All Activity
- Last week
-
SandyPro started following Can I Remove old SQL versions installed on our SCCM (v2309) server?
-
We have multiple versions of SQL installed on our SCCM server. We recently ran a Nessus scan on the server & there are many vulnerabilities for the old versions. I would like to uninstall the older SQL versions along with the ODBC drivers, if possible. Can I remove the old versions and just leave SQL server 2019? Will this break SCCM? I attached a screen shot below.
- Earlier
-
Hi, Has anyone come across this before? I am moving our SCCM database from SQL 2012 on a 2012r2 server to SQL 2019 on a 2019 server, by recovering from a backup. All seems to have gone fine, until the final step of running config manager setup again to choose the site maintenance option, to 'modify SQL server configuration', in order to point SCCM to the new server that is now hosting the database. ERROR: SQL Server error: [42000][137][Microsoft][SQL Server Native Client 11.0][SQL Server]Must declare the scalar variable "@String". : dbo.spCreateAndBackupSQLCert Create_BackupSQLCert : Failed to execute spCreateAndBackupSQLCert CSiteControlSetup::SetupCertificateForSSB : Failed to create/backup SQL SSB certificate. ERROR: Failed to set up SQL Server certificate for service broker on "SERVER NAME" . I have enabled broker, set trustworthy on and honor broker priority on, on the new instance before running setup.exe again. From some reading online, I believe it could be something to do with setting up SCCM initially with one account, but then changing it to another domain account running the service(s) and now somehow not being able to unlock the master key for the database certs. Sorry if this is making no sense, I am no SQL expert. Being right at the final stage of moving the database, I'm really stuck with this issue now, so any advice/pointers would be greatly welcomed, even if it's just to point me in the direction of which account I need to try to figure out was initially running things - I'm not clear whether that means the account running the config mgr console, the database instance, or the running the sql or sccm services. Thanks Paul
-
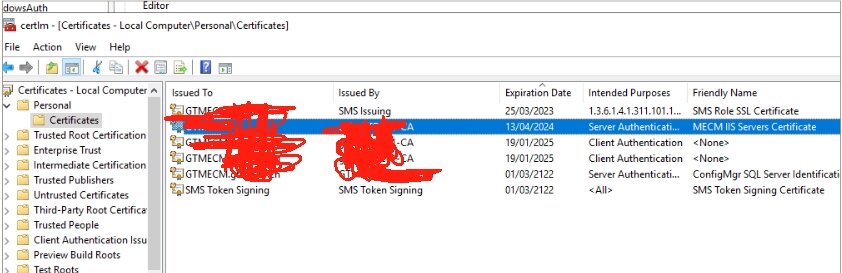
I‘m having issue with SMS_MP_CONTROL_MANAGER with Error 12175. I also checked my SCCM server's certificate and found that both SMS Role SSL Certificate expried 25/03/2023 and MECM llS Servers Certificate expired 13/04/2024. I suspected this might be the cause but how can I renew them step by step? If this is fixed, is it possible to renew them automatically? I have the GPO to handling certificate related configuration but maybe I've missted any? I've been using this SCCM server for around 2-3 years in production and recently I didn't touch it at all:( Any advice would be really appreciated. following are the erorr messages in SCCM console: MP Control Manager detected User Service is not responding to HTTP requests. The HTTP status code and text is 12175, . Possible cause: Internet Information Services (IIS) isn't running or configured to listen on the ports over which the site is configured to communicate. Solution: Verify that the designated Web Site is configured to use the same ports which the site is configured to use. Possible cause: The designated Web Site is disabled in IIS. Solution: Verify that the designated Web Site is enabled, and functioning properly. Possible cause: The User Service application pool identity does not have the required logon privileges. Solution: Verify that the User Service application pool is configured to run under Network Service account. Possible cause: ASP.NET is not installed. Solution: Ensure ASP.NET 4.5 or above is selected under Web Server - Application Development and Features in Windows Server. Possible cause: ASP.NET application does not function properly. Solution: Browse to http(s)://localhost/CMUserService_WindowsAuth/ApplicationViewService.asmx on the local server machine and follow error instructions.
-
Object Replication Error After R2 SP1 Upgrade
Wilson Betancurth replied to Aquintus's topic in Configuration Manager 2012
Your solution for this post worked, thanks. @Peter33 -
can you please show me a screenshot of where you are seeing this error ?
-
I have been trying to set this up but the "Boot to Cloud PC Enhanced" setting, set to "Enable Boot to Cloud Shared PC Mode", never works. It returns a 65000 error. Everything else from the wizard works as expected. I have been using the Windows 365 Boot wizard, as opposed to the Public Preview wizard you are using in this demo. I have opened a ticket with MS but things are moving very slowly with them. Any ideas?
-
Using UI++ With SCCM
coolsport00 replied to coolsport00's topic in System Center Configuration Manager (Current Branch)
I know it's been a while since I posted this question, I've been inundated with actual other work I wanted to provide an update on this. So, as I shared above, we use a default SCCM Web Site (SMS_DP_SMSPKG$) to house our UI++ xml file, which the physical location is in \\sccm-install-dir\SCCMContentLib\ folder. Then, we configure our Boot Image to point to this location in the Customization tab, as a prestart command, to use UI++. For us, we don't house the UI xml file in any of the default SCCM directories in this location, but seemingly a manually created "XML" folder, so: \\sccm-install-dir\SCCMContentLib\XML\UI.xml. When I was attempting to make changes (i.e. serverely clean up) our UI xml file, when attempting to image a device, UI++ wouldn't come up...our Task Sequence would. Someone above I believe suggested this could be because of an syntax error within the xml file. This still could be so. But, when I attempted to change the path of the xml in our Boot Image to point to an unaltered xml file, the same behavior happened...so I don't know. Fast foward to a day ago - we use our xml file to image various model computers in our environment. We since have procured a new model and needed to add it to our UI xml file. When we did so, it worked. No going directly to Task Sequence and skipping UI++ when imaging. 🤔 So, I don't know. That's where I'm at. I still need to make radical changes (remove a lot of things we no longer use/need) from our xml file. So, we'll see if the original unwanted behavior continues. For now, all is well. I'll post back if I continue having problems. Thanks for all the suggestions. -
Hello Please see screenshots of the log files. This system is in a lab of 25 machines and is the only one that not getting its updates. I will check the boundaries but i would think that the rest of the machines in that lab would have the same issue. I did check the software center and there are no updates available for this particular system. UpdateHandler.log no errors all successful... Please see the other 3 log files in screenshot. I am thinking i may remove the client from the machine and try reinstalling it. In the WUAHandler it states that the machine is not enrolled in MDM for some reason. You will see in the screenshot. Thanks for your help... Craig
-
My company is reviewing security vulnerabilities, and this certificate (specifically, the IIS certificate), comes back as vulnerable because the subject name is supplied in the request. I'm wondering if this option can be replaced with using the option to build the subject name from AD, as long as it includes the fully distinguished name DNS name for the SAN. Prevent users to request a certificate valid for arbitrary users based on the certificate template (ESC1) - Microsoft Defender for Identity | Microsoft Learn I understand that it may cause issues if you're doing IBCM, but we have DirectAccess and clients are encouraged to use FQDN wherever possible (to enforce Kerberos), so I'm just curious if I can have the certificate configured as I described, or should I just enable manager approval?
-
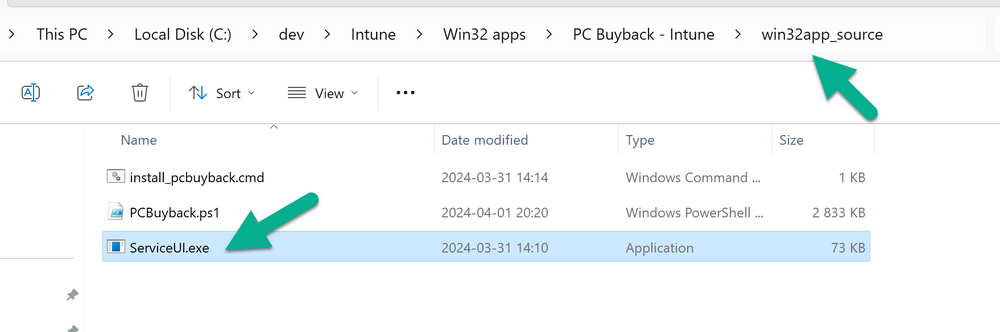
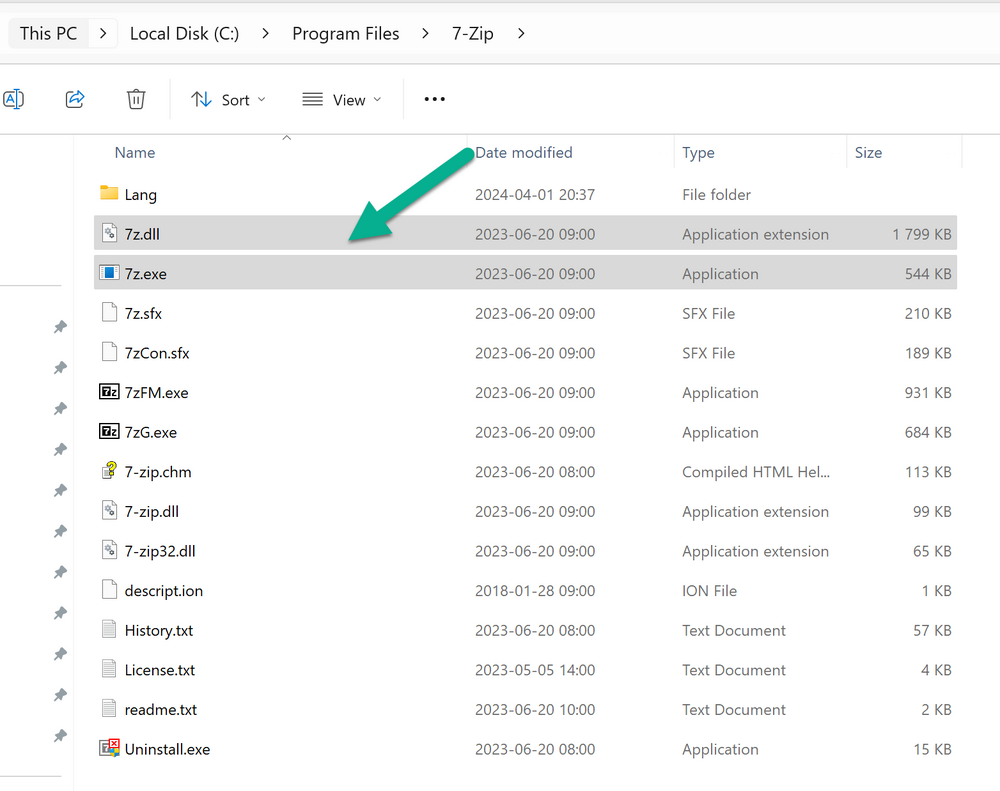
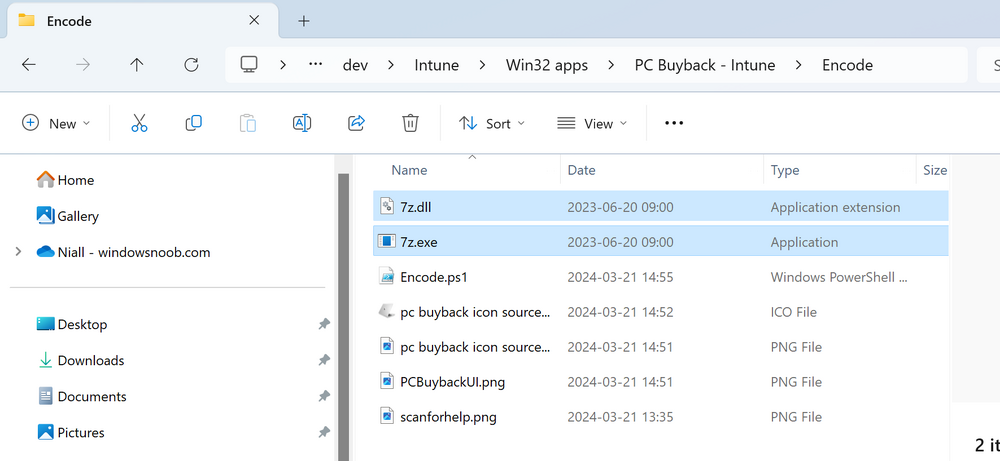
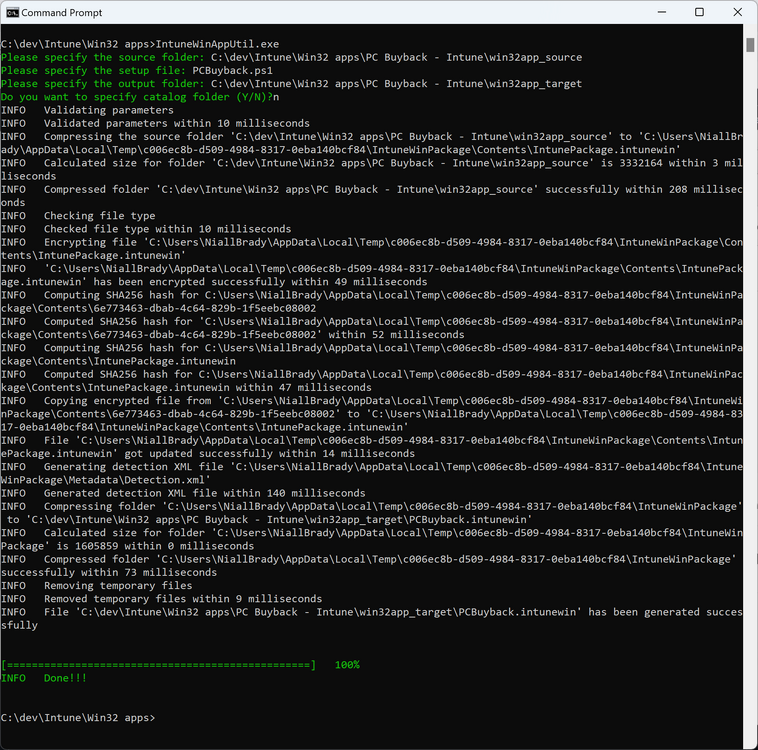
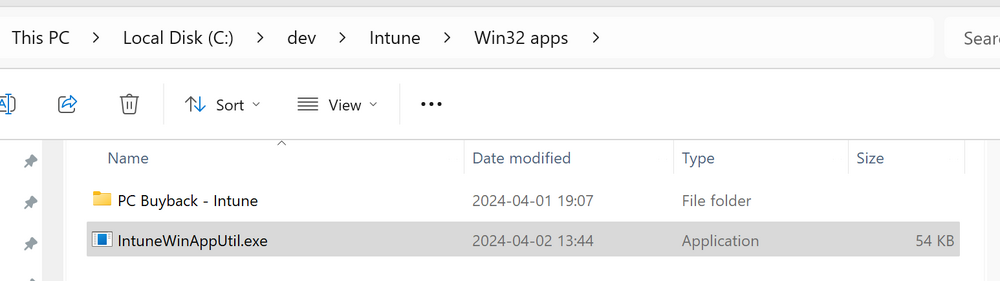
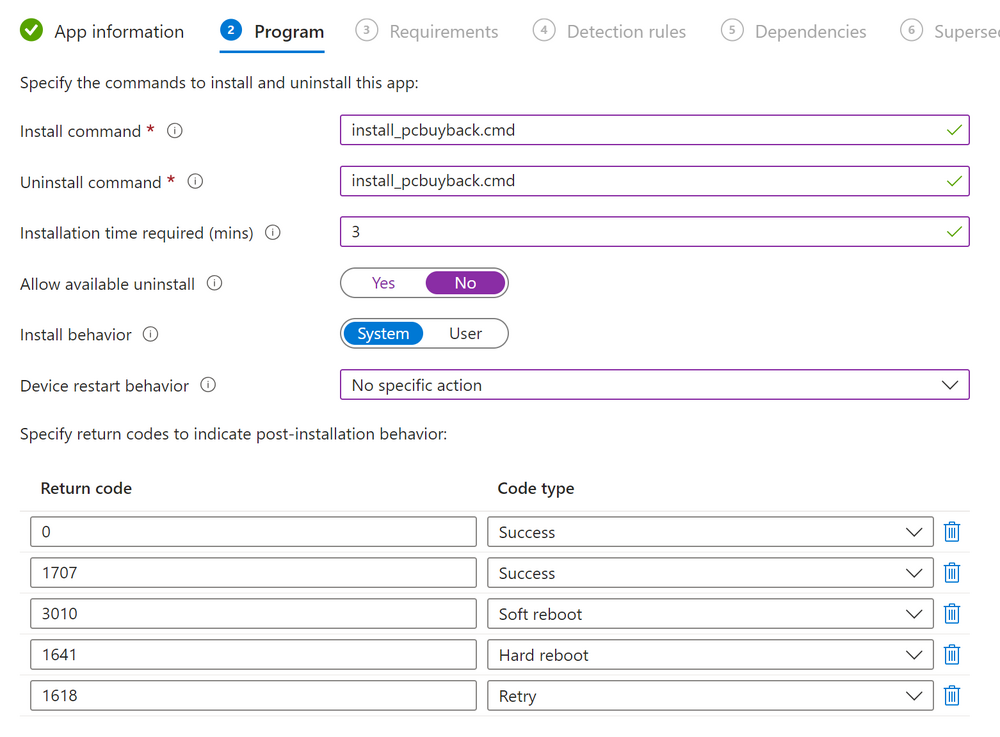
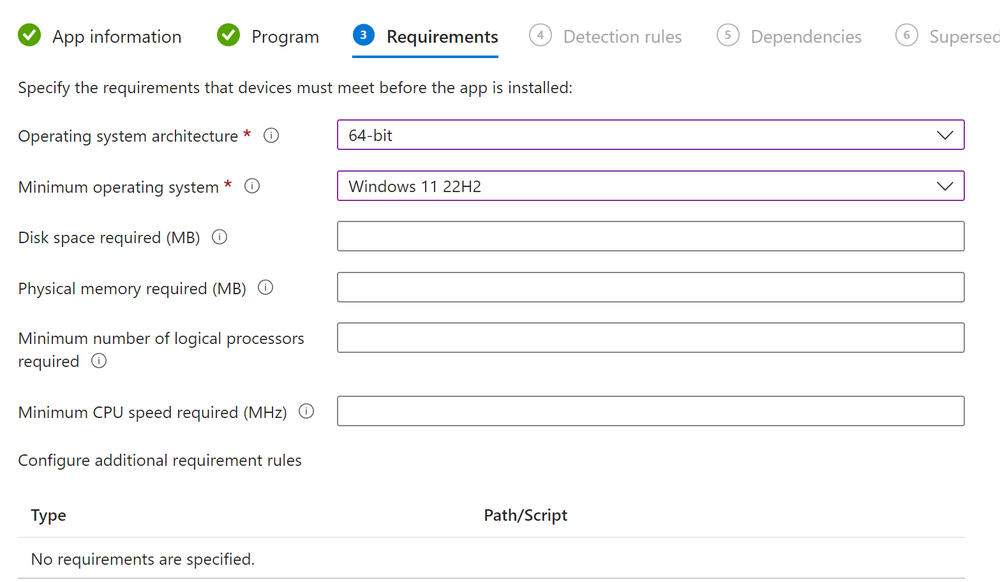
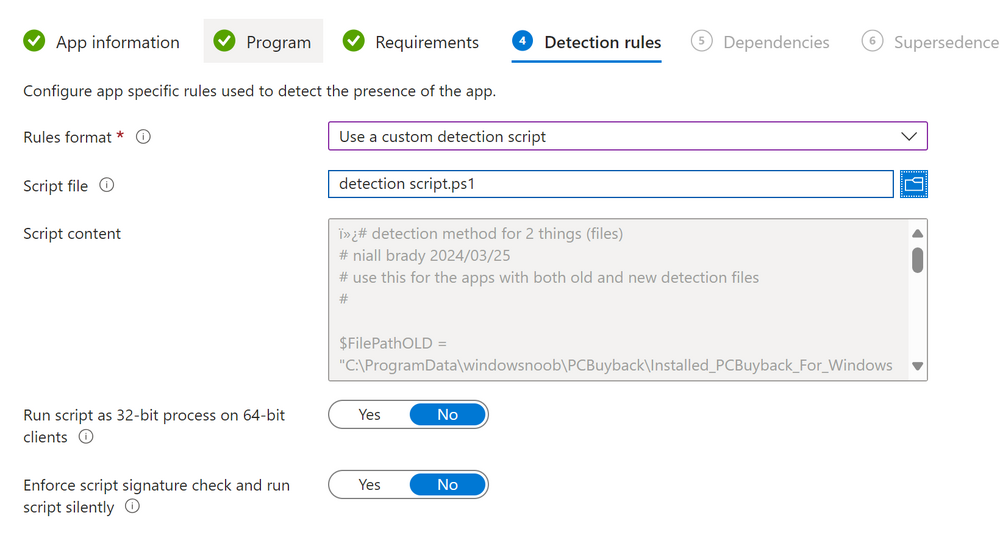
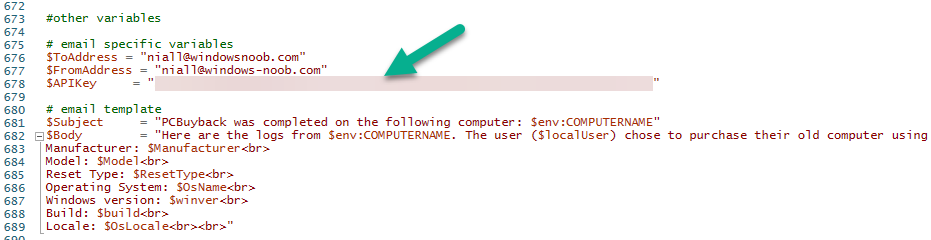
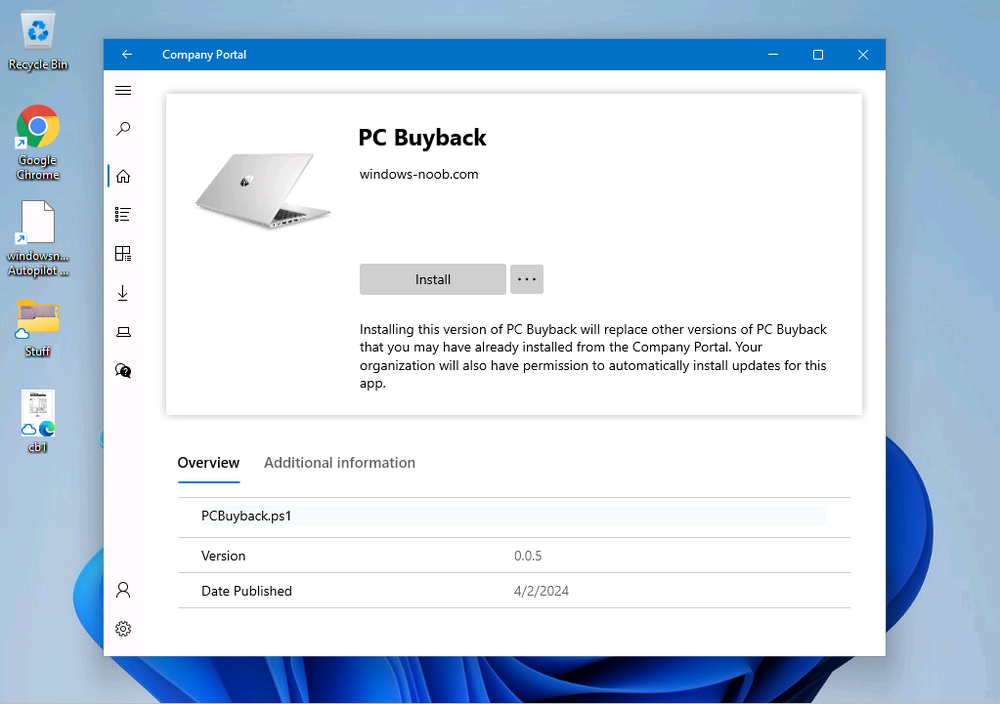
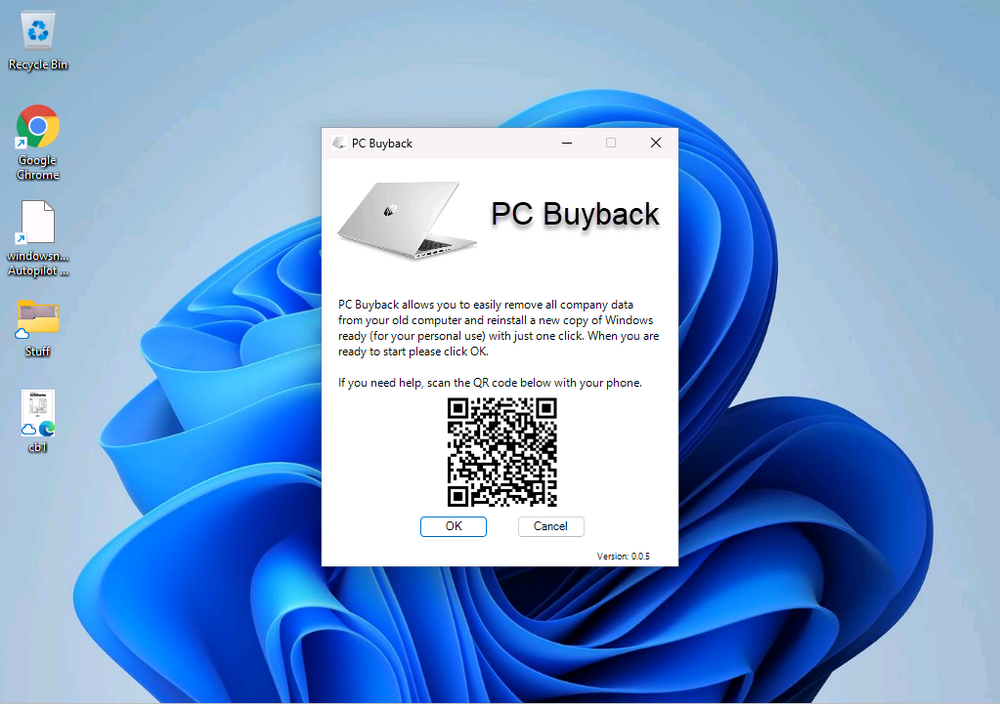
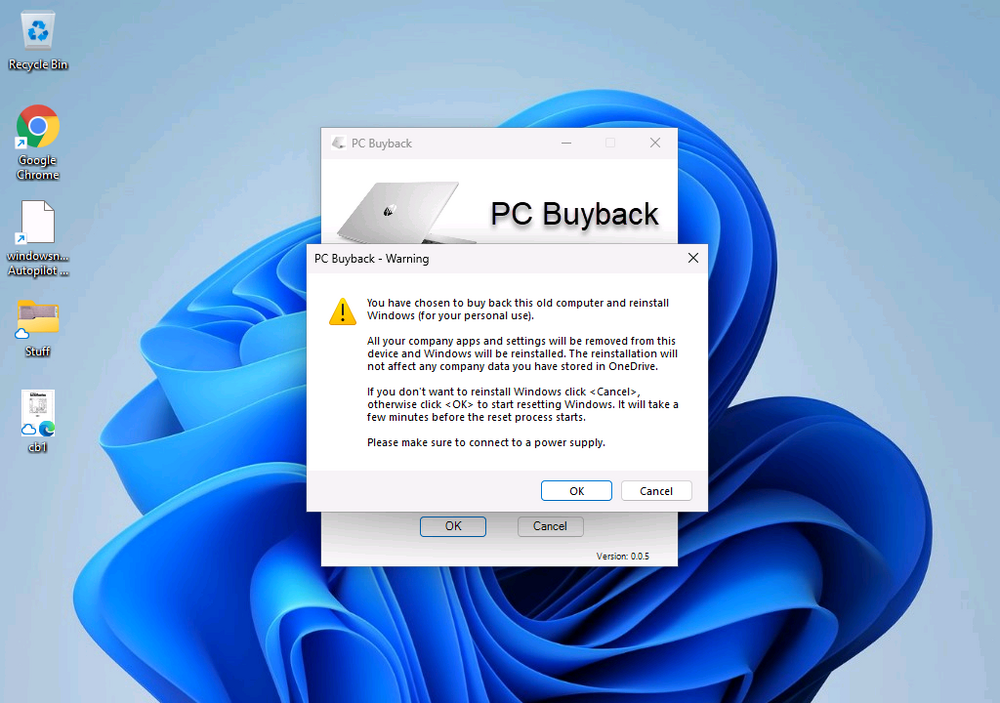
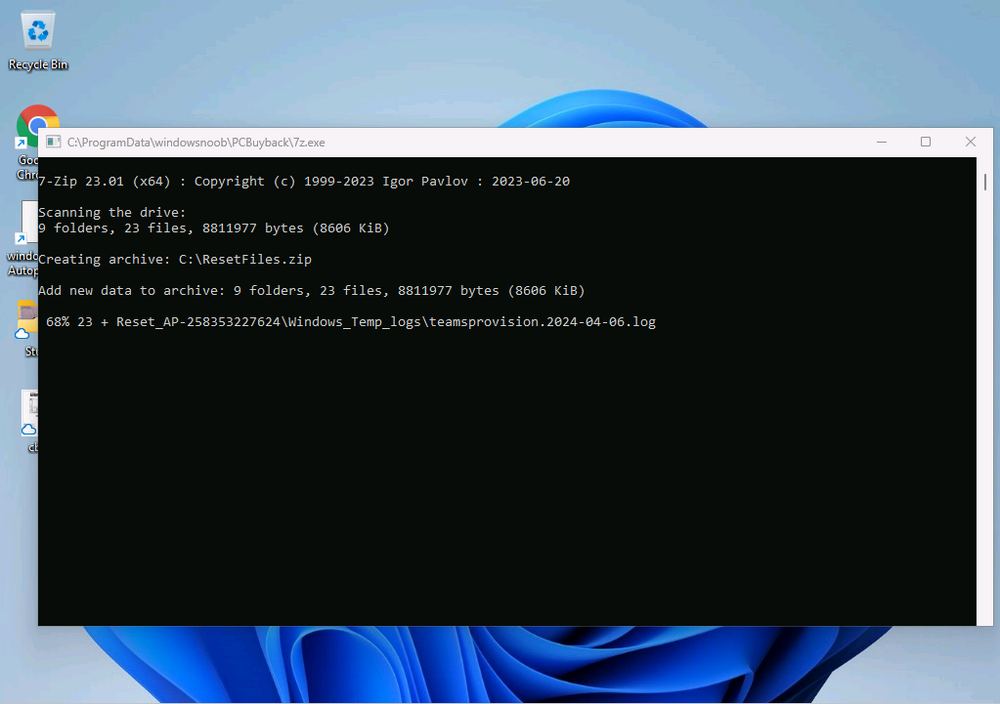
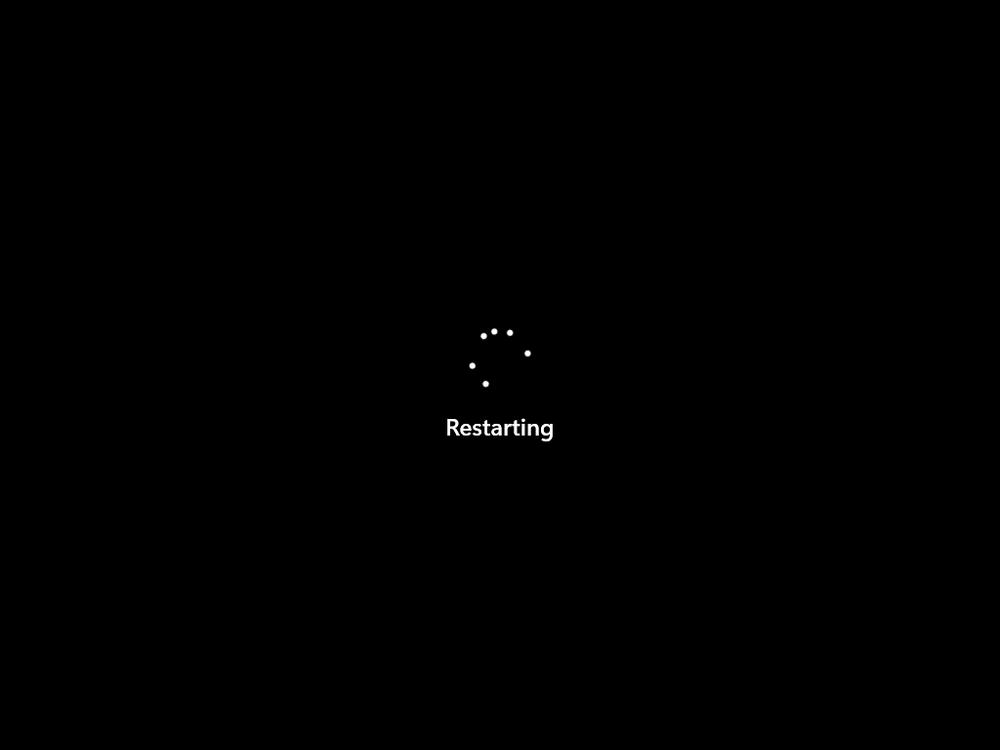
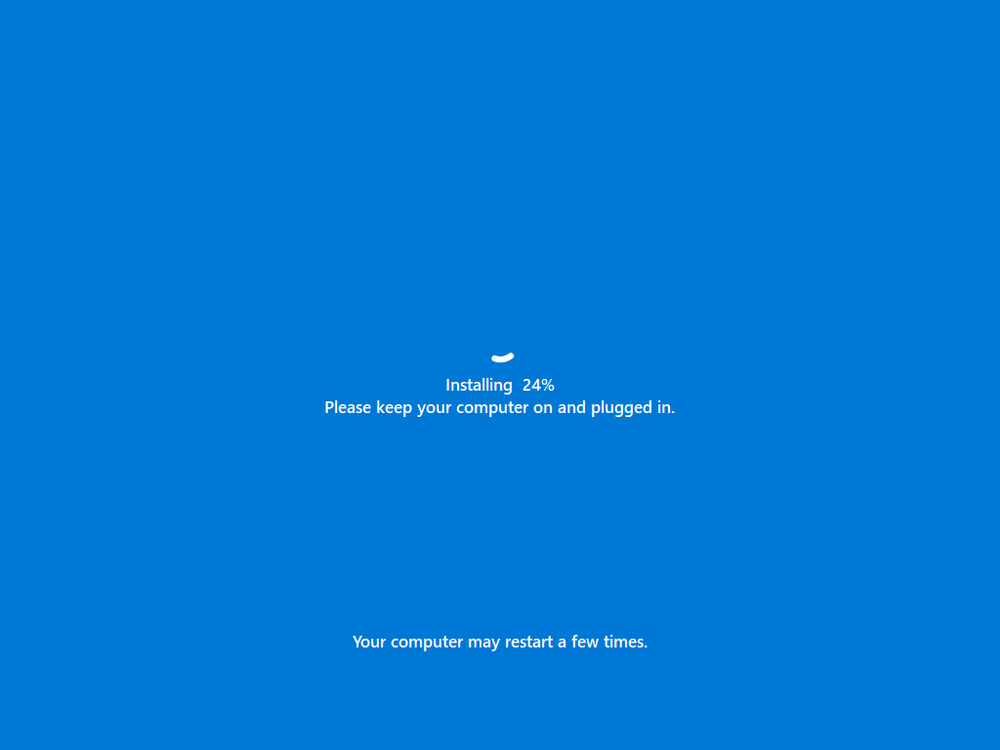
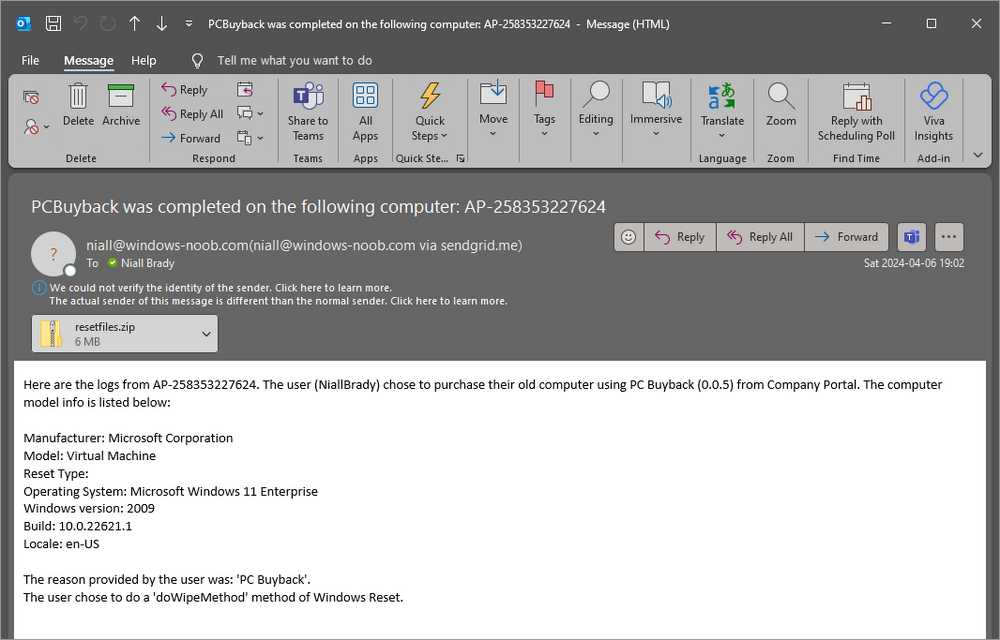
Introduction In part 1 I showed you how to prepare Azure for the PC Buyback app, in this part we'll add the Win32 app, deploy it and see how it behaves on a Windows Autopilot registered device. Step 1. Download the scripts Download this zip and extract to C:\Dev\Intune\Win32 apps Note: you must be a logged on member of windows-noob.com to download the ZIP PC Buyback - Intune.zip Step 2. Get ServiceUI.exe from MDT You'll need the ServiceUI.exe executable file to display user interfaces (UI) to end users when operating in SYSTEM context. To get the file, download and install MDT somewhere and navigate to C:\Program Files\Microsoft Deployment Toolkit\Templates\Distribution\Tools\x64. To download MDT click here. Copy the 64 bit version of ServiceUI.exe file to your extracted win32app_source folder so it looks like this. Step 3. Get 7Zip for compressing files Download 7Zip and install it. Copy 7z.dll and 7z.exe from the default folder C:\Program Files\7-Zip Copy those 2 files to C:\Dev\Intune\Win32 apps\PC Buyback - Intune\encode In PowerShell ISE run the Encode script.. After it is completed encoding the files, you'll have a bunch of additional text files in the encode folder. Open each text file using notepad, press CTRL+A to mark all the text, then copy using CTRL+C and paste the content of each file using CTRL+V into the corresponding section of the PCBuyback.ps1 script as shown below. Note: The QR code used in the PC Buyback app points to part 1 of this blog series, but you can customize it to point to an internal knowledge base article to assist users with the entire process. One thing to keep in mind, I used https://www.qr-code-generator.com to create the QR code, but after creating it, you'll need to resize it to 118x120 pixels (in MS paint or similar). Step 4. Modify variables In the PCBuyback.ps1 script, configure the following email related variables: $ToAddress $FromAddress $APIkey Next, copy the Function URL for each of the http triggers you created in part 1, below shows you how to do that paste those URLs into the corresponding variable in the script Save the changes to the PCBuyback.ps1 script. Step 5. Get the Microsoft Win32 content prep tool Download the Win32 content prep tool from here. Copy the IntuneWinAppUtil.exe file to your Win32 apps root folder, it should look like this. Open a command prompt and browse to the PCBuyback folder structure. Launch the IntuneWinAppUtil.exe file and answer the following. Please specify the source folder: win32app_source Please specify the setup file: PCBuyback.ps1 Please specify the output folder: win32app_target Do you want to specify catalog folder (Y/N)? n as shown here. Step 6. Add the Win32 app in Intune Log into Intune and add a new Win32 App. Below are some screenshots showing how I've configured the app. For Select app type, select Windows app (Win32) from the drop down menu Click on Select app package file and point it to the pcbuyback.intunewin file in the win32app_target folder, fill in some info about the app, for the logo, click on Select image and point it to the encode folder where the icon file can be used fill in the install commands, point it to install_pcbuyback.cmd fill in the requirements, and for detection rules point it to the detection script in the root of the PC Buyback - Intune files finally deploy it to an Entra ID group that contains the computers that are targeted for buyback, and deploy it as Available. Step 7. Test the app on a device On a test device that is already enrolled into Intune and Windows Autopilot registered, add the device to the azure ad group above and launch Company Portal. The PC Buyback app should appear. Click Install and after a few moments the app should appear. Clicking OK shows a warning and clicking OK to the warning starts the process, after a few moments it will remove the device from Intune, then remove the Windows Autopilot registered device and zip up the logs before emailing them After emailing the logs and confirmation that it's done PC Buyback, it will restart after the restart it will start resetting Windows removing all apps and settings that were on the device After the reset, Windows installs itself again... and after the reinstallation, it's back to the first screen of the OOBE, so the user can now setup their device personally When the user runs PC Buyback an email is sent to the email address you configured... and the process will store details in Azure tables (coming in Part 3) Troubleshooting If the app fails for whatever reason, it will log the details in C:\ProgramData\windowsnoob\PCBuyback\win.ap.pcbuyback.log Below is a sample of that log file from a successfully wiped device 04/06/2024 10:00:42 Starting script: 'Win.AP.PCBuyback' version: '0.0.5' ... 04/06/2024 10:00:42 extracting scripts to 'C:\ProgramData\windowsnoob\PCBuyback'... 04/06/2024 10:00:42 decoding BASE64 encoded file...'7z.exe' 04/06/2024 10:00:43 decoding BASE64 encoded file...'7z.dll' 04/06/2024 10:00:45 decoding BASE64 encoded file...'scanforhelp.png' 04/06/2024 10:00:45 decoding BASE64 encoded file...'PCBuybackUI.png' 04/06/2024 10:00:47 Detecting the logged on user... 04/06/2024 10:00:47 localuserfull was identified as: 'AzureAD\NiallBrady' 04/06/2024 10:00:47 Detection method 1: The user was identified as: NiallBrady 04/06/2024 10:00:47 SID: 'S-1-12-1-1583932090-1131944776-3006070936-2698034199' 04/06/2024 10:00:47 found sid 04/06/2024 10:00:48 registrypath is: HKU:\S-1-12-1-1583932090-1131944776-3006070936-2698034199\SOFTWARE\windowsnoob\Autopilot 04/06/2024 10:00:48 Checking if registryvalue: 'PCBuyback' in registrypath: 'HKU:\S-1-12-1-1583932090-1131944776-3006070936-2698034199\SOFTWARE\windowsnoob\Autopilot' exists... 04/06/2024 10:00:49 Reg key exists... 04/06/2024 10:00:49 registrypath is: HKU:\S-1-12-1-1583932090-1131944776-3006070936-2698034199\SOFTWARE\windowsnoob\Autopilot 04/06/2024 10:00:49 Checking if registryvalue: 'PCBuyback' in registrypath: 'HKU:\S-1-12-1-1583932090-1131944776-3006070936-2698034199\SOFTWARE\windowsnoob\Autopilot' exists... 04/06/2024 10:01:09 Reason added: '' 04/06/2024 10:01:11 The user chose OK to the PCBuyback warning, starting the reset process... 04/06/2024 10:01:11 Is this a Windows Autopilot device: 04/06/2024 10:01:11 Checking if the device is registered as a Windows Autopilot device started... 04/06/2024 10:01:11 Device serial number: 3135-5201-3107-6925-8353-2276-24 04/06/2024 10:01:19 DEBUG: The following was returned from the graph call. ' 04/06/2024 17:01:19 Starting Azure function... 04/06/2024 17:01:19 Connected to tenant: windowsnoob.com. 04/06/2024 17:01:19 supplied serial number: '3135-5201-3107-6925-8353-2276-24'. 04/06/2024 17:01:19 Get Device Reference from Intune. DeviceTrue. 04/06/2024 17:01:19 Serial number: 3135-5201-3107-6925-8353-2276-24 is an autopilot machine. Exiting Azure function.' 04/06/2024 10:01:19 the device was detected as a Windows Autopilot device, so let's remove it as a registered AP device 04/06/2024 10:01:19 Remove Windows Autopilot device from Intune started. 04/06/2024 10:01:19 Windows Autopilot device serial number: 3135-5201-3107-6925-8353-2276-24 04/06/2024 10:01:20 DEBUG: The following was returned from the graph call. 'Success' 04/06/2024 10:01:20 Removed Windows Autopilot device '3135-5201-3107-6925-8353-2276-24' from intune. 04/06/2024 10:01:20 Exiting the Intune based PC Buyback script, thanks for watching :-). If all went well and if the recovery partition on this device is healthy, Windows Reset should begin in the next few moments... 04/06/2024 10:01:20 DEBUG: The user chose OK to the PC Buyback Warning message. Starting the Windows reinstallation process now... 04/06/2024 10:01:20 checking for Power... 04/06/2024 10:01:20 virtual machine detected, will not check for power. 04/06/2024 10:01:20 Creating folder to store logs etc... 04/06/2024 10:01:20 Grabbing the reason why the user wanted to reset... 04/06/2024 10:01:20 Grabbing 'C:\ProgramData\windowsnoob\PCBuyback' logs 04/06/2024 10:01:20 Grabbing Windows temp logs 04/06/2024 10:01:20 DEBUG: Folder size (in bytes) = 2.22250366210938 04/06/2024 10:01:20 DEBUG: truncated bytes = 3 04/06/2024 10:01:20 Folder size (in MB) = 3 04/06/2024 10:01:20 Log files size: 3 04/06/2024 10:01:20 Log file size limit = 10 04/06/2024 10:01:20 Log file size (3) is less than 10, will include temp logs in email... 04/06/2024 10:01:20 Creating Autopilot cab file... 04/06/2024 10:01:42 adding C:\ProgramData\windowsnoob\PCBuyback\Win.AP.PCBuyback.log
-
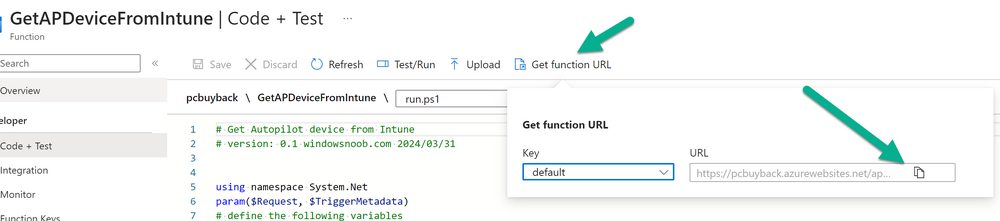
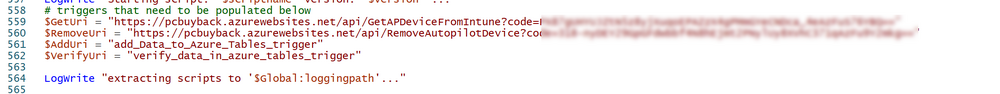
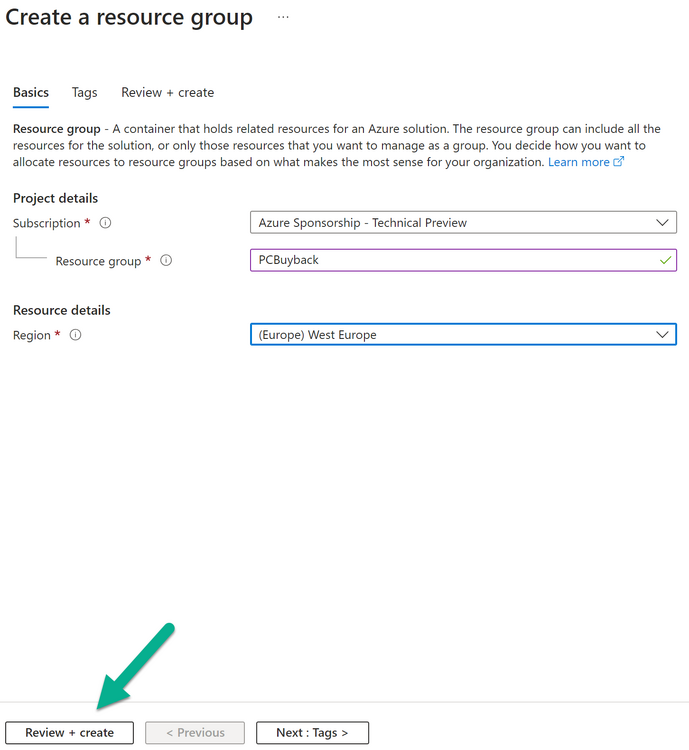
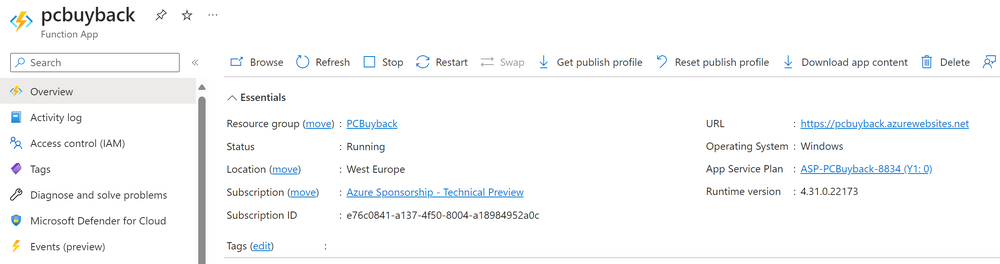
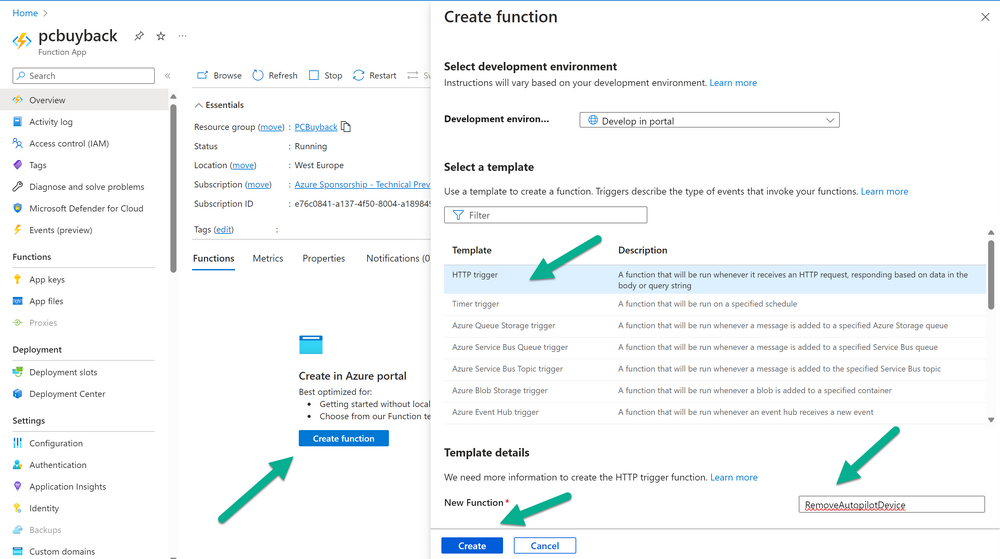
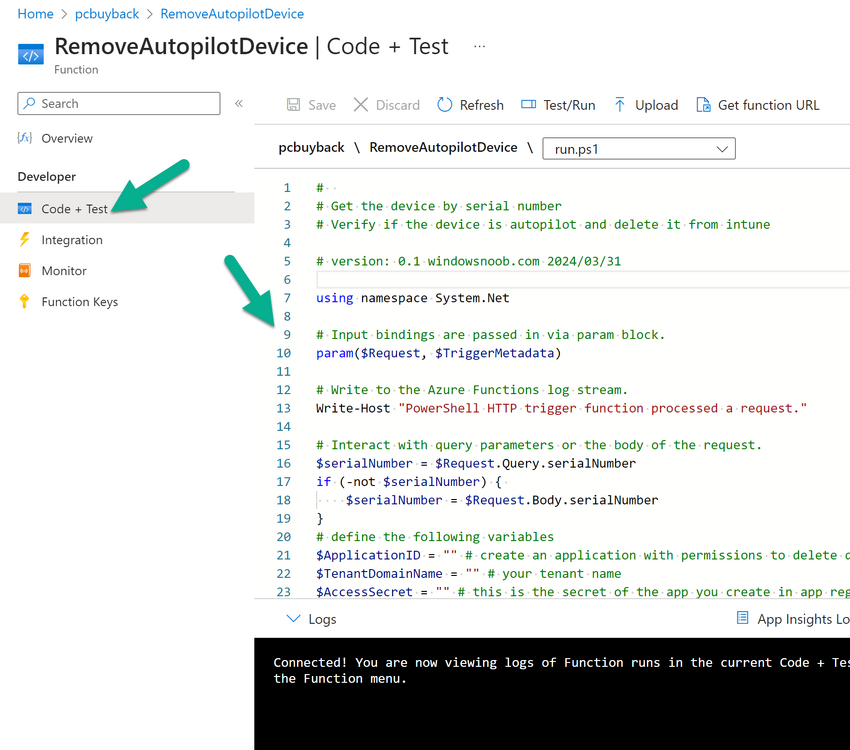
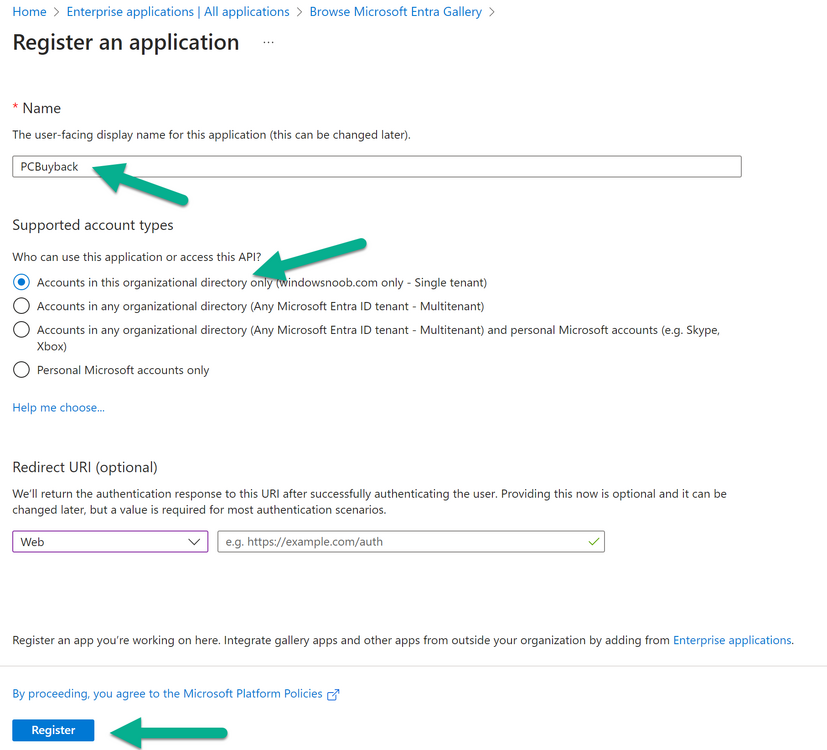
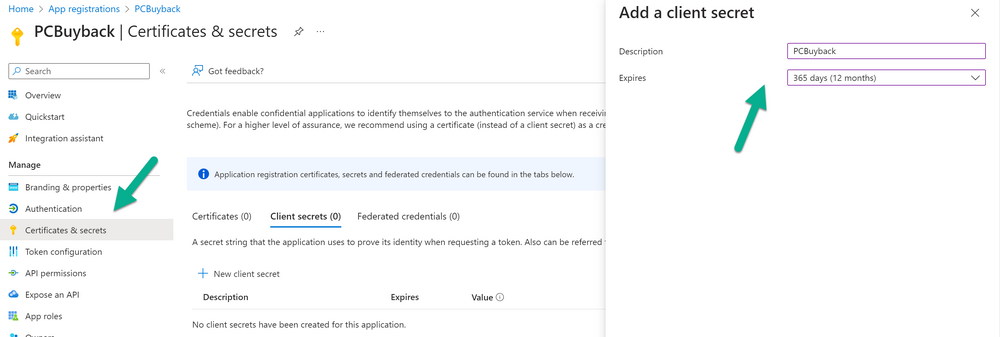
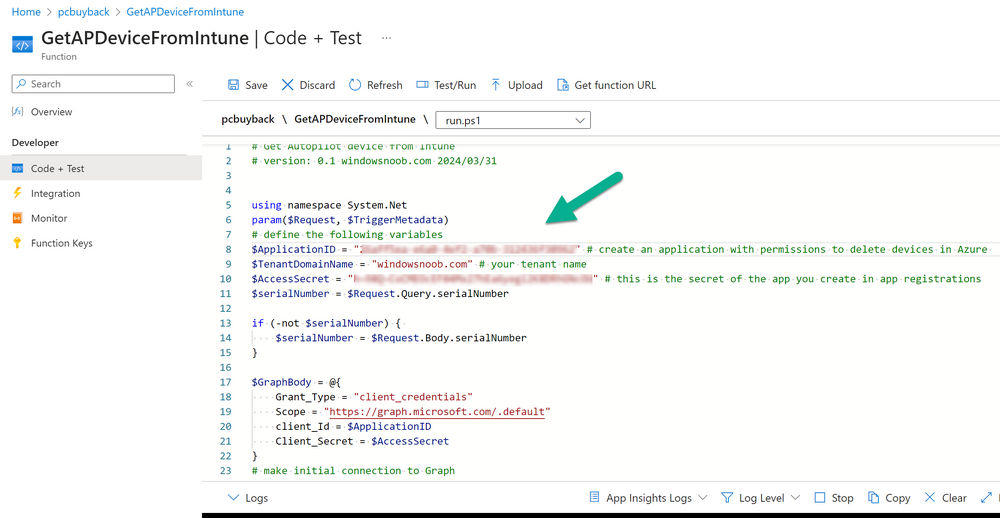
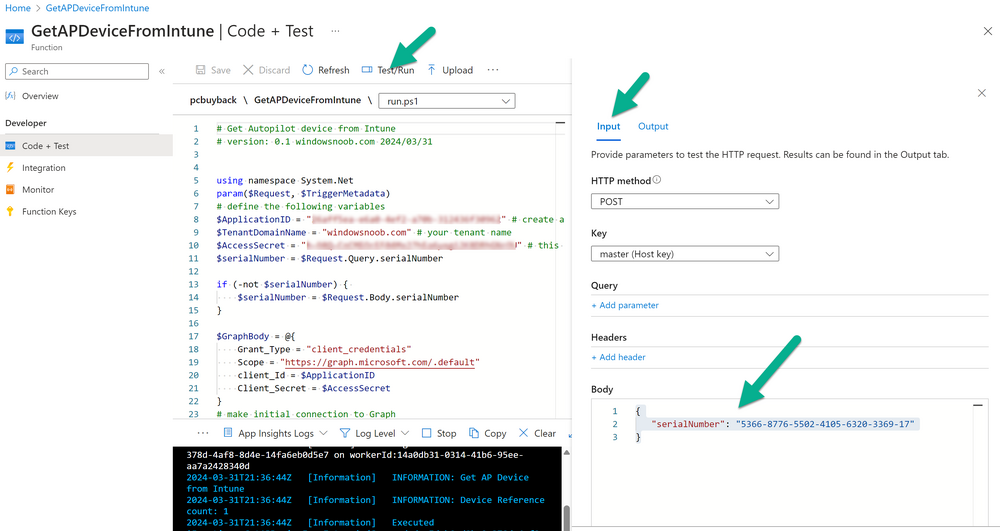
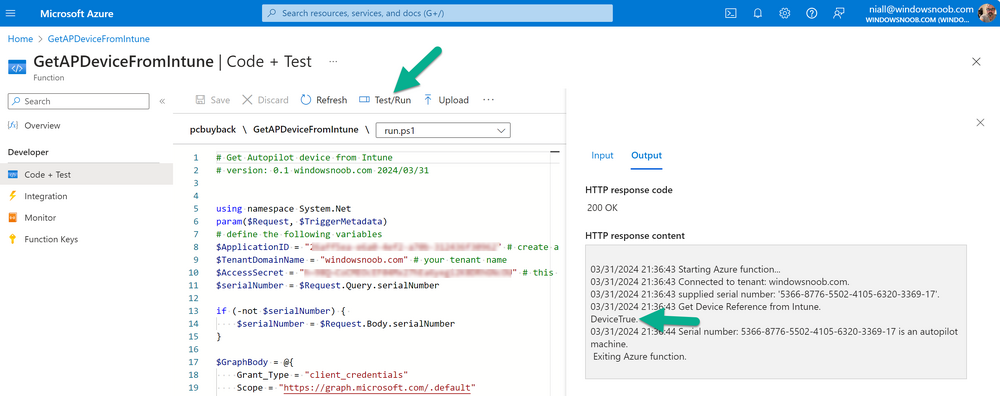
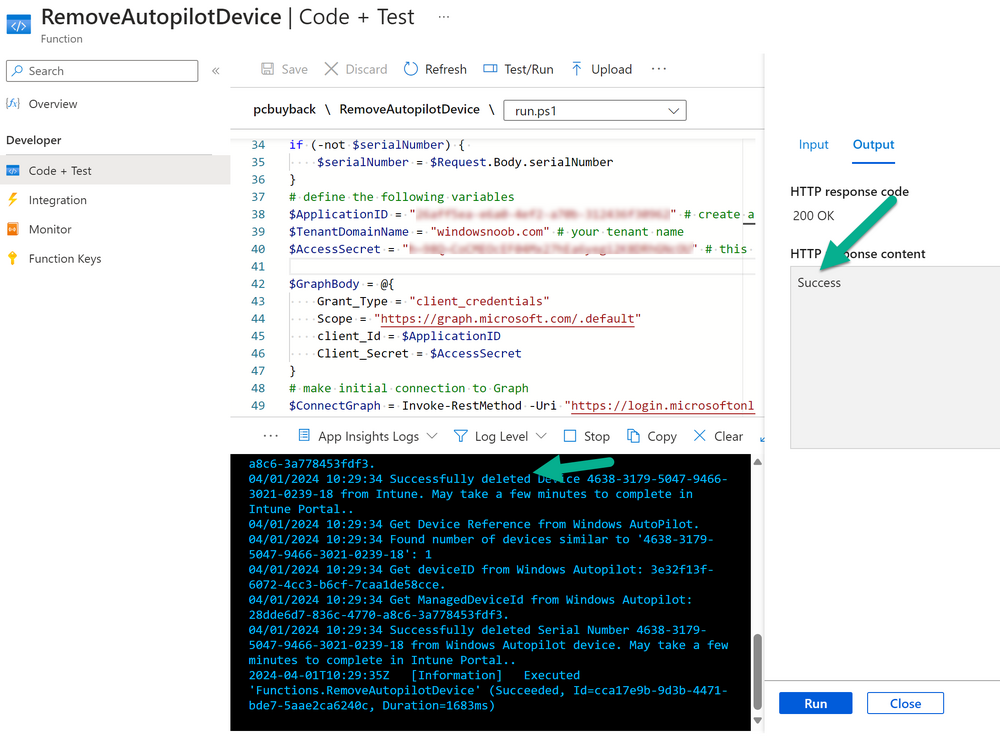
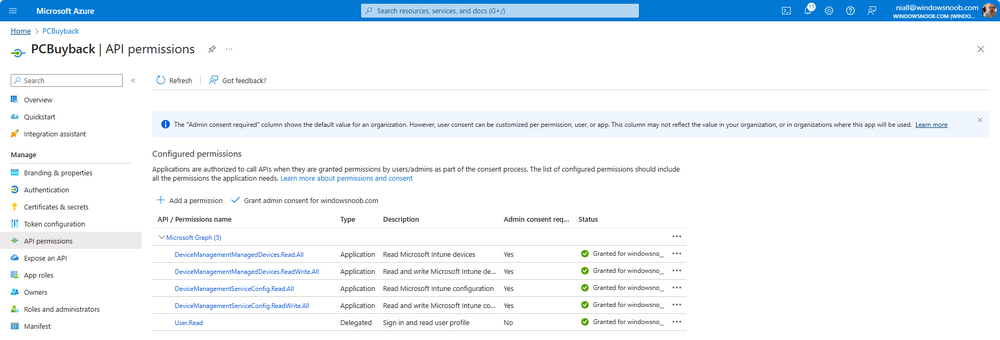
Introduction Windows Autopilot allows you to quickly enroll devices using policies, apps and settings applicable to your tenant, and that's great for deploying new Windows devices. Those devices can be registered as Windows Autopilot registered devices by the OEM (Original Equipment Manufacturer) or by a third party integrator or by the organization themselves by importing the Windows Autopilot hardware CSV into Intune. After a device has reached end of life however, it needs to be disposed of or sold on. It would be nice to offer end users the ability to buy back their old Company hardware with minimum fuss, but at the same time to remove Intune management and remove the device from Windows Autopilot registration while installing a new copy of Windows 11 professional that the end user could use for their own personal use. I created a Win32 app that does all this called PC Buyback. The app integrates with a back end Azure app using http triggers to do the magic. This post will cover the app features and code needed to implement it in your own tenant. The features of the app are as follows: Easy to use Self-Service app available in Company Portal Removes company data and apps Reinstalls Windows Changes Windows edition using OEM license info stored in BIOS Emails results to a company inbox Logging to Azure tables (optional) Note: In this blog, the app uses http triggers that use certificate secrets, this is fine in a lab, but in production you should use Azure Key Vault instead as it's more secure. Step 1. Create resource group In Entra, using an account that has permission to create Resource Groups in your subscription, create a resource group called PCBuyback, create it in the region that your tenant is located. Step 2. Create a function app in the resource group In the PCBuyback resource group, create a function app in the same region as the resource group you created above. Step 3. Create a RemoveAutopilotDevice http trigger In the Function app, create a trigger called RemoveAutopilotDevice In the newly created Http trigger, click on Code + Test and paste in the following code to overwrite the existing code... # # Remove Autopilot device by serial number # Verify if the device is autopilot and delete it from intune # version: 0.1 windowsnoob.com 2024/03/31 using namespace System.Net # Input bindings are passed in via param block. param($Request, $TriggerMetadata) # Write to the Azure Functions log stream. Write-Host "PowerShell HTTP trigger function processed a request." # Interact with query parameters or the body of the request. $serialNumber = $Request.Query.serialNumber if (-not $serialNumber) { $serialNumber = $Request.Body.serialNumber } # define the following variables $ApplicationID = "" # create an application with permissions to delete devices in Azure $TenantDomainName = "" # your tenant name $AccessSecret = "" # this is the secret of the app you create in app registrations $GraphBody = @{ Grant_Type = "client_credentials" Scope = "https://graph.microsoft.com/.default" client_Id = $ApplicationID Client_Secret = $AccessSecret } # make initial connection to Graph $ConnectGraph = Invoke-RestMethod -Uri "https://login.microsoftonline.com/$TenantDomainName/oauth2/v2.0/token" -Method POST -Body $GraphBody #get the token $token = $ConnectGraph.access_token # to improve logging... $body = " `n" $response = "" $body = $body + "$(Get-Date)" + " Starting Azure function...`n" $body = $body + "$(Get-Date)" + " Connected to tenant: $TenantDomainName.`n" # now do things... if ($serialNumber) { $body = $body + "$(Get-Date)" + " You supplied serialNumber: '$serialNumber'" + ".`n" Try{ # Get Device Reference from Intune $body = $body + "$(Get-Date)" + " Get Device Reference from Intune" + ".`n" $Device = Invoke-RestMethod -Method Get -uri "https://graph.microsoft.com/v1.0/deviceManagement/managedDevices?`$filter=contains(serialNumber,'$serialNumber')" -Headers @{Authorization = "Bearer $token"} | Select-Object -ExpandProperty Value If($Device){ $body = $body + "$(Get-Date)" + " Found number of devices similar to '$serialNumber': $($Device.count)" + "`n" Foreach($d in $Device){ If($d.serialNumber -eq $serialNumber){ $body = $body + "$(Get-Date)" + " Get deviceID from Intune: $($d.id)" + ".`n" Invoke-RestMethod -Method Delete -uri "https://graph.microsoft.com/v1.0/deviceManagement/managedDevices/$($d.id)" -Headers @{Authorization = "Bearer $token"} $body = $body + "$(Get-Date)" + " Successfully deleted Device $($d.serialNumber) from Intune. May take a few minutes to complete in Intune Portal." + ".`n" Write-Host $body $response = "Success" break } } } Else{ $body = $body + "$(Get-Date)" + " serialNumber: $serialNumber does not exist in Intune" + ".`n" $response += "Failed" Write-Host $body } } Catch{ $body = $body + "$(Get-Date)" + " $($Error)" + ".`n" $body = $body + "$(Get-Date)" + " Failed to get Device Reference from Intune." + ".`n" $response += "Failed" Write-Host $body } Try{ # Get Device Reference from Windows AutoPilot $body = $body + "$(Get-Date)" + " Get Device Reference from Windows AutoPilot" + ".`n" $Device = Invoke-RestMethod -Method Get -uri "https://graph.microsoft.com/v1.0/deviceManagement/windowsAutopilotDeviceIdentities?`$filter=contains(serialNumber,'$serialNumber')" -Headers @{Authorization = "Bearer $token"} | Select-Object -ExpandProperty Value If($Device){ $body = $body + "$(Get-Date)" + " Found number of devices similar to '$serialNumber': $($Device.count)" + "`n" Foreach($d in $Device){ If($($d.serialNumber) -eq $serialNumber){ $body = $body + "$(Get-Date)" + " Get deviceID from Windows Autopilot: $($d.id)" + ".`n" $body = $body + "$(Get-Date)" + " Get ManagedDeviceId from Windows Autopilot: $($d.managedDeviceId)" + ".`n" Invoke-RestMethod -Method Delete -uri "https://graph.microsoft.com/v1.0/deviceManagement/windowsAutopilotDeviceIdentities/$($d.id)" -Headers @{Authorization = "Bearer $token"} $body = $body + "$(Get-Date)" + " Successfully deleted Serial Number $($d.serialNumber) from Windows Autopilot device. May take a few minutes to complete in Intune Portal." + ".`n" $response = "Success" Write-Host $body break } } } Else{ $body = $body + "$(Get-Date)" + " Serial Number: $serialNumber does not exist in Windows Autopilot" + ".`n" $response += "Failed" Write-Host $body } } Catch{ $body = $body + "$(Get-Date)" + " $($Error)" + ".`n" $body = $body + "$(Get-Date)" + " Failed to get Serial Number: $serialNumber from Windows Autopilot." + ".`n" $response += "Failed" Write-Host $body } $body = $body + "$(Get-Date)" + " Exiting Azure function." } # Associate values to output bindings by calling 'Push-OutputBinding'. Push-OutputBinding -Name Response -Value ([HttpResponseContext]@{ StatusCode = [HttpStatusCode]::OK Body = $response }) Step 4. Create a GetAPDeviceFromIntune http trigger In the Function app, create a another http trigger called GetAPDeviceFromIntune and paste in the following code for that trigger. # Get Autopilot device from Intune # version: 0.1 windowsnoob.com 2024/03/31 using namespace System.Net param($Request, $TriggerMetadata) # define the following variables $ApplicationID = "" # create an application with permissions to delete devices in Azure $TenantDomainName = "" # your tenant name $AccessSecret = "" # this is the secret of the app you create in app registrations $serialNumber = $Request.Query.serialNumber if (-not $serialNumber) { $serialNumber = $Request.Body.serialNumber } $GraphBody = @{ Grant_Type = "client_credentials" Scope = "https://graph.microsoft.com/.default" client_Id = $ApplicationID Client_Secret = $AccessSecret } # make initial connection to Graph $ConnectGraph = Invoke-RestMethod -Uri "https://login.microsoftonline.com/$TenantDomainName/oauth2/v2.0/token" -Method POST -Body $GraphBody #get the token $token = $ConnectGraph.access_token Write-Host "Get AP Device from Intune" # to improve logging... $body = " `n" $body = $body + "$(Get-Date)" + " Starting Azure function...`n" $body = $body + "$(Get-Date)" + " Connected to tenant: $TenantDomainName.`n" # now do things... if ($serialNumber) { $body = $body + "$(Get-Date)" + " supplied serial number: '$serialNumber'" + ".`n" try { # Get Device Reference from Intune $body = $body + "$(Get-Date)" + " Get Device Reference from Intune" + ".`n" $DeviceReference = Invoke-RestMethod -Method Get -uri "https://graph.microsoft.com/v1.0/deviceManagement/windowsAutopilotDeviceIdentities?`$top=25&`$filter=contains(serialNumber,'$serialNumber')" -Headers @{Authorization = "Bearer $token"} | Select-Object -ExpandProperty Value #Write-Host $body Write-Host "Device Reference count: $($DeviceReference.Count)" if($DeviceReference.Count -gt 0) { $body = $body + "DeviceTrue" + ".`n" $body = $body + "$(Get-Date)" + " Serial number: $serialNumber is an autopilot machine" + ".`n" } Else { $body = $body + "DeviceFalse" + ".`n" $body = $body + "$(Get-Date)" + " Serial number: $serialNumber is not an autopilot machine" + ".`n" #Write-Host "Device doesn't Exists" } } Catch { $body = $body + "$(Get-Date)" + " $($Error)" + ".`n" $body = $body + "$(Get-Date)" + " Failed to get Device Reference from Intune." + ".`n" } } $body = $body + "$a Exiting Azure function." # Associate values to output bindings by calling 'Push-OutputBinding'. Push-OutputBinding -Name Response -Value ([HttpResponseContext]@{ StatusCode = [HttpStatusCode]::OK Body = $body }) Step 5. Create an enterprise app In Microsoft EntraId, create an enterprise app called PCBuyback Step 6. assign permissions to the app Once created, click on API permissions and using the + Add a permission button, add permissions as I've listed below. Note that these are Application permissions (type) for Microsoft Graph, once done, don't forget to grant permission for your tenant. Step 7. Create a secret In production use Azure key vault, for your lab you can quickly create a secret to test this. Copy the value somewhere safe as you'll need it for the next step. Step 8. Edit the variables in the two triggers In the two http triggers you just created, edit the variables and paste in the Enterprise App ID and secret, and your tenant name like so Once done, save the changes Step 9. Verify the http triggers Now that you've created the triggers and assigned permissions, you'll need to verify that they do what they are supposed to do. Let's start with the GetAPDeviceFromIntune. To test this, paste in the serial number of a Windows Autopilot registered device and click on Test/Run. Replace the serial number below with the serial number of the computer you want to test with. { "serialNumber": "5366-8776-5502-4105-6320-3369-17" } After running, we can see it reports that the device is true as it is a Windows Autopilot registered device. Now we know it works, let's test the other trigger. And that too, works great! That's it for part 1, see you in the next part where we'll create the Win32 app and test it !
-
SCCM - Bitlocker
Bocar FOFANA replied to Bocar FOFANA's topic in System Center Configuration Manager (Current Branch)
MCM vesion 2309. -

SCCM - Bitlocker
anyweb replied to Bocar FOFANA's topic in System Center Configuration Manager (Current Branch)
what version of SCCM are you testing with ? -
SCCM - Bitlocker
Bocar FOFANA replied to Bocar FOFANA's topic in System Center Configuration Manager (Current Branch)
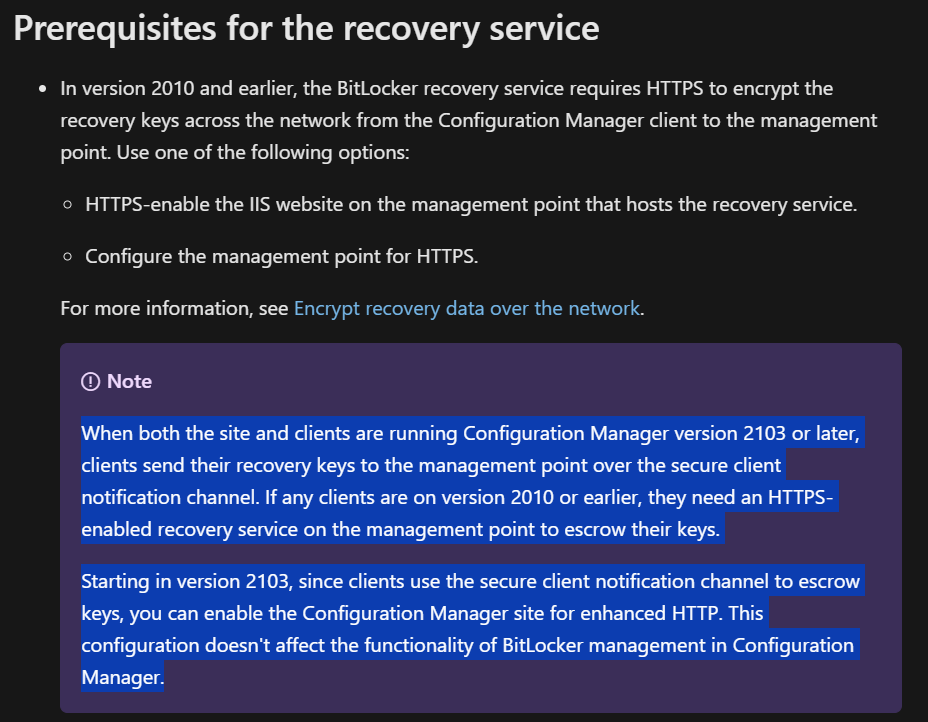
Yes, I saw your article and followed almost all the steps. The only difference is that with the new versions of SCCM, enabling HTTPS on the management point is no longer a prerequisite. Otherwise I did everything the same way. -

SCCM - Bitlocker
anyweb replied to Bocar FOFANA's topic in System Center Configuration Manager (Current Branch)
have you reviewed my guides here ? https://www.niallbrady.com/2019/11/13/want-to-learn-about-the-new-bitlocker-management-in-microsoft-endpoint-manager-configuration-manager/ -
SCCM - Bitlocker
Bocar FOFANA posted a topic in System Center Configuration Manager (Current Branch)
Hello everyone, I want to use SCCM to enable Bitloker encryption on my workstations. I have enabled the functionality on SCCM and created the "helpdesk" and "SelfService" sites. Then I created a Bitlocker policy which I deployed on a few workstations but nothing happens. On the workstations I see this entry in the event log: Unable to connect to the MBAM Recovery and Hardware service. Error code: -2147024809 Details: Incorrect parameter. Can anymone give me help ?? -
I have the following error when I execute my PS script via Run Command Line task in Task Sequence: Severity Type Site code Date / Time System Component Message ID Description Error Milestone CS1 3/22/2024 7:33:20 AM MININT-8DHB01O Task Sequence Engine 11135 The task sequence execution engine failed executing the action (Run Command Line - 15) in the group (Install Operating System) with the error code 3221225781 Action output: ... y Bypass -Command "& { [string] $MacAddress = Get-WmiObject Win32_networkadapterconfiguration | where {$_.ipenabled -match 'True'} | select -ExpandProperty MacAddress | select -First 1; $MacAddress = 'PC'+$MacAddress.Replace(':',''); $TSEnv = New-Objct -COMObject Microsoft.SMS.TSEnvironment; $TSEnv.Value('OSDComputerName') = $MacAddress;}"' SwdAction = '0001' Command line for extension .exe is "%1" %* Set command line: Run command line Working dir 'not set' Executing command line: Run command line Process completed with exit code 3221225781 Command line C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe -NoProfile -ExecutionPolicy Bypass -Command "& { [string] $MacAddress = Get-WmiObject Win32_networkadapterconfiguration | where {$_.ipenabled -match 'True'} | select -ExpandProperty MacAddress | select -First 1; $MacAddress = 'PC'+$MacAddress.Replace(':',''); $TSEnv = New-Object -COMObject Microsoft.SMS.TSEnvironment; $TSEnv.Value('OSDComputerName') = $MacAddress;}" returned 3221225781. The operating system reported error 1: Incorrect function. Regards. Xerkos.
-
Eaven HUANG started following Visio AD template for AD object schema?
-
Dear Experts, I'm trying to export our AD objects and wanted to use diagram software to visually create the schema for better understanding and maintenance of our whole AD hierarchy, mainly I need the OU, group, users and computers collations, I can have different files to store the different schemas. The question is that, I don't know if this is possible somehow in an automatic way? like I export the needed data via powershell then import it to visio for it to generate the schema for me? I'm trying to export the object properties in .csv format, but after importing it to the visio, I don't know how to link the data to the existing Active Directory template so the relationships among the objects can be auto-organized by visio? Any hints would be really appreciated.
-
I don't get involved too much with our SCCM system but I am building a large number of machines and making my own build stick. I'm struggling to work out where I'd put the files that are mapped to X in the above. Would there be a file share mapped during the build process? Could I drop the Disk-Part.Clean.txt file on a folder on the build stick, or at this point in the process can the system not see those folders? Usually we just drop a diskpart.cmd and the txt file on the build stick and press F8 to navigate to it and run it that way, but this obviously looks like a better option.
-
How to read reports
clush replied to clush's topic in System Center Configuration Manager (Current Branch)
Thank you for the clarification.