Search the Community
Showing results for tags 'hybrid azuread join'.
-
HI On a Windows 10 OSD TS, i want ot add the Bitlocker recover Key to Azure for Hybrid Joined devices. How can i achive this from an SCCM TS? Thanks
-
- hybrid azuread join
- task sequence
-
(and 3 more)
Tagged with:
-
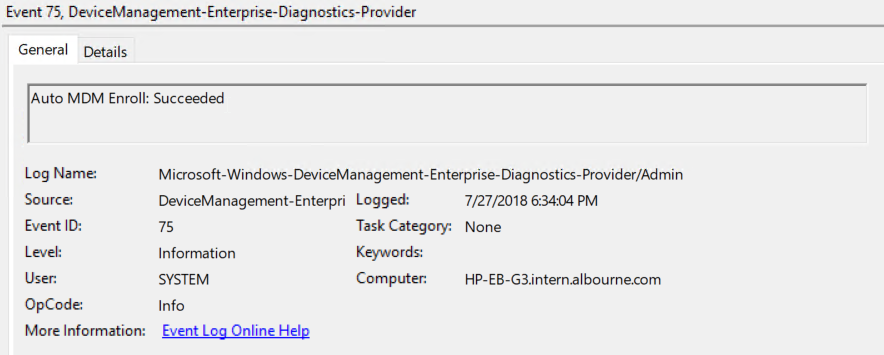
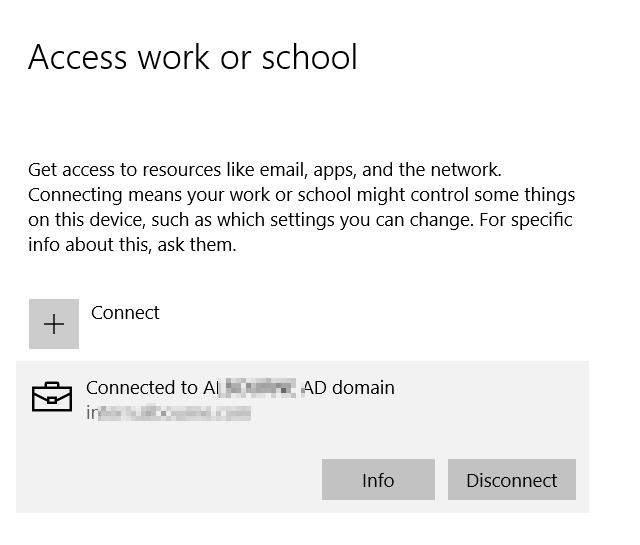
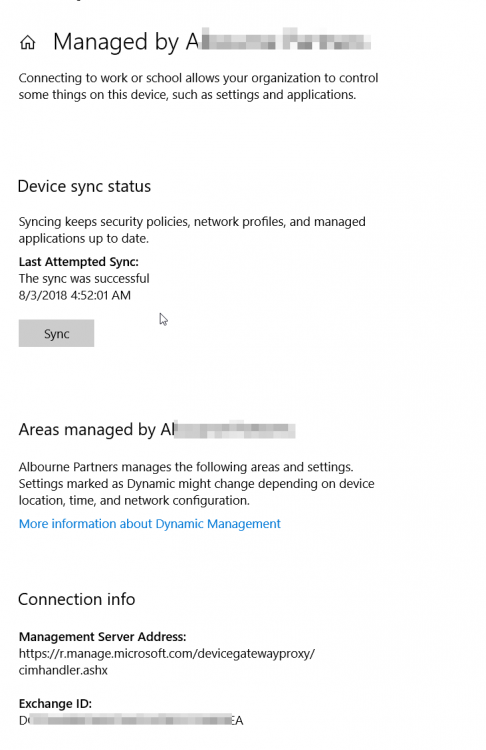
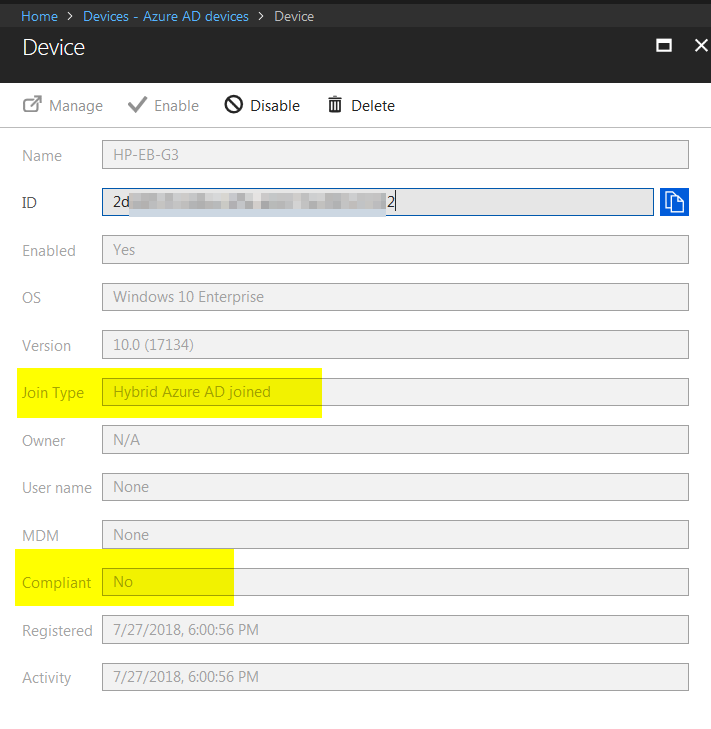
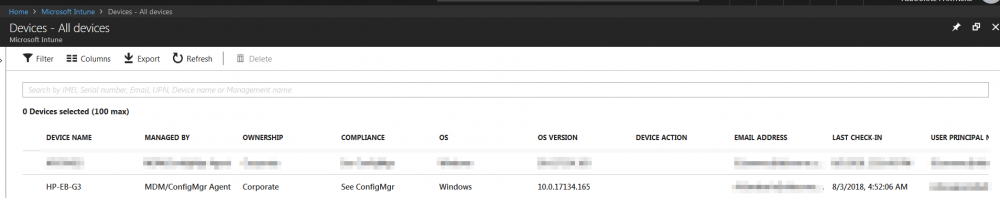
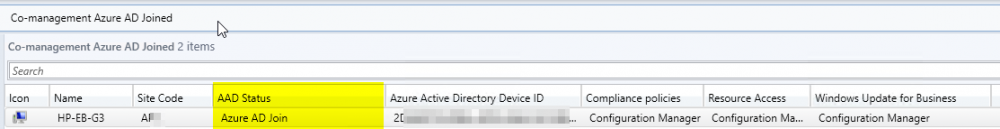
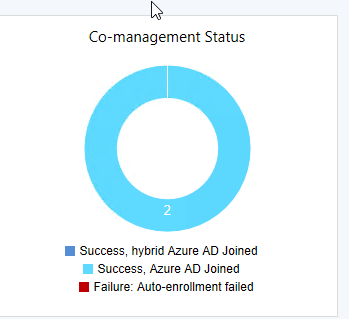
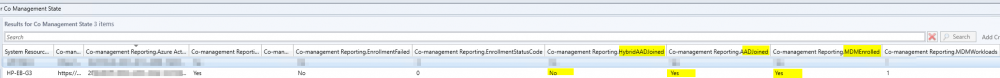
I am facing a very weird issue with SCCM CoManagement where Windows 10 machines registered to AzureAD in Hybrid Azure AD Join, are shown as Azure AD Joined. I will be focusing on one machine so we see the issue in depth. Configuration details SCCM Current Branch 1802 with all three hotfixes installed Windows 10 Enterprise 1803 with latest updates Co-Management Enabled for All Devices (no pilot group) No workloads have yet been migrated to Intune Group Policies for Automatic Enrollment to MDM and Automatic Registration with AzureAD enabled SCCM Client Cloud option for Automatic Registration enabled Intune set as Standalone Intune Enrollment set as MDM only (MAM disabled) ADFS Federated Domain 3.0 (2012R2) with AAD Connect Federation Facts SSO et. all are working as expected on the client Client detects client as Hybrid Azure AD Joined Intune detects client as Hybrid Azure AD Joined Issue SCCM detects client as Azure AD Joined I will now provide all relevant screenshots from Intune, SCCM and Client. SCCM As seen below, SCCM thinks the device is Azure AD Join and not Hybrid Azure AD Join. I also used the following SCCM query: select SMS_R_System.NetbiosName, SMS_Client_ComanagementState.Authority, SMS_Client_ComanagementState.AADDeviceID, SMS_Client_ComanagementState.ComgmtPolicyPresent, SMS_Client_ComanagementState.EnrollmentErrorDetail, SMS_Client_ComanagementState.EnrollmentFailed, SMS_Client_ComanagementState.EnrollmentStatusCode, SMS_Client_ComanagementState.HybridAADJoined, SMS_Client_ComanagementState.MDMEnrolled, SMS_Client_ComanagementState.MDMWorkloads, SMS_Client_ComanagementState.AADJoined from SMS_R_System inner join SMS_Client_ComanagementState on SMS_Client_ComanagementState.ResourceID = SMS_R_System.ResourceId where SMS_Client_ComanagementState.ComgmtPolicyPresent = 1 and SMS_Client_ComanagementState.MDMEnrolled = 1 And had the following results, same probem. Azure AD Joined = Yes, Hybrid Azure AD Joined = No AzureAD As seen on the Devices > Azure AD Devices, the machine is properly detected as Hybrid Azure AD Joined As seen below, DeviceTrustType = Domain Joined and DeviceTrustLevel = Managed should be correct (see here). Get-MsolDevice -Name hp-eb-g3 Enabled : True ObjectId : cxxxxxxxxxxxxxxxxxxxxxxxx0 DeviceId : 2xxxxxxxxxxxxxxxxxxxxxxxxxxxxx2 DisplayName : HP-EB-G3 DeviceObjectVersion : 2 DeviceOsType : Windows 10 Enterprise DeviceOsVersion : 10.0 (17134) DeviceTrustType : Domain Joined DeviceTrustLevel : Managed DevicePhysicalIds : {[USER-GID]:2xxxxxxxxxxxxxxxxxxxxxxxxxxxxxx2, [GID]:g:6xxxxxxxxxxxxxxxx2, [USER-HWID]:2xxxxxxxxxxxxxxxxxxxxxxxxxxxxx2, [HWID]:h:6xxxxxxxxxxxxxxxxxx2} ApproximateLastLogonTimestamp : 27/07/2018 15:00:56 AlternativeSecurityIds : {X509:<SHA1-TP-PUBKEY>0xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx} DirSyncEnabled : True LastDirSyncTime : 03/08/2018 02:31:16 RegisteredOwners : {} GraphDeviceObject : Microsoft.Azure.ActiveDirectory.GraphClient.Device Intune This is how the device shows up in Intune Client DeviceManagement Log event 75 properly happened Client properly seeing management from Intune dsregcmd properly recognizes machine as AAD and MDM enrolled and AD Domain Joined dsregcmd /status +----------------------------------------------------------------------+ | Device State | +----------------------------------------------------------------------+ AzureAdJoined : YES EnterpriseJoined : NO DeviceId : 2xxxxxxxxxxxxxxxxxxxxxxxxx2 Thumbprint : 0xxxxxxxxxxxxxxxxxxxxxxA KeyContainerId : cxxxxxxxxxxxxxxxxxxxxxx7 KeyProvider : Microsoft Platform Crypto Provider TpmProtected : YES KeySignTest: : PASSED Idp : login.windows.net TenantId : 9xxxxxxxxxxxxxxxxxxx2 TenantName : Axxxxxxxxxxxxxs AuthCodeUrl : https://login.microsoftonline.com/9xxxxxxxxxxxxxxxxxxxx2/oauth2/authorize AccessTokenUrl : https://login.microsoftonline.com/9xxxxxxxxxxxxxxxxxxxxxxxxx2/oauth2/token MdmUrl : https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc MdmTouUrl : https://portal.manage.microsoft.com/TermsofUse.aspx MdmComplianceUrl : https://portal.manage.microsoft.com/?portalAction=Compliance SettingsUrl : JoinSrvVersion : 1.0 JoinSrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/device/ JoinSrvId : urn:ms-drs:enterpriseregistration.windows.net KeySrvVersion : 1.0 KeySrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/key/ KeySrvId : urn:ms-drs:enterpriseregistration.windows.net WebAuthNSrvVersion : 1.0 WebAuthNSrvUrl : https://enterpriseregistration.windows.net/webauthn/9xxxxxxxxxxxxxxxxxxxxxxxxxxxx2/ WebAuthNSrvId : urn:ms-drs:enterpriseregistration.windows.net DeviceManagementSrvVersion : 1.0 DeviceManagementSrvUrl : https://enterpriseregistration.windows.net/manage/9xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx2/ DeviceManagementSrvId : urn:ms-drs:enterpriseregistration.windows.net DomainJoined : YES DomainName : XXXXXXXXXX +----------------------------------------------------------------------+ | User State | +----------------------------------------------------------------------+ NgcSet : NO WorkplaceJoined : NO WamDefaultSet : YES WamDefaultAuthority : organizations WamDefaultId : https://login.microsoft.com WamDefaultGUID : {Bxxxxxxxxxxxxxxxxxxxxxxxxxxxxx0} (AzureAd) AzureAdPrt : YES AzureAdPrtAuthority : https://login.microsoftonline.com/9xxxxxxxxxxxxxxxxxxxxxxxxxx2 EnterprisePrt : NO EnterprisePrtAuthority : +----------------------------------------------------------------------+ | Ngc Prerequisite Check | +----------------------------------------------------------------------+ IsUserAzureAD : YES PolicyEnabled : NO PostLogonEnabled : YES DeviceEligible : YES SessionIsNotRemote : NO CertEnrollment : none AadRecoveryNeeded : NO PreReqResult : WillNotProvision Can anyone having a similar configuration crosscheck and let me know what difference there is? References: https://www.imab.dk/flipping-the-switch-how-to-enable-co-management-in-configuration-manager-current-branch/ https://allthingscloud.blog/automatically-mdm-enroll-windows-10-device-using-group-policy/ -- Alex
- 6 replies
-
- hybrid azuread join
- aad
-
(and 6 more)
Tagged with: