Search the Community
Showing results for tags 'Software updates'.
-
Hello, The guy the use to do the server updates retired and my boss would like to utilize SCCM 2012 to do the updates. They are currently getting there updates from WSUS and group policy. He has specific policies setup to restart specific servers at certain times of the day according to what works for the users. I'm thinking the best way of doing this with SCCM would be to create a software update group that contains those servers he had in the policy which can get restarted on the same day or at the same time. My question is that these servers are Server 2003, Server 2008 and Server 2012 systems. Can I have one group that contains three different Operating Systems and apply all security and critical updates to these servers or should each group only contain one specific Operating System? Any help on the best way to setup these groups and deploy windows updates to them would be greatly appreciated. How does your organization go about deploying Windows Updates to your servers\desktops? Thanks Pat
- 1 reply
-
- Software Updates
- Windows Updates
- (and 6 more)
-
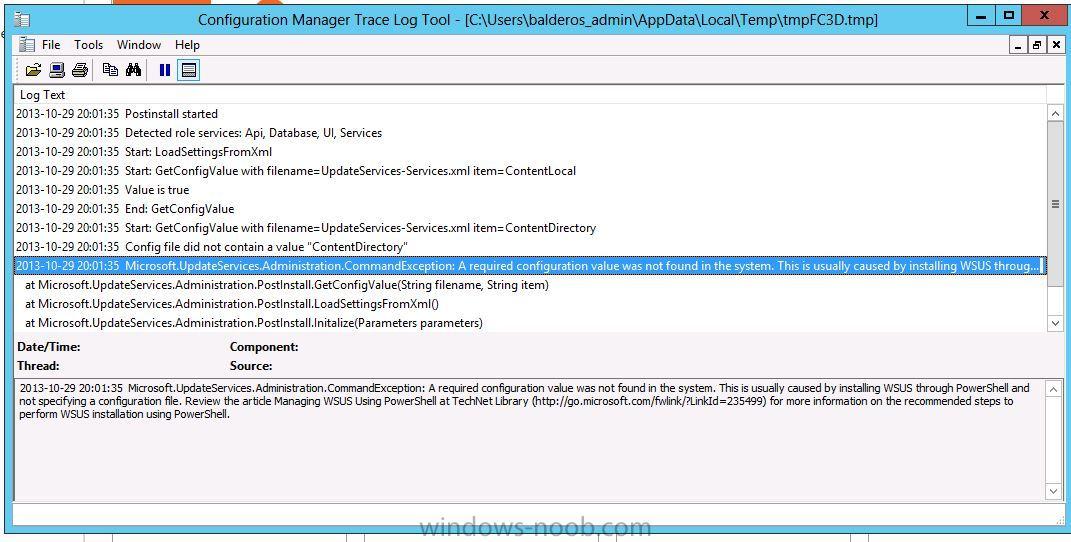
Hello all I am hoping I could get some help with this strange issue: I am trying to install WSUS on my sccm server prior to the software update point. This what I have done so far: In server manger I select to install the WSUS role>Click next (I notice there is a feature option to install Windows internal database) I unchecked this option because I am using my existing sql server for the WSUS instance. I cant seem to find anything that say tells me that when installing sccm 2012 on Windows Server 2012 and you are using the sql database instance for WSUS to do xyz. In my case as mentioned before unchecked the Windows Internal Database Feature. Then under Roles Services there are three option: WID Database, WSUS Services, Database. I chose WSUS Services and Database. On the next page I defined my source for the downloads, then the next page DB Instance I entered the instance of the sql server which in my case is also on my sccm 2012 server VMSCCM is the name> Click Check Connection and that was successfully connected to the server. So here is where everything goes wrong. I then select to install everything at the confirmation page. reboot the server once rebooted I open server manager and there is message that says Launch post - installation configuration. I then get the following error "Post-deployment configuration failed see log below is a image for the log located in c:\users\username\appdata\local\temp\tmpFC3D\
- 5 replies
-
- wsus
- sccm 2012R2
-
(and 1 more)
Tagged with:
-
We have a trouble patch (http://blogs.technet.com/b/office_sustained_engineering/archive/2013/09/11/outlook-folder-pane-disappears-after-installing-september-2013-public-update.aspx) that is messing things up and I can't figure out how remove this one update out of the Automatic Deployment Rule I setup for Office 2013 updates. Is there a simple way to remove one specific update out of the group? Thanks!
-
Can anyone tell me where to look to find out why software updates would not have run/installed at deadline? We deployed updates last night with a deadline of 8:00pm. We have a nightly maintenance window from 8:00pm to 4:00am. Typically updates run without issue, but this morning I've come in to updates being available for install. Nevermind i found it. For any other n00b that may be looking. UpdatesDeployment.log on the client, as if it could be any clearer. Sorry my brain is apparently sleeping in this morning.
- 3 replies
-
- maintenance window
- deadline
-
(and 2 more)
Tagged with:
-
Hi, we're looking at deploying windows / office updates to our Windows 7 machines via SCCM 2007 R3. We have both x64 and x86 machines in our environment. Most of the x64 machines are remote users and x86 machines are LAN connected in Head Office. Question is would you be better off patching these as seperate entities ie having deployment packages for x86 and x64 or have one set of packages that deploys to both machine types? We're trying to avoid making the packages we push out over VPN to the remote users larger than needed as they're cached locally from DP prior to installation. Any advice would be most helpful.... Cheers
-
I am trying to figure out how to remedy a bunch of expired Microsoft updates (1,000+) that Is showing up in my SCCM console after I ran my first sync once WSUS and SUP was installed. Below are the steps take so far: Removed SUP role from my site server (SCCM) Removed WSUS from Server 2012 Restarted server Reinstalled WSUS (I noticed that the 2 previous synchronizations I performed from the WSUS console on the server was still there as if I never deleted WSUS.) Reinstalled SUP on the site server (SCCM). This time from the product list I only selected Security updates as opposed to: Security, Critical, and just plain old updates, which is why I think I have over 1,000 expired updates Also I elected to delete the expired updates as soon as they are superseded. I then let the synced the updates from the SCCM and let it run over night. I went to check the All updates section under application management node and there are about 648 new none-expired updates but the old expired updates are still there (over 1,000) I did notice also that the previous syncs that I performed on the WSUS console are still there even after I removed the WSUS role Hmmm, scratching my head.
- 2 replies
-
- application management
- Software updates
-
(and 3 more)
Tagged with:
-
Hello all I just finish configuring WSUS and my SUP on my SCCM server but seem to have made an error in judgment. During the setup of the SUP I was given the option to select which software updates to received form Microsoft: Security, Critical, Office etc. Well I selected one called updates and I think that was a general option which is why I have like 1,000.00 updates siting in the All Software Updates section. I would like to do the following 1) reconfigure which updated I subscribe to (hopefully this does not involve removing sup or WSUS) 2) Remove all of the updates and resync from WSUS from scratch.
- 4 replies
-
- SCCM 2012 sp1
- software updates
-
(and 1 more)
Tagged with:
-
I am new to SCCM and have built a test lab to learn the product. So far everything has been good, but I am running into an issue where my clients are not respecting the defined maintenance window. As far as I can tell, the device is not a member of any other collections with additional windows defined. The deployment is not configured to allow installations outside the window after the deadline is reached, so I am not sure what is allowing the clients to pull the updates outside the window. Some advice would be greatly appreciated!
-
I feel like I keep posting questions. I tried to do a search on this but everything was bringing me to the exact opposite of what I am trying to do. It seems that even though I have maintenance window set for 18 hours on a collection every day for my testing. The machines install the updates but the user's are prompted to restart instead of just restarting the computers. I can't seem to figure out how to force the computers to restart, RESTART Suppression is only set for servers.
- 3 replies
-
- restart clients
- sccm 2012
-
(and 2 more)
Tagged with:
-
Hi, I've noticed something odd about my Windows Updates. I have ADRs which run on Patch Tuesday, one for Windows 7, 8, Office 2010 and 2013. The updates are placed in four respective Software Update Groups. It seems like older updates are removed from those SUGs. The rules have been in place since the beginning of January. Right now there should be a few dozen updates in this SUG but there are only two. If I filter all my updates like below (to double check that the updates aren't expired/superseded) it finds 24 updates. Why aren't these in my SUG above? The ADR is set to add updates to an existing SUG. Here are the filters. I can't figure out what's happening. My goal was to not really have to pay updates any attention but it seems like I now have to spend time double-checking that all my updates are deployed correctly.
- 6 replies
-
- adr
- software updates
-
(and 2 more)
Tagged with:
-
I've just setup SCUP 2011 on my SCCM 2012 (2008 R2) server and managed to do the following: Configured: WSUS on same server, connected to Config Manager. Downloaded Adobe Updates via the SCUP Catalogue. Got the updates Published to SCCM 2012 and assigned to a Package and Software Group within SCCM Exported the WSUS cert and reimported as Trusted Publisher and Root on the test client and also the server. Assigned deployment to test collection that has one computer in need of those updates. However, on the client itself, I cannot get it to detect and download the relevant updates for Adobe Reader, I've been trawling through the logs looking for evidence that the updates were detected and downloaded, and also manually checked the ccmcache and also (WSUS) softwaredownload folders, all had no downloaded files or references of the Adobe updates. I can't think of anything else and there is nothing obvious in the logs that I can see, hopefully someone with experience can point me in the right direction? The client has the following set via a test GPO: AcceptTrustedPublisherCerts = 1 WUServer = http:sccm-server:80 WUStatusServer = http:sccm-server:80 UpdatesHandler.log Successfully initiated scan. UpdatesHandler 08/04/2013 13:33:39 4036 (0x0FC4) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 13:33:39 3608 (0x0E18) Successfully initiated scan. UpdatesHandler 08/04/2013 13:33:39 3608 (0x0E18) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 13:33:40 4036 (0x0FC4) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 13:33:44 4980 (0x1374) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 13:33:48 3608 (0x0E18) Successfully initiated scan. UpdatesHandler 08/04/2013 13:33:49 3608 (0x0E18) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 13:34:54 4980 (0x1374) CUpdatesAgent::FinalConstruct entered UpdatesHandler 08/04/2013 14:50:07 3332 (0x0D04) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 14:56:43 3524 (0x0DC4) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 14:56:43 3108 (0x0C24) Successfully initiated scan. UpdatesHandler 08/04/2013 14:56:43 3524 (0x0DC4) Successfully initiated scan. UpdatesHandler 08/04/2013 14:56:43 3108 (0x0C24) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 14:56:43 3524 (0x0DC4) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 14:56:43 3416 (0x0D58) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 15:31:26 3864 (0x0F18) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 15:31:26 5916 (0x171C) Successfully initiated scan. UpdatesHandler 08/04/2013 15:31:26 3864 (0x0F18) Successfully initiated scan. UpdatesHandler 08/04/2013 15:31:26 5916 (0x171C) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 15:32:20 5232 (0x1470) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 15:32:21 5232 (0x1470) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:24:32 4816 (0x12D0) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:24:32 3068 (0x0BFC) Successfully initiated scan. UpdatesHandler 08/04/2013 16:24:32 4816 (0x12D0) Successfully initiated scan. UpdatesHandler 08/04/2013 16:24:33 3068 (0x0BFC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:25:21 4824 (0x12D8) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:25:21 3068 (0x0BFC) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:30:13 3744 (0x0EA0) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:30:13 4824 (0x12D8) Successfully initiated scan. UpdatesHandler 08/04/2013 16:30:13 3744 (0x0EA0) Successfully initiated scan. UpdatesHandler 08/04/2013 16:30:13 4824 (0x12D8) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:30:19 2160 (0x0870) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:30:21 3744 (0x0EA0) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:39:13 4016 (0x0FB0) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:39:13 4572 (0x11DC) Successfully initiated scan. UpdatesHandler 08/04/2013 16:39:13 4016 (0x0FB0) Successfully initiated scan. UpdatesHandler 08/04/2013 16:39:13 4572 (0x11DC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:40:02 2524 (0x09DC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:40:02 2524 (0x09DC) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:54:11 5192 (0x1448) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 16:54:11 3692 (0x0E6C) Successfully initiated scan. UpdatesHandler 08/04/2013 16:54:11 3692 (0x0E6C) Successfully initiated scan. UpdatesHandler 08/04/2013 16:54:11 5192 (0x1448) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:55:14 5624 (0x15F8) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 16:55:15 4904 (0x1328) CUpdatesAgent::FinalConstruct entered UpdatesHandler 08/04/2013 17:09:42 2604 (0x0A2C) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:11:17 4780 (0x12AC) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:11:17 4872 (0x1308) Successfully initiated scan. UpdatesHandler 08/04/2013 17:11:18 4872 (0x1308) Successfully initiated scan. UpdatesHandler 08/04/2013 17:11:18 4780 (0x12AC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:13:03 3812 (0x0EE4) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:13:03 4780 (0x12AC) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:13:37 3812 (0x0EE4) Successfully initiated scan. UpdatesHandler 08/04/2013 17:13:37 3812 (0x0EE4) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:13:37 4780 (0x12AC) Successfully initiated scan. UpdatesHandler 08/04/2013 17:13:37 4780 (0x12AC) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:14:16 5180 (0x143C) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:14:16 1056 (0x0420) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C) Successfully initiated scan. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C) Initiating updates scan for checking applicability. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C) Successfully initiated scan. UpdatesHandler 08/04/2013 17:46:08 4764 (0x129C) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:47:07 4500 (0x1194) Updates scan completion received, result = 0x0. UpdatesHandler 08/04/2013 17:47:07 964 (0x03C4) UpdatesDeployment.log Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_499fc6e1-f6de-4e4c-b98d-41ca21bee49b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e93c80ff-812b-4640-a7fb-d3712b86e3b1) added to the targeted list of deployment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B}) UpdatesDeploymentAgent 08/04/2013 16:55:15 5624 (0x15F8) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_49ddec56-93f2-48e7-98af-ecd54526d34c) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_5c22235f-a3d9-48db-95eb-a60ec1886e8e) added to the targeted list of deployment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B}) UpdatesDeploymentAgent 08/04/2013 16:55:15 5624 (0x15F8) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9e40eb5c-184a-494d-be46-8b140386179b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_da767d4a-8677-4b9d-9f0b-365f14e19ae1) added to the targeted list of deployment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B}) UpdatesDeploymentAgent 08/04/2013 16:55:15 5624 (0x15F8) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_d0fbac2f-d08f-4a7b-a826-92b1c5ae0bc5) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 16:55:15 4904 (0x1328) EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 0 UpdatesDeploymentAgent 08/04/2013 16:56:29 2892 (0x0B4C) User logoff system task UpdatesDeploymentAgent 08/04/2013 17:03:45 4708 (0x1264) Service startup system task UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) Software Updates feature is enabled UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) Total Pending reboot updates = 0 UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) No pending reboot updates at system restart. UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) No current service window available to run updates assignment with time required = 1 UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) CUpdateAssignmentsManager::OnThirdPartyOrchestrationSettingChange - No pending install assignment UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) Startup task completed UpdatesDeploymentAgent 08/04/2013 17:09:29 524 (0x020C) User logon system task UpdatesDeploymentAgent 08/04/2013 17:09:50 988 (0x03DC) Assignment {0ADCDD92-9E6F-4796-AFFD-7013EB4E554B} has total CI = 20 UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) OnPolicyDelete for assignment ({0ADCDD92-9E6F-4796-AFFD-7013EB4E554B})... UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_27fc50b4-5982-4d58-a13d-53bd1f3806ea", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_957317cf-ef0d-4fa7-a2ad-5d2db2cf355e", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_1f6d4200-fcb6-4a4c-8ad7-ab76c529bff3", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_7ad922e0-685f-4723-9da3-4d7acefb4706", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e9e8a81d-ed5a-4af3-963e-2dc4413e3c3e", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_42cc6726-c3fe-464b-b8ac-38ec00766262", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_f51bc4bd-7424-4c47-ae97-714a8e3895b5", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_04874d8a-71a5-43d9-8531-eb19fdf319e6", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_0e79069c-cdca-4c91-aad3-e21ede710634", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_6d8590bd-038e-4455-9764-30875ccbf0c7", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_02fe5101-40eb-4d91-aa9d-5727060aefba", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_07151137-3b83-4064-8fc2-7bf983d6b08b", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_421e86ff-37e0-4199-9a0c-4976332bbcdf", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_521d70cd-3256-4c26-96f8-b7c3c4adc113", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9b65fe9a-721e-4390-860d-02c1dbffa10f", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9caf7699-d7f8-4cbb-95c9-002cbe3df07d", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_022d7dab-a021-4318-9c71-16323944584d", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e93c80ff-812b-4640-a7fb-d3712b86e3b1", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_5c22235f-a3d9-48db-95eb-a60ec1886e8e", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) Raising client SDK event for class CCM_SoftwareUpdate, instance CCM_SoftwareUpdate.UpdateID="Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_da767d4a-8677-4b9d-9f0b-365f14e19ae1", actionType 12l, value NULL, user NULL, session 4294967295l, level 0l, verbosity 30l UpdatesDeploymentAgent 08/04/2013 17:10:01 2516 (0x09D4) EnumerateUpdates for action (UpdateActionInstall) - Total actionable updates = 0 UpdatesDeploymentAgent 08/04/2013 17:10:10 3484 (0x0D9C) Message received: '<?xml version='1.0' ?><SoftwareUpdatesMessage MessageType='EvaluateAssignments'><UseCachedResults>False</UseCachedResults></SoftwareUpdatesMessage>' UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Removing scan history to force non cached results UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Assignment {47ABB848-E3B5-405B-AA5E-01514176142F} has total CI = 7 UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Detection job ({C92EAD93-F8F7-4257-BD47-FF953B523427}) started for assignment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Started evaluation for assignment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Assignment {28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C} has total CI = 20 UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Detection job ({4BDCE35B-6B75-4DE8-BB1D-9ADD513CA2D0}) started for assignment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Started evaluation for assignment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) Evaluation initiated for (2) assignments. UpdatesDeploymentAgent 08/04/2013 17:11:17 2768 (0x0AD0) DetectJob completion received for assignment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:03 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9703dec9-deaf-4566-b966-aeca447a4ba4) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_a13356e5-6224-44e0-9020-9a3c924da131) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_244b7a38-eb9e-4632-a299-b085587d477c) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_499fc6e1-f6de-4e4c-b98d-41ca21bee49b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_49ddec56-93f2-48e7-98af-ecd54526d34c) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9e40eb5c-184a-494d-be46-8b140386179b) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_d0fbac2f-d08f-4a7b-a826-92b1c5ae0bc5) added to the targeted list of deployment ({47ABB848-E3B5-405B-AA5E-01514176142F}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) DetectJob completion received for assignment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_27fc50b4-5982-4d58-a13d-53bd1f3806ea) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_957317cf-ef0d-4fa7-a2ad-5d2db2cf355e) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_1f6d4200-fcb6-4a4c-8ad7-ab76c529bff3) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_7ad922e0-685f-4723-9da3-4d7acefb4706) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_e9e8a81d-ed5a-4af3-963e-2dc4413e3c3e) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_42cc6726-c3fe-464b-b8ac-38ec00766262) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_f51bc4bd-7424-4c47-ae97-714a8e3895b5) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_04874d8a-71a5-43d9-8531-eb19fdf319e6) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_0e79069c-cdca-4c91-aad3-e21ede710634) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_6d8590bd-038e-4455-9764-30875ccbf0c7) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_02fe5101-40eb-4d91-aa9d-5727060aefba) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_07151137-3b83-4064-8fc2-7bf983d6b08b) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_421e86ff-37e0-4199-9a0c-4976332bbcdf) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_521d70cd-3256-4c26-96f8-b7c3c4adc113) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9b65fe9a-721e-4390-860d-02c1dbffa10f) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 4780 (0x12AC) Update (Site_AF66F129-6866-43D5-B685-A61D11C4237C/SUM_9caf7699-d7f8-4cbb-95c9-002cbe3df07d) added to the targeted list of deployment ({28E59DB8-2FA1-4DDD-B25E-FE98FE18C18C}) UpdatesDeploymentAgent 08/04/2013 17:13:04 WUAHandler.log Async searching completed. WUAHandler 08/04/2013 15:32:17 4964 (0x1364) Successfully completed scan. WUAHandler 08/04/2013 15:32:19 1032 (0x0408) Scan results will include all superseded updates. WUAHandler 08/04/2013 15:32:20 1044 (0x0414) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 15:32:20 1044 (0x0414) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 15:32:20 1044 (0x0414) Async searching completed. WUAHandler 08/04/2013 15:32:20 4960 (0x1360) Successfully completed scan. WUAHandler 08/04/2013 15:32:20 1044 (0x0414) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 16:24:30 4816 (0x12D0) Existing WUA Managed server was already set (http://:80), skipping Group Policy registration. WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:30:21 2160 (0x0870) Async searching completed. WUAHandler 08/04/2013 16:31:08 1096 (0x0448) Successfully completed scan. WUAHandler 08/04/2013 16:31:11 3744 (0x0EA0) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:39:11 4016 (0x0FB0) Async searching completed. WUAHandler 08/04/2013 16:39:58 3424 (0x0D60) Successfully completed scan. WUAHandler 08/04/2013 16:40:00 4016 (0x0FB0) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:40:01 6024 (0x1788) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 16:40:01 6024 (0x1788) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:40:01 6024 (0x1788) Async searching completed. WUAHandler 08/04/2013 16:40:01 4956 (0x135C) Successfully completed scan. WUAHandler 08/04/2013 16:40:01 6024 (0x1788) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 16:54:09 5244 (0x147C) Enabling WUA Managed server policy to use server: http://sccmserver:80 WUAHandler 08/04/2013 16:54:09 5244 (0x147C) Waiting for 2 mins for Group Policy to notify of WUA policy change... WUAHandler 08/04/2013 16:54:09 5244 (0x147C) Waiting for 30 secs for policy to take effect on WU Agent. WUAHandler 08/04/2013 16:54:16 5244 (0x147C) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 16:54:46 5244 (0x147C) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:54:46 5244 (0x147C) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 16:54:46 5244 (0x147C) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:54:46 5244 (0x147C) Async searching completed. WUAHandler 08/04/2013 16:55:11 5944 (0x1738) Successfully completed scan. WUAHandler 08/04/2013 16:55:13 5624 (0x15F8) Scan results will include all superseded updates. WUAHandler 08/04/2013 16:55:14 5244 (0x147C) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 16:55:14 5244 (0x147C) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 16:55:14 5244 (0x147C) Async searching completed. WUAHandler 08/04/2013 16:55:14 5516 (0x158C) Successfully completed scan. WUAHandler 08/04/2013 16:55:14 4904 (0x1328) CWuaHandler::SetCategoriesForLeafStateReportingExclusion called with E0789628-CE08-4437-BE74-2495B842F43B WUAHandler 08/04/2013 17:09:26 2604 (0x0A2C) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:11:15 4780 (0x12AC) Async searching completed. WUAHandler 08/04/2013 17:13:00 4208 (0x1070) Successfully completed scan. WUAHandler 08/04/2013 17:13:02 4780 (0x12AC) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'E1D507BE-497C-D8FD-61D7-B0D93EE399CA') OR (DeploymentAction=* AND Type='Software' AND CategoryIDs contains '3B36FCFD-0384-EA97-2D49-1349AE748647') OR (DeploymentAction=* AND Type='Software' AND CategoryIDs contains '70CFAD70-6629-B54B-5819-C809A605515E')) WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4) Async searching completed. WUAHandler 08/04/2013 17:13:03 4344 (0x10F8) Successfully completed scan. WUAHandler 08/04/2013 17:13:03 3812 (0x0EE4) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:13:34 1056 (0x0420) Async searching completed. WUAHandler 08/04/2013 17:14:13 5476 (0x1564) Successfully completed scan. WUAHandler 08/04/2013 17:14:15 1056 (0x0420) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4) Async searching completed. WUAHandler 08/04/2013 17:14:16 5648 (0x1610) Successfully completed scan. WUAHandler 08/04/2013 17:14:16 3812 (0x0EE4) Its a WSUS Update Source type ({AF66F129-6866-43D5-B685-A61D11C4237C}), adding it. WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Existing WUA Managed server was already set (http://sccmserver:80), skipping Group Policy registration. WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Added Update Source ({AF66F129-6866-43D5-B685-A61D11C4237C}) of content type: 2 WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Search Criteria is (DeploymentAction=* AND Type='Software') OR (DeploymentAction=* AND Type='Driver') WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:46:06 964 (0x03C4) Async searching completed. WUAHandler 08/04/2013 17:47:03 4948 (0x1354) Successfully completed scan. WUAHandler 08/04/2013 17:47:05 964 (0x03C4) Scan results will include all superseded updates. WUAHandler 08/04/2013 17:47:06 4764 (0x129C) Search Criteria is ((DeploymentAction=* AND Type='Software' AND CategoryIDs contains 'BFE5B177-A086-47A0-B102-097E4FA1F807')) WUAHandler 08/04/2013 17:47:06 4764 (0x129C) Async searching of updates using WUAgent started. WUAHandler 08/04/2013 17:47:06 4764 (0x129C) Async searching completed. WUAHandler 08/04/2013 17:47:06 5180 (0x143C) Successfully completed scan. WUAHandler 08/04/2013 17:47:07 4764 (0x129C) UpdateStore.log Update status from update (eb303398-da7c-4ce6-b8db-254409b32c39) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (eb30575d-51df-4c24-87dc-9b9c6dc8aa04) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (eb7a169f-6bca-4e00-a52a-623c063c162d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (ebbdc330-bd19-47b9-9e08-c4f32694429b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (ec1f4a29-8828-4fbe-b101-5a89321d8e7f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (edcc7a72-ffa0-4753-b59a-976044bbb012) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (efb911ae-5fba-48c7-8060-51734e3c1144) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f019d0aa-dfcf-4af8-b846-d38f8f7239e7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f0b50507-6c86-41d6-9350-6a8af21f76c7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f120b7a8-9ee3-4e95-8628-ac27b0d1df85) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f19502ff-7637-4ed8-bbc1-1b2508e56e2b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f1b1b1e1-2b22-4445-8a9c-5924bf945d32) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f21b0303-4d18-4a9b-9bda-8a796062189b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f284dc51-5659-4534-a1c7-6b9dbfe9453a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f2b28914-a6bc-44c5-ac04-9e7fbdea657e) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f2c6b0b8-f2cf-4f6c-8d64-6a21b9ca86d2) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f307ffeb-f424-4a79-8bc3-d472be542dec) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f45f3c72-427b-4889-a627-836244bf1ce1) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f4683760-71cc-4e3f-82a0-e1c164955163) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f51a0e5b-24a9-4be1-8b36-0f22f99949e7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f5202a56-ff34-401d-a040-f97c7f70891c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f53b1817-e327-438b-afb8-0cd5a0f95cb2) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f54ace97-a003-44a4-9e36-ef7071f6ce9d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f591538a-2c8f-4dc4-8b17-8b07c9a851ca) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f808dbaf-bec7-4dfb-a0cc-25290a7cd368) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (f9b10375-898c-4d12-8722-b2f7f6e81521) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fabc6fae-c385-4543-a483-1b1cadfade98) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fabea4ad-b256-4b4e-b9cf-988bcfd5463f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fbc62e30-1128-4af5-9cb7-e1e349eb1b23) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fc5608e4-a70d-4344-b358-2847f4a57434) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fc5b1588-f912-4c1b-9f87-4ee1b427c5b1) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fc7c3752-4c17-473c-8bff-75eed375fd61) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fd8b7365-bc78-48e5-96c0-53682b94a607) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (fdc8ef3a-11eb-45e6-9e0e-38a193f7b48c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (ff1d0808-8bb8-47ea-90c4-f7e806f7bde0) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Successfully done with SetStatus() operation. UpdatesStore 08/04/2013 17:47:06 964 (0x03C4) Update status from update (097d6f40-e0dc-4410-893f-24d5326aed8a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (0aa3cf0a-2269-4356-ad99-0e3ca8eb439f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (0b92accc-057d-408a-8e6e-0867f21f015f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (138bccfd-40ac-4a5d-84f0-3e5bf9743e42) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (161ed7f2-9f54-4625-914c-2b3c93040db4) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (2b487f1d-e072-4be7-986c-4355c3372cd1) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (324f1032-de0c-406e-b611-34b99c64e21d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (3abe760c-4578-4c84-a1cb-bf1df019efe4) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (40bd5a76-a368-4088-b172-a9e5dd1e5e3a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (40ccd4f1-cc6f-4368-968b-29d10e57b05f) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (48f658bc-fec4-4464-8f01-db68c5ab1720) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (596adb47-108d-482d-85ba-a513621434b7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (5eca77b2-63e0-4df3-b1b0-acb90f28c532) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (7079beeb-6120-4afd-ad07-fb4dfa284fbe) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (71a29c39-e160-4b00-9b2f-d9924c8e09d5) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (744f9366-c308-44b2-8542-ca31c229179d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (75914178-2bdf-4fd3-b537-e2a517734bc7) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (79f342ab-66e7-42a7-8315-2677f99f20c5) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (7c25aee0-71f5-4fda-8763-effae905b564) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (82538218-b3eb-4c56-a9b8-fdb358869d2b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (979b9aa2-dcf8-45d6-a31d-63df2a02d043) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (97e091c7-35eb-4da0-9346-e6f33115c8ed) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (98c62b24-a3dd-4843-ad1a-e08d95624f00) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (a429515b-9216-4277-bd4d-bf0593542c0d) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (a61bd9f9-6940-408c-a80e-5a7dc4f5e1a2) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (a643a7c6-aa86-480c-b9e8-7f9abca811e6) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (ac8b33b5-2df2-4e6a-8d48-105ba0cc3bff) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (af91fcf0-fc28-4293-acc6-598fdcea359a) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (afdd5d5e-2cc2-4a6a-a44f-e45a275702f5) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (b047a38c-47a5-4ac7-b42a-0c4d80f3341c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (b14fba1c-2b3b-4746-8801-104180701e7e) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (b628f40e-33de-4a37-81ae-9c2868c75373) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (c6164205-7295-4670-8a2f-8dad2d0682b0) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (d7568b8a-3d37-43de-8d65-b6a0a73b010c) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (de4cbbf4-443f-4bb7-aebf-8da2fcc7b706) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (e5cbc9ff-0953-4efc-8acc-6a130bd4385b) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (eb30575d-51df-4c24-87dc-9b9c6dc8aa04) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Update status from update (fc5608e4-a70d-4344-b358-2847f4a57434) already exists, will modify existing instance. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Successfully done with SetStatus() operation. UpdatesStore 08/04/2013 17:47:07 4764 (0x129C) Querying update status of 20 updates. UpdatesStore 08/04/2013 17:47:07 4500 (0x1194) Querying update status completed successfully. UpdatesStore 08/04/2013 17:47:07 4500 (0x1194) Querying update status of 7 updates. UpdatesStore 08/04/2013 17:47:07 964 (0x03C4) Querying update status completed successfully. UpdatesStore 08/04/2013 17:47:07 964 (0x03C4) Querying update status of 20 updates. UpdatesStore 08/04/2013 18:01:00 6032 (0x1790) Querying update status completed successfully. UpdatesStore 08/04/2013 18:01:00 6032 (0x1790) Querying update status of 20 updates. UpdatesStore 08/04/2013 18:01:00 3748 (0x0EA4) Querying update status completed successfully. UpdatesStore 08/04/2013 18:01:00 3748 (0x0EA4)
-
ConfigMgr 2012 not downloading Software Updates
P@docIT posted a topic in Configuration Manager 2012
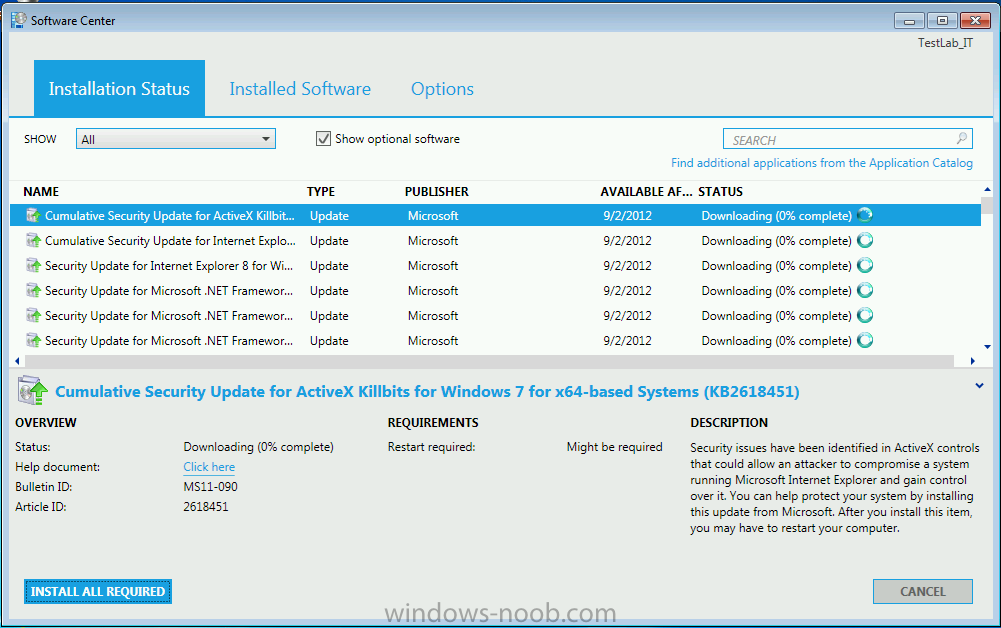
I setup a test lab using Hyper-V and following the guides here. Everything seems to have gone OK, however I tried deploying software updates to my test client and get what you see in the screenshot below. I tried tracking down a log file that might tell me what is going on however nothing jumped out at me. The client has a few software update logs but I'm not seeing any errors in any of them. -
Hi everybody After I have downloaded the first set of updates, subsequently set up the first Software Update Group and assigned it to a Device Collection I defined beforehand, I am currently struggling with the following issue: Not even one single Software Update in the Software Update Group is shown as "Required" in the Console. The clients in the Device Collection are definitely not having these updates installed already. Which should put the status of all the Updates to "Required". To me, this makes absolutely no sense since applications can be deployed without any problems. So it's not basically a communication issue between the client(s) and the backend. The architecture here consists of 4 servers and is set up as the following (NAME - ROLES): SRV1 - Component, Site Server, Site System, Reporting, DB SRV2 - Component, Site Server, Site System, App Catalog, DB, Management Point SRV3 - Component, Site Server, Site System, Distribution Point SRV4 - Component, Site Site System, Software Update Point Some logfile-entries from the client: UpdatesDeployment.log <![LOG[Evaluation initiated for (0) assignments.]LOG]!><time="09:50:44.931-120" date="08-31-2012" component="UpdatesDeploymentAgent" context="" type="1" thread="5272" file="assignmentsmanager.cpp:1108"> <![LOG[Message received: '<?xml version='1.0' ?><SoftwareUpdatesMessage MessageType='EvaluateAssignments'><UseCachedResults>False</UseCachedResults></SoftwareUpdatesMessage>']LOG]!><time="10:06:15.033-120" date="08-31-2012" component="UpdatesDeploymentAgent" context="" type="1" thread="5996" file="cdeploymentagent.cpp:189"> <![LOG[Removing scan history to force non cached results]LOG]!><time="10:06:15.033-120" date="08-31-2012" component="UpdatesDeploymentAgent" context="" type="1" thread="5996" file="assignmentsmanager.cpp:1217"> <![LOG[Assignment({8E213C0E-2B01-46C8-9293-8F9DA552C464}) already in progress state (AssignmentStateDetecting). No need to evaluate]LOG]!><time="10:06:15.065-120" date="08-31-2012" component="UpdatesDeploymentAgent" context="" type="1" thread="5996" file="updatesassignment.cpp:819"> ScanAgent.log <![LOG[- -Processing Scan Job TTL invalidity request]LOG]!><time="09:50:44.915-120" date="08-31-2012" component="ScanAgent" context="" type="1" thread="5272" file="scanjobmgr.cpp:600"> <![LOG[Message received: '<?xml version='1.0' ?> <UpdateSourceMessage MessageType='ScanByUpdateSource'> <ForceScan>TRUE</ForceScan> <UpdateSourceIDs> <ID>{0483E1D4-E0E8-4AE5-8319-7918DF5942BB} </ID> </UpdateSourceIDs> </UpdateSourceMessage>' ]LOG]!><time="10:06:12.707-120" date="08-31-2012" component="ScanAgent" context="" type="1" thread="920" file="cscanagent.cpp:956"> <![LOG[*****ScanByUpdateSource request received with ForceReScan=2, ScanOptions=0x0000000a, WSUSLocationTimeout = 604800]LOG]!><time="10:06:12.707-120" date="08-31-2012" component="ScanAgent" context="" type="1" thread="920" file="cscanagent.cpp:181"> <![LOG[sources are not current]LOG]!><time="10:06:12.723-120" date="08-31-2012" component="ScanAgent" context="" type="1" thread="920" file="utils.cpp:109"> UpdatesHandler.log <![LOG[initiating updates scan for checking applicability.]LOG]!><time="09:39:35.118-120" date="08-31-2012" component="UpdatesHandler" context="" type="1" thread="3552" file="capplicabilityhandler.cpp:434"> <![LOG[successfully initiated scan.]LOG]!><time="09:39:35.290-120" date="08-31-2012" component="UpdatesHandler" context="" type="1" thread="3552" file="capplicabilityhandler.cpp:490"> <![LOG[CUpdatesAgent::FinalConstruct entered]LOG]!><time="09:43:52.719-120" date="08-31-2012" component="UpdatesHandler" context="" type="1" thread="5204" file="cupdatesagent.cpp:48"> <![LOG[initiating updates scan for checking applicability.]LOG]!><time="09:43:52.751-120" date="08-31-2012" component="UpdatesHandler" context="" type="1" thread="5200" file="capplicabilityhandler.cpp:434"> <![LOG[successfully initiated scan.]LOG]!><time="09:43:52.829-120" date="08-31-2012" component="UpdatesHandler" context="" type="1" thread="5200" file="capplicabilityhandler.cpp:490"> I don't have a PatchDownloader.log on any client. So ... Any input would be greatly appreciated, since this stuff is driving me nuts :angry:
- 7 replies
-
- Software Updates
- Required
-
(and 1 more)
Tagged with:
-
Not sure what is going on here but my Client workstations are not detecting any windows updates from SCCM software update point. I installed the WSUS on the SCCM server, configured GPOs to point to the SCCM server per AnyWeb's guide on this forum. I tried the following to resolve but failed to fix: net stop "Windows Update" del /f /s /q %windir%\SoftwareDistribution\*.* REG DELETE "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update" /v NextDetectionTime /f REG DELETE "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate" /v SusClientId /f REG DELETE "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate" /v SusClientIdValidation /f net start "Windows Update" wuauclt.exe /resetauthorization /detectnow Here is what I see in my WindowsUpdate.log 2012-08-30 09:56:52:157 312 17dc Setup Checking for agent SelfUpdate 2012-08-30 09:56:52:159 312 17dc Setup Client version: Core: 7.6.7600.256 Aux: 7.6.7600.256 2012-08-30 09:57:04:029 312 17dc Misc Validating signature for C:\Windows\SoftwareDistribution\SelfUpdate\wuident.cab: 2012-08-30 09:57:04:252 312 17dc Misc Microsoft signed: Yes 2012-08-30 09:57:04:417 312 17dc Misc Validating signature for C:\Windows\SoftwareDistribution\SelfUpdate\wsus3setup.cab: 2012-08-30 09:57:04:507 312 17dc Misc Microsoft signed: Yes 2012-08-30 09:57:04:686 312 17dc Setup Determining whether a new setup handler needs to be downloaded 2012-08-30 09:57:04:686 312 17dc Setup SelfUpdate handler is not found. It will be downloaded 2012-08-30 09:57:04:686 312 17dc Setup Evaluating applicability of setup package "WUClient-SelfUpdate-ActiveX~31bf3856ad364e35~amd64~~7.6.7600.256" 2012-08-30 09:57:07:210 312 17dc Setup Setup package "WUClient-SelfUpdate-ActiveX~31bf3856ad364e35~amd64~~7.6.7600.256" is already installed. 2012-08-30 09:57:07:211 312 17dc Setup Evaluating applicability of setup package "WUClient-SelfUpdate-Aux-TopLevel~31bf3856ad364e35~amd64~~7.6.7600.256" 2012-08-30 09:57:07:245 312 17dc Setup Setup package "WUClient-SelfUpdate-Aux-TopLevel~31bf3856ad364e35~amd64~~7.6.7600.256" is already installed. 2012-08-30 09:57:07:245 312 17dc Setup Evaluating applicability of setup package "WUClient-SelfUpdate-Core-TopLevel~31bf3856ad364e35~amd64~~7.6.7600.256" 2012-08-30 09:57:07:302 312 17dc Setup Setup package "WUClient-SelfUpdate-Core-TopLevel~31bf3856ad364e35~amd64~~7.6.7600.256" is already installed. 2012-08-30 09:57:07:302 312 17dc Setup SelfUpdate check completed. SelfUpdate is NOT required. 2012-08-30 09:57:08:418 312 17dc PT +++++++++++ PT: Synchronizing server updates +++++++++++ 2012-08-30 09:57:08:420 312 17dc PT + ServiceId = {3DA21691-E39D-4DA6-8A4B-B43877BCB1B7}, Server URL = http://SccmServer.com:8530/ClientWebService/client.asmx 2012-08-30 09:57:08:848 312 17dc Agent Switching to hardware-verified ClientId. 2012-08-30 09:57:08:888 312 17dc PT WARNING: Cached cookie has expired or new PID is available 2012-08-30 09:57:10:070 312 17dc Agent Created new random SusClientId e9beecb8-80a6-452a-b557-111a3d1c8311. Old Id: 055efdc3-6f40-42a2-abde-bdba5e6a511a. 2012-08-30 09:57:10:070 312 17dc PT Initializing simple targeting cookie, clientId = e9beecb8-80a6-452a-b557-111a3d1c8311, target group = , DNS name = Win7PC.domain.lan 2012-08-30 09:57:10:070 312 17dc PT Server URL = http://SccmServer.com:8530/SimpleAuthWebService/SimpleAuth.asmx 2012-08-30 09:58:57:520 312 17dc Agent WARNING: Failed to evaluate Installed rule, updateId = {189A8F50-0C3A-4FDF-8BC2-BC23A3EB11FB}.101, hr = 80242013 2012-08-30 09:58:59:417 312 17dc PT +++++++++++ PT: Synchronizing extended update info +++++++++++ 2012-08-30 09:58:59:418 312 17dc PT + ServiceId = {3DA21691-E39D-4DA6-8A4B-B43877BCB1B7}, Server URL = http://SccmServer.com:8530/ClientWebService/client.asmx 2012-08-30 09:59:07:266 312 17dc Misc WARNING: WinHttp: SendRequestToServerForFileInformation failed with 0x80190194 2012-08-30 09:59:07:267 312 17dc Misc WARNING: WinHttp: ShouldFileBeDownloaded failed with 0x80190194 2012-08-30 09:59:07:267 312 17dc Agent WARNING: Fail to download eula file http://SccmServer.com:8530/Content/23/14D19C27B28CC3990260D7191F6E0FF6C7483623.txt with error 0x80244019 2012-08-30 09:59:07:282 312 17dc Misc WARNING: WinHttp: SendRequestToServerForFileInformation failed with 0x80190194 2012-08-30 09:59:07:282 312 17dc Misc WARNING: WinHttp: ShouldFileBeDownloaded failed with 0x80190194 2012-08-30 09:59:07:283 312 17dc Agent WARNING: Fail to download eula file http://SccmServer.com:8530/Content/AE/C3248EB572CB5F82E63CE9C6D73CFBF39B1052AE.txt with error 0x80244019 2012-08-30 09:59:07:295 312 17dc Misc WARNING: WinHttp: SendRequestToServerForFileInformation failed with 0x80190194 2012-08-30 09:59:07:295 312 17dc Misc WARNING: WinHttp: ShouldFileBeDownloaded failed with 0x80190194 2012-08-30 09:59:07:298 312 17dc Agent WARNING: Fail to download eula file http://SccmServer.com:8530/Content/86/2057F9A9878799A92846947E7F8CB15BA7F8F086.txt with error 0x80244019 2012-08-30 09:59:07:345 312 17dc Misc WARNING: WinHttp: SendRequestToServerForFileInformation failed with 0x80190194 2012-08-30 09:59:07:346 312 17dc Misc WARNING: WinHttp: ShouldFileBeDownloaded failed with 0x80190194 2012-08-30 09:59:07:348 312 17dc Agent WARNING: Fail to download eula file http://SccmServer.com:8530/Content/13/33D8A4B8183134CA79120BB436C18DDAB713E713.txt with error 0x80244019 2012-08-30 09:59:07:698 312 17dc Agent * Found 0 updates and 74 categories in search; evaluated appl. rules of 1920 out of 3047 deployed entities 2012-08-30 09:59:07:700 312 17dc Agent ********* 2012-08-30 09:59:07:700 312 17dc Agent ** END ** Agent: Finding updates [CallerId = AutomaticUpdates] 2012-08-30 09:59:07:700 312 17dc Agent ************* 2012-08-30 09:59:07:740 312 17dc Report REPORT EVENT: {DE179B6B-77D6-425A-875F-60B41B4300B7} 2012-08-30 09:56:52:023-0500 1 202 102 {00000000-0000-0000-0000-000000000000} 0 0 AutomaticUpdates Success Content Install Reboot completed. 2012-08-30 09:59:07:740 312 1694 AU >>## RESUMED ## AU: Search for updates [CallId = {1B633229-0977-4773-8D54-78A15FEEB5DF}] 2012-08-30 09:59:07:740 312 1694 AU # 0 updates detected 2012-08-30 09:59:07:751 312 1694 AU ######### 2012-08-30 09:59:07:751 312 1694 AU ## END ## AU: Search for updates [CallId = {1B633229-0977-4773-8D54-78A15FEEB5DF}] 2012-08-30 09:59:07:751 312 1694 AU ############# 2012-08-30 09:59:07:769 312 1694 AU Successfully wrote event for AU health state:0 2012-08-30 09:59:07:770 312 1694 AU Featured notifications is disabled. 2012-08-30 09:59:07:770 312 1694 AU AU setting next detection timeout to 2012-08-30 18:40:45 2012-08-30 09:59:07:772 312 1694 AU Setting AU scheduled install time to 2012-08-31 08:00:00 2012-08-30 09:59:07:772 312 1694 AU Successfully wrote event for AU health state:0 2012-08-30 09:59:07:774 312 1694 AU Successfully wrote event for AU health state:0 2012-08-30 09:59:08:417 312 17dc Report CWERReporter finishing event handling. (00000000) 2012-08-30 09:59:12:699 312 17dc Report REPORT EVENT: {51E9B20E-19ED-463A-A122-68B10BFA31A2} 2012-08-30 09:59:07:699-0500 1 147 101 {00000000-0000-0000-0000-000000000000} 0 0 AutomaticUpdates Success Software Synchronization Windows Update Client successfully detected 0 updates. 2012-08-30 09:59:12:699 312 17dc Report REPORT EVENT: {9BE62487-8948-4BC0-9A9F-63AF472B9BAA} 2012-08-30 09:59:07:700-0500 1 156 101 {00000000-0000-0000-0000-000000000000} 0 0 AutomaticUpdates Success Pre-Deployment Check Reporting client status. 2012-08-30 09:59:12:700 312 17dc Report CWERReporter finishing event handling. (00000000) If I click on check Windows Online for updates it shows me there are updates that need to be installed. I check my Software update groups and the Compliance is at 0%. Can anyone help me here?
-
I am implenting ADR for patch managment and I am having a bit of a Property filter issue. I would like to create an ADR that creates monthly deployments for my patch managment that I have control on when deploying. So I have checked Create new Software Update Group under general and cleared the "enable the deployment after this rule is run". My problem is setting up the property filters under software updates. Here are my concern: If I check "date released or revised" and set it to last 30 days, my first Software Update Group will only have Updates valid for the last 30 days. If I don't set that time frame it will create a new group each month with all the current updates and over time that will put me over the 1000 update mark esplecially if I incorprate SCUP. What should i do to set that first deployment or how should i setup my property filters? Any thoughts?
- 3 replies
-
- Automatic Deployment Rules
- ADR
-
(and 2 more)
Tagged with:
-
I figured I start a new post on this. My CIO and I have been going back and forth on this question for several days now and I want to share some insight and get some opinions. We used this post as a starting point http://blogs.technet...nager-2012.aspx Our Goals Protect all Windows 7 Machines with the latest security patches (Builten Id:MS) and Updates Protect all deployments of Mircrosoft - Now Windows Desktop (Office, Visual Studio, ETC) with latest security patches and updates Protect all Windows 2008R2 Servers with the latest security patches and Updates Protect all deployments of Adobe Acrobat, Adobe Reader, Adobe Flash with securty Updates and Patches Deploy Latest Drivers and Updates to our Dell PC's Monitor Compliance of Deployments Implementation, Limitations & Concerns All Updates Create an All Update Group for Reporting Purposes. We Selected all updates and put them in this group. DO NOT DEPLOY this group to anyone. We will use it only for reporting Purposes. (Not sure exactly how yet) WIndows 7 Machines Inital Setup 1. Create an Initial Updates Package. We called it "Windows 7 Software Udpates - Initial". This package contained all updates up to and including 05.31.2012. Our Search Criteria consisted of: Product=WIndows7 Expired=no Superseeded=No Date Released or Revised is less than or equal to 05/31/2012 This gave us at the time of writing this 286 Updates 2. Create The Monthly Update Package for June 2012. We called it "Windows 7 Software Updates - 2012 06" This Package contained all the updates in the month of June. Similiar Search criteria as above only different Date Range. This gave us 37 More Updates 3. Both of these Software Updates Groups where then deployed to a "Windows 7 Machines" Device Collection we created based on the following WMI Query: select SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client from SMS_R_System where SMS_R_System.OperatingSystemNameandVersion like "%Workstation 6.1%" Monthly Procedure Create a New Monthly Update Package after each "Patch Tuesday" and Deploy it to our Windows 7 Machine Device Collection. (We may do an Automatic Deployment Rule for this that we can later Green Light, not sure how to yet. We are currently using an ADR for Endpoint Protection Definiton Updates) Remove all the Expired and Superseeded updates from all Deployments - Just create a search criteria for Expried and Supersceded to yes and Edit Membership. Uncheck the Check Box and they will remove themselves from your deployment group and delete themselves off the server in 7 days. Another good post about this procedure http://blogs.technet.com/b/configmgrteam/archive/2012/04/12/software-update-content-cleanup-in-system-center-2012-configuration-manager.aspx Update the All Software Group with New Updates Concern - We will never be able to delete any of our Monthly Updates or the Intitial Update package as that would create a hole in our security Updates. I.E. If a laptop left the network for 6 months and came back. I am not sure if I care, it's just that in 5 years I will have 60 of these Update Groups. I also do not know if having so many deployments will effect Client / Server Performance in anyway. Microsoft - Non-Windows Inital Setup 1. Create an Initial Updates Package. We called it "Microsoft Udpates - Initial". This package contained all updates up to and including 05.31.2012. Our Search Criteria consisted of: Product=Expression Design 4 Product=Office 2010 Product=Visual Studio 2010 Expired=no Superseded=No Date Released or Revised is less than or equal to 05/31/2012 This gave us at the time of writing this 103 Updates 2. Create The Monthly Update Package for June 2012. We called it "Microsoft Updates - 2012 06" This Package contained all the updates in the month of June. Similiar Search criteria as above only different Date Range. This gave us 2 More Updates 3. We had to create serveral deployments for this. One for each application that we deployed. Concern/Question 1. Again you will not be able to delete any of these deployments for threat of creating a security hole. 2.. Should we just combine the packages and deploy them to all Windows 7 Machines? Will this create any Client/Server Performance Issues? Adobe Updates **This Assumes you have already setup SCUP and have an understanding of it. We used this youtube tutorial to get started. http://www.youtube.com/watch?v=fyEGWSFWyy0 SCUP In SCUP we are going to Create 2 Publications. One for the intial Deployment and then another for the Monthly Updates. You will find that the updates here or a bit more infrequent and you may switch to a quaterly update 1. The Inital Publication we selected all updates, there were 39. 2. We assign the updates to a new Publication called "Adobe Updates - Inital" 3. We published Full Content 4. We will do the same thing for "Adobe Updates- 2012 06" ***Not 100% sure we need to seperate out these updates or if we can publish to an all encompasing group. Inital Setup 1. Create an Initial Updates Package. We called it "Adobe Udpates - Initial". This package contained all updates up to and including 05.31.2012. Our Search Criteria consisted of: Product=Adobe Acrobat Product=Adobe Reader Product=Adobe Flash Player Expired=no Superseded=No Date Released or Revised is less than or equal to 05/31/2012 This gave us at the time of writing this 39 Updates 2. Create The Monthly Update Package for June 2012. We called it "Adobe Updates - 2012 06" This Package contained all the updates in the month of June. Similiar Search criteria as above only different Date Range. This gave us 2 More Updates 3. We had to create serveral deployments for this. One for each application that we deployed. Same Concerns and Questions 1. Again you will not be able to delete any of these deployments for threat of creating a security hole. 2.. Should we just combine the packages and deploy them to all Windows 7 Machines? Will this create any Client/Server Performance Issues? Conclusions I know I left out a bunch here, Still have to discuss Windows Server 2008 Updates and Dell Update. THe main thing we are still trying to figure out if it is OK just to have Several Big Intial Updates and then Just one Software Update for Everything. How will that effect client/server performance. I will clean this post up over time. Just wanted to get some feed back to start. Not sure if I am overthinking this or not..
-
I wanted to put this topic in the main CM2012 forum, but I can't, for some reason. That's why it's posted here. Hello, I was really hoping someone could help me with this. Background information: - We have a CM07 server in a production environment. - I've set up a CM12 RTM server, following the guides in this forum, with the hopes of migrating soon. - I wanted to do OSD from scratch to learn more and to take advantage of new features in CM12. - I have a few virtual machines running for testing OSD/apps (these are the only clients managed by my CM12 server). - Since it's not possible to have two WDS servers running at the same time AFAIK (without using registry tweaks, the F11 trick, that by the way doesn't work for me) I have created a bootable TS media that I mount on the virtual machines whenever I want to test OSD. Now, to my problem: I can't figure out why my Build and Capture TS is failing on the Install Software Updates step. smsts.log file says: Failed to RefreshUpdates, hr=087d00272, followed by: Failed to run the action: Install Software Updates. Component is disabled (Error: 87D00272; Source: CCM). I have read about similar issues occurring in CM07 capture task sequences since the machine is joined to a Workgroup. The proposed solution was adding SMSSLP=FQDN to the client installation properties, but since that functionality is moved to the MP in CM12, it should be enough to specify SMSMP=FQDN in my case. It's not working anyway. Tried it to a Deploy TS also, where the machine is domain joined, but I got the same error. The error code 87D00272 returns no results on Google. This stumps me, as someone surely has had the same problem? Here is the relevant portions of the smsts.log file If someone had the chance to look at this, I would greatly appreciate it. Thank you! Refreshing Updates InstallSWUpdate 2012-06-13 10:15:33 228 (0x00E4) spInstall->RefreshTargetedUpdates( spCallback, &bAlreadyCompleted ), HRESULT=87d00272 (e:\nts_sccm_release\sms\client\osdeployment\installswupdate \installswupdate.cpp,467) InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) Failed to RefreshUpdates, hr=0x87d00272 InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) RefreshTargetedUpdates(spInstall, spCallback, bAlreadyCompleted), HRESULT=87d00272 (e:\nts_sccm_release\sms\client\osdeployment\installswupdate \installswupdate.cpp,1295) InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) RefreshUpdates(), HRESULT=87d00272 (e:\nts_sccm_release\sms\client\osdeployment \installswupdate\installswupdate.cpp,906) InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) InstallUpdates(pInstallUpdate, tType, sJobID, sActiveRequestHandle), HRESULT=87d00272 (e:\nts_sccm_release\sms\client\osdeployment\installswupdate \main.cpp,248) InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) Setting TSEnv variable SMSTSInstallUpdateJobGUID= InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) Process(pInstallUpdate, tType), HRESULT=87d00272 (e:\nts_sccm_release\sms\client \osdeployment\installswupdate\main.cpp,304) InstallSWUpdate 2012-06-13 10:15:34 228 (0x00E4) Process completed with exit code 2278556274 TSManager 2012-06-13 10:15:34 912 (0x0390) !----------------------------------------------------------------------------------- ---------! TSManager 2012-06-13 10:15:34 912 (0x0390) Failed to run the action: Install Software Updates. Component is disabled (Error: 87D00272; Source: CCM) TSManager 2012-06-13 10:15:34 912 (0x0390) MP server http://CFGMGR-SRV.zenit.brummer.se. Ports 80,443. CRL=false. TSManager 2012-06-13 10:15:34 912 (0x0390) Setting authenticator TSManager 2012-06-13 10:15:35 912 (0x0390) Set authenticator in transport TSManager 2012-06-13 10:15:35 912 (0x0390) Sending StatusMessage TSManager 2012-06-13 10:15:35 912 (0x0390) Setting message signatures. TSManager 2012-06-13 10:15:35 912 (0x0390) Setting the authenticator. TSManager 2012-06-13 10:15:35 912 (0x0390) CLibSMSMessageWinHttpTransport::Send: URL: CFGMGR-SRV.zenit.brummer.se:80 CCM_POST /ccm_system/request TSManager 2012-06-13 10:15:35 912 (0x0390) Request was succesful. TSManager 2012-06-13 10:15:35 912 (0x0390) Set a global environment variable _SMSTSLastActionRetCode=-2016411022 TSManager 2012-06-13 10:15:35 912 (0x0390) Set a global environment variable _SMSTSLastActionSucceeded=false TSManager 2012-06-13 10:15:35 912 (0x0390) Clear local default environment TSManager 2012-06-13 10:15:35 912 (0x0390) Let the parent group (Setup Operating System) decides whether to continue execution TSManager 2012-06-13 10:15:35 912 (0x0390) The execution of the group (Setup Operating System) has failed and the execution has been aborted. An action failed. Operation aborted (Error: 80004004; Source: Windows) TSManager 2012-06-13 10:15:35 912 (0x0390) Failed to run the last action: Install Software Updates. Execution of task sequence failed. Component is disabled (Error: 87D00272; Source: CCM) TSManager 2012-06-13 10:15:35 912 (0x0390) MP server http://CFGMGR-SRV.zenit.brummer.se. Ports 80,443. CRL=false. TSManager 2012-06-13 10:15:35 912 (0x0390) Setting authenticator TSManager 2012-06-13 10:15:35 912 (0x0390) Set authenticator in transport TSManager 2012-06-13 10:15:35 912 (0x0390) Sending StatusMessage TSManager 2012-06-13 10:15:35 912 (0x0390) Setting message signatures. TSManager 2012-06-13 10:15:35 912 (0x0390) Setting the authenticator. TSManager 2012-06-13 10:15:35 912 (0x0390) CLibSMSMessageWinHttpTransport::Send: URL: CFGMGR-SRV.zenit.brummer.se:80 CCM_POST /ccm_system/request TSManager 2012-06-13 10:15:35 912 (0x0390) Request was succesful. TSManager 2012-06-13 10:15:35 912 (0x0390) Launching command shell. OSDSetupHook 2012-06-13 10:15:45 1932 (0x078C) executing command: C:\WINDOWS\system32\cmd.exe /k OSDSetupHook 2012-06-13 10:15:45 1932 (0x078C) executed command: C:\WINDOWS\system32\cmd.exe /k OSDSetupHook 2012-06-13 10:15:45 1932 (0x078C) Execution::enExecutionFail != m_eExecutionResult, HRESULT=80004005 (e: \nts_sccm_release\sms\client asksequence smanager smanager.cpp,756) TSManager 2012-06-13 10:16:57 912 (0x0390) Task Sequence Engine failed! Code: enExecutionFail TSManager 2012-06-13 10:16:57 912 (0x0390) **************************************************************************** TSManager 2012-06-13 10:16:57 912 (0x0390) Task sequence execution failed with error code 80004005 TSManager 2012-06-13 10:16:57 912 (0x0390)
-
Below is an error message I'm getting when I launch a Sync from the Config Manager console. This error shows in my site system status. Failures were reported on WSUS Server "TECH-SCCM1-MSV.forneyisd.net" for WSUS components "WSUSService,". Solution: Verify that the failed WSUS components are installed and running. Any ideas?
- 2 replies
-
- software updates
- wsus
-
(and 2 more)
Tagged with:
-
Dear All, Some background information... Over the last few months my colleagues and I have been working on building the foundations for our Windows 7 project. We have previously used WSUS as a stand alone service (This will still be used for Windows XP and Server based updates), however we have now built a new WSUS server specifically for use with SCCM 2007 SP2. Now for my problem... Our WSUS server has been installed and the updates are being populated into SCCM. I have created an update list and i am now attempting to download the updates and assign them to our deployment package. It appears that some of the updates download OK but as for other i am prompted with errors such as below: - Warning: Security Update for Microsoft Chart Controls for Microsoft .NET Framework 3.5 Service Pack 1 (KB2500170) Errors The requested header was not found What have a i tried so far to troubleshoot the error? I have attempted to download the update on both the SCCM Server and the WSUS Server directly - this works OK I have checked and compared the proxy/PAC File settings on the old WSUS and the new WSUS/SCCM Servers and all of these match OK I have attempted to re-create an update list, deployment package and share but i am still prompted with the same error message I have compared the source location with the distribution folder and these match like for like, however not all updates are visible in the deployment package If anyone else has come across similar issues or can provide further suggestions this would be highly appreciated Thanks Richard
-
- Software updates
- wsus
-
(and 2 more)
Tagged with:
-
Hi I have question regarding some OS installations that are stuck in the running state long after the installation has finished. This is a problem for us because other software will not get installed unless the OSD has finished successfully. The final step in our OSD task sequence installs all software updates that are advertised. And I have selected to ignore errors in case they do occur. Because software updates will get install later on anyway (not preferred). But the problem is that when we are advertising more updates to a computer than are available on the DP. Reason might be that the updates are currently being staged or we have forgotten to stage them. And the installation waits until they are available. Is there a way to change the installation status from running to succeeded? Either by a registry hack or an sql query? Or to have a time out in the task sequence causing it to "fail" which is ok because it's the last step. I have found the following key in the registry and someone here pointed out that if you want to rerun an advertisement that has the option rerun failed advertisements you can change it from succeeded or exit code 0 to exit 1 or whatever and the installation will restart next policy refresh. HKLM>Software>Microsoft>SMS>Mobile Client>Software Distribution>Execution History>System>"advID".
-
- osd
- software updates
-
(and 2 more)
Tagged with: