Search the Community
Showing results for tags 'issuing'.
-
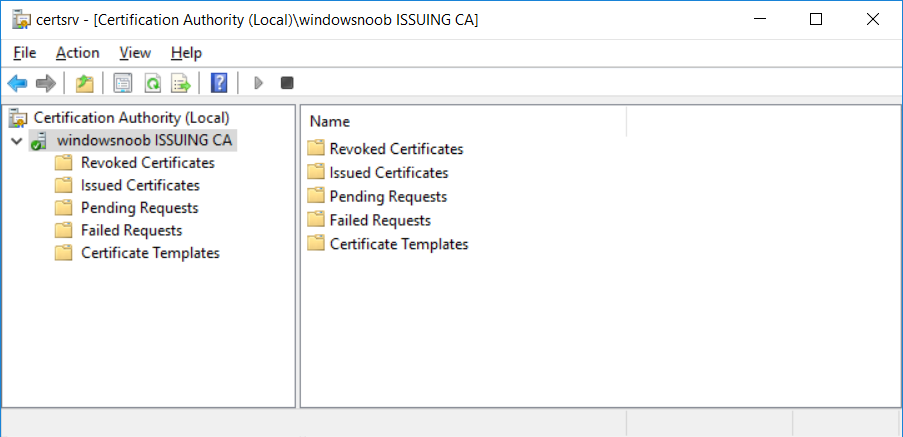
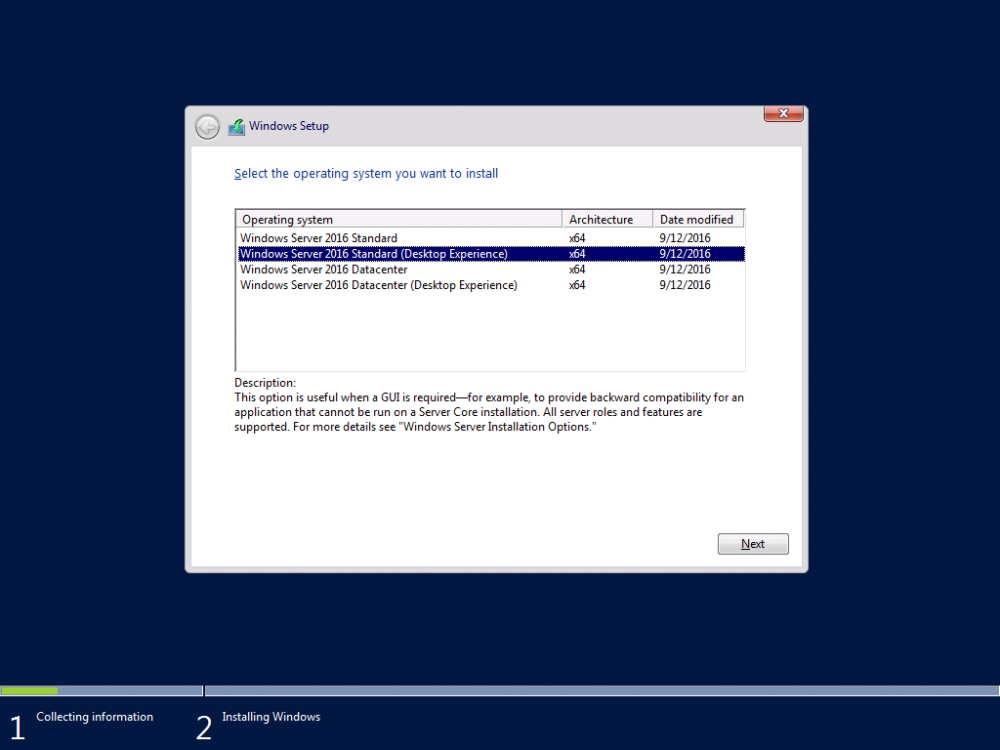
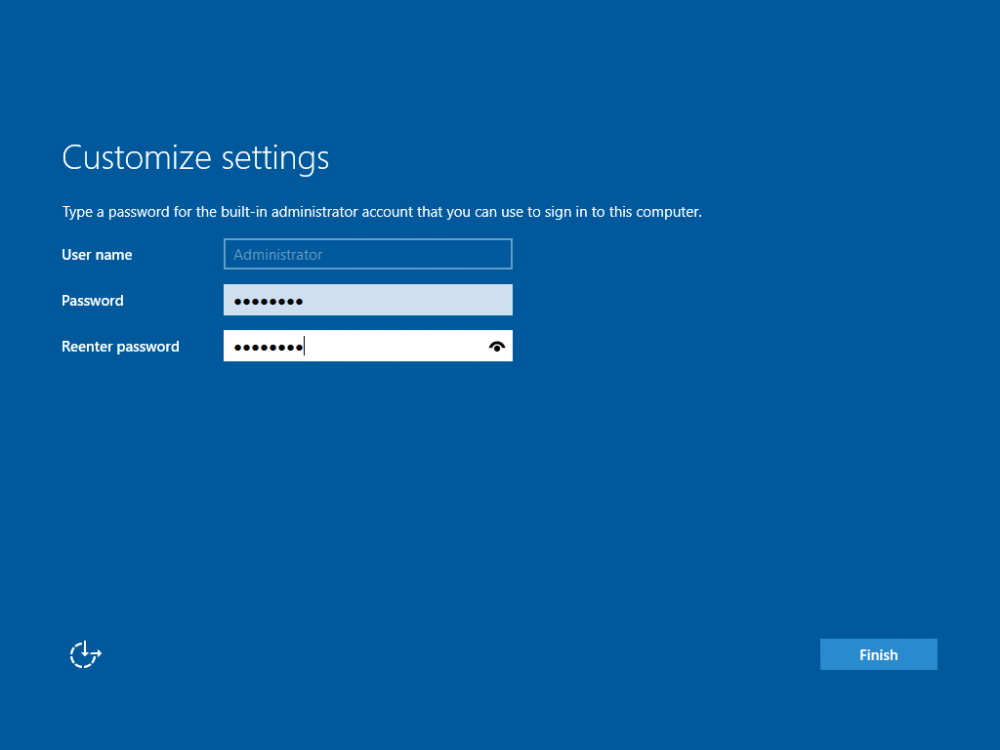
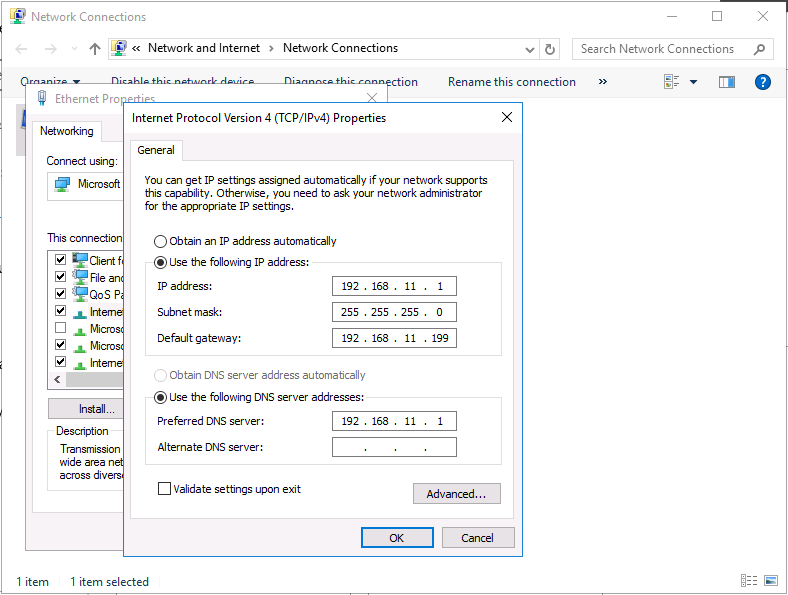
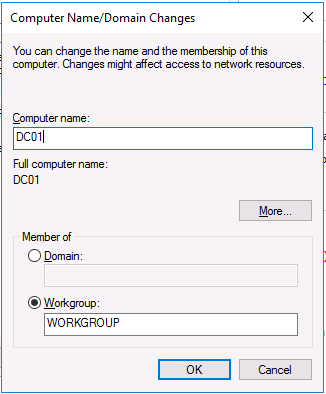
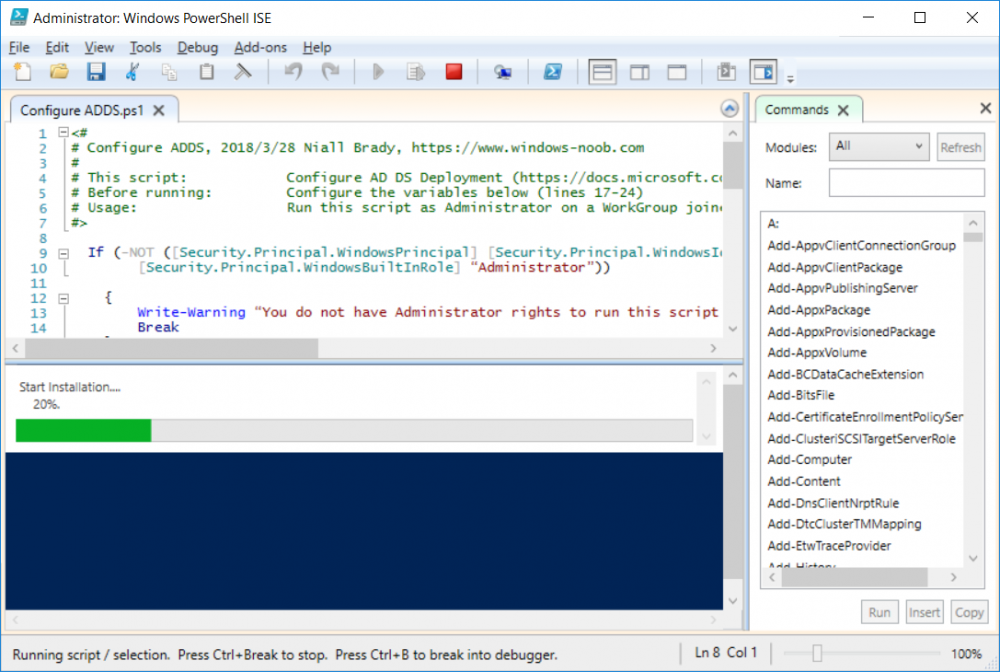
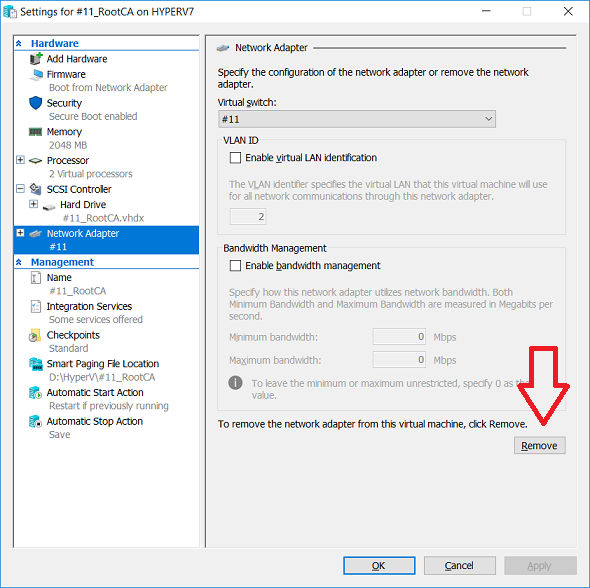
This series is comprised of different parts, listed below. Part 1 - Introduction and server setup (this part) Part 2 - Install and do initial configuration on the Standalone Offline Root CA Part 3 - Prepare the HTTP Web server for CDP and AIA Publication Part 4 - Post configuration on the Standalone Offline Root CA Part 5 - Installing the Enterprise Issuing CA Part 6 - Perform post installation tasks on the Issuing CA Part 7 - Install and configure the OCSP Responder role service Part 8 - Configure AutoEnroll and Verify PKI health Introduction Security is everywhere, and a core component of security is certificates. Public key infrastructure (PKI) is a set of roles, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates and manage public-key encryption (1). In this series of guides I will show you how to set up a 2 tier PKI hierarchy running on Windows Server 2016 and you can use this to set up your own LAB so that you can learn about PKI and later use it for related System Center Configuration Manager roles such as Co-Management (3). Note: I don't claim to be an expert on PKI and would absolutely advise you to consult with a PKI expert if you plan on setting up PKI in production. This guide is designed to help you setup your LAB, it's based on a Windows Server 2012 R2 PKI guide on Technet from here and kudos to those guys for writing it (2). The difference here is you'll be using Windows Server 2016 and you'll see more screenshots and hints to guide you through the experience. I'd highly recommend you go through this entire series at least twice, just to get a feel for how PKI works and to become familiar with the terms involved. The first time you complete this series will probably feel laborious, however the second time you do it things will start to make sense and you'll have a better understanding of why you are doing it. This series will be tough to wrap your head around especially if you are new to PKI, but take it one part at a time, one step at a time, methodically. If in any doubt, about any of the content then please ask your questions here by starting a new thread. By the end of this series of guides you'll have the following setup and running in your windowsnoob.lab.local PKI LAB. Domain Controller (Windows Server 2016) - 192.168.11.1 Issuing CA (Windows Server 2016) - 192.168.11.2 Webserver (Windows Server 2016) - 192.168.11.3 Offline Root CA (Windows Server 2016) Windows 10 (Windows 10 Enterprise, version 1803) - 192.168.11.4 (Optional) Smoothwall NAT (linux) - 192.168.11.199 and MMC based applications like this screenshot from the Enterprise Issuing CA will become familiar to you Before we start the series let's list some of the terms you'll see popping up over and over. I will try to explain them as we move through the guide. PKI - Public Key Infrastructure AIA - Authority Information Access CDP - Certificate revocation list Distribution Point CRL - Certificate Revocation List OCSP - Online certificate status protocol CA - Certificate Authority Note: I'd recommend that you snapshot (checkpoint) the Virtual Machines at the end of each part of this series, so if you make a mistake, you can always back track to a known good state. Step 1. Create the Virtual Machines I use Hyper-V for my labs, as it's a role built into Windows Server 2016 (and even Windows 10), so as long as your computer is relatively new and the hardware supports virtualization, you can use it (simply enable the role, reboot, and start using it). You should have at least 16GB of ram and 500GB of SSD storage to set this lab up comfortably. To quickly create the virtual machines I use a PowerShell script which I wrote, you can download it here. Download the script - Create HyperV VMv2.ps1 Virtual Machine Names For this LAB, please use the following naming convention for your virtual machines (note this is not the computer name but the virtual machine name). #11_DC01 #11_IssuingCA #11_RootCA #11_W10_1803 #11_Webserver #11_Smoothwall Note: The #11 prefix is simply a method I use in Hyper-V to separate my labs visually in Hyper-v manager, so #11 is one lab, and #10 is another (and so on). You don't have to use the same convention as I do, but it would make it easier for you to follow the entire series. I use the Smoothwall linux based NAT to provide Port Forwarding capability and to share internet into my various LABs. Virtual Machine Roles The Virtual Machines created will have the following functions #11_DC01 Roles: DC, DNS, LDAP CDP,AIA #11_IssuingCA Roles: Enterprise Issuing CA #11_RootCA Roles: Standalone Offline Root CA #11_W10_1803 Roles: A Windows client #11_Webserver Roles: Webserver HTTP CDP, AIA #11_Smoothwall Roles: Port Forward, Internet sharing Note: When prompted for a network switch, create a unique one (#11) for the first VM created, and use the same one for each of the other vm's (we will remove the network from the Offline Root CA). For generation type, use Gen 2. Below is how I created the virtual machines listed above. Note: After creating the virtual machines and before installing Windows Server 2016 on the Offline Root CA, you must remove the Network Card for the Offline Root CA virtual machine as it should not be connected to any network. Step 2. Install the virtual machines Install Server 2016 On DC01, RootCA, IssuingCA and Webserver, install Windows Server 2016. It's up to you how to do this, you can use an Automated MDT PowerShell script, or install them manually. To install all Windows Server 2016 on all 4 servers as WorkGroup joined computers do as follows.. Choose Windows Server 2016 Standard (Desktop Experience) Continue through the installation wizard until prompted for a password, use P@ssw0rd as the Administrator password Click Finish. And then logon using the Administrator username and password configured above. Once Windows is installed, set the IP address for each virtual machine as shown below. Note: Below are the Computer Name and IP addresses used in this guide. For the Offline Root CA, you must remove the Network card in the Hyper-V virtual machine settings. Computer Name: DC01, IP address: 192.168.11.1, Subnet mask 255.255.255.0, Default gateway: 192.168.11.199, Preferred DNS server: 192.168.11.1 Computer Name: IssuingCA, IP address: 192.168.11.2, Subnet mask 255.255.255.0, Default gateway: 192.168.11.199, Preferred DNS server: 192.168.11.1 Computer Name: Webserver, IP address: 192.168.11.3, Subnet mask 255.255.255.0, Default gateway: 192.168.11.199, Preferred DNS server: 192.168.11.1 Computer Name: RootCA, IP: <NO NETWORK> Computer Name: W101803, IP address: 192.168.11.4, Subnet mask 255.255.255.0, Default gateway: 192.168.11.199, Preferred DNS server: 192.168.11.1 Computer Name: smoothwall11, IP address: (Green, static) 192.168.11.199 (Red, DHCP internet IP) x.x.x.x Here's how you can set the IP address for DC01. And configure the Computer Name as per the list (in this example it's for the Domain Controller) Reboot when prompted. Install Windows 10 Enterprise version 1803 Install Windows 10 Enterprise, version 1803 on the remaining virtual machine (#11_W10_1803). Configure the Computer Name and IP address as specified. Leave it WorkGroup joined. Optionally install Smoothwall To learn how to setup Smoothwall express as a firewall see this blog post. Step 3. Configure ADDS on DC01 Now that you've installed the servers, it's time to make DC01 a domain controller, to do that we'll install Active Directory Domain Services (ADDS) and to do that we'll use this PowerShell script, simply run the script as Administrator in Windows PowerShell ISE on DC01. Download the script -Configure ADDS.ps1 After running the script, DC01 is prompted to a Domain Controller and is ready for the next part of this series. Note: Please only run this script on the DC01 virtual machine. After running the script, the Domain Controller is ready for Part 2 (configured as dc01.windowsnoob.lab.local) and internet is working (via the Smoothwall) To continue with Part 2 of this series, click here. Recommended reading (1) - https://en.wikipedia.org/wiki/Public_key_infrastructure (2) - https://social.technet.microsoft.com/wiki/contents/articles/15037.ad-cs-step-by-step-guide-two-tier-pki-hierarchy-deployment.aspx (3) - https://docs.microsoft.com/en-us/sccm/core/clients/manage/co-management-overview
- 2 replies
-
- 2
-

-
- co-mangement
- ca
-
(and 12 more)
Tagged with: