-
Posts
9257 -
Joined
-
Last visited
-
Days Won
371
Everything posted by anyweb
-

issue with Powershell script in Task Sequence (output)
anyweb replied to keywan's question in Deploy software, applications and drivers
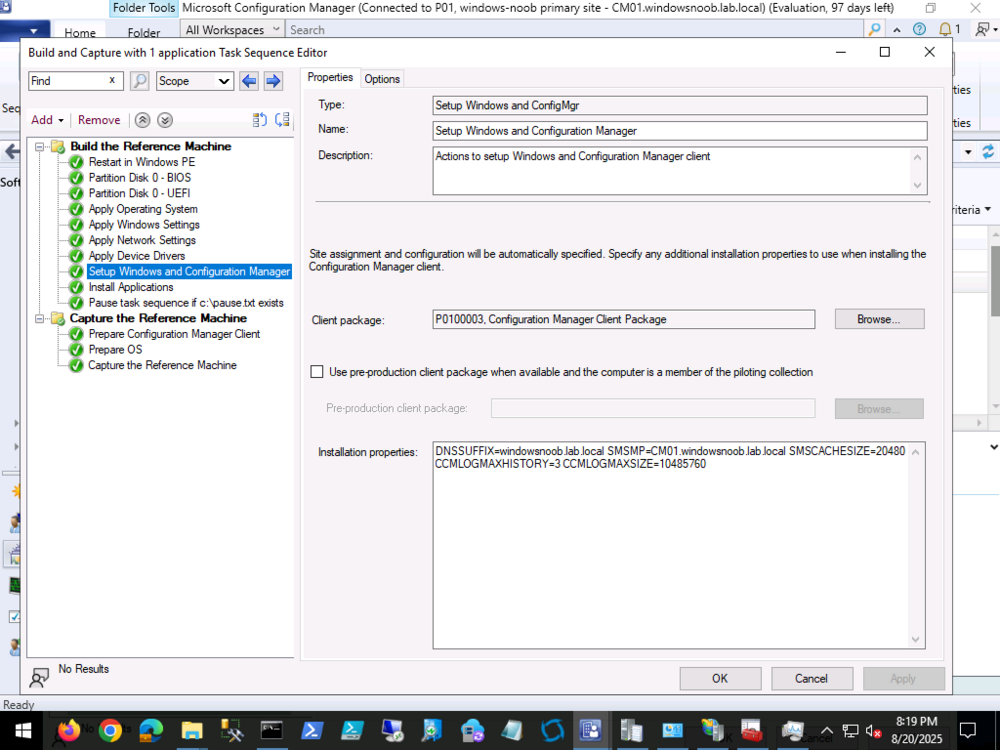
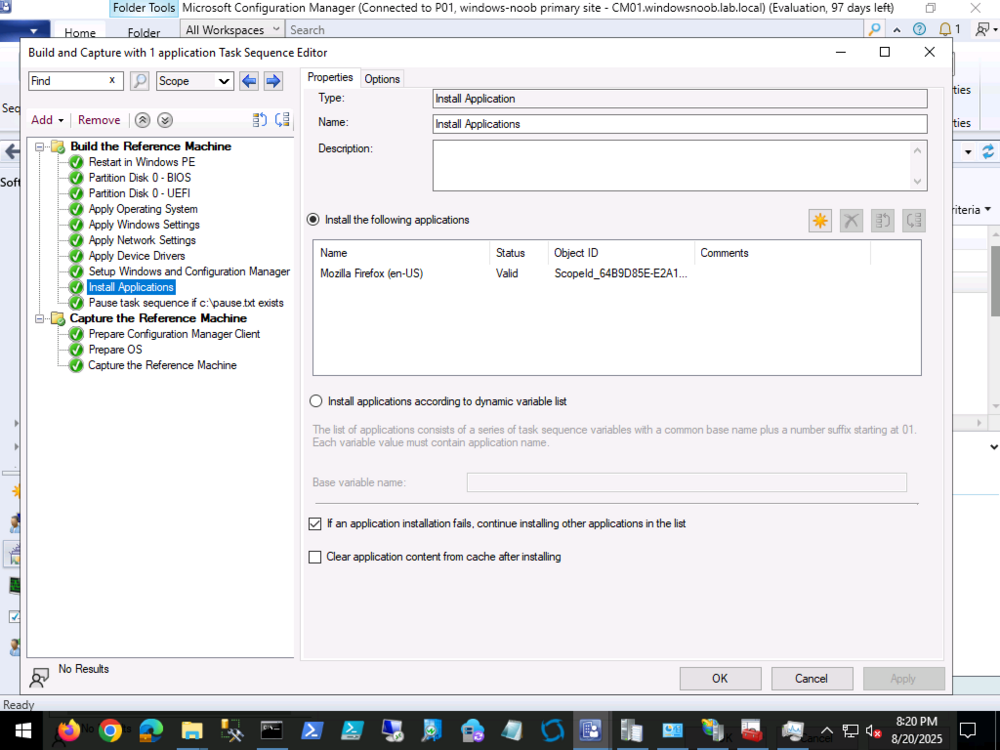
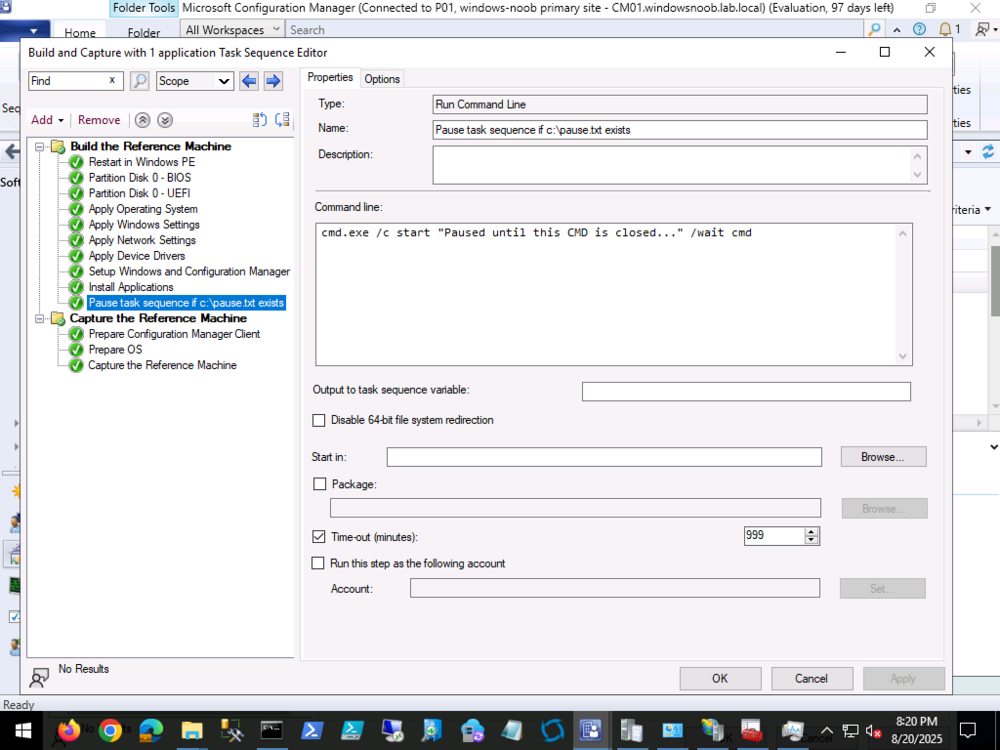
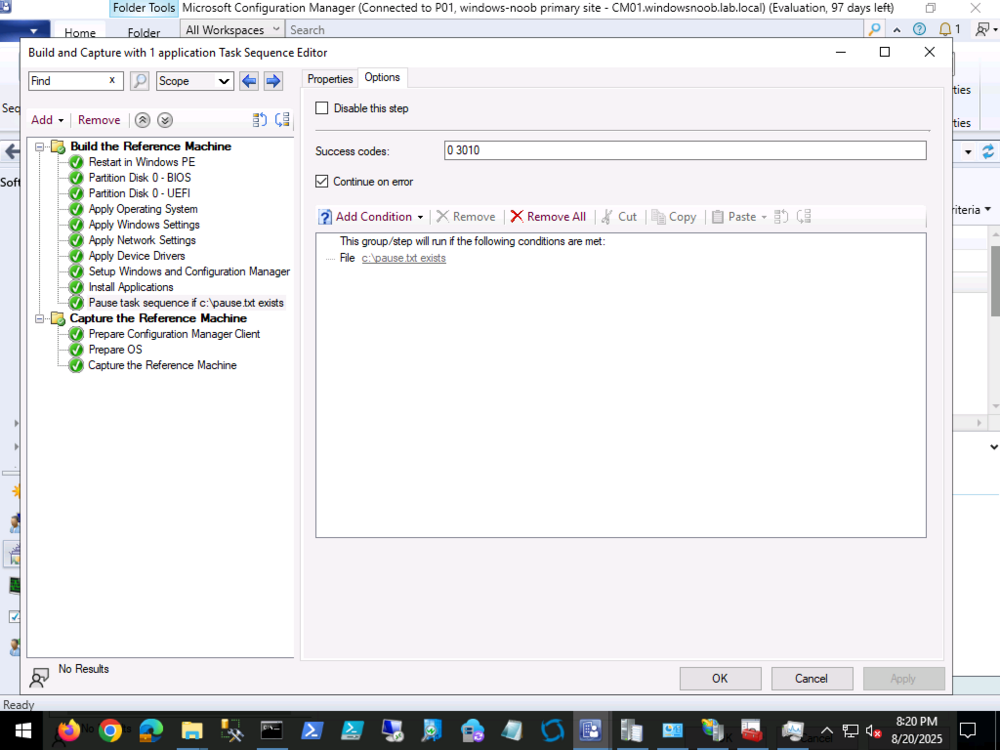
when you create a custom variable in the collection, you assign a value to it, eg: CheckOutput = 100 In your task sequence, you CHECK for the value of the CheckOutput variable and act accordingly. For example you can have a step or group that checks if CheckOutput = 100 and if so it runs, if not, it does not run that step or group. Does that make sense ? -
Introduction In the previous post I showed you what happens when a user or admin reset’s Windows after the August 2025 cumulative update (KB5063875) , basically the reset fails (rolls back). That problem can be fixed by applying an out of band update which can be deployed manually or automatically to affected clients. In this post I’ve once again teamed up with my buddy Paul to automate fixing this reset problem using Windows Autopatch in Microsoft Intune. It has a feature to Expedite updates. We’ve both tested this in our separate labs and are happy to share the results with you so that you too, can fix this in an automated way using Windows Autopatch. Expediting updates As the name sounds, this allows us to expedite (rush) updates to an Entra ID group containing our target computers, and this method can be used to get Quality Updates including Out of band updates to your devices via Windows Autopatch. There are some prerequisites, listed below: Devices meet the prerequisites for Windows Autopatch. Devices installed the update described in KB4023057 – Update for Windows 10 Update Service components (or a newer version). To verify that your devices meet the prerequisites for receiving an expedited update, use the Readiness test for expediting updates. Let’s create our Expedite updates policy. In Intune, browse to Devices, Windows Updates and select Quality Updates. In the Create + drop down, select Expedite policy. Give the policy a suitable name and description. In the Select the quality update you would like to expedite, select the 08/26/2025 D Update for Windows 10 and later option. If you are wondering what the D Update and B Security Updates are, here’s an explanation. B updates Released on the second Tuesday of each month (commonly called Patch Tuesday). These are the mandatory, cumulative updates that include security fixes and sometimes reliability improvements. D updates Released on the fourth week of the month (usually the preview releases). These are optional, non-security preview updates. They contain fixes and improvements that will roll into the next month’s B update. to summarize… B = Security & required (Patch Tuesday) D = Optional preview (late month, contains fixes but no new security fixes) So, as we already have deployed the August Cumulative update that would be the B update. We definitely need the fixes (out of band) that came after that and that would be the contained in the D updates. Finally, if a reboot is required (and it is required), decide on how many days before it’s enforced, so we’ll set it to 0 days. After clicking Next, select the group(s) you want to target with these out of band updates. Don’t worry about the fact that there’s no devices in that group yet, we’ll add them as needed later. Click Next and the policy is created. Finally, when you are ready to test this add one or more devices to the target Entra Id groups. After the device gets the policy, and as long as there are no policy conflicts your end users should be notified about the pending restart. After the restart is completed, you can verify Windows update settings, and view the history. The latest OOB (Out of band) update should be installed and as it’s also cumulative it will contain the fix to allow Windows reset to work again. Job done! Summary While this ability to expedite updates in Windows Autopatch is welcome, it’s far from perfect. There are several problems, which we’ll list here: Speed of delivery. The blurb from Microsoft claims the following, highlighted below But in several VM’s where myself and Paul tested, the expedited update arrived in an anything but their claimed speed. In reality, the update took several hours to approx one day and numerous syncs on the clients and in the Intune console before we saw the popup. On some vm’s we are still waiting for the magic to happen even though all the prerequisites are in place. Update: We got a reply from Peter Braune on Twitter, who stated the following, it may help you if you are going down this path. We actually had to create a policy via settings catalog “Automatically receive optional updates”, to get this update rolling out to clients. Once the policy was in place the update was installed immediately. Downside, preview updates being rolled out automatically too. Lack of ability to target a specific hotfix. You you can only choose between B or D updates and hope that they include the fix you need. What we really wanted was to be able to specficially install KB5066189, but that’s not possible currently with this method via the console. Lack luster reporting. If you want to see what’s happening with your expedited update in real time then you are out of luck. Of the several machines we targeted the reporting suggested nothing was wrong, which in a way was true because nothing was happening. And that’s the problem, how can you quickly determine whether your hotfix is applied or not to these target devices ? Policy conflicts. After enabling Expedited updates, you might end up troubleshooting policy conflicts on your target devices if your tenant has had the following installed. Windows Autopatch – Office Update Configuration – Expedited (Expedited updates for CVE-2023-23397). Hopefully Microsoft is listening and will improve this service going forward. That’s it from us, see you in the next one.
-

Repair .EXE Application from Software Center
anyweb replied to jackie_jack86's topic in Configuration Manager 2012
why not just wrap the exe as an MSI ? -
looks like you are missing storage drivers, if you open a cmd prompt (f8) and type diskpart, list disk does it list any hdd(s) ? if not, there's the answer, missing storage drivers. if it is showing, then what type of storage is it ? also what ADK are you using and what version of SCCM
-
Introduction If you work with computers like I do, then the Patch My PC name should be very familiar to you. They’ve been at the forefront of Patching Windows computers in enterprises for years now and are well known, trusted, admired and praised. They have some of the smartest names in tech working for them and certainly know how to produce excellent software. They actually started out in 2011 by releasing a free tool to Windows users to patch their PC’s and that tool was originally called PatchMyPC. They’ve since renamed that free tool to Patch My PC home updater. As the name implies, you can use home updater on your home computers and I’ll take a good look at it in this blog post. Home updater is designed for home use, not for your business, and it can patch up to 532 or so applications natively (the list is growing). But first off, why would you want to patch your 3rd party applications on your home computers ? well that’s how 70% of malware attacks exploit outdated vulnerabilities. Windows update will handle things like security updates for Windows and drivers, but third party apps are your problem. Not any more 🙂 Download home updater You can download the home updater from here. It comes in both MSI (installer) and EXE (executable) formats, I chose the MSI. After accepting the license terms and conditions it’s ready to install. After it’s installed you’ll be presented with (in my case) and load of apps that are out-dated. I’m so glad I decided to run this. When you start it it won’t automatically update these out-of-date applications until you actually click on the Start Updater button, however there is an option in the Settings to enable that and you can also configure it to run on a schedule. Let’s take a look at the options in the left of the app. Apps – The main interface screen, shows you which apps you have installed and whether they are out of date or not Startup – Gives an extensive list of apps that startup when your computer starts, this is great and shows much more than you see in the ‘startup apps’ option of Task Manager. Uninstaller – Use this to uninstalls apps you may not need any more Scheduler – use this to schedule scans and updates, comes with recommended settings and is disabled by default. Settings – Use this to configure home-updater specific settings About – About the home-updater app. On the right of the app you’ll see a Start Updater button, I wanted to see how good it was so that’s exactly what I clicked. After clicking that you’ll see your selected apps pending update as it attempts to download and update the latest version of those apps. Note: If you don’t want an app automatically updated, you can disable that ability by clicking on the three dots beside the app in question (ellipses) and selecting “Disable Auto Updating”. When running the updater, let it do it’s thing, you’ll see apps starting and updating right before your very eyes. Some apps may also prompt you to login, I’m not sure if that is required in order to complete the update but I hadn’t used some apps in a while and therefore those apps wanted me to login, such as the EA Account app shown below. After letting the home updater app run for some time, the status of individual applications started to change from Outdated, to PENDING, UPDATING and finally Up to Date as shown below. Side note. I’m not sure why pending and updating ended up all caps but that’s one for the UI guys at the Patch My PC team. After waiting some time, I could see that the home-updater was sitting on the Logitech G HUB app for quite some time. I can understand that, as it’s a terrible piece of software and has bricked a keyboard on me. But… what should I do ? Wait or try and move on. At this point the ‘tech in me’ wanted to look at the log file for the home-updater. I checked the installed folder but couldn’t find any logs there, next I checked the Settings section of the app, and it listed the log file location, great. And here’s the log, and guess what, there’s the Logitech app too… Opening the C:\ProgramData\PatchMyPC\PatchMyPCHomeUpdater.log file up with CMTrace (the best log file reader ever IMHO) revealed that not a whole lot has been happening for the last hour or more. So it does look like Logitech G Hub has thrown a spanner in the works. To fix it, I’ll cancel the updater. And for now, exclude Logitech’s crappy app. Except, after clicking Cancel Updater, nothing happened apart from the main UI showing most apps as Outdated in red again. Shouldn’t the Cancel Updater button change to Start updater again ? When I tried to exclude the troublesome app (Logitech G Hub) by clicking on Disable Auto Updating it was greyed out. most likely because the exe file for updating that app was in the logfile source folder and it was still trying to update that app. But then, why didn’t Cancel Updater kill it ? So I closed the home updater app, and restarted it to see would there be a difference. There was, now I could disable the auto-updating feature for Logitech G HUB. Once done, I clicked on Start Updater, and off it went for the second time. This time however, you can see the Logitech G HUB app has a disabled icon in red. Cool, let’s hope it works. This time around I could see it updating each app quickly, which was great, and I was seeing more and more green Up to date statuses. The OCD in me wants all the apps up to date, but let’s see what we can do. After a few more minutes it was done, as the updater button reverted to Start Updater, and all but 2 apps were updated! At this point, I wanted to see if it could fix Logitech G Hub and the other app, so I re-enabled updating on the troublesome app and started the updater again. It gave up and the log file revealed some issues with the EXE and a call to some SSL address. I don’t blame the home-updater tool here at all for this, but maybe it could inform the end user with a popup or some UI hint other than Outdated that clearly stated that it had a problem updating this app. At this point I managed to get 34 out of 36 apps updated. Not bad at all. Uninstalling bad apps As I had two apps that clearly were not interested in updating, I decided to uninstall them. You can do that by navigating to the Uninstaller section of the app or simply clicking the three dots on the app in question and selecting Uninstall App. That action prompted the apps to present me with various popups about uninstalling the app, which is OK, but would be nicer if it was a silent uninstall. Once done, I clicked on Re-Scan to check my current status as one of the two bad apps was still listed (guess which one). After the Re-Scan, it all looked good. Note to developers at Patch My PC, trigger a re-scan automatically, after a user chooses to Uninstall and app. I’m sure you are doing that already as it worked for the CrystalDiskMark app, but not for the Logitech G HUB app. Below you can see that All apps are up to date! Job done! Setting up a schedule Security waits for no one, so you should definitely setup a schedule for your Patch My PC home updater. Click on the Scheduler button and select the + ON button. Once done you can see that it has a default of running at Monday, 7PM and to repeat daily. What I like is it also enables the Run ASAP when Missed option by default, which is great as you probably are not using your computer every day. Once you are happy with your settings, make sure to click on Save Schedule, to save the schedule otherwise nothing will happen. You’ll get a popup (aha, they can do popups!) informing you that it’s saved. After clicking OK, you can see the schedule tasks are created, one for updating the app itself, and one for updating your third party apps. Modifying Startup apps I mentioned that the Startup button allows you to modify startup apps, and it does it much better than the similar option in Windows Task Manager Startup Apps. Compare these results. Below is what you see available in the Startup Apps view of Task Manager. Versus the really populated view from Patch My PC home-updater. Quite a difference! Summary The Patch My PC home updater app is incredible, it helps you patch your home computers third party apps with ease, and does it using a very easy to use interface. It also allows you to setup schedules to make sure those third party apps are kept up to date to ensure that you are as secure at home, as you are at work. I can highly recommend this software, and best of all, its FREE.
-
Introduction Microsoft pushed out some new updates for Windows 365 Cloud PC’s recently and one that we thought was interesting was this one, the ability to recover a Cloud PC that was de-provisioned due to license expiration. The de-provisioning of a Cloud PC normally means that it is unusable and unrecoverable, it’s a destructive action. However, with this new feature and as long as you have previously enabled Point-in-Time-restore explained here then you should be covered by this new ability (for Windows 365 Cloud PC Enterprise only). In this blog post myself and my good friend Paul look at the new feature and test it out. We’ll be collaborating on more Windows 365 and Azure Virtual Desktop content during the year so stay tuned on the SCCMentor and windowsnoob websites! The prerequisites Before we test it, let’s look at what you need to have in place. To recover a previously de-provisioned Cloud PC, ensure that the expired Windows 365 licenses are renewed. The replacement licenses must be of the same SKU, so if the previous Cloud PC’s were Cloud PC Enterprise 2vCPU/8GB/128GB then the replacement license assigned must be for Cloud PC Enterprise 2vCPU/8GB/128GB. To recover a previously de-provisioned Cloud PC, ensure that the provisioning policy of the de-provisioned Cloud PC still exists. To recover a previously de-provisioned Cloud PC, ensure that assignments with the right users are assigned to the provisioning policy. To recover a previously de-provisioned Cloud PC, ensure the end users still exists, and are still assigned to the same Entra ID groups as before or the ones included in the policy assignments. Testing the new feature Ok now that’s all clear, let’s test it out. Before starting, we verified that our test Cloud PC had a point-in-time restore policy (User settings) applied. We also made sure to place a file on the Cloud PC outside of Onedrive known folders. And before continuing, we verified that there was at least one backup for this Cloud PC, and there were several. Note: If you are also testing this feature and you are doing it on a newly provisioned Cloud PC, you can click on Create restore point to create a manual restore point. As simulating a license expiry and then re-purchasing the same license is easier said than done we’ll simulate it by deleting a user that was assigned the following Cloud PC SKU: Cloud PC Enterprise 2vCPU/8GB/128GB. Below you can see that user (testuser100@windowsnoob.com) and their respective Cloud PC. Next, we deleted our licensed user. and were notified of that… Shortly after, the status of the Cloud PC that that user was using, changed from Provisioned to In-grace period. Clicking that In-grace period status and selecting Deprovision now, speeds up the testing process. Which kick starts de-provisioning Some time later, the Cloud PC was no longer in the Intune console and was no longer available to the (now deleted) end user to use. At this point, the de-provisioning process was completed. Recovering de-provisioned Cloud PCs In the real world, to see this new feature you’d renew an expired license and make sure that the user/group/policy and so on didn’t change during that time period. But we are simulating that, so to simulate it we’ll restore the user we deleted earlier, again, nothing else has changed other than that users Cloud PC’s went from in-grace period to de-provisioned. So let’s restore the deleted user. In Azure (Entra Id) select users, click Deleted users and locate your deleted user. Select the user and click Restore users. You’ll be notified of the restore. And as the user was still in the same groups, they’ll pick up the Cloud PC assignments targeting them and a new Cloud PC matching the SKU in question will be provisioned. After the Cloud PC is provisioned, you’ll see it appear with a new computer name. We need to do some final actions. Select the newly provisioned Cloud PC and click the Restore option. This will show a retention restore point. Select it and click the Select option to restore that de-provisioned Cloud PC. You’ll get a popup warning you about the restore. Click Restore and the restore will be initiated, you’ll see the status change to Restore pending. And during the restore the status will then change to Restore active. and after a while refreshing that device will reveal a ‘Not found‘ statement (sorry no screenshot, we’ll add it shortly). However, if you navigate back to Windows 365 devices, you’ll see that the old name (old Cloud PC) is back ! and logging on to that Cloud PC using the same user will indeed reveal that the content is as expected. Job done! Read more To learn more about this new feature see Microsoft’s own page here. To learn how to use Point-in-time-restore read here.
-
Introduction Look out for a new series of blogs from myself and my MVP buddy, Paul Winstanley as we explore the world of Azure Virtual Desktop (AVD). In the meantime, we have collaborated on a kick the tyres exercise to experience the AVD solution via the Microsoft quickstart. This blog post details that experience with a simple step-by-step guide. Microsoft provides the quickstart as a great way to test out an AVD environment with minimal fuss. It will create a small, low cost environment in approximately 20 minutes. Prerequisites To create the environment you will need to meet the following prerequisites: An active Azure subscription An Entra account with the following roles assigned: Contributor User access administrator Some test Entra accounts, for authentication into the AVD environment Available quota for your subscription for the Standard_D4ds_v4 virtual machine. If you have insufficient quote then you can increase – https://learn.microsoft.com/en-us/azure/quotas/per-vm-quota-requests Access to the required FQDNs and endpoints in Azure – https://learn.microsoft.com/en-us/azure/virtual-desktop/required-fqdn-endpoint?tabs=azure What gets deployed during the Quickstart A resource group called rg-avd-quickstart-<GUID> A virtual network and subnet. The IPv4 address space will be 192.168.0.0/24 and will use Azure provided DNS servers A network security group that is associated with the subnet of the virtual network and uses only the default rules. No inbound rules are required for Azure Virtual Desktop A host pool with single-sign-on (SSO) enabled An Entra joined session host running Windows 11 Enterprise multi-session with Microsoft 365 apps preinstalled with English (US). The virtual machine is a Standard_D4ds_v4 size virtual machine (4 vCPUs, 16 GiB memory) configured with a standard SSD disk An application group that publishes the desktop from the session host A workspace For a complete list of the resource published by the quickstart, take a look the Microsoft documentation https://learn.microsoft.com/en-us/azure/virtual-desktop/quickstart?tabs=windows#deployed-resources. Getting started The first step is to register the Microsoft.DesktopVirtualization resource provider on your Azure subscription In the Azure portal, go to your Subscriptions and select that one you will use for this exercise. Select Resource providers from the menu and look for Microsoft.DesktopVirtualization. If this is listed as NotRegistered in your subscription, then click the three dots and select Register as shown below. If it is already listed as Registered then there is nothing else you need to do. Before continuing, ensure that Microsoft.DesktopVirtualization is listed as registered. Deploying the quickstart solution You can find the quickstart solution in the Azure portal by searching for Azure Virtual Desktop and then selecting Quickstart from the menu. Click the Create button to begin the process. You will need to enter specific information on the Basics tab. Subscription: Ensure you choose the subscription where you have registered the resource provider previously. Location: Select the Azure region where you want the AVD resources deployed to. Local administrator account: Username: Enter the name for a local administrator Password: Enter and confirm your password for the local admin User assignment: Select a maximum of two users who will have access to the AVD devices (see screenshot below) Once all the details have been entered click Review + create to continue through the quickstart wizard. Ensure you receive a confirmation that Validation passed and click Create. The deployment of the resources will be in progress. If all goes well, Your deployment is complete will be returned. Connecting to your AVD desktops You can connect to your AVD desktops via the Windows app, which is available from the Microsoft Store. When installed, and one of your allocated users is authenticated to the app, you should see a SessionDesktop item (in addition to any Cloud PC’s or other AVD’s available to that user). This is your AVD desktop. Click Connect to access. Once done, you will be prompted to enter your password, or MFA details and then asked to Allow remote desktop connection. This message can be suppressed using a list of trusted devices (see https://learn.microsoft.com/en-us/azure/virtual-desktop/configure-single-sign-on for more information). Just to note, you can also alter the display settings for your AVD session by clicking the ellipsis (three dots) and adjusting. Eventually, you will hit the Windows 11 desktop. Since this is multi session, your other allocated user can log in and use the AVD desktop at the same time. Note, the screenshot below, the same hostname is in use. Removing the quickstart services Once you have used the quickstart, you may wish to clean up the resources, ready for your deeper dive into AVD. To do this, locate your AVD virtual machine under Virtual machines in the Azure portal and click on the device. Click Stop to deallocate the device. You will be prompted to confirm the deallocation. Make sure you have ony selected the AVD virtual machine that you want to stop. Click Yes. Wait until the device reports back as Stopped (deallocated) under its Status. Now we need to remove the resources which were created, as they encur costs when running. You can do this 2 ways, in Azure, search for Resource groups and find the one created by AVD. As mentioned, this will have a naming convention of rg-avd-quickstart-<GUID>, or simply click the AVD virtual machine and then select the resource group it’s in as shown here. Click into the resource group, select all the resources under Overview and then click Delete. You will need to confirm their removal by entering delete in the field below and also you can select Apply force delete for selected Virtual machines and Virtual machine scales sets, if you so wish. Once done, click the red Delete button. You will then need to confirm the deletion of the resources. Click Delete one more time. The resources will no longer be listed when they are removed. Next, click Delete resource group to remove the quickstart resource group. Enter the name of the resource group to confirm its deletion and click Delete. Once again, confirm by clicking Delete. I hope this guide gives you a good oversight into how quickly you can test out the Azure Virtual Desktop using Microsoft’s quickstart option. You can get a VM up and running in no time and experiment with it. As mentioned, we will be taking a deeper dive look at AVD very soon, so watch this space and keep an eye on the SCCMentor and windowsnoob websites.
-

SSRS SCCM Reporting Log
anyweb replied to Cerberus24's topic in System Center Configuration Manager (Current Branch)
great findings and glad you got it sorted are you sure with the changes made that it's going to work security wise ? -

SCCM 2007 SP2 prerequisites download
anyweb replied to EngiNerd's topic in Configuration Manager 2007
send me a pm -
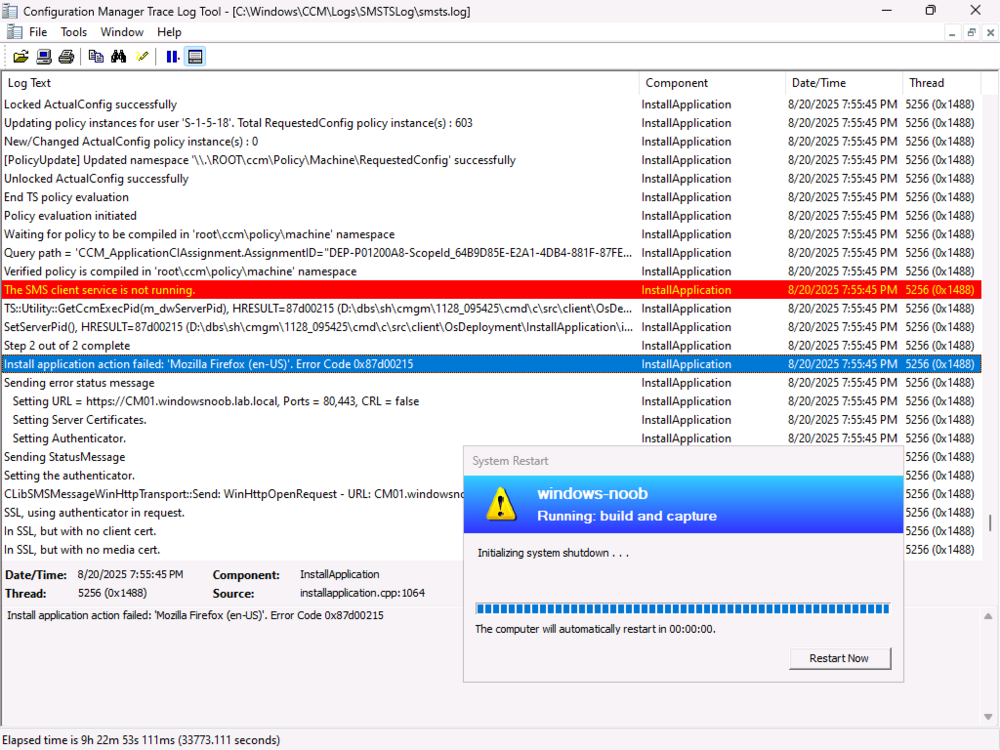
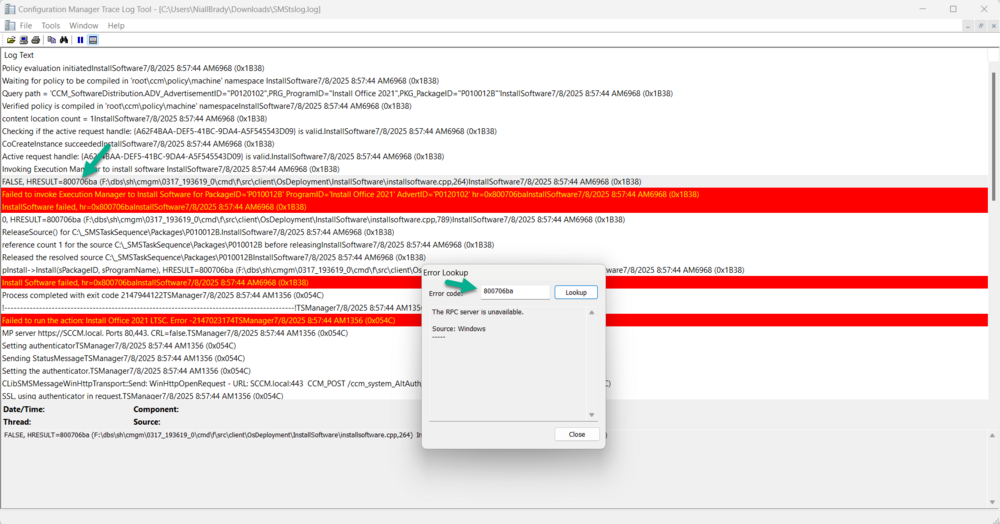
Using CMTrace error lookup, I can see that the error message is actually an RPC server is unavailable I asked Google (ai) what this could be, The "RPC server is unavailable" error (0x800706BA) in SCCM (System Center Configuration Manager) typically indicates a problem with communication between the SCCM server and a client machine. This usually stems from network connectivity issues, firewall restrictions, or incorrect service configurations. Here's a breakdown of potential causes and solutions: 1. Network Connectivity Issues: Verify Network Connectivity: Ensure that the SCCM server and the client machine can communicate over the network. Try accessing the client machine from the server using its hostname or IP address in Windows Explorer (e.g., \\clientname\c$ or \\192.168.1.10\c$). Check DNS Settings: Incorrect DNS settings can cause name resolution issues, preventing the server from finding the client. Verify that the DNS settings are correct on both the server and client. Time Synchronization: Ensure the time and time zone settings are synchronized between the client and server. Inaccurate time can also cause communication problems. 2. Firewall Restrictions: Firewall Configuration: Firewalls, both on the client and potentially on the network infrastructure, might be blocking the necessary ports for RPC communication. Specifically, verify that ports 135 (TCP and UDP) and the dynamic RPC port range are open. Outbound Traffic Inspection: Some firewalls with outbound traffic inspection capabilities might be blocking RPC traffic. Check if any such rules are in place. 3. Service Issues: RPC Services: The Remote Procedure Call (RPC) service and other related services, like the "DCOM Server Process Launcher" and "Remote Registry" services, must be running on both the client and server. Service Configuration: Ensure that these services are set to start automatically (Automatic) after a system restart. 4. Account Permissions: User Account Permissions: Verify that the account used for the SCCM connection has the necessary permissions to access the client machine and its resources. DCOM Permissions: Check DCOM (Distributed Component Object Model) permissions on the client machine, as they might be preventing the connection. 5. Troubleshooting Steps: Restart RPC Services: Restart the RPC service on both the client and server to reset its state. Reboot the Client: After making configuration changes, reboot the client machine to ensure the changes are applied. Use wbemtest.exe: Test WMI connectivity to the client machine using the wbemtest.exe tool. This can help isolate whether the issue is WMI-related or broader RPC communication problem. Deploy Recast Agents: If using Recast Software's Right Click Tools, deploying their agents can help resolve RPC communication issues. In Summary: The "RPC server is unavailable" error in SCCM is often a network or configuration issue. By systematically checking network connectivity, firewall settings, service states, and account permissions, you can identify and resolve the problem.
-
You can upgrade directly to 2503 it's cumulative. So it should contain all the fixes and updates from the previous version. do check out the official known issues here: https://learn.microsoft.com/en-us/intune/configmgr/core/plan-design/changes/whats-new-in-version-2503 and my take here: https://www.niallbrady.com/2025/04/04/configuration-manager-2503-is-out-350-bugs-fixed/
-

Windows Driver Foundation - CPU Utilisation High
anyweb replied to jackie_jack86's question in Windows 10
I would escalate this to your Dell Technical Account Manager, this is not an SCCM problem,unless of course your quote here: was when you imaged the Dell using your own task sequence, is that the case ? -

SCCM - Task Sequence (Softwares)
anyweb replied to jackie_jack86's topic in Configuration Manager 2012