-
Posts
9,108 -
Joined
-
Last visited
-
Days Won
363
Posts posted by anyweb
-
-
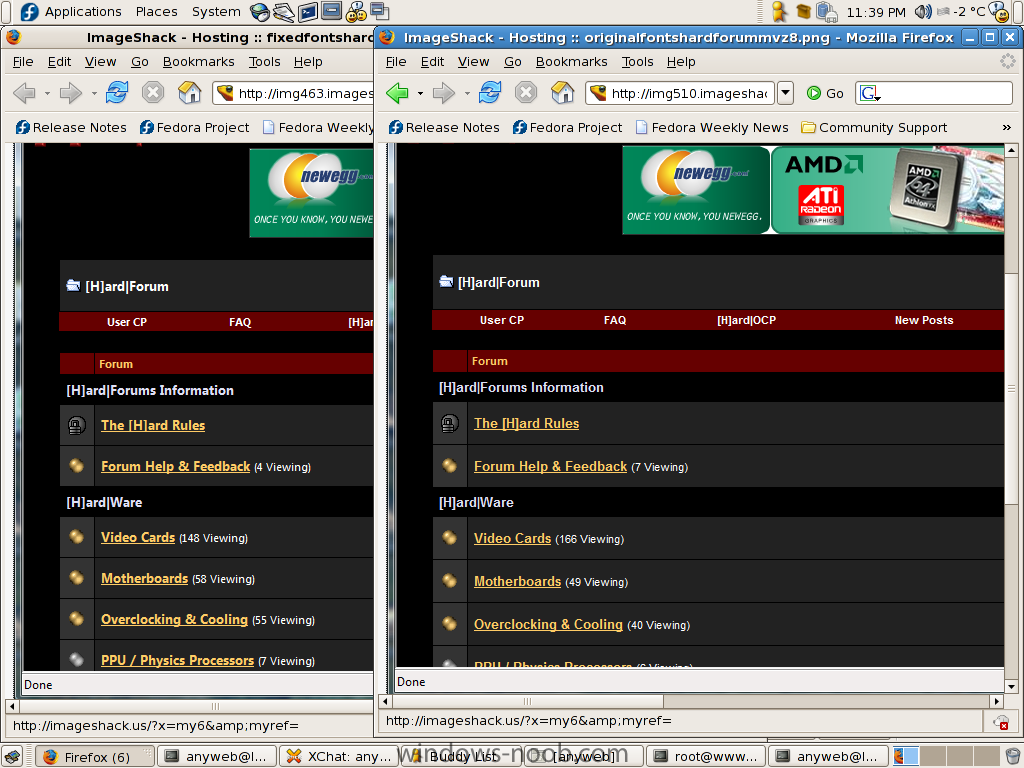
spot the difference
http://img510.imageshack.us/my.php?image=o...rdforummvz8.png
http://img463.imageshack.us/my.php?image=f...orummainqy8.png
cheers
anyweb
-
if you are testing vista and the 30 days are about to run out (and you want to preserve your MSDN keys...) then try this for an extra 30 days
Approx 29.5 days in, press Windows + R and type cmd.exe then Enter. When the Command Prompt appears, type: slmgr -rearm (press Enter)
cheers
anyweb
-
welcome to the forums !

-
if you have windows vista and 4gb ram you might not see it all reported in the os, if so consider getting the 64bit edition of vista instead, but make sure that your hardware will run with it (plus 64bit drivers are harder to get)
cheers
anyweb
-
have a look at this photo (top) found on the intarweb today http://www.googlethedamnthing.com/mirror/v...owned/owned.jpg
reminds me of this one (bottom) a few years back
-
during windows setup you got an error 'no hard disc drives found'.
This is due to the fact that windows doesn’t know how to communicate with the AHCI sata controller, and hence, cannot see the hard discs,
To solve this we first had to determine what Massstoragedrivers section he had to add to his winnt.sif file (same applies to unattended and Ris installs of xp..)
Here's a sample one (note- the sample below is only for precision 470/ 670)
[MassStorageDrivers]
"Adaptec Embedded Serial ATA HostRAID Controller" = "OEM"
"IDE CD-ROM (ATAPI 1.2)/PCI IDE Controller" = "RETAIL"
The first line (in bold) is the line that tells the unattended (ris) install what driver it should be loading from the corresponding TXTSETUP.OEM file,
Below we can see the reference to that in the TXTSETUP.OEM file
[Disks]d1 = "Adaptec Embedded Serial ATA HostRAID Controller", \hraidsk1,.
Ok now that we know the above, let's apply that logic to the Precision Workstation 490,
Looking at the TXTSETUP.OEM file (suplied from support.dell.com here > http://ftp.us.dell.c...ATA/R126479.EXE )
We can see the following sections:-
[Disks]disk1 = "Intel Matrix Storage Manager driver", iaStor.sys, \
[Defaults]
scsi = iaStor_ICH7MDH
;----------- Component Section -----------
[scsi]
iaStor_ESB2 = "Intel® ESB2 SATA RAID Controller (Server ESB2)"
iaAHCI_ESB2 = "Intel® ESB2 SATA AHCI Controller (Server ESB2)"
iaStor_ICH7MDH = "Intel® 82801GHM SATA RAID Controller (Mobile ICH7MR/DH)"
iaStor_ICH7DH = "Intel® 82801GR/GH SATA RAID Controller (Desktop ICH7R/DH)"
iaAHCI_ICH7R = "Intel® 82801GR/GH SATA AHCI Controller (Desktop ICH7R/DH)"
iaAHCI_ICH7M = "Intel® 82801GBM SATA AHCI Controller (Mobile ICH7M)"
iaStor_ICH6R = "Intel® 82801FR SATA RAID Controller (Desktop ICH6R)"
iaAHCI_ICH6R = "Intel® 82801FR SATA AHCI Controller (Desktop ICH6R)"
iaAHCI_ICH6M = "Intel® 82801FBM SATA AHCI Controller (Mobile ICH6M)"
However, adding the following secion to winnt.sif or ris.sif file does NOT work
[MassStorageDrivers] "Intel Matrix Storage Manager driver" = "OEM" "IDE CD-ROM (ATAPI 1.2)/PCI IDE Controller" = "RETAIL"
The above will still generate 'hard disc drive not found' type of error messages, so how exactly DO we determine the correct controller from the 9 listed,
The answer is suprisingly straight forward,
Go into device manager
Once you've opened Device Manager,expand the IDE/AHCI/SATA controller listed
double click on it and choose the details TAB.
Scroll down to hardware IDs section with the drop down menu
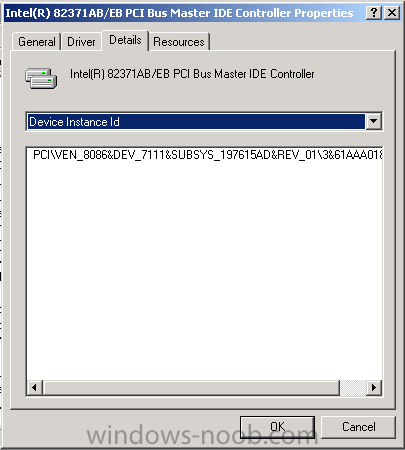
Now here's the important bit…..
Make a note of the PCI\VEN….. Linesand verify if any of them MATCH with the corresponding lines in TXTSETUP.OEM
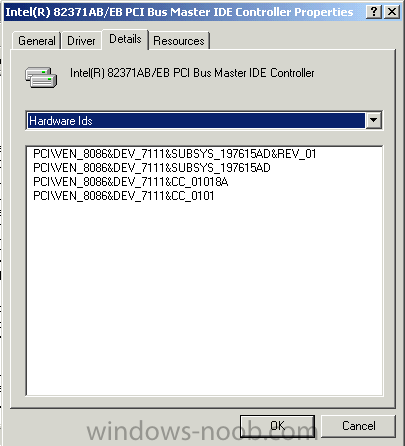
In the case of the Precision Workstation 490 (no screenshots sorry, don't have the hardware) the pci ven/dev ID's matched to the following line in the Hardware.Ids.scsi section of TXTSETUP.OEM
[HardwareIds.scsi.iaAHCI_ESB2]
id = "PCI\VEN_8086&DEV_2681&CC_0106","iaStor"
That line above in turn is tied to the second one in the 'scsi' list of TXTSETUP.OEM
[scsi]
iaStor_ESB2 = "Intel® ESB2 SATA RAID Controller (Server ESB2)"
iaAHCI_ESB2 = "Intel® ESB2 SATA AHCI Controller (Server ESB2)"
iaStor_ICH7MDH = "Intel® 82801GHM SATA RAID Controller (Mobile ICH7MR/DH)"
iaStor_ICH7DH = "Intel® 82801GR/GH SATA RAID Controller (Desktop ICH7R/DH)"
iaAHCI_ICH7R = "Intel® 82801GR/GH SATA AHCI Controller (Desktop ICH7R/DH)"
iaAHCI_ICH7M = "Intel® 82801GBM SATA AHCI Controller (Mobile ICH7M)"
iaStor_ICH6R = "Intel® 82801FR SATA RAID Controller (Desktop ICH6R)"
iaAHCI_ICH6R = "Intel® 82801FR SATA AHCI Controller (Desktop ICH6R)"
iaAHCI_ICH6M = "Intel® 82801FBM SATA AHCI Controller (Mobile ICH6M)"
So armed with this information you can now add the correct values to your [MassStorageDrivers] section of winnt.sif/ris.sif file for precision workstation 490/690
And in case you havn't figured it out yet, here's what it should now look like
[MassStorageDrivers]"Intel® ESB2 SATA AHCI Controller (Server ESB2)"= "OEM"
"IDE CD-ROM (ATAPI 1.2)/PCI IDE Controller" = "RETAIL"
; Use info from the Txtsetup.oem file
[OEMBootFiles]
iaahci.cat
iaahci.inf
iastor.cat
iastor.inf
iastor.sys
license.txt
txtsetup.oem
-
I'm sure some of you have come across this problem (or will..) so I'm going to tell you how to solve it,
Please archive this, you'll need it one day...
Customers scenario:- The customer has a whole load of computers and they want to do RIS (remote installation services) installs on their new computerss and they want to use the OEM provided Windows XP SP2 OEM cd, I normally would NOT recommend this method as it is troublesome and may lead to activation issues amongst other things.
If you use the OEM cd to install computers using RIS, please note that the OEM cd has modified files on it that can cause errors during the RIS process. The first error you may encounter is likely to be something along the lines of
File iastor.sys caused an unexpected error (21) at line 3540 in
d:\xpsprtm\base\boot\setup\setup.c.
The above error is misleading as you might think you actually need this file (and you most likely don't as the drivers you require can be installed properly via the oempnpdrivers path or install.bat).
NOTE: This error can also be seen on workstations, and if so, have a read of this http://www.msfn.org/board/index.php?showtopic=7454
To get around this problem we have to understand where it's coming from.
When risetup is run on the RIS server, a read only file called txtsetup.sif is created at risserver\risdrive\remote install\setup\english\images\<baseinstallname>\I386.
Remove the read only properties from the file then open it in notepad and find the [sCSI Load] section. In this section you will find the driver that is causing the error. Comment out any lines that produce a similiar error when you try to load the system.
DO NOT comment out all the lines in this section, as the system will not be able to find a hard drive after getting past the errors. What happens here is the OEM cd has several references to drivers (for raid/scsi and so on) that you won't find on a Volume License Key cd's txtsetup.sif file.
Have a look at the two samples below, the first part is from a (danish winxpsp2) OEM txtsetup.sif file, the second part is from the VLK cd txtsetup.sif file.
[sCSI.Load]iastor = iastor.sys,4a320raid = a320raid.sys,4
aac = aac.sys,4
cpqarray = cpqarray.sys,4
atapi = atapi.sys,4
aha154x = aha154x.sys,4
sparrow = sparrow.sys,4
symc810 = symc810.sys,4
aic78xx = aic78xx.sys,4
i2omp = i2omp.sys,4
dac960nt = dac960nt.sys,4
ql10wnt = ql10wnt.sys,4
amsint = amsint.sys,4
asc = asc.sys,4
asc3550 = asc3550.sys,4
mraid35x = mraid35x.sys,4
ini910u = ini910u.sys,4
ql1240 = ql1240.sys,4
aic78u2 = aic78u2.sys,4
symc8xx = symc8xx.sys,4
sym_hi = sym_hi.sys,4
sym_u3 = sym_u3.sys,4
asc3350p = asc3350p.sys,4
abp480n5 = abp480n5.sys,4
cd20xrnt = cd20xrnt.sys,4
ultra = ultra.sys,4
adpu160m = adpu160m.sys,4
dpti2o = dpti2o.sys,4
ql1080 = ql1080.sys,4
ql1280 = ql1280.sys,4
ql12160 = ql12160.sys,4
perc2 = perc2.sys,4
hpn = hpn.sys,4
cbidf2k = cbidf2k.sys,4
dac2w2k = dac2w2k.sys,4
aarich = aarich.sys,4
And now here's the same part from the VLK txtsetup.sif file…
[sCSI.Load]cpqarray = cpqarray.sys,4atapi = atapi.sys,4
aha154x = aha154x.sys,4
sparrow = sparrow.sys,4
symc810 = symc810.sys,4
aic78xx = aic78xx.sys,4
i2omp = i2omp.sys,4
dac960nt = dac960nt.sys,4
ql10wnt = ql10wnt.sys,4
amsint = amsint.sys,4
asc = asc.sys,4
asc3550 = asc3550.sys,4
mraid35x = mraid35x.sys,4
ini910u = ini910u.sys,4
ql1240 = ql1240.sys,4
aic78u2 = aic78u2.sys,4
symc8xx = symc8xx.sys,4
sym_hi = sym_hi.sys,4
sym_u3 = sym_u3.sys,4
asc3350p = asc3350p.sys,4
abp480n5 = abp480n5.sys,4
cd20xrnt = cd20xrnt.sys,4
ultra = ultra.sys,4
adpu160m = adpu160m.sys,4
dpti2o = dpti2o.sys,4
ql1080 = ql1080.sys,4
ql1280 = ql1280.sys,4
ql12160 = ql12160.sys,4
perc2 = perc2.sys,4
hpn = hpn.sys,4
cbidf2k = cbidf2k.sys,4
dac2w2k = dac2w2k.sys,4
As you can see from above, there are quite a few differences between the OEM txtsetup.sif file and the one on the VLK cd. So the first step in resolving your customer's 'iastor.sys errors' is to very simply copy/paste the VLK section directly into their original OEM txtsetup.sif file's [scsi.load] section (marked in RED above) replacing the OEM references with the original VLK references (which leaves out the OEM iles which cause the issues in the first place).
Once this is done, you can restart the RIS service and attempt another RIS install. Things will look much better but then half way through the RIS install there will be several references to files 'not found… press ESC to ignore' , the files that are 'missing' are likely to be any of the files below (or more)
To resolve those issues we need to edit the TXTSETUP.SIF file some more. We need to locate another section in the TXTSETUP.SIF file called '[sourceDisksFiles]'.Megasas.pdbMegasas.sys
Nodev.inf
Oemsetup.inf
Delpseud.inf
Mpixp32.cat
Symmpi.inf
Symmpi.sys
Symmpi.tag
Symmpi.pdb
Idecoi.dll
NavAtaBus.sys
Nvrais.sys
Nvraidco.dll
Nvraid.inf
Nvraid.cat
Iastor.sys
Iastor.inf
Iastor.cat
Iaahci.cat
Iaahci.inf
A320RAID.SYS
A320RAID.INF
A320RAID.CAT
A320MGT.INF
A320MGT.CAT
Cercsr6.sys
Cercsr6.inf
Cercsr6.cat
Cercmgt.inf
Cerccin.dll
Afamgt.sys
Aichmgt.inf
Aichmgt.cat
Aarich.sys
Aarich.inf
Aarich.cat
Aacmgt.inf
Aacevt.exe
Aaccin.dll
Aac.sys
Aac.inf
Aac.cat
!Dell_XP.cab
!DPCHFEN.CAB
NOTE: you will find SEVERAL references to [sourceDisksFiles] in the TXTSETUP.SIF file, but only ONE of them is the one we need to edit, the one we need to edit will have the following line in it
bootvid.dll = 1,,,,,,3_,2,0,0,,1,2
So once you've located the right one do as follows:-
delete everything between [sourceDisksFiles] and bootvid.dll = 1,,,,,,3_,2,0,0,,1,2
so it now starts to look like...
[sourceDisksFiles]bootvid.dll = 1,,,,,,3_,2,0,0,,1,2
kdcom.dll = 1,,,,,,3_,2,0,0,,1,2
c_1252.nls = 1,,,,,,3_,2,0,0,,1,2
c_437.nls = 1,,,,,,3_,2,0,0,,1,2
l_intl.nls = 1,,,,,,3_,2,0,0,,1,2...........
(the file list continues on and on and on, only delete the lines BETWEEN '[sourceDisksFiles] and bootvid.dll = 1,,,,,,3_,2,0,0,,1,2
Ok, now that you have completed editing the TXTSETUP.SIF file, save it, and restart the RIS service, then complete another PXE boot to the RIS server and enjoy the fact that it's working now !!
For your reference I'm including a copy of the VLK TXTSETUP.SIF file and the Danish TXTSETUP.SIF file (there will be minor differences between the languages but the scenario will always be the same, to fix an OEM ris install, you must edit the TXTSETUP.SIF file.
-
Hi,
In case you come across this one ...
Problem:-
Customer is using a windows 2003 server (probably Windows Server 2003 R2 Standard Edition) and attempts to do a RIPREP install on their newly acquired computers.
The first phase of the RIPREP install (ie: getting riprep to run on the computer and copy the contents over to the server) works fine, nothing to report.
However, when the customer then boots the computer via PXE to test RIPREPing the image back they get the following cryptic error message:
Unable to display the operating system (OS) choices.
You may not have sufficient network permissions to view the OS choices on the server, or the server might not contain any OS images.
For assistance, contact your network administrator.
Workaround:-
Verify if the customers Group Policy settings for end users on the active directory are set to the following settings:- (On the server select start/programs/administrative tools/group policy management or the GPMC snap in in MMC.)
If they appear as above (and by default they do if you are using active directory on your domains….) then get the customer to set them as followsUser Configuration (Enabled)Windows Settings
Remote Installation Services
Client Installation Wizard options
Policy Setting
Automatic Setup Disabled
Custom Setup Disabled
Restart Setup Disabled
Tools Enabled
User Configuration (Enabled)Windows Settings
Remote Installation Services
Client Installation Wizard options
Policy Setting
Automatic Setup Enabled
Custom Setup Enabled
Restart Setup Enabled
Tools Enabled
Restart the RIS service and the customer should be able to see the OS coices (sif files) stored on their server, please note that if they have only RIPREP'd one machine that the menu will auto RIPREP the machine without displaying the os list, you need at least 2 or more SIF files in order for RIS to list the 'choices'.
If the customers Group policy settings are not being used then try editing the SIF file directly and rem out the HalName=halmacpi.dll entry and it will become visible...or enter the correct one.
here's a list of HAL's you could experiement with
HAL descriptive name
HaLname=halmacpi.dll
HaLname=halaacpi.dll
HaLname=halacpi.dll
HaLname=halsp.dll
HaLname=halapic.dll
HaLname=halmps.dll
HaLname=hal.dll
HaLname=halborg.dll
-
http://blogs.msdn.com/ts/archive/2006/11/2...y-released.aspx
To install the new version, go to Windows Update on the target computer and look for optional software updates, or download it from the Microsoft Download Center.Remote Desktop Connection (Terminal Services Client 6.0) for Windows Server 2003 (KB925876)
http://www.microsoft.com/downloads/details...2C-D71ADC98ADB1
Remote Desktop Connection (Terminal Services Client 6.0) for Windows Server 2003 x64 Edition (KB925876)
http://www.microsoft.com/downloads/details...DC-F97F5A1B4493
Remote Desktop Connection (Terminal Services Client 6.0) for Windows XP (KB925876)
http://www.microsoft.com/downloads/details...CF-D4F18C8F5DF9
Remote Desktop Connection (Terminal Services Client 6.0) for Windows XP x64 Edition (KB925876)
http://www.microsoft.com/downloads/details...35-E2ABBC55D8E8
Localized versions and the Multi-User Interface Pack will be released in the coming months.
cheers
anyweb
-
if you try to edit your hosts file (for example to add a local ip address as your webserver) manually in Vista you;ll be denied from doing so by the file security laid down in Vista.
To fix it, you'll need to change the user 'users' file permissions to 'modify' on the hosts file.
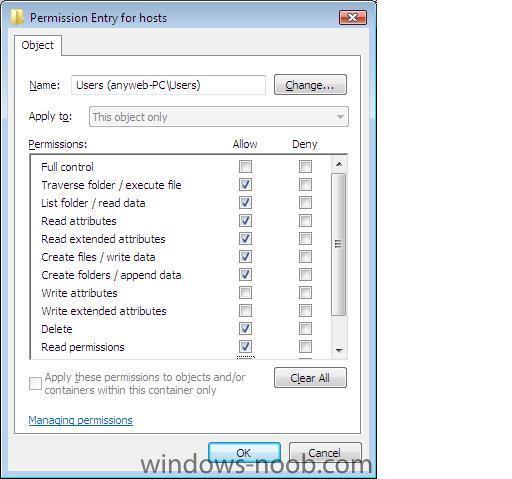
To do this right click on the file, choose properties, security, advanced, then click on 'Edit'
Accept (continue) the UAC warning dialog, and click and highlight the 'users' username. click 'edit' and make sure to select all of the following attributes
Traverse Folder/Execute FileList Folder/Read Data
Read Attributes
Read Extended Attributes
Create Files/Write Data
Create Folders/Append Data
Write Attributes
Write Extended Attributes
Delete
Read Permissions
Synchronize
once those are selected and you apply your changes you can indeed 'finally' save the hosts file changes...
-
-
here's all the info I have
Windows Vista RTM Announcement - 11AM PST Today - Vista - RTM = 6000.16386.061101-2205
cheers
anyweb
-
At a press conference in San Francisco, Microsoft CEO Steve Ballmer is expected to announce a new partnership between Microsoft and Novell. The unprecedented deal will have Microsoft offering a degree of sales support for Novell's SUSE Linux while both companies work towards better interoperability between their respective operating systems. As part of the agreement, Microsoft also promises not to wield its patent portfolio against SUSE Linux. More here. You can follow the live webcast announcement, by Steve Ballmer, here. Update: Novell has put up a detailed FAQ about this deal.
-
Responding to the myriad complaints over ambiguities and outright uncool (that's a technical term) licensing terms, Microsoft has revised the Vista retail license to remove some of the most major causes of complaint. A previous version of the Windows Vista retail license restricted the number of times you may transfer Vista from one device to another. The license read: "The first user of the software may reassign the license to another device one time. If you reassign the license, that other device becomes the 'licensed device'." The new license has removed this language relating to device transfers.
cheers
anyweb
-
-
-
-
ok, At this stage Internet Explorer 7 in Vista 5728 is looking a mess, over half the screen's real estate is taken up with toolbars, but I want to take this further and try installing some more toolbars. In addition to looking ridiculous, opening TABs no longer works and IE crashes with ease.
Once I've subjected it to some more toolbars, I will then attempt to 'reset' IE to it's default settings to see can it remove most of the junk I stuck onto it.
Next up on my list of toolbars is one called toolbarbrowser.
I clicked on the download link and chose 'run' I got the usual Internet Explorer Security warning, followed by accepting it. Next up, UAC asked my permission to 'allow' the installation. I accepted.
As a result, IE7 now looks like this
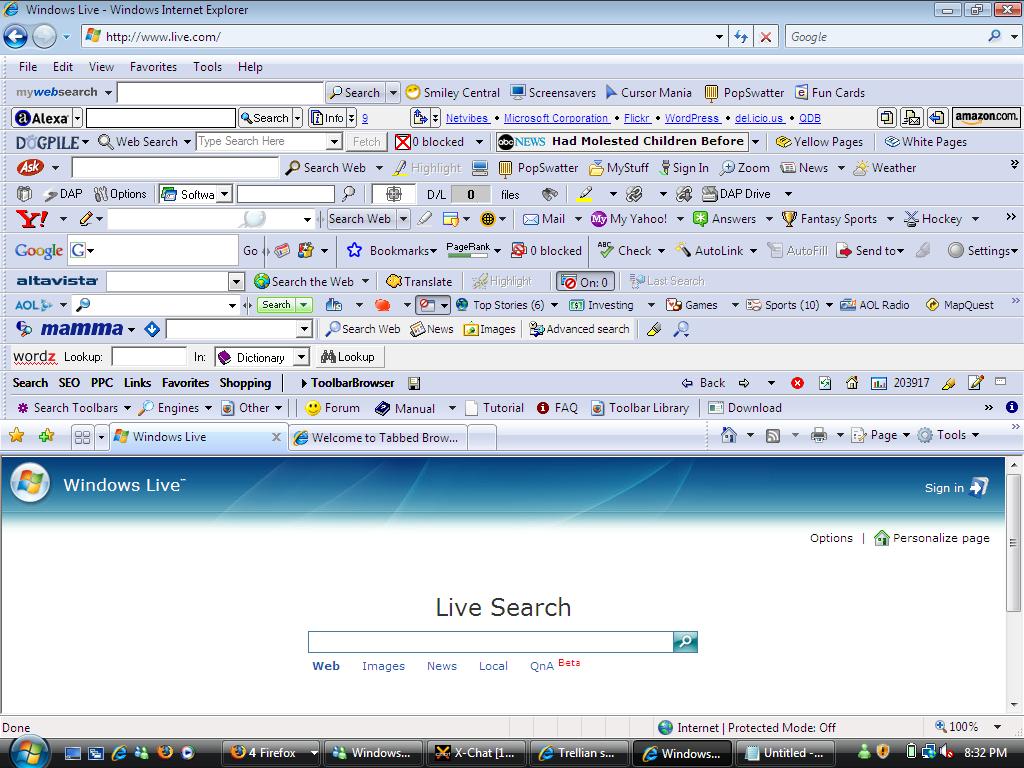
Groovy !
Time for yet another toolbar, this time one that'll help you get a job. Without restarting IE, so that i'm not bugged by UAC, i click on the download link. I install the activeX plugin when prompted then install the software after accepting yet another license agreement.
At this point IE becomes unusable with 17 popup windows saying 'error' and i have to kill the tasks in task manager.
On with the show, time for another toolbar. This time its one called goodsearch toolbar.
It installed painlessly and I didn't notice any warnings about security. Looking closely I could see Internet Explorer protected mode was off, but I restarted IE after killing all it's processes so that was odd. No UAC at all this time.
I can still see some real estate in IE so I decide to torture it some more and go in search of yet another toolbar. After some googling I find one called 'http://www.spiderpilot.com/toolbar/' so i go ahead and attempt to install it. I click on the download link and choose 'run'. Strangely enough UAC now prompts me to give the file permission to install, I allow it. It installs fine.
I'm not done yet ! so I install a few more toolbars namely:-
At this point I couldn't seem to add any more toolbars, so I called it a day,
here's what IE looks like now after my toolbar mayhem.
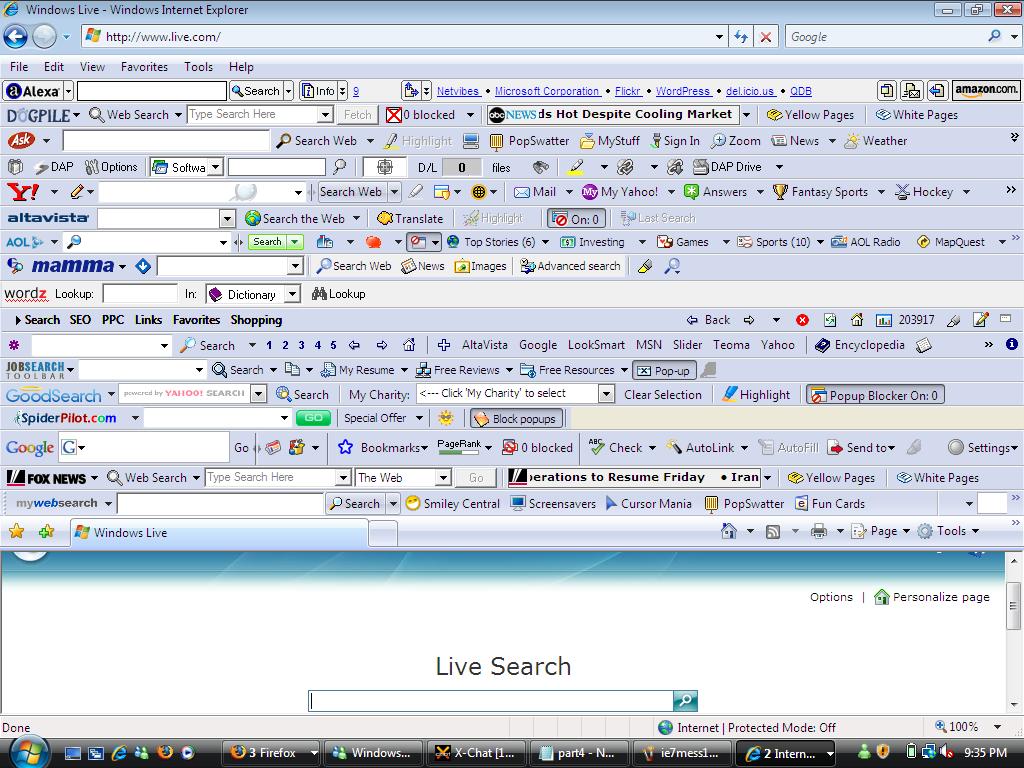
Mission accomplished I think !
Lastly, I decide to test if Internet Explorer can reset itself, so I click on tools, internet options, Advanced, and click on Reset.
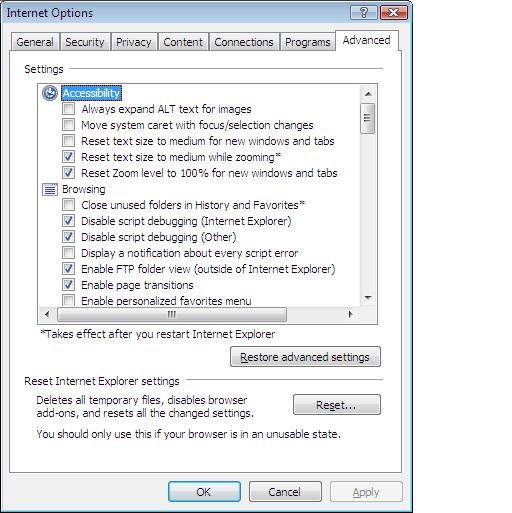
I had to close messenger live to continue, so I did, and tried again.
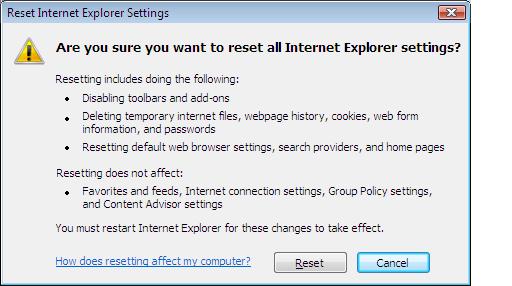
And considering what I put Internet Explorer 7 through, the reset tool did a very very very good job, see below.
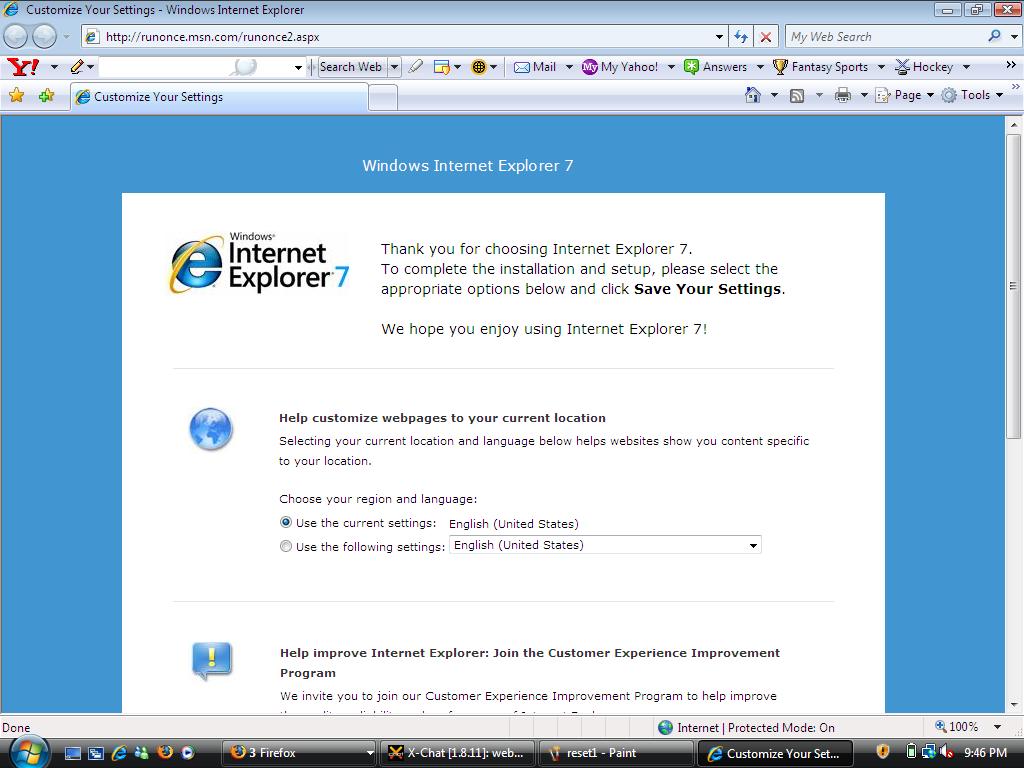
Update:-
The yahoo toolbar was sucessfully removed via add/remove programs in Control Panel, in addition, even though the RESET worked very well in IE, all of those toolbar programs were still listed as installed in add/remove programs in Control Panel.
Cheers
anyweb.
-
In Part 1 and part 2 of this article, I have subjected IE in Vista 5728 to an assault of 'toolbars' and it has coped quite well. In some cases refusing to install them and in every case warning the end user of what is happening.
However one thing bothers me and that's what happens after UAC prompts you to install some software,
If you allow it then IE remains with 'protected mode OFF' until you restart it. I hope this is fixed in later versions of IE7.
I'm now going to continue attempting to install toolbars in IE7 to see how it copes and also to see if I can reproduce the following infamous screenshot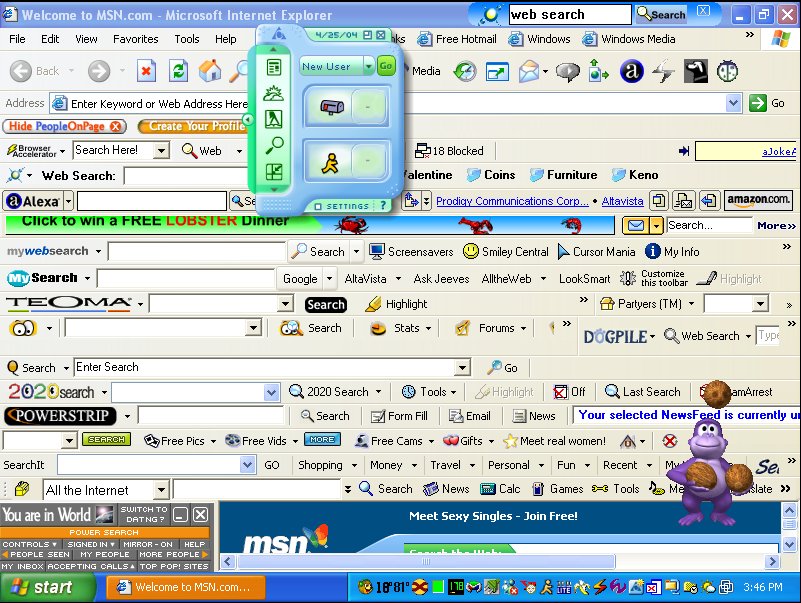
Next on my list is a toolbar that many use, Yahoo's own toolbar. After accepting to click on the 'ActiveX control' warning bar at the top of IE, I was then prompted (as usual) to review my decision to run the software via the UAC prompt, I chose 'continue.
After accepting that, I'm shown another Internet explorer security warning (below) to which I chose 'install'. I want more toolbars !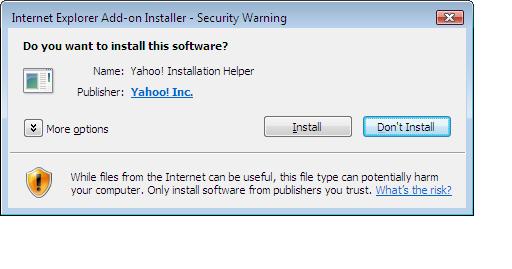
Next up I was prompted with yet another security warning, and once again UAC popped up (which I wasn't expecting considering my point above...).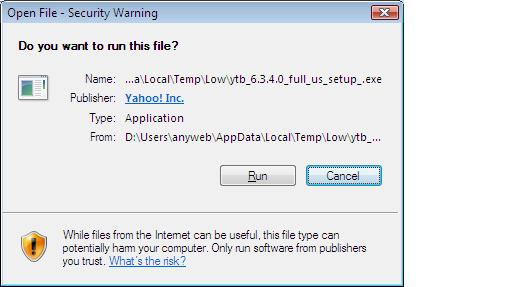
Well after accepting the EULA I was now installing the yahoo toolbar along with Norton spyware whether I wanted it or not.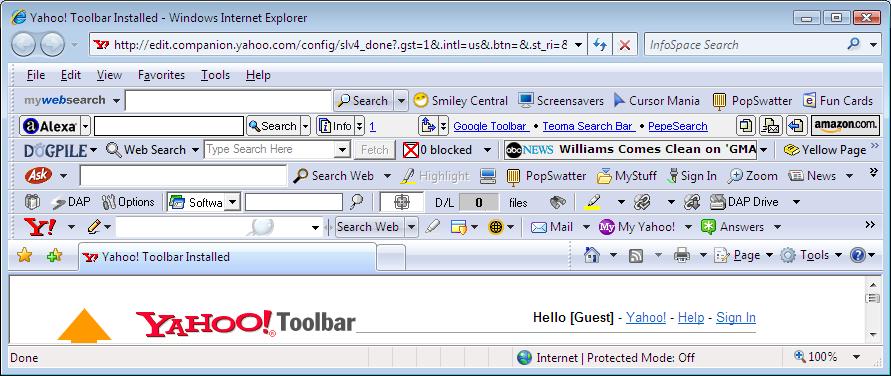
As we can now see, the toolbar installed just fine, and next I'm now going to try and install another toolbar without restarting IE to test my 'protected mode off' concerns.
What would IE be without a google toolbar, so off I go to install it.
I clicked on the 'download google toolbar' link and was prompted with a 'file download security warning' to 'run' 'save' or 'cancel'.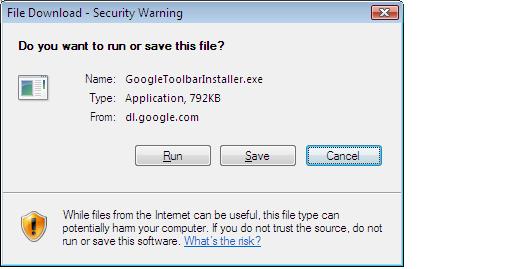
Obviously I clicked 'run'.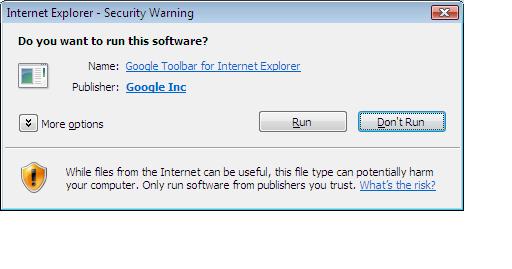
Yet again I chose 'run' but this time I saw NO UAC SECURITY PROMPTS AT ALL.
After agreeing to google's 'yada yada' EULA, it completed it's installation.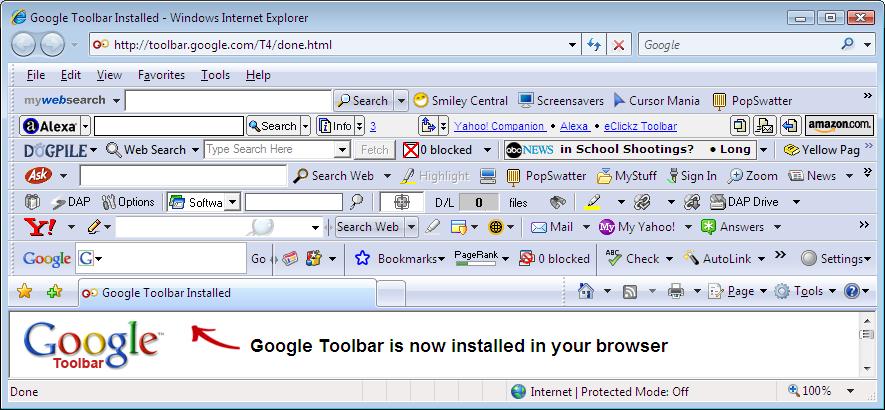
No errors, totally painless, no UAC prompt whatsoever.
Ok, on with the next toolbar, Groowe toolbar.
As before, I will not restart IE as I want to see if UAC comes back or not. After clicking on the download link i was brought to another site and then Internet Explorer crashed (or rather, restarted itself), which is ok as by this time it was unstable (right clicking on a link and choosing open in new tab did nothing).
I tried again, same thing. So I closed IE completely as it was obviously confused. After restarting IE, I got an Internext Explorer Security warning about 'norton'.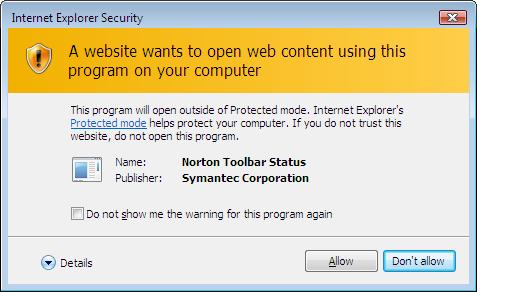
I chose to 'allow' to both prompts (it asked again). After doing this I successfully downloaded the Groowe toolbar by accepting the 'popup warning' from Internet Explorer to allow me to download the file.
I now had the file on my desktop and I have to manually run it, so i did. Up pops the usual security warning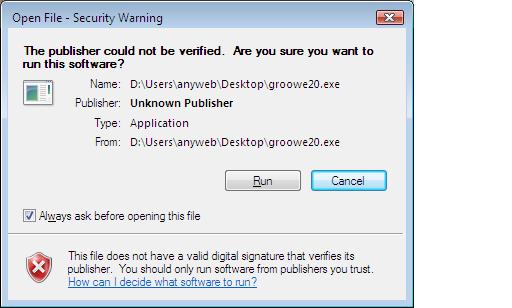
followed by UAC asking me to 'allow' it or not. (remember IE was restarted before this...). I clicked allow.
Funnily enough, Groowe ended up installing it's toolbar in Firefox which wasn't what I had hoped for, but what the heck, on with the show.
I decide to continue with my mission to try and install as many toolbars as I can, so I get busy with the following:-
Altavista toolbar .
Aol Toolbar.
Wordz Toolbar.
The above websites were found after a quick google with one of my new toolbars (can't remember which one ;-))
Checkout how IE7 looks now in Vista.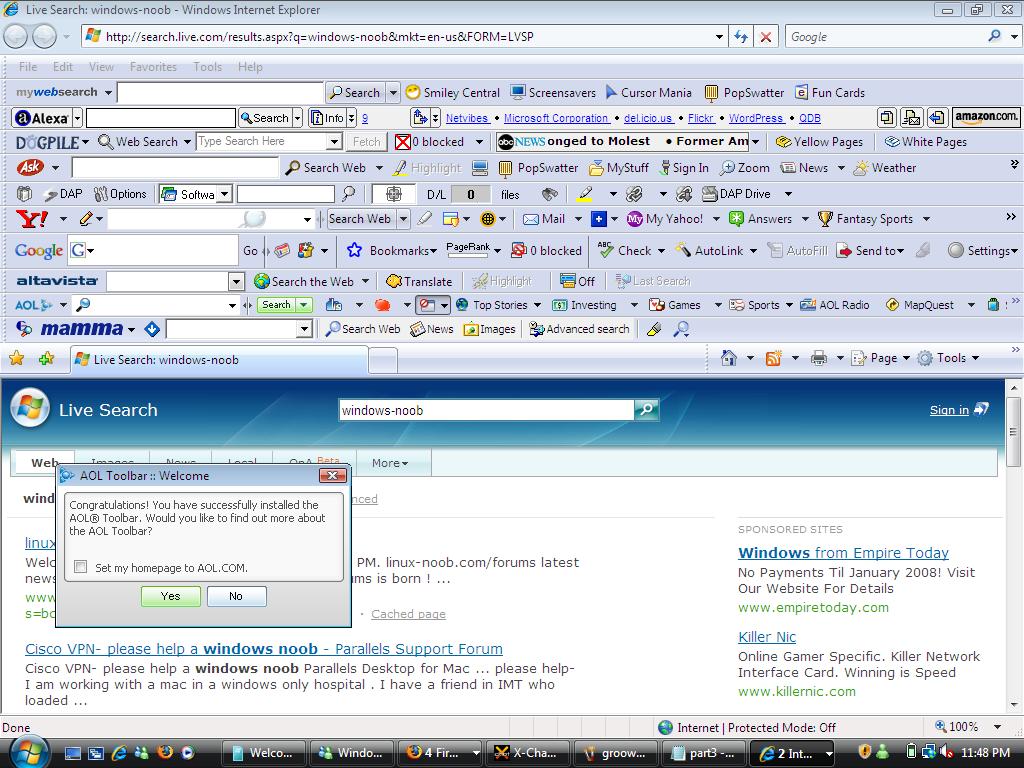
part 1 - smileys anyone ?
part 2 - a handful of toolbars
part 3 - more toolbars !!
part 4 - more toolbars plus can we reset Internet Explorer ? -
As we saw in Part I IE7 did quite a good job of stopping software from installing, forcing me to manually install the application.
Next up we'll install some more toolbars !
First on the list, Alexa toolbar
I started up IE7, and headed over to Alexa's website, and chose to download the toolbar that they are offering. Interestingly it's 'supported' on IE6 and Firefox, so I thought this should be interesting with IE7.
I clicked on the 'Install Toolbar' icon on the webpage, that opened up a window which prompted me to 'run' the downloadable EXE file. So I chose 'run'.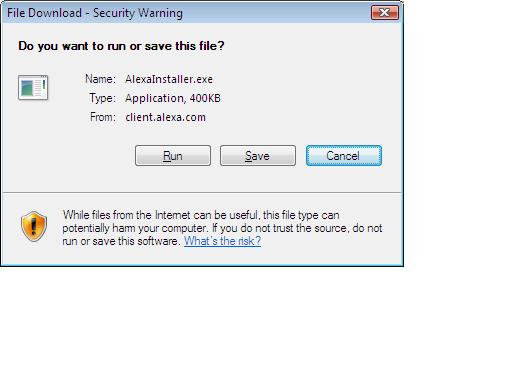
This prompts Internet Explorer to give you a Security Warning
so as usual, I chose 'run'. This in turn pops up a window which you can't miss, User Account Control (UAC) which asks do you really want to allow this executable file to install.
I chose to continue, and the Alexa Toolbar installer program appears. I chose next, accept the EULA for Alexa toolbar, and continue with its default installation options. When the installation is complete, Alexa restarts IE, and I here a 'bleep' to signify that something stopped a popup, but what ? I check if 'mywebsearch' did the business but no, it didn't (or at least it's not listed in 'my recently swatted popups') and in addition, the yellow popup bar on the top of IE's window does not appear. So I'm none the wiser, It looks like Alexa's toolbar has failed to install but I can't be sure. IE opens one of Alexa's webpages but nowhere do I see any sign of my new Alexa toolbar. Where is it ? The only evidence I see that I tried to install it is if i right click on the toolbar area in IE, and it's listed there, but no physical signs of it otherwise. Oh well...
Once done looking for Alexa, the alexa installer very nicely brought me to one of their antispyware webpages. While there, I was still looking for the Alexa toolbar so I clicked on 'unlock toolbars' and found the missing Yellow Information Bar which beeped at me earlier.
It informed me that it wanted this website to install the following add-on, 'AlxTB Module'. Well I was curious so of course I clicked to install it.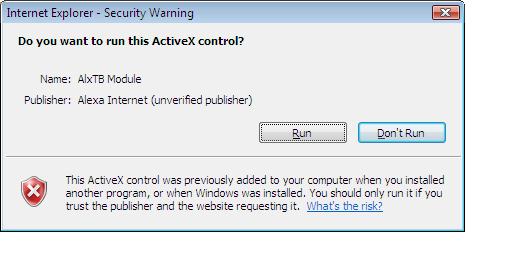
Once I chose to 'Run ActiveX control' Internet Explorer finally had the alexa toolbar. Woohoo !.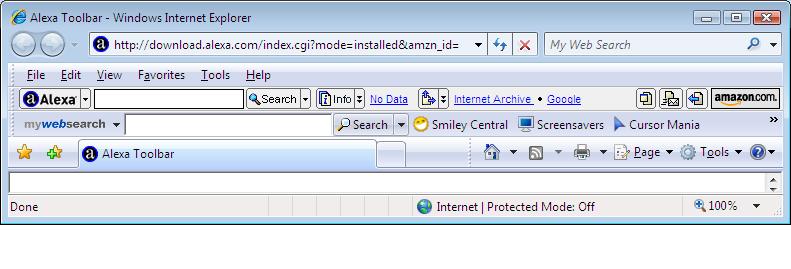
So after jumping through a few hoops, IE7 is starting to look like IE6 in the original screenshot in Part 1 of this article, but I must stress that so far, IE7 is making it DIFFICULT for these additional apps to install themselves at all.
On with the show !
Next I headed over to dogpiles website to install their toolbar.
I clicked on the 'Install the Dogpile Toolbar' button and got the IE7 ActiveX warning line at the top of my browser, I chose to install the ActiveX control.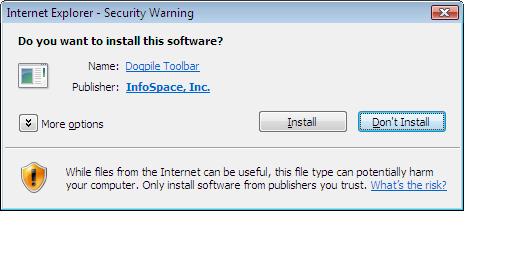
Yup, by now I am getting used to the routing, so I clicked on 'Install' to install the dogpile goodies. After accepting yet another license agreement i was prompted to enter some personal info (date of birth etc) in order to get some targetted assistance while browsing (or something like that).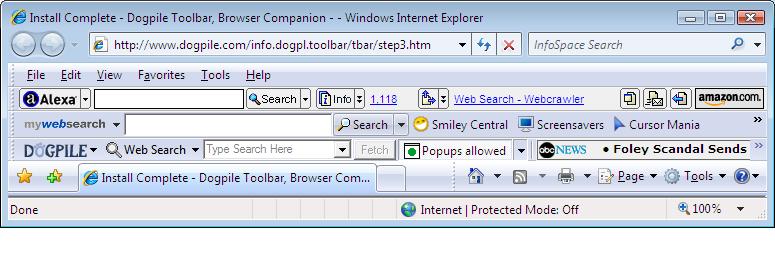
After dogpile is done installing, it opens up a new Internet Explorer window for you, and comes complete with its new toolbar. All in all, dogpile was the easiest of the toolbars to install so far, but the reason for that is because Internet Protected mode in IE7 was OFF. It seems that once you knock this mode off by accepting some UAC program dialogue, it remains off until you completely restart the browser.
So that's what I did next, I restarted IE7 completely. Now after the restart, Internet Protected mode is ON again but my Alexa toolbar looks 'blank'.
Next on the list of my toolbars, was (in no particular order) was Ask's toolbar (formally Teoma from what I can make out). I downloaded and installed it and was prompted with the UAC prompt once again, and once again I accepted the risk.
The only difference this time, is that the Ask Toolbar told me that IE7 wasnt supported (will not work correctly) and that I could run the addon anyway or disable it. I chose to run it anyway.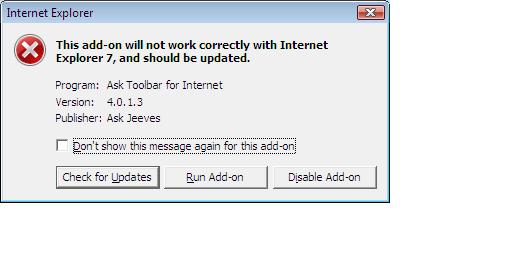
Now IE7 is starting to look more interesting, I've got 4 new toolbars installed !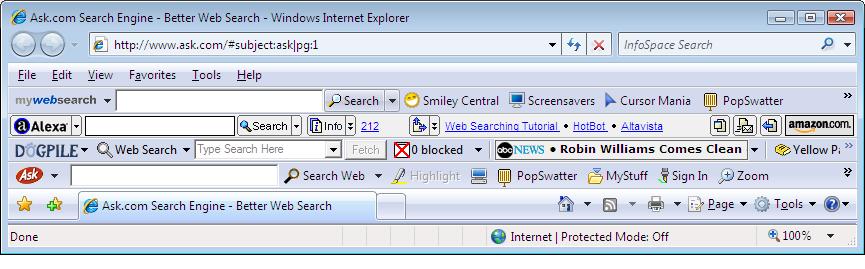
Note that in the screenshot above, that 'Internet Protected Mode' is OFF (as I mentioned above). This seems to be a bug in IE7 from what I can see, as once you accept ONE UAC prompt in IE7 is disables the protection for subsequent browsing until you completely restart IE7. This make it easy for malware to install itself without alerting you (too much) that it is doing so.
Next up on my list is Download-Accelerator-Plus.
So I restarted IE7 (closed all windows, then start IE7 again) to set it back into Protected Mode, then clicked on the download link, as usual an UAC prompt appears asking for permission to install the software. I chose yes. After going through the installtion routing, the only thing i had to manually add was to tell the program that I wanted the toolbar added to IE, by default, the option wasnt selected.
After yet more configuration screens with DAP reminiscent of Realplayers installation routines in times gone past, I was hoping to see a new toolbar in IE7, but instead, I got an error message stating that DAP has stopped working....
However, some quick thinking on my part, and a restart of IE7 plus right clicking in the browser toolbar area and selecting the DAP bar, all seemed ok and I now have a new toolbar !
Checkout IE7 now !!! (sadly the Alexa toolbar doesnt seem to display properly when Protected mode is enabled).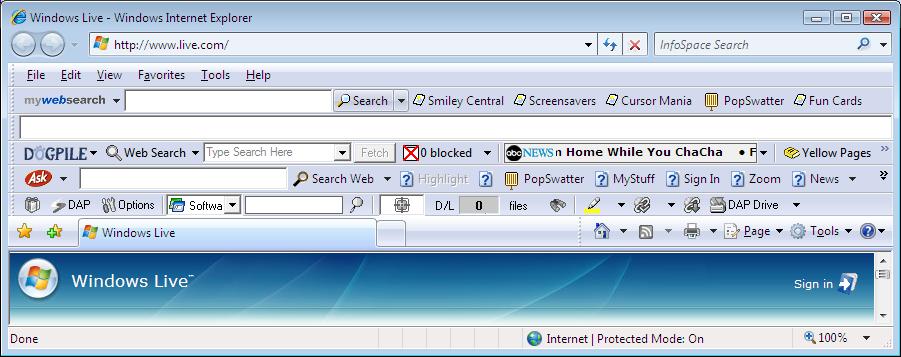
The last toolbar for this part of the article, is the Searchit Toolbar, so I did the usual (restart IE7 to re-enable Protected Mode) and clicked on the download link. Funnily enough, the DAP program installed above, now prompts me with an Internet Explorer Security warning text box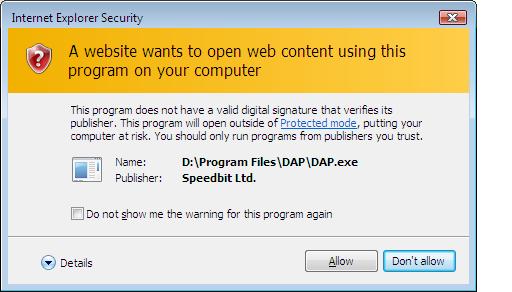
I chose to allow the program to download the software. Unfortunately it seems that DAP and IE7 are not too compatible so i had to manually download the ZIP file for searchit by using Firefox as DAP has confused IE7 a bit.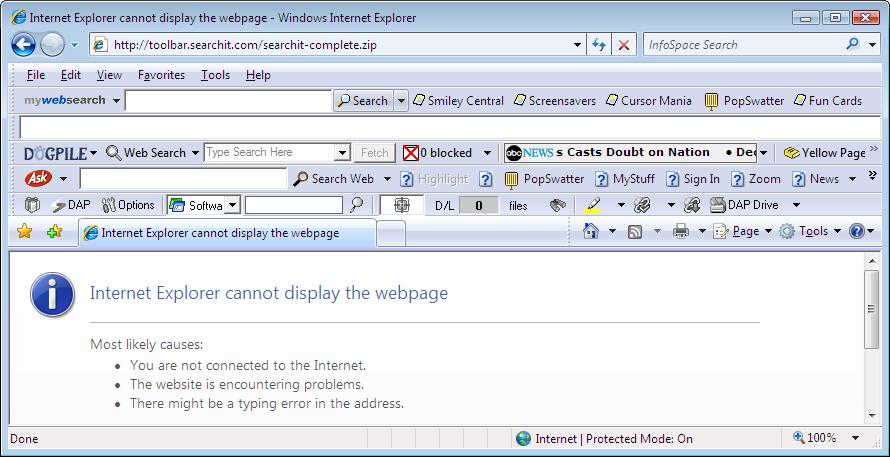
Ok, now that I had the 'windows installer package' for Searchit, I ran it and proceeded with the installation.
UAC popped up asking my permission to install the MSI, I chose 'Allow', however once done, i can find no evidence of the toolbar whatsoever in IE7. I noticed a searchit icon on the desktop, and clicked it, and got an JAva Virtual machine error, I guess that is why the searchit toolbar doesnt work at all in IE7.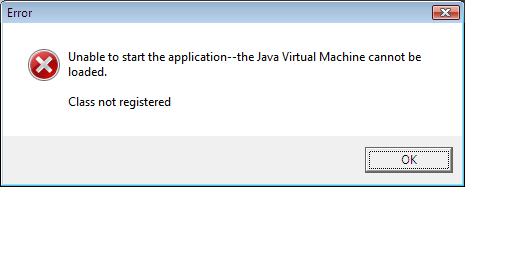
part 1 - smileys anyone ?
part 2 - a handful of toolbars
part 3 - more toolbars !!
part 4 - more toolbars plus can we reset Internet Explorer ? -
This test assumes that the user clicks 'yes/apply/accept/next' to just about anything, so security or not, how will IE7 cope ?
The test was carried out on a full install of Windows Vista Ultimate Edition version 5728 (Aero not enabled) with IE7 as shipped. I used the default user that Vista prompted me to create at the end of the install which according to Users/Groups, is a member of Administrators.
Unless otherwise mentioned, all of the software 'installed' for this test is not considered to be spyware (according to the manufacturers of said software), I'll leave you to make up your mind about that.
Part 1 - Smiley's anyone ?
After looking at this picture from some poor noob's pwn3d Windows XP desktop, I wanted to see if IE7 in Vista 5728 could hold it's own. So I set about testing it !
first of all here's how IE7 looks before I started the test. Pretty standard. Nothing much to write home about.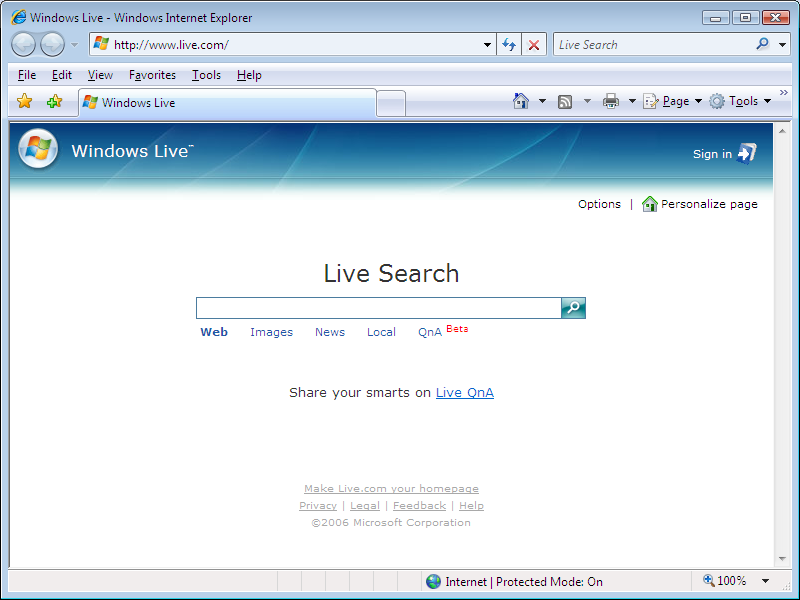
ok now lets head over to a welllovedhated site called smileycentral (why anyone WOULD go there voluntarily is still beyond me...).
IE7 prompted me to install Adobe Flash Player 9 as you see in this screenshot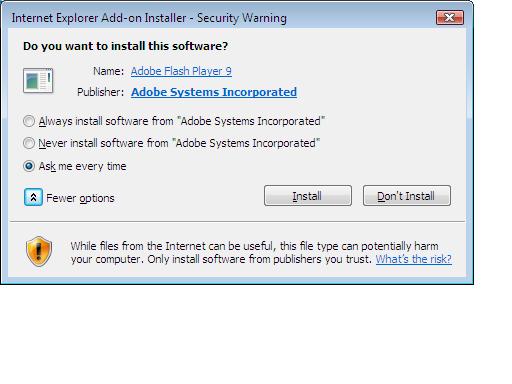
so I clicked on 'install' and IE7 now renders the smiley site correctly (so i believe, trust me when I say this was the FIRST and LAST time I went to that site) and still no smiley things stuck to my IE7 yet.
I decide it's time to start installing some stuff.
I click on 'download now' and I'm prompted to install an Active X script via a yellow WARNING bar at the top of IE7. Good. IE7 is trying to protect me.
Next I click on that warning bar and choose 'install Active X script', then I am prompted twice to accept some new software, the first time the details of which are listed as some cryptic {Bd......} registry class looking key, the second time it mentions 'Ask Jeeves' So I click 'install' of course !.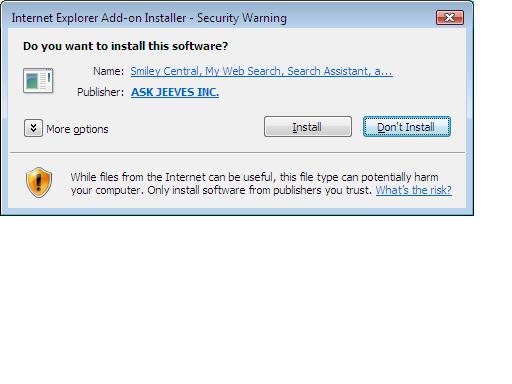
Once done, another big box appears 'Internet Explorer Security'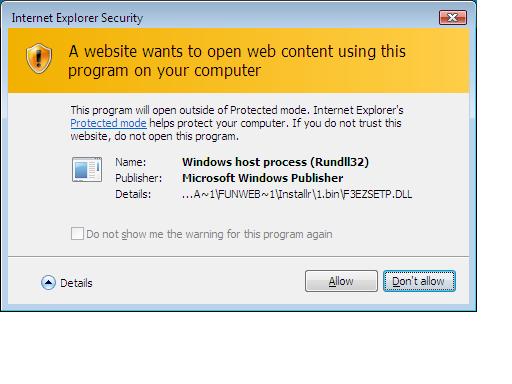
This one is interesting as it notes that the spyware, er program, will open OUTSIDE OF PROTECTED MODE.
Ok, I click 'Allow'.
Amazingly enough, IE7 or vista, or something seems to have caused the smileycentral program to FAIL TO INSTALL. But All is not lost, as it wants us to try a 'manual install' instead.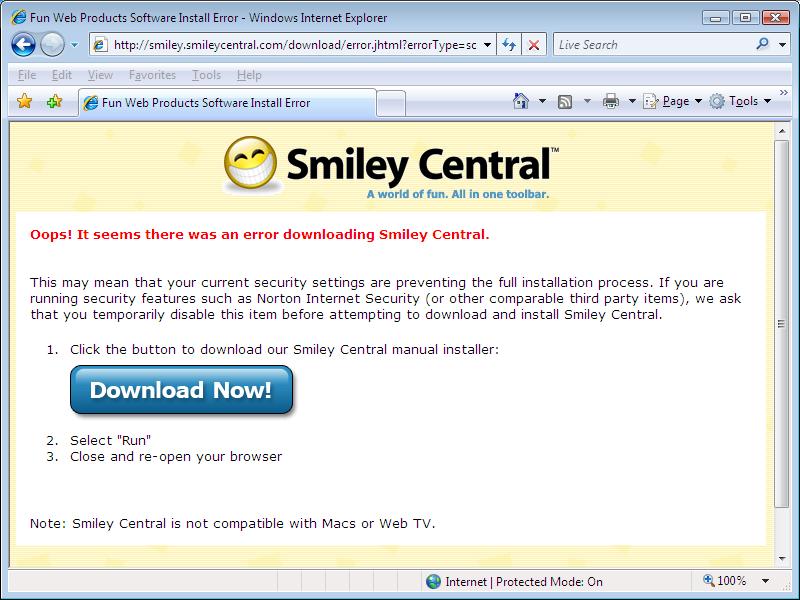
After clicking on the manual install download link, i chose 'run' to install it. Vistas User Account Control popped up asking me did I want to allow the program to 'run', I clicked 'continue'.
I clicked 'accept' to the smiley EULA, and 'Finish'.
Ok, now I'm getting somewhere ! IE7 is now starting to look more 'used'.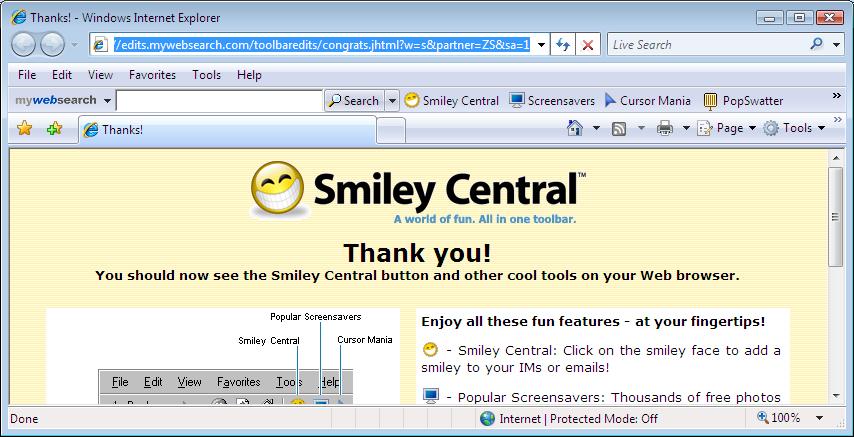
Next I type in http://www.live.com (IE7's default page) to see whats new. I can now see that IE7 displays the page fine but at the bottom right hand corner in IE, it says 'Internet Protected Mode OFF' whereas in the first screenshot in this post, on the very same website, it was ON.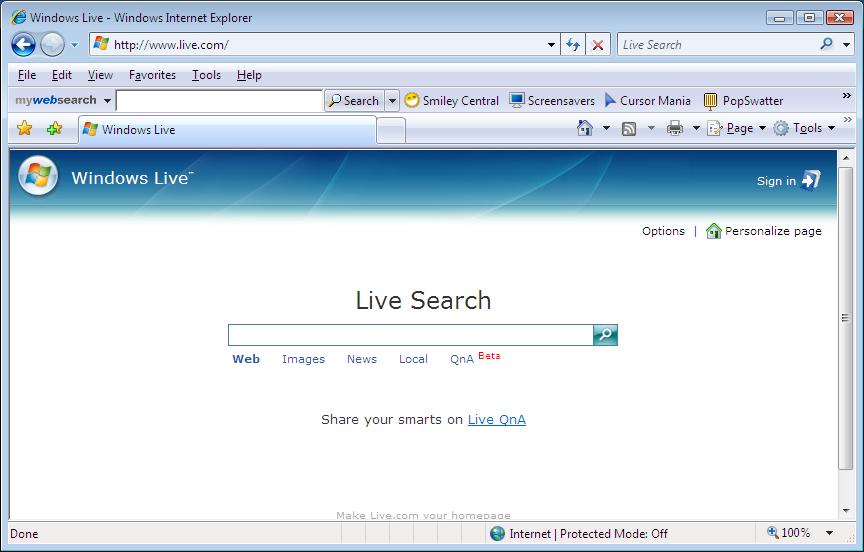
Hmm, ok time for the next stage, I opened up windows Task Manager to see if things look interesting, and sure enough, our smileycentral fiends have added a new process to my list - gee thanks.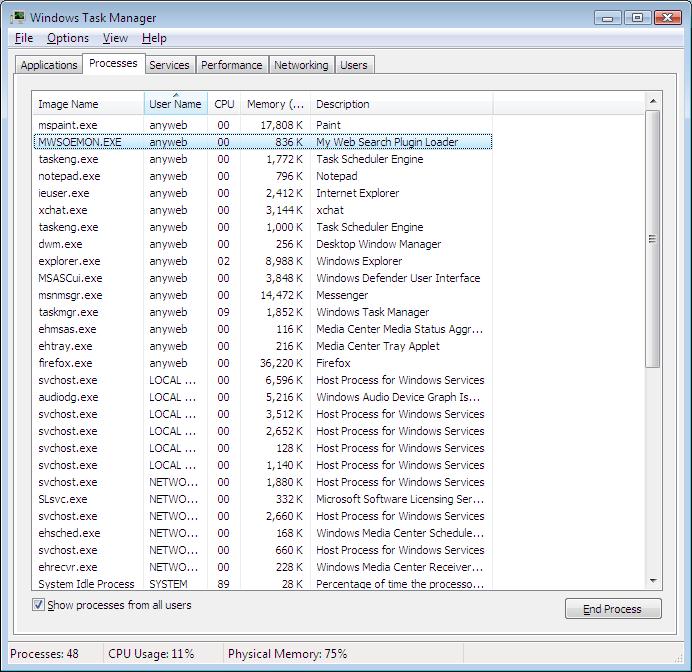
In addition to loading a new process, they have very kindly placed some registry entries on my computer, one of which is pictured below.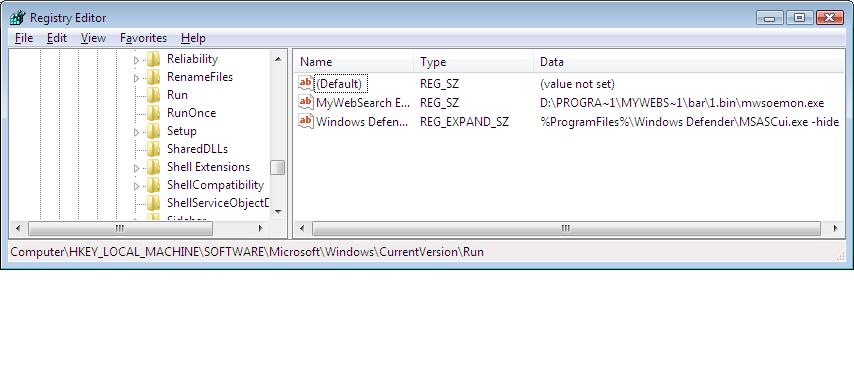
Next up I closed IE7 and restarted it, this time http://www.live.com came up in protected mode, instead of smiley's search site. Interesting !.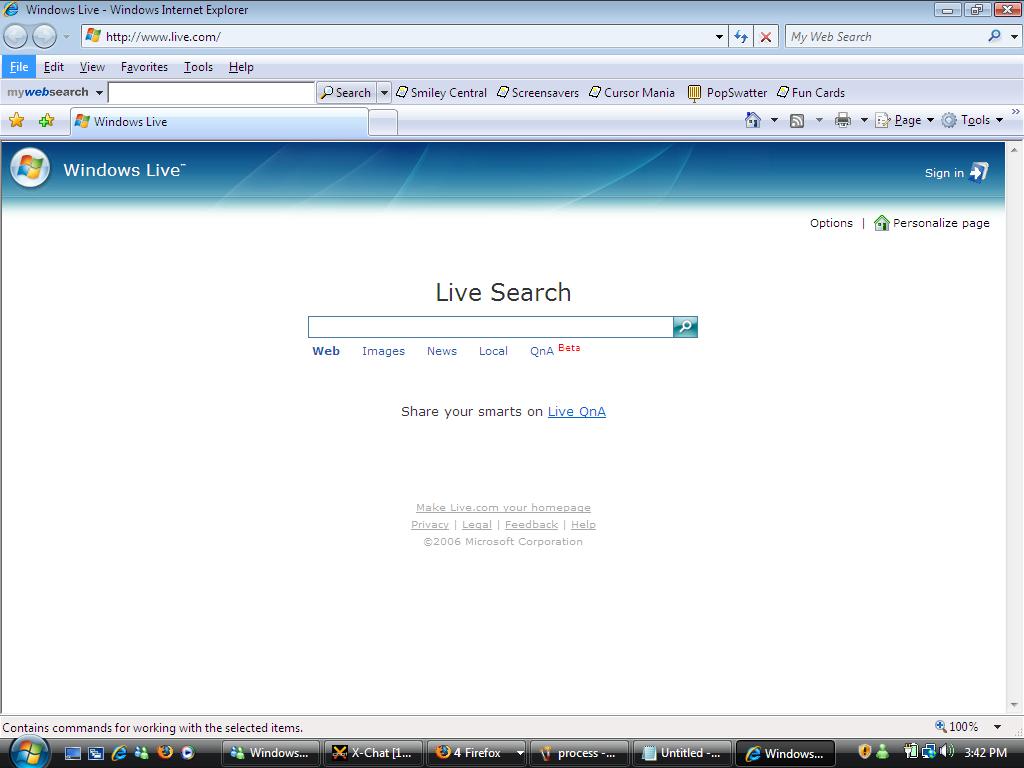
Part 2 - http://www.windows-noob.com/forums/index.php?showtopic=9 -
the original article was written for Windows XP Professional but many of the points raised apply also to Windows 2000 Pro/Server and Windows 2003 server if you plan on using IIS.
Checklist for Securing a Windows XP IIS 5.1 Webserverby Greg Thatcher, MCSE, CCNA and Niall Brady, CNA.
This document was inspired by the need for Windows XP Professional IIS 5.1 administrators to have a checklist available for them which clearly explains how to secure their Web Server from the many Worms and script kiddies who will inevitably target them. Windows XP Professional includes IIS 5.1, it is not installed by default, you have to physically install it as an optiontal extra. By default, XP will install several folders, help files, ASP files, remote web support and more. If you are reading this document and already have a running XP Pro IIS Webserver then you should consider backing it up first. XP includes a backup feature for IIS and it is explained below. If however, you are just installing IIS for the first time, read this first, then go ahead and install everything (we're going to remove or disable most of it anyway).
Before implementing any of these changes on your XP machine, it is strongly recommended that you backup your system (including the "System State") and also backup IIS. Click here for examples of how to do this.
* 1.) Verify that Automatic Updates are set to install automatically. This utility is built into Windows XP and keeps you notified of Critical Updates and Service Packs. Most hacker attacks target machines that DO NOT have the latest Service Packs and Hotfixes installed on them. To see how to set this up click here. Alternatively you can manually update your system by going to Microsoft at http://windowsupdate.microsoft.com
* 2.) Disable and Audit the following files: ftp.exe, tftp.exe, command.com, cmd.exe, telnet.exe, wscript.exe, and cscript.exe. Regardless of the mechanism a hacker uses to break into your machine, the goal is the same: to execute the hacker's code on your machine. The above mentioned programs can be used by hackers to install hacker software, and also run code of the hackers choice.
By disabling and auditing a file, you prevent the hacker from doing damage, and also audit the hacker's activities in Event Viewer so that you can detect the attacks.
It is not recommended that you Delete or Rename any of these files. Windows XP includes a feature called "Windows File Protection" which will automatically replace some of these files (e.g. cmd.exe) if they are deleted or renamed.
If you need access to one of these programs, it is recommended that you make a copy of the program with a different name (e.g. "cmdsafe.exe" or "ftp99.exe") -- don't forget to update any shortcuts to these files. This way, the hacker will not likely be able to find it (only you will know the name).
o Click here to learn how to disable a file.
o Click here to learn how to audit a file.
* 3.) Rename the Administrator account and disable the Guest account.
By default, winXP creates two accounts that many hackers look for on your machine, "Guest" and "Administrator". If your machine is a member of a domain, you will need to do this twice: Once on your machine, and once in Active Directory (Active Directory is beyond the scope of this article).
Click here to see an example of disabling the Guest account, and renaming the Administrator account.
* 4.) Use strong Account Policies:
The easiest way for a hacker to break into your network is via weak passwords and account policies. Using "Local Security Settings" (or Group Policy if you are using Active Directory), you should set the following:
o Password Policy (these make it hard for hackers to guess passwords)
+ Enforce password history: 24 passwords remembered
+ Maximum password age: 42 days
+ Minimum password age: 2 days
+ Minimum password length: 8 characters
+ Passwords must meet complexity requirements: Enabled
+ Store passwords using reversible encryption: Disabled (this may create problems for Macintosh or RAS users in your network)
o Account policies (these make it hard to run dictionary attacks against your machine)
+ Account lockout duration: 60 minutes
+ Account lockout threshold: 3 invalid logon attempts
+ Reset account lockout counter after: 60 minutes
Note that these account lockout policies do not apply to the Administrator account. It is very important to rename the Administrator account, as hackers will often run dictionary attacks against the Administrator account.
Click here to see an example of setting account policies.
* 5.) Auditing Windows XP Pro allows you to audit your machine through several mechanisms:
o IIS Logs: You should enable IIS Logging on all websites your machine hosts. You should periodically review these log files for hacker attempts. Specifically, search these files for failed (e.g. 404) requests, and also for the following words: echo, copy, rename, dir, del, format, cmd.exe, command.com, tftp.exe, ftp.exe, and in general, any .exe, .com, .bat or other file extension which your web users should not be using. The IIS Log files will also include the IP address of the attacker. You can use the Whois Tool included with InternetPeriscope to find out information about the hacker and his ISP from this IP address.
Click here to see how to setup IIS logging.
o Event Viewer -- Security Log: Windows XP Pro comes with a tool called Event Viewer (available under the Programs-Administrative Tools menu.) This tool logs Application, System, and Security Events. Unfortunately, the default installation of winXP does not enable any Security logging; you must turn on Security Auditing manually.
It is recommended that you configure the following using "Local Security Policy" or Active Directory Group policy (if your machine is a member of a domain.)
+ Audit account logon events: Failure
+ Audit account management: Success/Failure
+ Audit logon events: Failure
+ Audit object Access: Failure
(Note: This allows you to audit failed access to files. In addition to enabling this policy, you must also explicitly configure the file or directory for auditing. Click here to see an example of this.)
+ Audit policy change: Success/Failure
+ Audit privilege use: Failure
+ Audit system events: Success/Failure
Of course, it is very important to periodically review the Event Viewer Security log. It is strongly recommended that you backup ALL log files and set Event logs to "Do not overwrite events (clear log manually)".
Click here to see an example of setting up Audit Policy.
* 6.) Disable unnecessary services/drivers
o Disable Ftp Service: Ftp sends passwords in cleartext. This makes it easy for a hacker to "snoop" on traffic to your machine, and obtain your passwords. If you must run an ftp service on your webserver, it is strongly recommended that you disable "Write" access (Click here for info on how to do this.) If you must enable ftp write access, it is strongly recommended that you use IPSec to encrypt ftp traffic between your ftp server and clients. IPSec is beyond the scope of this article.
o Disable SNMP: Recently, many flaws have been found in the implementation and specification of SNMP. In addition, the default installation of SNMP allows hackers to obtain information on your server via the "Public" Community string.
Click here to learn how to determine if your machine is running an SNMP agent, and how to remove it.
o Disable Indexing Service: This indexing service allows you (and hackers) to quickly search for files on your system. Unless your webserver is using the Indexing Service to create a "Site Search" of your website, it is strongly recommended that your remove this service (More on this later.)
Click here to learn how to remove the Indexing Service.
o Disable Simple TCP/IP Services: These services are not installed by default, but many Sys Admins install them because they include such fun services as "Quote of the Day" and "Daytime". These services have been favorite targets of attackers for many years.
Click here to learn how to determine if your machine is running these services.
o Disable Network Monitor Driver. This driver is used by "Network Monitor" and/or SMS to analyze traffic on your machine.
* 7.) Default winXP Installation Directories.
Many hacker scripts depend on the default installation of Windows to work. For example, a hacker may, through a variety of mechanisms, attempt to run the following command from inside your Web directory: ..\..\windows\system32\cmd.exe /C del c:\*.*
This command would successfully delete the files on your C drive provided that:
o A.) Your website was installed in the c:\Inetpub\wwwroot directory.
o B.) Windows is installed in the c:\windows directory.
When installing ANY software on your machine, it is very important that you not choose the default installation directory. When installing Windows XP, don't install it in the default c:\windows (or c:\winnt) directory. Instead, install it in the j:\winXP10 directory (or something else that's hard to figure out). When creating a website, don't install it in c:\inetpub\wwwroot, instead, install it in m:\internet\websites\public directory.
Most hackers are running scripts that were written by someone else. These scripts often make default assumptions about how your server was installed. By not using the default partitions (or volumes) and directories, you can "fool" their scripts.
* 8.) IIS Server Configuration
o a.) Remove FrontPage Extensions. There are a number of exploits against FrontPage. It is strongly recommended that you remove this. Click here to learn how.
o b.) Remove Remote Desktop Web Connection (TSWEB). By default, IIS includes a website that enables you to administer the computer hosting IIS via a website. Typically that would show up as a url such as http://www.yoursitename.com/tsweb. Click here to learn how to remove this.
o c.) Remove unused App Mappings from Web Server. IF YOU DO NOTHING ELSE, AT LEAST DO THIS!
IIS includes a number of "Application Mappings" that invoke various programs when a web page with a certain file extension (e.g. .asp or .pl) is called. Even if you don't have a file in your website with one of these extensions, your server may still be vulnerable to an exploit against one of these file types -- and there are MANY exploits against various Application Mappings.
It is strongly recommended that you remove all unused Application mappings. "IIS Security Audit" can help you determine which Application Mappings you need to remove.
Specifically, you should remove the following: .cer .cdx .asa .htr .idc .shtm .shtml .stm .printer plx
In addition, if you are not using .asp or Perl files, you should remove the following application mappings: .asp, .pl
Click here to learn how to remove Application Mappings.
Click here to learn more about vulnerabilities against various App Mappings.
* 9.) Website Configuration
o a.) Disable the "Default Web Site" and delete all of its files. Hackers look for this configuration -- get rid of it. Create your own website, and don't put it in the c:\inetpub\wwwroot directory.
o b.) Turn off "Index this resource" on ALL websites. If you want to create a "Site Search" for your website, use a 3rd party tool that does not index the SOURCE CODE of your server-side scripts.
o c.) Turn off "Directory browsing" on ALL websites and virtual directories. Don't allow hackers to "browse" through your files.
o d.) Delete the "AdminScripts", "IISSamples" and "Scripts" directories. Hackers know of these default directories, and know of many exploits against the files that are installed in these directories in a default installation of IIS. Get rid of these directories, and never name your directories with these names.
o e.) Remove any residual FrontPage directories. Frontpage installs a bunch of directories that begin with the "_" character. Delete all of these directories and files, and get rid of any files or directories that your website is not using.
o f.) Make sure that none of your websites have the "Write" Permission turned on.
To learn how to configure an IIS website, click here.
* 10.) Enable auditing on Web and Ftp directories for Write, Delete, and Change Permissions.
Remember that to enable auditing, you must perform two steps:
o A.) Turn on "Audit object access" in "Local Security Settings" or "Group Policy".
o B.) Enable auditing for individual files and directories.
You should only enable auditing on files and directories that do not change often. Do not enable auditing on your mail directories (e.g. mailroot), or web directories that are generated periodically by log analysis programs (like Analog).
Be sure to check the Event Viewer - Security log periodically for hacker attempts.
* 11.) Check all open TCP/IP ports.
First, check to see which ports your machine has open, and figure out which services the ports map to. For the former, you can use "netstat -an" from a DOS prompt. Many users may find the Port Scan feature of InternetPeriscope easier to use, as it tells you which services are commonly used by which ports. Install and run InternetPeriscope ON your server for this first test.
Next, perform a Port Scan on your server from a machine that is OUTSIDE of your firewall. Again, InternetPeriscope can help you to do this. This will give you an idea of what ports the hacker's see when they scan your system.
If you see any services on your machine that you do not need, you should remove them to further "harden" your server's security.
* 12.) Miscellaneous Tasks
o A.) winXP Servers include a "Security Configuration and Analysis Tool". Unfortunately, this tool is well hidden in a default installation. Click here to learn how to use this tool.
o B.) Disable "Enumeration of SAM accounts and Shares (by anonymous users)". Depending on your configuration, Hackers can sometimes get a list of the usernames and share names on your machine using a "Null Session Vulnerability". This information can help the hacker to more easily crack passwords or take advantage of an unsecured share.
Click here to learn how to turn off "Enumeration of SAM accounts and Shares (by anonymous users)".
* 13.) Disable Remote Data Services (RDS)
RDS is known to be vulnerable to hacker attacks that enable a hacker to run files on your machine. Most websites do not use RDS, so RDS can be safely disabled. "IIS Security Audit" can help you determine if your machine is vulnerable to an RDS attack.
Click here to learn more about the RDS vulnerability.
* 14.) Disable ODBC Shell Access Vulnerability
IIS is vulnerable to an attack via the Jet Database Engine that can enable a malicious user to execute programs on an IIS Server. "IIS Security Audit" can help you determine if your machine is vulnerable to an ODBC Shell Access attack.
Click here to learn more about the ODBC vulnerability.
* 15.) Check Startup Files for Hacker Software
Windows has a number of methods for automatically launching software when a machine first boots or when a user first logs in. If your machine is attacked by hackers or infected by a Trojan, it is very likely that malicious software will be installed that uses one of these "auto-starting" mechanisms.
It is recommended that you periodically check and document which software is configured to "auto-start" on your server. If you believe your machine has been compromised, it is important that you check for "auto-starting" software before you reboot your machine.
"InternetPeriscope" can help you check for "auto-starting" software on your machine.
Click here to learn more about the "auto-starting" methods used by hackers.
* 16.) Use NTFS permissions to block Write Access
For many companies, the most horrifying danger posed by hackers is the modification of their web or ftp site. Specifically, they don't want hackers to deface their web pages or install trojan software on their ftp site. Fortunately, this is easy to prevent using NTFS.
NTFS allows you to specify which users can read or write specific directories and files. Unfortunately, the group "Everyone" is given the "Full Control" permission by default. This means that anyone who gains access to your web directory can write to it through a variety of hacks.
It is strongly recommended that you either "Deny" or remove the "Write" permission from the "Everyone" Group on your web and ftp directories. This way even if a hacker gains access to your system, it very unlikely that he will be able to modify your web or ftp files, causing your company great embarrasment.
Click here to learn how to change NTFS permissions.
* 17.) Remove Remote Access capability to your Windows XP computer.
Click here to learn how to change your Remote Access capability via Microsoft Terminal Services.
-
hi everyone,
i'm anyweb (the person who setup, runs, and maintains www.windows-noob.com),
real name, Niall C. Brady,
i'm an irish man, 39 years old (grey hairs too) and with three sons (Christopher - 7 and Sebastian (nearly) 3, Benjamin 1 and a half), and a girlfriend Annelie.
I live in Sweden.
I love working with computers, and my job involves that, I'm an SMS/SCCM admin by day...
I was born in Dublin, Ireland in 1966 and lived in Zambia, Africa for about 7 years from the ages of 3 to 10 or so. I've travelled to alot of different places in the world and am very happy living in Sweden now.
I've always been interested in computers, right from when i first got a ZX81 from my dad, i then progressed to an Amstrad CPC 6128 and taught myself how to program in assembly language in Z80 using a MAXAM rom and disassember. I started to first 'hack' games, and then went on to change the games by adding entire new levels and even new maps, it was fun fun fun. And very addictive. I was publised 14 times on popular English magazines at that time and all the results of that are here
I hope you all enjoy using these forums, and that we develop into a strong community.
cheers
anyweb
-
Protect yourself from Spyware.
This article is broken down into the following sections:-
Introduction
Enable a Firewall
Update Windows
Install Microsoft Windows Defender (anti-spyware software)
Use Antivirus software
Use a different Web Browser
Disable System Restore (optional)
Install LavaSoft Ad-Aware
Install HijackThis
Get Spybot Search And Destroy
Get or Enable the Browser popup blocker
Install an Anti-Phishing toolbar.
Conclusion
Introduction
Windows gets a lot of bad press because alot of it's users are generally clueless about protecting themselves from virus's and trojans (until it's too late). They get infected easily either by clicking on attachments in email or just browsing some lame site.
If you have come here to try and fix your broken Windows then I wish you all the best, do try and consider a web browser other than Internet Explorer, such as Firefox or Mozilla, and do try to follow all of the steps below to make your eXPerience with Windows, a better one. If Windows is running incredibly slow, acting weird or you notice that lots of popup windows are appearing on your desktop advertising stuff, or if Internet Explorer seems to have lots of unwelcome new websites loading, or if you are plagued with millions of Search 'Assistants', then try ALL of the following in the order listed.
Enable the built-in Firewall
A firewall is a computers way of protecting your computer from unwanted attacks via your internet connection. An unpatched Windows XP computer, with no firewall enabled will quickly succumb to worms such as Blaster. Protect yourself now and enable XP's built in FIREWALL if you don't have a hardware or software one running. It's included with Windows XP, but prior to Windows XP SP2, it was NOT enabled by default when you installed Windows. You could of course get one free like ZoneAlarm or even better a dedicated one such as Smoothwall.
.
Go to http://www.windowsupdate.com and update Windows
Amazingly, there are people out there who are still running Windows XP, as in, not even Windows XP SP1 (service pack 1) let alone Windows XP SP2 (the current latest service pack). Windows update allows your computer to be 'patched' with the latest security updates from Microsoft, if you are not updated, then every second you spend on the internet is a second nearer being 'owned' by the bad guys. Keep updating Windows until it reports 'no updates available'. Reboot when prompted.
Download, install and use Windows Defender
Believe it or not, this piece of software from Microsoft actually does a great job and has got good reviews all over the internet. Check it out right here on Microsoft's download page. Install it, check for updates, and do a full scan to see if you are infected by any Spyware.
Use AntiVirus software, and UPDATE it
There are no excuses nowadays for not having antivirus software installed. AVG is a really good alternative to Norton/Mcaffe, and guess what, its FREE as in beer. Download it yourself from http://free.grisoft.com/doc/5390/lng/us/tpl/v5#avg-free. This antivirus product works very well in Windows XP and is compatible with Service Pack 2. Needless to say, there is no point in having antivirus software if you don't update it regularly, so get updating and scan your hard discs often. In addition to the FREE AVG they offer a FREE antispyware application too.
Use a different Web Browser
Using a web browser other than Microsoft Internet Explorer will probably halt most of the bad stuff you are getting (at least until IE7 proves itself in Vista). Consider excellent alternatives such as Opera or Firefox. Once you start using browsers such as those, you'll notice life in Windows can be much less of a pain than you were used to.
Disable System Restore
This is an optional step. Disable SYSTEM RESTORE if it is running. To do this, right click on My Computer, choose Properties, and click on the 'System Restore' tab. Why disable this ? well because those nasties can hide themselves in your 'restore points' and the same is true for virus's. so, I'd recommend disabling it, it's not necessary anyway and saves on hard disc space.
Download Lavasoft Ad-Aware
Ok, next step is to download and run a few programs to remove the nasties. Download and install Lavasoft Ad-Aware® SE Personal Edition. Once installed, the first thing you need to do is to download the latest updates reference file. once done, Ad-Aware will want to perform a full scan, let it and make sure to quarantine any stuff that it finds. It is also a good idea to look through the list of 'problems' it finds for any real references to files, for example c:\windows\bundles\bundles.exe. If you see something like that, then manually delete the file. Once done, reboot, then run Ad-Aware again, hopefully it shouldnt report anything but if it does, keep going through this list or post your problem on the forums right here.
Download HijackThis
Now download the following program to check Internet Explorer (and the registry RUN commands) for any 'hijack' attempts (very common). Download HijackThis from here. Run the file and see what it reports, please note that not everything it reports is a problem, if in doubt, ask someone who knows or post the results on the forums.
Download Spybot Search And Destroy
Ok we are still not done, now we want to be absolutely sure that all the crap is gone, so lets install and run Spybot Search and Destroy. As above, it will scan your system for any bad stuff and report the results to you, if in doubt, ask an expert !
Download a popup-blocker
Install a popup blocker in Internet Explorer, so in case you end up using Internet Explorer (instead of FireFox or another browser) then at least you'll have some protection from the nasties out there. Thats Easy, either update to Windows XP service pack 2 (a popup blocker is included in Internet Explorer updates from SP2) or, download the popup blocker (toolbar) from MSN or (preferred) get Google's Popup blocker toolbar. These popup blockers are customisable and allow you to block those annoying advertisements and a whole lot more in Internet Explorer. Now that you have your popup-blocker installed, make sure to set it's internal settings to HIGH. In other words, block ALL popups. You can easily 'unblock' certain sites (such as banks) later on a site by site basis.
Install an Anti-phishing toolbar
Phishing spam is becoming very very popular with criminals, and is one of many methods they use to get your private details. You will most likely receive emails in your inbox claiming to be from your Bank, or from PayPal, or Ebay, asking you to 'update your records'. These are 'phishing' emails, and unless you know what to look for (view the source of the email in html to see if the web site URLS really ARE pointing to where they say they are) you might be one of those unlucky enough to get sucked in. This toolbar takes the hard work away from you and tells you when you are being stung before it happens.
Conclusion
By now, if you have followed the steps above, then your Windows box is hopefully a bit more secure than it was when you arrived here. Hopefully your malware, popups, popunders, worms, viruses and what not are now history, and not only that, but hopefully you have learned an important lesson in modern day computing.
Failure to update and/or protect your computer operating system, will leave you vulnerable to attack.
cheers
anyweb






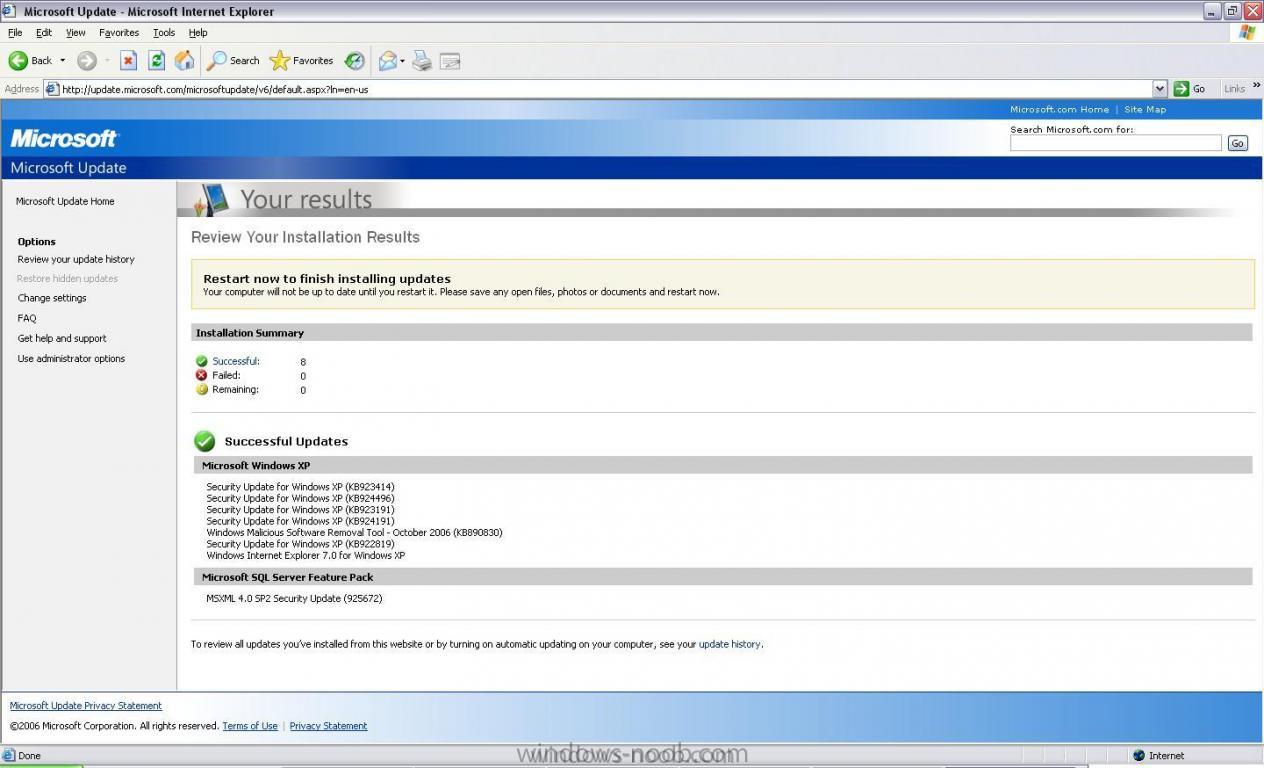
change partition sizes within windows vista
in installation issues
Posted
http://vistarewired.com/2007/02/16/how-to-...-windows-vista/
cheers
anyweb