
Gar
-
Posts
7 -
Joined
-
Last visited
Posts posted by Gar
-
-
So the purpose of this thread is directly related to my issue in TechNet Post
But I justified it deserves a separate post of itself. To summarise the problem, I have extended the scope of our SCCM to cover another domain, of which it has no problems deploying applications/updates to Desktops, but with servers it is only deploying applications but not software updates (although they are detected under UpdatesDeployment.log and UpdatesHandler.log).
Before I continue, Boundaries and Boundary Groups are configured and working, as some of the working desktops fall in the same IP Range as the servers that are not working.
For Example
Boundaries IP Range: 10.10.10.1 - 10.10.10.254
Boundary Group: All DPs/MPs
Working Desktop IP: 10.10.10.50
Non-Working Server IP: 10.10.10.200
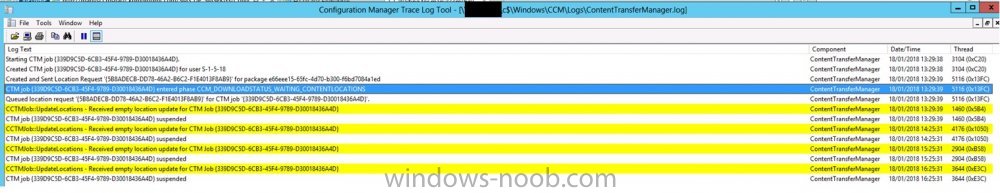
Non-Working Client - ContentTransferManager.log
CTM job {339D9C5D-6CB3-45F4-9789-D30018436A4D} entered phase CCM_DOWNLOADSTATUS_WAITING_CONTENTLOCATIONS
Queued location request '{5B8ADECB-DD78-46A2-B6C2-F1E4013F8AB9}' for CTM job '{339D9C5D-6CB3-45F4-9789-D30018436A4D}'.
CCTMJob::UpdateLocations - Received empty location update for CTM Job {339D9C5D-6CB3-45F4-9789-D30018436A4D}
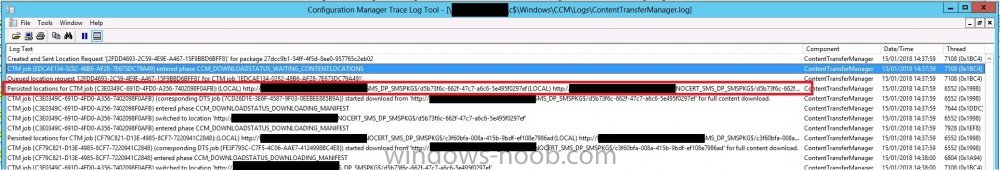
Working Client - ContentTransferManager.log
CTM job {EDCAE134-0282-48B6-AF28-7E673DC79A49} entered phase CCM_DOWNLOADSTATUS_WAITING_CONTENTLOCATIONS
Queued location request '{2FDD4693-2C59-4E9E-A467-15F9BBD6BFF8}' for CTM job '{EDCAE134-0282-48B6-AF28-7E673DC79A49}'.
Persisted locations for CTM job {C3E0349C-691D-4FD0-A356-7402098F0AFB}:
(LOCAL) http://SCCM_SERVER#/SMS_DP_SMSPKG$/d5b73f6c-662f-47c7-a6c6-5e495f0297ef
(LOCAL) http:// SCCM_SERVER#/NOCERT_SMS_DP_SMSPKG$/d5b73f6c-662f-47c7-a6c6-5e495f0297ef
(LOCAL) http:// SCCM_SERVER#/SMS_DP_SMSPKG$/d5b73f6c-662f-47c7-a6c6-5e495f0297ef
(LOCAL) http:// SCCM_SERVER#.SMS_DP_SMSPKG$/d5b73f6c-662f-47c7-a6c6-5e495f0297ef
(LOCAL) http:// SCCM_SERVER#/SMS_DP_SMSPKG$/d5b73f6c-662f-47c7-a6c6-5e495f0297ef
(LOCAL) http:// SCCM_SERVER#/SMS_DP_SMSPKG$/d5b73f6c-662f-47c7-a6c6-5e495f0297ef
I want to trace each granular step of this entire process to the point where I can see the CTM job {EDCAE134-0282-48B6-AF28-7E673DC79A49} entered phase CCM_DOWNLOADSTATUS_WAITING_CONTENTLOCATIONS job request on the server, and hopefully whatever the server is doing causing it send no DPs back to the client requesting this. I can't seem to find the root cause of this issue and really need to make some progress as it's already behind schedule and Management are waiting on me on this problem.
-
I posted this on TechNet already, but as I'm still experiencing the issue I'm posting here as well.
I’ve been bashing my head on this issue for some time now, and trawled through many, many posts on the Internet without being able to resolve my issue.
Background
We have a working SCCM setup on Domain1. Recently I pushed out Domain1’s agent to all Domain2 computers and servers via a Powershell script with explicit install parameters; this is all fine.
Patching and Software deployments are working are on all the test desktops I’ve deployed on, so this is a checkpoint for me as I know that MP/DP/BITs (firewall ports) connectivity is all working fine. On the server I’m testing on with Software Updates I get the following:
UpdatesStore.log – Recognises software update deployments and missing updates are returning the correct Status = Missing entry in the log.
UpdatesDeployment.log – Acknowledges the above with “EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 1”
Further down the log, I get this error being flagged. I cannot determine if this is a red herring or not, but this post references the exact error and MS has dismissed it as not having any functional impact to SCCM.
Failed to get SDM CI for update (Site_E0302A3C-FCA2-434A-8822-A1806E8739D3/SUM_96d2119c-c85d-4490-b58c-927d2ebe297c) from type store, error = 0x80070002
I never see any entries for the “CIStateDownloadingPercent” at all though, so it never even attempts to download, which leads me onto ContentTransferManager.log.
ContentTransferManager.log
CCTMJob::UpdateLocations - Received empty location update for CTM Job {D6A97A39-6FE4-4524-BFAD-7AE24F2A1019}
WUAHandler.log – Correct SCCM server set as WSUS source. “Existing WUA Managed server was already set”.
LocationServices.log - Correct SCCM server set as WSUS Path.
Boundaries and Boundary Groups
I’ve configured IP Range Boundaries which covers the IP of the server in question. Additionally I have subsequently added Active Directory Site Boundaries as well, with no difference. The IP Range and AD Site Boundaries are members of the Boundary Group which is referencing our MPs and DPs on Domain1.
Deployment Package and DP
These are always at 100% compliance state before I reinitiate scans on the server having the issue.
Additionally, I've successfully tested an application deployment to the affected server and this was deployed fine, and the source files reside in the CCMCACHE folder which is even more confusing!
Need some guidance on what else to check or look out for please, I keep getting pointed back to Boundary Group definitions which makes sense, but I've checked this over and over again, and there is only so much validation I can do on an IP address; I even ran a PS script on the site server to see what Boundaries the affected IP falls under and of course, it returned the Boundaries I defined.
-
Someone else figured out my miconfiguration in the original technet thread, i've marked it as answered.
How have you configured the Receive Connector? For SSRS create a Receive Connector as follows:
In Network tab, add the IP address of the SSRS server
In Authentication tab, only select the option "Externally Secured".
In permission groups tab, select all items.
-
Hi Garth,
Thanks for the response. I was under the impression that CM12 uses SSRS (and thus the SQL Mail configuration) to send out the Subscription Reports, if that is definitely not the case I can eliminate that part from my configuration all together.
So, to clarify:
CM12 Alerts have always been working fine - no issue here and I understand this is a different kettle of fish to SSRS.
Why do you think that SSRS can send test message, where did you do this action?I actioned the "Send Test E-mail" option when you right-click on the Database Mail option within SQL2012. However, as you pointed out already, if this has absolutely nothing to do with the Subscription Reports configuration, then this is no longer relevant. If anything it just proves that e-mails can be sent via the Exchange server (using basic authentication).
Now, I guess, I just need to figure what within SSRS Configuration Manager is missing, my trouble is that there isn't any detailed settings I can configure and Exchange logs doesn't indicate anything that isn't already reported by SCCM:
2014-06-25T14:09:14.168Z,Exchange\SCCM01 - Subscription Reports Receiver,08D15B57A7508DA3,21,10.2.2.202:25,10.2.2.213:63905,>,530 5.7.1 Client was not authenticated,
-
I posted this issue yesterday on Technet without much feedback that was of help, so i'm trying my luck here!
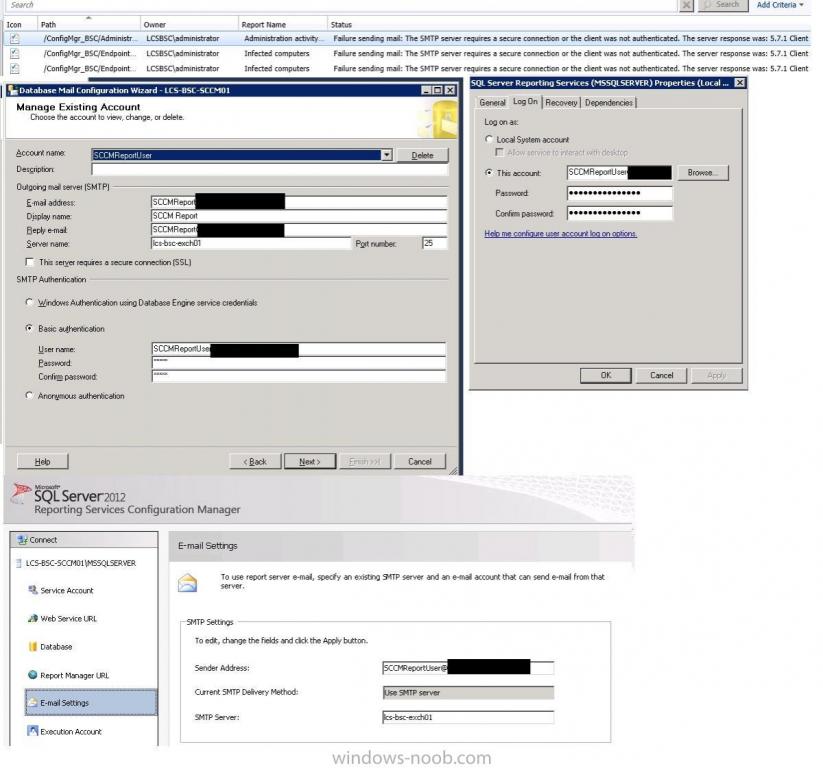
To summarise, I've created a report subscription which constantly fails with the Client was not authenticated, here's what I have done to try and resolve this issue:
- SCCM - Email Notification Component is configured correctly. The SMTP test works and I also receive alerts when one of my SCEP rules are triggered.
- SQL Management Studio - DataBase Mail is configured; sending a test e-mail works. Using Basic Authentication with a network account specified.
- Exchange 2010 has a Receiver Connector created to relay e-mails from the SCCM Server.
- Reporting Services Configuration Manager - Email Section has been completed.
- The SSRS Service is using a domain account with has an associated e-mail address and mailbox.
- Tried using anonymous authentication set on the Database Mail and also on the Exchange Receiver Connector - this actually stops Database Mail from from working.
I'm under the impression that if SSRS can send out test e-mails successfully, then SCCM should also work, as SCCM just uses SSRS to fire off those reports i'm subscribing to?
I've attached the screenshots of the various configurations within SCCM and also SQL 2012.
I've been bashing my head on this one for hours without any progress, so any advice is welcome!
-
I've just setup SCUP 2011 on my SCCM 2012 (2008 R2) server and managed to do the following:
- Configured: WSUS on same server, connected to Config Manager.
- Downloaded Adobe Updates via the SCUP Catalogue.
- Got the updates Published to SCCM 2012 and assigned to a Package and Software Group within SCCM
- Exported the WSUS cert and reimported as Trusted Publisher and Root on the test client and also the server.
- Assigned deployment to test collection that has one computer in need of those updates.
However, on the client itself, I cannot get it to detect and download the relevant updates for Adobe Reader, I've been trawling through the logs looking for evidence that the updates were detected and downloaded, and also manually checked the ccmcache and also (WSUS) softwaredownload folders, all had no downloaded files or references of the Adobe updates.
I can't think of anything else and there is nothing obvious in the logs that I can see, hopefully someone with experience can point me in the right direction?
The client has the following set via a test GPO:
AcceptTrustedPublisherCerts = 1
WUServer = http:sccm-server:80
WUStatusServer = http:sccm-server:80
UpdatesHandler.log
Successfully initiated scan. UpdatesHandler 08/04/2013 13:33:39 4036 (0x0FC4)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 13:33:39 3608 (0x0E18)
Successfully initiated scan. UpdatesHandler 08/04/2013 13:33:39 3608 (0x0E18)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 13:33:40 4036 (0x0FC4)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 13:33:44 4980 (0x1374)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 13:33:48 3608 (0x0E18)
Successfully initiated scan. UpdatesHandler 08/04/2013 13:33:49 3608 (0x0E18)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 13:34:54 4980 (0x1374)
CUpdatesAgent::FinalConstruct entered UpdatesHandler 08/04/2013 14:50:07 3332 (0x0D04)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 14:56:43 3524 (0x0DC4)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 14:56:43 3108 (0x0C24)
Successfully initiated scan. UpdatesHandler 08/04/2013 14:56:43 3524 (0x0DC4)
Successfully initiated scan. UpdatesHandler 08/04/2013 14:56:43 3108 (0x0C24)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 14:56:43 3524 (0x0DC4)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 14:56:43 3416 (0x0D58)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 15:31:26 3864 (0x0F18)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 15:31:26 5916 (0x171C)
Successfully initiated scan. UpdatesHandler 08/04/2013 15:31:26 3864 (0x0F18)
Successfully initiated scan. UpdatesHandler 08/04/2013 15:31:26 5916 (0x171C)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 15:32:20 5232 (0x1470)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 15:32:21 5232 (0x1470)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:24:32 4816 (0x12D0)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:24:32 3068 (0x0BFC)
Successfully initiated scan. UpdatesHandler 08/04/2013 16:24:32 4816 (0x12D0)
Successfully initiated scan. UpdatesHandler 08/04/2013 16:24:33 3068 (0x0BFC)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:25:21 4824 (0x12D8)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:25:21 3068 (0x0BFC)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:30:13 3744 (0x0EA0)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:30:13 4824 (0x12D8)
Successfully initiated scan. UpdatesHandler 08/04/2013 16:30:13 3744 (0x0EA0)
Successfully initiated scan. UpdatesHandler 08/04/2013 16:30:13 4824 (0x12D8)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:30:19 2160 (0x0870)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:30:21 3744 (0x0EA0)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:39:13 4016 (0x0FB0)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:39:13 4572 (0x11DC)
Successfully initiated scan. UpdatesHandler 08/04/2013 16:39:13 4016 (0x0FB0)
Successfully initiated scan. UpdatesHandler 08/04/2013 16:39:13 4572 (0x11DC)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:40:02 2524 (0x09DC)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:40:02 2524 (0x09DC)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:54:11 5192 (0x1448)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:54:11 3692 (0x0E6C)
Successfully initiated scan. UpdatesHandler 08/04/2013 16:54:11 3692 (0x0E6C)
Successfully initiated scan. UpdatesHandler 08/04/2013 16:54:11 5192 (0x1448)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:55:14 5624 (0x15F8)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:55:15 4904 (0x1328)
CUpdatesAgent::FinalConstruct entered UpdatesHandler 08/04/2013 17:09:42 2604 (0x0A2C)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:11:17 4780 (0x12AC)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:11:17 4872 (0x1308)
Successfully initiated scan. UpdatesHandler 08/04/2013 17:11:18 4872 (0x1308)
Successfully initiated scan. UpdatesHandler 08/04/2013 17:11:18 4780 (0x12AC)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:13:03 3812 (0x0EE4)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:13:03 4780 (0x12AC)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:13:37 3812 (0x0EE4)
Successfully initiated scan. UpdatesHandler 08/04/2013 17:13:37 3812 (0x0EE4)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:13:37 4780 (0x12AC)
Successfully initiated scan. UpdatesHandler 08/04/2013 17:13:37 4780 (0x12AC)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:14:16 5180 (0x143C)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:14:16 1056 (0x0420)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C)
Successfully initiated scan. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C)
Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C)
Successfully initiated scan. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:47:07 4500 (0x1194)
Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:47:07 964 (0x03C4)UpdatesDeployment.log
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_499fc6e1-f6de-4e4c-b98d-41ca21bee49b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e93c80ff-812b-4640-a7fb-d3712b86e3b1) added to the targeted list of deployment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B}) UpdatesDeploymentAgent 08/04/2013 16:55:15 5624 (0x15F8)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_49ddec56-93f2-48e7-98af-ecd54526d34c) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_5c22235f-a3d9-48db-95eb-a60ec1886e8e) added to the targeted list of deployment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B}) UpdatesDeploymentAgent 08/04/2013 16:55:15 5624 (0x15F8)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9e40eb5c-184a-494d-be46-8b140386179b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_da767d4a-8677-4b9d-9f0b-365f14e19ae1) added to the targeted list of deployment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B}) UpdatesDeploymentAgent 08/04/2013 16:55:15 5624 (0x15F8)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_d0fbac2f-d08f-4a7b-a826-92b1c5ae0bc5) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328)
EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 0 UpdatesDeploymentAgent 08/04/2013 16:56:29 2892 (0x0B4C)
User logoff system task UpdatesDeploymentAgent 08/04/2013 17:03:45 4708 (0x1264)
Service startup system task UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C)
Software Updates feature is enabled UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C)
Total Pending reboot updates = 0 UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C)
No pending reboot updates at system restart. UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C)
No current service window available to run updates assignment with time required = 1 UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C)
CUpdateAssignmentsManager::OnThirdPartyOrchestrationSettingChange - No pending install assignment UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C)
Startup task completed UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C)
User logon system task UpdatesDeploymentAgent 08/04/2013 17:09:50 988 (0x03DC)
Assignment {0ADCDD92-9E6F-4796-AFFD-7013EB4E554B} has total CI = 20 UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
OnPolicyDelete for assignment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B})... UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_27fc50b4-5982-4d58-a13d-53bd1f3806ea", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_957317cf-ef0d-4fa7-a2ad-5d2db2cf355e", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_1f6d4200-fcb6-4a4c-8ad7-ab76c529bff3", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_7ad922e0-685f-4723-9da3-4d7acefb4706", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e9e8a81d-ed5a-4af3-963e-2dc4413e3c3e", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_42cc6726-c3fe-464b-b8ac-38ec00766262", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_f51bc4bd-7424-4c47-ae97-714a8e3895b5", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_04874d8a-71a5-43d9-8531-eb19fdf319e6", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_0e79069c-cdca-4c91-aad3-e21ede710634", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_6d8590bd-038e-4455-9764-30875ccbf0c7", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_02fe5101-40eb-4d91-aa9d-5727060aefba", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_07151137-3b83-4064-8fc2-7bf983d6b08b", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_421e86ff-37e0-4199-9a0c-4976332bbcdf", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_521d70cd-3256-4c26-96f8-b7c3c4adc113", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9b65fe9a-721e-4390-860d-02c1dbffa10f", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9caf7699-d7f8-4cbb-95c9-002cbe3df07d", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_022d7dab-a021-4318-9c71-16323944584d", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e93c80ff-812b-4640-a7fb-d3712b86e3b1", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_5c22235f-a3d9-48db-95eb-a60ec1886e8e", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_da767d4a-8677-4b9d-9f0b-365f14e19ae1", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4)
EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 0 UpdatesDeploymentAgent 08/04/2013 17:10:10 3484 (0x0D9C)
Message received: '<?xml version='1.0' ?><SoftwareUpdatesMessage MessageType='EvaluateAssignments'><UseCachedResults>False</UseCachedResults></SoftwareUpdatesMessage>' UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0)
Removing scan history to force non cached results UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0)
Assignment {47ABB848-E3B5-405B-AA5E-01514176142F} has total CI = 7 UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0)
Detection job ({C92EAD93-F8F7-4257-BD47-FF953B523427}) started for assignment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0)
Started evaluation for assignment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0)
Assignment {28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C} has total CI = 20 UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0)
Detection job ({4BDCE35B-6B75-4DE8-BB1D-9ADD513CA2D0}) started for assignment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0)
Started evaluation for assignment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0)
Evaluation initiated for (2) assignments. UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0)
DetectJob completion received for assignment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:03 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9703dec9-deaf-4566-b966-aeca447a4ba4) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_a13356e5-6224-44e0-9020-9a3c924da131) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_244b7a38-eb9e-4632-a299-b085587d477c) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_499fc6e1-f6de-4e4c-b98d-41ca21bee49b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_49ddec56-93f2-48e7-98af-ecd54526d34c) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9e40eb5c-184a-494d-be46-8b140386179b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_d0fbac2f-d08f-4a7b-a826-92b1c5ae0bc5) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
DetectJob completion received for assignment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_27fc50b4-5982-4d58-a13d-53bd1f3806ea) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_957317cf-ef0d-4fa7-a2ad-5d2db2cf355e) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_1f6d4200-fcb6-4a4c-8ad7-ab76c529bff3) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_7ad922e0-685f-4723-9da3-4d7acefb4706) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e9e8a81d-ed5a-4af3-963e-2dc4413e3c3e) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_42cc6726-c3fe-464b-b8ac-38ec00766262) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_f51bc4bd-7424-4c47-ae97-714a8e3895b5) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_04874d8a-71a5-43d9-8531-eb19fdf319e6) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_0e79069c-cdca-4c91-aad3-e21ede710634) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_6d8590bd-038e-4455-9764-30875ccbf0c7) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_02fe5101-40eb-4d91-aa9d-5727060aefba) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_07151137-3b83-4064-8fc2-7bf983d6b08b) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_421e86ff-37e0-4199-9a0c-4976332bbcdf) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_521d70cd-3256-4c26-96f8-b7c3c4adc113) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9b65fe9a-721e-4390-860d-02c1dbffa10f) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC)
Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9caf7699-d7f8-4cbb-95c9-002cbe3df07d) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04WUAHandler.log
Async searching completed. WUAHandler 08/04/2013 15:32:17 4964 (0x1364)
Successfully completed scan. WUAHandler 08/04/2013 15:32:19 1032 (0x0408)
Scan results will include all superseded updates. WUAHandler 08/04/2013 15:32:20 1044 (0x0414)
Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 15:32:20 1044 (0x0414)
Async searching of updates using WUAgent started. WUAHandler 08/04/2013 15:32:20 1044 (0x0414)
Async searching completed. WUAHandler 08/04/2013 15:32:20 4960 (0x1360)
Successfully completed scan. WUAHandler 08/04/2013 15:32:20 1044 (0x0414)
Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 16:24:30 4816 (0x12D0)
Existing WUA Managed server was already set (http://:80), skipping Group Policy registration. WUAHandler 08/04/2013 16:30:21 2160 (0x0870)
Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 16:30:21 2160 (0x0870)
Scan results will include all superseded updates. WUAHandler 08/04/2013 16:30:21 2160 (0x0870)
Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 16:30:21 2160 (0x0870)
Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:30:21 2160 (0x0870)
Async searching completed. WUAHandler 08/04/2013 16:31:08 1096 (0x0448)
Successfully completed scan. WUAHandler 08/04/2013 16:31:11 3744 (0x0EA0)
Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0)
Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0)
Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0)
Scan results will include all superseded updates. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0)
Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0)
Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0)
Async searching completed. WUAHandler 08/04/2013 16:39:58 3424 (0x0D60)
Successfully completed scan. WUAHandler 08/04/2013 16:40:00 4016 (0x0FB0)
Scan results will include all superseded updates. WUAHandler 08/04/2013 16:40:01 6024 (0x1788)
Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 16:40:01 6024 (0x1788)
Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:40:01 6024 (0x1788)
Async searching completed. WUAHandler 08/04/2013 16:40:01 4956 (0x135C)
Successfully completed scan. WUAHandler 08/04/2013 16:40:01 6024 (0x1788)
Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 16:54:09 5244 (0x147C)
Enabling WUA Managed server policy to use server: http://sccmserver:80 WUAHandler 08/04/2013 16:54:09 5244 (0x147C)
Waiting for 2 mins for Group Policy to notify of WUA policy change... WUAHandler 08/04/2013 16:54:09 5244 (0x147C)
Waiting for 30 secs for policy to take effect on WU Agent. WUAHandler 08/04/2013 16:54:16 5244 (0x147C)
Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 16:54:46 5244 (0x147C)
Scan results will include all superseded updates. WUAHandler 08/04/2013 16:54:46 5244 (0x147C)
Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 16:54:46 5244 (0x147C)
Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:54:46 5244 (0x147C)
Async searching completed. WUAHandler 08/04/2013 16:55:11 5944 (0x1738)
Successfully completed scan. WUAHandler 08/04/2013 16:55:13 5624 (0x15F8)
Scan results will include all superseded updates. WUAHandler 08/04/2013 16:55:14 5244 (0x147C)
Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 16:55:14 5244 (0x147C)
Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:55:14 5244 (0x147C)
Async searching completed. WUAHandler 08/04/2013 16:55:14 5516 (0x158C)
Successfully completed scan. WUAHandler 08/04/2013 16:55:14 4904 (0x1328)
CWuaHandler::SetCategoriesForLeafStateReportingExclusion called with E0789628-CE08-4437-BE74-2495B842F43B WUAHandler 08/04/2013 17:09:26 2604 (0x0A2C)
Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC)
Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC)
Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 17:11:15 4780 (0x12AC)
Scan results will include all superseded updates. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC)
Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 17:11:15 4780 (0x12AC)
Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC)
Async searching completed. WUAHandler 08/04/2013 17:13:00 4208 (0x1070)
Successfully completed scan. WUAHandler 08/04/2013 17:13:02 4780 (0x12AC)
Scan results will include all superseded updates. WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4)
Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'E1D507BE-497C-D8FD-61D7-B0D93EE399CA') OR (DeploymentAction=* AND Type='Software' AND CategoryIDs contains '3B36FCFD-0384-EA97-2D49-1349AE748647') OR (DeploymentAction=* AND Type='Software' AND CategoryIDs contains '70CFAD70-6629-B54B-5819-C809A605515E')) WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4)
Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4)
Async searching completed. WUAHandler 08/04/2013 17:13:03 4344 (0x10F8)
Successfully completed scan. WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4)
Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 17:13:34 1056 (0x0420)
Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 17:13:34 1056 (0x0420)
Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 17:13:34 1056 (0x0420)
Scan results will include all superseded updates. WUAHandler 08/04/2013 17:13:34 1056 (0x0420)
Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 17:13:34 1056 (0x0420)
Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:13:34 1056 (0x0420)
Async searching completed. WUAHandler 08/04/2013 17:14:13 5476 (0x1564)
Successfully completed scan. WUAHandler 08/04/2013 17:14:15 1056 (0x0420)
Scan results will include all superseded updates. WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4)
Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4)
Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4)
Async searching completed. WUAHandler 08/04/2013 17:14:16 5648 (0x1610)
Successfully completed scan. WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4)
Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 17:46:06 964 (0x03C4)
Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 17:46:06 964 (0x03C4)
Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 17:46:06 964 (0x03C4)
Scan results will include all superseded updates. WUAHandler 08/04/2013 17:46:06 964 (0x03C4)
Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 17:46:06 964 (0x03C4)
Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:46:06 964 (0x03C4)
Async searching completed. WUAHandler 08/04/2013 17:47:03 4948 (0x1354)
Successfully completed scan. WUAHandler 08/04/2013 17:47:05 964 (0x03C4)
Scan results will include all superseded updates. WUAHandler 08/04/2013 17:47:06 4764 (0x129C)
Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 17:47:06 4764 (0x129C)
Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:47:06 4764 (0x129C)
Async searching completed. WUAHandler 08/04/2013 17:47:06 5180 (0x143C)
Successfully completed scan. WUAHandler 08/04/2013 17:47:07 4764 (0x129C)UpdateStore.log
Update status from update (eb303398-da7c-4ce6-b8db-254409b32c39) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (eb30575d-51df-4c24-87dc-9b9c6dc8aa04) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (eb7a169f-6bca-4e00-a52a-623c063c162d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (ebbdc330-bd19-47b9-9e08-c4f32694429b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (ec1f4a29-8828-4fbe-b101-5a89321d8e7f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (edcc7a72-ffa0-4753-b59a-976044bbb012) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (efb911ae-5fba-48c7-8060-51734e3c1144) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f019d0aa-dfcf-4af8-b846-d38f8f7239e7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f0b50507-6c86-41d6-9350-6a8af21f76c7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f120b7a8-9ee3-4e95-8628-ac27b0d1df85) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f19502ff-7637-4ed8-bbc1-1b2508e56e2b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f1b1b1e1-2b22-4445-8a9c-5924bf945d32) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f21b0303-4d18-4a9b-9bda-8a796062189b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f284dc51-5659-4534-a1c7-6b9dbfe9453a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f2b28914-a6bc-44c5-ac04-9e7fbdea657e) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f2c6b0b8-f2cf-4f6c-8d64-6a21b9ca86d2) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f307ffeb-f424-4a79-8bc3-d472be542dec) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f45f3c72-427b-4889-a627-836244bf1ce1) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f4683760-71cc-4e3f-82a0-e1c164955163) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f51a0e5b-24a9-4be1-8b36-0f22f99949e7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f5202a56-ff34-401d-a040-f97c7f70891c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f53b1817-e327-438b-afb8-0cd5a0f95cb2) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f54ace97-a003-44a4-9e36-ef7071f6ce9d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f591538a-2c8f-4dc4-8b17-8b07c9a851ca) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f808dbaf-bec7-4dfb-a0cc-25290a7cd368) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (f9b10375-898c-4d12-8722-b2f7f6e81521) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (fabc6fae-c385-4543-a483-1b1cadfade98) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (fabea4ad-b256-4b4e-b9cf-988bcfd5463f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (fbc62e30-1128-4af5-9cb7-e1e349eb1b23) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (fc5608e4-a70d-4344-b358-2847f4a57434) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (fc5b1588-f912-4c1b-9f87-4ee1b427c5b1) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (fc7c3752-4c17-473c-8bff-75eed375fd61) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (fd8b7365-bc78-48e5-96c0-53682b94a607) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (fdc8ef3a-11eb-45e6-9e0e-38a193f7b48c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (ff1d0808-8bb8-47ea-90c4-f7e806f7bde0) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Successfully done with SetStatus() operation. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4)
Update status from update (097d6f40-e0dc-4410-893f-24d5326aed8a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (0aa3cf0a-2269-4356-ad99-0e3ca8eb439f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (0b92accc-057d-408a-8e6e-0867f21f015f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (138bccfd-40ac-4a5d-84f0-3e5bf9743e42) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (161ed7f2-9f54-4625-914c-2b3c93040db4) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (2b487f1d-e072-4be7-986c-4355c3372cd1) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (324f1032-de0c-406e-b611-34b99c64e21d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (3abe760c-4578-4c84-a1cb-bf1df019efe4) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (40bd5a76-a368-4088-b172-a9e5dd1e5e3a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (40ccd4f1-cc6f-4368-968b-29d10e57b05f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (48f658bc-fec4-4464-8f01-db68c5ab1720) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (596adb47-108d-482d-85ba-a513621434b7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (5eca77b2-63e0-4df3-b1b0-acb90f28c532) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (7079beeb-6120-4afd-ad07-fb4dfa284fbe) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (71a29c39-e160-4b00-9b2f-d9924c8e09d5) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (744f9366-c308-44b2-8542-ca31c229179d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (75914178-2bdf-4fd3-b537-e2a517734bc7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (79f342ab-66e7-42a7-8315-2677f99f20c5) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (7c25aee0-71f5-4fda-8763-effae905b564) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (82538218-b3eb-4c56-a9b8-fdb358869d2b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (979b9aa2-dcf8-45d6-a31d-63df2a02d043) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (97e091c7-35eb-4da0-9346-e6f33115c8ed) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (98c62b24-a3dd-4843-ad1a-e08d95624f00) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (a429515b-9216-4277-bd4d-bf0593542c0d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (a61bd9f9-6940-408c-a80e-5a7dc4f5e1a2) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (a643a7c6-aa86-480c-b9e8-7f9abca811e6) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (ac8b33b5-2df2-4e6a-8d48-105ba0cc3bff) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (af91fcf0-fc28-4293-acc6-598fdcea359a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (afdd5d5e-2cc2-4a6a-a44f-e45a275702f5) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (b047a38c-47a5-4ac7-b42a-0c4d80f3341c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (b14fba1c-2b3b-4746-8801-104180701e7e) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (b628f40e-33de-4a37-81ae-9c2868c75373) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (c6164205-7295-4670-8a2f-8dad2d0682b0) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (d7568b8a-3d37-43de-8d65-b6a0a73b010c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (de4cbbf4-443f-4bb7-aebf-8da2fcc7b706) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (e5cbc9ff-0953-4efc-8acc-6a130bd4385b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (eb30575d-51df-4c24-87dc-9b9c6dc8aa04) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Update status from update (fc5608e4-a70d-4344-b358-2847f4a57434) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Successfully done with SetStatus() operation. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C)
Querying update status of 20 updates. UpdatesStore 08/04/2013 17:47:07 4500 (0x1194)
Querying update status completed successfully. UpdatesStore 08/04/2013 17:47:07 4500 (0x1194)
Querying update status of 7 updates. UpdatesStore 08/04/2013 17:47:07 964 (0x03C4)
Querying update status completed successfully. UpdatesStore 08/04/2013 17:47:07 964 (0x03C4)
Querying update status of 20 updates. UpdatesStore 08/04/2013 18:01:00 6032 (0x1790)
Querying update status completed successfully. UpdatesStore 08/04/2013 18:01:00 6032 (0x1790)
Querying update status of 20 updates. UpdatesStore 08/04/2013 18:01:00 3748 (0x0EA4)
Querying update status completed successfully. UpdatesStore 08/04/2013 18:01:00 3748 (0x0EA4)



Updates Missing, Not Downloaded into CCMCACHE but also No Errors?
in System Center Configuration Manager (Current Branch)
Posted
Hi All,
Need some guidance on this one as it has me puzzled and I must be overlooking something.
Started a new role and in the environment we have a fair number of servers across the board that are not downloading software updates and are in the dreaded Client check passed/Active UNKNOWN state in the Deployment status. The CCMCACHE remains empty bar the ccmsetup.exe, however, all relevant logs do not contain any errors whatsoever.
I have completely uninstalled the CCM client cleanly (including renaming of CCM/CCMCACHE folder), removed the Server’s device object from the SCCM console, reinstalled the client and waited for the device object to repopulate. Fast forward 24 hours, the Device Object reports fine and looks fine, Control Panel applet looks fine on the server, Deployments tab list updates that it has picked up from inherited Device Collections yet the same symptoms appear.
UpdatesStore.log indicates that the server performed SU evaluation and has identified at least one patch that it is missing. I manually checked and the patch is in an active Software Update deployment targeted at the server in question, also this update appears in the deployments tab of the device object in SCCM.
But with all that said, I don’t see any attempts to connect to a DP to download the source content; nothing in UpdatesDeployment or LocationServices logs. If the content was not available at the designated DP it would display a unique error for that, but I don't see any references to DPs at all.
The only thing in the CCMCACHE folder is a single folder containing the ccmsetup.exe file?
Out of the entire UpdateStore.log Update for Microsoft Silverlight (KB4481252) is the only update that is missing. I've manually checked that this update is in an Active Deployment targeting a collection that the server is a member of, of which the software update is Deployed as Required also.
Can someone point me to the next thing I should check?
SCCM v1810
Some (small) excerpts of the logs:
UpdatesStore.log Querying update status of 2 updates. UpdatesStore 28/03/2019 09:29:37 4236 (0x108C) Queried Update (1ccbf8d2-e571-44a9-bbfe-b9bef824cd4a): Status=Missing, Title=Update for Microsoft Silverlight (KB4481252), BulletinID=, QNumbers=4481252, LocaleID=, ProductID=9f3dd20a-1004-470e-ba65-3dc62d982958, UpdateClassification = 28bc880e-0592-4cbf-8f95-c79b17911d5f, ExcludeForStateReporting=FALSE. UpdatesStore 28/03/2019 09:29:37 4236 (0x108C) Queried Update (b9887966-c14d-4a16-9c6f-196f30b29a30): Status=Missing, Title=Update for Microsoft Silverlight (KB4481252), BulletinID=, QNumbers=4481252, LocaleID=, ProductID=9f3dd20a-1004-470e-ba65-3dc62d982958, UpdateClassification = 28bc880e-0592-4cbf-8f95-c79b17911d5f, ExcludeForStateReporting=FALSE. UpdatesStore 28/03/2019 09:29:37 4236 (0x108C) Querying update status completed successfully. UpdatesStore 28/03/2019 09:29:37 4236 (0x108C) UpdatesHandler.log OnJobRestart Job ({25883751-5C83-4E09-8E8F-D46AD0BF61EC}) - State = 1 UpdatesHandler 28/03/2019 09:29:37 7264 (0x1C60) Initiating Scan. Forced = (1) UpdatesHandler 28/03/2019 09:29:37 7264 (0x1C60) Successfully initiated scan for job ({25883751-5C83-4E09-8E8F-D46AD0BF61EC}). UpdatesHandler 28/03/2019 09:29:37 7264 (0x1C60) Reconnecting to the Job {EB10B4F8-25CA-427A-8B5C-F88A8E6F4AB7} UpdatesHandler 28/03/2019 09:29:37 4236 (0x108C) Reconnected job with id = {EB10B4F8-25CA-427A-8B5C-F88A8E6F4AB7} UpdatesHandler 28/03/2019 09:29:37 4236 (0x108C) OnJobRestart Job ({EB10B4F8-25CA-427A-8B5C-F88A8E6F4AB7}) - State = 1 UpdatesHandler 28/03/2019 09:29:37 4236 (0x108C) Initiating Scan. Forced = (1) UpdatesHandler 28/03/2019 09:29:37 4236 (0x108C) Successfully initiated scan for job ({EB10B4F8-25CA-427A-8B5C-F88A8E6F4AB7}). UpdatesHandler 28/03/2019 09:29:37 4236 (0x108C) UpdatesDeployment.log EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 0 UpdatesDeploymentAgent 28/03/2019 10:33:52 4184 (0x1058) CUpdateAssignmentsManager received a SERVICEWINDOWEVENT START Event UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) No current service window available to run updates assignment with time required = 1 UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) No current or future service window available to run updates assignment with time required = 1 UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) Suspend activity in presentation mode is selected UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) At least one user has elected to suspend non-business hours activity when in presentation mode. Checking for presentation mode. UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) Proceeding to non-business hours activites as presentation mode is off. UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) Auto install during non-business hours is disabled or never set, selecting only scheduled updates. UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) A user-defined service window(non-business hours) is available. We will attempt to install any scheduled updates. UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) Attempting to install 0 updates UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) Unable to find CCM_PrePostActions.SiteSettingsKey=1. UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) GetActions() did not succeed. 80070490. UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) No actionable updates for install task. No attempt required. UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) Updates could not be installed at this time. Waiting for the next maintenance window. UpdatesDeploymentAgent 28/03/2019 22:00:00 7408 (0x1CF0) CUpdateAssignmentsManager received a SERVICEWINDOWEVENT END Event UpdatesDeploymentAgent 29/03/2019 05:00:00 4472 (0x1178) No current service window available to run updates assignment with time required = 1 UpdatesDeploymentAgent 29/03/2019 05:00:00 4472 (0x1178) Attempting to cancel any job started at non-business hours. UpdatesDeploymentAgent 29/03/2019 05:00:00 4472 (0x1178) CEvalO365ManagementTask::Execute() UpdatesDeploymentAgent 29/03/2019 09:41:35 6340 (0x18C4) Not RS3+, this device is SCCM managed. UpdatesDeploymentAgent 29/03/2019 09:41:35 6340 (0x18C4) LocationServices.log Current AD site of machine is Virtual-DC LocationServices 29/03/2019 09:39:39 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 09:39:39 7216 (0x1C30) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 09:39:39 7864 (0x1EB8) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 09:39:39 620 (0x026C) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 09:39:39 7864 (0x1EB8) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 09:39:39 7216 (0x1C30) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 09:39:39 620 (0x026C) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 09:39:40 7864 (0x1EB8) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 09:39:40 7216 (0x1C30) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 09:39:40 7216 (0x1C30) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 09:39:40 7864 (0x1EB8) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 09:39:40 620 (0x026C) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 09:39:40 620 (0x026C) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 09:39:41 7864 (0x1EB8) Executing Task LSRefreshLocationsTask LocationServices 29/03/2019 10:39:38 1816 (0x0718) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 10:39:38 1816 (0x0718) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 10:39:39 1816 (0x0718) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 10:39:39 1816 (0x0718) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 10:39:39 1816 (0x0718) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 10:39:39 1816 (0x0718) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 10:39:39 1816 (0x0718) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 10:39:39 1816 (0x0718) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 10:39:39 1816 (0x0718) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 10:39:39 1816 (0x0718) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 10:39:39 1816 (0x0718) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 10:39:39 1816 (0x0718) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 10:39:39 1816 (0x0718) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 10:39:39 6340 (0x18C4) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 10:39:39 7864 (0x1EB8) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 10:39:39 6340 (0x18C4) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 10:39:39 7952 (0x1F10) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 10:39:40 1816 (0x0718) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 10:39:40 7864 (0x1EB8) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 10:39:40 7864 (0x1EB8) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 10:39:40 7952 (0x1F10) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 10:39:40 1816 (0x0718) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 10:39:40 6340 (0x18C4) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 10:39:40 7864 (0x1EB8) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 10:39:41 7952 (0x1F10) Executing Task LSRefreshLocationsTask LocationServices 29/03/2019 11:39:38 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 11:39:38 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 11:39:38 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 11:39:38 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 11:39:38 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 11:39:38 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 11:39:38 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 11:39:39 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 11:39:39 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 11:39:39 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 11:39:39 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 11:39:39 7216 (0x1C30) Current AD site of machine is Virtual-DC LocationServices 29/03/2019 11:39:39 7216 (0x1C30) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 11:39:39 7952 (0x1F10) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 11:39:39 1816 (0x0718) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 11:39:39 7216 (0x1C30) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 11:39:39 4864 (0x1300) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 11:39:39 7952 (0x1F10) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 11:39:39 4864 (0x1300) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 11:39:40 7952 (0x1F10) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 11:39:40 1816 (0x0718) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 11:39:40 7216 (0x1C30) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 11:39:40 1816 (0x0718) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 11:39:40 7952 (0x1F10) ConfigMgr is no longer managing WindowsDO GPO. Set to default values. Mode = LAN. GroupID = empty LocationServices 29/03/2019 11:39:40 4864 (0x1300) ContentTransfer.log CTM job {B9F53641-1AE2-490D-87BA-1CBD325D2746} (corresponding DTS job {B18ABC87-02BF-4985-A326-C1FC65F0A74E}) started download from 'http:// ConfigServer04.domain /SMS_DP_SMSPKG$/PCM00003' for full content download. ContentTransferManager 27/03/2019 12:56:30 5996 (0x176C) CTM job {B9F53641-1AE2-490D-87BA-1CBD325D2746} entered phase CCM_DOWNLOADSTATUS_DOWNLOADING_MANIFEST ContentTransferManager 27/03/2019 12:56:30 3664 (0x0E50) CTM job {B9F53641-1AE2-490D-87BA-1CBD325D2746} entered phase CCM_DOWNLOADSTATUS_PROCESSING_MANIFEST ContentTransferManager 27/03/2019 12:56:30 5996 (0x176C) CTM job {B9F53641-1AE2-490D-87BA-1CBD325D2746} entered phase CCM_DOWNLOADSTATUS_PREPARING_DOWNLOAD ContentTransferManager 27/03/2019 12:56:30 776 (0x0308) CTM job {B9F53641-1AE2-490D-87BA-1CBD325D2746} entered phase CCM_DOWNLOADSTATUS_DOWNLOADING_DATA ContentTransferManager 27/03/2019 12:56:30 5124 (0x1404) CTM job {B9F53641-1AE2-490D-87BA-1CBD325D2746} successfully processed download completion. ContentTransferManager 27/03/2019 12:56:49 5124 (0x1404) In CTMAggregateDownloadHistoryTask::Execute, preparing to aggregate and send download history to server. ContentTransferManager 27/03/2019 13:01:26 7600 (0x1DB0) Sending client download history summary XML with character length of 645. ContentTransferManager 27/03/2019 13:01:26 7600 (0x1DB0) This client will report download history every 1440 min. ContentTransferManager 28/03/2019 09:29:36 6720 (0x1A40) In CTMAggregateDownloadHistoryTask::Execute, preparing to aggregate and send download history to server. ContentTransferManager 28/03/2019 09:49:36 7264 (0x1C60) Sending client download history summary XML with character length of 645. ContentTransferManager 28/03/2019 09:49:36 7264 (0x1C60) In CTMAggregateDownloadHistoryTask::Execute, preparing to aggregate and send download history to server. ContentTransferManager 29/03/2019 09:49:34 6340 (0x18C4) Not reporting any download events to server. No recent downloads found. ContentTransferManager 29/03/2019 09:49:34 6340 (0x18C4) CAS.log =========================================================== ContentAccess 28/03/2019 09:29:05 7496 (0x1D48) Superpeercontroller agent stopping ContentAccess 28/03/2019 09:29:05 7496 (0x1D48) The thread is not yet started or already stopped, so no need to stop it again here. ContentAccess 28/03/2019 09:29:05 7496 (0x1D48) SuperPeerController has stopped ContentAccess 28/03/2019 09:29:05 7496 (0x1D48) =========================================================== ContentAccess 28/03/2019 09:29:36 5028 (0x13A4) WinPEBranchCacheStartup task is starting... ContentAccess 28/03/2019 09:29:36 5028 (0x13A4) CSuperPeerController::FinalConstruct entered ContentAccess 28/03/2019 09:29:36 5028 (0x13A4) Un-configuring cache size. ContentAccess 28/03/2019 09:29:36 5028 (0x13A4) Not starting superpeer agent since the client agent setting for superpeer is disabled ContentAccess 28/03/2019 09:29:36 5028 (0x13A4) ===== CacheManager: Initializing cache state from Wmi. ===== ContentAccess 28/03/2019 09:29:40 5028 (0x13A4) Cache size is 5120 MB. Location is C:\Windows\ccmcache ContentAccess 28/03/2019 09:29:40 5028 (0x13A4) CacheManager: MaxCacheDuration:43200 - MinTombstoneDuration:1440 ContentAccess 28/03/2019 09:29:40 5028 (0x13A4) CacheManager: There are currently 4074496 bytes used for cached content items (1 total, 1 active, 0 tombstoned, 0 expired). ContentAccess 28/03/2019 09:29:40 5028 (0x13A4) ===== CacheManager: Cache state initialization completed ===== ContentAccess 28/03/2019 09:29:40 5028 (0x13A4) DataTransferService.log UpdateURLWithTransportSettings(): OLD URL - http://ConfigServer05.domain/SMS_MP DataTransferService 29/03/2019 04:29:39 7216 (0x1C30) UpdateURLWithTransportSettings(): NEW URL - http:// ConfigServer05.domain:80/SMS_MP DataTransferService 29/03/2019 04:29:39 7216 (0x1C30) Added (source=.sms_pol?{09d3b615-62a8-4300-b6a3-5c6941d40f1f}.5717_00,dest={3B976522-D24B-4D48-8772-E7C4073B6B8F}.tmp) pair from manifest. DataTransferService 29/03/2019 04:29:39 7216 (0x1C30) DTSJob {629109FE-31FB-4FBE-A79E-A85EF5D28F6D} created to download from 'http:// ConfigServer05.domain:80/SMS_MP' to 'C:\Windows\CCM\Temp'. DataTransferService 29/03/2019 04:29:39 7216 (0x1C30) DTSJob {629109FE-31FB-4FBE-A79E-A85EF5D28F6D} in state 'PendingDownload'. DataTransferService 29/03/2019 04:29:39 7864 (0x1EB8) DTSFlag is 0x0020bc8a DataTransferService 29/03/2019 04:29:39 7864 (0x1EB8) Exclude file list: DataTransferService 29/03/2019 04:29:39 7864 (0x1EB8) Using branch cache option DataTransferService 29/03/2019 04:29:39 7864 (0x1EB8) DTSJob {629109FE-31FB-4FBE-A79E-A85EF5D28F6D} in state 'DownloadingData'. DataTransferService 29/03/2019 04:29:39 7864 (0x1EB8) DTSJob {629109FE-31FB-4FBE-A79E-A85EF5D28F6D} in state 'RetrievedData'. DataTransferService 29/03/2019 04:29:45 7936 (0x1F00) DTSJob {629109FE-31FB-4FBE-A79E-A85EF5D28F6D} successfully completed download. DataTransferService 29/03/2019 04:29:45 7936 (0x1F00) DTSJob {629109FE-31FB-4FBE-A79E-A85EF5D28F6D} in state 'NotifiedComplete'. DataTransferService 29/03/2019 04:29:45 7864 (0x1EB8) DTS job {629109FE-31FB-4FBE-A79E-A85EF5D28F6D} has completed: Status : SUCCESS, Start time : 03/29/2019 04:29:39, Completion time : 03/29/2019 04:29:45, Elapsed time : 6 seconds DataTransferService 29/03/2019 04:29:45 7864 (0x1EB8) UpdateURLWithTransportSettings(): OLD URL - http:// ConfigServer05.domain /SMS_MP DataTransferService 29/03/2019 08:55:39 7864 (0x1EB8) UpdateURLWithTransportSettings(): NEW URL - http:// ConfigServer05.domain:80/SMS_MP DataTransferService 29/03/2019 08:55:39 7864 (0x1EB8) Added (source=.sms_pol?{09d3b615-62a8-4300-b6a3-5c6941d40f1f}.5718_00,dest={1BCA6517-5EF4-4436-83A4-84AA6544E2E2}.tmp) pair from manifest. DataTransferService 29/03/2019 08:55:39 7864 (0x1EB8) DTSJob {3E552E27-06C7-472B-80C5-D3089FBCC0F3} created to download from 'http:// ConfigServer05.domain:80/SMS_MP' to 'C:\Windows\CCM\Temp'. DataTransferService 29/03/2019 08:55:39 7864 (0x1EB8) DTSJob {3E552E27-06C7-472B-80C5-D3089FBCC0F3} in state 'PendingDownload'. DataTransferService 29/03/2019 08:55:39 3960 (0x0F78) DTSFlag is 0x0020bc8a DataTransferService 29/03/2019 08:55:39 6340 (0x18C4) Exclude file list: DataTransferService 29/03/2019 08:55:39 6340 (0x18C4) Using branch cache option DataTransferService 29/03/2019 08:55:39 6340 (0x18C4) DTSJob {3E552E27-06C7-472B-80C5-D3089FBCC0F3} in state 'DownloadingData'. DataTransferService 29/03/2019 08:55:39 6340 (0x18C4) DTSJob {3E552E27-06C7-472B-80C5-D3089FBCC0F3} in state 'RetrievedData'. DataTransferService 29/03/2019 08:55:45 6448 (0x1930) DTSJob {3E552E27-06C7-472B-80C5-D3089FBCC0F3} successfully completed download. DataTransferService 29/03/2019 08:55:45 6448 (0x1930) DTSJob {3E552E27-06C7-472B-80C5-D3089FBCC0F3} in state 'NotifiedComplete'. DataTransferService 29/03/2019 08:55:45 7864 (0x1EB8) DTS job {3E552E27-06C7-472B-80C5-D3089FBCC0F3} has completed: Status : SUCCESS, Start time : 03/29/2019 08:55:39, Completion time : 03/29/2019 08:55:45, Elapsed time : 6 seconds DataTransferService 29/03/2019 08:55:45 7864 (0x1EB8)