
Welcome to windows-noob.com!
Logging in will allow you to download scripts used in the guides.
If you came here looking for the Endpoint Manager step-by-step guides then please start here.
Register for free and ask your questions in our forums.
- 4 replies
- 310 views
- Add Reply
- 0 replies
- 180 views
- Add Reply
- 0 replies
- 458 views
- Add Reply
- 1 reply
- 665 views
- Add Reply
- 5 replies
- 1,258 views
- Add Reply
- 2 replies
- 2,051 views
- Add Reply
- 23 replies
- 6,790 views
- Add Reply
- 1 reply
- 4,954 views
- Add Reply
Issue with Bilocker Administration and Monitoring and "Reports"
By keywan,
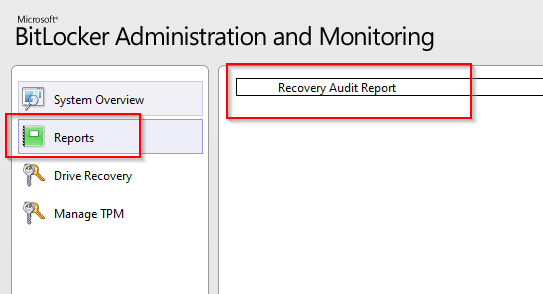

Hi,
I am really not sure why my Reports Button on Bilocker Administration and Monitoring does not work
If I do start the report server on the SCCM server, it is working
http://cmmgr:80/ReportServer
or if I connect to
http://cmmgr:80/Reports
What is wrog here?
Thank you fro help
Issue with Bitlocker Administration and Monitoring
By keywan,
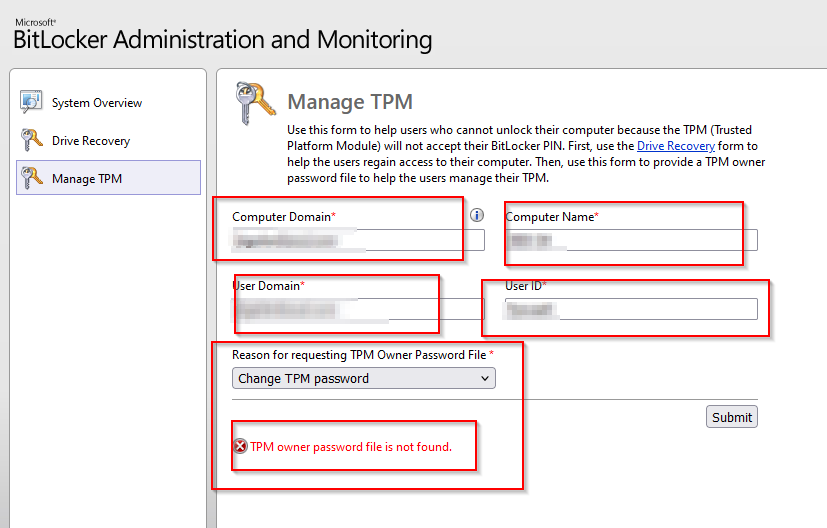

Hi,
I have a issue with Bitlocker Administration and Monitoring, if I go to "Manage TPM" and put my information's and want to reset the TPM password, getting the Error
"The TPM owner password file is not found"
Any Idea?
Deploy a Application on specific Windows machine when the user has logged in to multiple machines with the same user account
By keywan,
Hi,
I want to deploy a Application (with approval option on User Collections) on specific Windows machine when the user has logged in to multiple machines with the same user account.
It mean as following:
- Device A (Windows 10) , User A
- Device B (Windows 10, User A (same user account)
The user A log to the Device A and Device B, I deploy for example "ZOOM" on User Collections( here User A) but the User A can see on the Software only on Device A and not on Device B.
Logon Error using run as service account in task sequence
By pamulli,
I have a standalone task sequence that is not part of OSD so there is no domain join step and I'm trying to use a valid service account to run a script, but it's getting a logon error. The exact same step is copied out of an OSD task sequence with a domain join step and it works fine in the source task sequence. From some research, it seems the issue is that it needs the domain join account/step in order to be able to validate the account credentials. So my question is, how can I do this with a
SCCM and Bitlocker migration, failing with error code 18
By NSCOTT,
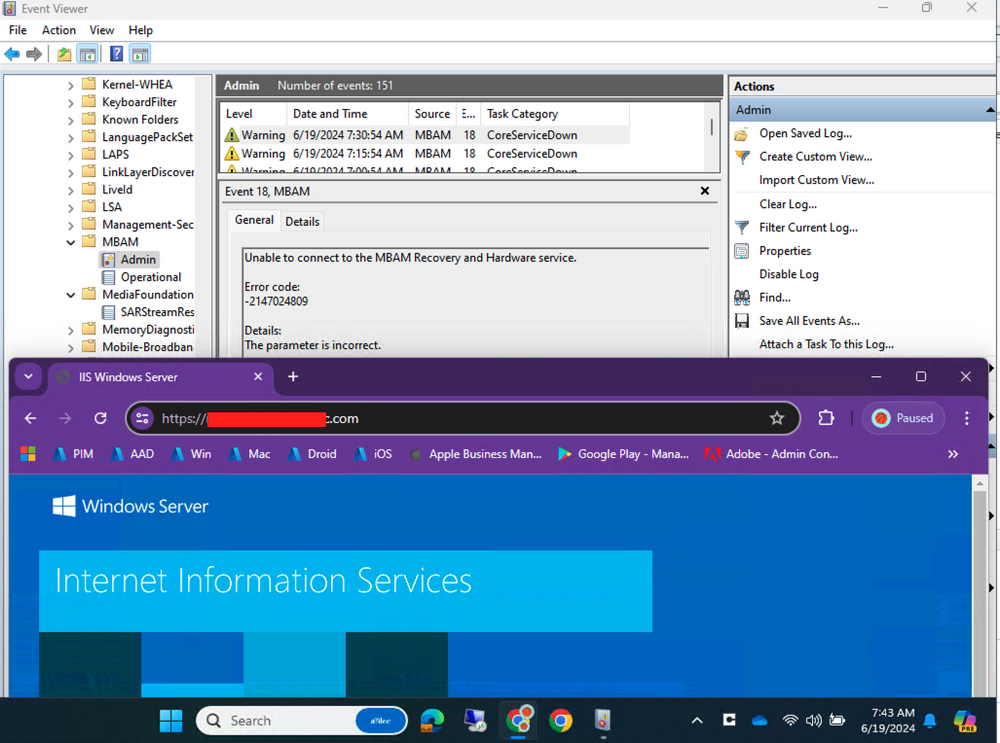

I'm really confused and need some assistance. Long story short, we've been using straight GPO's for bitlocker forever. Management wants some reports that i cannot currently generate without SCCM or MBAM ingesting this service... as MBAM is going away in the future, so i'm just importing it all, or trying, into SCCM.
- Computer
1. Decrypted the drive
2. Tossed the computer into an OU that has absolutely no bitlocker policies enabled (verified via RSOP)
- SCCM / MP
- s
Assistance with eHTTP Certificates and Spoofing/Forging
By NullSID,
Hi Folks!
I'm working with a customer that has an SCCM environment, (2309). Currently setup as eHTTP. We are working through the logistics with Security on setting up a CMG, but on a side note they've asked some questions that I'm not 100% positive how to answer. The first question being: "How do the Self Signed Certs protect against spoofing/forging?"
My assumption is that the signing certificate on the client validates the policies sent from the MP were not tampered with in any way.
SCCM 2403 and MDT and UDI Issue
By keywan,
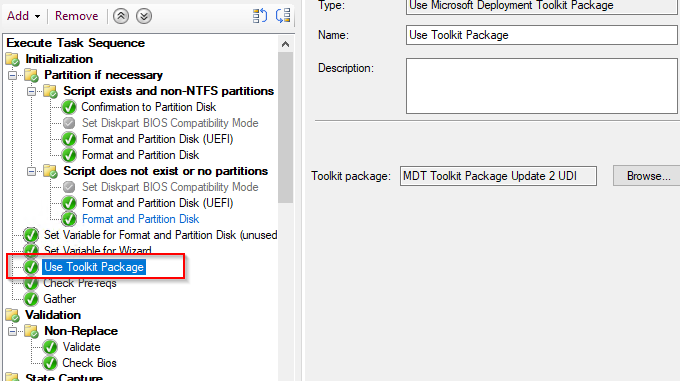

Hi,
Since I upgraded my SCCM to the version 2403, I cannot use any more MDT and UDI.
I cannot create a new MDT Task Sequence and all my created MDT Package for UDI does not work too.
I could to use UDI for Task sequence in my previous SCCM 2207 and could install Windows with UDI, but since SCCM 2403, I get every time by the step "Use Toolkit Package" the error
Task Sequence has failed with the error code 0x00000001 in the task sequence step 'Use Toolkit Package.
Failed to create/backup SQL SSB certificate error when moving SCCM database
By PH25,
Hi,
Has anyone come across this before? I am moving our SCCM database from SQL 2012 on a 2012r2 server to SQL 2019 on a 2019 server, by recovering from a backup. All seems to have gone fine, until the final step of running config manager setup again to choose the site maintenance option, to 'modify SQL server configuration', in order to point SCCM to the new server that is now hosting the database.
ERROR: SQL Server error: [42000][137][Microsoft][SQL Server Native Client 11.0][SQ

