-
Posts
43 -
Joined
-
Last visited
-
Days Won
2
khawkins last won the day on August 25 2022
khawkins had the most liked content!
Recent Profile Visitors
1,519 profile views
khawkins's Achievements
-

Software Update Point
khawkins replied to khawkins's topic in System Center Configuration Manager (Current Branch)
You're welcome, I remember pulling my hair out over that one for a long time. Will never forget it either. -

CB 1706 PXE boot
khawkins replied to khawkins's topic in System Center Configuration Manager (Current Branch)
Yeah I get a valid IP and can ping the DP\PXE server when F8 in WinPE. I will run the attached script to see if it throws up any missing drivers. -
khawkins started following SCCM 2012 - Active Clients at Risk "Cleaned" , CB 1706 PXE boot and Software Update Point
-
Hi all, I have been working on an issue for the last week relating to PXE booting . It seems to have happened when upgrading to 1706 CB and ADK 1709. I have updated the boot image in sccm and imported the new boot into WDS. All devices boot into PXE but restart after preparing network connections. F8 shows I am getting a valid IP and can ping the DP\PXE server. The boot image is 10.0.16299. We use Dell devices (E7450 Opti 9020 etc) Error Failed to download PXE variable file after retrials. Exit code=22. PxeGetPxeData failed with 0x8004016c smsts.log Troubleshooting; Uninstalled PXE, WDS and deleted the Remoteinstall folder. Reinstalled PXE point Redistributed boot image Can anyone tell me what I am doing wrong here? Thanks Kevin
-
Ok so I got this working after making a lot of work out of it. I hope this helps someone, here are my exact steps; Objective: Powershell script to rename workstation %MODEL%-%SERIALNUMBER% Here is the PowerShell script ******* $ModelNo = (Get-WMIObject -Class WIN32_ComputerSystem).Model.Split(' ')[1] $SerialNo = (Get-WMIObject -Class WIN32_BIOS).SerialNumber $WorkstationName = $ModelNo + '-' + $SerialNo # Workstations $TSEnv = New-Object -COMObject Microsoft.SMS.TSEnvironment $TSEnv.Value("OSDComputerName") = "$WorkstationName" ******** Within the task sequence, this step NEEDS to be AFTER the apply OS and before the domain join Create a package pointing to the .ps1, but do not create a program. Add a TS step as follows -Run PowerShell Script -Package = "package created earlier" -Script name = "scriptname.ps1" -PowerShell execution policy = bypass Thanks everyone for the help. Kevin
-
I'm still not having much luck with this. I have created a package that points to the powershell folder, but with no program. Here is the script; ************ $ModelNo = (Get-WMIObject -Class WIN32_ComputerSystem).Model.Split(' ')[1] $SerialNo = (Get-WMIObject -Class WIN32_BIOS).SerialNumber $WorkstationName = $ModelNo + '-' + $SerialNo Rename-Computer -NewName $WorkstationName -Restart ********** I can confirm it works, as I have ran it manually on an OS and it renames and auto restarts. I then add a run command to the TS (just after the Apply OS step) with the command powershell.exe -file rename.ps1 -executionpolicy -bypass Which fails. I also added a run powershell step and select set to bypass, with the command line rename.ps1 Which also fails. Any ideas?
-

Software Update Point
khawkins replied to khawkins's topic in System Center Configuration Manager (Current Branch)
Ok so finally figured this out. On the ScanAgent.log I was seeing a lot of "Sources are not current" messages. This led me to dig further and that the SUP MUST be in the default boundaries group, which I didn't know. It apparently is new to 1702?!?! Once I added the SUP to the default group clients started reporting in instantly! Hope this helps someone out there. Regards Kevin -

Software Update Point
khawkins replied to khawkins's topic in System Center Configuration Manager (Current Branch)
The Scan update log states that the "Software Updates client configuration policy has not been received, default settings will be used.". I'm very confused, as it is enabled on the default client policy as well as a custom client policy. Just wondering if this could be getting blocked by the AV? <![LOG[Software Updates client configuration policy has not been received, default settings will be used.]LOG]!><time="16:15:11.948-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="11236" file="scantoolpolicy.cpp:648"> <![LOG[- -Recovering persisted Scan requests...]LOG]!><time="16:15:11.948-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="11236" file="scanjobmgr.cpp:118"> <![LOG[CScanAgent::CleanDeletedUpdateSources- entered. This will clean any update sources for which policy no longer exists.]LOG]!><time="16:15:11.963-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="11236" file="cscanagent.cpp:1579"> <![LOG[Software update client config event __InstanceCreationEvent received.]LOG]!><time="16:17:01.015-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="3056" file="cscanagent.cpp:1220"> <![LOG[- -Recovering persisted Scan requests...]LOG]!><time="16:17:37.642-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="9292" file="scanjobmgr.cpp:118"> <![LOG[CScanAgent::CleanDeletedUpdateSources- entered. This will clean any update sources for which policy no longer exists.]LOG]!><time="16:17:37.658-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="9292" file="cscanagent.cpp:1579"> <![LOG[- -Recovering persisted Scan requests...]LOG]!><time="16:25:58.301-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="4148" file="scanjobmgr.cpp:118"> <![LOG[CScanAgent::CleanDeletedUpdateSources- entered. This will clean any update sources for which policy no longer exists.]LOG]!><time="16:25:58.353-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="4148" file="cscanagent.cpp:1579"> <![LOG[Message received: '<?xml version='1.0' ?> <UpdateSourceMessage MessageType='ScanByUpdateSource'> <ForceScan>TRUE</ForceScan> <UpdateSourceIDs> <ID>{349E5FC2-62B1-4624-8733-9C7EAC502719} </ID> </UpdateSourceIDs> </UpdateSourceMessage>' ]LOG]!><time="16:34:01.916-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="3360" file="cscanagent.cpp:1042"> <![LOG[*****ScanByUpdateSource request received with ForceReScan=2, ScanOptions=0x0000000a, WSUSLocationTimeout = 604800]LOG]!><time="16:34:02.837-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="3360" file="cscanagent.cpp:216"> <![LOG[Sources are not current]LOG]!><time="16:34:04.556-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="3360" file="utils.cpp:104"> <![LOG[ScanJob({7B191E15-CD28-4FE8-9578-D05F84B25036}): - - - - - -Locations requested for ScanJobID={7B191E15-CD28-4FE8-9578-D05F84B25036} (LocationRequestID={40869FF1-8BCF-4021-A1A0-7FCAF8ED9B71}), will process the scan request once locations are available.]LOG]!><time="16:34:06.713-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="3360" file="utils.cpp:477"> <![LOG[Software update client config event __InstanceModificationEvent received.]LOG]!><time="16:58:03.507-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="1384" file="cscanagent.cpp:1220"> <![LOG[- -Recovering persisted Scan requests...]LOG]!><time="17:37:16.987-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="4396" file="scanjobmgr.cpp:118"> <![LOG[ScanJob({7B191E15-CD28-4FE8-9578-D05F84B25036}): CScanJob::Scan - Recovered Scan request with LocationRequestID={40869FF1-8BCF-4021-A1A0-7FCAF8ED9B71}. It is still waiting for Locations, will process the scan request once Locations are available.]LOG]!><time="17:37:17.019-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="4396" file="utils.cpp:477"> <![LOG[CScanAgent::CleanDeletedUpdateSources- entered. This will clean any update sources for which policy no longer exists.]LOG]!><time="17:37:17.019-60" date="06-07-2017" component="ScanAgent" context="" type="1" thread="4396" file="cscanagent.cpp:1579"> <![LOG[- -Recovering persisted Scan requests...]LOG]!><time="09:38:43.471-60" date="06-08-2017" component="ScanAgent" context="" type="1" thread="6872" file="scanjobmgr.cpp:118"> <![LOG[ScanJob({7B191E15-CD28-4FE8-9578-D05F84B25036}): CScanJob::Scan - Recovered Scan request with LocationRequestID={40869FF1-8BCF-4021-A1A0-7FCAF8ED9B71}. It is still waiting for Locations, will process the scan request once Locations are available.]LOG]!><time="09:38:43.565-60" date="06-08-2017" component="ScanAgent" context="" type="1" thread="6872" file="utils.cpp:477"> <![LOG[CScanAgent::CleanDeletedUpdateSources- entered. This will clean any update sources for which policy no longer exists.]LOG]!><time="09:38:43.580-60" date="06-08-2017" component="ScanAgent" context="" type="1" thread="6872" file="cscanagent.cpp:1579"> <![LOG[- -Processing Scan Job TTL invalidity request]LOG]!><time="16:28:11.219-60" date="06-08-2017" component="ScanAgent" context="" type="1" thread="2804" file="scanjobmgr.cpp:610"> <![LOG[Message received: '<?xml version='1.0' ?> <UpdateSourceMessage MessageType='ScanByUpdateSource'> <ForceScan>TRUE</ForceScan> <UpdateSourceIDs> <ID>{349E5FC2-62B1-4624-8733-9C7EAC502719} </ID> </UpdateSourceIDs> </UpdateSourceMessage>' ]LOG]!><time="16:28:13.769-60" date="06-08-2017" component="ScanAgent" context="" type="1" thread="2804" file="cscanagent.cpp:1042"> <![LOG[*****ScanByUpdateSource request received with ForceReScan=2, ScanOptions=0x0000000a, WSUSLocationTimeout = 604800]LOG]!><time="16:28:13.769-60" date="06-08-2017" component="ScanAgent" context="" type="1" thread="2804" file="cscanagent.cpp:216"> <![LOG[Sources are not current]LOG]!><time="16:28:13.805-60" date="06-08-2017" component="ScanAgent" context="" type="1" thread="2804" file="utils.cpp:104"> <![LOG[ScanJob({60E34093-608A-479C-849B-82745C72A00E}): - - - - - -Locations requested for ScanJobID={60E34093-608A-479C-849B-82745C72A00E} (LocationRequestID={8711969D-99B1-48E3-8014-118A3BDD3EC0}), will process the scan request once locations are available.]LOG]!><time="16:28:13.974-60" date="06-08-2017" component="ScanAgent" context="" type="1" thread="2804" file="utils.cpp:477"> -
Hi guys, I have read a few articles on this but I am struggling on how to get this to work. We have dell PC's\Laptops and we need to automate the name of a new device build with the format ModelNumber-SerialNumber eg. "E5550-JAJJAJA". I have MDT integrated and I am using the gather step to gather device info. I have set the OSDComputerName value to %MODEL%-%SERIALNUMBER% This isn't working, which I suspect is because the model name is usually "Latitude E5550". Am I going about this the right way? Should I be using gather or is there another option to automate this? Thanks Kevin
-
Hi all, I am having an issue with clients contacting the SCCM SUP. This is a fresh install of SCCM 1702 on a server 2012 R2 and Windows 10 environment. All is working as expected, except even the Software Update Point. WSUS is on its own Server and SCCM talks to it and pulls in all the updates. I can create SU groups and used scheduled updates to inject the patches into my wim. BUT clients are not talking to SCCM SUP, all the updates have "0" required\installed against them. The environment did have WSUS for patching previously, so I have excluded all WSUS Group Policies, by blocking inheritance on the OU. I have enabled SUP in client settings and applied them to the clients. When I check the locationservices.log there is no trace of the "WSUS path=http://" telling the clients to go to their SCCM SUP server. Also the clients do not have any register settings created by SCCM to point them to their SUP. I'm at a loss as to where to look now? It must be something simple! Any advice much appreciated. Thanks Kevin
-
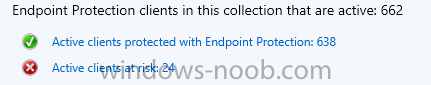
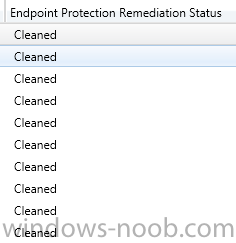
Hi all, So we have SCEP deployed to all clients in our environment. When looking at our servers status there is 24 at risk. When I dig in further they all have an "Endpoint Protection Remediation Status" of "Cleaned". Great! From my understanding, the server has had a threat and it has automatically been cleaned. My question is, how do I reset this status back to "Active clients protected with Endpoint Protection"? When we have a status of 24 at risk, it looks bad and they never seem to go back to a protected status. Thanks Kevin
-
Thanks M13LU, Thats how I uninstalled it initially. It eventually started working after a week of failing. I'm still unsure of why it started working. The only thing I can think of that might have fixed it was installing a new Web Server Cert on the server that was not installing the client, even though the original cert was working. I'm not convinced though. Regards Kevin