Search the Community
Showing results for tags 'scup'.
-
Hello All, I am running SCUP 2011 and its working fine. Since SCUP 2017 is released, I installed on the same server where SCUP 2011 installed. Since the install paths are different, there is no option for upgrade but luckily post install it detects exsiting SCP 2011 setting and prompts to import which I done. After checking in SCUP 2017, I found that Published updates status is not imported from SCUP 2011 showing publication date blank and Publication workplace is empty. Does that mean that I have to re-create the publication and assign updates to it for earlier published updates from SCUP 2011? Will SCUP 2011 and SCUP 2017 can co-exist? What is the implication if I published those same updates from SCUP 2017 as well? Will they appear double in SCCM post syncing?
-
Afternoon all, Long time reader but first time posting on the forum. We have SCCM deploying updates via WSUS and SCUP for updating Dell drivers, Adobe etc. On all client machines I'm receiving the following error message when running Windows Update: "There were some problems installing updates, but we'll try again later. If you keep seeing this and want to search the web or contact support for information, this may help: (0x8024000f)" My colleague who has since left the company had a similar issue which he described the fix in the following blog post: http://gsilt.blogspot.co.uk/2014/09/scup-wsus-dell-and-error-0x8024000f.html. I've followed this through however I believe with Windows 10 this has now changed slightly as I can no longer find the keywords mentioned in the blog regarding find the references for "cycle" and "DetectUpdates" in the WindowsUpdate.log. All Windows 8.1 and Windows 10 clients are effected by this issue. I have attatched a log file from a Windows 10 machine and also one from Windows 7. Can someone point me in the right direction to get this sorted please as I'm about ready to pull my hair out. I've deleted the published updates from SCUP, imported from the latest catalog and re-published the updates and still no joy.WindowsUpdate.log Any help would be much appreciated. Thanks, C Windows10Update.log
-
I figured this out yesterday and wanted to share as it may help someone else as the internet failed to help me. Our SCUP 2011 started to fail to launch. It would show the splash screen then crash a few seconds later. In the Application event log there are two entries .NET framework and App Crash error (No help in these errors). Monitoring the size of the SCUPDB.SDF file to grew to ~256MB and that is the max size in the SCUP application (I couldn't figure out how to make this limit bigger.) The SQL Compact Edition 3.5 max size is 4GB. "Fixing it" I used SQL Server Management Studio to load the SCUPDB.SDF file (you have to change the maximum size in SSMS). Then I poked around in the tables and decided to delete a Vendor (Dell) and subsequent products, updates and bundles. (Make a backup of the SCUPDB.SDF file!) SELECT * FROM Vendors - Take the Id of the Vendor SELECT * FROM Products WHERE Vendor_Id = 'VENDORID' - Save the Product Id(s) SELECT * FROM UpdatePackages WHERE Product_Id IN ('PRODUCTID','PRODUCTID') - Use this query in the IN clause in the next query ( SELECT * changes to SELECT PackageId) SELECT * FROM BundledPackages WHERE UpdatePackage_PackageId IN (SELECT PackageId FROM UpdatePackages WHERE Product_Id IN ('PRODUCTID','PRODUCTID')) Now I ran these in reverse to delete data from the tables. DELETE FROM BundledPackages WHERE UpdatePackage_PackageId IN (SELECT PackageId FROM UpdatePackages WHERE Product_Id IN ('PRODUCTID','PRODUCTID')) DELETE FROM UpdatePackages WHERE Product_Id IN ('PRODUCTID','PRODUCTID') DELETE FROM Products WHERE Vendor_Id = 'VENDORID' DELETE FROM Vendors WHERE Id = 'VENDORID' Right click on the on the file in the object explorer and select properties. From there run a full database compaction. In my case I used Dell as the vendor. We never used their updates for drivers and etc. This reduced the file from 256MB to under 70MB. I hope this helps someone else!
-
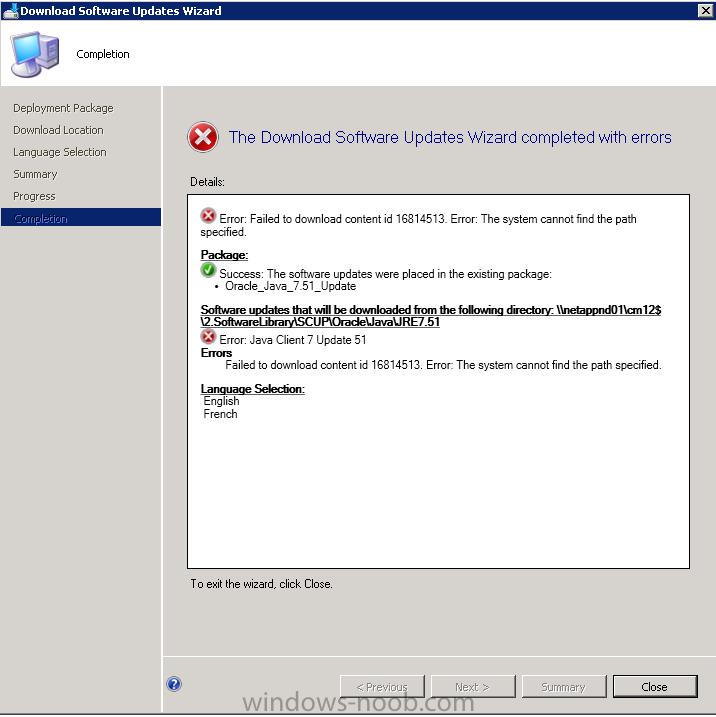
Hello all, I trying to update Java with SCUP Now, the update is visible in software update on the sccm server and i'm trying to create the package. In the download location setting, i type the UNC path on the network share used by the sccm server I tried with other location with the same error. Thanks in advance for any help Regards Laurent ----------------------------------------------------------------------------------------------------------------------------- Error: Failed to download content id 16814513. Error: The system cannot find the path specified. Package: Success: The software updates were placed in the existing package: • Oracle_Java_7.51_Update Software updates that will be downloaded from the following directory: \\netappnd01\cm12$\2.SoftwareLibrary\SCUP\Oracle\Java\JRE751 Error: Java Client 7 Update 51 Errors Failed to download content id 16814513. Error: The system cannot find the path specified. Language Selection: English French -----------------------------------------------------------------------------------------------------------------------------
-
Hi. Ran into a weird thing. We're deploying Config Manager updates via SCUP, and a number of our clients (all of them 32-bit so far) were failing to install the SP1 CU 5 patch for the CM client. The error in the event log was a 1706 saying it couldn't find a valid client.msi package. Digging around in the registry, all of these clients that I've seen so far had an installsource value in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{FD794BF1-657D-43B6-B183-603277B8D6C8} of "\\siteServer\Client\i386" - this share was indeed inaccessible Clients that patched successfully (both 32 and 64 bit) had a value of "c:\windows\ccmsetup\{Product Code for 32 or 64-bit client}" in there, instead. Changing the reg key on problem systems to point to the local copy of the .msi did not work, though I didn't try rebooting them, since they're all live systems. Changing the NTFS permissions on the \\siteserver\client share to grant everyone read (share permissions were already everyone=read) allowed these systems to patch. A system I was testing with and had changed the reg key to point at the local copy of the MSI actually changed that key back to \\siteServer\Client\i386 after patching was complete. So what I'm wondering, is: Is the differing InstallSource location normal behavior? Should the client share have had Everyone with Read on it already? If 2. is "yes" then what's the best way to make sure permissions aren't hosed elsewhere as well? Just wait til something breaks? Reset? Other? If 2. is "no" then what are potential repercussions of granting everyone read access? I'm thinking nothing, but...
-
- client share
- permissions
-
(and 2 more)
Tagged with:
-
Afternoon All, Hopefully there are some experienced SCUP users here on the forums. I seem to have an issue with the "Automatic" publishing feature of SCUP. They publish metadata only, despite client requesting that they need the update. My understanding is that if any Configuration Manager clients are requesting the update a full content will be initiated otherwise only metadata will be published. Am i missing something? Is there a specific log I can look at to see why it's not switching to full content automatically when requested?
- 3 replies
-
- SCUP
- Configuration Manager 2012
- (and 3 more)
-
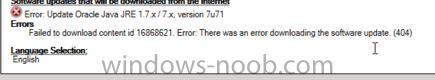
Hello, I am troubleshooting on behalf of another user. We have created a 3rd party update for Java 7 update 71, synched it into the SUP, elected the category and it is displayed in system center 2012 r2 for deployment. User is a full admin in system center, domain admin and local admin to the box they are running this action on. Every attempt to create the package fails with download error 404. The content is already in the WsusContent folder and the UpdateServicesPackages. What are we missing as far as permissions go that is causing this 404 error? Many thanks, CSC_dhudak
-
- sccm2012r2
- SUP
-
(and 2 more)
Tagged with:
-
I've just setup SCUP 2011 on my SCCM 2012 (2008 R2) server and managed to do the following: Configured: WSUS on same server, connected to Config Manager. Downloaded Adobe Updates via the SCUP Catalogue. Got the updates Published to SCCM 2012 and assigned to a Package and Software Group within SCCM Exported the WSUS cert and reimported as Trusted Publisher and Root on the test client and also the server. Assigned deployment to test collection that has one computer in need of those updates. However, on the client itself, I cannot get it to detect and download the relevant updates for Adobe Reader, I've been trawling through the logs looking for evidence that the updates were detected and downloaded, and also manually checked the ccmcache and also (WSUS) softwaredownload folders, all had no downloaded files or references of the Adobe updates. I can't think of anything else and there is nothing obvious in the logs that I can see, hopefully someone with experience can point me in the right direction? The client has the following set via a test GPO: AcceptTrustedPublisherCerts = 1 WUServer = http:sccm-server:80 WUStatusServer = http:sccm-server:80 UpdatesHandler.log Successfully initiated scan. UpdatesHandler 08/04/2013 13:33:39 4036 (0x0FC4) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 13:33:39 3608 (0x0E18) Successfully initiated scan. UpdatesHandler 08/04/2013 13:33:39 3608 (0x0E18) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 13:33:40 4036 (0x0FC4) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 13:33:44 4980 (0x1374) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 13:33:48 3608 (0x0E18) Successfully initiated scan. UpdatesHandler 08/04/2013 13:33:49 3608 (0x0E18) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 13:34:54 4980 (0x1374) CUpdatesAgent::FinalConstruct entered UpdatesHandler 08/04/2013 14:50:07 3332 (0x0D04) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 14:56:43 3524 (0x0DC4) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 14:56:43 3108 (0x0C24) Successfully initiated scan. UpdatesHandler 08/04/2013 14:56:43 3524 (0x0DC4) Successfully initiated scan. UpdatesHandler 08/04/2013 14:56:43 3108 (0x0C24) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 14:56:43 3524 (0x0DC4) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 14:56:43 3416 (0x0D58) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 15:31:26 3864 (0x0F18) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 15:31:26 5916 (0x171C) Successfully initiated scan. UpdatesHandler 08/04/2013 15:31:26 3864 (0x0F18) Successfully initiated scan. UpdatesHandler 08/04/2013 15:31:26 5916 (0x171C) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 15:32:20 5232 (0x1470) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 15:32:21 5232 (0x1470) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:24:32 4816 (0x12D0) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:24:32 3068 (0x0BFC) Successfully initiated scan. UpdatesHandler 08/04/2013 16:24:32 4816 (0x12D0) Successfully initiated scan. UpdatesHandler 08/04/2013 16:24:33 3068 (0x0BFC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:25:21 4824 (0x12D8) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:25:21 3068 (0x0BFC) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:30:13 3744 (0x0EA0) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:30:13 4824 (0x12D8) Successfully initiated scan. UpdatesHandler 08/04/2013 16:30:13 3744 (0x0EA0) Successfully initiated scan. UpdatesHandler 08/04/2013 16:30:13 4824 (0x12D8) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:30:19 2160 (0x0870) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:30:21 3744 (0x0EA0) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:39:13 4016 (0x0FB0) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:39:13 4572 (0x11DC) Successfully initiated scan. UpdatesHandler 08/04/2013 16:39:13 4016 (0x0FB0) Successfully initiated scan. UpdatesHandler 08/04/2013 16:39:13 4572 (0x11DC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:40:02 2524 (0x09DC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:40:02 2524 (0x09DC) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:54:11 5192 (0x1448) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:54:11 3692 (0x0E6C) Successfully initiated scan. UpdatesHandler 08/04/2013 16:54:11 3692 (0x0E6C) Successfully initiated scan. UpdatesHandler 08/04/2013 16:54:11 5192 (0x1448) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:55:14 5624 (0x15F8) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:55:15 4904 (0x1328) CUpdatesAgent::FinalConstruct entered UpdatesHandler 08/04/2013 17:09:42 2604 (0x0A2C) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:11:17 4780 (0x12AC) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:11:17 4872 (0x1308) Successfully initiated scan. UpdatesHandler 08/04/2013 17:11:18 4872 (0x1308) Successfully initiated scan. UpdatesHandler 08/04/2013 17:11:18 4780 (0x12AC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:13:03 3812 (0x0EE4) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:13:03 4780 (0x12AC) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:13:37 3812 (0x0EE4) Successfully initiated scan. UpdatesHandler 08/04/2013 17:13:37 3812 (0x0EE4) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:13:37 4780 (0x12AC) Successfully initiated scan. UpdatesHandler 08/04/2013 17:13:37 4780 (0x12AC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:14:16 5180 (0x143C) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:14:16 1056 (0x0420) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C) Successfully initiated scan. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C) Successfully initiated scan. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:47:07 4500 (0x1194) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:47:07 964 (0x03C4) UpdatesDeployment.log Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_499fc6e1-f6de-4e4c-b98d-41ca21bee49b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e93c80ff-812b-4640-a7fb-d3712b86e3b1) added to the targeted list of deployment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B}) UpdatesDeploymentAgent 08/04/2013 16:55:15 5624 (0x15F8) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_49ddec56-93f2-48e7-98af-ecd54526d34c) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_5c22235f-a3d9-48db-95eb-a60ec1886e8e) added to the targeted list of deployment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B}) UpdatesDeploymentAgent 08/04/2013 16:55:15 5624 (0x15F8) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9e40eb5c-184a-494d-be46-8b140386179b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_da767d4a-8677-4b9d-9f0b-365f14e19ae1) added to the targeted list of deployment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B}) UpdatesDeploymentAgent 08/04/2013 16:55:15 5624 (0x15F8) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_d0fbac2f-d08f-4a7b-a826-92b1c5ae0bc5) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328) EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 0 UpdatesDeploymentAgent 08/04/2013 16:56:29 2892 (0x0B4C) User logoff system task UpdatesDeploymentAgent 08/04/2013 17:03:45 4708 (0x1264) Service startup system task UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) Software Updates feature is enabled UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) Total Pending reboot updates = 0 UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) No pending reboot updates at system restart. UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) No current service window available to run updates assignment with time required = 1 UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) CUpdateAssignmentsManager::OnThirdPartyOrchestrationSettingChange - No pending install assignment UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) Startup task completed UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) User logon system task UpdatesDeploymentAgent 08/04/2013 17:09:50 988 (0x03DC) Assignment {0ADCDD92-9E6F-4796-AFFD-7013EB4E554B} has total CI = 20 UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) OnPolicyDelete for assignment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B})... UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_27fc50b4-5982-4d58-a13d-53bd1f3806ea", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_957317cf-ef0d-4fa7-a2ad-5d2db2cf355e", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_1f6d4200-fcb6-4a4c-8ad7-ab76c529bff3", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_7ad922e0-685f-4723-9da3-4d7acefb4706", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e9e8a81d-ed5a-4af3-963e-2dc4413e3c3e", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_42cc6726-c3fe-464b-b8ac-38ec00766262", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_f51bc4bd-7424-4c47-ae97-714a8e3895b5", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_04874d8a-71a5-43d9-8531-eb19fdf319e6", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_0e79069c-cdca-4c91-aad3-e21ede710634", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_6d8590bd-038e-4455-9764-30875ccbf0c7", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_02fe5101-40eb-4d91-aa9d-5727060aefba", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_07151137-3b83-4064-8fc2-7bf983d6b08b", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_421e86ff-37e0-4199-9a0c-4976332bbcdf", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_521d70cd-3256-4c26-96f8-b7c3c4adc113", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9b65fe9a-721e-4390-860d-02c1dbffa10f", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9caf7699-d7f8-4cbb-95c9-002cbe3df07d", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_022d7dab-a021-4318-9c71-16323944584d", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e93c80ff-812b-4640-a7fb-d3712b86e3b1", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_5c22235f-a3d9-48db-95eb-a60ec1886e8e", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_da767d4a-8677-4b9d-9f0b-365f14e19ae1", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 0 UpdatesDeploymentAgent 08/04/2013 17:10:10 3484 (0x0D9C) Message received: '<?xml version='1.0' ?><SoftwareUpdatesMessage MessageType='EvaluateAssignments'><UseCachedResults>False</UseCachedResults></SoftwareUpdatesMessage>' UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Removing scan history to force non cached results UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Assignment {47ABB848-E3B5-405B-AA5E-01514176142F} has total CI = 7 UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Detection job ({C92EAD93-F8F7-4257-BD47-FF953B523427}) started for assignment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Started evaluation for assignment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Assignment {28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C} has total CI = 20 UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Detection job ({4BDCE35B-6B75-4DE8-BB1D-9ADD513CA2D0}) started for assignment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Started evaluation for assignment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Evaluation initiated for (2) assignments. UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) DetectJob completion received for assignment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:03 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9703dec9-deaf-4566-b966-aeca447a4ba4) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_a13356e5-6224-44e0-9020-9a3c924da131) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_244b7a38-eb9e-4632-a299-b085587d477c) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_499fc6e1-f6de-4e4c-b98d-41ca21bee49b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_49ddec56-93f2-48e7-98af-ecd54526d34c) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9e40eb5c-184a-494d-be46-8b140386179b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_d0fbac2f-d08f-4a7b-a826-92b1c5ae0bc5) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) DetectJob completion received for assignment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_27fc50b4-5982-4d58-a13d-53bd1f3806ea) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_957317cf-ef0d-4fa7-a2ad-5d2db2cf355e) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_1f6d4200-fcb6-4a4c-8ad7-ab76c529bff3) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_7ad922e0-685f-4723-9da3-4d7acefb4706) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e9e8a81d-ed5a-4af3-963e-2dc4413e3c3e) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_42cc6726-c3fe-464b-b8ac-38ec00766262) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_f51bc4bd-7424-4c47-ae97-714a8e3895b5) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_04874d8a-71a5-43d9-8531-eb19fdf319e6) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_0e79069c-cdca-4c91-aad3-e21ede710634) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_6d8590bd-038e-4455-9764-30875ccbf0c7) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_02fe5101-40eb-4d91-aa9d-5727060aefba) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_07151137-3b83-4064-8fc2-7bf983d6b08b) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_421e86ff-37e0-4199-9a0c-4976332bbcdf) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_521d70cd-3256-4c26-96f8-b7c3c4adc113) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9b65fe9a-721e-4390-860d-02c1dbffa10f) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9caf7699-d7f8-4cbb-95c9-002cbe3df07d) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 WUAHandler.log Async searching completed. WUAHandler 08/04/2013 15:32:17 4964 (0x1364) Successfully completed scan. WUAHandler 08/04/2013 15:32:19 1032 (0x0408) Scan results will include all superseded updates. WUAHandler 08/04/2013 15:32:20 1044 (0x0414) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 15:32:20 1044 (0x0414) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 15:32:20 1044 (0x0414) Async searching completed. WUAHandler 08/04/2013 15:32:20 4960 (0x1360) Successfully completed scan. WUAHandler 08/04/2013 15:32:20 1044 (0x0414) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 16:24:30 4816 (0x12D0) Existing WUA Managed server was already set (http://:80), skipping Group Policy registration. WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Async searching completed. WUAHandler 08/04/2013 16:31:08 1096 (0x0448) Successfully completed scan. WUAHandler 08/04/2013 16:31:11 3744 (0x0EA0) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Async searching completed. WUAHandler 08/04/2013 16:39:58 3424 (0x0D60) Successfully completed scan. WUAHandler 08/04/2013 16:40:00 4016 (0x0FB0) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:40:01 6024 (0x1788) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 16:40:01 6024 (0x1788) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:40:01 6024 (0x1788) Async searching completed. WUAHandler 08/04/2013 16:40:01 4956 (0x135C) Successfully completed scan. WUAHandler 08/04/2013 16:40:01 6024 (0x1788) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 16:54:09 5244 (0x147C) Enabling WUA Managed server policy to use server: http://sccmserver:80 WUAHandler 08/04/2013 16:54:09 5244 (0x147C) Waiting for 2 mins for Group Policy to notify of WUA policy change... WUAHandler 08/04/2013 16:54:09 5244 (0x147C) Waiting for 30 secs for policy to take effect on WU Agent. WUAHandler 08/04/2013 16:54:16 5244 (0x147C) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 16:54:46 5244 (0x147C) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:54:46 5244 (0x147C) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 16:54:46 5244 (0x147C) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:54:46 5244 (0x147C) Async searching completed. WUAHandler 08/04/2013 16:55:11 5944 (0x1738) Successfully completed scan. WUAHandler 08/04/2013 16:55:13 5624 (0x15F8) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:55:14 5244 (0x147C) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 16:55:14 5244 (0x147C) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:55:14 5244 (0x147C) Async searching completed. WUAHandler 08/04/2013 16:55:14 5516 (0x158C) Successfully completed scan. WUAHandler 08/04/2013 16:55:14 4904 (0x1328) CWuaHandler::SetCategoriesForLeafStateReportingExclusion called with E0789628-CE08-4437-BE74-2495B842F43B WUAHandler 08/04/2013 17:09:26 2604 (0x0A2C) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Async searching completed. WUAHandler 08/04/2013 17:13:00 4208 (0x1070) Successfully completed scan. WUAHandler 08/04/2013 17:13:02 4780 (0x12AC) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'E1D507BE-497C-D8FD-61D7-B0D93EE399CA') OR (DeploymentAction=* AND Type='Software' AND CategoryIDs contains '3B36FCFD-0384-EA97-2D49-1349AE748647') OR (DeploymentAction=* AND Type='Software' AND CategoryIDs contains '70CFAD70-6629-B54B-5819-C809A605515E')) WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4) Async searching completed. WUAHandler 08/04/2013 17:13:03 4344 (0x10F8) Successfully completed scan. WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Async searching completed. WUAHandler 08/04/2013 17:14:13 5476 (0x1564) Successfully completed scan. WUAHandler 08/04/2013 17:14:15 1056 (0x0420) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4) Async searching completed. WUAHandler 08/04/2013 17:14:16 5648 (0x1610) Successfully completed scan. WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Async searching completed. WUAHandler 08/04/2013 17:47:03 4948 (0x1354) Successfully completed scan. WUAHandler 08/04/2013 17:47:05 964 (0x03C4) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:47:06 4764 (0x129C) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 17:47:06 4764 (0x129C) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:47:06 4764 (0x129C) Async searching completed. WUAHandler 08/04/2013 17:47:06 5180 (0x143C) Successfully completed scan. WUAHandler 08/04/2013 17:47:07 4764 (0x129C) UpdateStore.log Update status from update (eb303398-da7c-4ce6-b8db-254409b32c39) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (eb30575d-51df-4c24-87dc-9b9c6dc8aa04) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (eb7a169f-6bca-4e00-a52a-623c063c162d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (ebbdc330-bd19-47b9-9e08-c4f32694429b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (ec1f4a29-8828-4fbe-b101-5a89321d8e7f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (edcc7a72-ffa0-4753-b59a-976044bbb012) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (efb911ae-5fba-48c7-8060-51734e3c1144) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f019d0aa-dfcf-4af8-b846-d38f8f7239e7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f0b50507-6c86-41d6-9350-6a8af21f76c7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f120b7a8-9ee3-4e95-8628-ac27b0d1df85) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f19502ff-7637-4ed8-bbc1-1b2508e56e2b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f1b1b1e1-2b22-4445-8a9c-5924bf945d32) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f21b0303-4d18-4a9b-9bda-8a796062189b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f284dc51-5659-4534-a1c7-6b9dbfe9453a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f2b28914-a6bc-44c5-ac04-9e7fbdea657e) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f2c6b0b8-f2cf-4f6c-8d64-6a21b9ca86d2) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f307ffeb-f424-4a79-8bc3-d472be542dec) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f45f3c72-427b-4889-a627-836244bf1ce1) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f4683760-71cc-4e3f-82a0-e1c164955163) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f51a0e5b-24a9-4be1-8b36-0f22f99949e7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f5202a56-ff34-401d-a040-f97c7f70891c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f53b1817-e327-438b-afb8-0cd5a0f95cb2) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f54ace97-a003-44a4-9e36-ef7071f6ce9d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f591538a-2c8f-4dc4-8b17-8b07c9a851ca) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f808dbaf-bec7-4dfb-a0cc-25290a7cd368) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f9b10375-898c-4d12-8722-b2f7f6e81521) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fabc6fae-c385-4543-a483-1b1cadfade98) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fabea4ad-b256-4b4e-b9cf-988bcfd5463f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fbc62e30-1128-4af5-9cb7-e1e349eb1b23) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fc5608e4-a70d-4344-b358-2847f4a57434) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fc5b1588-f912-4c1b-9f87-4ee1b427c5b1) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fc7c3752-4c17-473c-8bff-75eed375fd61) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fd8b7365-bc78-48e5-96c0-53682b94a607) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fdc8ef3a-11eb-45e6-9e0e-38a193f7b48c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (ff1d0808-8bb8-47ea-90c4-f7e806f7bde0) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Successfully done with SetStatus() operation. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (097d6f40-e0dc-4410-893f-24d5326aed8a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (0aa3cf0a-2269-4356-ad99-0e3ca8eb439f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (0b92accc-057d-408a-8e6e-0867f21f015f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (138bccfd-40ac-4a5d-84f0-3e5bf9743e42) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (161ed7f2-9f54-4625-914c-2b3c93040db4) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (2b487f1d-e072-4be7-986c-4355c3372cd1) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (324f1032-de0c-406e-b611-34b99c64e21d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (3abe760c-4578-4c84-a1cb-bf1df019efe4) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (40bd5a76-a368-4088-b172-a9e5dd1e5e3a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (40ccd4f1-cc6f-4368-968b-29d10e57b05f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (48f658bc-fec4-4464-8f01-db68c5ab1720) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (596adb47-108d-482d-85ba-a513621434b7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (5eca77b2-63e0-4df3-b1b0-acb90f28c532) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (7079beeb-6120-4afd-ad07-fb4dfa284fbe) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (71a29c39-e160-4b00-9b2f-d9924c8e09d5) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (744f9366-c308-44b2-8542-ca31c229179d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (75914178-2bdf-4fd3-b537-e2a517734bc7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (79f342ab-66e7-42a7-8315-2677f99f20c5) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (7c25aee0-71f5-4fda-8763-effae905b564) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (82538218-b3eb-4c56-a9b8-fdb358869d2b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (979b9aa2-dcf8-45d6-a31d-63df2a02d043) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (97e091c7-35eb-4da0-9346-e6f33115c8ed) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (98c62b24-a3dd-4843-ad1a-e08d95624f00) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (a429515b-9216-4277-bd4d-bf0593542c0d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (a61bd9f9-6940-408c-a80e-5a7dc4f5e1a2) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (a643a7c6-aa86-480c-b9e8-7f9abca811e6) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (ac8b33b5-2df2-4e6a-8d48-105ba0cc3bff) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (af91fcf0-fc28-4293-acc6-598fdcea359a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (afdd5d5e-2cc2-4a6a-a44f-e45a275702f5) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (b047a38c-47a5-4ac7-b42a-0c4d80f3341c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (b14fba1c-2b3b-4746-8801-104180701e7e) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (b628f40e-33de-4a37-81ae-9c2868c75373) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (c6164205-7295-4670-8a2f-8dad2d0682b0) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (d7568b8a-3d37-43de-8d65-b6a0a73b010c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (de4cbbf4-443f-4bb7-aebf-8da2fcc7b706) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (e5cbc9ff-0953-4efc-8acc-6a130bd4385b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (eb30575d-51df-4c24-87dc-9b9c6dc8aa04) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (fc5608e4-a70d-4344-b358-2847f4a57434) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Successfully done with SetStatus() operation. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Querying update status of 20 updates. UpdatesStore 08/04/2013 17:47:07 4500 (0x1194) Querying update status completed successfully. UpdatesStore 08/04/2013 17:47:07 4500 (0x1194) Querying update status of 7 updates. UpdatesStore 08/04/2013 17:47:07 964 (0x03C4) Querying update status completed successfully. UpdatesStore 08/04/2013 17:47:07 964 (0x03C4) Querying update status of 20 updates. UpdatesStore 08/04/2013 18:01:00 6032 (0x1790) Querying update status completed successfully. UpdatesStore 08/04/2013 18:01:00 6032 (0x1790) Querying update status of 20 updates. UpdatesStore 08/04/2013 18:01:00 3748 (0x0EA4) Querying update status completed successfully. UpdatesStore 08/04/2013 18:01:00 3748 (0x0EA4)
-
Hello all, I installed and configured SCUP 2011 on my CM. I generated a cert, and imported it into the two certificate catagories that you need to. When i install the updates from sccm that I imported using SCUP, they failed with a cert error. Is there somewhere else that the certs need to be? I'm putting the certs under system account, do they need to go under user account? -Thanks as always!
-
Trying to configure SCUP so that we can import updates into SCCM. However, when trying to download the Dell Cab Files i'm getting the following error. Just wondering if anyone has seen this before and got any ideas on how to resolve? Passive FTP has been unchecked as that's what I initially thought Download file: ftp://ftp.dell.com/catalog/DellSDPCatalogPC.cab failed with message "The remote server returned an error: 227 Entering Passive Mode
-
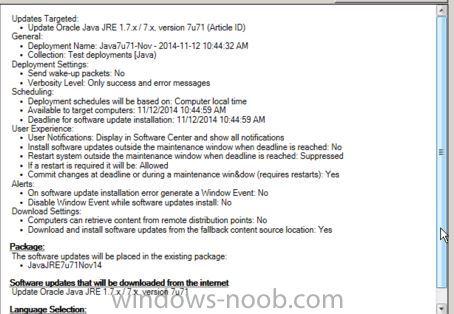
Hi all This is the first time i'm using SCUP, so there is perhaps an error somewhere I've published Java 7.51 from SCUP and the logs seems correct. scup.log Publications workspace: Starting publish wizard for publication 'Java JRE7.51'. Updates Publisher 1/01/1601 00:00:00 1 (0x0001) Publish: Preparing list of selected updates for publishing. Updates Publisher 1/01/1601 00:00:00 7 (0x0007) Connecting to a local update server with locally detected settings. Updates Publisher 1/01/1601 00:00:00 7 (0x0007) Publish: Update server name: SRVWSUSND01 Updates Publisher 1/01/1601 00:00:00 7 (0x0007) Publish: Publish operation starting for 1 updates. Updates Publisher 1/01/1601 00:00:00 7 (0x0007) Publish: Publish: Verifying update server is configured with a certificate prior to publishing. Updates Publisher 1/01/1601 00:00:00 7 (0x0007) Publish: Publish: Update server appears to be configured with a certificate. Updates Publisher 1/01/1601 00:00:00 7 (0x0007) Building dependency graph for update 'Java Client 7 Update 51 (UpdateId:'dc003514-5edc-4b87-9da1-f3e3cd38a924' Vendor:'Oracle' Product:'Java Client')' Updates Publisher 1/01/1601 00:00:00 7 (0x0007) No dependencies found for update 'Java Client 7 Update 51 (UpdateId:'dc003514-5edc-4b87-9da1-f3e3cd38a924' Vendor:'Oracle' Product:'Java Client')' Updates Publisher 1/01/1601 00:00:00 7 (0x0007) Found total of 0 dependencies (may include duplicates). Updates Publisher 1/01/1601 00:00:00 7 (0x0007) PublishItem: Update ''Java Client 7 Update 51 (UpdateId:'dc003514-5edc-4b87-9da1-f3e3cd38a924' Vendor:'Oracle' Product:'Java Client')'' has no dependencies. Updates Publisher 1/01/1601 00:00:00 7 (0x0007) PublishItem: Publishing update 'Java Client 7 Update 51 (UpdateId:'dc003514-5edc-4b87-9da1-f3e3cd38a924' Vendor:'Oracle' Product:'Java Client')'. Updates Publisher 1/01/1601 00:00:00 7 (0x0007) PublishItem: --- Evaluating software update 'Java Client 7 Update 51 (UpdateId:'dc003514-5edc-4b87-9da1-f3e3cd38a924' Vendor:'Oracle' Product:'Java Client')' for publishing as FullContent. Updates Publisher 1/01/1601 00:00:00 7 (0x0007) PublishItem: Item 'Java Client 7 Update 51 (UpdateId:'dc003514-5edc-4b87-9da1-f3e3cd38a924' Vendor:'Oracle' Product:'Java Client')' is already published on the update server and has not changed so no action will be taken. Updates Publisher 1/01/1601 00:00:00 7 (0x0007) PublishItem: --- Skipping software update 'Java Client 7 Update 51 (UpdateId:'dc003514-5edc-4b87-9da1-f3e3cd38a924' Vendor:'Oracle' Product:'Java Client')'. Updates Publisher 1/01/1601 00:00:00 7 (0x0007) PublishProgress: Publish operation completed. Updates Publisher 1/01/1601 00:00:00 7 (0x0007) Publish: Background processing completed. Updates Publisher 1/01/1601 00:00:00 1 (0x0001) Then i synchronize from SCCM 2012 and nothing happened ! wsyncmgr.log Found local sync request file SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:42 PM 8292 (0x2064) Starting Sync SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:42 PM 8292 (0x2064) Performing sync on local request SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:42 PM 8292 (0x2064) Read SUPs from SCF for srvsccmnd01.xxxxx SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:42 PM 8292 (0x2064) Found 1 SUPs SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:42 PM 8292 (0x2064) Found active SUP srvwsusnd01.ghdc.local from SCF File. SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:42 PM 8292 (0x2064) STATMSG: ID=6701 SEV=I LEV=M SOURCE="SMS Server" COMP="SMS_WSUS_SYNC_MANAGER" SYS=srvsccmnd01.GHDC.LOCAL SITE=GHC PID=11808 TID=8292 GMTDATE=mer. févr. 26 12:46:42.923 2014 ISTR0="" ISTR1="" ISTR2="" ISTR3="" ISTR4="" ISTR5="" ISTR6="" ISTR7="" ISTR8="" ISTR9="" NUMATTRS=0 SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:42 PM 8292 (0x2064) Synchronizing WSUS server srvwsusnd01.ghdc.local SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:43 PM 8292 (0x2064) STATMSG: ID=6704 SEV=I LEV=M SOURCE="SMS Server" COMP="SMS_WSUS_SYNC_MANAGER" SYS=srvsccmnd01.GHDC.LOCAL SITE=GHC PID=11808 TID=8292 GMTDATE=mer. févr. 26 12:46:43.927 2014 ISTR0="" ISTR1="" ISTR2="" ISTR3="" ISTR4="" ISTR5="" ISTR6="" ISTR7="" ISTR8="" ISTR9="" NUMATTRS=0 SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:43 PM 8292 (0x2064) Synchronizing WSUS server srvwsusnd01xxxx... SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:43 PM 3616 (0x0E20) sync: Starting WSUS synchronization SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:43 PM 3616 (0x0E20) sync: WSUS synchronizing categories SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:47 PM 3616 (0x0E20) Done synchronizing WSUS Server srvwsusnd01.xxxx SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:49 PM 3616 (0x0E20) Sleeping 2 more minutes for WSUS server sync results to become available SMS_WSUS_SYNC_MANAGER 2/26/2014 1:46:49 PM 3616 (0x0E20) When i search though "All software updates", Java doesnt appears but if if filtered through "VENDOR", i can see Oracle ! (cfr attached file) But no Oracle or Java updates appears. Thanks Laurent
-
I have SCUP hooked into my SCCM installation and I push out adobe flash updates like the rest of the windows updates. I notice that SCCM doesn't know when to supersede the flash updates. Is the best way to work with this to only keep the most recent in the update group that contains the flash updates? I don't want it pushing out old ones and new ones all at the same time over and over. I have attached a picture just to clarify if needed.
-
Hello All -- i'm having a issue where some clients seem to stall on random updates. The ones I can list right now are the following: KB2393802 KB977165 Below is the windowsupdate.log file where the errors are showing: 2012-03-29 10:44:42:472 908 99c Agent WARNING: Failed to evaluate Installable rule, updateId = {DA6B31D6-B702-4E4A-BD22-748936012392}.102, hr = 80080005 2012-03-29 10:45:42:505 908 99c Agent WARNING: Failed to evaluate Installed rule, updateId = {84AB24E9-6CD3-4113-8376-28349505359B}.105, hr = 80080005 2012-03-29 10:46:12:527 908 99c Agent WARNING: Failed to evaluate Installable rule, updateId = {84AB24E9-6CD3-4113-8376-28349505359B}.105, hr = 80080005 2012-03-29 10:47:12:546 908 99c Agent WARNING: Failed to evaluate Installed rule, updateId = {B6B62539-AF33-4073-8D78-32EC53FE2AD8}.102, hr = 80080005 2012-03-29 10:47:42:558 908 99c Agent WARNING: Failed to evaluate Installable rule, updateId = {B6B62539-AF33-4073-8D78-32EC53FE2AD8}.102, hr = 80080005 2012-03-29 10:48:42:584 908 99c Agent WARNING: Failed to evaluate Installed rule, updateId = {43845711-F505-43A7-9EAB-592A2E7453DF}.103, hr = 80080005 2012-03-29 10:49:12:594 908 99c Agent WARNING: Failed to evaluate Installable rule, updateId = {43845711-F505-43A7-9EAB-592A2E7453DF}.103, hr = 80080005 2012-03-29 10:50:12:630 908 99c Agent WARNING: Failed to evaluate Installed rule, updateId = {56745877-75B3-4B52-85F5-6648928A5FF6}.103, hr = 80080005 2012-03-29 10:50:42:640 908 99c Agent WARNING: Failed to evaluate Installable rule, updateId = {56745877-75B3-4B52-85F5-6648928A5FF6}.103, hr = 80080005 2012-03-29 10:51:42:660 908 99c Agent WARNING: Failed to evaluate Installed rule, updateId = {3CF0933C-65EB-4825-B1EE-84157F638463}.103, hr = 80080005 2012-03-29 10:52:12:676 908 99c Agent WARNING: Failed to evaluate Installable rule, updateId = {3CF0933C-65EB-4825-B1EE-84157F638463}.103, hr = 80080005 2012-03-29 10:53:12:736 908 99c Agent WARNING: Failed to evaluate Installed rule, updateId = {373F82CB-B6C9-4C6B-8AF2-9A5C4D9E7251}.103, hr = 80080005 2012-03-29 10:53:42:742 908 99c Agent WARNING: Failed to evaluate Installable rule, updateId = {373F82CB-B6C9-4C6B-8AF2-9A5C4D9E7251}.103, hr = 80080005 This output is from the WUHandler.log in the CCM\LOGS folder of the client having the issue Going to search using WSUS update source. WUAHandler 3/29/2012 12:20:16 AM 1616 (0x0650) Synchronous searching of all updates started... WUAHandler 3/29/2012 12:20:16 AM 1616 (0x0650) Successfully completed synchronous searching of updates. WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) Update(s) were found in WUA, now going to download binary files to WUA file cache WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) Flattening update tree... WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) 1. Update: 15b8ae3b-e200-47fe-afc1-45eedee16d2c, 105 BundledUpdates: 1 WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) Update: df9c03ff-629d-443d-8d07-f37421b37e0a, 105 BundledUpdates: 0 WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) 2. Update: 9bca5a73-cc9a-4f6b-a5b4-fd7cb4b3e122, 100 BundledUpdates: 1 WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) Update: e4bf7c98-c3a1-4c2c-aac6-a06d86e1bdf6, 100 BundledUpdates: 0 WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) Flattening update collection... WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) 1. Update (Missing): Security Update for Windows 7 (KB2393802) (15b8ae3b-e200-47fe-afc1-45eedee16d2c, 105) WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) Leaf: df9c03ff-629d-443d-8d07-f37421b37e0a, 105 Status: Missing WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) 2. Update (Missing): Security Update for Windows 7 (KB977165) (9bca5a73-cc9a-4f6b-a5b4-fd7cb4b3e122, 100) WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) Leaf: e4bf7c98-c3a1-4c2c-aac6-a06d86e1bdf6, 100 Status: Missing WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) Update(s) downloaded to WUA file cache, starting installation. WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) Async installation of updates started. WUAHandler 3/29/2012 5:36:26 AM 1616 (0x0650) Its a WSUS Update Source type ({6C725974-EE51-4F35-B18F-92E26BD9C225}), adding it. WUAHandler 3/29/2012 5:36:26 AM 4092 (0x0FFC) WSUS update source already exists, checking whether correct server is set. WUAHandler 3/29/2012 5:36:26 AM 4092 (0x0FFC) Existing WUA Managed server was already set (http://SERVER:8530), skipping Group Policy registration. WUAHandler 3/29/2012 5:36:26 AM 4092 (0x0FFC) Added Update Source ({6C725974-EE51-4F35-B18F-92E26BD9C225}) of content type: 2 WUAHandler 3/29/2012 5:36:26 AM 4092 (0x0FFC) No proxy information available, not setting proxy. WUAHandler 3/29/2012 5:36:26 AM 4092 (0x0FFC) Running single-call scan of updates. WUAHandler 3/29/2012 5:36:26 AM 4092 (0x0FFC) Async searching of updates using WUAgent started. WUAHandler 3/29/2012 5:36:26 AM 4092 (0x0FFC) Installation progress of update (1) in percent: 0 Total Percent: 0 WUAHandler 3/29/2012 5:44:02 AM 356 (0x0164) Installation progress of update (1) in percent: 0 Total Percent: 0 WUAHandler 3/29/2012 5:44:02 AM 356 (0x0164) Installation progress of update (1) in percent: 100 Total Percent: 50 WUAHandler 3/29/2012 5:44:02 AM 396 (0x018C) Update 1 (15b8ae3b-e200-47fe-afc1-45eedee16d2c) finished installing (0x00000000), Reboot Required? No WUAHandler 3/29/2012 5:44:02 AM 396 (0x018C) Installation progress of update (2) in percent: 0 Total Percent: 50 WUAHandler 3/29/2012 5:44:02 AM 396 (0x018C) Installation progress of update (2) in percent: 0 Total Percent: 50 WUAHandler 3/29/2012 5:44:02 AM 396 (0x018C) Installation progress of update (2) in percent: 100 Total Percent: 100 WUAHandler 3/29/2012 5:44:02 AM 1308 (0x051C) Installation progress of update (2) in percent: 100 Total Percent: 100 WUAHandler 3/29/2012 5:44:02 AM 3684 (0x0E64) Update 2 (9bca5a73-cc9a-4f6b-a5b4-fd7cb4b3e122) finished installing (0x00000000), Reboot Required? No WUAHandler 3/29/2012 5:44:02 AM 3684 (0x0E64) Async install completed. WUAHandler 3/29/2012 5:44:02 AM 3800 (0x0ED8) Installation job hresult code: 0x00000000. WUAHandler 3/29/2012 5:44:02 AM 3700 (0x0E74) Installation of updates completed. WUAHandler 3/29/2012 5:44:02 AM 3700 (0x0E74) Async searching completed. WUAHandler 3/29/2012 10:15:40 AM 984 (0x03D8) OnSearchComplete - Failed to end search job. Error = 0x8024001e. WUAHandler 3/29/2012 10:15:40 AM 3824 (0x0EF0) Scan failed with error = 0x8024001e. WUAHandler 3/29/2012 10:15:40 AM 3824 (0x0EF0) Its a WSUS Update Source type ({6C725974-EE51-4F35-B18F-92E26BD9C225}), adding it. WUAHandler 3/29/2012 10:18:05 AM 4044 (0x0FCC) WSUS update source already exists, checking whether correct server is set. WUAHandler 3/29/2012 10:18:05 AM 4044 (0x0FCC) Existing WUA Managed server was already set (http://SERVER:8530), skipping Group Policy registration. WUAHandler 3/29/2012 10:18:05 AM 4044 (0x0FCC) Added Update Source ({6C725974-EE51-4F35-B18F-92E26BD9C225}) of content type: 2 WUAHandler 3/29/2012 10:18:05 AM 4044 (0x0FCC) No proxy information available, not setting proxy. WUAHandler 3/29/2012 10:18:05 AM 4044 (0x0FCC) Running single-call scan of updates. WUAHandler 3/29/2012 10:18:05 AM 4044 (0x0FCC) Async searching of updates using WUAgent started. WUAHandler 3/29/2012 10:18:10 AM 4044 (0x0FCC) Its a WSUS Update Source type ({6C725974-EE51-4F35-B18F-92E26BD9C225}), adding it. WUAHandler 3/29/2012 10:36:29 AM 2408 (0x0968) WSUS update source already exists, checking whether correct server is set. WUAHandler 3/29/2012 10:36:29 AM 2408 (0x0968) Existing WUA Managed server was already set (http://SERVER:8530), skipping Group Policy registration. WUAHandler 3/29/2012 10:36:29 AM 2408 (0x0968) Added Update Source ({6C725974-EE51-4F35-B18F-92E26BD9C225}) of content type: 2 WUAHandler 3/29/2012 10:36:29 AM 2408 (0x0968) No proxy information available, not setting proxy. WUAHandler 3/29/2012 10:36:30 AM 2408 (0x0968) Running single-call scan of updates. WUAHandler 3/29/2012 10:36:30 AM 2408 (0x0968) Async searching of updates using WUAgent started. WUAHandler 3/29/2012 10:36:34 AM 2408 (0x0968)