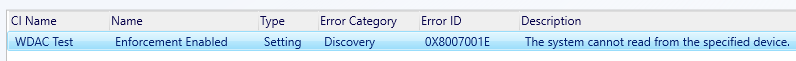
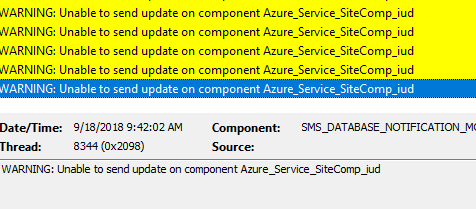
-
Posts
54 -
Joined
-
Last visited
Everything posted by Judical
-

Missing some Office 365 Updates
Judical replied to hecke1234's topic in System Center Configuration Manager (Current Branch)
Hello, It looks like the download for that update was broken at some point. -Judical -
deleted
-
Hello, Has any devised a way to separate Office 2013 from 2016 (Click to Run) in a query? -Judical
-
Are you using this Peter? Its pointing at the old Lenovo site that was removed just like the original script I had linked. -Judical
-
This was resolved by updating SCCM.
-
Update to this. I called Microsoft and they gave me the missing files, problem solved.
-

Adding currently loggin in user to Admin Group
Judical replied to Judical's topic in Configuration Manager 2012
for /F "tokens=1,2" %%i in ('qwinsta /server:%COMPUTERNAME% ^| findstr "console"') do set tempVar=%%j -
Is there an up to date way for pulling this information with SCCM? This was the previous way to do it. https://sccmguru.wordpress.com/2014/04/24/hp-and-lenovo-warranty-information-in-configuration-manager-2012-r2/ This script is attached since its not available anymore on the site Can any scriptwriters in the forums try to modify the existing script to add this; $test = Invoke-WebRequest -uri http://support.lenovo.com/us/en/warrantylookup-SessionVariable ln $form = $test.forms[0] $serial = 'MJNECHL' $form.Fields["serialCode"]="$($serial)" $answer = Invoke-WebRequest -Uri ("http://support.lenovo.com"+ $form.Action) -WebSession $ln -Method $form.Method -Body $form.Fields $a = $answer.ParsedHtml.getElementById("warranty_result_div").outerText $a.Substring(39,10) -Judical
-

Adding currently loggin in user to Admin Group
Judical replied to Judical's topic in Configuration Manager 2012
deleted resolved -
Hello, Is there a way to do this? I have tried several different methods and it just ends up adding the computer name to admin group. When run a package from SCCM with admin rights %username% ends up being the computer name. Is there a way around this? -Judical
-
I was hoping it could be done without a GPO. Looking around the internet people say they have it working with a similar script to mine.
-
I am having issues trying to get the lockscreen to stick. It will show for for the first boot then revert back to a Microsoft picture. This is what I am currently using; echo f | XCOPY "%~dp0lockscreen.jpg" "C:\Windows\Web\Screen\img100.jpg" /HRCY REG ADD "HKLM\SOFTWARE\Policies\Microsoft\Windows\Personalization" /V "LockScreenImage" /T REG_SZ /D "C:\Windows\Web\Screen\img100.jpg" /F I recently added the registry entry but that isn't making a difference. Can this only be done through GPO or am I doing something wrong? -Judical
-
My backups do not go back far enough. I will be able to modify the files if I can get my hands on them. I'm looking for smsbkup.ctl and afterbackup.bat
-
Can someone please share the contents of smsbkup.box so that I may resolve my problem?
-
Hello, Does anyone have any knowledge to recreate this folder. For some reason I do not have it and constantly seeing SMS_SITE_BACKUP failures. If someone could send me this folder from their current setup I could modify the smsbkup.ctl file for my environment and it should work. -Judical
-
Device: * Component: BITS Server Extensions Severity: Warning Time: 2015/12/17 07:53:53.000 Message: The user Anonymous-Null could has created 52 upload sessions in virtual directory /LM/W3SVC/1/Root/CCM_Incoming. Over the past 3 days I have started receiving these warnings caused by my SCCM server. Does anyone know what would prompt this? I am running SCCM 2012 R2 SP1 CU2 -Justin
-
I have been testing this with no luck. There is only 1 group with .Net updates. Here is UpdatesStore.log Querying update status of 14 updates. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (151e15f7-fa7a-40c4-a58a-721cb88e8071): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB2972107), BulletinID=MS14-057, QNumbers=2972107, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (9a905b4e-94e7-4f23-891c-40c0185605de): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB2972107), BulletinID=MS14-057, QNumbers=2972107, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (6c8c0ac4-f40b-4e4b-aa83-1694fe0dbec2): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB3037581), BulletinID=MS15-041, QNumbers=3037581, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (647db682-170f-4d52-b682-50a587669fc8): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB3037581), BulletinID=MS15-041, QNumbers=3037581, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (84baf93f-3645-4ef2-887a-d1e5e883adc7): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB3023224), BulletinID=MS15-048, QNumbers=3023224, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (25cbae55-974b-45c9-8b4b-78ed1485ed45): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB3023224), BulletinID=MS15-048, QNumbers=3023224, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (922de694-c7e6-42ac-8738-95f5a8e2390e): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB3035490), BulletinID=MS15-048, QNumbers=3035490, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (642b981f-bf50-467e-b0f3-30ef96ca6cd9): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB3035490), BulletinID=MS15-048, QNumbers=3035490, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (d44bd7d1-ec33-4a65-942c-093aec39b02b): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB2979578), BulletinID=MS14-057, QNumbers=2979578, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (3301d1d8-517e-4e7e-81c3-42ca6609a31a): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB2979578), BulletinID=MS14-057, QNumbers=2979578, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (e257d135-40b9-4361-9e7d-8537d256d54b): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB2978128), BulletinID=MS14-072, QNumbers=2978128, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (cedf67fc-735e-4360-8db4-c8cb5d39663c): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB2978128), BulletinID=MS14-072, QNumbers=2978128, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (e63b4eca-27a1-4fd0-b311-e468da0cd02e): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB2972216), BulletinID=MS14-053, QNumbers=2972216, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Queried Update (108336d1-2d2c-4d93-87b3-49d335640f2a): Status=Missing, Title=Security Update for Microsoft .NET Framework 4.5, 4.5.1 and 4.5.2 on Windows 7, Vista, Server 2008, Server 2008 R2 x64 (KB2972216), BulletinID=MS14-053, QNumbers=2972216, LocaleID=, ProductID=0fa1201d-4330-4fa8-8ae9-b877473b6441, UpdateClassification = 0fa1201d-4330-4fa8-8ae9-b877473b6441, ExcludeForStateReporting=FALSE. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) Querying update status completed successfully. UpdatesStore 7/31/2015 10:48:40 AM 1328 (0x0530) All of the updates are found as missing. Then here is UpdatesDeployment.log EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 0 UpdatesDeploymentAgent 7/31/2015 11:36:03 AM 1816 (0x0718) EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 0 UpdatesDeploymentAgent 7/31/2015 11:36:42 AM 4428 (0x114C) EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 0 UpdatesDeploymentAgent 7/31/2015 11:36:42 AM 3144 (0x0C48) -Judical
-

Windows 8.1 doesn't continue after 1st reboot
Judical replied to Rushal's topic in Configuration Manager 2012
2015-07-24 00:42:21, Warning [0x0606cc] IBS GetSystemPartitionPath: Unable to find DOS drive path for system partition [\Device\HarddiskVolume1]. Run diskpart clean disk 0 and give it another try. -
Hello, When you run the task sequence it installs the image, installs the drivers, then restarts. You need to make sure the correct drivers are in your driver package not in the boot image. Since your task sequence is starting you already have the correct drivers in your boot image. -Judical
-
Is there a setting somewhere that would not allow .Net updates to deploy? My client sees them as missing but they do not install and there are no errors in the logs. I assume I'm just missing some setting somewhere that would fix this. Please let me know what you think. -Judical
-

SCCM 2012 "Updates will not be made available"
Judical replied to Judical's topic in Configuration Manager 2012
I do not see the updates in software center only available applications. UpdatesStore.log is finding that many updates are missing(which they are), all of the updates are deployed to the collection that the computers reside in. Office updates and Endpoint Protection definitions are deploying without any issues. WUAHandler.log and WindowsUpdate.log have no errors.