-
Posts
9256 -
Joined
-
Last visited
-
Days Won
371
Everything posted by anyweb
-

Prerequsites for SCCM 2012 R2 and SCCM 1606
anyweb replied to charris211's topic in Configuration Manager 2012
check your pm. -
Introduction Windows 365 User Experience Sync (UES) is a cloud‑native capability designed to give users a seamless, consistent, and personalised Windows experience across Windows 365 Cloud PCs and Windows 365 Cloud Apps. Without UES in place on Frontline Shared devices, Windows personalisation, user settings, application settings, and application data are retained on logoff/logon which can be frustrating for end users who need to reauthenticate or reconfigure to set up their device how they need to use it, only to have to do this each time they log on to the Cloud PC. Instead of relying on traditional profile‑management tools, UES automatically preserves the settings every time the user signs in. Microsoft manages the UES infrastructure, vastly decreasing the implementation complexity and cost compared to other profile based solutions. At the core of User Experience Sync is dedicated, cloud‑hosted user storage that follows each user from session to session. When a user signs in, their individual storage is dynamically attached, providing immediate access to their personal settings and app data. As the user signs out, the profile is detached and stored securely ready for the next session. In this blog post myself and fellow MVP buddy Niall Brady overview this new feature and show you how you can set this up for Windows 365 Frontline Shared Cloud PCs and Cloud Apps. Myself and Niall were part of the private preview for the solution and were heavily involved at that stage. The feature was made generally available in November and we will be interested to see that changes have been made to the solution, based on our feedback, in that time. Requirements The following requirements are needed at present. Windows 365 Frontline license Access to required Windows 365 and Microsoft 365 endpoints Intune management permissions Setting it up When it comes to setting up the Windows 365 User Experience Sync, the enablement of the feature is achieved in the configuration of the Frontline Shared Provisioning Policy. This can be done when creating a new policy, or an existing policy can be modified to add or remove the feature. Let’s focus initially on creating a policy and enabling the UES solution. In the Intune admin center, navigate to Devices | Device onboarding | Windows 365. Select Provisioning policies from the menu and choose Create Policy. When creating the provisioning policy, ensure that you select Frontline as the License type and enable Shared from the Frontline type choice. For Experience, you can choose either Access a full Cloud PC desktop, or Access only apps which run in the cloud, since both Cloud PCs and Cloud Apps support UES. The Configuration section of the provisioning policy wizard is where we configure the UES solution. We have two choices to make; Enable user experience sync and User Storage Size. Check Enable user experience sync to turn on the feature. Managing the UES storage For the User Storage Size, Microsoft offer a predefined pool of user storage that comes included with your Frontline licence. The total available storage is determined by the Cloud PC’s OS disk size and is scaled based on the number of Cloud PCs assigned within the policy. For our Frontline model, we have a Cloud PC Frontline 2vCPU/8GB/128GB licence and 1 Frontline device, therefore the amount of pooled storage available to us is 128 x 1 or 128GB. The User Storage Size allows us to assign up to 64GB per user as you can see from the drop-down menu below. Be aware of the pooled disk space limitations when assigning the the User Storage Size. Exceeded limits: When pooled storage runs out, new users can still sign in, but they receive a temporary profile and cannot create their own user storage. Users who already have allocated storage can continue signing in with their full personalised experience. Exceeded tolerance period: If the pooled storage limit remains exceeded, a 7‑day tolerance window begins. After this period ends, the system automatically removes individual user storage starting with the one that has the oldest “last attach” timestamp. Once the total storage usage drops back below the limit, the tolerance period resets and won’t start again until storage is exceeded in the future. You can manage the user storage by selecting going to Provisioning policies and clicking your newly created policy. Next, select User storage and you will be presented with a view of the Storage information which includes the Total, Available and Used data. Since we are currently provisioning the devices, nothing will be used. Some recommendations to assist with UES are to: Enable OneDrive redirection Manage Edge for cache and temporary data retention Deploy Storage Sense to clean up temporary files, delete downloads and cloud backed files (OneDrive) You can set up alert monitoring for the user storage. This is achieved by navigating to Tenant administration | Alerts | Alert Rules and clicking Frontline Cloud PC User Experience Sync Storage Limits. In the System rule view, you can set to alert when used space is Greater then or equal to a certain percentage. You can set a Severity for the alert, if the Status of the rule is On or Off, whether to have a Portal pop-up Notification and if someone should receive an Email alert. You can enter multiple recipients for the email. What’s Included and Exclude from User Experience Sync (UES) The following is included in the UES solution: User storage includes all data from C:\Users%username%, such as: User settings and application data Registry files, (NTUSER.dat and USRCLASS.dat) Personal files and folders What’s not included: Nonroamable application data AppData\Local\Packages*\AC AppData\Local\Packages*\SystemAppData AppData\Local\Packages*\LocalCache AppData\Local\Packages*\TempState AppData\Local\Packages*\AppDat Nonroamable identity data AppData\Local\Packages\Microsoft.AAD.BrokerPlugin_cw5n1h2txyewy AppData\Local\Packages\Microsoft.Windows.CloudExperienceHost_cw5n1h2txyewy AppData\Local\Microsoft\TokenBroker AppData\Local\Microsoft\OneAuth AppData\Local\Microsoft\IdentityCache The UES Experience When a user signs on for the first time to a Cloud PC or Cloud App with UES enabled, the personal storage will be created and attached to the session and capture of settings will be automatically enabled and redirected to the storage. On the next login, the UES will be reattached and any saved configuration loaded. Do bear in mind that UES does not roam or persist user installed applications, only settings and preferences are captured. On a Frontline Shared UES enabled device, we are loading the store app Sticky Notes for the first time. We are requested to authenticate to use the app on first run. After authenticating, we can create content in the app with the expectation that this is stored within the UES storage and retained for our next session. If we do not have Frontline Shared UES enabled, then the end user would need to re-authenticate with the Sticky Notes app on each logon to bring up their personalised notes. Installing apps Another thing to note is if the user downloads and installs an app, let’s say Firefox. While this works during the session that the user is logged on to, once they logoff/logon any remnant of that (shortcut, etc) are gone. If you want apps to persist then install them in the base image (custom image). Filling up the storage and reporting on usage One of the areas we fed back on during the private preview, was the lack of warning or information for the end user when the UES becomes full. In the screenshot below, for example, the user has downloaded too many ISO files and filled up their allocation of 16GB. The only message the end user gets is Couldn’t download – Disk full. This isn’t informative enough for the end user in our opinion. Improvements to the experience should be forthcoming and we hope that this is one which is being taken into account by Microsoft. When it comes to usage, the admin can take a look at what allocation of their Total amount is in use in the User storage section of the Provisioning Policy. Remember from earlier, you need to click Provisioning policies and select your policy. Select User storage to view. We can now see that 16GB from the Total of 128GB has been allocated to a user. These stats do not give us a real time view of what a user has actually used from that 16GB allocation. This is another area that we fed back on that we feel needs improvement. If we have set up alerts and total usage across all UES compromises the percentage stated in the rule, then the recipient of the alert rule will receive an email with details of the provisioning policy where the usage is a concern. In Tenant administration | Alerts admins will be alerted with the relevant Severity and with a pop-up, if enabled. Amending an Existing Provisioning Policy To be able to amend an existing provisioning policy to add or remove UES, you first need to remove the the current group assignment from the policy. Navigate back to Provisioning policies and select your Frontline shared policy. Choose Properties. Scroll down to the Assignments and click Edit. Delete the assignment. Click Remove to confirm the removal of the assignment. Click through the wizard to Update the policy. Now Edit the Configuration section of the policy. This is our UES policy with UES enabled. We can, therefore, remove UES by deselecting the Enable user experience sync checkbox. If this was a policy which never utilised UES, we could go into here and select to use and set a corresponding User Storage Size. Once amended, Update the policy and head back to Assignments and Edit. Reassign the policy and enter the relevant Cloud PC size, select your Frontline subscription and Assignment details. The Frontline shared devices will then be in a Provisioning state as the amended configuration is laid down. Read more User Experience Sync for Windows 365 Frontline in shared mode – https://learn.microsoft.com/en-us/windows-365/enterprise/frontline-user-experience-sync Troubleshoot User Experience Sync for Windows 365 Frontline in shared mode – https://learn.microsoft.com/en-us/troubleshoot/windows-365/troubleshoot-user-experience-sync Summary Windows 365 User Experience Sync is a welcome feature for Frontline Shared devices which has been on the wish list for some time now. It is very simple to get up and running, without all the complexity of other solutions and provides instant access to storage of settings and application data. Microsoft is taking into the account the feedback it received during the private preview and we should see some feature changes happening very shortly to improve the end user experience. We look forward to seeing how this new feature matures and develops over time and we’ll blog about the feature improvements as they are released.
-
can you show a screenshot of your task sequence please, and secondly, share your smsts.log
-
Introduction I started my day as always and launched the Windows app, I clicked my Cloud PC, entered my credentials and after a short delay I got an error shown below. The error shown above was “something went wrong” with a very not useful error code, -895352830. I tried this on multiple tenants with the same error code being generated. I asked Copilot what this meant and got the following details This code corresponds to an AADSTS65002 token/permission issue during authentication. Microsoft documentation shows the same error pattern: Error: -895352830 (0xCAA20002) — occurs when a Microsoft first‑party app is missing required preauthorized API consent, causing token broker authentication to fail. [learn.microsoft.com] This means the Windows App cannot obtain a valid authentication token due to a Microsoft Entra (Azure AD) app permission issue, often triggered by: Broken SSO token broker A corrupted local identity cache A bad Windows Update interfering with Windows App authentication The last point above (a bad Windows Update) is indeed the cause. More details below: January 2026 security patches (notably KB5074109) are currently breaking logins in the Windows App and Remote Desktop authentication: Microsoft confirms widespread credential failures after the January 2026 update, impacting Windows App sign-ins for Azure Virtual Desktop & Windows 365. [theregister.com] Users report the app immediately fails with authentication errors after pressing Connect. [theregister.com] Removing KB5074109 restores normal Windows App login functionality (confirmed by multiple users on Jan 15–16, 2026). [learn.microsoft.com] According to theregister.com The upshot is that connecting to Windows 365 or Azure Virtual Desktop from the Windows App could be borked due to credential problems. Microsoft posted: “Investigation and debugging are ongoing, with coordination between Azure Virtual Desktop and Windows Update teams.” The problem is widespread and appears to affect every supported version of Windows, from Windows 10 Enterprise LTSC 2016, right up to Windows 11 25H2. Windows Servers 2019 to 2025 are also affected. Great, so now what ? Suggested workarounds are that you can connect to your Cloud PC using the soon to be unsupported Remote Desktop Client Agent available from here. Windows 64-bit Windows 32-bit Windows ARM64 I tried it, but it too failed to connect. Next, I tried via a web-browser, but that also didn’t work. The Cloud PC I’m trying to connect to is protected using the new CKIO feature and the web browser version does not support that. Verifying the problem A quick look in Intune, revealed that indeed the problematic CU was indeed applied to my Cloud PC’s and the PC I was making the connection from (Windows 11 25H2 ARMx64). Here’s a sample. As you can see below Below you can see the CU details… 10.0.26200.7623 10.0.26100.7623 https://support.microsoft.com/en-us/topic/january-13-2026-kb5074109-os-builds-26200-7623-and-26100-7623-3ec427dd-6fc4-4c32-a471-83504dd081cb and within that you can see the known issues including the suggested workaround, which is to install KB5077744. As it’s so new this update is not even available in Windows Autopatch so you cannot currently use expedite updates policy to deploy this. KB5077744 is an Out‑of‑Band (OOB) update for Windows 11 25H2/24H2. It is not delivered through Windows Update automatically and must be manually downloaded and installed from the Microsoft Update Catalog. You must use the Microsoft Update Catalog to obtain the standalone package (MSU). [support.mi…rosoft.com] The fix As KB5077744 is only currently available (at the time of writing, 2026/01/19) via Microsoft’s Catalog, you must deploy it (the msu) from Intune by wrapping it as a Win32 app. Because Intune does not directly deploy .MSU updates as updates, the supported method is to wrap the MSU as a Win32 app and deploy it to your affected clients. Go to Microsoft Update Catalog and search for kb5077744. Download the update that is applicable to your Windows OS version. Be aware that the file size is big, my download was approx 3.6GB. Place the downloaded msu file and this Powershell script in a folder called KB5077744. here’s the contents of the Powershell script, modify it so that it has the exact file name of the msu file you downloaded otherwise it won’t install. Save the file as Install_KB5077744.ps1. wusa.exe windows11.0-kb5077744-x64_fb63f62e4846b81b064c3515d7aff46c9d6d50c8.msu /quiet /forcerestart exit $LASTEXITCODE Note: If you want to control reboot notifications and other options, package this instead using Powershell Application Deployment Toolkit and customize those options as necessary. Using Intunewinapputil.exe wrap the package as a Win32 app. Then add the Win32 app use this command line powershell.exe -ExecutionPolicy Bypass -File Install_KB5077744.ps1 and the following detection script. $sysinfo = systeminfo.exe $result = $sysinfo -match "KB5077744" if ($result) { Write-Output "Found KB5077744" exit 0 } else { Write-Output "KB5077744 not found" exit 1 } Finally, after deploying the update to your affected clients, and waiting for it to install and restart, you’ll be able to connect again. Phew. What a relief. The new Windows build number is highlighted below. 10.0.26200.7627 from a Windows 11 25H2 Cloud PC. and here you can see it successfully installed on the client and of course, via Intune, however Intune still has not yet updated the build number of the CPC yet in the Win32 app install status. Update It seems you need to patch the host PC making the connection to the Cloud PC also, if it’s running x64 Windows and has the .7623 patch level (January update). Strangely I didn’t need to patch the ARM PC at all even though it had the .7623 patch level. Related reading Reddit: https://www.reddit.com/r/AzureVirtualDesktop/comments/1qc3g1x/comment/nzmy4fv/ theregister: https://www.theregister.com/2026/01/15/windows_app_credential_failures/ KB5077744 – https://support.microsoft.com/en-us/topic/january-17-2026-kb5077744-os-builds-26200-7627-and-26100-7627-out-of-band-27015658-9686-4467-ab5f-d713b617e3e4#id0ejbd=catalog
-

Random Issue Plaguing OSD Deployments: Exit Code 16389
anyweb replied to BzowK's topic in Configuration Manager 2012
based on what a previous guy said " I guess you could create a powershell script to check for msiexec process doing this and if so 'wait' until it's done, before installing the app, have you tried that ? here's some untested code that you could use as a wrapper for each app, maybe it will help [CmdletBinding()] param( [int]$TimeoutSeconds = 0, # 0 = wait indefinitely [int]$PollIntervalSeconds = 3, # how often to poll [switch]$Quiet # suppress non-verbose status messages ) function Write-Info { param([string]$Message) if (-not $Quiet) { Write-Host $Message } } function Test-MsiInProgressRegistry { # Windows Installer sets this key while an MSI is actively installing $keyPath = 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\InProgress' try { if (Test-Path $keyPath) { # Some builds create the key with values; treat existence as "busy" $item = Get-Item $keyPath -ErrorAction SilentlyContinue $props = $null try { $props = Get-ItemProperty $keyPath -ErrorAction SilentlyContinue } catch {} return $true } } catch {} return $false } function Get-MsiexecProcesses { # Fetch msiexec.exe along with command lines (CIM needed for CommandLine) try { return Get-CimInstance Win32_Process -Filter "Name='msiexec.exe'" -ErrorAction SilentlyContinue } catch { # Fallback to Get-Process (no command line available) try { return (Get-Process -Name msiexec -ErrorAction SilentlyContinue | ForEach-Object { [pscustomobject]@{ ProcessId = $_.Id Name = $_.ProcessName CommandLine = $null } }) } catch { return @() } } } function Test-MsiexecDoingWork { # Heuristic: if command line indicates an actual MSI operation (install/repair/uninstall/update) param( [Parameter(Mandatory)] $Proc ) $cl = $Proc.CommandLine if ([string]::IsNullOrWhiteSpace($cl)) { # If we lack command line, be conservative: any msiexec process could be active return $true } # Common operation switches for msiexec: # /i, /x, /f*, /update, /uninstall, /package, /qn, /qb, /passive often accompany installs $patterns = @( '\s/([ix])\b', # /i install, /x uninstall '\s/f[a-z]*\b', # /f, /fa, /fu, etc. (repair) '\s/update\b', # patch/update '\s/uninstall\b', '\s/package\b', '\.msi(\s|$)', # explicit MSI file '\.msp(\s|$)' # patch file ) foreach ($p in $patterns) { if ($cl -match $p) { return $true } } # Sometimes msiexec runs as the service side without clear switches; if in doubt, treat as busy return $true } function Test-MsiBusy { # Returns $true if Windows Installer is likely busy $procs = @(Get-MsiexecProcesses) if ($procs.Count -gt 0) { foreach ($p in $procs) { if (Test-MsiexecDoingWork -Proc $p) { return $true } } } if (Test-MsiInProgressRegistry) { return $true } return $false } # ---------------------------- # Main wait loop # ---------------------------- $start = Get-Date if ($TimeoutSeconds -gt 0) { Write-Info "Waiting for Windows Installer (msiexec) to finish (timeout: $TimeoutSeconds s, poll: $PollIntervalSeconds s)..." } else { Write-Info "Waiting for Windows Installer (msiexec) to finish (no timeout, poll: $PollIntervalSeconds s)..." } # If already idle, return immediately if (-not (Test-MsiBusy)) { Write-Info "Windows Installer appears idle." return } # Otherwise, poll until idle or timeout while (Test-MsiBusy) { if ($TimeoutSeconds -gt 0) { $elapsed = (New-TimeSpan -Start $start -End (Get-Date)).TotalSeconds if ($elapsed -ge $TimeoutSeconds) { Write-Warning "Timed out waiting for Windows Installer after $([int]$elapsed) seconds." exit 1 } if (-not $Quiet) { $remaining = [math]::Max([int]($TimeoutSeconds - $elapsed), 0) Write-Host ("MSI busy... ({0}s remaining). Next check in {1}s." -f $remaining, $PollIntervalSeconds) } } else { if (-not $Quiet) { Write-Host "MSI busy... next check in $PollIntervalSeconds s." } } Start-Sleep -Seconds $PollIntervalSeconds } Write-Info "Windows Installer is now idle." -

Prerequsites for SCCM 2012 R2 and SCCM 1606
anyweb replied to charris211's topic in Configuration Manager 2012
it's no longer supported so i doubt it, i'll share a link with you -
Introduction While Windows 365 Cloud PCs deploy robust perimeter defences—encrypted transmission channels and multi-factor authentication that thwart network-level attacks—a critical vulnerability persists at the endpoint itself. Malicious software operating on local devices, particularly keystroke capture tools, can intercept sensitive information before it ever reaches the cloud environment. These endpoint-resident threats create regulatory exposure and potential financial damage that traditional cloud security measures cannot address. Windows Cloud IO Protection closes this gap by introducing a kernel-level driver and system-level encryption that sends keystrokes directly to the Cloud PC, bypassing OS layers vulnerable to malware. When enabled on a Cloud PC it enforces a strict trust model: Only verified physical endpoints can connect. Endpoints must have the Windows Cloud IO Protect MSI installed. If the MSI is missing, the session is blocked and an error is displayed. This ensures a secure, uncompromised input channel between the Windows client and the Cloud PC. In this blog post myself and fellow MVP buddy Paul Winstanley overview this new feature and show you how you can set this up for Windows 365 Cloud PCs. Requirements The following requirements are needed at present. The feature is public preview and could change as this becomes Generally Available: Host physical Windows 11 devices Devices must have TPM 2.0 Host devices must have the Windows Cloud IO Protect agent installed Download the Windows x64 release Download the Windows ARM 64 release Windows App running 2.0.704.0 or later The following is not currently supported: macOS iOS Android Windows 365 Link Using the Web client Setting it up When it comes to setting up the Windows Cloud Keyboard Input Protection feature, Microsoft has an interesting approach in that its documentation currently only supports using group policy to achieve this. The setting Windows Components > Remote Desktop Services > Remote Desktop Session Host > Azure Virtual Desktop > Enable Keyboard Input Protection needs to be enabled. During our testing phase, we were fortunate enough to be part of the private preview release, we had to set the following registry keys for Windows 365 devices, with just the former key being required for AVD devices: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services\ DWORD - fWCIOKeyboardInputProtection Value - 1 HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server\RdpCloudStackSettings DWORD - SecureInputProtection.KeyboardProtection.IsEnabled Value - 1 To assist with this on your Entra only Cloud PCs, we have created an Intune proactive remediation script to set the values, if they are not present on your Windows 365 devices. These scripts need to be targeted to the Cloud PCs, and not the host devices. You can download the detection and remediation scripts from GitHub. Adding the Proactive Remediation script for Keyboard Protection In the Intune admin center, navigate to Devices | By platform | Windows | Manage devices | Scripts and remediations. Ensure you are in the Remediation view and click Create. Enter a Name for the custom script and add an optional Description. Click Next when done. Click the browse icon for the Detection script file and upload the Detect-KeyboardProtection.ps1 downloaded from GitHub. Repeat the process for the Remediation script file by uploading the Remediate-KeyboardProtection.ps1 script. Leave all other options as default and click Next. At the Assignments section, choose the group of devices that you wish to targeted. You can adjust the schedule for the execution of the remediation by clicking the Daily link under Schedule. For example, for our testing we have set the remediation to run Hourly. Click Apply when you have made your adjustment. The new schedule will be reflected accordingly in the Intune console. When you have completed the proactive remediation wizard, you will see the new remediation listed and with a Status of Active. When the script has executed against devices, the Detection status will be reported back to Intune with statuses of Without issues, With issues, Failed or Not applicable. Any Remediation status data will also be reported where applicable. Installing the Windows Cloud Input Protect MSI Agent Referring back to the Microsoft documentation, the MSI install is documented using a manual method of installation the application, and this would require local admin rights to achieve this. Instead, we can push the Windows Cloud Input Protect MSI via Microsoft Intune to an Intune managed host device. We can configure the application as a Win32 app and, therefore, we need to use the Microsoft Win32 Content Prep Tool, which you download from https://github.com/microsoft/Microsoft-Win32-Content-Prep-Tool, to convert the app into the .intunewin format. Here is a blog written back in 2019 on how to use the Content Prep Tool https://sccmentor.com/2019/02/17/keep-it-simple-with-intune-4-deploying-a-win32-app/ We can package the MSI into the required .intunewin format with three simple switches: -c – this points the tool to the source folder containing the binaries -s – this points the tool to the setup file used to execute the application -o – this tells the tool where to output the .intunewin to Once the tool is run, it quickly creates the .intunewin file for the Windows Cloud Input Protect MSI. We can now take this file and import it into Intune when we create the Win32 app. Navigate to Apps | Platform | Windows, in the Intune admin center. Click Create. From the App type drop-down, select Windows app (Win 32) and then choose Select. You will now be navigating through the Add App wizard. Start by clicking Select app package file. Click the browse icon and locate the .intunewin file that you created. Click OK to upload the file. Details will be automatically added to the App information fields. The only mandatory field you will need to complete is the Publisher field. Feel free to add any further information you require. Click Next when done. In the Program section of the wizard, further details will be automatically added, such as Install command and Uninstall command. We will use these default values for our application. Click Next to continue. In the Requirements section, you can be selective on the specific requirements for the installation of the app. We have ensured that Yes. Specify the systems the app can be installed on is selected and we have chosen Install on x64 systems as we downloaded the x64 release of the MSI. You must also select a Minimum operating system level for the install. Click Next when you have completed this section. For the Detection rules, we have kept this simple and chosen Manually configure detection rules from the Rules format drop-down and chosen the MSI type, which automatically uses the MSI ID for the application. Finally, a reminder that when targeting the Windows Cloud Input Protect MSI agent, we are targeting Windows 365 host devices and not the Cloud PCs themselves. When the Windows Cloud Input Protect MSI agent installs, you will see an entry for the Windows Cloud IO Protection driver in Program and Features on your host device. and, hopefully, this is reflected in the Intune admin center in the apps Overview section. Connecting from a host device which is not running the Windows Cloud Input Protect MSI agent At present, there is no visual indication to let you know if the Cloud PC is running with keyboard protection enabled, and this was one of the feed back areas in the private preview. It is coming and we should expect something fairly soon. When you attempt to connect from a device which is not running the agent, you will get the following error dialog box. and Windows App will report similar. We expect to see something similar, like the AI-enabled heading on a device which has the AI features enabled. Fingers crossed that this arrives soon. Connecting from a non supported device platform can produce different error messages that are less intuitive. For example, the screenshot below shows the error when connecting from the Windows App on an Android device. Hopefully, support will be extended to other device platforms over time, and error messages updated to reflect the connection issue. Read more Keyboard Input Protection for Windows 365 and Azure Virtual Desktop now in preview – https://techcommunity.microsoft.com/blog/windows-itpro-blog/keyboard-input-protection-for-windows-365-and-azure-virtual-desktop-now-in-previ/4468102 Windows Cloud IO Protection – https://learn.microsoft.com/en-us/windows-365/enterprise/windows-cloud-input-protection Summary Windows Cloud IO Protection is a powerful security feature that ensures keystrokes are encrypted and sent directly to the Cloud PC, bypassing OS layers vulnerable to malware. By requiring trusted endpoints with the protection agent installed, it creates a secure, uncompromised input channel that blocks keyloggers and prevents data leaks. Microsoft is taking into the account the feedback it received during the private preview and we should see some feature changes happening very shortly to improve the end user experience. Beyond this, we hope that support is adopted for all device platforms, so that this security feature becomes OS agnostic. We look forward to seeing how this new feature matures and develops before being released to production.
-
Introduction Microsoft have invested a lot of time, effort and money on adding AI abilities to core parts of the Windows Operating System and the apps that run on it, for example Office 365 apps or dedicated AI apps such as Microsoft 365 Copilot. Myself and my good friend Paul Winstanley took a look at a new feature to add select AI features to Windows 365 Cloud PC’s and share our thoughts below. Windows 365 AI-enabled Cloud PCs run in Microsoft’s Cloud and stream AI-powered Windows to any device and platform. This allows you to use select AI features that would traditionally be found on physical NPU powered Copilot+ PC’s. Those select AI features are: Improved Windows search Click to Do You can test these AI features on any device using your Cloud PC for example, below you can see an AI-enabled Cloud PC available from an Android powered phone. Note: In the screenshots below from our Android phones, the AI-enabled Cloud PC has an AI-enabled label in the top left corner. But first, let’s take a look at what you need in order to set this up. Requirements The requirements below will most likely change as this becomes Generally Available, but to test it right now in this Frontier release you’ll need to do the following: The end user must be registered in the Windows Insider program The Cloud PC must be in the Windows Insider Beta channel Enable Data diagnostics in your settings Have a Cloud PC that supports AI abilities (8vCPU, 32GB ram, 256GB HDD) The Cloud PC must be in a supported location Setting it up To set it up make sure you’ve enabled data diagnostics in your Windows Privacy settings, as shown here. Set the Send optional diagnostics data to On. Next, enroll into Windows Insider Program and select the Beta Channel (Recommended). Once done you’ll most likely have to restart the CPC, so go ahead and do that. Next, you’ll need to configure a policy (targeted to users) which enables the feature for Cloud PC’s that meet the minimum requirements. To do that select the Windows 365 node in Intune, click Settings and select Create to create the policy. Select Cloud PC configurations (preview) from the options presented. In the Configuration settings part of the wizard, select Enable from the drop down menu to enable AI features. and on the Assignments screen, select a previously created Entra Id group with users that will be using this new ability. Once done, make sure one or more users are in that group and the policy should flow to the CPC’s. Exploring the new AI abilities The first thing you’ll most likely notice is that your AI Enabled Cloud PC’s are now clearly labelled with an AI-enabled label in the Windows app. After connecting to that Cloud PC, you’ll notice the search icon looks different. AI-enabled Cloud PCs are marked by a magnifying glass with a sparkle icon within the search box on the taskbar. Those of you who already have physical Copilot + PC’s will already be familiar with this new search icon. The new AI search abilities are supposed to be better than built-in traditional search, so we put it to the test. We decided to start with by simply searching for a word via the search feature in Windows File Explorer on the users OneDrive. We performed the same search on the AI-enabled CPC as well as on a regular non-AI powered physical device. The AI search results are on the left, and the traditional search results on the right. Look at the difference, 37 hits versus 10, not bad at all. Lets try another search. This time again, more results from the AI search versus traditional search. Click to do Microsoft Click to do is a feature on all Copilot+ PC’s and Windows 365 AI-enabled Cloud PC’s. To use it simply search for it in the start menu and click the app. Once started, you can browse websites with pictures of text (for example) and press the Windows key + mouse click anywhere in the website. This can give you options to do things with what it sees, such as copy text within an image to paste into your favorite text editor, Depending on what you click on you get more or less options, such as below when clicking on the image of a blue CRT. Cool! Changes in Intune When using Windows 365 AI-enabled Cloud PC’s there are some additional things that you can see in the Intune portal to reveal the finer details. There’s a report here to show AI-enabled CPC’s and what (if anything) is wrong with them. To find it select Reports, and select Cloud PC overview. Select the AI-enabled Cloud PC report, and you can then click through the Status column for any Cloud PC that has reported data up to Intune. Once you’ve fixed the issues reported, which in our case we provisioned the Cloud PC in a location that was not yet supported for AI-enabled abilities, you’ll see a new status of Ready to use. You can also see a new status in Cloud PC’s overview, called AI-enabled, which will report Yes or No. Read more AI-enabled Cloud PCs – https://learn.microsoft.com/en-us/windows-365/enterprise/ai-enabled-cloud-pcs Experience next-gen productivity with Windows 365 AI-enabled Cloud PCs – https://techcommunity.microsoft.com/blog/windows-itpro-blog/experience-next-gen-productivity-with-windows-365-ai-enabled-cloud-pcs/4467875 Experience next-gen productivity with Windows 365 AI-enabled Cloud PCs – https://youtu.be/CvL8UXCYzDk Using Microsoft Click-To-Do https://support.microsoft.com/en-us/windows/click-to-do-do-more-with-what-s-on-your-screen-6848b7d5-7fb0-4c43-b08a-443d6d3f5955 Summary This new feature via the Microsoft Frontier Program has a lot of cool potential! It’s great to see that Microsoft is continuing its investment in Windows 365 Cloud PC development, and adding key features like this brings the power of AI to all devices, whether they are Android, macOS, Windows. We look forward to seeing how this new feature matures and develops before being released to production.
-
can't you boot it into safe mode and then uninstall whatever driver/app that caused the problem ? as it's an old Windows 7 computer have you verified if the disk (hdd) is ok ??
-

Windows 11 DAO acces to old SQL Server 2005/2008 database
anyweb replied to cliv's question in SQL Server
can't you use Windows 10 LTSC then ? (Long Term Servicing Channel) ? -

Prerequsites for SCCM 2012 R2 and SCCM 1606
anyweb replied to charris211's topic in Configuration Manager 2012
hi Andy, drop me a message and i'll make them available to you cheers niall -
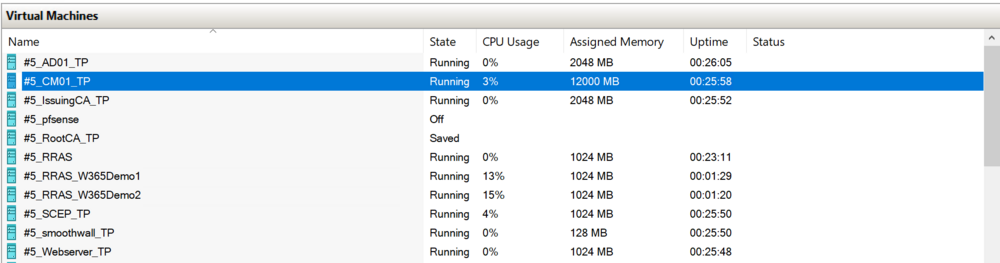
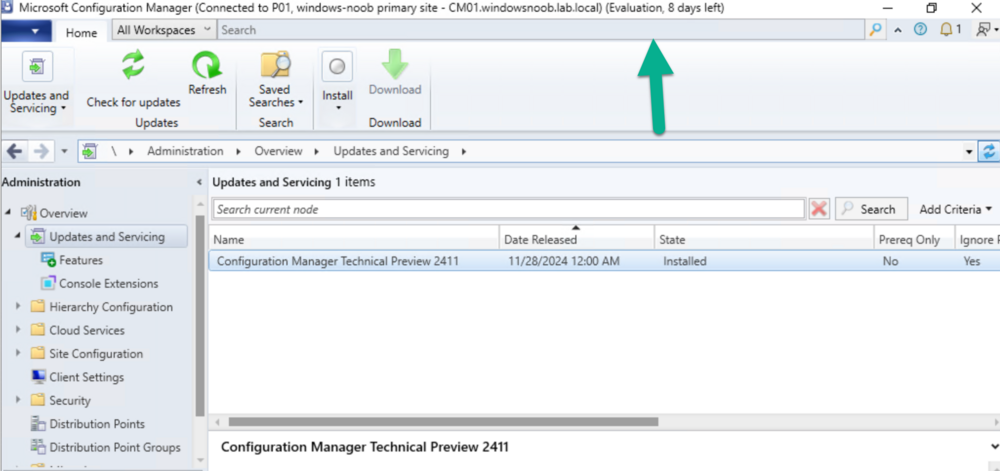
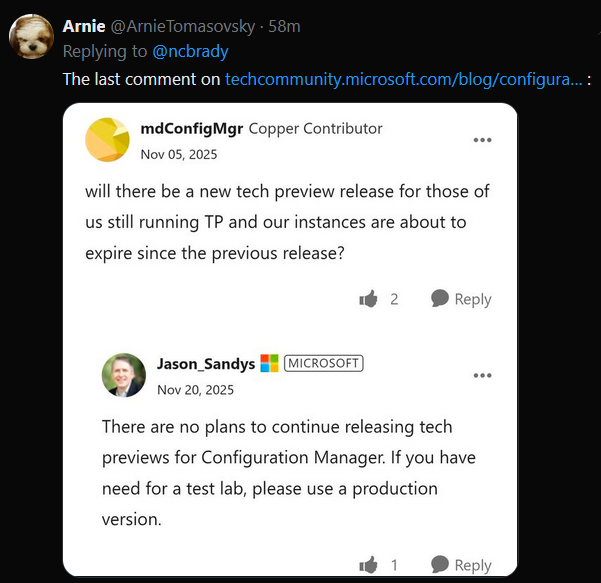
Introduction Microsoft recently released a blog post outlining predictable changes to the cadence of update releases for SCCM formally known as System Center Configuration Manager. The pinned tweet below had some interesting replies which you can read yourself here. The blog post didn’t even mention SCCM Technical Preview at all, but did TAG it as you can see here. What exactly is SCCM Technical Preview ? SCCM Technical Preview has been a test release of Configuration Manager that has been released very regularly (at first) and developed for years allowing SCCM admins to test the latest and greatest features coming to the product in advance, and allowing them to give valuable feedback to the product team, thereby shaping the mainstream product (Microsoft Configuration Manager) into what it is today. Technical Preview launched publicly in May 2015 and that journey started a decade long coding frenzy, where a large team of motivated developers led by none other than the great David James (djammmer) developed great features at an outstanding pace, at least until the last few years when things slowed down to a noticeable crawl about a year after David left in October 2021. Without the Technical Preview releases you could argue that the move to the Cloud would have taken a lot longer. Moving forward to today, the last documented release of SCCM Technical Preview was 2411 and you can still (at the time of writing) read documentation about that version here. I’ve personally tested and blogged about most of those releases over the last 10 years. Below you can see the timeline of upgrades I’ve done in my lab via the History feature within Configuration Manager. Note how it states Evaluation, 8 days left. And below are my many blog posts on the subject: Installation – How can I install System Center Configuration Manager and Endpoint Protection Technical Preview 4 Spot the difference, maintenance windows versus service windows, Microsoft is listening and fixing ! System Center Configuration Manager Technical Preview 1601 is now available ! System Center Configuration Manager Technical Preview 1602 is now available ! System Center Configuration Manager Technical Preview 1603 is now available ! System Center Configuration Manager Technical Preview 1604 is now available ! System Center Configuration Manager Technical Preview 1605 is now available ! System Center Configuration Manager Technical Preview 1606 is now available ! System Center Configuration Manager Technical Preview 1607 is now available ! System Center Configuration Manager Technical Preview 1608 is now available ! System Center Configuration Manager Technical Preview 1609 is now available ! System Center Configuration Manager Technical Preview 1610 is now available ! System Center Configuration Manager Technical Preview 1611 is now available ! System Center Configuration Manager Technical Preview 1612 is now available ! System Center Configuration Manager Technical Preview 1701 is now available ! What is the ContentLibraryCleanup tool and how can I use it ? System Center Configuration Manager Technical Preview 1702 is now available ! Video – Upgrading to System Center Configuration Manager 1703 Technical Preview System Center Configuration Manager Technical Preview 1704 is now available ! System Center Configuration Manager Technical Preview 1705 is now available ! System Center Configuration Manager Technical Preview 1706 is now available ! System Center Configuration Manager Technical Preview 1707 is now available ! System Center Configuration Manager Technical Preview 1708 is now available ! System Center Configuration Manager Technical Preview 1709 is now available ! System Center Configuration Manager Technical Preview 1710 is now available ! System Center Configuration Manager Technical Preview 1711 is now available ! System Center Configuration Manager Technical Preview 1712 is now available ! System Center Configuration Manager Technical Preview 1801 is now available ! Update 1802 for Configuration Manager Technical Preview available now Update 1803 for Configuration Manager Technical Preview available now ! System Center Configuration Manager Technical Preview 1804 released System Center Configuration Manager Technical Preview 1805 released System Center Configuration Manager Technical Preview 1806 released System Center Configuration Manager Technical Preview 1807 released System Center Configuration Manager Technical Preview 1808 released System Center Configuration Manager Technical Preview 1809 is out A quick look at System Center Configuration Manager Technical Preview version 1810 A quick look at System Center Configuration Manager Technical Preview version 1810.2 System Center Configuration Manager Technical Preview version 1901 is now available System Center Configuration Manager 1902 Technical Preview is available System Center Configuration Manager 1902.2 Technical Preview is now available System Center Configuration Manager 1903 is now available and it includes my uservoice ConfigMgr log files help you when you least expect it, oh and SCCM 1904 TP is out ! How can I use the new Community hub in SCCM Technical Preview 1904 SCCM Technical Preview version 1905 is available and this is a HUGE release ! SCCM Technical Preview version 1906 is available System Center Configuration Manager Technical Preview version 1907 is available now ! System Center Configuration Manager Technical Preview version 1908 is available now ! Make your task sequences go faster with the Run as high performance power plan How to configure keyboard layout in WinPE in SCCM How to select an index when importing an Upgrade package into SCCM System Center Configuration Manager Technical Preview version 1909 is released ! System Center Configuration Manager TP1910 is out ! Microsoft Endpoint Manager Configuration Manager technical preview version 1911 is released Microsoft Endpoint Manager Configuration Manager Technical Preview version 1912 released New BitLocker Management features in Microsoft Endpoint Manager Configuration Manager Technical Preview 2002 Microsoft Endpoint Manager Configuration Manager Technical Preview 2002.2 is out Microsoft Endpoint Manager TP 2003 is out Microsoft Endpoint Manager Technical Preview 2004 is out Microsoft Endpoint Manager Configuration Manager technical preview version 2005 is out Microsoft Endpoint Manager TP2006 is out Slides and recording from “New cloud features in Configuration Manager Technical Preview” A look at task sequence media support for cloud-based content Technical Preview 2007 is out ! Technical Preview 2007 Timeline improvements Cool new features in Technical Preview 2008 OSD via boot media and CMG, available in TP2009 New features in Configuration Manager Technical Preview 2010 Manage BitLocker policies and escrow recovery keys over a cloud management gateway (CMG) Required application deployments visible in Microsoft Endpoint Manager admin center Fixing One or more Azure AD app secrets used by Cloud Services will expire soon Improvements to BitLocker support via cloud management gateway Technical preview 2104 get BitLocker recovery keys for a tenant-attached device Creating a VMSS CMG and setting VM size with Technical Preview 2105 How to change the CMG (VMSS) size after it is deployed Use Windows Updates notifications instead of ConfigMgr client notifications in tp2105.2 Configuration Manager Technical Preview 2106 is out, and it’s huge !! Technical Preview 2108 is out ! Technical Preview 2109 is out, update your console manually Technical Preview 2201 – Tenant attach is now GA Technical Preview 2202 – delete collection references Enabling dark-mode in Configuration Manager 2203 Escrow BitLocker recovery password to the site during a task sequence in Configuration Manager 2203 Technical Preview 2204 is out, brings ADR organization, Admin service + dark mode improvements New video: First looks at Distribution point content migration in Configuration Manager 2207 First looks at Distribution point content migration Technical Preview 2208 is out, adds RBAC for tenant attached devices Technical Preview 2209 is out, adds improvements to search in the console and dark mode theme Quick tip: Free up space on your ConfigMgr server Technical Preview 2302 is out Technical Preview 2305 is out, should you upgrade ? yes A quick look at Technical Preview 2307 Technical Preview 2401 is out Technical Preview 2411 is out, upgrade now before your lab times out Who cares ? My trusty SCCM Technical Preview lab support is coming to an end, and currently there’s no sign that Microsoft will do anything about it. It has 8 days left of support and after that, if Microsoft doesn’t release an update for Technical Preview, then it will become unsupported and unusable. I’ve pinged some of the official product teams on Twitter, asking if SCCM Technical Preview is dead but so far, there is no response. If they do update or reply I’ll post it here. This IMHO is a crying shame as many dedicated SCCM admins like me have updated these labs for years, and now those very same labs are left to die by the very company that encouraged us to not only use them, but to provide ongoing feedback. My Technical Preview lab shown below, was used for things like setting up bitlocker management via Configuration Manager, Co-Management setup, Cloud Managed Gateway (CMG), hybrid management of Windows 365 Cloud PCs, tenant attach, OSD via CMG and most recently the integration of Microsoft Intune’s Cloud PKI & SCEP when I technically reviewed this great book from my friends Paul & David. But now the clock is ticking and soon I won’t be able to even use the console. Is this the end of Configuration Manager Technical Preview ? it certainly looks like it and based on this quote in their opening paragraph, I think the answer is yes. Microsoft Intune is the future of device management, and all new innovations will occur there. Update: No sooner than I posted this I got an reply on Twitter from Arnie, and here it is, confirmation from Jason Sandys @ Microsoft that Technical Preview is no more. RIP
-
cool but i found the issue comes back, please let me know how it goes for you, by the way are your users 'standard' users or local administrators ?
-

Slow App Deployment on Windows 365 During Initial Login
anyweb replied to PingPanda's topic in Windows 365
have you looked at the following, specifically the second link ? Application deployment in Windows 365: recommended practices | Microsoft Community Hub Use the Enrollment Status Page with Cloud PCs | Microsoft Learn @PingPanda -
Introduction Ever wished you could spin up a Cloud PC not just for your employees, but for contractors, partners, or even external collaborators? Good news—External Identity (preview) support in Entra ID now makes that possible. You can invite external users into your tenant and give them access to Cloud PCs, extending the same secure, managed experience your internal users already enjoy. Of course, there are a few strings attached. Prior to deploying out Cloud PCs to outside identities, you will need to be aware of a number of significant requirements and limitations so that everything runs smoothly. In this blog post, myself and my good friend Paul Winstanley took a look at what you need to be aware of and how to set up and access. Requirements The Cloud PC must be running Windows 11 Enterprise with the 2025-09 Cumulative Updates for Windows 11, version 24H2 (KB5065789) or later installed. The Cloud PC must be Entra only joined, hybrid is not supported. Single-sign on must be enabled in the provisioning policy. Connection to the Cloud PC must be via the Windows App or browser. Limitations User based Intune device configurations profiles will not be applied to the external users Cloud PC. Ensure you target the profiles to devices. Windows 365 Enterprise, Business, and Frontline are supported, Windows 365 Government is not. Cross-cloud users are not supported, i.e. you can’t invite users from Microsoft Azure Government or Microsoft Azure operated by 21Vianet. Be aware of the token limitations for external identities – https://learn.microsoft.com/en-us/entra/identity/conditional-access/concept-token-protection#known-limitations Authentication to on-premises resources with Kerberos or NTLM is not supported for external identities. Assigning the Windows 365 licence Assigning the licence should be a simple case of heading over to the Microsoft 365 admin center, navigating to Billing | Licenses and selecting the required Windows 365 subscription. When selected, we clicked Assign licenses and chose the guest user, in our case Niall’s guest account in Paul’s tenant. When finished we clicked Assign licenses. In our tenant, we received the following error message ‘Failed to assign license for Niall Brady: Cannot process request because a referenced item has an invalid usage location.’ You may not receive this error and not have to perform the fix. To fix this up for us, we went to the Entra admin center and clicked on Users. We located Niall’s guest account and clicked Edit properties. Under the Settings menu, we clicked the Usage location drop-down and selected a location for his account, then clicked Save. After a short period of time, we were able to assign a licence to Niall’s account with no issue. Provisioning the Cloud PC for the External Identity Back in the Intune admin center, under Devices | Device onboarding | Windows 365 | All Cloud PCs there should be a Not provisioned Cloud PC. It reports as Not provisioned as the user has not been assigned a provisioning policy. To resolve this we can either create a provisioning policy and assign this or we can use an existing policy, so long as we have single sign-on enabled and that the Cloud PC is running with 2025-09 Cumulative Updates for Windows 11, version 24H2 (KB5065789) or later. If using an existing policy, take a look at the assignment to ensure that Niall’s account is targeted. We decided to create a new provisioning policy using the new 25H2 release of Windows 11. We navigated to Devices | Device onboarding | Windows 365 | Provisioning policies in our tenant and clicked Create policy. As mentioned, ensure Use Microsoft Entra single sign-on is enabled and Microsoft Entra Join is selected for Join type as hybrid is not supported. We selected the Windows 11 Enterprise + Microsoft 365 Apps 25H2 gallery image to ensure that we met the O/S requirements. When assigning the policy, we targeted a group called Windows 365 External Identities. After completing the provisioning policy wizard, the policy was visible. Next, we simply added Niall’s guest account to the Windows 365 External Identities group. We navigated to Groups and searched for the group and added his account. Back in All Cloud PCs, a Cloud PC now reported a Status of Provisioning. After a period of time, the Cloud PC reported as Provisioned. Accessing the Cloud PC The Cloud PC can be accessed via the Windows App or web browser, however prior to attempting to access the following registry key needs to be created on the host device. Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsApp\Flights DWORD - EnableIdSignInUx Value - 0 There are slight variations to accessing via the app or the browser so let’s take a look at both. Also, thanks to our MVP friend Sune Thomsen for providing the details that steered us in the right direction to make this work! Windows App The user must be authenticated in the Windows App. They need to click their account profile picture on the top right of the application and click Sign in with another account. If the registry key has been entered, then the following Sign in window will be displayed. Note Sign-in options is available. This would not be displayed if the registry key is not present. Click Sign-in options. The next step is to click the Sign in to an organization option. and enter the domain of the organization hosting the Windows 365 Cloud PC. In our case, sccmsolutions.co.uk. Now, the guest account must authenticate in the tenant using their account credentials, and respond to any multi-factor authentication or other prompts. When authentication is complete, the user will be presented with their Cloud PC in the Windows app. The user is able to switch between organizations by clicking their account profile and selecting accordingly. Web Browser When navigating to windows365.microsoft.com, the user will authenticate with their account. Then in the top right hand corner of the web page, the user clicks their profile and then chooses Sign in with another account. Now, choose Use another account. The user will then have the Sign-in options available to select (if the reg key is present on the device). After selecting Sign-in options, choose Sign in to an organization. As with the Windows App, they enter the domain name of the organization hosting the Windows 365 Cloud PC. and authenticate with their user account. Finally, the user will be presented with the provisioned Cloud PC in the web browser. Using either Windows App or the web browser to log on to the Cloud PC, will allow the guest account access to the device, where previously they would have had to have had an account created in that tenant for them to have a Cloud PC assigned. As we can see, Niall’s account is accessing CPC-niall-ZMTAD in the sccmsolutions tenant. This is a hotly awaited addition to Windows 365 Cloud PC features. We look forward to using this feature with our customers. We hope that the registry key requirement is soon removed and is added as part of the installation of the Windows App, as this will help reduce steps required for onboarding for guest accounts. See you next time.
-
Introduction In a previous post we took a look at how you can determine the health of the Windows app and you can read about that here. Please read it to understand the new feature and why this blog post improves things from an admin perspective. In this blog post myself and my good friend Paul Winstanley took a look at yet another Windows 365 related ability and that is an Intune remediation solution called Windows App Health Check Log Reader. Note: This remediation solution is not supported by Microsoft. If your Windows app detects a health issue it’s logged in the following log file: C\Users\<USERNAME>\AppData\Local\Temp\DiagOutputDir\Windows365\logs\health_checks.log But that log file is on the device hosting the Windows app used to connect to your Windows 365 Cloud PC’s and that requires remote access by an admin or some other way of grabbing the log to determine the issue. In this blog post we take a look at a remedition solution which does just that, it looks at Windows devices that you target, determines if they have the Windows app installed and if that app matches a minimum version (needed for health checks), parses the health_checks.log file to see if there were any recent errors reported. If so, based on the cadence you select, it will copy that log to the root of your Intune logs folder, which is located at the following path: C:\ProgramData\Microsoft\IntuneManagementExtension\Logs Doing this allows you to grab the logs via the Intune console collect diagnostics ability. So let’s take a look at how it works. Get the scripts Head over to Github and download the 2 scripts here. They’ve changed a bit lately based on feedback we submitted, so do check regularly for updates. Once you’ve downloaded the scripts, extract them somewhere useful. Create the remediation In Microsoft Intune, create a remediation solution using these 2 scripts. On the Settings page, point it to the 2 scripts as appropriate. Once done, assign it to some devices that you want to monitor the health of the Windows app on, we used an Entra Id group containing some devices with and without the Windows app installed and we set a cadence of every hour to see the results quickly, however in production you’ll probably want to set that to run once a day. Analyzing the results After the remediation has run for some time, you can analyze the data it created by clicking on Device status in the remediation. In here we can see that most devices are without issues (good) but one device reports a detection status of With issues and it has recurred. Back in the Intune console, locate the device highlighted with issues, and click on the Collect diagnostics button. answer Yes when prompted. After some time those log files will be captured and you’ll see the status has changed. Click on Device diagnostics to download those files, by clicking the three dots and then selecting download. Within the extracted ZIP file, locate the (67) FoldersFiles ProgramData_Microsoft_IntuneManagementExtension_Logs folder and you’ll see the health_checks.log file. Open that file in CMTrace to review the issue. That’s a result! With this new remediation solution, you (as an Intune admin) can automate the copying of the health_checks.log file to a location that is easy to remotely grab without needing to bother the end user or use remote access to their PC. Awesome. see you in the next one !
-
please try again, the link only works for logged on users and now you are logged on
-
Introduction Microsoft has just pushed out yet another new feature for Windows 365 and Azure Virtual Desktop environments which is called health checks. Myself and my good friend Paul Winstanley took a look at the new feature and wanted to share our thoughts with you. We looked at the new functionality of the Windows app on Windows devices but this new feature is available via the Windows app on the following platforms: Windows: version 2.0.703.0 or later macOS: version 11.1.8 or later iOS: version 11.1.7 or later Android: version 11.0.0.46 or later What are health checks ? Good question. Think of it as a way for the Windows app to carry out a series of checks to verify that everything is in place to ensure that you have a consistently good connection to your Cloud PC and if something is not right, to report that there’s a problem to you via the app and via logs. These checks happen if it detects a network change, or can be triggered manually by the end user or automatically when the Windows App itself starts or when the user makes a connection to a resource such as a Cloud PC or Cloud App. Let’s take a look In the current version of the Windows app (2.0.704.0 at the time of writing), the health checks ability has been added. Please note that it is gradually rolling out to all regions, so if you have updated your Windows app and still don’t see the health symbol, don’t panic, it’s on its way. To verify which version of Windows app you are running see here. Before the feature rolls out your Windows app will look something like this. After the health check feature is enabled for your region, the Windows app will appear something like this, notice the new heart shaped icon on the left menu highlighted with a green arrow. Clicking it, brings up some information on the right side of the Windows app detailing the health of your connection. In there you can see the computer name, and what it determines to be the state of the system, the date and time of the check and the result of the check, in this case Everything looks good. You can also manually check the health by clicking Check again which will kick off the health checks, or click on Open log to see a log file containing what it has checked and the results of that check. Below is what the log file content looks like when everything is OK. The health_checks.log file location on Windows devices is: C\Users\<USERNAME>\AppData\Local\Temp\DiagOutputDir\Windows365\logs\health_checks.log You can also click on See all health checks to expand a list of what is checked. that’s all fine when everything is working, but what about when you have an actual problem ? Detecting network issues If something is detected to be not working, such as a failure to reach a required endpoint, then the Windows app will alert you with a banner, and the Health Check icon will have a red dot to signify something is wrong. These changes to the Windows App appearance happen if a network change is detected. Clicking on the health check icon itself, or clicking the Check device health warning button will allow you to check and reveal what the problem is. At this point you have many options. Check again Open log See all health checks Open network settings Clicking on See all health checks in this example reveals that the network connection is disconnected. And as mentioned above, that was detected when a network change was detected, as is revealed in the log file by clicking on Open log. Clicking on Check again in this failed state reveals (in the log) that this was a user initiated check. After you’ve sourced the root of the problem (in this case the router was turned off to simulate a network failure), and resolved it, the log reveals that there was another network change, and this time all is good. So there you have it, automated and manual health checks are now possible using the new feature in the Windows app. More info You can get more info about the new feature from Microsoft below: Run health checks to detect issues with Windows App connections – Windows App | Microsoft Learn https://techcommunity.microsoft.com/blog/windows-itpro-blog/enhancing-azure-virtual-desktop-and-windows-365-experience-with-health-checks/4446612 Summary The new health checks feature is a very welcome addition to the Windows app, as more and more companies have complex environments that contains proxies, ssl inspection, network sniffers that can interuppt or block the necessary traffic routes. The health check feature highlights when there is a problem with one or more of these endpoints, and alerts the end user with a popup. The admin in their turn can utilize the health check log to get more info about exactly what is failing. Thanks Microsoft for the feature and in particular thanks to the very helpful PM, Pavithra Thiruvengadam.
-
Introduction A new feature for Windows 365, and now in preview, is Windows 365 Cloud Apps. Instead of giving users a full remote desktop session, Windows 365 Cloud Apps are published as individual applications that run on a Cloud PC but look and behave like they are installed locally on the device. If you are familiar with Remote Apps, first introduced in Windows Server 2008 as part of Remote Desktop Services, then you will have an understand of how these operate. When Windows 365 Cloud Apps are published, you will be able to load up that individual application and if any interaction with another application is required, then that application will also fire up, even if it has not been published to the user. Note that Windows 365 Cloud Apps are only available to you with a Windows 365 Frontline subscription. myself and my good friend Paul Winstanley sat down to test run this new Windows 365 feature. It is nice and simple to set up so follow along. Create the Windows 365 Cloud Apps Provisioning Policy The first step is to create a provisioning policy for the Windows 365 Cloud Apps. This is done in the usual place for Windows 365 provisioning Devices | Device onboarding | Windows 365 | Provisioning Policies | Create Policy. You will notice a new Experience section in the policy wizard, here you will need to select Access only apps which run on a Cloud PC (preview) as the selection defaults to Access a full Cloud PC desktop. When you select the Access only apps which run on a Cloud PC (preview) option, Frontline will be automatically selected for License type and Frontline type will be Shared. All other options are greyed out as they are not applicable to Windows 365 Cloud Apps as mentioned earlier. Enter any other relevant information for join type, geography, region and SSO before proceeding through the wizard. The selection of the Image type is crucial for Windows 365 Cloud Apps as the solution will make available any discoverable applications in the devices’ start menu (Appx and MSIX are currently not supported discoverable app type – therefore Teams is not available at this stage). You can import a custom image to take advantage of other applications which are not included in the Microsoft Gallery images. Clicking the View link for Apps available on the image will display a list of the Cloud Apps that will be available to you when the device is provisioned. When assigning the policy, you will need to select the Frontline Cloud PC size from your Available Cloud PC’s drop down and create an Assignment name and choose the Number of Cloud PC’s, this number will reflect the number of licenses that you have available to use. After creating your policy, the Frontline Shared device, which will host the Cloud Apps will being provisioning. You can view this under All Cloud PCs. Give the device some time to provision and once completed it will report as such. Publishing some Cloud Apps Whilst clicking though the menu system, you may have noticed a new All Cloud Apps option, this is where we need to go to publish the discovered apps, making them available to the assigned users. We can see that 32 items were discovered from the image we selected and their App status is currently set to Ready to publish. Simply select the apps you want to publish and click Publish. Confirm your choice to Publish the apps. The App status will change to Publishing. and will, very quickly, become Published. You now have the option to Unpublish apps. The process is identical. Select apps you want to remove and click Unpublish. Confirm to remove them. The App status will revert to Ready to publish. How to access the Windows 365 Cloud Apps Windows App is the place to go to access your Windows 365 Cloud Apps. Prior to publishing apps to the users, the application will display any device based Cloud PCs the user has access to. With apps assigned a new option Apps appears. Look out for it as it’s a subtle addition and you could miss it initially. Clicking on Apps will display the published apps that you have made available. You can make an app a Favorite by clicking the ellipses. When launching an app a RemoteApp connection to the Frontline device will initiate and you may be prompted to authenticate along the way. and Allow remote desktop connection, depending on policies assigned to you. If this is the first time connecting to the Cloud App, it will take a little long to load up. You can click Configuring remote session to see that Windows is being prepared. You can identify the Cloud App from the icon on the Windows task bar, there is a Windows App logo on the top right hand corner of the icon. Once launched, you will feel as it the application is running on locally on your device. Pretty cool! Things to note To remove Cloud Apps from the All Cloud Apps view, you will need to delete the assignment of the provisioning policy. Since Cloud Apps run as Frontline Shared, the management of them is identical to management of a Frontline Shared Cloud PC, so be aware of any max connection limitations due to licencing. You can utilise policies assigned to Frontline devices, such as redirection. These will apply to Cloud Apps. When using a custom image, Windows 365 Cloud Apps will use a PowerShell script to scan the Start Menu for apps, so ensure that your tenant policies do not require extra authentication for PowerShell scripts to achieve this. Currently only apps discovered in the Start Menu are available. Microsoft are developing the ability to publish apps that are installed by Intune and are included in the Autopilot Device Preparation Policy associated with the Cloud App provisioning policy. We hope this blog post gives you a tester of this great new feaure.
-

SCCM 2007 SP2 prerequisites download
anyweb replied to EngiNerd's topic in Configuration Manager 2007
i'm curious, why are you guys installing such an old unsupported version of SCCM like this today anyway, can you please enlighten me ? -

SCCM Software Updates - KB5063875
anyweb replied to jackie_jack86's topic in Configuration Manager 2012
it looks to me like the update is failing on your clients, have you tried troubleshooting that ? I don't think this is an SCCM problem but a client problem. I asked copilot what it thought about the error given above and it came up with this script which does the following:... Renames Spupdsvc.exe to prevent interference. Stops Windows Update services. Renames update cache folders (SoftwareDistribution and Catroot2). Restarts update services. Runs sfc /scannow to fix system file corruption. Runs DISM /RestoreHealth to repair the Windows image. Prompts you to manually download KB5063875 if needed. Right-click the .bat file and choose "Run as administrator". Let it complete all steps (may take several minutes). Restart your PC and try installing the update again. fix_update_error_0x8024000B.bat -
I asked copilot, and here's the summary of it's answer: For a 12 TB upload to Azure Blob Storage, your main costs will be: Storage tier cost (Hot: $220/month, Cool: $122/month, Archive: $24.50/month) Write operations (~$9–$22 depending on tier) No cost for uploading (data ingress)
-

issue with Powershell script in Task Sequence (output)
anyweb replied to keywan's question in Deploy software, applications and drivers
when you create a custom variable in the collection, you assign a value to it, eg: CheckOutput = 100 In your task sequence, you CHECK for the value of the CheckOutput variable and act accordingly. For example you can have a step or group that checks if CheckOutput = 100 and if so it runs, if not, it does not run that step or group. Does that make sense ?