-
Posts
9253 -
Joined
-
Last visited
-
Days Won
369
Everything posted by anyweb
-

Build and Capture or Build from Media - Windows 10
anyweb replied to MagnumVP's topic in Configuration Manager 2012
use a vm to build any reference image, always, I cover how to do this in my book here > http://www.amazon.com/Windows-noob-Guides-Configuration-Manager-2012/dp/9187445166 -

W10 Ent Upgrade to build 10586
anyweb replied to Siroj's topic in System Center Configuration Manager (Current Branch)
we are still waiting on a fix... -
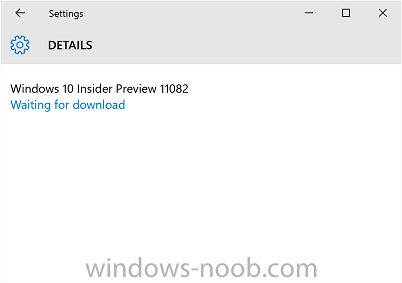
Microsoft have released yet another Windows 10 build to insiders, details below With this build, you won’t see big noticeable changes or new features just yet. Right now, the team is focused on product improvements based on the feedback we’re hearing on the November update to Windows 10. This includes the changes that have also been going out as cumulative updates through Windows Update on your PCs running the Windows 10 November Update as well as on phones running Windows 10 too. We’re also working on some structural improvements to OneCore, which is the shared core of Windows across devices. Essentially, OneCore is the heart of Windows, and these improvements to OneCore make building Windows across PC, tablet, phone, IoT, Hololens and Xbox more efficient. We’re doing some code refactoring and other engineering work to make sure OneCore is optimally structured for teams to start checking in new features and improvements in the new year. https://blogs.windows.com/windowsexperience/2015/12/16/announcing-windows-10-insider-preview-build-11082/
-

First Major Update for Windows 10 Available Today - Windows 10 version 1511
anyweb replied to anyweb's topic in Windows News
hi Leon, yup i'm aware i'll adjust this post accordingly, thanks -
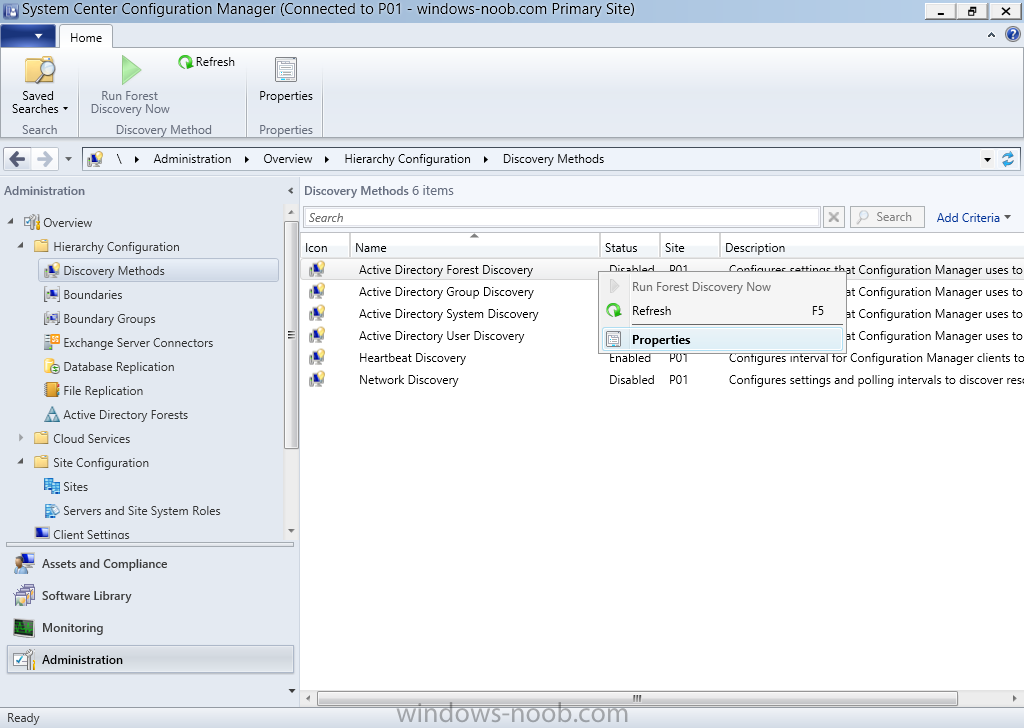
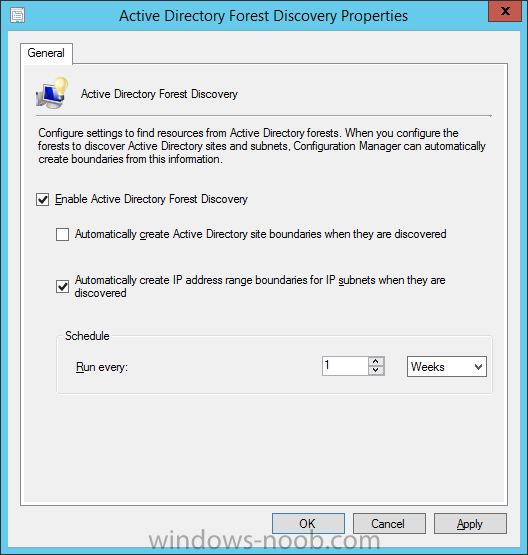
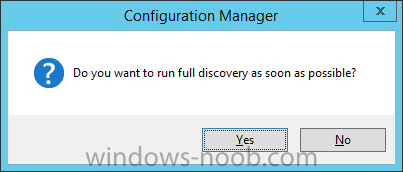
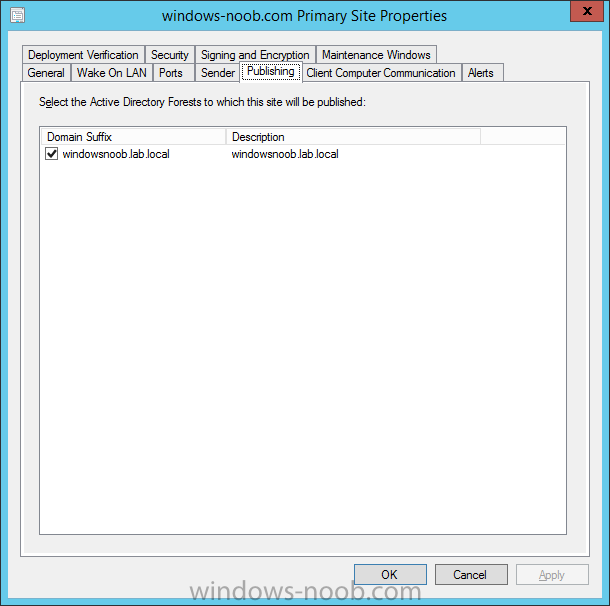
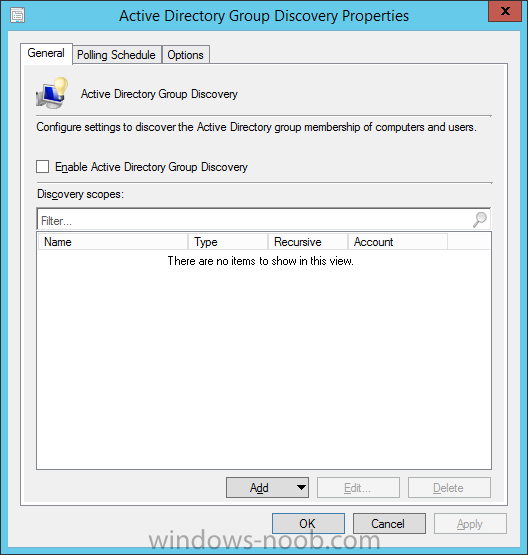
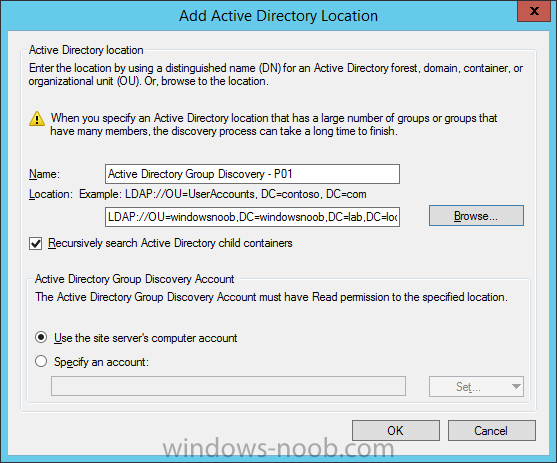
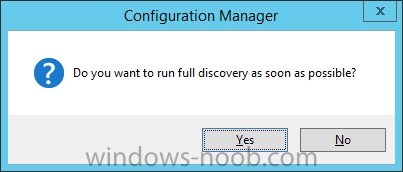
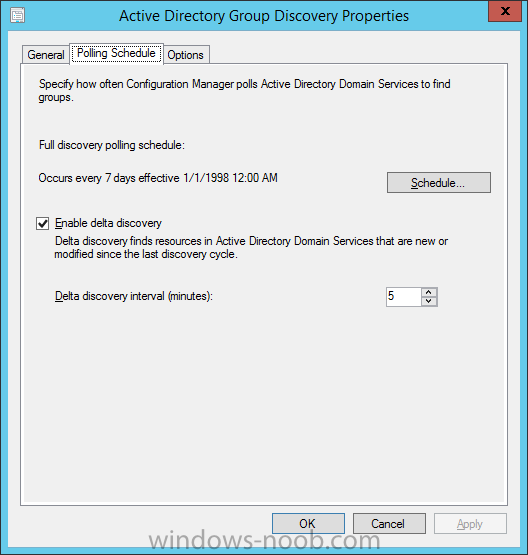
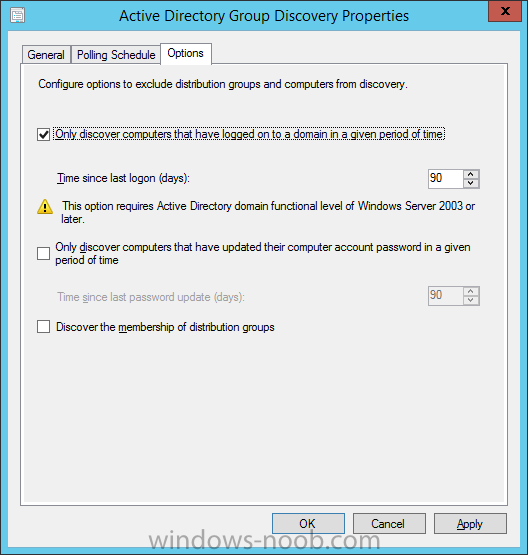
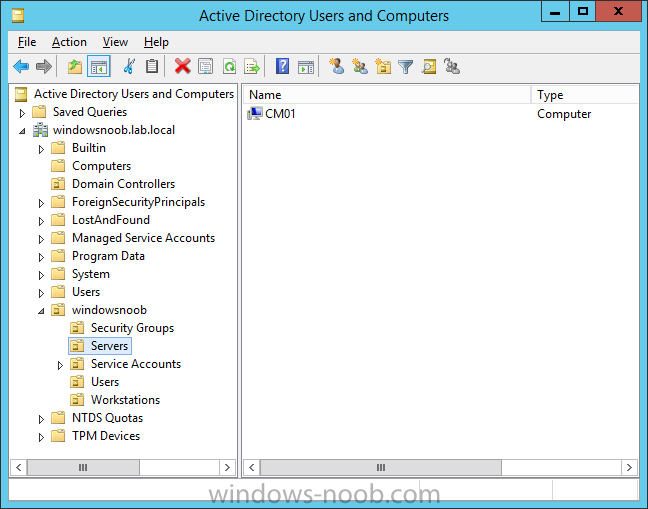
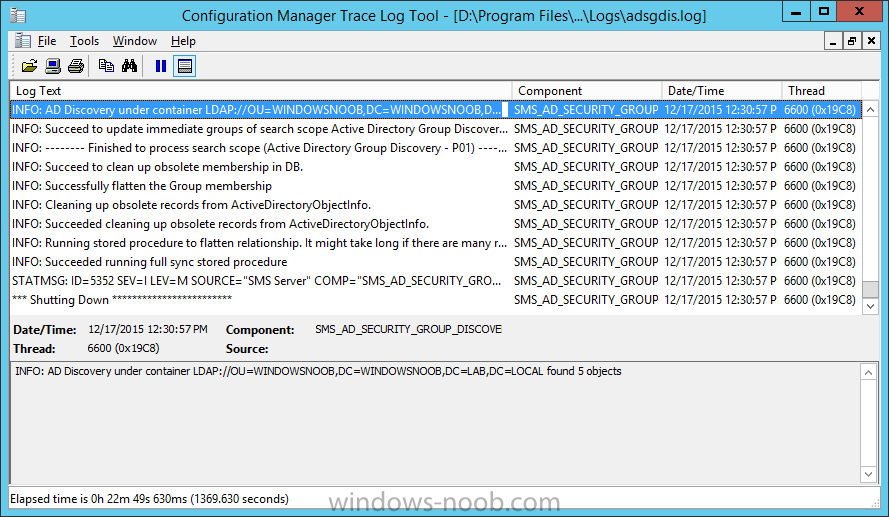
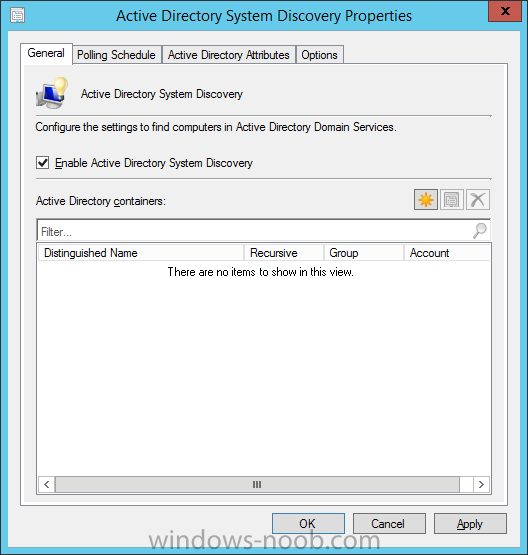
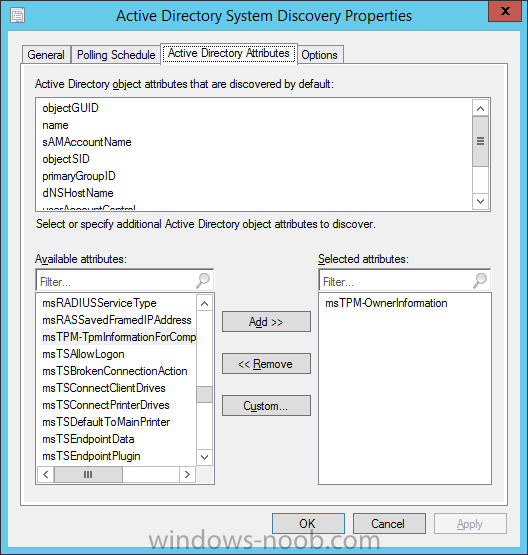
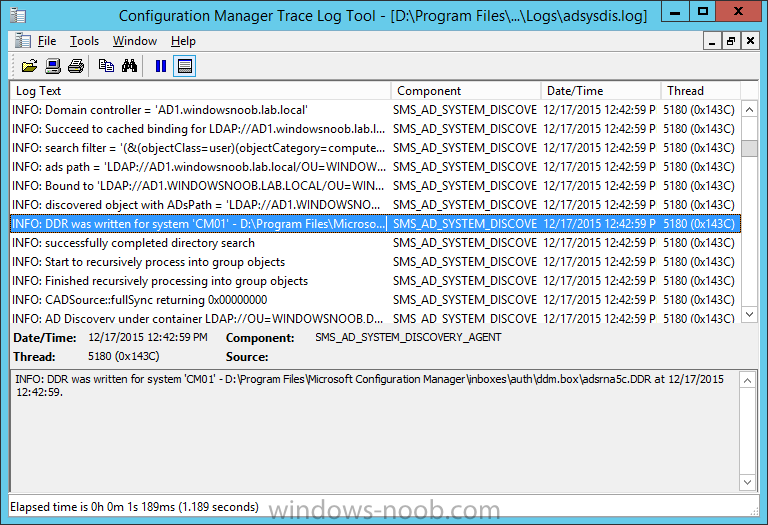
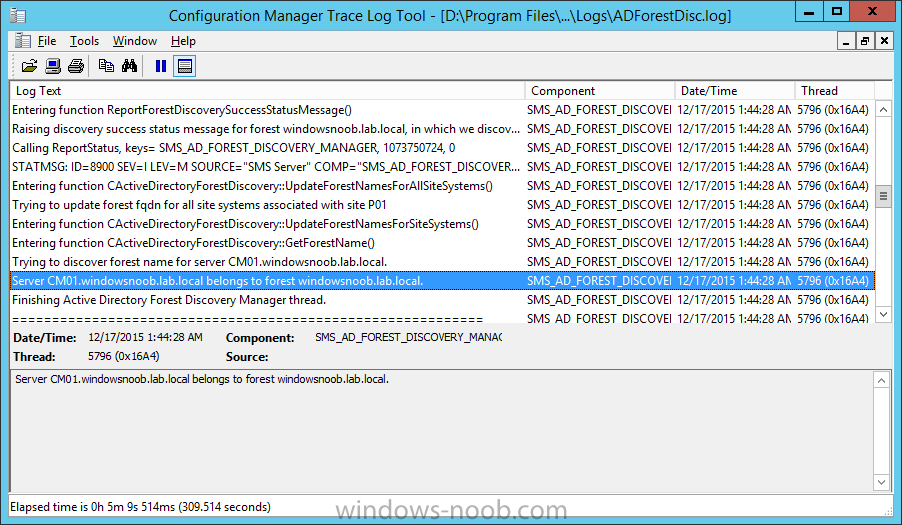
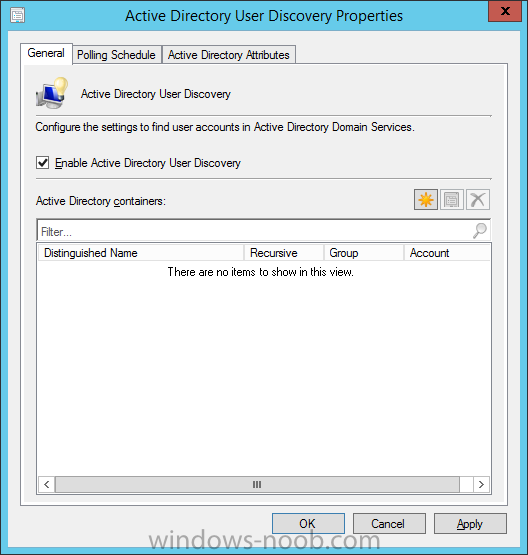
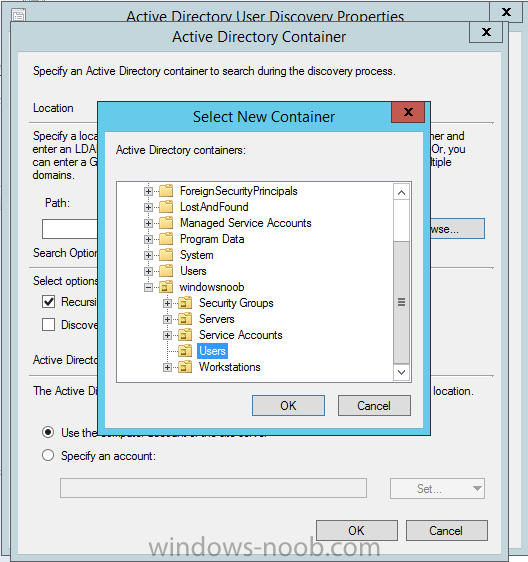
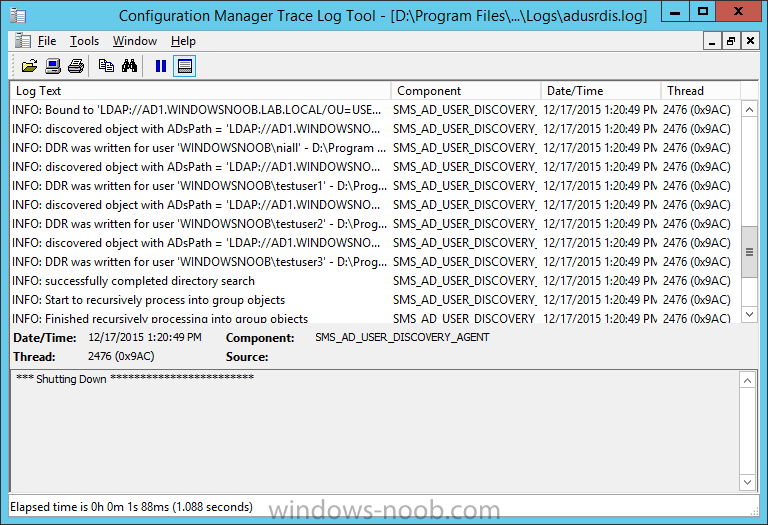
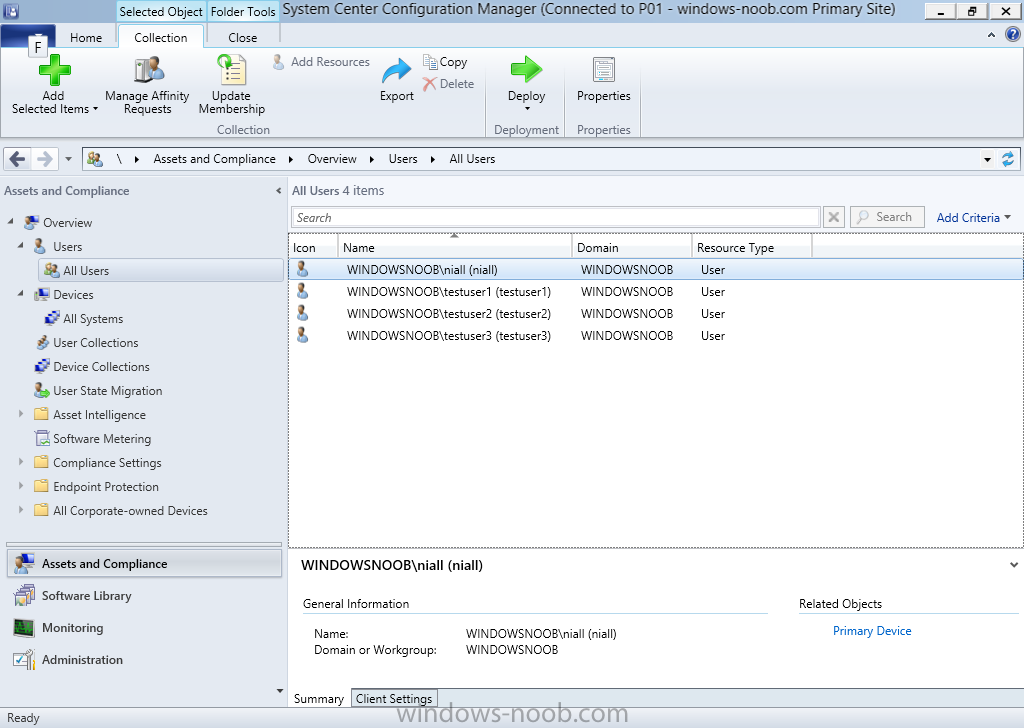
Introduction In an earlier post you installed System Center Configuration Manager (Current Branch). In this post you will learn about configuring discovery. Planning for discovery in ConfigMgr is an important step while configuring your sites and hierarchies. You need to discover objects in locations that you select and these discovered resources are what you want to manage (devices/users). These discovered resources can be targeted with software and/or get the ConfigMgr client agent installed via Client Push functionality. Discovery within System Center Configuration Manager (Current Branch) has 6 methods listed below: Active Directory Forest Discovery Active Directory Group Discovery Active Directory System Discovery Active Directory User Discovery Heartbeat Discovery Network Discovery When a discovery method successfully finds a new resource, discovery puts information about that resource into a file that is called a discovery data record (DDR), which is processed by a primary or central administration site. Processing of a DDR creates a new record in the site database for newly discovered resources, or updates existing records with the DDRs new information. [source: Technet] Step 1. Enable Active Directory Forest Discovery Note: Perform the following on your ConfigMgr server as a user with Full Administrator permissions in the ConfigMgr console. In the Configuration Manager console, click on Administration and select Hierarchy Configuration, click on Discovery Methods. The first discovery method listed is Active Directory Forest Discovery. This discovery method can be enabled on CAS or Primary site(s). Unlike other discovery methods, Active Directory Forest Discovery does not discover resources that you can manage. Instead, this method discovers Active Directory network locations and can convert those locations into boundaries for use throughout your hierarchy. To discover Active Directory network locations and convert those locations into boundaries open the ConfigMgr console, in the Administration workspace, select Hierarchy Configuration, then select Discovery Methods and right click Active Directory Forest Discovery for the primary site and right click, choose Properties. The General window appears with one option, Enable Active Directory Forest Discovery. Select it and two more choices are revealed: Automatically create active directory site boundaries when they are discovered Automatically create IP address range boundaries for IP subnets when they are discovered. Select the second option and leave the default schedule for every 1 weeks. Tip: Selecting both options above is fine in a LAB. In Production however, you should consider only selecting to discover IP address ranges. For clarification about this point please review this post from Jason Sandys (Enterprise Mobility MVP) about why IP Subnet Boundaries are EVIL Click Apply, you'll be prompted if you want to run a discovery as soon as possible, answer Yes. Tip: If you want to review the discovery of objects via this discovery method, you can use CMTrace to open the ADForestDisc.log file. The log file will be located in in the <InstallationPath>\LOGS folder. When publishing is enabled for a forest and that forests schema is extended for Configuration Manager, the following information is published for each site that is enabled to publish to that Active Directory forest: SMS-Site-<site code> SMS-MP-<site code>-<site system server name> SMS-<site code>-<Active Directory site name or subnet> To verify that you've enabled publishing browse to Administration, Site Configuration, Sites, and check the properties of your Primary site server. Click on the Publishing tab. Step 2. Enable Active Directory Group Discovery Note: Perform the following on your ConfigMgr server as a user with Full Administrator permissions in the ConfigMgr console. You can use Active Directory Group Discovery to search Active Directory Domain Services (AD DS) to identify the group memberships of computers and users. This discovery method searches a discovery scope that you configure, and then identifies the group memberships of resources in that discovery scope. By default, only security groups are discovered. However, you can discover the membership of distribution groups when you select the checkbox for the option Discover the membership of distribution groups on the Option tab in the Active Directory Group Discovery Properties dialog box. When you discover a group, you can also discover limited information about its members. Note: This does not replace Active Directory System Discovery or Active Directory User Discovery and is usually insufficient to build complex queries/collections or to serve as the bases of a client push installation. Active Directory Group Discovery can discover the following information: Groups Membership of Groups Limited information about a groups member computers and users, even when those computers and users have not previously been discovered by another discovery method Tip: This step assumes you want to discover resources recursively in the windowsnoob OU. Therefore, it may be necessary to move servers into their respective OU which is a child OU under the windowsnoob OU created in this guide otherwise they will not be discovered by this discovery method. You can do that via Active Directory Users and Computers on AD1. In the ConfigMgr console, in the Administration workspace, select Hierarchy Configuration, then select Discovery Methods and right click Active Directory Group Discovery and choose properties. Select the option to Enable Active Directory Group Discovery and click on Add to see two more choices, Groups and Location. These options are explained below: Groups: Use groups if you want to search one or more specific Active Directory groups. You can configure the Active Directory Domain to use the default domain and forest, or limit the search to an individual domain controller. Additionally, you can specify one or more groups to search. If you do not specify at least one group, all groups found in the specified Active Directory Domain location are searched. Location: Use a location if you want to search one or more Active Directory containers. This scope option supports a recursive search of the specified Active Directory containers that also searches each child container under the container you specify. This process continues until no more child containers are found. Note: When you configure a discovery scope, select only the groups that you must discover. This is because Active Directory Group Discovery attempts to discover each member of each group in the discovery scope. Discovery of large groups can require extensive use of bandwidth and Active Directory resources. Select Location from the drop down menu. Give it a name like Active Directory Group Discovery - P01 and select browse to decide where to recursively search. In this example I select the previously created windowsnoob Organizational Unit (OU) which will contain your servers, users, computers and devices. Click on the Polling schedule tab and decide what is appropriate for your setup, the default is 7 days for a full Active Directory Group Discovery and you can enable Delta Discovery (enabled by default). This discovery method finds resources in Active Directory Domain services that are new or modified since the last discovery cycle in the time interval specified (default is 5 minutes). Next, you can review the three options on the Options tab and click Apply when ready and answer Yes to running the full discovery. Tip: If you want to review the discovery of objects via this discovery method, you can use CMTrace to open the adsgdis.log file. The log file will be located in in the <InstallationPath>\LOGS folder. Step 3. Enable Active Directory System Discovery Note: Perform the following on your ConfigMgr server as a user with Full Administrator permissions in the ConfigMgr console. Use Configuration Manager Active Directory System Discovery to search the specified Active Directory Domain Services (AD DS) locations for computer resources that can be used to create collections and queries. You can then install the client to discovered computers by using client push installation. To successfully create a discovery data record (DDR) for a computer, Active Directory System Discovery must be able to identify the computer account and then successfully resolve the computer name to an IP address. By default, Active Directory System Discovery discovers basic information about the computer including the following: Computer name Operating system and version Active Directory container name IP address Active Directory site Last Logon Timestamp In the ConfigMgr console, in the Administration workspace, select Hierarchy Configuration, then select Discovery Methods and right click Active Directory System Discovery and choose Properties, place a checkmark in Enable Active Directory System Discovery. Click on the yellow starburst to add some Active Directory containers. For path click on browse and browse to the location you want to discover systems in. Tip: You can add several locations by repeating this process and selecting different locations, but only add the locations you need to add as you don't want to generate unnecessary network and CPU bandwidth. On the Polling schedule tab, stick to the defaults and then select the Active Directory Attributes tab, if you want to add an attribute to discover select one from the list and choose Add >> in the example below you are adding an Active Directory attribute called msTPM-ownerinformation. There are many attributes to choose from, use only the ones you need to get your job done. and click Apply and Ok and answer Yes to run a full discovery as soon as possible. Tip: If you want to review the discovery of objects via this discovery method, you can use CMTrace to open the adsysdis.log file. The log file will be located in in the <InstallationPath>\LOGS folder. Step 4. Enable Active Directory User Discovery Note: Perform the following on your ConfigMgr server as a user with Full Administrator permissions in the ConfigMgr console. Use Configuration Manager Active Directory User Discovery to search Active Directory Domain Services (AD DS) to identify user accounts and associated attributes. You can view the default list of object attributes returned by Active Directory User Discovery, and configure additional attributes to be discovered in the Active Directory User Discovery Properties dialog box on the Active Directory Attributes tab. By default, Active Directory User Discovery discovers basic information about the user account including the following: User name Unique user name (includes domain name) Domain Active Directory container names In the ConfigMgr console, in the Administration workspace, select Hierarchy Configuration, then select Discovery Methods and right click Active Directory User Discovery and choose Properties. Place a checkmark in Enable Active Directory User Discovery as shown below. Select the Enable Active Directory User Discovery box and click on the yellow starburst to add some active directory locations to discover users. You can configure the Polling tab and Active Directory Attributes tab settings if you wish, then click apply and answer yes to Run a Full Discovery now. Tip: If you want to review the discovery of objects via this discovery method, you can use CMTrace to open the adusrdis.log file. The log file will be located in in the <InstallationPath>\LOGS folder. Step 5. Review what has been discovered in the console Note: Perform the following on your ConfigMgr server as a user with Full Administrator permissions in the ConfigMgr console. In the ConfigMgr console, in the Assets and Compliance workspace, select Users, then select All Users, the discovered Users should appear. In the Assets and Compliance workspace, select All User Groups, the discovered User Groups should appear. In the ConfigMgr console, in the Assets and Compliance workspace, select Devices, then select All Systems, the discovered Systems should appear. Note: If you are wondering why AD1 does not appear it is because that server is placed under the Domain Controllers container and that container path was not added to any system discovery method. Summary In this guide you configured Discovery methods in System Center Configuration Manager (Current Branch) to discover resources that you want to manage. In the next part of this new series you will configure Boundaries. until next time, adios and thanks for reading. Related Reading Run discovery for System Center Configuration Manager - https://technet.microsoft.com/en-us/library/mt621991.aspx Downloads You can download a Microsoft Word copy of this guide (dated 2015/12/17) here: Configuring Discovery for System Center Configuration Manager (Current Branch).zip Next Post > Configuring Boundaries
-

Windows 10 Deployment with Integrated MDT Task Sequence Fails
anyweb replied to allenr74's question in Deploying Operating Systems
attach the logs here so we can see- 3 replies
-
- Windows 10
- SCCM 2012 R2 SP1
-
(and 1 more)
Tagged with:
-

need to install internet explorer 11 by group policy
anyweb replied to mohd aamir's topic in Configuration Manager 2012
try this link instead http://lmgtfy.com/?q=+install+internet+explorer+11+by+group+policy -

install host file to all system by sccm
anyweb replied to mohd aamir's topic in Configuration Manager 2012
look at this https://www.windows-noob.com/forums/topic/2758-how-can-i-copy-files-from-a-package/ -
We received a report from a user of an unusual alert from their anti-malware software, where it appeared that a domain known to host malicious JavaScript was accessed from a Windows-Noob page. An analysis at the time did not detect any unusual changes to the forum software and concluded that the most likely scenario was a malicious advertisement in the Google/DoubleClick ecosystem. At this time, the skins for the IP.Board software were re-cached as a precaution. Some time later, some proxy servers' content categorisation system began to categorise Windows-Noob.com as "Suspicious". We were frustrated at the time to have little to no further information as to why this was the case. Only one of the website scanners we used to try and externally determine if there was an infection showed an issue: it had "Detected reference to malicious blacklisted domain myitforum.com". This domain obviously is quite legitimate, but had been compromised in the past, as have many websites that accept user generated content. We were assured that the infection issue on myitforum.com had been resolved, but in an effort to remove the "Suspicious" category from Windows-Noob.com, removed all outbound links to myitforum.com from our site. We did not at this stage connect the earlier report and this issue. None of the highly respected external systems like Google Webmaster Tools at any point suggested that we had been infected, and the 'detection' was limited to this one website scanner, which gave us these results referencing myitforum.com. Later still, we received another report from a user that their browser had been redirected to a malicious domain after visiting Windows-Noob from a search engine result page. We also finally received detailed information from the proxy server categorisation system provider that gave specific detail as to our “Suspicious” categorisation. A packet capture on the Windows-Noob server was taken over a few hours and then analysed. With the reported information from the user, we quickly identified injected JavaScript based on the reported malicious domain. The injected JavaScript was located in the theme cache files and was removed. Additional aggressive monitoring was put in place to try and determine if there was an active entry vector for the attacker. Later on that evening, malicious JavaScript re-appeared, detected by our additional monitoring that was put in place, and we promptly removed it again. Detailed analysis, including log file and packet capture analysis was performed to try and determine the attack vector, but no promising leads were found. The injected JavaScript then did not re-appear after that second appearance, and we unfortunately remain in the dark as to how the attack occurred. Our improved monitoring systems remain in place. The code, once unpacked and analysed, was actually quite rudimentary and simply injected references to the malicious JavaScript if certain conditions were met (user was referred from a search engine result page, and using certain browsers). Extensive reviewing of log files revealed no evidence of any other intrusion, but we accept that given our lack of understanding of the original attack vector, we cannot determine if any other actions were taken. Because we were unable to determine with confidence the source of the injected JavaScript and the attack vector used, we took the step of a complete server reinstall from known good media. The forum software has been completely reinstalled from a fresh download of the IP.Board software and all old and non-essential files removed. At the same time, we have taken other steps to protect users, including implementing mandatory HTTPS across the site (long overdue!), which would have, in this scenario, prevented injected JavaScript on HTTP domains executing in users' browsers and also protects passwords in transit. We apologise to users that this happened and particularly that we didn't spot it quickly enough. We hope as fellow IT professionals you appreciate the challenges in defending complex systems that are exposed to the world, especially on a very modest budget. We have learned a lot from this incident, despite the frustration of not knowing the original attack vector, and will continue to work hard to do better. It is a good idea, given what has happened, to reset your password for this site. This will also have the effect of invalidating the passwords that used to transit in the clear over HTTP and mean that your new password will not have traversed the public internet unencrypted. The standard advice about also resetting any other password that you might have shared with this site applies too.
-
- 1
-

-

W10 Ent Upgrade to build 10586
anyweb replied to Siroj's topic in System Center Configuration Manager (Current Branch)
yeah the errors you are seeing is what everyone else is seeing so we have to wait for a fix from microsoft I guess. -

install host file to all system by sccm
anyweb replied to mohd aamir's topic in Configuration Manager 2012
why not let Active Directory DNS do it's job ? why do you want to copy this file to every system, please explain -

W10 Ent Upgrade to build 10586
anyweb replied to Siroj's topic in System Center Configuration Manager (Current Branch)
it seems that EDU and ENT editions are not available in WSUS/SUP yet, so i'd suggest you wait, the ones that currently are there don't work properly either, see my bug on Connect here. -
thanks 1. use the Windows 10 USMT package for your task sequences and you should be fine. 2. you've used the 1511 Windows 10 adk which is why your version is 10586, you can uninstall that ADK and use the original Windows 10 ADK instead which doesn't suffer from the issues mentioned in the post after yours.
-
first things first you cant upgrade from cu5 now because you've already upgraded to SP1 (or sp2 depending on how you look at it) as regards your console not connecting, have you tried installing the console directly from the sp1 media ? would you like me to do a teamviewer session to your computer to have a look ?
-
hi guys, please take a moment to read this uservoice, I can see a lot of people gettng problems due to this requirement and it's not checked for currently - if you vote for this then it's likely that Microsoft will fix it:- https://configurationmanager.uservoice.com/forums/300492-ideas/suggestions/10997490-modify-the-configuration-manager-prerequisites-che thanks ! cheers niall
-

Deploying apps via UDI - Issues!
anyweb replied to MorsePacific's topic in Configuration Manager 2012
search for smsts*.log and app*.log and attach them here zipped (for starters) -
are you running the script as system or as the logged in user, by the sounds of it you are running it as system when you should be running it as the logged in user...
- 2 replies
-
- windows 8.1
- sccm 2012
-
(and 2 more)
Tagged with:
-
I hope you are aware that this software (System Center Configuration Manager version 1511) went GA yesterday, it takes a lot of time (and effort) to write the guides ! you have a number of options, do a site backup (content and db) and then install the new site with the same computer name, once installed do a site restore, or use the migration feature to migrate what you want from one site to the other. The following guide should give you enough ideas of how a migration is done. http://www.windows-noob.com/forums/topic/4926-using-sccm-2012-rc-in-a-lab-part-14-performing-a-side-by-side-migration-from-configuration-manager-2007/ I'm separating your post into it's own topic.
-

SCCM 2012 R2 SP1 upgrade to Config Manager
anyweb replied to SKCalgary's topic in Configuration Manager 2012
while Server 2008 R2 is currently supported, it is deprecated and planned to be removed from support in 12 months with SCCM current branch. See https://technet.microsoft.com/en-us/library/mt628077.aspx.