of content if the drive is lost. Even if a password is on the drive the user could just decide to just turn it off and if the drive is lost then the content is accessible. I can't find any GPO setting that would stop the ability for a user to turn this off. Nor can I find anything online about it. Surely I'm not the only one to have spotted this. Anyone thought about this and have a way to stop this?
-
Is it possible for me to use a task sequence to pre provision and setup bitlocker on an existing drive? I don't want to have to reinstall OS on existing machines in order to get this working. So, we have OS already installed and i want to use a task sequence to perhaps shrink volume and create a new bitlocker volume, then enable bitlocker.
-
Hi Everyone, I am trying to automate MBAM Encryption during the OSD Task Sequence using the "StartMBAMEncryption.wsf" script provided in the following blog. http://blogs.technet.com/b/deploymentguys/archive/2012/02/20/using-mbam-to-start-bitlocker-encryption-in-a-task-sequence.aspx The command I use is - cscript.exe StartMBAMEncryption.wsf /MBAMServiceEndPoint:http://<MBAM Server Name>/MBAMRecoveryAndHardwareService/CoreService.svc I have used the script in both a "Install a Package" & "Run Command Line" group & both fail with the below error. Failed to run the action: Install a Package The system cannot find the file specified. (Error: 80070002; Source: Windows) Yet if I exit out of the Task Sequence, log onto the Laptop, & run the exact same command, MBAM Encryption starts first time without any problems. Any help would be much appreciated. Thanks! Jordan,
-
I seem to have an issue where I cannot control the behaviour of our TPMs in our Panasonic Devices via Group Policy. I have issues where the TPMs (Manufactured by Infineon) in our Panasonic AX3s seem to lockout far too easily, previously I have not applied any group policy settings to control the behaviour of the TPMs themselves as during testing they seemed fine. Now I have tried to apply settings to set the standard user lockout threshold and maximum number of authorisations, on our Panasonic Devices I cannot seem to set these settings, its like the TPM ignores the commands from group policy. I have tried this on some Lenovo devices (TPM is manufactured by STM) built in exactly the same manner and the TPM will accept the commands. Has anyone else had this issue with these or similar devices at all?, all of our devices are built identical with the TPM being initialised during a build sequence and they are setup with Bitlocker using MBAM 2.0. Any help would be most appreciated. Thanks
-
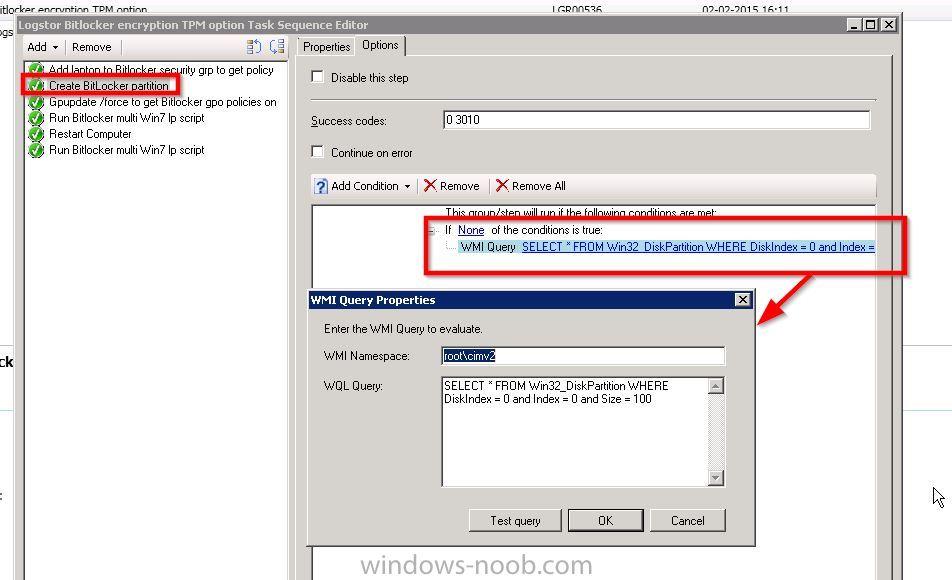
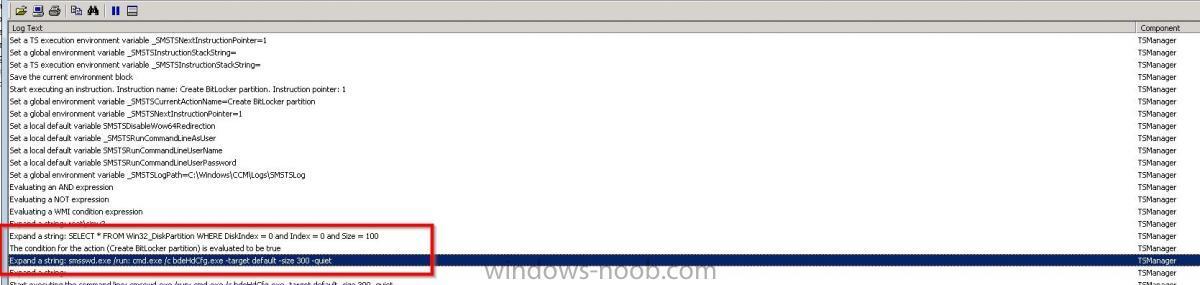
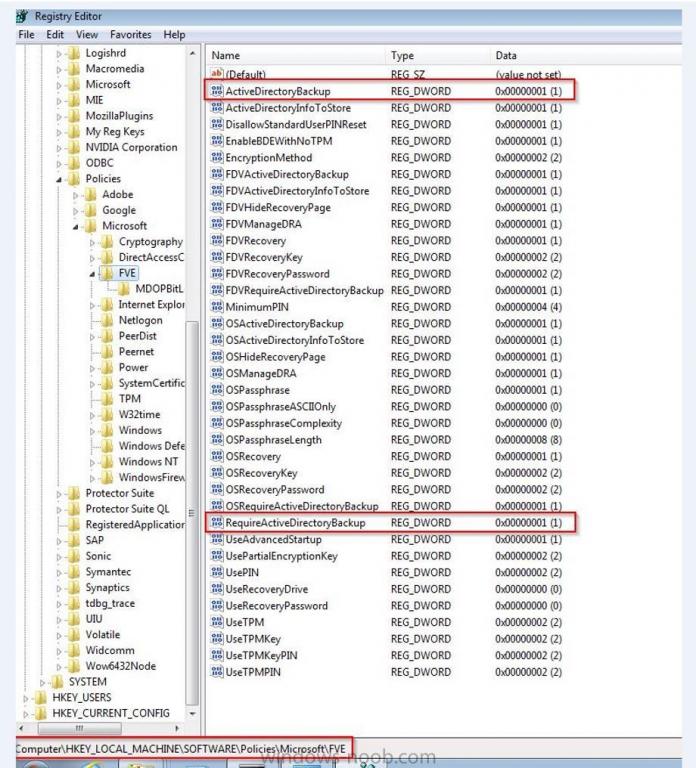
Hi All, Recently I have been trying to bit locker devices during OSD on a 2008r2 domain, with sccm 2012 r2 sp1. the schema has been checked and is correct (the 5 entries are present) CN=ms-FVE-KeyPackage – attributeSchema object CN=ms-FVE-RecoveryGuid – attributeSchema object CN=ms-FVE-RecoveryInformation – classSchema object CN=ms-FVE-RecoveryPassword – attributeSchema object CN=ms-FVE-VolumeGuid – attributeSchema object CN=ms-TPM-OwnerInformation – attributeSchema object The ad DC's have the bitlocker tools installed, and I can see the 'bitlocker recovery key' tab for a device in ADUC. I have a AD GPO in place on an OU where the device exists in AD But my task sequence fails at the ENABLE BITLOCKER stage towards the end of the TS. The TS was created by sccm wizard, nothing special in it as yet. If I disable the DISABLE BITLOCKER, PREPROVISION BITLOCKER and ENABLED BITLOCKER steps in the TS and build the device, then enable bitlocker manually logged on to the device, it works and saves the key to AD, I am obviously missing something here, anyone know where I should look in the logs... The device is uefi and has secureboot enabled The OS is Windows 81 x32
- 2 replies
-
- bitlocker
- sccm 2012 r2 sp1
-
(and 2 more)
Tagged with:
-
Hi all, I have a SCCM MDT TS that I have created for laptops. The TPM is on and set to active in the BIOS. This is a Dell E5500. The BIOS has the latest version. If I leave the SCCM MDT template as is the TS installs correctly however Bitlocker does not start and the PIN is not entered. The laptop is not added to the domain and is set to add to Workgroup (which is what I need it to do). The SCCM client installs fine (CU4). I noticed the template default with a few bitlocker options: Pre-provision BitLocker =Logical Drive letter stored in a varible then Set Variable for Pre-provision BitLocker = True then right before installing packages Enable Bitlocker cscript.exe "%deployroot%\scripts\ZTIBde.wsf" /UDI I am not using UDI in this TS. I have tried disabling the Enbable Bitlocker and add the SCCM Enable Bitlocker and specify a PIN. When I do the TS fails with error code 0x80070002. In the CS.ini I tried having the settings of OSDBitLockerMode=TPMPIN BDEInstallSuppress=NO This scenario works great in MDT with the Enable Bitlocker step in the TS and my CS.ini looks like the below. We are not saving the recovery key to AD but a network share. BDEInstall=TPMPin BDEPin= some numbers TPMOwnerPassword=some password BDEInstallSuppress=NO BDEWaitForEncryption=FALSE BDEDriveSize=3000 BDEDriveLetter=S: BDERecoveryKey=AD BDEKeyLocation=\\servername\LaptopRecoveryKeys BDEAllowAlphaNumericPin=Yes Also how can I save the key to a network share like I do in MDT? I understand some of my bitlocker commands above are not supported in SCCM 2012 TS like saving the key to a network share. Thank You all
-
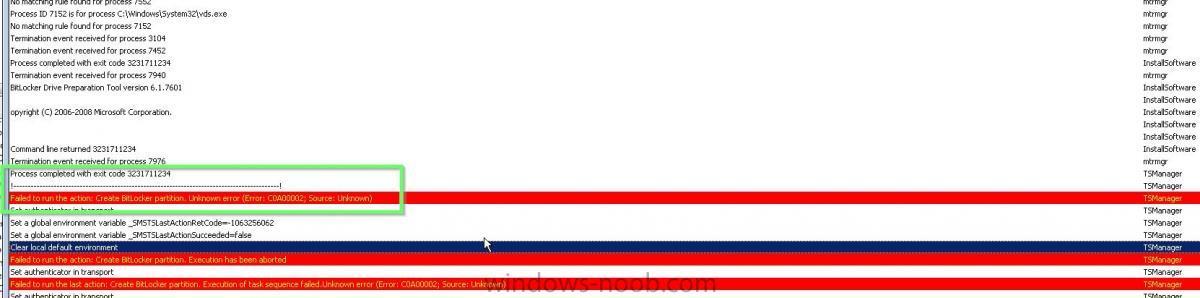
Hi I still have problems with deploying Bitlocker in our environment (on laptops that don't need / haven't been reinstalled through SCCM yet) We switched to SCCM from Altiris around 2 years ago, the laptops that were installed through Altiris were setup with 2 partitions and the ones installed through SCCM I only installed Win7 Ent on 1 partition. See attached screenshots. Any ideas on the error message in the smsts.log file from the Altiris laptop (the one I have marked with a green square)?
-
- wmi
- task sequence
-
(and 1 more)
Tagged with:
-
I am trying to add step to my HTA file, an extra OU value if Windows 8 checkbox is checked (OU=Windows8,) in front of the OU path that gets outputted (OUName). Currently my drop down contains the following: td colspan=1 class="taskTableLeftCell">OU</td> <td class="taskTableSpanSecondAndThirdCell"> <select name="OUName" id="OUName"> <option value="LDAP://OU=Administrative,OU=Workstations,DC=imo-online,DC=com" >Administrative</option> <option value="LDAP://OU=Development,OU=Workstations,DC=imo-online,DC=com" >Development</option> <option value="LDAP://OU=External,OU=Workstations,DC=imo-online,DC=com" >External</option> <option value="LDAP://OU=IT,OU=Workstations,DC=imo-online,DC=com">IT</option> <option value="LDAP://OU=Restricted,OU=Workstations,DC=imo-online,DC=com">Restricted</option> <option value="LDAP://OU=Sales,OU=Workstations,DC=imo-online,DC=com" >Sales</option> <option value="LDAP://OU=Service_Computers,OU=Workstations,DC=imo-online,DC=com" >Service Computers</option> </select> My checkbox says the following <input type>"checkbox" id="mycheck" value"OU=Win8,"/> Then I have my Java saying: function Win8() { var x=document.getElementById("myCheck").value; document.getElementsById("Win8").innerhtml=x; } The other java code is below which adds these 2 ou values together: var OUDrop = document.getelementById("OUName") + document.getElementById("Win8"); When I try to run this and proceed in my script I get an answer- Unable to get property 'undefined' of undefined or null reference. Not sure what I am doing wrong.
-
Hi I have deployed Mbam 2.5 in our environment and the first tests (manual deployment of mbam client and encryption) have been successfull.(tpm and volume recovery work fine) However when trying to use the latest features, we can't get the TPM owner password to be backed up in Mbam. We use pre provisionning wih used space during the task sequence and it works fine. The user is prompted at first logon for the Pin and drive recovery is reported to the DB. However TPM password is not present. Whatever we tried, the TPM did not show up unless we suppressed pre provisionning. Has someone been able to take ownership of the TPM with preprovisioning ? During the TS, at the preprovisioning step, the Tpm shows as Enabled, Activated and Not owned, then in the log it shows that pre provisioning takes ownership. Of course, this prevents Mbam to do the same so no backup of TPM. in the following post, someone from Microsoft states that ownership is not taken, but it seems it does anyway. http://social.technet.microsoft.com/Forums/en-US/b915cd54-6371-4b28-aac7-bd3103dfd7ca/preprovisioning-bitlocker-mbam-and-tpm-password?forum=mdopmbam Thanks in advance for your feedback bruno
-
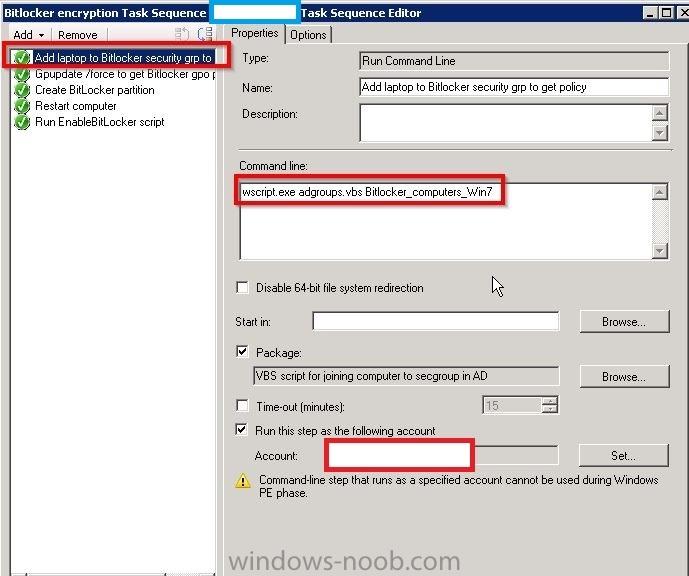
Hi Im wondering if anyone in here has some experience in deploying Bitlocker encryption from a SCCM task sequence? The steps in my task sequence have each been tested ok, want to make sure that it assigns the group policy that makes it required to save the Bitlocker recovery key in the AD under computer properties. I want to make sure it continues from Step 5 after it completes Step 4 (see my attached screenshots). The script source is this one: http://gallery.technet.microsoft.com/780d167f-2d57-4eb7-bd18-84c5293d93e3#content I have seen on test runs that this .vbs script will force a restart of the laptop, if the TPM chip is not activated outside Windows. Any good advice or best practice to this is appreciated. It is around 400 Lenovo laptops that needs to have Bitlocker encryption on in our enterprise, the oldest we have is the T60/T61 model and the newest is the T440 and X240 from last year. PS Is there also a best practice for getting this to work in an OS Deployment TS ? So far the one Microsoft have by default in SCCM doesn't work as automatic as I want it to be
-
Hello, i've had some success deploying WIndows 7 / 8.1 with bitlocker pre-provisioning. However today i've tried to bitlocker a Dell Latitude E6540 laptop and noticed the bitlocker pre provisioning step taking very long. After the wim file and the drivers are applied the disk is only encrypted to 8 % or so. After the setup configuration manager reboot the enable bitlocker ts step fails because the encryption is not completed. I've seen this behavior on older models (eg. Optiplex 960) but i would not have expected this to happen on new hardware. Has anyone experienced something similar ? I'm using: SCCM 2012 R2 on Windows Server 2008 R2 Windows ADK 8.1 Boot Images with MDT Integration (64-Bit) Models i've successfully bitlockered so far: Dell Venue Pro 11 7130 Dell Latitude E7440 Dell Latitude E6520 At first i was suspecting missing cpu features, however it might also be larger and slower disks. On working models the disk is already encrypted when maybe 10 % of the wim file is downloaded. It looks like the encryption initially (after the pre provsion step) does not complete fast enough and when the download starts the system does not keep up downloading, applying and encrypting. If i pause the the task sequence before the first reboot the encryption completes and the task sequence completes successfully.
-
Hello, I was curious if anyone is using MBAM and also storing the Bit Locker recovery keys in active directory? We are starting to Bit Locker all of our workstations, and we are currently storing the recovery keys in active directory. I was thinking about implementing MBAM also, but management wants the keys to be in active directory. Can you store the keys in a MBAM database as well as in active directory? My searches have given me conflicting information. Any help is much appreciated Ron
- 6 replies
-
- MBAM
- Active Director Bitlocker
-
(and 3 more)
Tagged with:
-
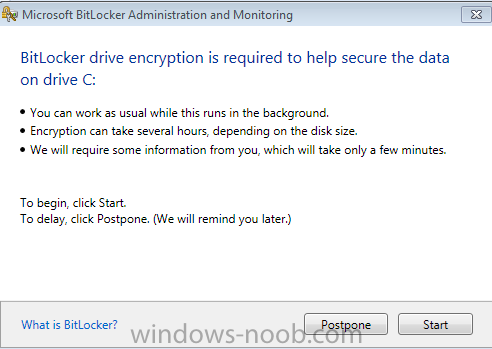
Currently I am in the process of testing out the GPO settings including a pilot group of users for MDOP MBAM Bitlocker encryption. The only question I have is how do you suppress that box where it ask for Postpone/Start; (below image). I am doing this on machines who already have Windows 7 and deployed without Bitlocker enabled. First project was XP -> Windows 7 migrations. Now we are circling back around enabling Bitlocker on existing machines. All clients have MDOP MBAM 2.0 installed already. Everything works as I have intended, but with Postpone and Start GUI popping up to initiate it from the user. So we are looking to have it without any user interactions soon as Policy kicks in, so forth. I did try using the supplied regkey template in C:\Program Files\Microsoft\MDOP MBAM but I can't figure out what keys to add/remove, if any that could run without user interaction. Adding NoStartDelay DWORD doesn't seem to do anything other than display the pop-up sooner than the default 90 minute random cycle. Any suggestions is greatly appreciated. Eric Lenovo Shop - Desktops/Laptops 2000+ nodes - Windows 7 x64-bit SCCM 2012 (non-SP/CU) MBAM Server v.2.0 (non-SP1) - Stand-alone configuration with SQL
- 3 replies
-
- bit locker
- windows 7
-
(and 3 more)
Tagged with:
-
Hi All, I have searched high and low, non-stop for days trying to find an answer. I have finally admitted defeat because I am unable to find the information "out there", as I can normally find "anything" within minutes of searching and so after 3 days, it's fair to say I have been unsuccessful. Task 1: Create a regular task sequence to install my OS image. My task sequence is very generic and is built from the default structure/template assigned by the wizard when installing an image package TS. The task sequence works perfectly fine when a machine PXE boots and the respective TS is selected. The process goes from end to end, and results with an install OS that uses my unattend.xml to make the operation as lite touch as possible. The only drive (C:) is bitlocked in the process by design. Everything is great so far! Task 2: Create a USB Media of the Task Sequence I have a requirement to port this over to a USB pen drive. Using the "Create Task Sequence Media" wizard, I built a USB pen drive. I tested it by booting from the pen drive on physical hardware, and watched the process all the way through. There were NO errors - perfect! Then I shortly realised that when I removed the USB pen drive and started up the computer, I got the Bitlocker Drive Encryption Password Entry screen. The computer had encrypted with the assumption that my USB pen drive was a part of the hardware, and so when it was removed, it believes the hardware had changed. I had to insert the USB pen drive in order to boot the computer to Windows, and only then could I remove the USB pen drive. Problem/Question: What do I need to do to bypass/ignore the USB Media being apart of the hardware? My thoughts were: Method 1: implement a script that forces the user to eject/remove the USB pen drive at a specific step in the TS so that the sequence will continue and bitlocker the hard disk, and since there is no USB pen drive present at this time, everything should be OK. Concerns: I have written a script that will not "finish/exit" unless the USB drives are all empty and do not contain any mass storage devices. My concerns are that once the USB has been removed, I would assume an error would occur because the USB media is missing here on and it can not be read from. How do I overcome this - is this the right thought process? Method 2: Script the bit locker step so that it totally ignores the USB drive when encrypting. Concerns: I don't know how to tell bit locker to ignore the USB pen drive (baring in mind that the USB drive letter could vary depending on the specs of the hardware it is inserted into). Also, encrypting the USB drive is not the actual problem because that doesn't happen (only the C: drive is encrypted), the problem is that the system appears to think the USB pen drive is part of the physical machine. As I have said, I've been hurting my brain for days now to get at least some guidance on this, and I've come up with nothing. This must have been done before by *someone, somewhere*, right? Any advice or tips are appreciated - but better yet, if anyone has first hand experience of doing this, I would love to hear from you. Thanks, WizzKidd
-
Hi guys. I have been working on deploying bitlocker on running windows 7 machines using a task sequence. I have only found guides showing how to do this via scripts, or how to do this when deploying a computer. Not how to push this on active running windows 7 machines. Im hoping that this thread could help me with some issues i have, and hopefully assist others. Im using scripts from here: http://archive.msdn.microsoft.com/bdedeploy/Release/ProjectReleases.aspx?ReleaseId=3205 So there are a couple of Scenarios i have to consider when deploying bitlocker: * Computers with a bitlocker partition, but not active TPM chip * Computer with active TPM chip but no partition * Computers that does not have active TPM chip or a bitlocker partition (would be most common) Im running allot of batch files, this is because it gives me better logging possibilities. I want to store what happens on a network drive so in case of problems we can easy find out what have happened. Plus, i just like batch files. Outline of the current tasksequence (all steps have continue on error) Connect to network folder (maps a network folder, in my case W: in order to later copy log files to network share). Create a folder. Command line, that runs a .bat with a service account that´s local admin on machine folder.bat :md c:\Bitlockertemp Create partition (have issues with this step). Command line: Partition.bat >>c:\Bitlockertemp\DOSpartition.txt Disable 64-bit file system redirection, running with service account. Partition.bat: PATH=C:\WINDOWS\system32;C:\WINDOWS;C:\WINDOWS\System32\Wbem;C:\WINDOWS\System32\WindowsPowerShell\v1;C:\WINDOWS\system32\en-us; bdehdcfg.exe -target default This should either create a bitlocker partiotion, or say that you already have one Enable TPM (and bitlocker if possible), command line: enable.bat >>c:\Bitlockertemp\DOSLogEnable.txt . Running with service account This will either enable TPM and require a restart, or enable bitlocker Enable.bat: cscript.exe %~dp0EnableBitLocker.vbs /on:tpm /l:C:\bitlockertemp\BitLocker.log echo off if EXIST w:\%computername%\bitlocker-backup-key-package1 (echo "Already done") ELSE ( %~dp0keyupload.bat>>c:\Bitlockertemp\DOSLogKeyupload.txt) echo on Net use w: /delete /y rd c:\bitlockertemp /s /q Keyupload.bat: echo off md w:\%computername% cscript %~dp0GetBitLockerKeyPackage.vbs C:\Bitlockertemp\bitlocker-backup-key-package >> c:\Bitlockertemp\BitLockerKey.txt copy c:\Bitlockertemp\BitLockerKey.txt w:\%computername% copy c:\Bitlockertemp\DOSpartition.txt w:\%computername% copy c:\Bitlockertemp\DOSLogEnable.txt w:\%computername% copy c:\Bitlockertemp\DOSLogKeyupload.txt w:\%computername% copy c:\Bitlockertemp\bitlocker-backup-key-package1 w:\%computername% copy c:\Bitlockertemp\BitLocker.log w:\%computername% copy c:\Bitlockertemp\ADupload.log w:\%computername% rd c:\bitlockertemp /s /q The get GetBitLockerKeyPackage.vbs is for checking if AD have recived the bitlocker key 5. Restart computer, set to " The currently installed defualt operating system" Notify the user before restarting "Your computer is being restarted, if prompted to press F1, please do so" 6.Connect to Network Folder again 7. Enable bitlocker, runs enable.bat again, same as step 4 8. Disconnect network drive, simple command: Net use w: /delete /y My current issue: It´s with creating a bitlocker partition, Running just "bdehdcfg.exe -target default" , fails. I had to add PATH=C:\WINDOWS\system32;C:\WINDOWS;C:\WINDOWS\System32\Wbem;C:\WINDOWS\System32\WindowsPowerShell\v1;C:\WINDOWS\system32\en-us; In order to get it to actually run. But the issue im seeing is that when running this the computer stops at creating partition. Nothing happens, the tasksequence does not stop. Not sure if the whole tasksequence is fubar or if I am on the right track. Running the scrips by double clicking on them works like a charm. And the rest of the steps seems to work fine. Any assistance or input would be appreciated. Edit: Im running SCCM 2007
-
Hi, this is my 1st post, and I'm a complete noob to SCCM and Bitlocker. I'm currently using Server 2008 R2, with SCCM 2012 SP1. I've followed various guides online for deploying BitLocker, and have managed to do so successfully....but, In many guides, when created the GPO on the DC for BitLocker, I don't have the option for selecting 'used space only' or 'full disk encryption' Is this option only available with Win8 or Server 2012? I have also read up on using MBAM with SCCM, but I cannot find where you download this from. Any help would be much appreciated. thanks, mdc111
-
We have a requirement to set AES-256 cipher strength for Windows 8. In my Windows 7 TS I use this command to set it to 256-bit before the Enable BitLocker step: reg add HKLM\SOFTWARE\Policies\Microsoft\FVE /v EncryptionMethod /t REG_DWORD /d 4 /f This works fine in Windows 7, but Windows 8 ignores the same command and defaults to 128-bit If I decrypt the drive, set the reg key and manually run BitLocker it encrypts as 256-bit. So the key does work, but not inside the task sequence. I may have to log this with Microsoft but any ideas before I do?
-
Hi, Let me firts explain how i inherited this: I have a TS in sccm 2007R3 that deployes windows 7 and does the following in the bitlocker steps on standalone laptops(not domain joined after ts finishes): ( password and tpm already activated and set in bios with cctk tools) Bitlocker step: 1. manage-bde -tpm -turnon 2. reboot 3. (depending on the laptop model we must manualy press "y" to activate the tpm. In our case fujitsu laptops S781. for our dell laptops this is not requierd) 4. manage-bde -tpm -takeownership <password> 5. manage-bde -protectors -add c: -tpmandpin <password> 6. default enabel bitlocker step with default values(recovery key in ad etc ) Bitlocker policy's are set via localgpo tool before bitloker step. This all works for new deployments. When reimaging these standalone laptops steps 1-4-5 fail because this has already been set. Question: 1. Is this the best way to do this? 2. Does the tpm ownership get wiped when laptops are reimaged or is this the same password? 3. Can u use the same recovery key from AD or is there a new one generated every time we reimage a laoptop? 3. Is it needed to take ownership for tpm? Keep in mind that after these laptops are imaged, users must logon with pin number and users must not be able to change bitlocker or tpm ownership/keys. thanks in advanced for ur help. Charles
-
I am just curious if there are steps beyond the typical enable TPM and BitLocker steps if you have an MBAM back-end. Has anyone setup an OSD for this scenario? I assume the MBAM client piece needs to be installed as well. Just trying to find the best way to encrypt laptops during the imaging process and have them connect up with MBAM or maybe i'm going about this all wrong. Any info would be great. Thanks, EDIT: Found the link below which I believe will do what I need. http://blogs.technet.com/b/deploymentguys/archive/2012/02/20/using-mbam-to-start-bitlocker-encryption-in-a-task-sequence.aspx If anyone has any info to add, please feel free to do so.
-
I have finally figured out the TS to set a BIOS password, enable and activate the TPM... However, the built in 'Enable Bitlocker' step fails, with no error codes, and no logs. It appears to successfully complete, but it doesn't. I think I may need a script to take ownership. All of the scripts that I am running work beautifully within the OS via cmd, but through configmgr, not so good. Any help/advice would be great. Thanks!