-
Posts
9253 -
Joined
-
Last visited
-
Days Won
369
Everything posted by anyweb
-
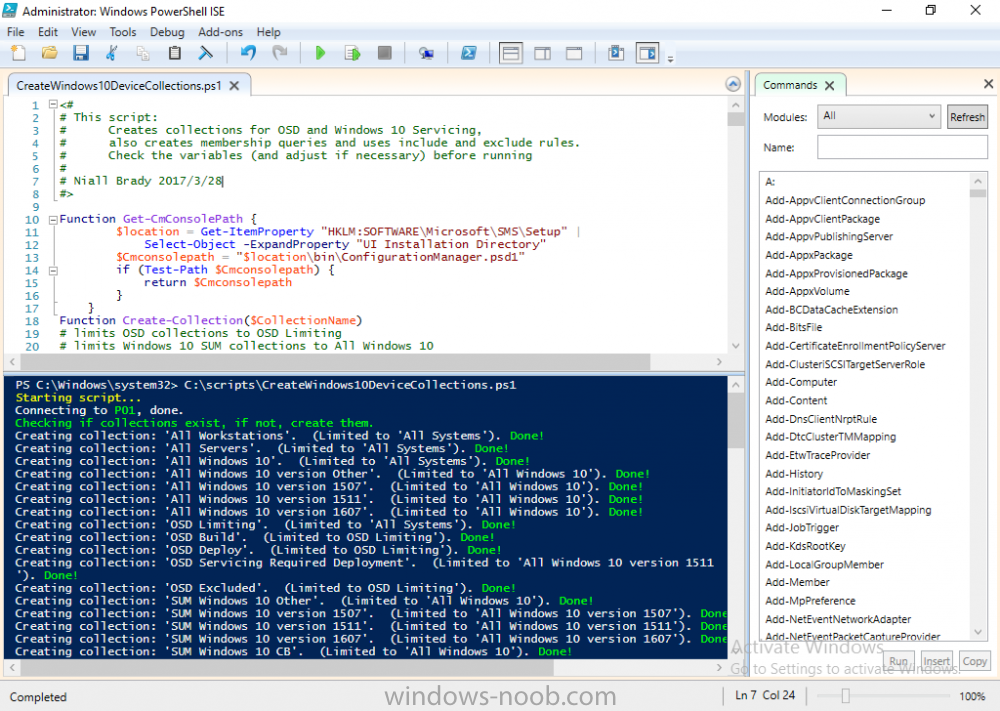
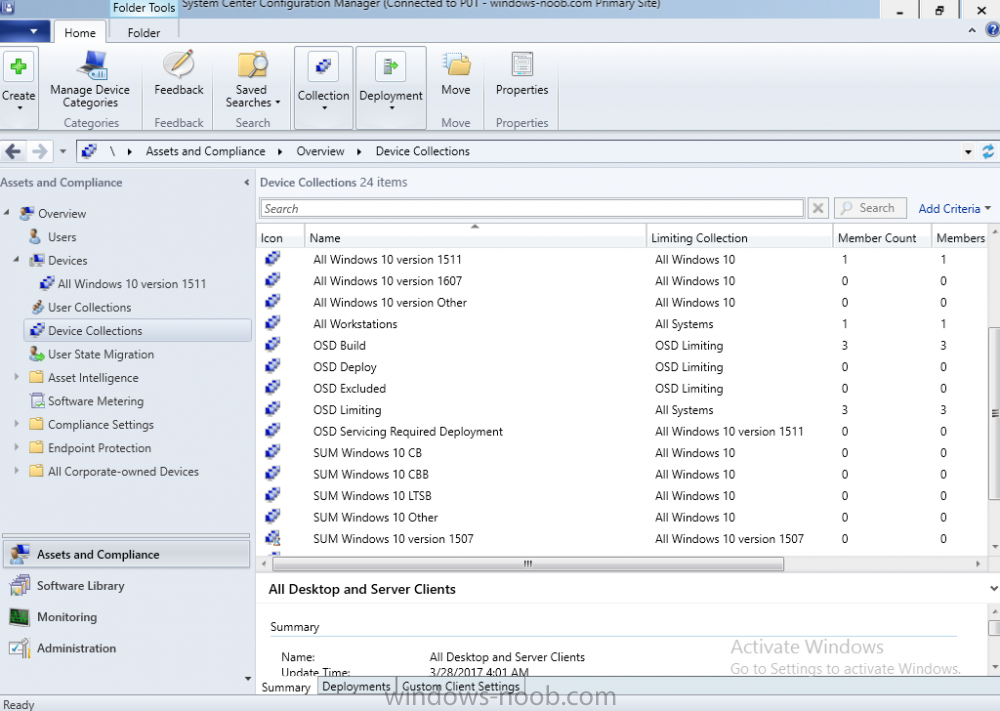
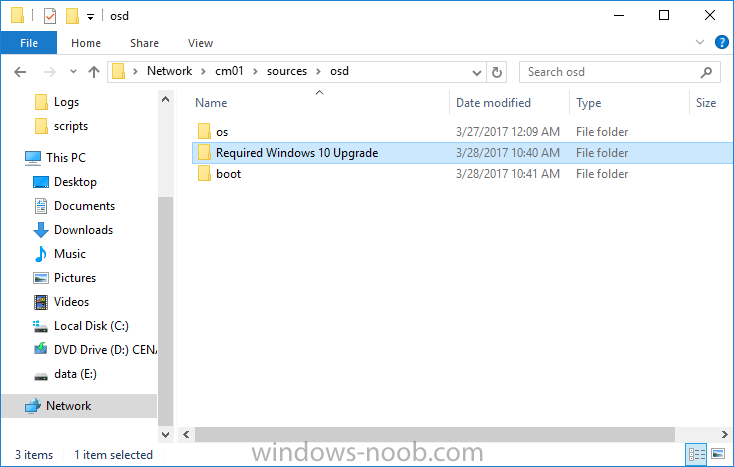
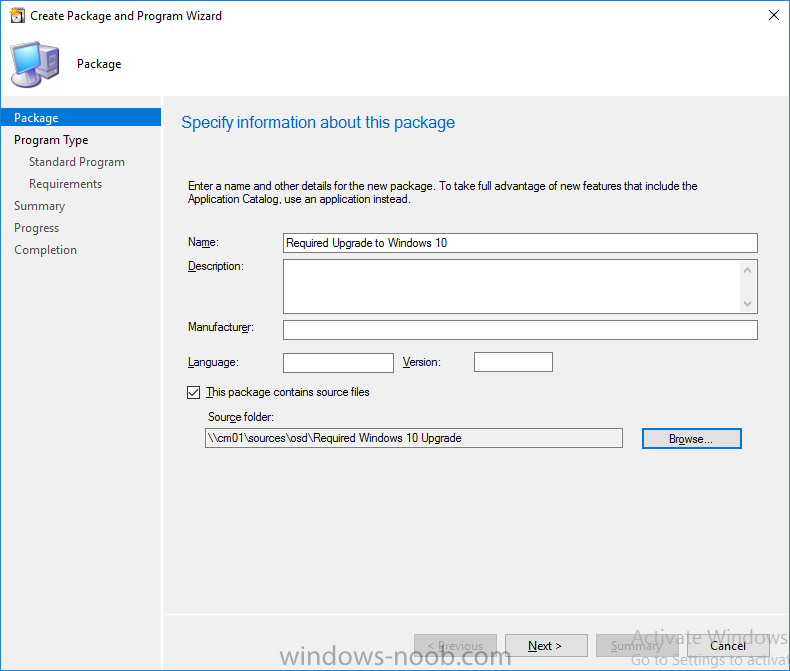
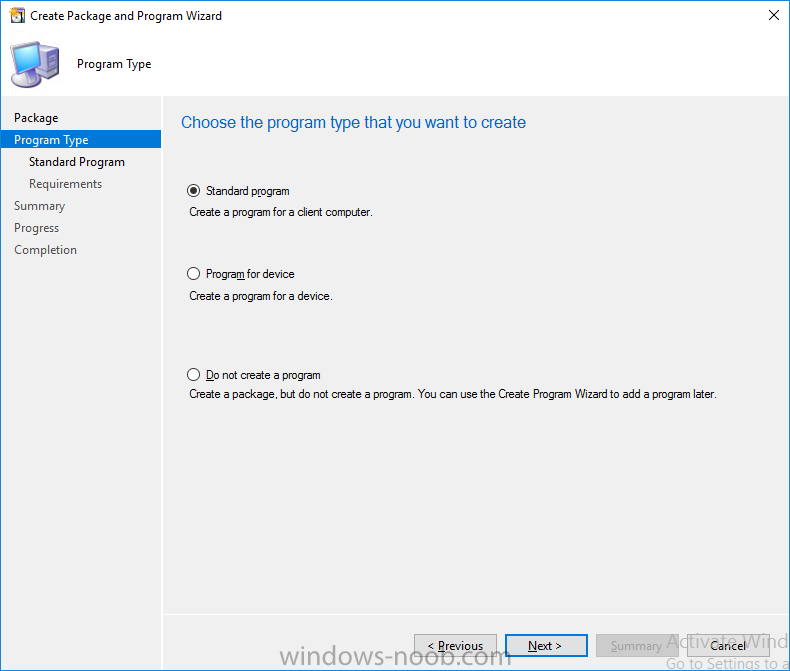
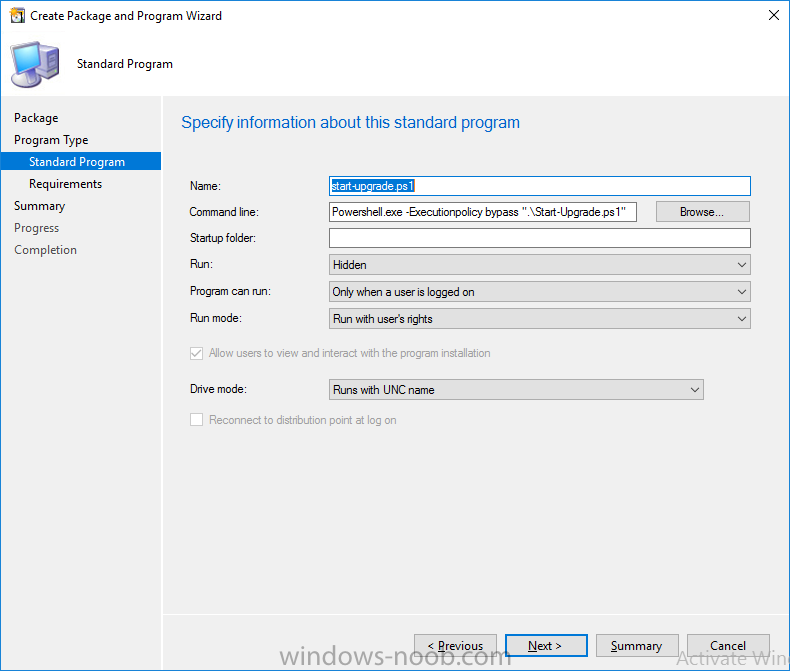
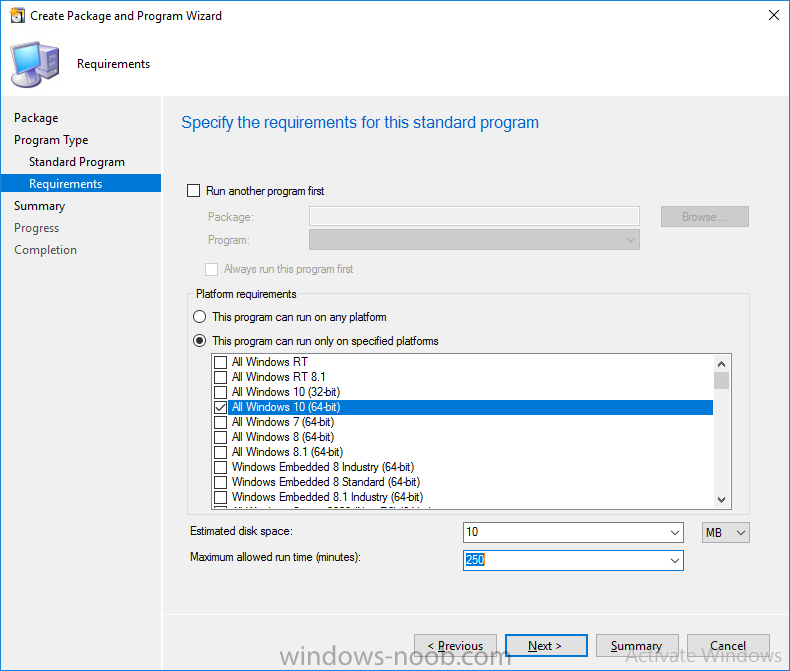
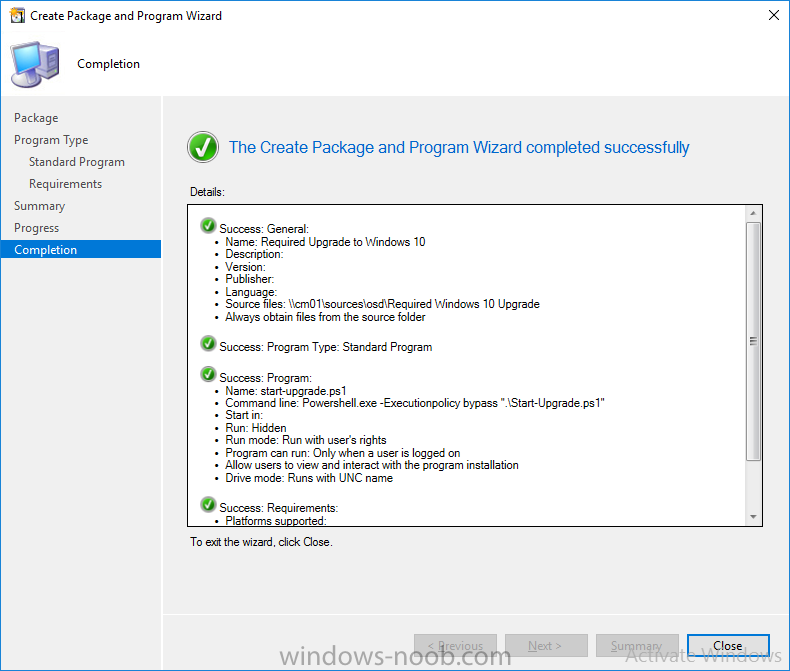
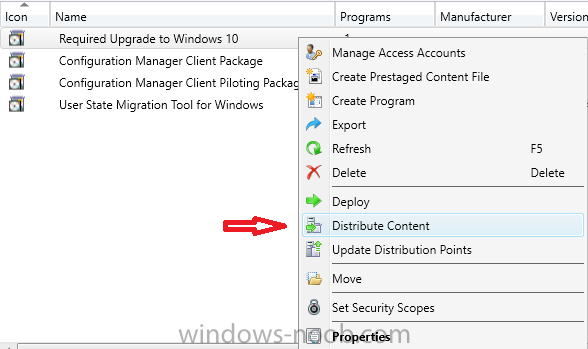
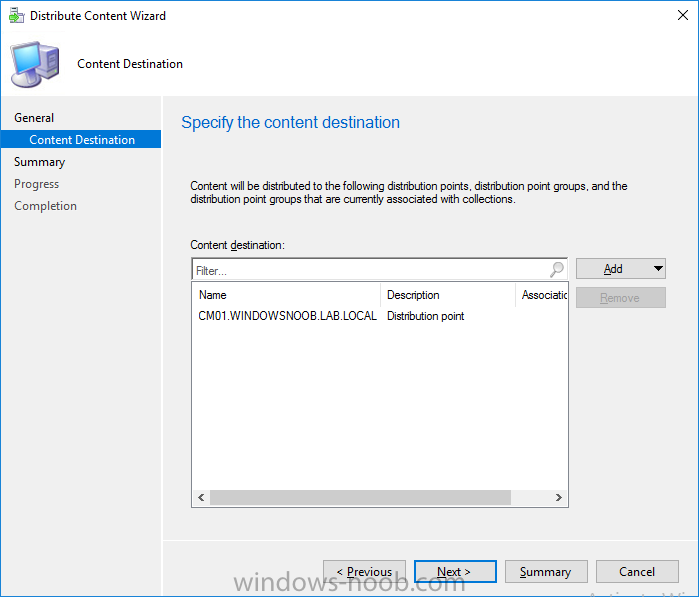
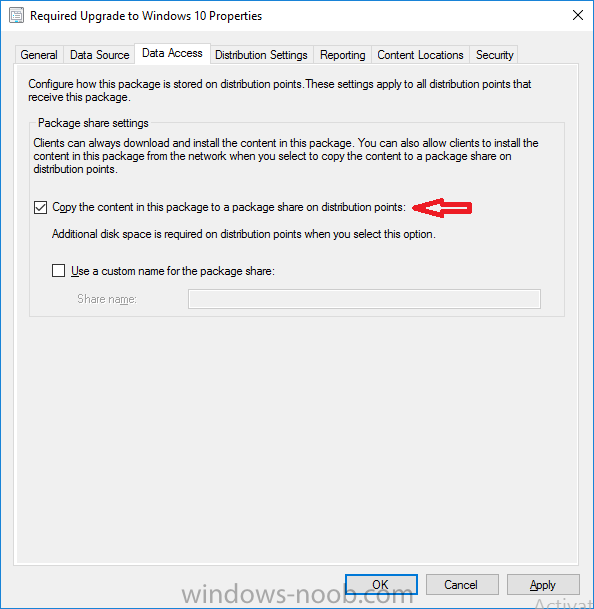
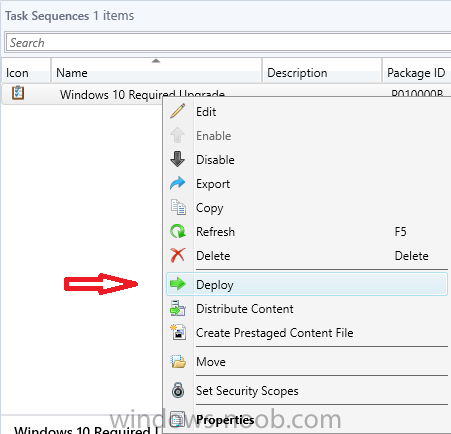
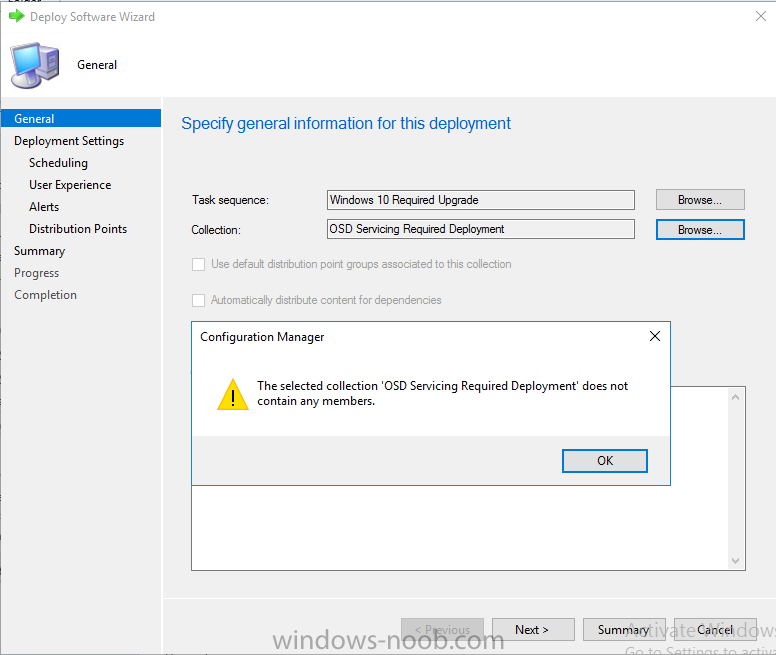
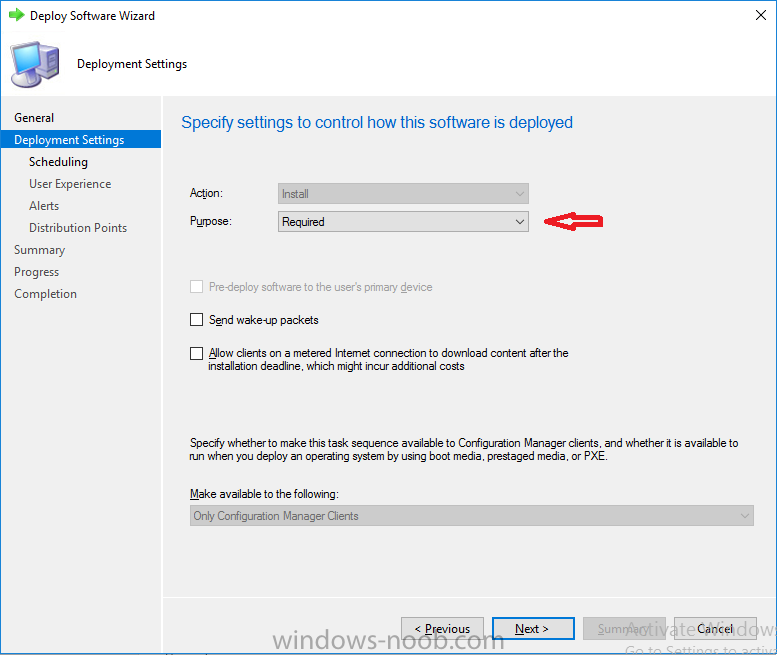
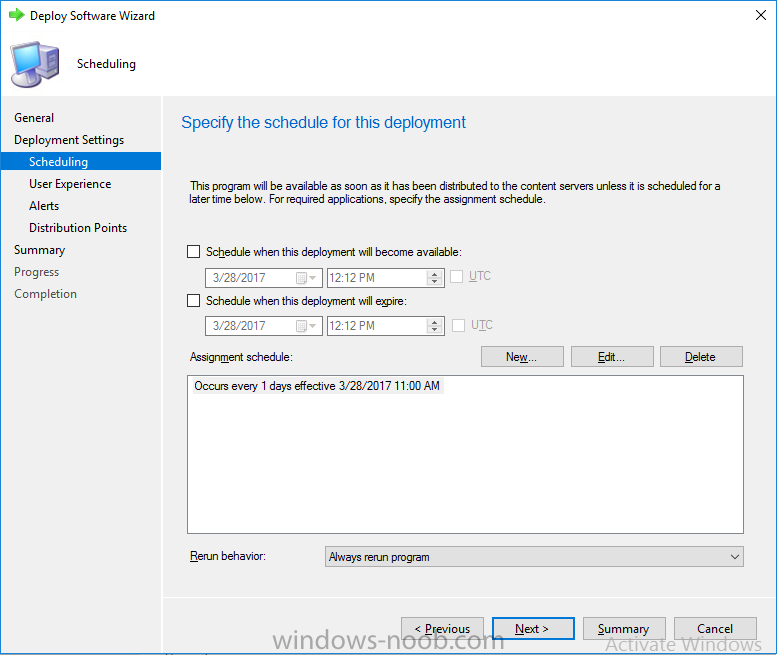
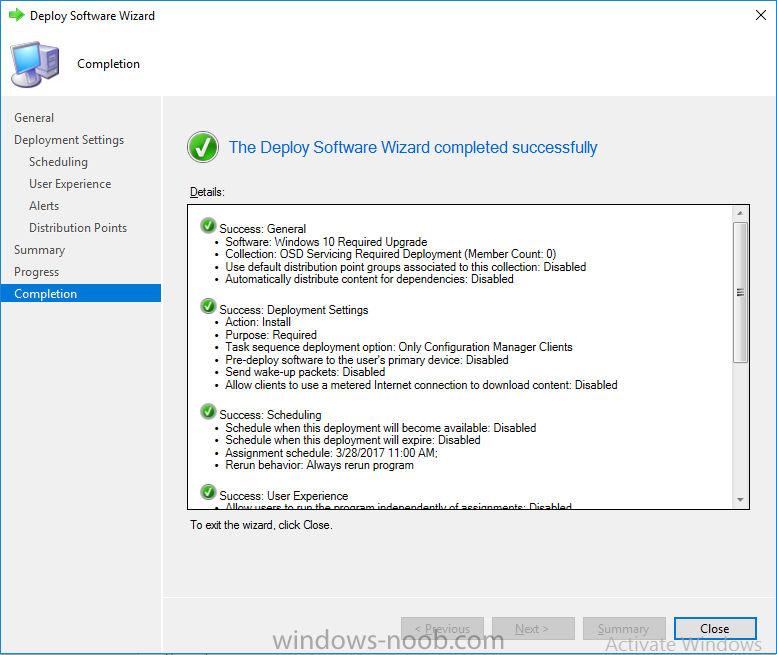
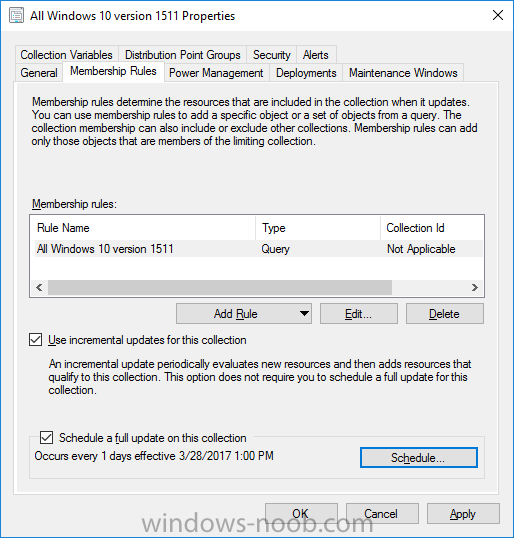
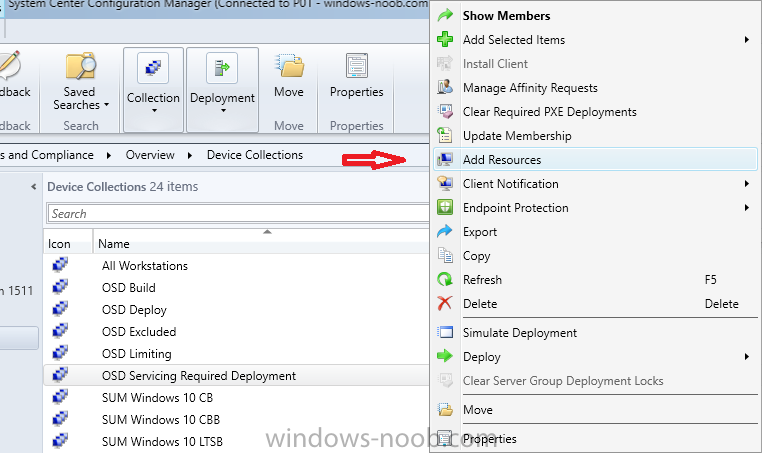
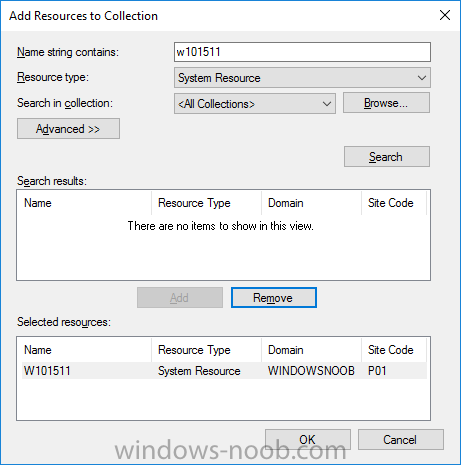
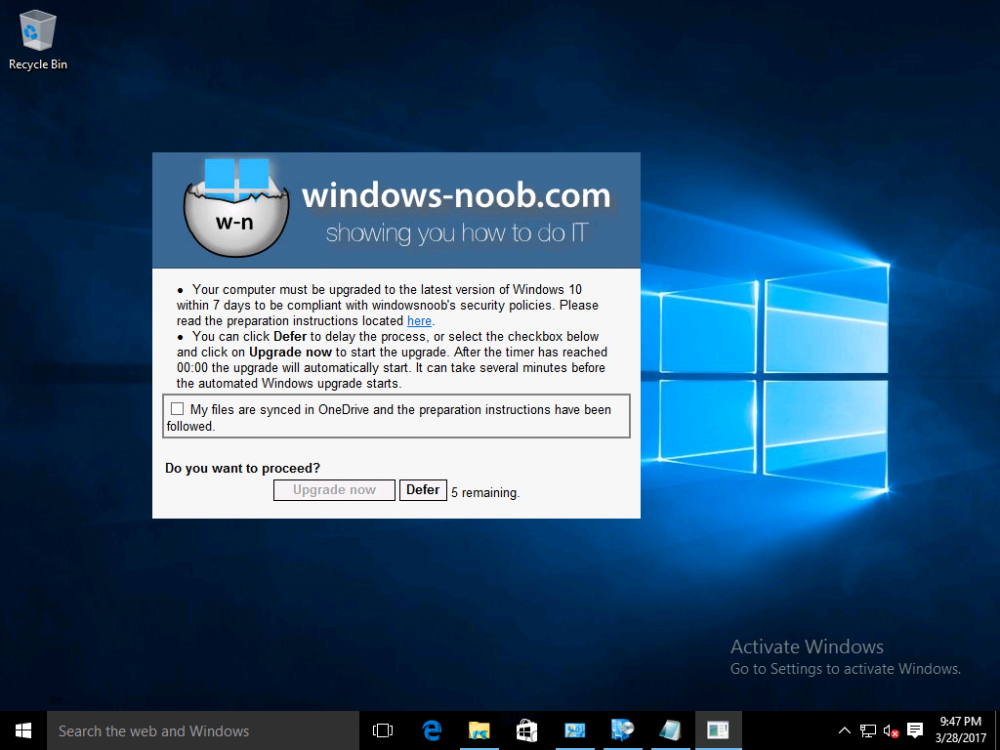
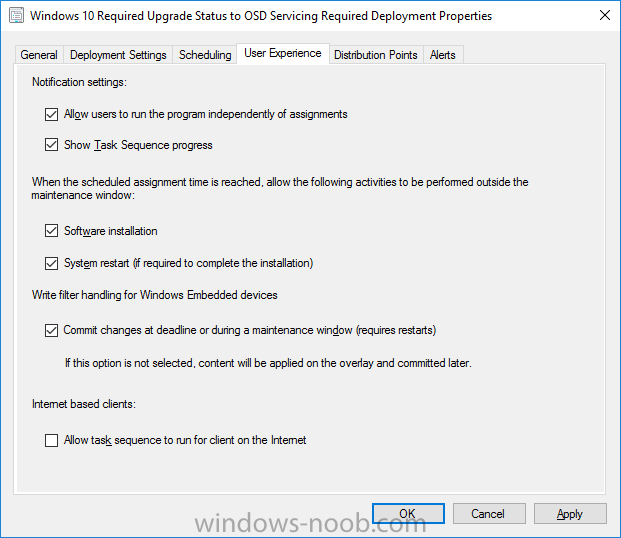
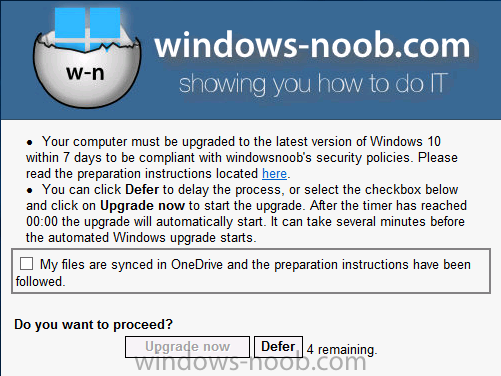
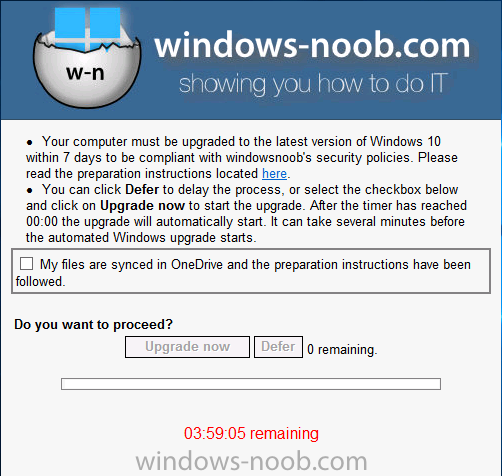
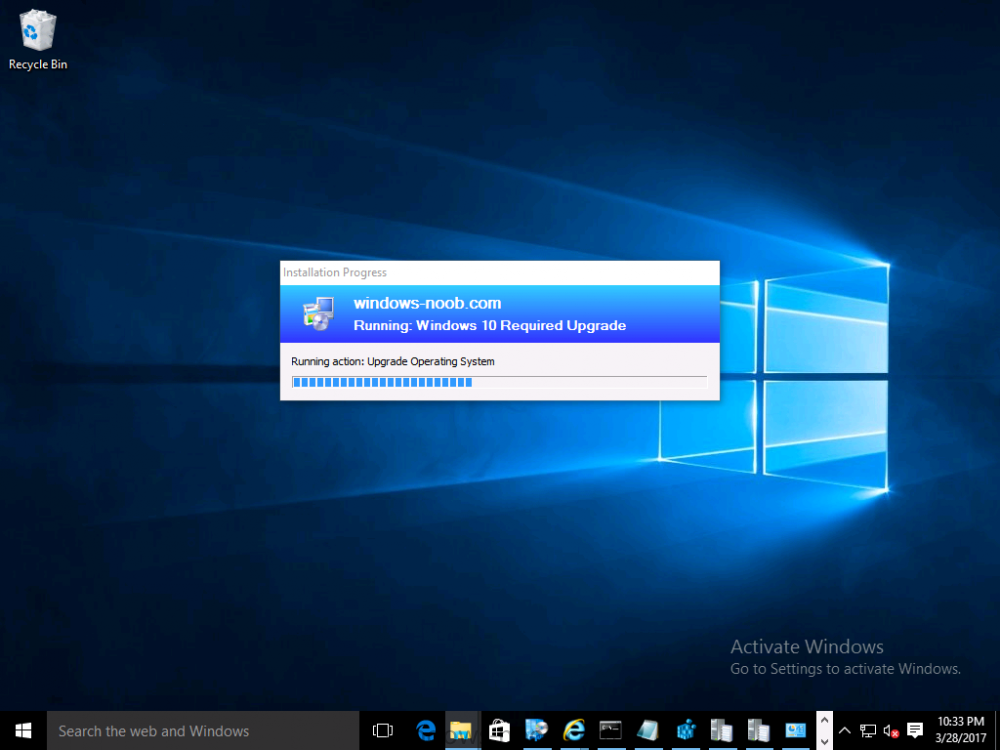
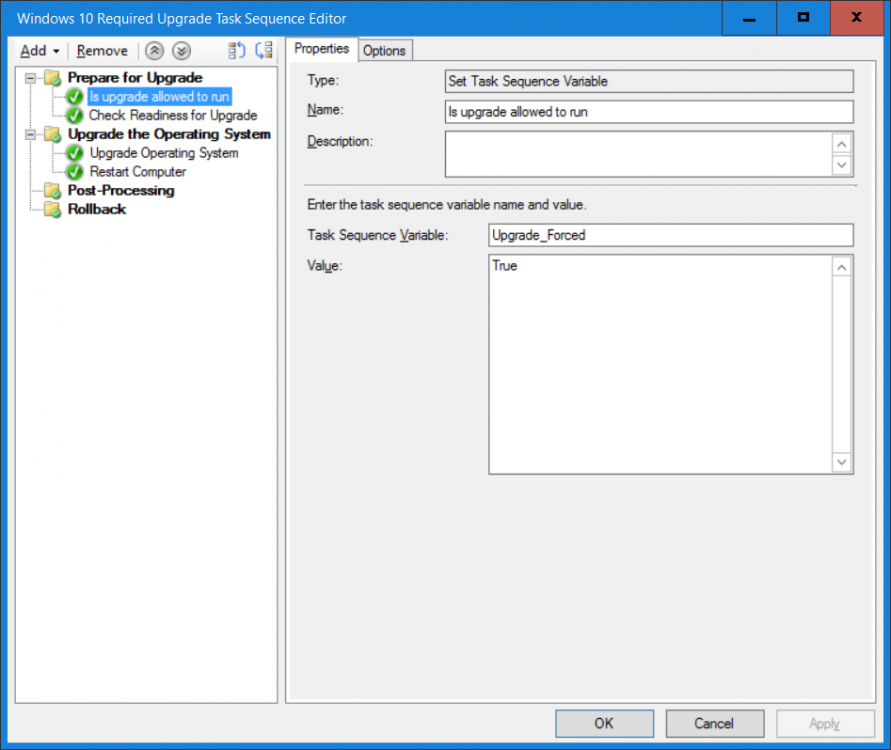
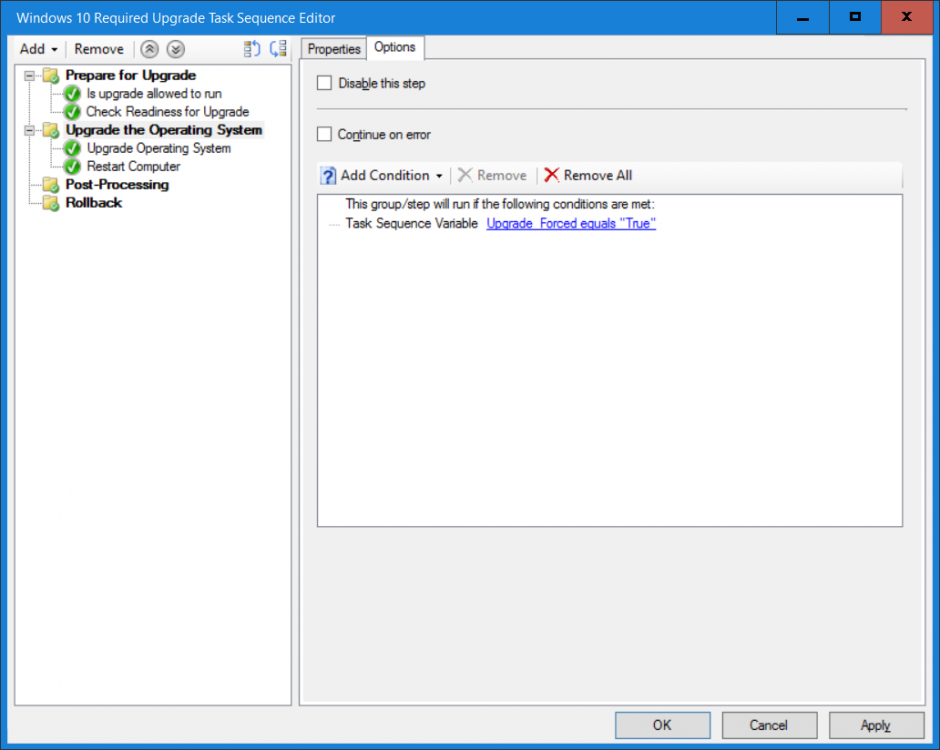
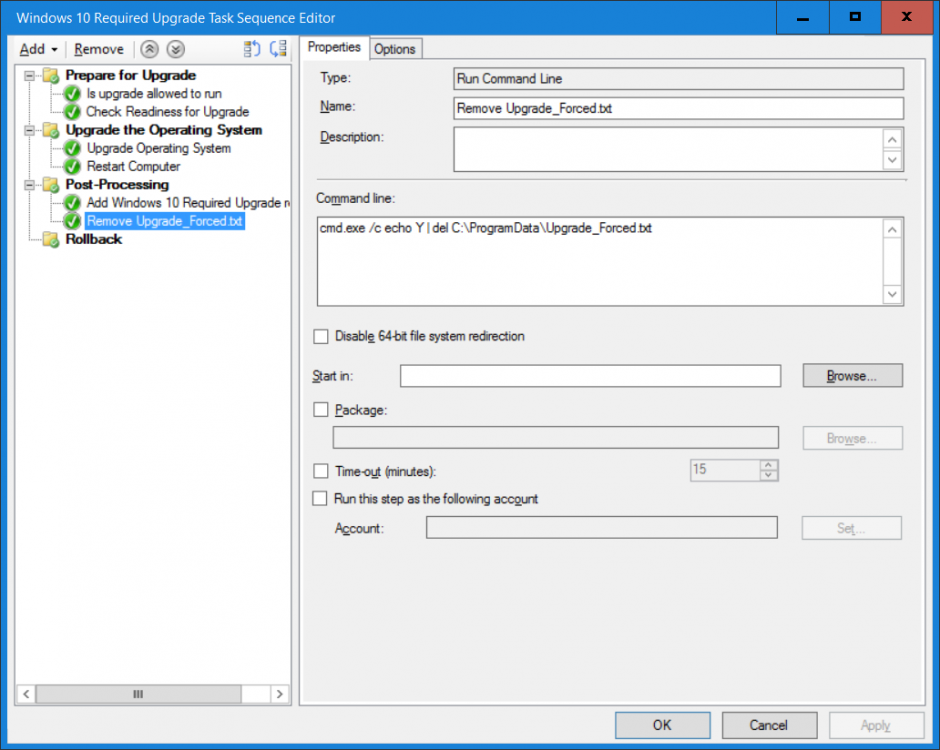
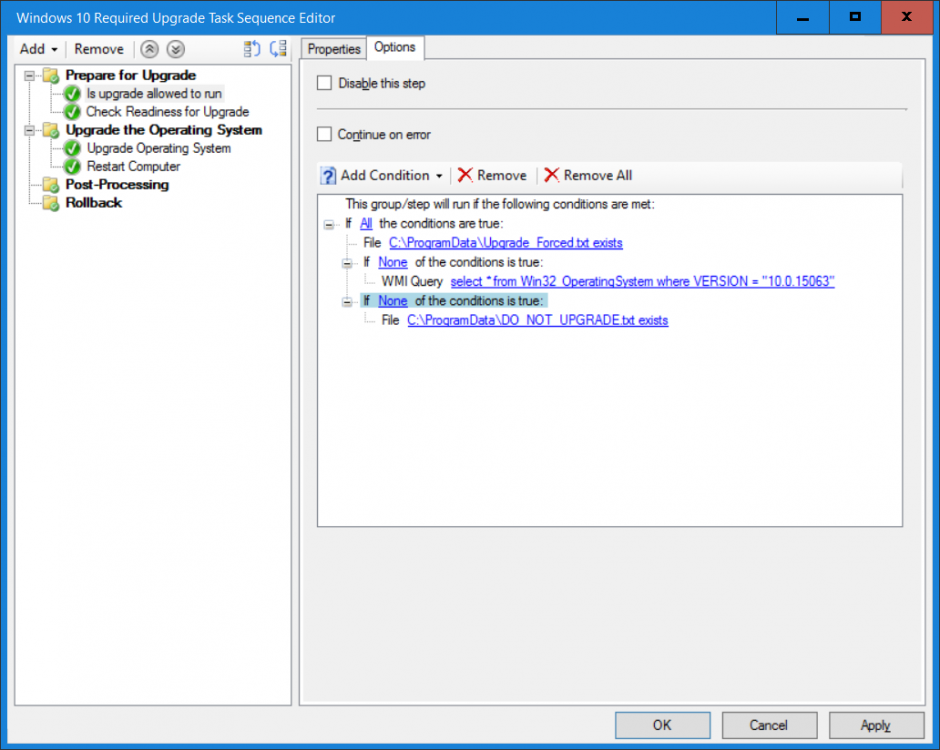
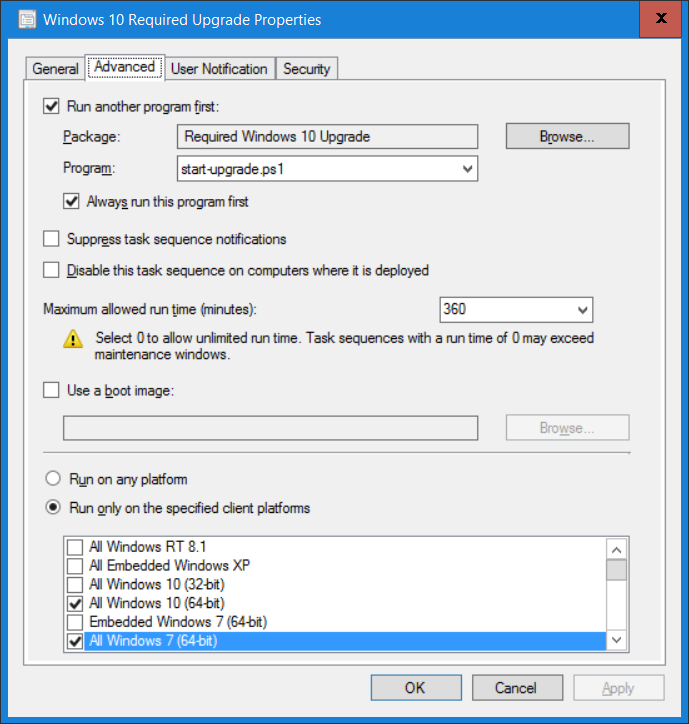
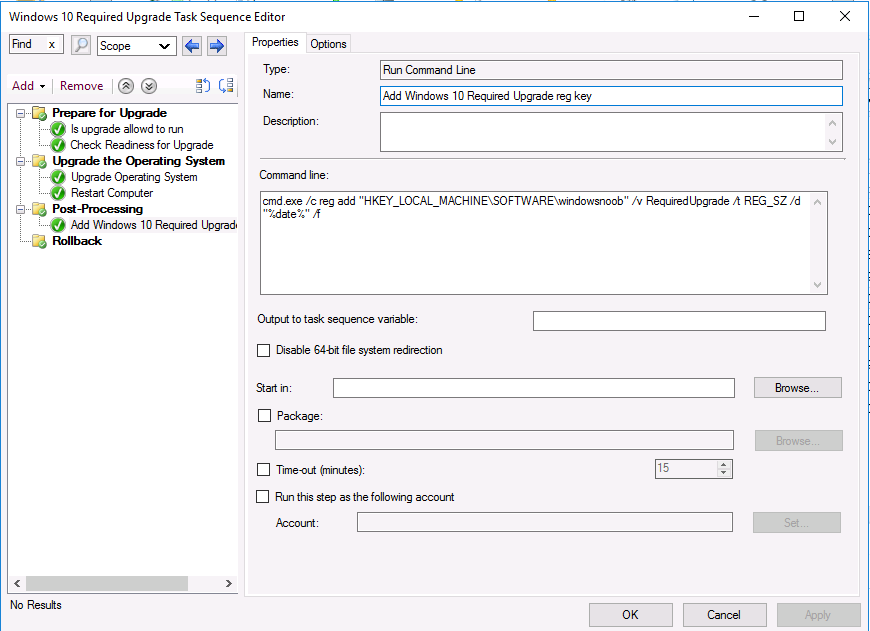
Note: I've upgraded the wrapper to PowerShell 2019/01/06 as explained here. Introduction This blog post is all about upgrading to Windows 10, either from Windows 7 or from an earlier release of Windows 10 to the latest release of Windows 10. Windows 10 is probably one of the fastest developing operating systems from Microsoft yet, and was initially released in July 2015 as Windows 10 version 1507. The version 1507 nomenclature equates to (YYMM) or year year, month month so you'll always know when a version was released to manufacturing (declared RTM). So far we've seen the following Windows 10 mainstream versions (not including LTSB/LTSC) Windows 10 version 1507 Windows 10 version 1511 Windows 10 version 1607 Windows 10 version 1703 Windows 10 version 1709 Windows 10 version 1803 Windows 10 version 1809 As each new version of Windows 10 is released, the new features it contains ensure that it is desirable to some and it's just a matter of time before people want to upgrade to that version given the chance, but even with all the latest and greatest features, some users just won't upgrade if given the choice for whatever reason. There is however another element to consider and that how long Microsoft will release security updates for any given release of Windows 10 (i.e. how long is that release supported by Microsoft). Michael Niehaus discusses simplifying Windows As A Service (WAAS) here but in a nutshell there is an 18-month servicing timeline for each release however, Microsoft have added an additional 6 months to ease your pain, for now. Update: In September 2018, Microsoft blogged the following after years of listening to customers complaining about the WAAS support lifecycle. In a nutshell, there are two main releases of Windows 10 for the Enterprise to think about going forward, the 03 releases (18 month support) and the 09 releases (30 months support). Based on that statement alone, Enterprises will most likely opt for the 09 releases to avoid disruption to business and to their end users. This leads you to deal with the security support ability in a couple of ways, you can make the new upgrade available in Software center and hope your users will upgrade (seriously do you think they will ?), or you can get tough and decide when and where they will upgrade. To do that you have two options: servicing plans task sequences I've discussed servicing plans here so I won't go over that subject again, they are a valid option for many but are not very dynamic. With task sequences you have far greater control over how to deal with things that can break servicing plans (such as incompatible AntiVirus software or Windows Language packs). Assuming that you've made the choice to use task sequences to forcefully upgrade your computers to the next version of Windows the next problem is how do you force the upgrade. The answer is defined by the purpose of the task sequence deployment, namely Required (or mandatory). Just mentioning the words Required and Task Sequence is usually enough to make any seasoned ConfigMgr admin shiver. Why ? well there are many cases of people who've had career changing events in relation to required task sequences, therefore using them must come with a big fat warning, so here it is. WARNING! Using required task sequences is risky! Use them with extreme care and always test thoroughly. Disclaimer: if you choose this method and it all goes wrong, I'm sorry, I cannot accept liability. In this guide I show you how to set it up in a safe way and I include a 'get out of jail free' in case you make a mistake. It's up to you to test what works in your organization and what doesn't. My advice is that you test this thoroughly in a lab and once you are happy with the results, recreate it in production and continue to test it thoroughly. Also, be very careful about how you add computers to the required collection especially if it involves queries. Note: The Get out of Jail free step will help to secure your environment towards any accidental upgrades. Now that that is out of the way, let's get on with it. In this post I'll show you one way of forcefully upgrading your computers from a soon to be unsupported version of Windows 10 to the latest and greatest, and I'll include steps and advice to help you 'protect' yourself from disaster. In this guide we'll be forcing our source Windows 10 version 1511 computers to upgrade to the target Windows 10 version 1607. Note: you can always change the target Windows 10 version to whatever build you want (using the TargetBuild variable) as described in the Troubleshooting section at the end of this guide. Notifying users There is one other thing to consider about required task sequences, they are normally for all intents and purposes zero touch meaning no user interaction. That is fine for simple quick changes such as upgrading applications but if your users are going to have one or two hours downtime due to a forced Windows upgrade, you'll want to notify them and give them options to defer for a limited time period to a time that makes sense for them. In this guide I assume that the client setting Show notifications for new deployments in Computer Agent is set to No, that is a common client setting in organizations as it means less annoyances for the end user and of course there are other ways to notify a user about mandatory actions (PowerShell Application Deployment Toolkit for example). The recently released System Center Configuration Manager (Current Branch) version 1702 contains a great ability to edit the user notification message shown to users but it's limited in ability and it depends on your configured notification settings. So how do we solve that problem in a nice way. ConfigMgr allows us to chain programs before the task sequence begins and that's the key to this solution. Step 1a. Get out of jail free (recommended) The wrapper will not allow the HTA to display if a file called DO_NOT_UPGRADE.txt is present in C:\ProgramData. If you are paranoid about accidental upgrades (and you should be if using required task sequences) then do as follows. 1. Create a package (with no content) with a program to deploy a text file to all computers that are at risk of accidental deployment. Run the package daily. The program is simply a one liner as follows: cmd.exe /c echo "Windows 10 Required Upgrade" > C:\ProgramData\DO_NOT_UPGRADE.txt 2. Target the OSD Servicing Required Deployment collection with another package/program that will remove the Do_NOT_Upgrade.txt file. Run the package every 2 hours. The program is again a one-liner, as follows: cmd.exe /c echo "Y" | del C:\ProgramData\Do_Not_Upgrade.txt The above actions should protect your computers from accidentally being targeted by the task sequence. Any computer that has the Do_NOT_Upgrade.txt file present, will not show the popup (HTA) and will not run the task sequence and thus, will not upgrade until you are ready to do so. Step 1b. Create some collections (optional) This step is optional but recommended as it will give you a base of collections to manage your deployments. To complete this step download the CreateWindows10DeviceCollections.ps1 PowerShell script in the downloads section and run it as Administrator in PowerShell ISE as shown below. This script not only creates collections to make your job of finding different versions of Windows 10 easier, but it adds queries, include and exclude rules as necessary. and below is a subset of the collections created (there are 18 in total). The OSD Servicing Required Deployment collection is limited to Windows 10 version 1511 as that is our target for the required upgrade. This does not mean that it will use all computers in that collection it just means it will only use computers added to the OSD Servicing Required Deployment collection provided that they are also present in All Windows 10 version 1511. This ensures that you are targeting the correct version of Windows 10 for the required upgrade. Step 2. Create a Package/Program In this step you'll add a simple package/program that contains a few scripts. These scripts have error checking, logging and more built in so that you can trace what was done and when. These scripts will be chained to the required task sequence meaning that they must run successfully (with an exit code of 0) before the actual task sequence can start. User actions such as Defer in the popup will force an exit code 99 and the task sequence cannot start. Download the scripts in the downloads section and extract somewhere useful. Copy the Required Windows 10 Upgrade folder to your source folder on your ConfigMgr server. In the ConfigMgr console, select Application Management, Packages and Create Package. Give the new package a suitable name such as Required Upgrade to Windows 10 and point it to the source folder. For Program Type, choose Standard Program. In the Specify information about this standard program screen fill in the following details, Note: keep in mind that if you set Program can run Only when a user is logged on that that becomes a requirement, i.e. that a user must be logged on in order for this to run. You may want to get even tougher and set the Program can run option to Whether or not a user is logged on. If you do set it to Whether or not a user is logged on, and if the user is not logged on, the scripts will write to HKEY_USERS\.DEFAULT\Software\windowsnoob and you may need to update the scripts to detect this change. Name: start-upgrade.ps1 Command line: Powershell.exe -Executionpolicy bypass ".\Start-Upgrade.ps1" Startup folder: Run: Hidden Program can run: Only when a user is logged on Run mode: Run with user's rights Drive Mode: Runs with UNC name Note: If your target computers are running Windows 7, then place a check mark in the All Windows 7 (64 bit) box also. in the Specify the requirements for this standard program screen use the following values This Program can run on only on specified platforms: All Windows 10 (64 bit) Estimated disk space: 10 MB Maximum allowed time (minutes): 250 click next through to completion. Step 3. Modify the package On the newly created package, right click and choose Properties, click the Data Access tab. Select Copy the content in this package to a package share on distribution points Click Apply and OK. Step 4. Distribute the package to your distribution points Right click the package and choose Distribute Content select your distribution points and continue through the wizard until completion Step 5. Modify an existing Windows 10 Required Upgrade task sequence In this step I'll assume you've already created your Windows 10 Required Upgrade task sequence. If you haven't already then take a look at this post to see how. Locate the task sequence in the ConfigMgr console, right click and choose Properties, in the Advanced tab place a check mark in Run another program first and select the Windows 10 Required Upgrade program. In the Run only on the specified client platforms screen select All Windows 10 (64 bit). Note: Make sure that Always run this program first is checked. Note: If your target computers are running Windows 7, then place a check mark in the All Windows 7 (64 bit) box also. Next, edit the task sequence and add a new Set Task Sequence Variable step as the first step in the task sequence, name it Is upgrade allowed to run. Fill in the following values Task Sequence Variable: Upgrade_Forced Value: True Click on the options tab and add the following options: If ALL the conditions are true: File C:\ProgramData\Upgrade_Forced.txt exists If None of the conditions is true: WMI Query: select * from Win32_OperatingSystem where VERSION = "10.0.15063" If None the conditions are true: File C:\ProgramData\DO_NOT_UPGRADE.txt exists These three checks allow us to halt the task sequence on computers that don't meet our upgrade criteria. Note: You'll need to decide what build is deemed 'the latest version' of Windows 10 in your organization and change accordingly. In this post I'm assuming that is Windows 10 version 1703 (build 10.0.15063). On the Upgrade Operating System step, edit the Options and include the following Task Sequence Variable: Upgrade_Forced=True Note: This will ensure that the required upgrade only occurs if the Upgrade_Forced.txt file was present in C:\ProgramData. Next in the Post-Processing group add a new Run Command Line step called Add Windows 10 Required Upgrade reg key with the following command line: cmd.exe /c reg add "HKEY_LOCAL_MACHINE\SOFTWARE\windowsnoob" /v RequiredUpgrade /t REG_SZ /d "%date%" /f This will allow you to run reports on when computers were upgraded using this method. Close the task sequence. Next create a new Run command line step called Remove Upgrade_Forced.txt with a cmd line of cmd.exe /c echo Y | del C:\ProgramData\Upgrade_Forced.txt Step 6. Deploy the task sequence In this step we deploy the task sequence with a purpose of required. Note: I'd strongly advise you to test this thoroughly in your lab and make sure to pick your collections correctly and to populate them very carefully. Right click on the task sequence and choose Deploy For collection choose OSD Servicing Required Deployment, and ignore the popup telling you it's empty, you can add computers to that collection later. Change the Purpose to Required For Scheduling click on New, then choose Schedule, then change it to run daily at 11am. For rerun, choose Always rerun program as you will update the limiting collection (All Windows 10 version 1511) membership daily @ 1pm and upgraded computers will fall out of the collection. In case they don't (for whatever reason) the wrapper checks for the targetbuild and if the computer matches that build, it will abort and not start the upgrade. Note: The above schedule will run our popup daily at 11am for 6 days prior to forcing the upgrade to Windows 10. You should change the schedule according to your preferences. Continue through the wizard until completion. Note: If you want to test run the Task Sequence from the Software Center or if you want your users to do this, then enable the Allow users to run the program independently of assignments checkbox on the User Experience tab. Step 7. Adjust Windows 10 limiting collections membership schedule Below you can see the membership rules update frequency on the limiting collection, it's set to run two hours after our Upgrade, adjust as necessary for your organization and your agreed schedule. Step 8. Add test computers to the OSD Servicing Required Deployment collection Note: Before doing this step, carefully read the Warning and Disclaimer at the top of this guide! Right click on the collection and choose Add Resources (or use your own chosen method to add computers) to add one or more test computer to the OSD Servicing Required Deployment collection. As this collection now has a live required task sequence deployed to it, do this step very very carefully, if in doubt stop what you are doing, go and have a coffee and try again when your nerves are calm. and add your test computers as you see fit.. Step 8. Monitor the experience on test computers Login to a test computer, do a machine policy update in the ConfigMgr client actions and wait for the popup or kick it off via software center. After the computer receives the policy and the scheduled time is reached a popup is shown offering the user to Defer the upgrade or Upgrade now by selecting the appropriate checkbox and then clicking on Upgrade Now. Note: The clickable link goes to a non-existant url, you need to point it to whatever documentation you want your users to read in preparation for the upgrade. As each day passes (or based on your custom schedule) the counter reduces by 1 every time the popup appears. When there are no more deferrals left, a 4 hour countdown starts and when it reaches 00:00:00 the Windows 10 Required Upgrade will start. If the user closes the popup, the timer will resume where it left off when it is restarted. Alternatively, if the user doesn't want to defer, and they want to run the upgrade right now, they can place a checkmark in the 'My files are synced in OneDrive...' and then click Upgrade Now to start the task sequence. Either way, regardless of what your user clicks on, (based on the schedule in this guide) the computer will start the upgrade within 7 days (or earlier or later if you adjust the schedule). Once the Upgrade Now button is clicked on, or once the Timer reaches 00:00:00 the task sequence will automatically start (assuming that the DO_NOT_UPGRADE.txt is not present). Branding Simply replace the banner.png file included with one matching your Company Name, edit the upgrade.hta and locate the 'windowsnoob' name in the text field (line 347) and replace it with your own Company Name. Troubleshooting The popup creates 3 log files to troubleshoot the process, they are located in C:\ProgramData and named Windows10RequiredUpgradeHTA.log Windows10RequiredUpgradeWrapper.log Windows10RequiredUpgradeStartUpgrade.log The wrapper writes to the registry in HKCU\Software\windowsnoob Note: The collections, scripts and task sequence assume you are upgrading from Windows 10 version 1511 to Windows 10 version 1607, you'll need to edit the WMI Query in the task sequence to change Windows 10 build version when you move to creators update and for later versions of Windows, and you'll need to edit the TargetBuild variable in the wrapper.vbs script accordingly. Once done, you should change the Limiting Collection for the OSD Servicing Required Deployment collection to match the n-1 version of Windows 10 you want to migrate from. Tip: If you have rendering issues with the popup on different devices then edit the call ResizeWindow(425,335,500,375) values and ResizeWindow Function to fit your specific needs, I don't have access to too much hardware to test this on. The popup is fixed, if you want the user to be able to move it change the line caption="no" to caption="yes". If you want to programmatically use it then add a Window.moveTo(x, y) line. Downloads You can download the scripts used above in the following zip files: windowsnoob Required Upgrade HTA.zip CreateDeviceCollectionsWindows10.zip Summary Forcefully upgrading computers is a tricky area but hopefully this method gives you one more option to consider.
- 242 replies
-
- 1
-

-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-

Enable Bitlocker, assistance
anyweb replied to xerxes2985's topic in System Center Configuration Manager (Current Branch)
hi please attach your smsts.log so i can see what's failing -
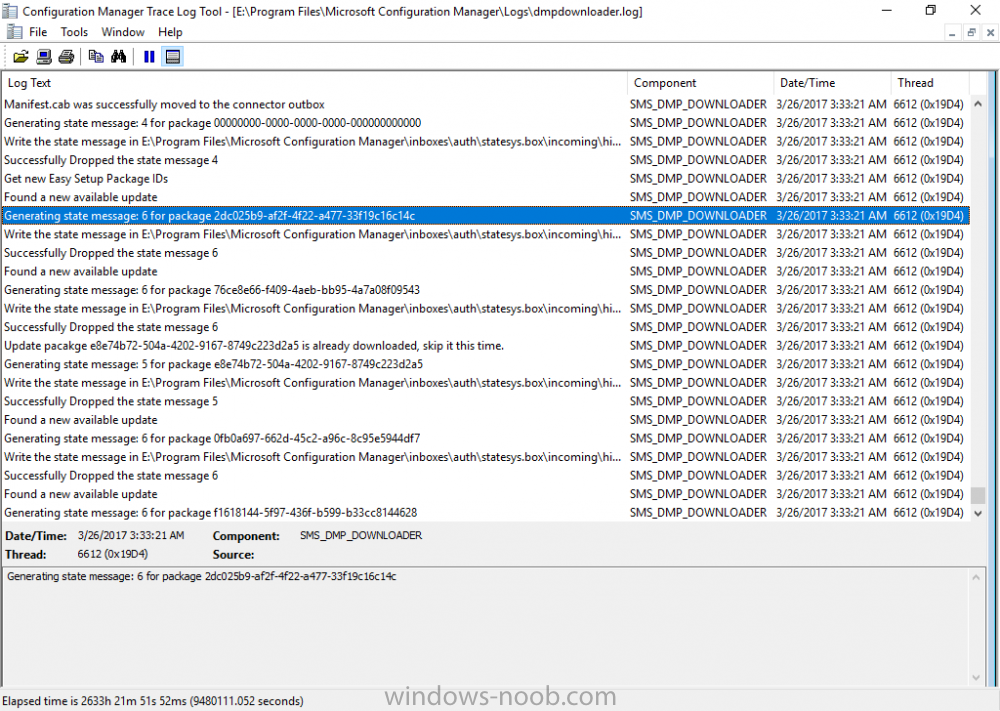
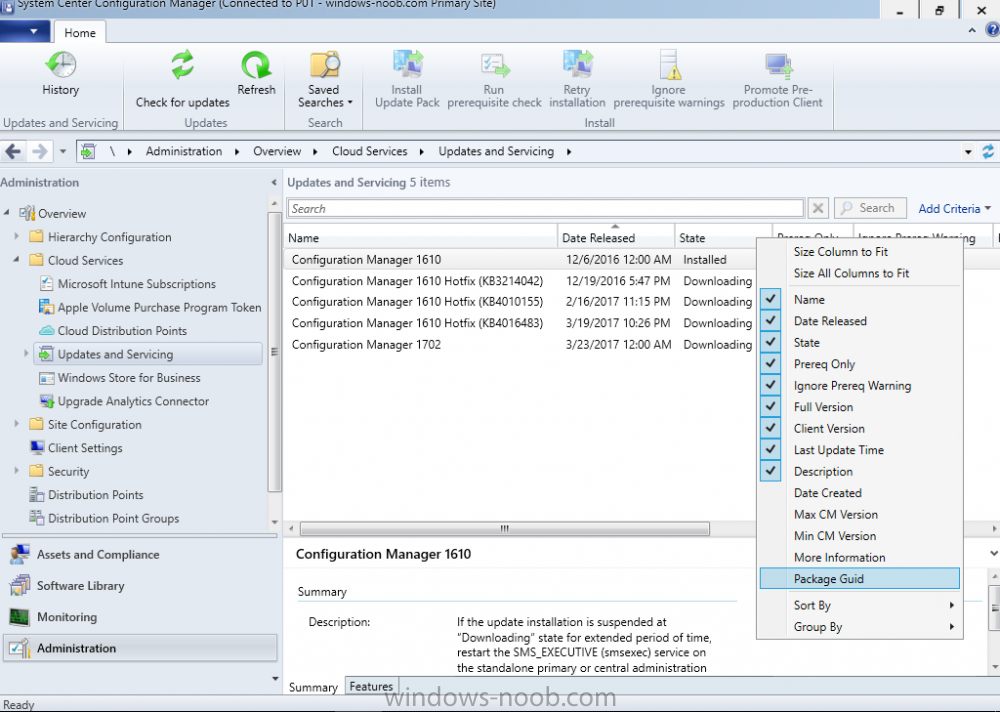
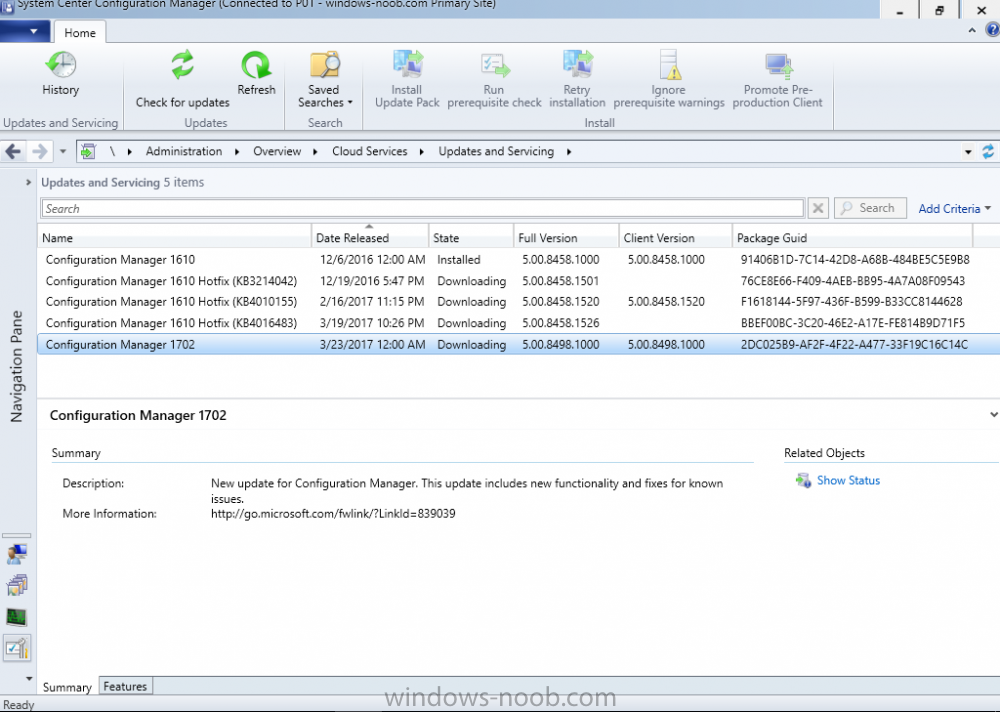
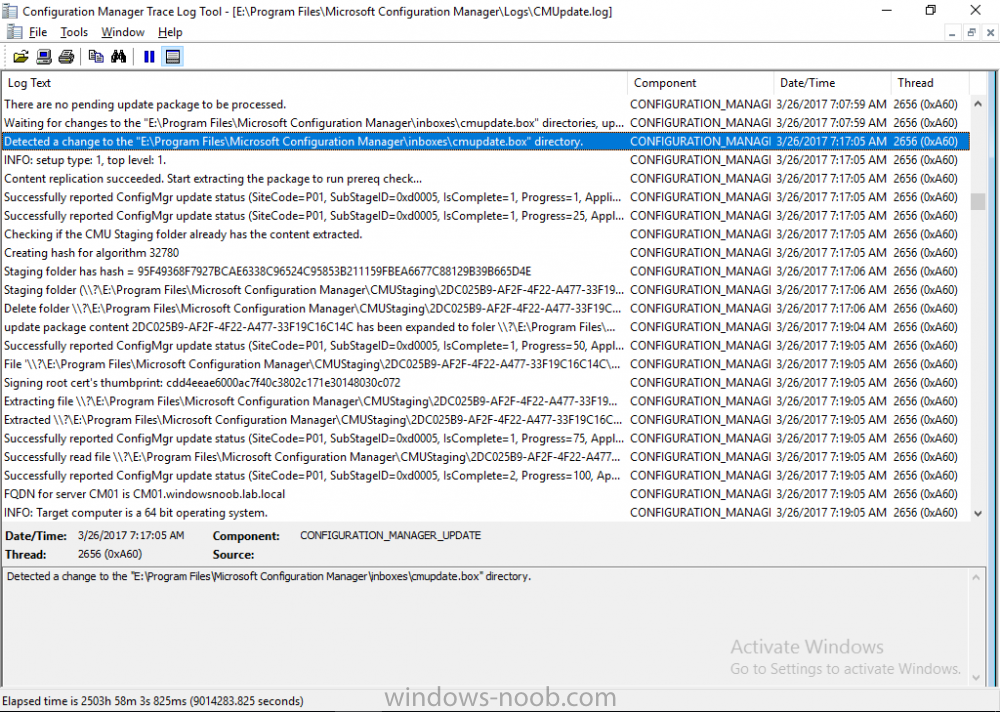
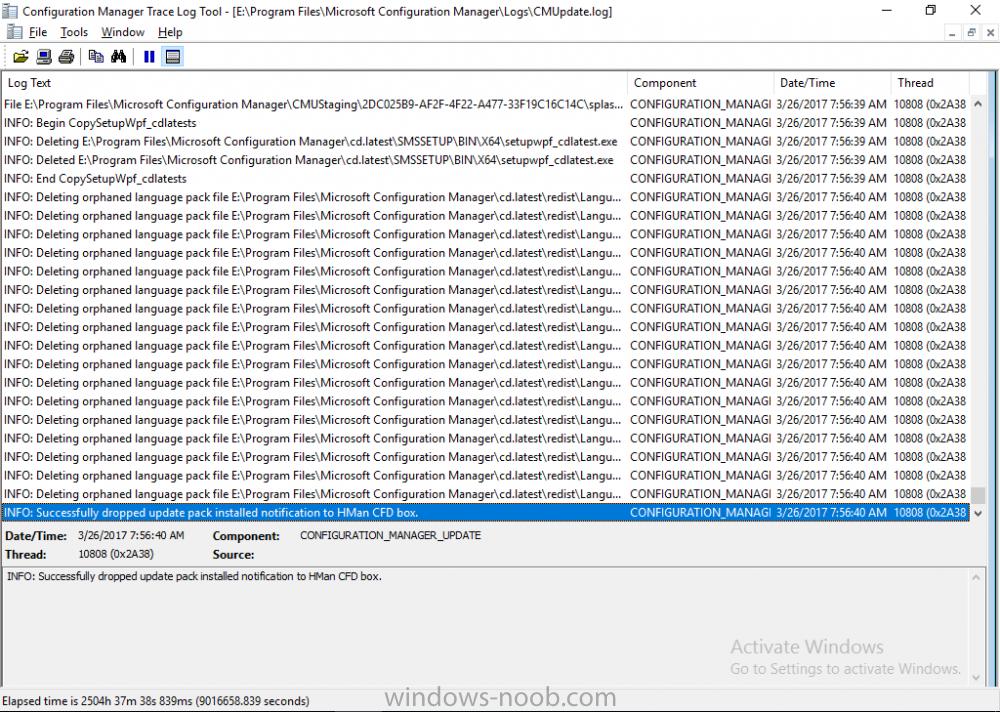
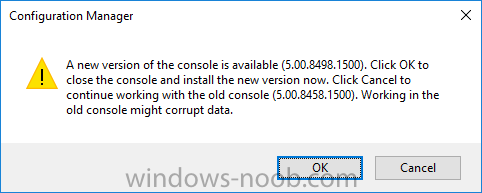
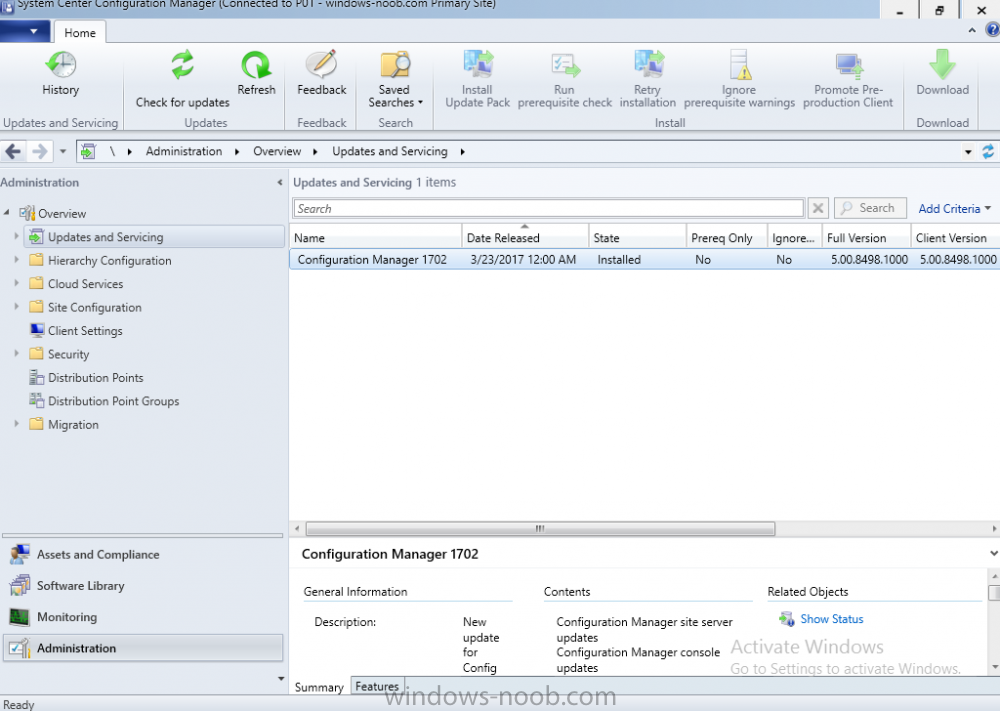
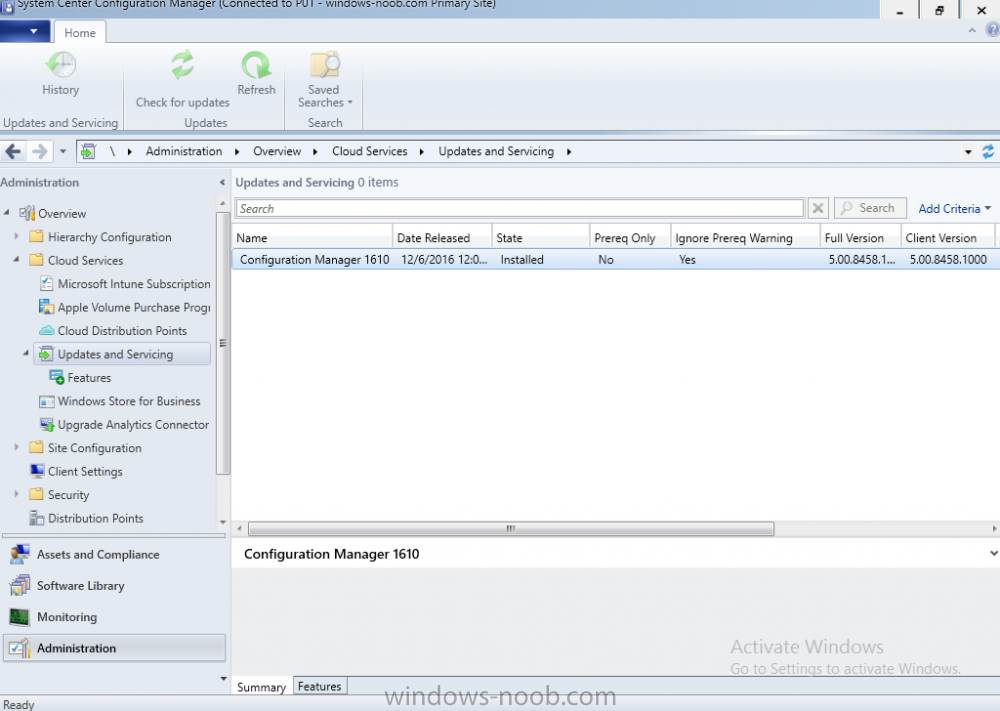
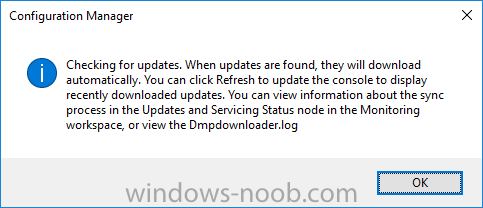
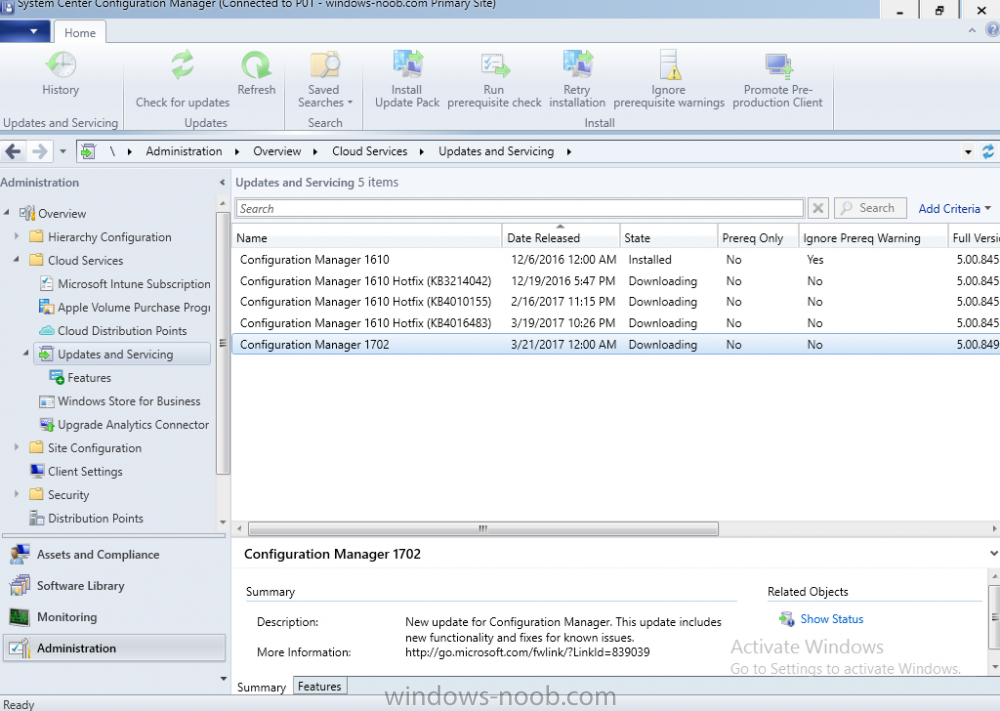
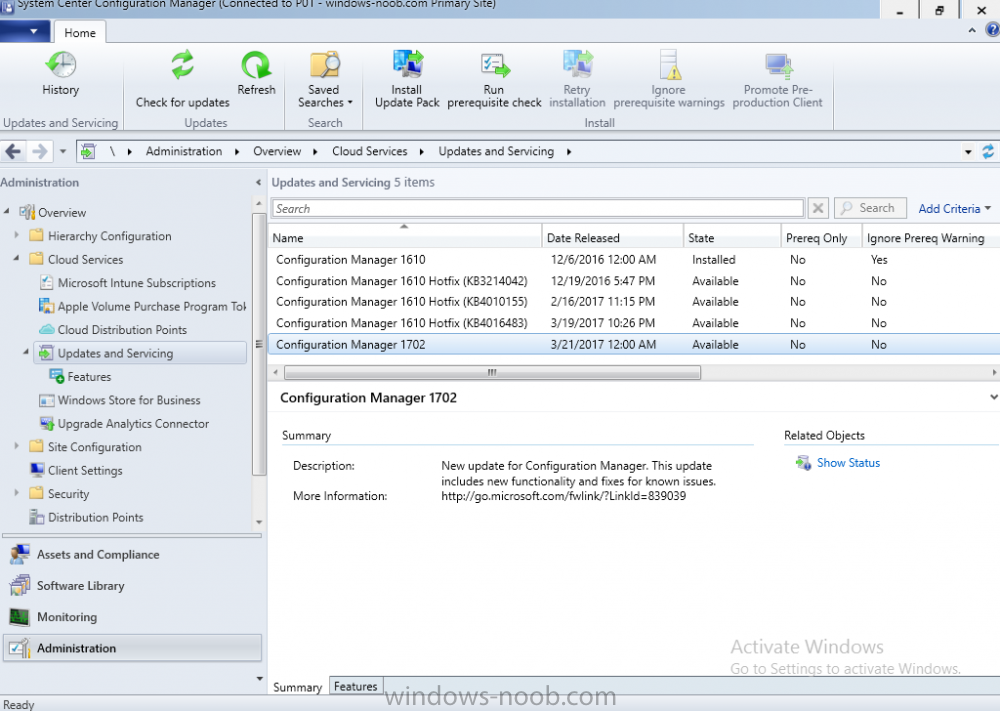
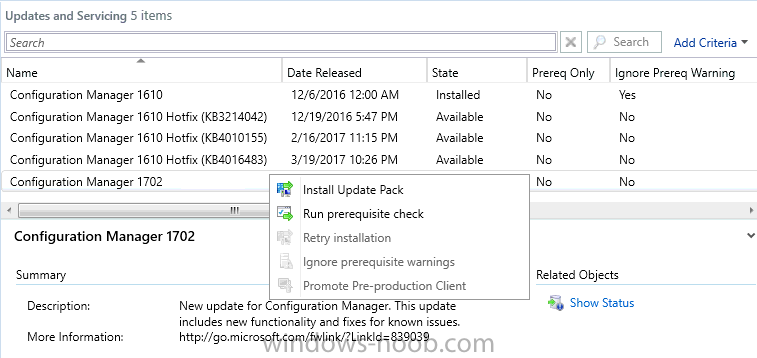
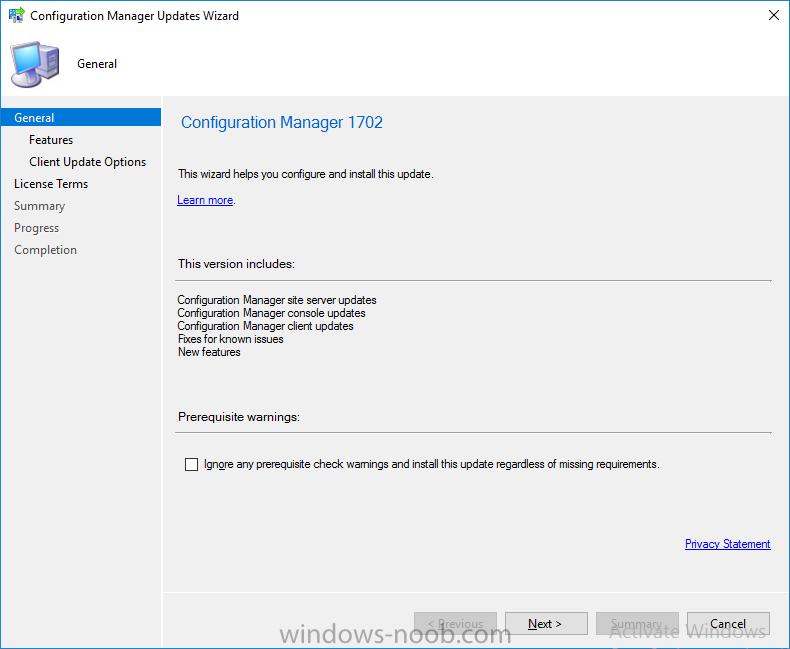
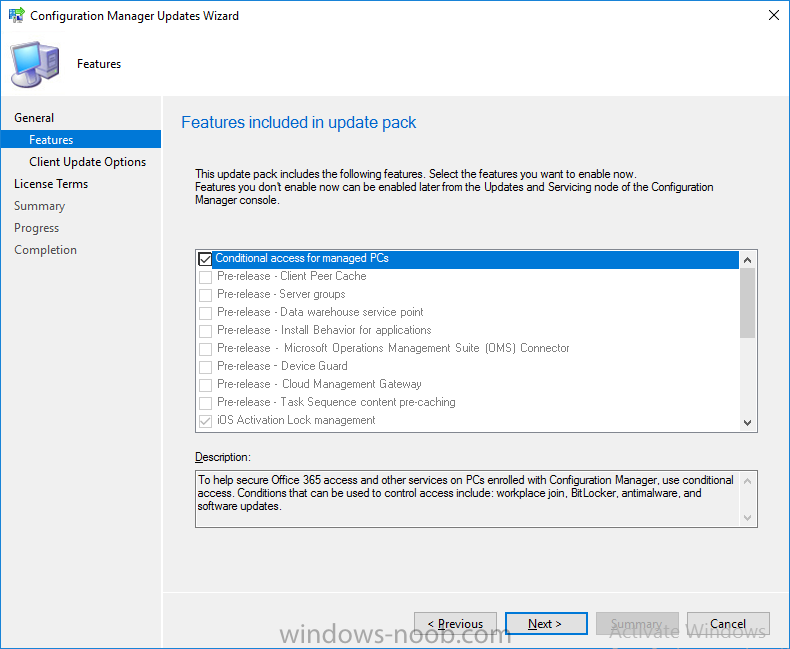
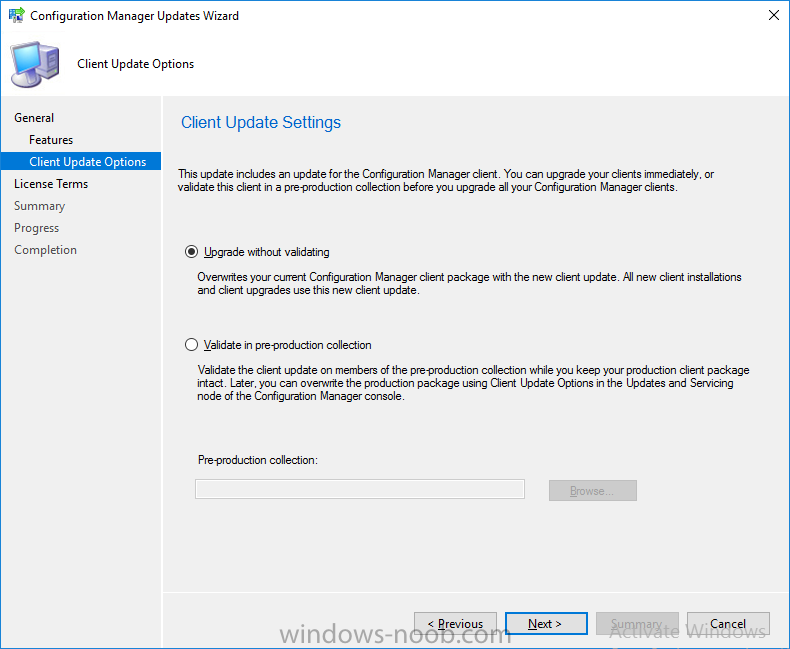
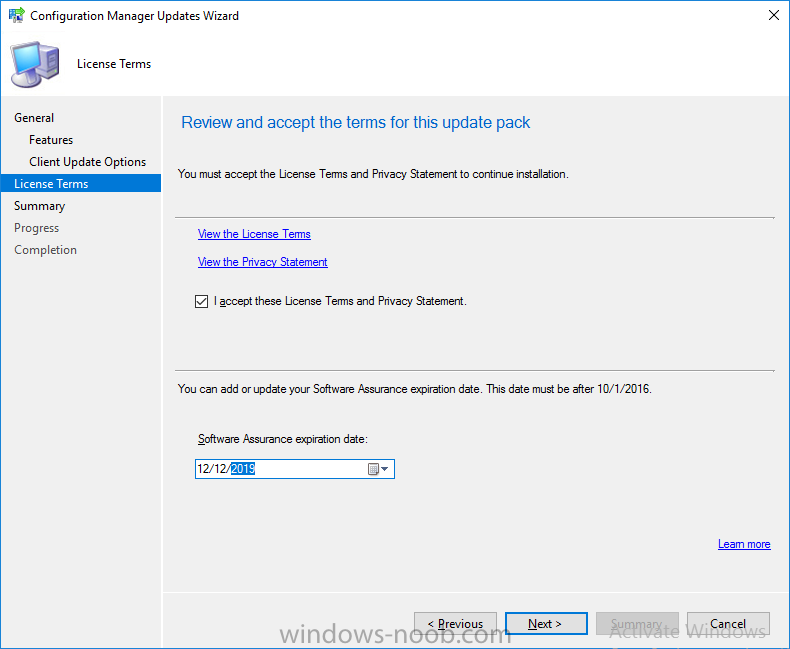
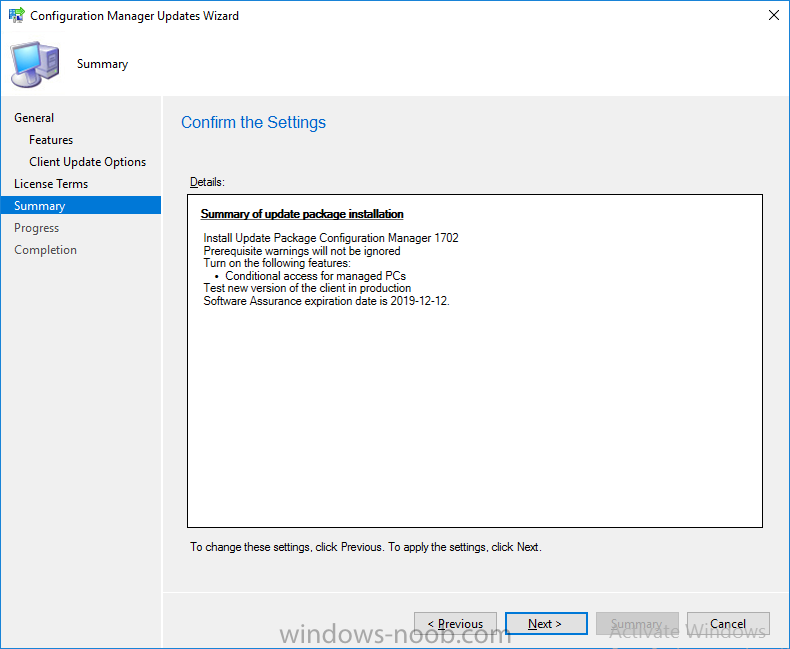
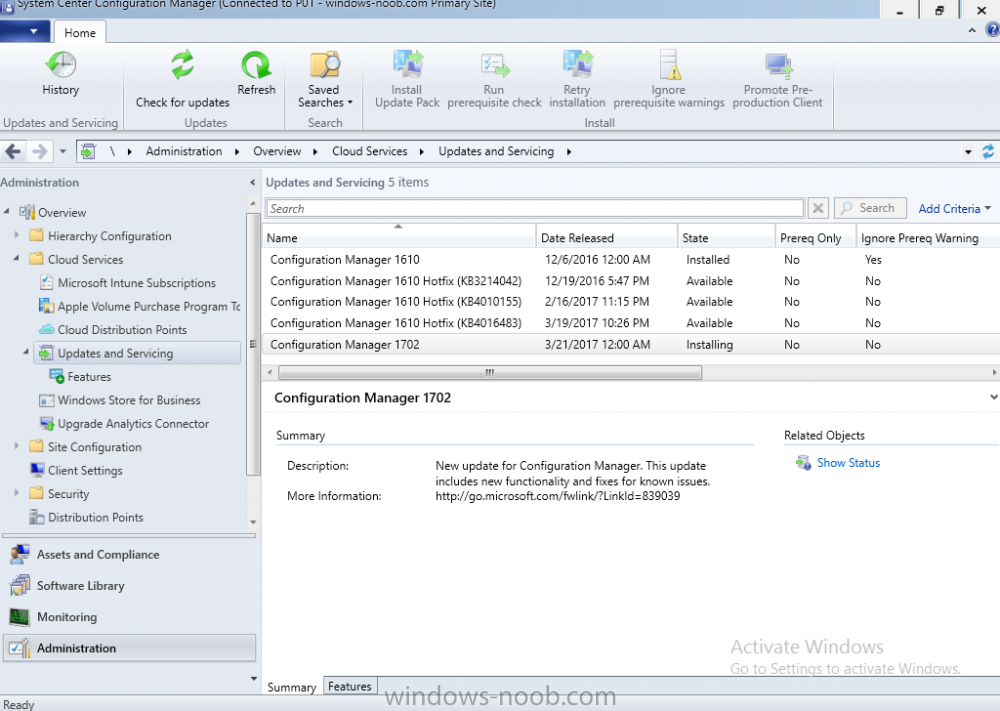
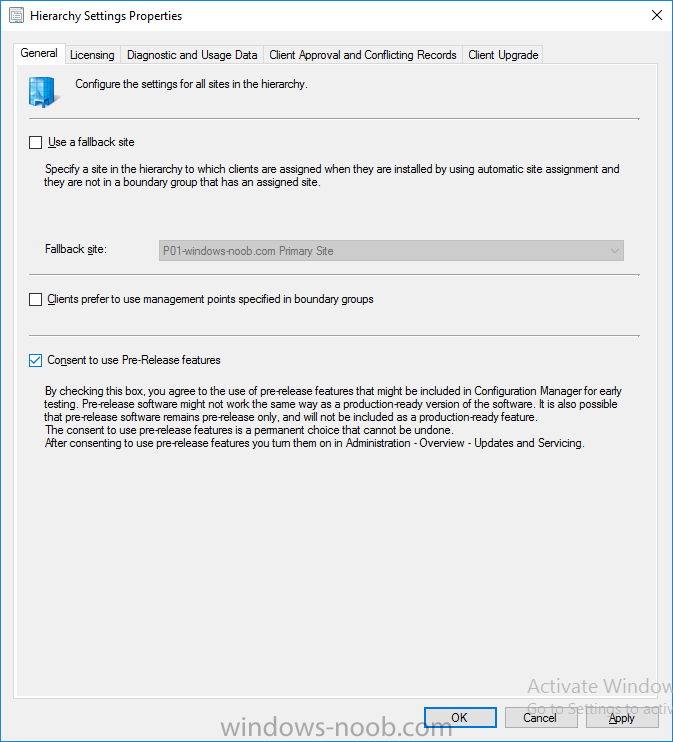
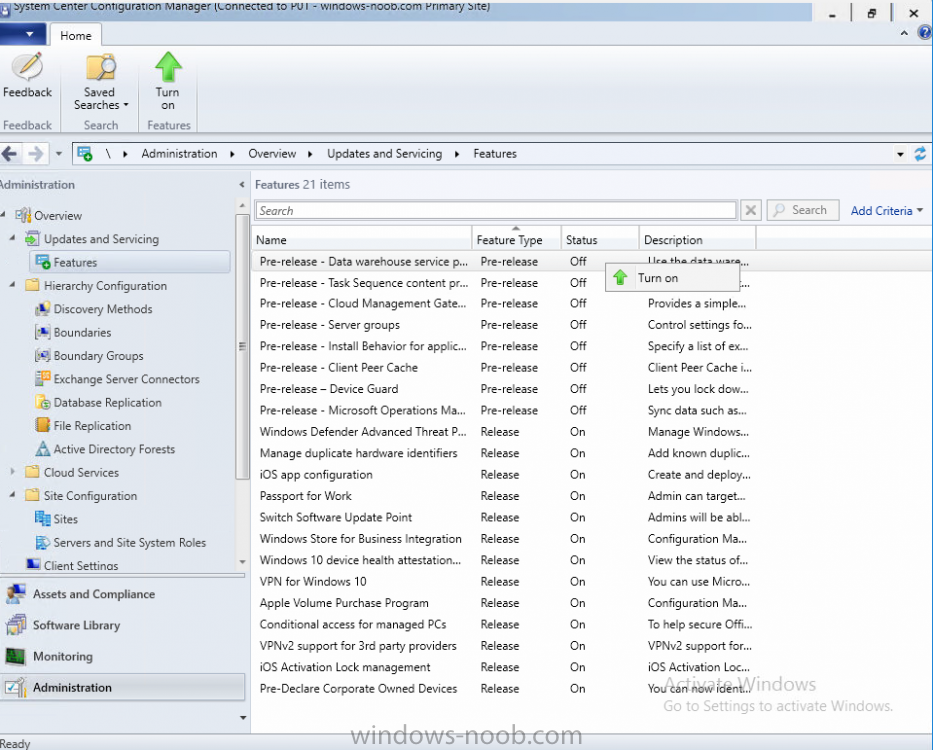
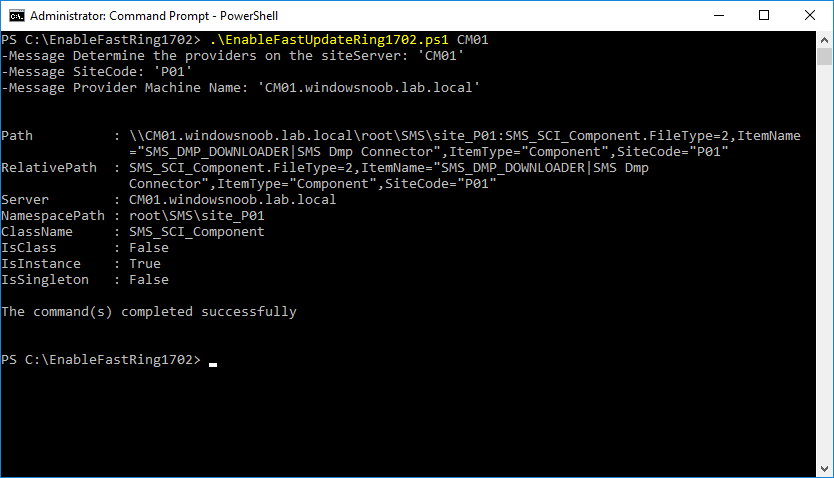
Introduction In a previous post you used PowerShell scripts to quickly install System Center Configuration Manager (Current Branch) version 1606 and then upgraded it using Updates and Servicing to System Center Configuration Manager (Current Branch) version 1610. In case you are not already aware there are two main branches (of Configuration Manager) available: System Center Configuration Manager (Current Branch) System Center Configuration Manager (Technical Preview) System Center Configuration Manager (Current Branch) is designed for use in production environments, for managing anything from small to very large Enterprises, whereas System Center Configuration Manager (Technical Preview) is for lab testing environments only and is limited to 10 clients. The Technical Preview releases are released monthly, and contain the latest and greatest features being trialed in the product, and usually these new features are the result of feedback from uservoice. Current Branch releases on the other hand are released only a few times per year and contain stable, tested features that are mature enough to release into production environments. Microsoft have released the latest Current Branch offering known as System Center Configuration Manager (Current Branch) version 1702, so it's time to upgrade again. This release offers many new features, one of which I’m especially proud of because it was my uservoice ! For details about this change see the following post. Support for Windows 10 Creators Update – This version of Configuration Manager now supports the release of upcoming Windows 10 Creators Update. You can upgrade Windows 10 ADK to the latest version for full OS imaging support. Express files support for Windows 10 Cumulative Update – Configuration Manager now supports Windows 10 Cumulative Update using Express files. Customize high-risk deployment warning – You can now customize the Software Center warning when running a high-risk deployment, such as a task sequence to install a new operating system. Close executable files at the deadline when they would block application installation – If executable files are listed on the Install Behavior tab for a deployment type and the application is deployed to a collection as required, then a more intrusive notification experience is provided to inform the user, and the specified executable files will be closed automatically at the deadline. This is currently the feature with the second highest number of votes on UserVoice. Conditional access for PCs managed by System Center Configuration Manager – Now production ready in update 1702, with conditional access for PCs managed by Configuration Manager, you can restrict access to various applications (including but not limited to Exchange Online and SharePoint online) to PCs that are compliant with the compliance policies you set. This release also includes new features for customers using Configuration Manager connected with Microsoft Intune. Some of the new feature include: Android for Work support – You can now enroll devices, approve and deploy apps, and configure policies for devices with Android for Work. Lookout threat details – You can view threat details as reported by Lookout on a device. Apple Volume Purchase Program (VPP) enhancements – You can now request a policy sync on an enrolled mobile device from the Configuration Manager console. Additional iOS configuration settings – We added support for 42 iOS device settings for configuration items. For more details and to view the full list of new features in this update check out the What’s new in version 1702 of System Center Configuration Manager documentation. The Release Notes are worth a ready also. Upgrading to 1702 When new Current Branch releases are made public, you have the choice of getting it immediately using a fast ring PowerShell script, or to wait a couple of weeks until it is made available to the slow ring (and then show up in the ConfigMgr console). To use the fast ring PowerShell script, download it, and run it to self-extract to C:\EnableFastRing1702. Once extracted, start a PowerShell cmd prompt in that folder and from there use the following command (where CM01 is the <SiteServer_Name | SiteServer_IP> of your CAS or standalone Primary site server). .\EnableFastUpdateRing1702.ps1 CM01 and below is sample output from that script. To start the upgrade open the ConfigMgr console and find the Updates and servicing node as shown here. You can see that Configuration Manager 1610 Current Branch is already installed. Click on Check for Updates in the ribbon. And as instructed open the DMPDownloader.log using CMTrace to monitor the process of checking for updates. Here you can see Generating state message: 6 which highlights that it’s found an applicable update. Generating state message: 6 for package 2DC025B9-AF2F-4F22-A477-33F19C16C14C Tip: you can identify the Package GUID in the console by enabling the GUID column and then scroll to the right to see what's listed Note: The Package GUID shown above was for the Configuration Manager 1702 CB release that has a release date of 2017/3/23. Later releases (which may incorporate changes/fixes) will have a different GUID. In the ConfigMgr console you’ll see it’s in a state of downloading, in this example it is also downloading hotfixes released since 1610 was installed (this is a Lab which was powered off for a month or more). Once it has completed downloading it will be listed as a state of Available. You need to click refresh in the ConfigMgr console to update the view. Installing the Update Right click on the update and choose Install Update Pack. when the Wizard appears, make your choice for pre-reqs and click next. review the features included in this update pack , I selected Conditional access for managed PCs, Note: You'll also notice lots of Pre-Release features that are greyed out, to turn them on see the steps after upgrading the console the bottom of this guide. Before clicking next at the Client update settings please see this post accept the EULA and configure the software assurance expiration date and click through to the summary at which point the update will be listed with a state of Installing. Monitor the installation At this point you can use CMTrace to open the CMUpdate.log file in <drv>\Program Files\Microsoft Configuration Manager\Logs (where drv is the drive letter you installed ConfigMgr on) to monitor the installation live. Note: The CMUpdate.log will take some time to start logging the installation of the update, so be patient if nothing appears to happen, it will. Look for a line like the one below to signal the update has begun. Detected a change to the "E:\Program Files\Microsoft Configuration Manager\inboxes\cmupdate.box" directory. Once the update is complete, you should see a hman notification in the log . Note: If you don’t see this and see an upgrade failure message then scroll up in the CMUpdate.log file to determine what the failure reason was. You can always retry an upgrade (maybe not enough available ram for example). After the update is complete, click refresh in the console and you'll be reminded to update the ConfigMgr Console via a popup, the new version is 5.00.8498.1500. Make sure to update your console as you cannot use the new features until you do. Click OK to upgrade your ConfigMgr console, and after all is done you’ll see the 1702 version listed in the console. After upgrading the site Tip: If you want to gain access to the Pre-Release features, then select Sites, Hierarchy Settings, and place a checkmark in Consent to use Pre-Release features. Then go to Overview, Updates and Servicing and expand Features as shown below, you can then turn on (or off) any of the Pre-Release features you want to test in Production. Related reading What's new in System Center Configuration Manager version 1702 - https://docs.microsoft.com/en-us/sccm/core/plan-design/changes/whats-new-in-version-1702 What is the content library cleanup tool and how can I use it ? https://www.niallbrady.com/2017/01/24/what-is-the-contentlibrarycleanup-tool-and-how-can-i-use-it/ Release Notes - https://docs.microsoft.com/en-us/sccm/core/servers/deploy/install/release-notes
-

Issues Upgrading to SCCM 1610
anyweb replied to Edgy41's topic in System Center Configuration Manager (Current Branch)
could your proxy be blocking urls in the download, it's referred to in your dmpdownloader.log, can you bypass the proxy ? -
Hello Windows Insiders! Today we are excited to be releasing Windows 10 Insider Preview Build 15060 for PC to Windows Insiders in the Fast ring. NOTE: The builds for Brazil (PT-BR) and Polish (PL-PL) are not yet available so Insiders will see the message “An update is being prepared for your device, but it’s not quite ready yet. We will keep trying or you can try again now.” when checking for updates. Windows 10 Home for 32-bit is also not yet available. Other changes, improvements, and fixes for PC We fixed an issue resulting in the Settings icon appearing plating in the taskbar. This issue also resulted in another issue now fixed, where if Settings had been pinned to Start, the tile would become greyed out after the first time it was clicked. Thank you all for your feedback on this. We fixed an issue resulting in 3rd party IMEs not showing up in Settings after being installed. We fixed an issue in Microsoft Edge where quickly typing and deleting characters into a website’s search box while using the MS Pinyin IME might result in the IME becoming stuck and the website showing “Not responding”. Surface Pro 3 and Surface 3 devices should no longer fail to update to new builds if a SD memory card is inserted if you have the latest Surface drivers and firmware installed. We fixed an issue where taskhost.exe might crash after pressing Tab while quickly typing in UWP app sign in fields, resulting in not being able to type for a few seconds. We fixed an issue for Insiders where, after a crash, Microsoft Edge might fail to launch again for a few minutes because previous instances were still suspended in the background. We fixed the issues occurring when exploring pages using the F12 Developer Tools in Microsoft Edge with cross-origin iframes (e.g. the DOM explorer shows only the iframe DOM, the Console frame selector doesn’t list the iframes, etc.). Known issues for PC You will be unable to download new (additional) language packs on this build. Currently installed language packs will not be impacted. If your PC fails to install this build on reboot with the error 8024a112, reboot manually again. If your PC appears to hang during the reboot, power your PC off and back on and the install will proceed. Some Insiders have reported seeing this error “Some updates were cancelled. We’ll keep trying in case new updates become available” in Windows Update. If you encounter it, please try deleting the following registry key: 1 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update\RequestedAppCategories\8b24b027-1dee-babb-9a95-3517dfb9c552 See this forum post for more details. Some apps and games may crash due to a misconfiguration of advertising ID that happened in a prior build. Specifically, this issue affects new user accounts that were created on Build 15031. The misconfiguration can continue to persist after upgrading to later builds. The ACL on the registry key incorrectly denies access to the user and you can delete the following registry key to get out of this state:HKCU\Software\Microsoft\Windows\CurrentVersion\AdvertisingInfo There is a bug where if you need to restart your PC due to a pending update like with the latest Surface firmware updates, the restart reminder dialog doesn’t pop up. You should check Settings > Update & security > Windows Update to see if a restart is required. [GAMING] Certain hardware configurations may cause the broadcast live review window in the Game bar to flash Green while you are Broadcasting. This does not affect the quality of your broadcast and is only visible to the Broadcaster.
-

UEFI PXE OSD Background Picture size
anyweb replied to act_cpsb's topic in Configuration Manager 2012
if you add a restart computer step, does it improve ? -
have you deployed both architecture boot images to the dp's ? and both are PXE enabled ?
-

Service plans look strange
anyweb replied to P3nnyw1se's topic in System Center Configuration Manager (Current Branch)
are they deployed to the same collection or different ? and if different what computers are in each- 2 replies
-
- service plan
- windows 10
-
(and 2 more)
Tagged with:
-
what does the ZTIPatches_DISM.log tell you, can you attach it here
-
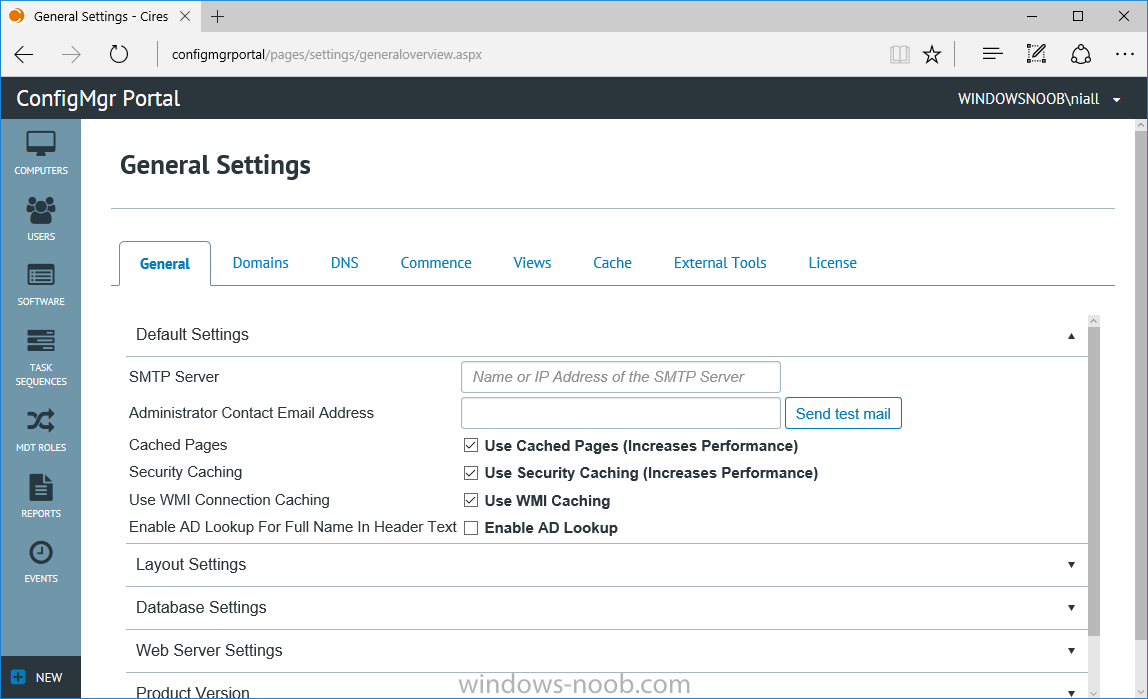
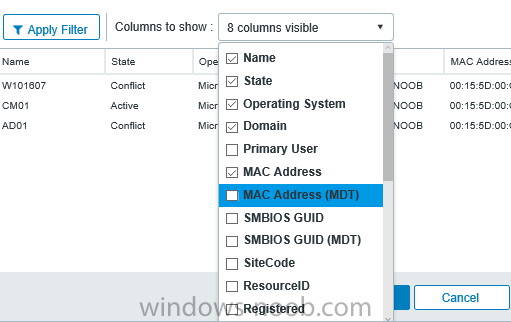
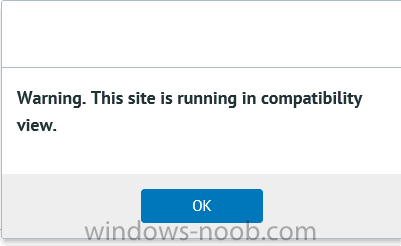
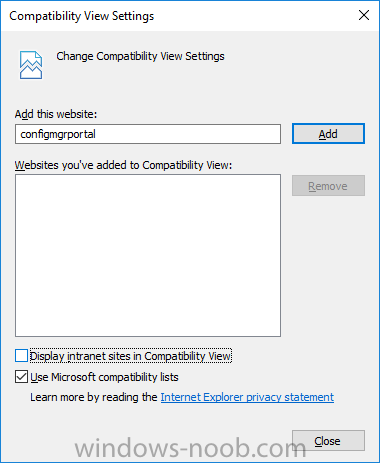
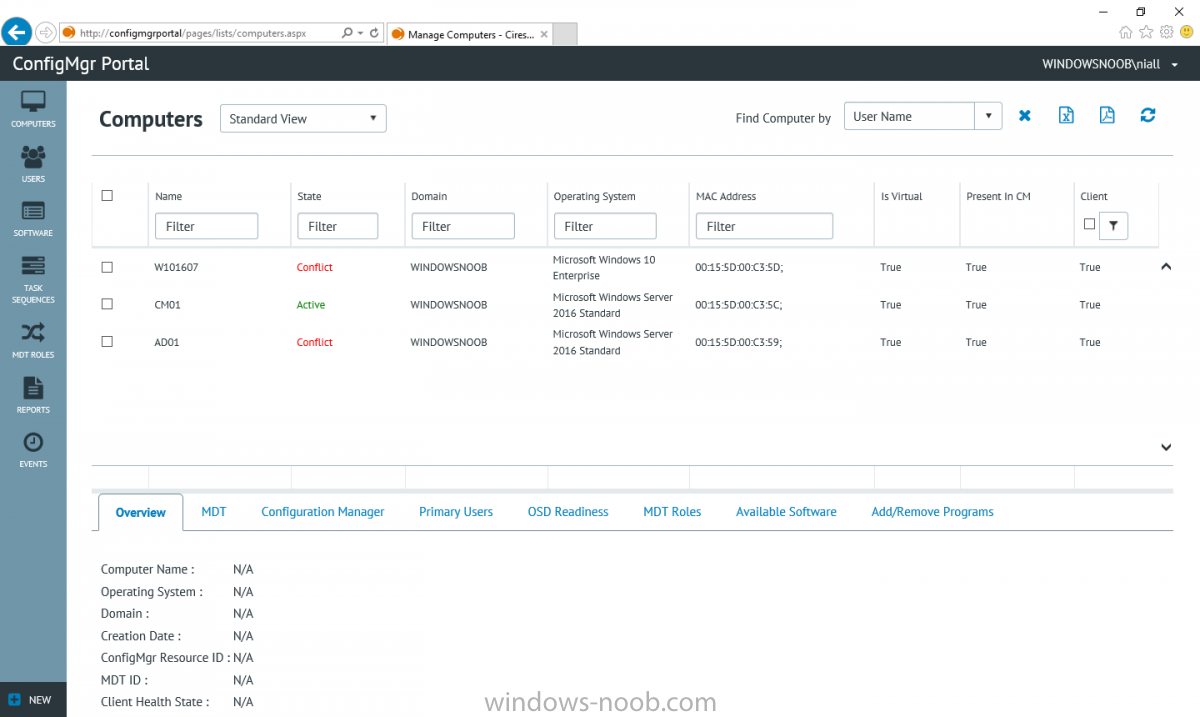
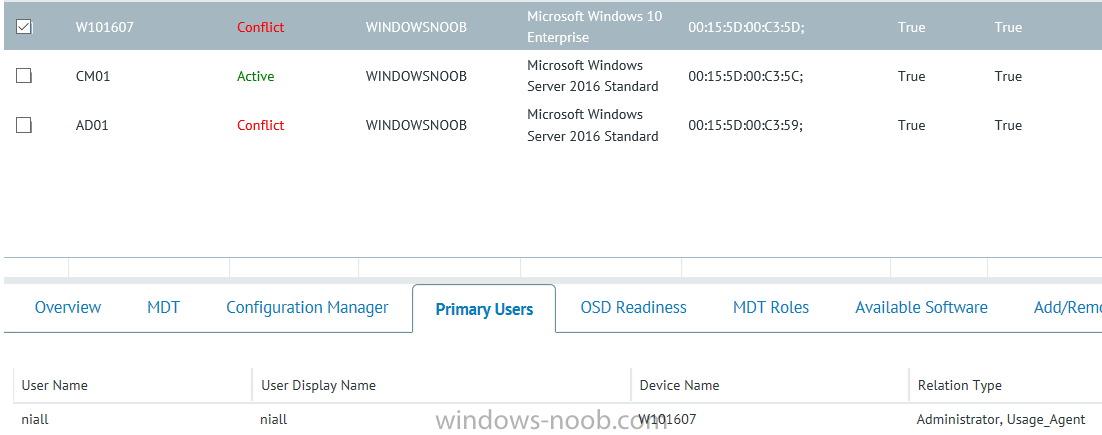
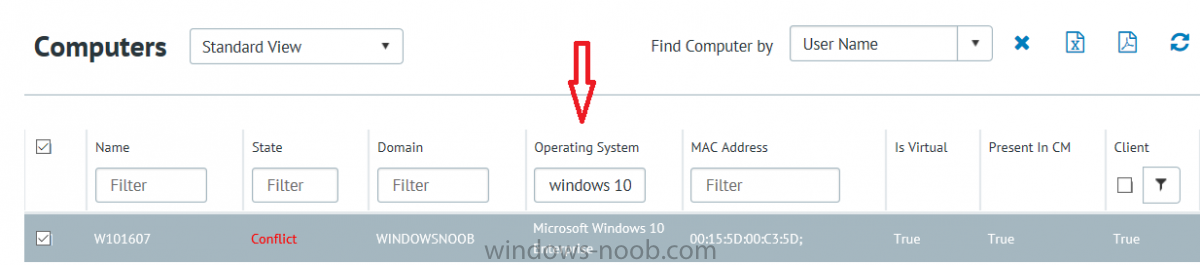
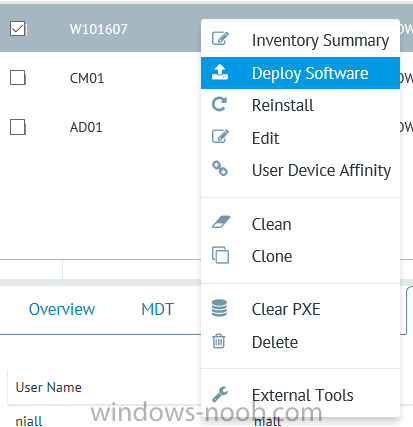
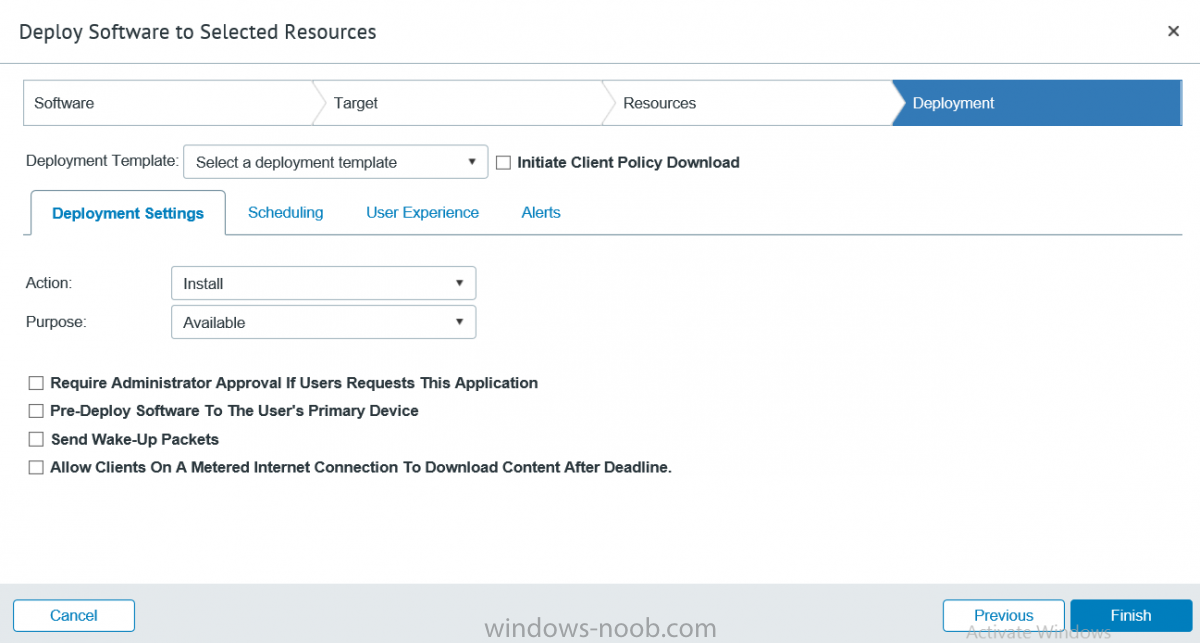
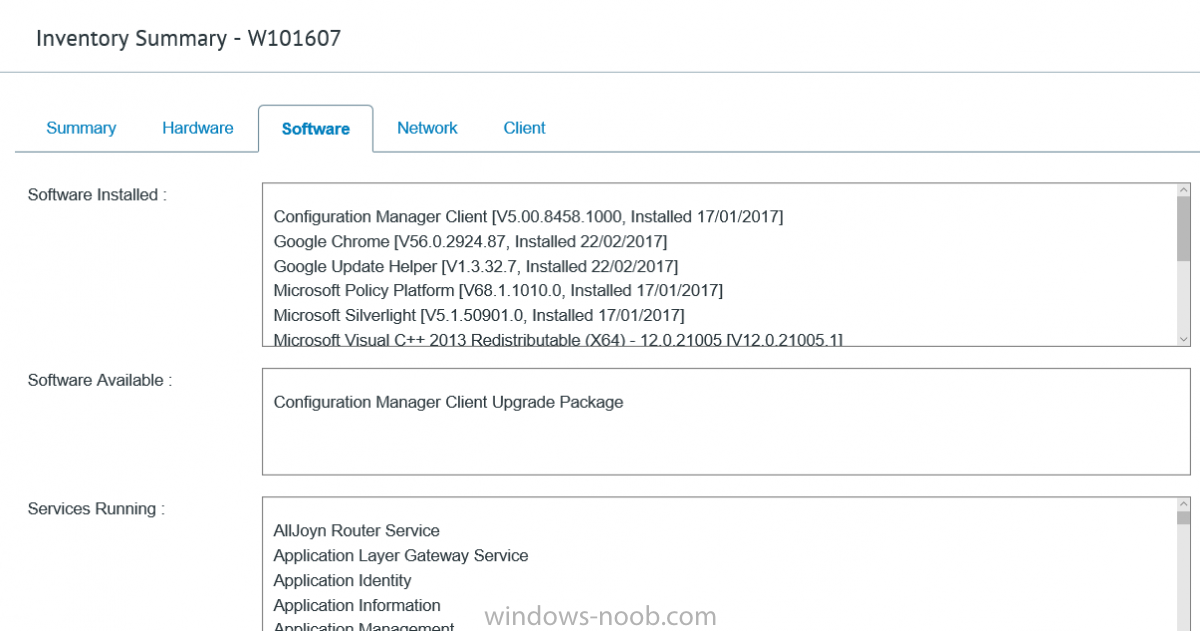
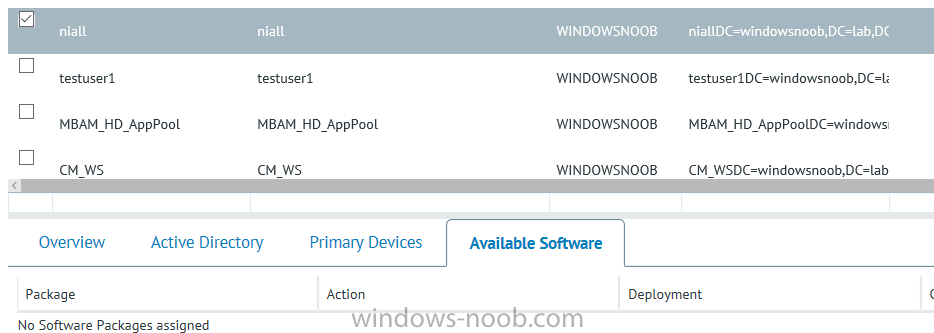
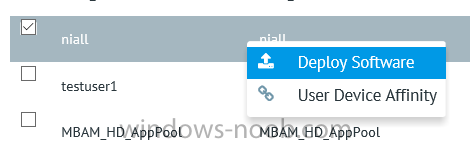
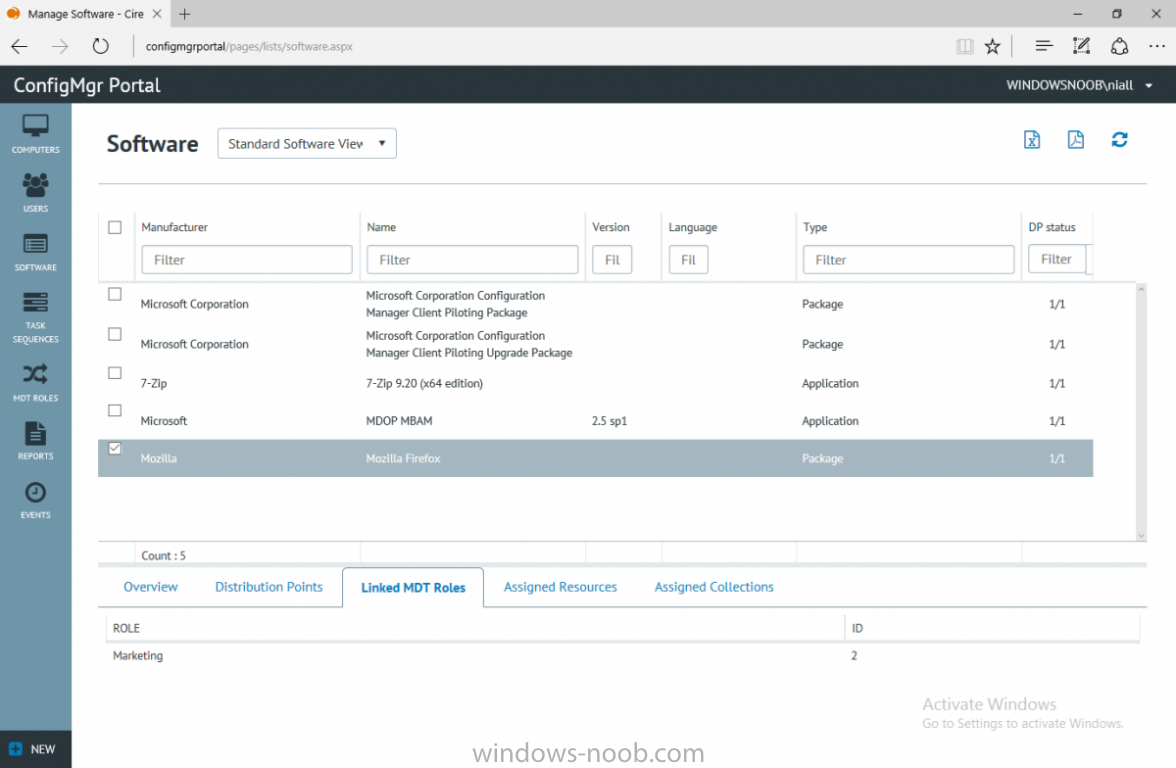
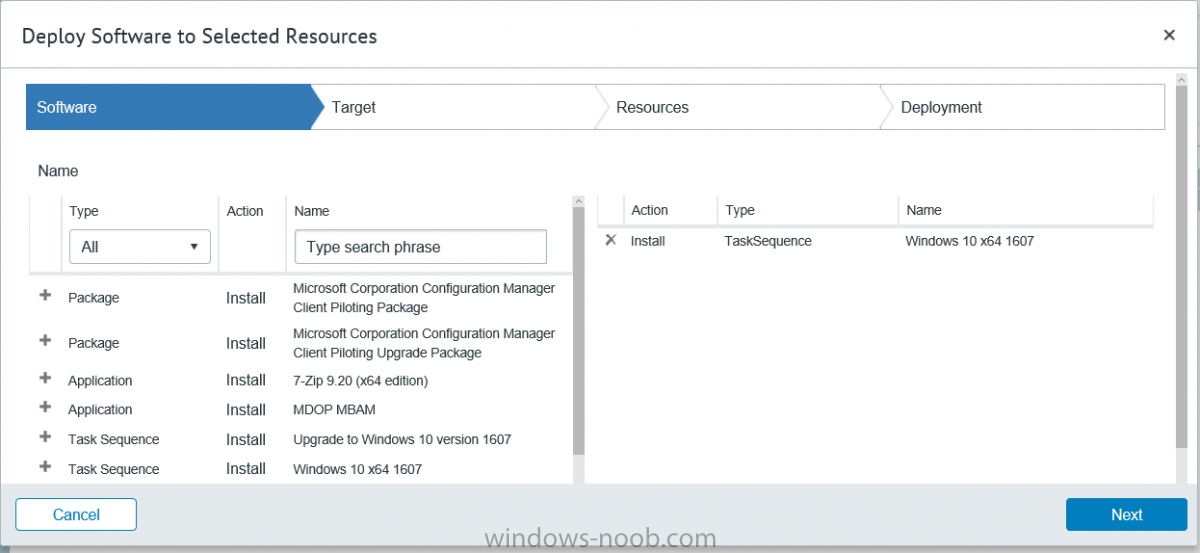
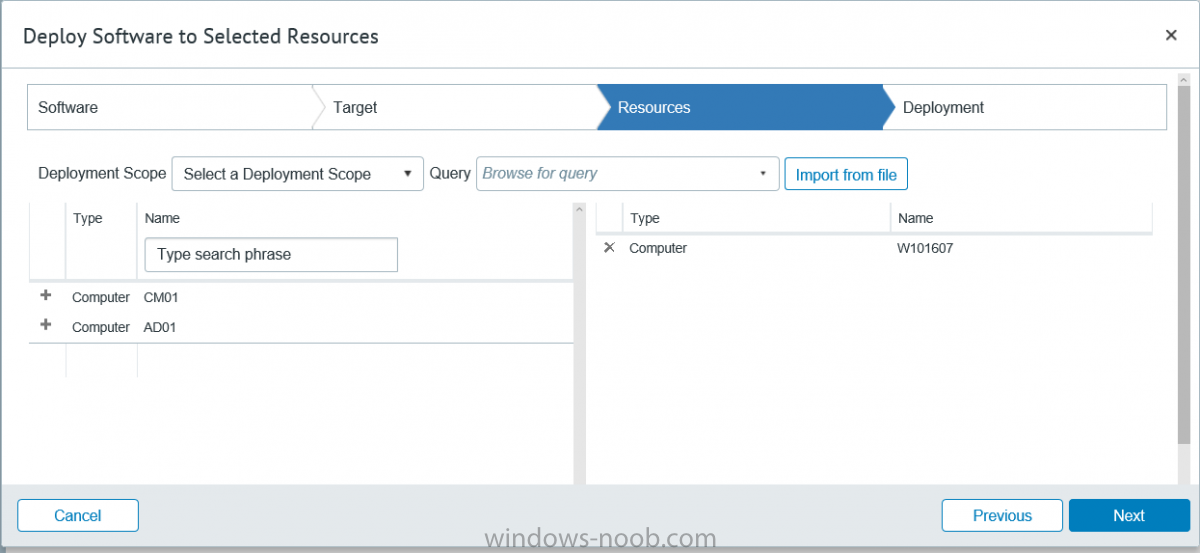
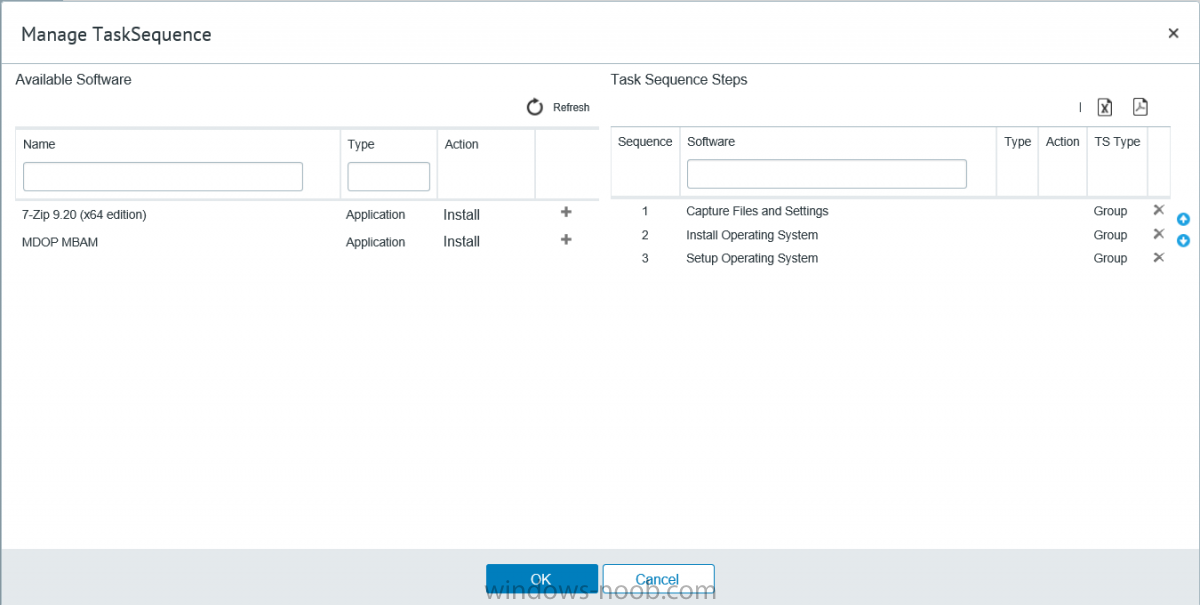
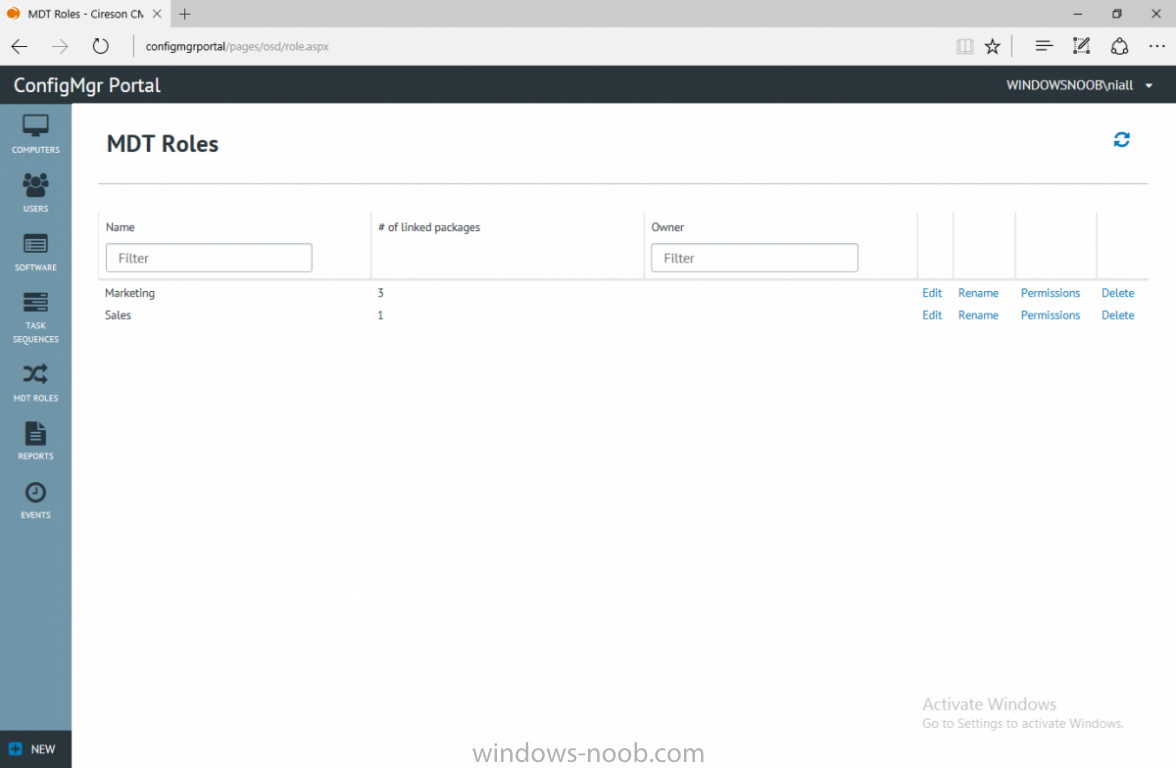
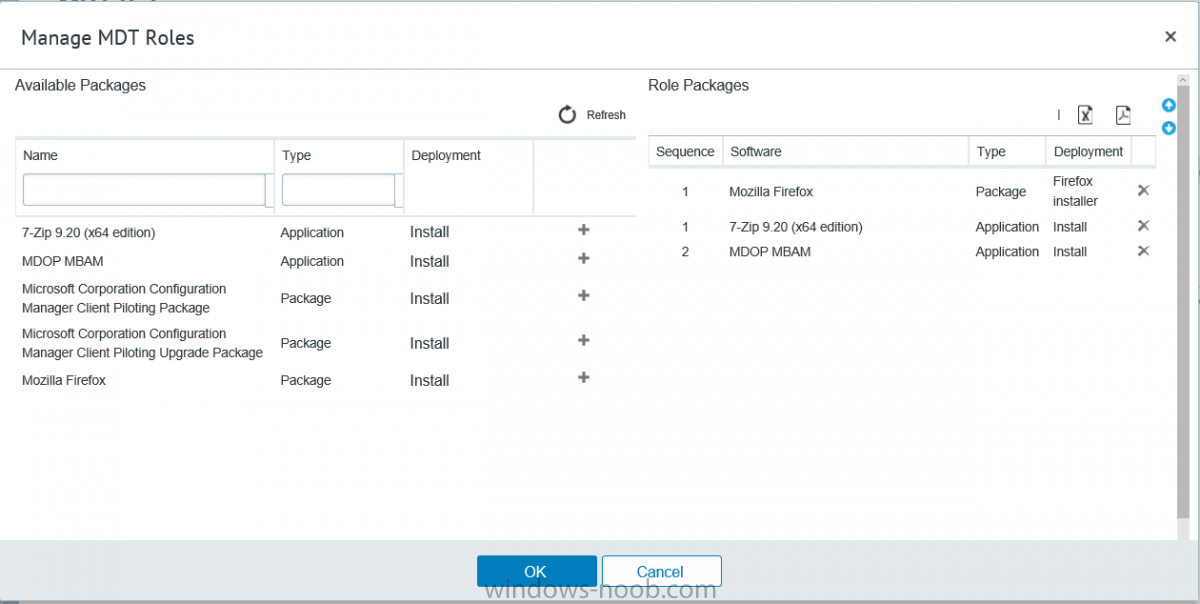
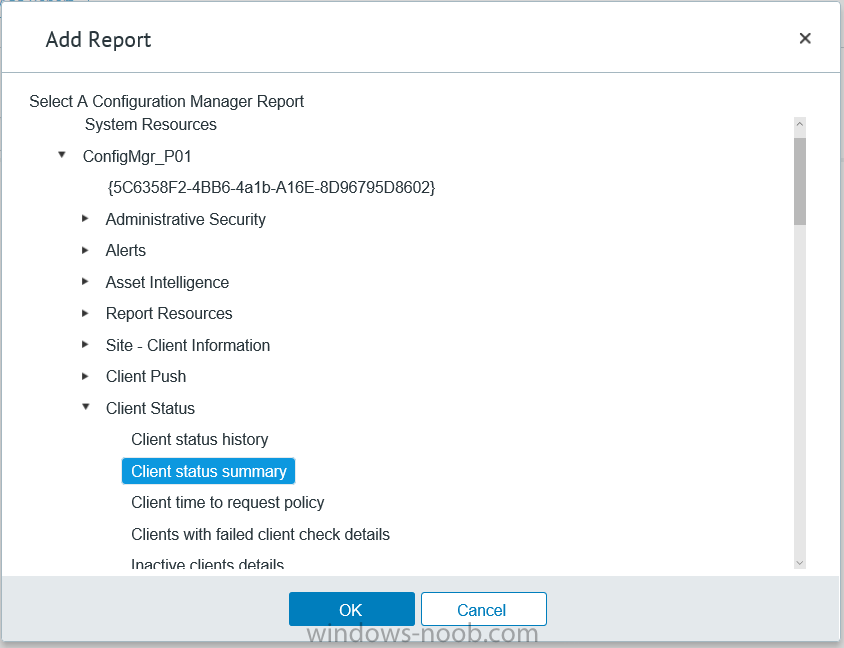
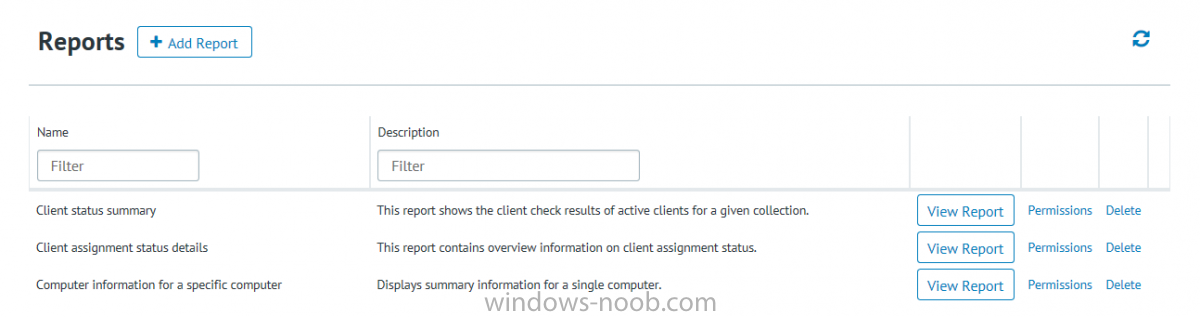
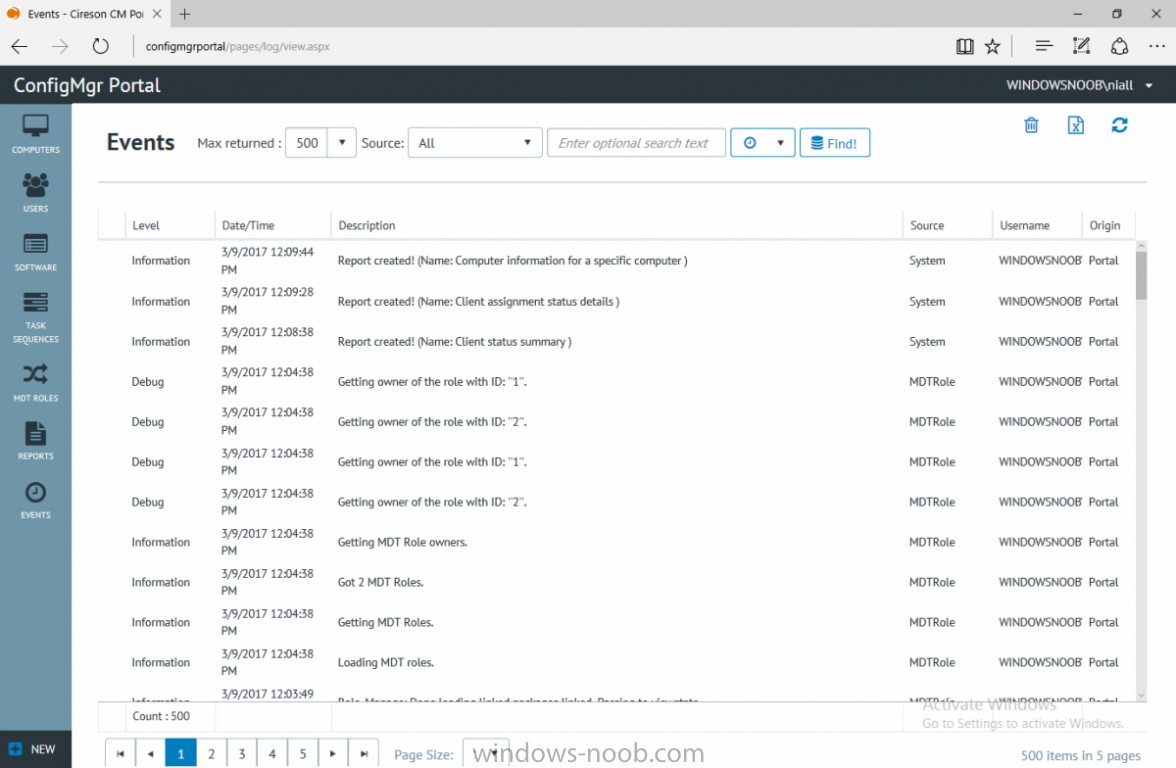
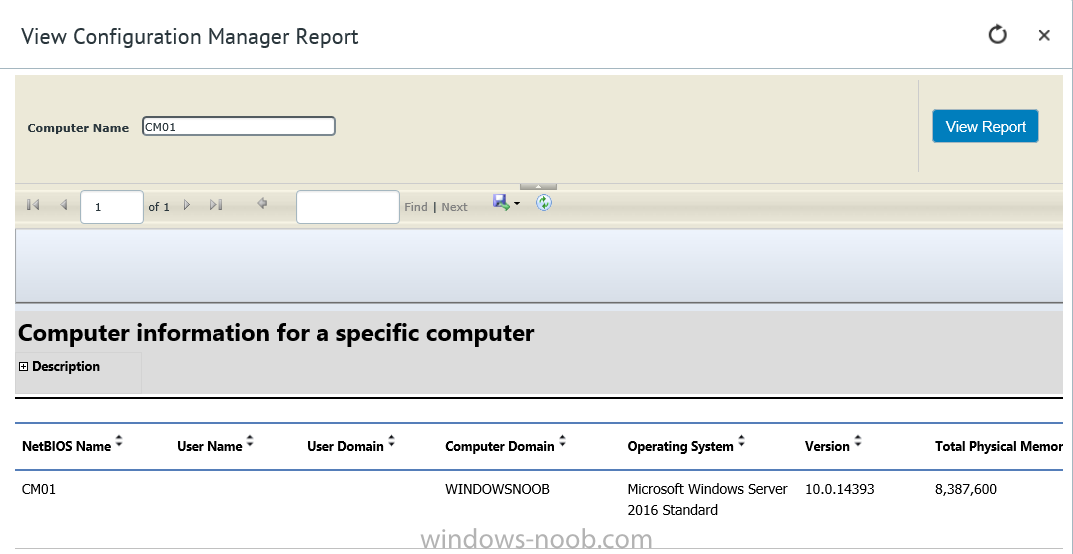
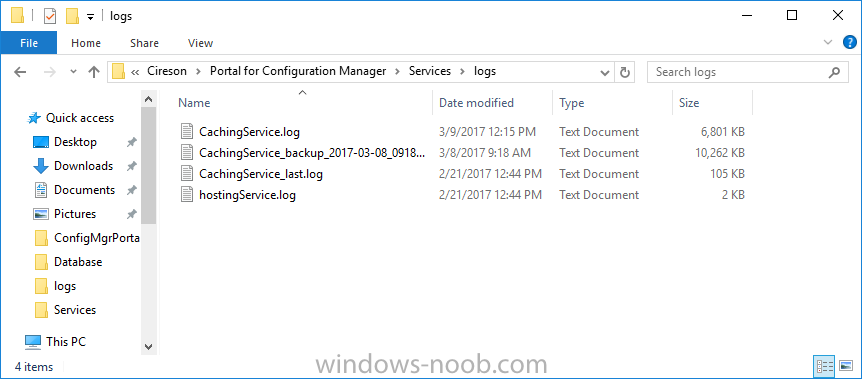
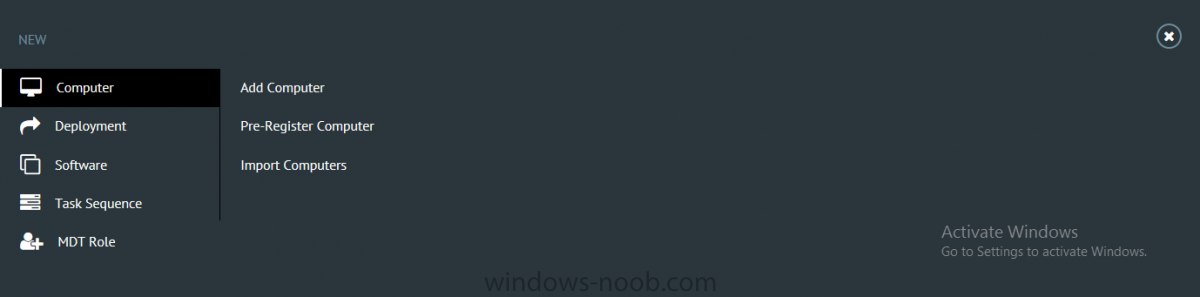
I’ve spent the last few weeks getting familiar with the new ConfigMgr Portal for System Center Configuration Manager (Current Branch) and System Center Configuration Manager 2012 available from Cireson (a windows-noob.com sponsor) and I have to say, I’m impressed. Cireson is a company dedicated to Microsoft Cloud and System Center products and has its headquarters in San Diego. It is well regarded in System Center circles. The company’s quick rise to prominence is no doubt related to the excellent products and services they offer coupled with a team of highly skilled staff. About the portal The Cireson Portal for Configuration Manager is in Ciresons’ own words “a web-based experience for those who would use the Configuration Manager Console to create and deploy software or operating systems. In addition, the Cireson Portal for Configuration Manager allows great customization”. Before I installed the ConfigMgr Portal, I viewed a video by Wally Mead and Shaun Ericson available here. This video covered some of the products functionalities and is well worth seeing. The video explains why using the Cireson ConfigMgr portal can help reduce the number of people having direct access to the Configuration Manager console. After watching the video I quickly built a new lab based on Windows Server 2016, SQL Server 2016 and Configuration Manager 1610 Current Branch as detailed with lots of PowerShell scripts here. Once I had my lab setup I was ready to install the portal, which is currently still in Preview (Preview 2). Requirements The portal has some requirements such as a backend Configuration Manager installation (obviously) and it needs a SQL Server database to host the portal data. You’ll need to provide credentials for connections to the ConfigMgr site database, Reports Server database, ConfigMgr portal database, IIS application pool and MDT database if used. The installation installs a Cireson ConfigMgr Portal hosting service which is used to extract data from the ConfigMgr and MDT databases and to insert it into the portals database. Installing the portal Installation of the portal was straightforward and not too complex, it comes with very detailed instructions for setting up and configuring everything including SQL server changes and IIS manipulation on the ConfigMgr server itself. I took my time with the setup and it took a couple of hours to complete including some emails back and forth with the helpful folks at Cireson who answered any questions I had during the setup. I initially installed Preview 1, and configured it as per the post installation configuration section of the guide and then later upgraded to Preview 2. Upgrading was a straightforward and quick process and instructions were provided to assist with that also. Configuring the Portal It’s recommended to configure settings in the portal prior to using it. To configure settings in the portal simply click on the drop down menu in the upper right corner beside your username as shown here. You have a bunch of options available, the first is General Settings which has a bunch of settings related to the portal. In General Settings you have tabs with different options and expandable content. To change how you ‘view’ the nodes on the left, click on the Views tab. In here you’ll see the standard views that ship with the product and you can edit them to suit your needs or create new views. By clicking on Standard View, Computer View and selecting edit, you can add or remove columns from the view. Tip: To see all of the options in the Columns to show drop down, change your web browsers zoom level to 80%. Once you’ve configured the view to your desires click on Save. Another area of the settings that you should take a look at is Services Settings, and the Scheduled Task Settings for Groups and Users, these specify how often the Hosting Service is set to get data from ConfigMgr. Using the portal Once the ConfigMgr Portal is installed and configured login to a computer with no ConfigMgr console installed, and point your browser to the http://ConfigMgrPortal web address as seen below (in Internet Explorer). You’ll get different results when using different web browsers, and I guess that’s down to what the browsers do or don’t support, for example I had an issue moving a settings window in Edge, but it worked fine in Google Chrome, however zooming the web browser window may solve the problem for you. Note: The first time you open the portal in Internet Explorer you may get a Compatibility View warning as shown below. This is easily fixed with a change to Internet Explorer Compatibility view settings as shown here, remove the checkbox from display intranet sites in compatibility view. Once done the page renders without any warnings and all looks good, but I’d recommend you use a high resolution for the portal (I used 1440x900 for this VM) otherwise objects may clunk together and be hard to read. So what do we have here, well on the left side of the portal is the action pane, which has nodes to manage Computers, Users, Software, Task Sequences, MDT Roles (optional), Reports (requires the Reporting Services Point role installed and configured) and Events. Let’s take a look at these one by one. Computers The ConfigMgr Portal by default, only computers with the client agent installed (but you can of course create a custom view to show those without a client agent installed). The center of the screen is split into two views, with the top showing computer objects and below are various tabs that can reveal information about the computer selected. That’s an important point, you need to select a computer in order to populate the tabs below with data. So for example if you want to see who is the primary user (UDA) of a computer, select it and click on the Primary Users tab. You can even filter your results, so for example to search for all computer with Windows 10, enter that in the Operating System filter and press enter. If you right click on a computer you get a right click menu filled with useful choices such as the ability to Deploy Software or Reinstall the computer. Deploying software to a computer using the portal is as easy as selecting the option from the right click menu and going through a quick and easy to understand wizard. You can even select ConfigMgr options like the purpose of the deployment (Required or Available) or choose to uninstall the software instead of installing it if that rocks your boat. The wizards are clean, modern looking and purposeful. Another right click option, Inventory summary allows you to see what software was inventoried by the ConfigMgr client agent on the computer. Users The Users node is for doing user related actions, and those options are clearly visible. Once again the tabs don’t populate until you select a user, so go ahead and do that. Next click on Available Software to see what software has been deployed to this user. In this case you can see that no software packages are assigned to this user. To deploy software to a user simply right click on the username and choose Deploy Software, as you see the options are less that we have for computers, but this is adequate for our needs. Continue through that wizard until done. Once done you can verify that the software is indeed deployed to the user (it is in the ConfigMgr console, but doesn’t show up in the ConfigMgr Portal due to a known bug with this release explained in the release notes). Software The software node lists all applications and packages you’ve linked to (via settings) in ConfigMgr. The tabs below allow you to get an Overview about the application or package itself, what distribution points it’s distributed to, whether it has any linked MDT Roles, and whether it’s assigned to any resources or collections. You can also right click on a selected application to see what actions are available and they are shown below. The wizards are again, easy to use and modern looking. Task Sequences Task sequences are usually used by ConfigMgr admins to deploy operating systems to computers but can also be used for custom tasks or application installations. The ConfigMgr Portal allows you to view, deploy and even edit (to a degree) task sequences. The right click options offer you the ability to deploy, delete, edit or view the properties of the task sequence as you can see below. The deploy task sequence wizard is the same as for deploying other software and you have a few options to click through. I like the fact that you can add resources during the deployment, so even if the target collection is empty you can add resources by clicking on the + beside the computer name. In the Edit task sequence function you can do basic tasks such as add applications or move groups up or down (change their order). It would be great if this functionality was improved in a later release of the portal. MDT Roles MDT roles allows you to edit applications or packages assigned to roles that were previously created you can’t create the roles here directly, but if you scroll down to the New button section you can do it there. To edit a role click edit in the link on the right, strange that right click doesn’t offer the options here. Reports Reports gives you access to the reports section, as long as you’ve configured the connection to your Reporting Services Point role in settings. When you open the reports node for the first time, it’s blank and that might be confusing, it’s not that it doesn’t see your reports, you just need to link them here by clicking on the Add Report button. Once done your added reports will be listed in Reports. It would be nice to multi-select reports here but I guess that’s a coming feature. To view an added report click on View Report, again a right click action would be nice. Reporting is a key feature in ConfigMgr so having this is essential, I look forward to the improvements that will no doubt come to this area. Events If you want to check on the status of the ConfigMgr Portal click on Events, and below you can see some of the info it logs. Speaking of logs you’ll find a bunch of them at the following location if you want to troubleshoot anything that doesn’t work as planned. Program Files\Cireson\Portal for Configuration Manager\Services\logs\ New button Lastly, there’s nice New button in the bottom left of the portal that gives you access to most of the functions. Click on it to get access to what it provides such as creating a new MDT role, or even creating a custom task sequence (with no steps). And here is what that looks like Summary Using the Cireson ConfigMgr Portal was a joy, it’s intuitive, easy to use, visually clean and modern and you can clearly see the huge amount of work the Cireson team have put into this product to make it stand out from the crowd, I can definitely see people using this for help desks and other roles to ease the burden of ConfigMgr management. You can also customize security roles in the portal (in settings, Security settings) to define what the user sees and has access to, pretty much like RBAC in ConfigMgr. I’m happy to recommend this, and with people like Wally Mead behind it, you know it’s going to be excellent.
-

System Center Endpoint / Data Transfer Service 0X80072EFE Error
anyweb replied to mrey's question in Endpoint Protection
if you move one of these systems to a non remote location, does it start to work ? -

System Center Endpoint / Data Transfer Service 0X80072EFE Error
anyweb replied to mrey's question in Endpoint Protection
the error you get translates to The connection with the server was terminated abnormally Source: Winhttp ----- so do you have network issues ? -
and for those of you reading this topic, do checkout https://www.windows-noob.com/forums/topic/12277-updated-script-how-can-i-check-for-network-connectivity-storage-before-starting-a-task-sequence-in-system-center-2012-r2-configuration-manager/as it automates telling you what the problem is and with what hardware instructions for the previous version here and this is based on this post http://www.niallbrady.com/2011/08/31/missing-nic-driver-in-winpe-boot-image-no-problem/
-
IntroductionIf you’ve been using Intune Preview in Azure you’ll be familiar with the following set of blades in the azure portal, from Intune version 1702 (as explained in this blog post) That view has now been replaced with a new slimmed down ‘modern’ look shown below which just so happens to be Intune version 1703. On the left side you’ll see what options you have to manage devices and users using Intune, In the center, you have 4 big sections to learn more about Intune and to the right side you’ll see quick tasks which are shortcuts to frequently used activities. Changes visibleYou’ll probably noticed the new Software Updates node which you can use for deploying Windows 10 updates to CB or CBB rings and that the link to the legacy or Classic Intune Portal is gone. Access Control is now labeled Intune Roles and On-Premise access is visible also. There’s a Setup TeamViewer Connector under devices, but it doesn’t do anything yet. I’ll report more about the new changes as I dig into them cheers niall
-
you can adjust the SQL services as you require them, but this script should be enough to get you up and running with SCCM in a SQL Server 2016 environment, I have it running just fine in 3 labs as regards where you store the logs that only really matters if the drives are on different spinning disks
-
just to be clear, do you want to manage updates using WSUS or SCCM ?
-

Windows 10 Deployment (Getting stuck after OS Install)
anyweb replied to curtblunt's question in Microsoft Deployment Toolkit (MDT)
hmm can you email me the log file then ? niall @ windows-noob.com -
Introduction Another month has passed by and finally we get to play with the latest Technical Preview release of System Center Configuration Manager from Microsoft. There are two main versions (of Configuration Manager) available: System Center Configuration Manager (Current Branch) System Center Configuration Manager (Technical Preview) System Center Configuration Manager (Current Branch) is designed for use in production, for managing anything from small to very large Enterprises whereas System Center Configuration Manager (Technical Preview) is for lab environments only and is limited to 10 clients. The Technical Preview releases are released monthly, and contain the latest and greatest features being trialed in the product, and usually these new features are the result of feedback from uservoice. Current Branch releases on the other hand are released only a few times per year and contain stable, tested features that are mature enough to release into production environments. System Center Configuration Manager Technical Preview 1702 is now available, it was originally scheduled to be released last Friday (Friday 24th, 2017) but was delayed due to upgrade problems. This release offers the following new features, one of which I’m proud of because it was my uservoice !: Azure Active Directory Domain Services support – You can install a ConfigMgr site on an Azure virtual machine that is connected to Azure Active Directory Domain Services, and use the site to manage other Azure virtual machines connected to the same domain. Improvements for in-console search – Based on User Voice feedback, we have added several improvements to in-console search, including searching by Object Path, preservation of search text and preservation of your decision to search sub-nodes. Windows Update for Business integration – You can now implement Windows Update for Business assessment results as part of Conditional Access compliance policy conditional rules. Customize high-risk deployment warning – You can now customize the Software Center warning when running a high-risk deployment, such as a task sequence to install a new operating system. The default string regarding data may not apply in scenarios like in-place upgrade. Close executable files at the deadline when they would block application installation – If executable files are listed on the Install Behavior tab for a deployment type and the application is deployed to a collection as required, then a more intrusive notification experience is provided to inform the user, and the specified executable files will be closed automatically at the deadline. This release also includes the following improvements for customers using System Center Configuration Manager connected with Microsoft Intune to manage mobile devices: Non-Compliant Apps Compliance Settings – Add iOS and Android applications to a non-compliant apps rule in a compliance policy to trigger conditional access if the devices have those applications installed. PFX Certificate Creation and Distribution and S/MIME Support – Admins can create and deploy PFX certificates to users. These certificates can then be used for S/MIME encryption and decryption by devices that the user has enrolled. Android for Work Support – You can now manage Android for Work devices. This enables you to enroll devices, approve and deploy apps, and configure policies for Android for Work devices. Installing Technical Preview 1702So how do you get Technical Preview 1702 installed ? There are two methods: Upgrade from a previous installation of Technical Preview (as shown below) Do a clean install of Technical Preview 1610 by using the following guide and replace the base version in the guide (which is TP1510) with the TP1610 release and then upgrade. Upgrading to TP1702Once you have a Technical Preview release installed, in the Configuration Manager console browse to Cloud Services, Updates and Servicing (or if you already are using TP1701 then choose Administration, Overview, Updates and Servicing) as shown below and click on Check for Updates (in the ribbon) followed by clicking on the OK button. And as instructed open the DMPDownloader.log in CMTrace to monitor the process of checking for updates. Here you can see Generating state message: 6 which highlights that it’s found an applicable update. Generating state message: 6 for package 0aff9384-6a8d-4dc5-a8bf-4e9afd2d51f1 and looking in the ConfigMgr console you’ll see it’s in a state of downloading And then with a state of Available once it has completed downloading. You need to click refresh in the ConfigMgr console to update the view. Installing the Update Right click on the update and choose Install Update Pack. when the Wizard appears, make your choice for pre-reqs and click next. review the features included in this update pack Before clicking next at the Client update settings please see this post accept the EULA and configure the software assurance expiration date and click through to the summary at which point the update will be listed as a state of Installing. Monitor the installationIn the console, the state will change to Installing. At this point you can use CMTrace to open the CMUpdate.log file to monitor the installation live. Note: The CMUpdate.log will take some time to start logging the installation of the update, so be patient if nothing appears to happen, it will. Once the update is complete, you should see a hman notification in the log, don’t worry about those red lines, they are normal. Note: If you don’t see this and see an upgrade failure message then scroll up in the CMUpdate.log file to determine what the failure reason was. You can always retry an upgrade (maybe not enough available ram for example, which a server restart before the upgrade can solve). After the update is complete, you get the chance to update the ConfigMgr Console via a popup, the new version is 5.00.8496.1000 And after all is done you’ll see this Capabilities in SCCM 1702 TP – https://docs.microsoft.com/en-us/sccm/core/get-started/capabilities-in-technical-preview-1702
-

Widows Update location The secondary distribution
anyweb replied to honestvip's question in Software Update Point
look at the windowsupdate.log in C:\Windows (or use Powershell with the get-windowsupdatelog cmdlet in windows 10) to see where your clients are downloading updates from.- 1 reply
-
- 1
-

-
why do you want to use this tool, i'm not familiar with it, can't you do the partitioning using a task sequence ?