
Welcome to windows-noob.com!
Logging in will allow you to download scripts used in the guides.
If you came here looking for the Endpoint Manager step-by-step guides then please start here.
Register for free and ask your questions in our forums.
- 1 reply
- 5929 views
- Add Reply
- 5 replies
- 8304 views
- Add Reply
- 1 reply
- 4605 views
- Add Reply
- 0 replies
- 4707 views
- Add Reply
- 5 replies
- 13579 views
- Add Reply
- 7 replies
- 12052 views
- Add Reply
- 3 replies
- 12790 views
- Add Reply
OSD Task Sequences failing on Install Software RPC error
By jbudd0649,
We are a small school district in northern VA, every summer we wipe and reload all of our Windows PC's so that the students and staff have a fresh PC at the beginning of the year. Each school has a task sequence unique to their building for software programs. All software is being deployed via the package model during the TS. I recently upgraded our server to CM 2503. We do not use intune nor do we have any type of cloud presence. We have been imaging PC's this way for years. This issue just sta
Can I upgrade my SCCM Server from 2403 directly to 2503 or should I upgrade first to 2409?
By keywan,


Hi,
At the time I have running SCCM 2403 with hotfix. Can I upgrade it directly to the new Version 2503 without any issue? Or should I first upgrade to 2409 with hotfix and then to 2503?
Thank you for help.
Regards
Create a Report by SCCM 2403 issue with Value
By keywan,
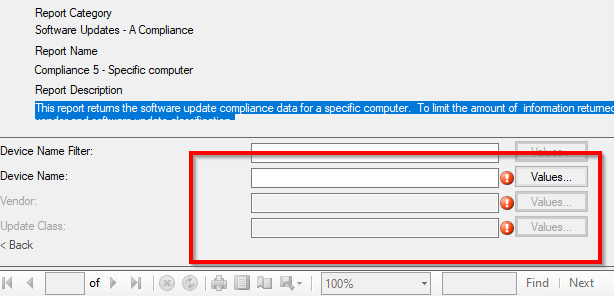

Hi,
I am trying to create on the SCCM 2403 an Report for example for "Complaince 5 - Specific computer. As you know, it should fill many "Valuses" to create an Report.
IS there any way select all Values together as "ALL"?
Migrated Drivers using old content location
By david_pvusd,
I have what seems to be a weird one. My site server is Server 2019 and I am running MECM 2409 with no hotfixes.
About a year ago I migrated all my software from the old MECM server to the new one. I updated the content source path for all the software and things seemed to be fine. I finally got around to shutting down the old server around November.
I have added some new drivers recently and needed to add them to my boot image. No problems on the import or package creation/distribu
SCCM - SSRP - Http 503 Error
OSD Broke after updating to Dec 2024 ADK/PE and Configmgr 2503 - "Failed to initialize task sequence advertisement (Code 0x80004005)"
By Aurock,
Last week I updated from an old Win10 ADK to the Win11 December 2024 ADK and associated PE Package. Then I installed the v2503 update for Configmgr. After the upgrade, my OSD is completely broken. I've tried creating new USB boot media based on WinPE 11 to run my Win11 TS, and also tried pxe booting an existing client to run my Old Win10 TS that was working prior to the upgrade. Both fail, rebooting immediately after the task sequence background screen loads.
Using the Win11 media, I can
Agents will install on 2 DC's but will not get configurations
By menz,

Hello,
I have 2 DC's that when i install the MECM agent on them, they will install but will not get the configuration files and when i open the client on the machines its missing the configurations tab and the action tab only has 2 actions. also, on the general tab of the client, the Client Certificate says "none"
I know the easy answer is this is a "boundary issue" but it is not. i have other servers with the same IP address range and they have no issue getting the client fully config
Windows 11 OSD Task Sequence Progress hidden behind "Just a Moment"
By jbudd0649,
I am deploying Windows 11 24H2 in our environment, but I have a rather annoying issue. When my OSD TS reaches the "Setup Windows and Configuration Manager" task, the PC reboots and all of the rest of the TS is hidden behind the "Just a moment" black screen. If the user is patient, the OSD completes like normal. The problem is that users are sitting down and seeing the "just a moment" screen and rebooting the PC. This causes a bunch of issues. Yes, I realize this is a user issue, but I am trying

