-
Posts
9254 -
Joined
-
Last visited
-
Days Won
369
Everything posted by anyweb
-

SCCM 2012 R2 SP1 CU2 WDS service restarting 7031
anyweb replied to Leon1983's topic in Configuration Manager 2012
i would reinstall WDS as a start, see what happens -

Limit which OSD Task Sequences A User Can Run
anyweb replied to surfincow's topic in Configuration Manager 2012
yup here you go How can I password Protect a Task Sequence ? Password Protecting a Task Sequence -

Limit which OSD Task Sequences A User Can Run
anyweb replied to surfincow's topic in Configuration Manager 2012
you could make it hidden (as you've found) or use a password on the task sequence itself, or use devel mode -
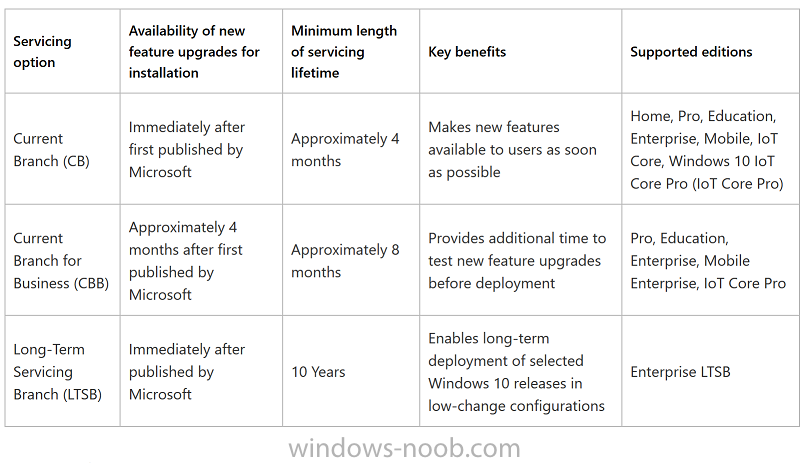
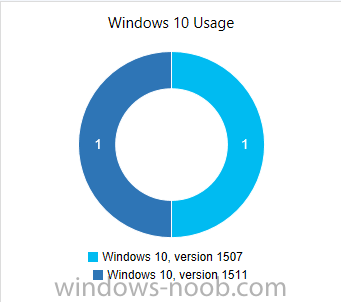
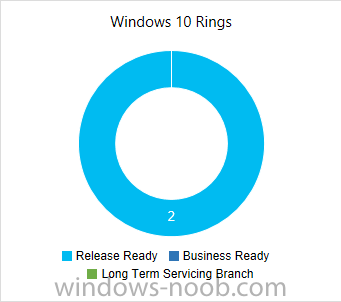
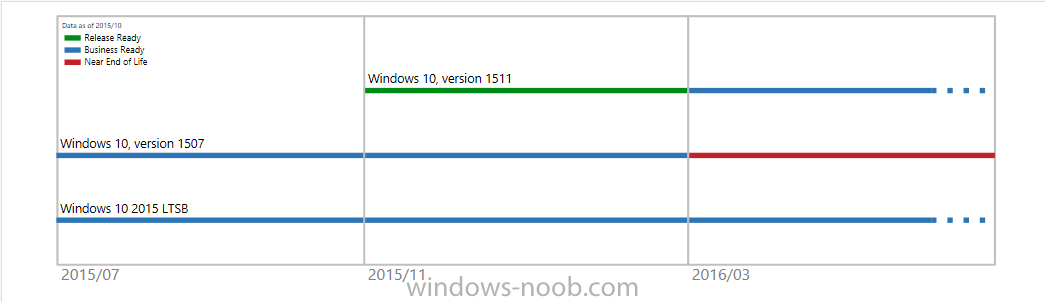
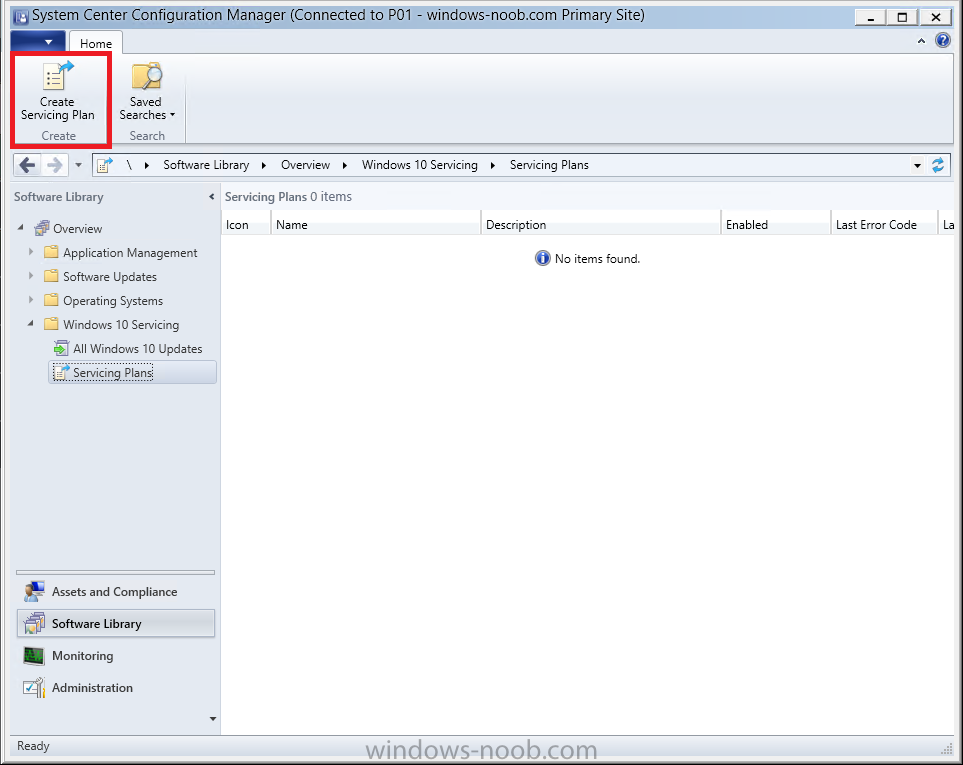
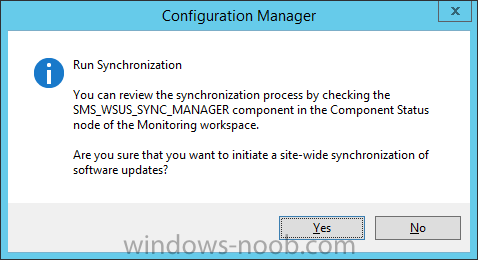
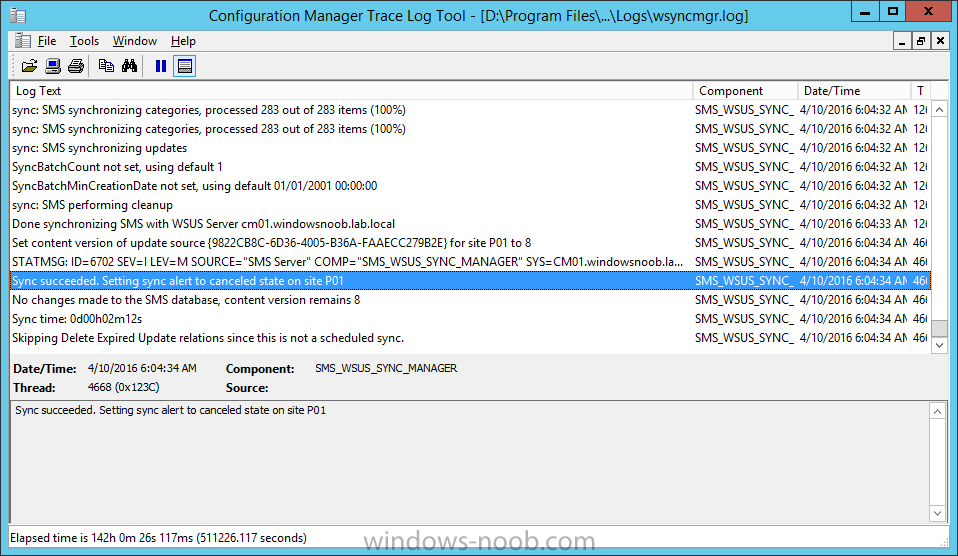
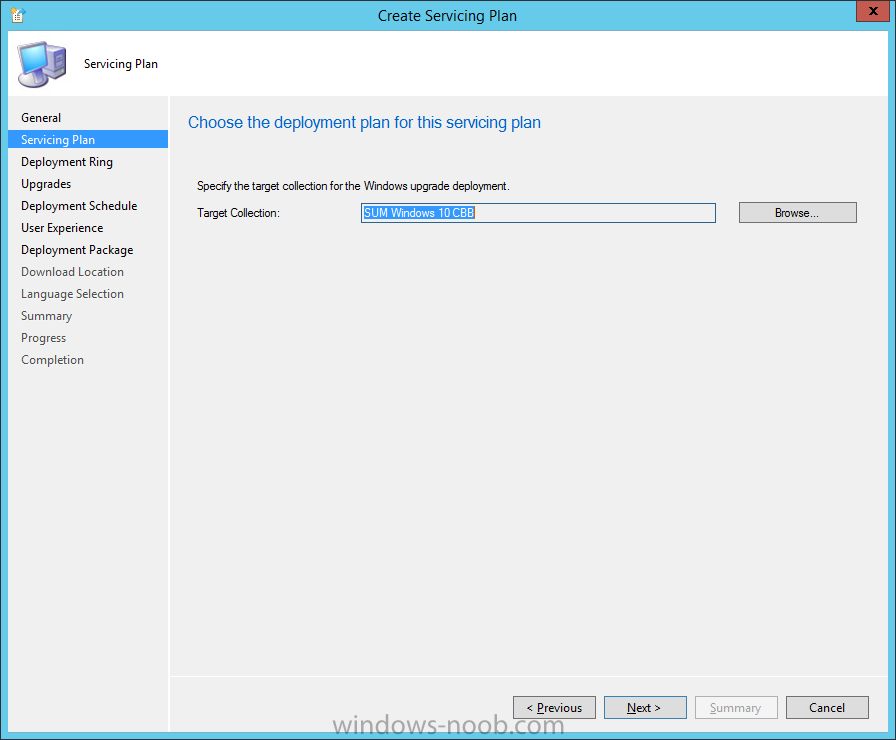
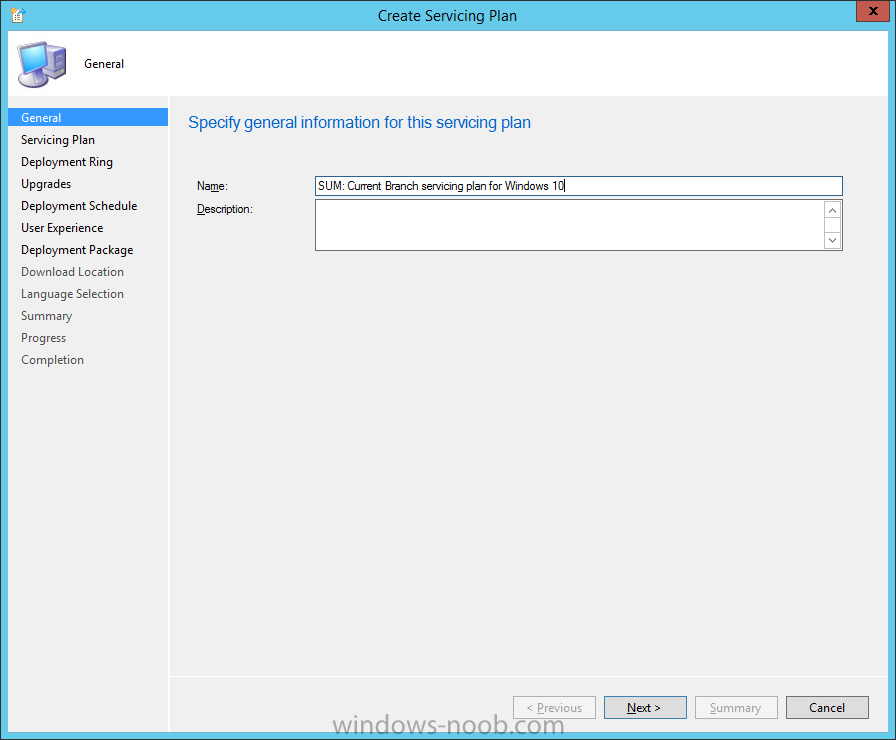
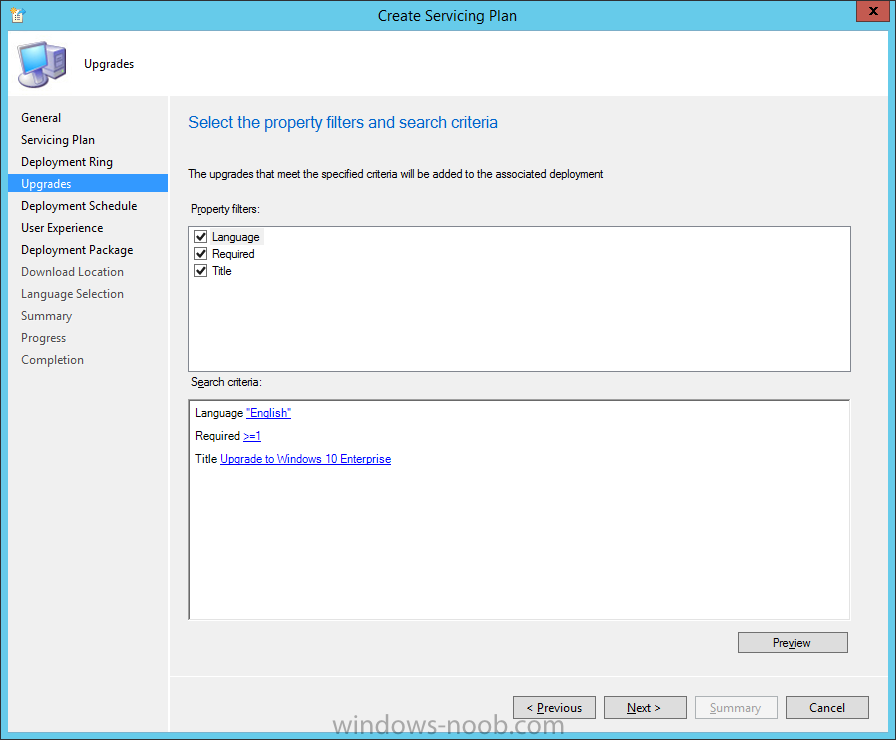
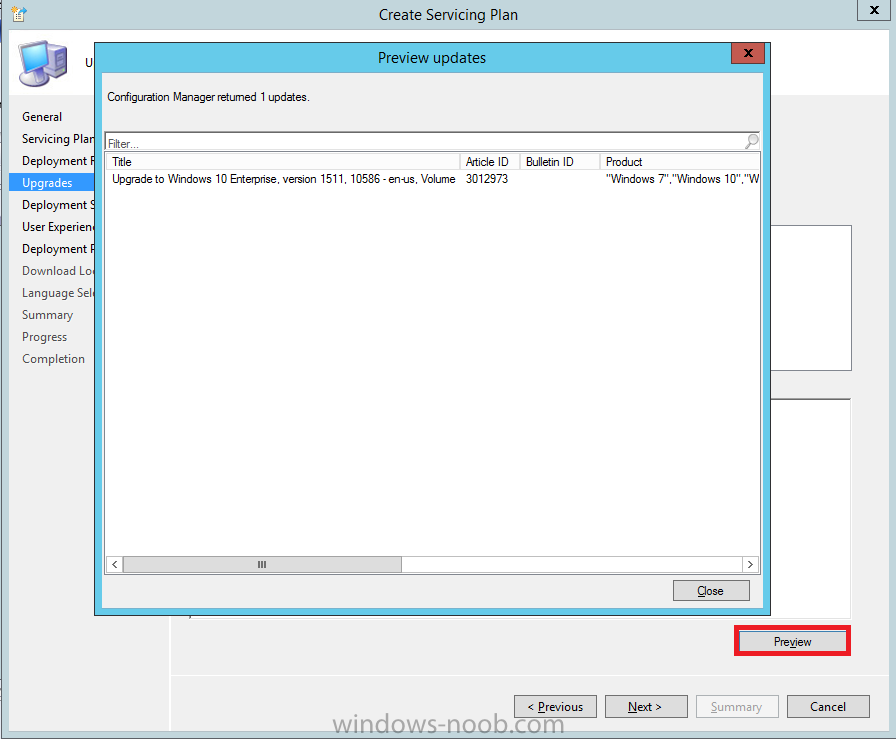
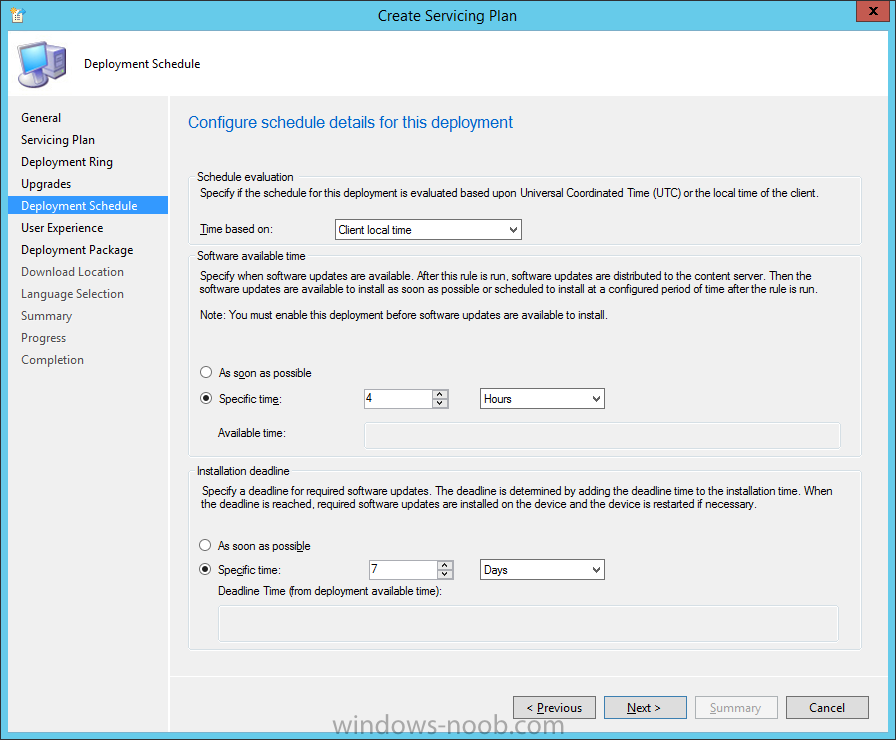
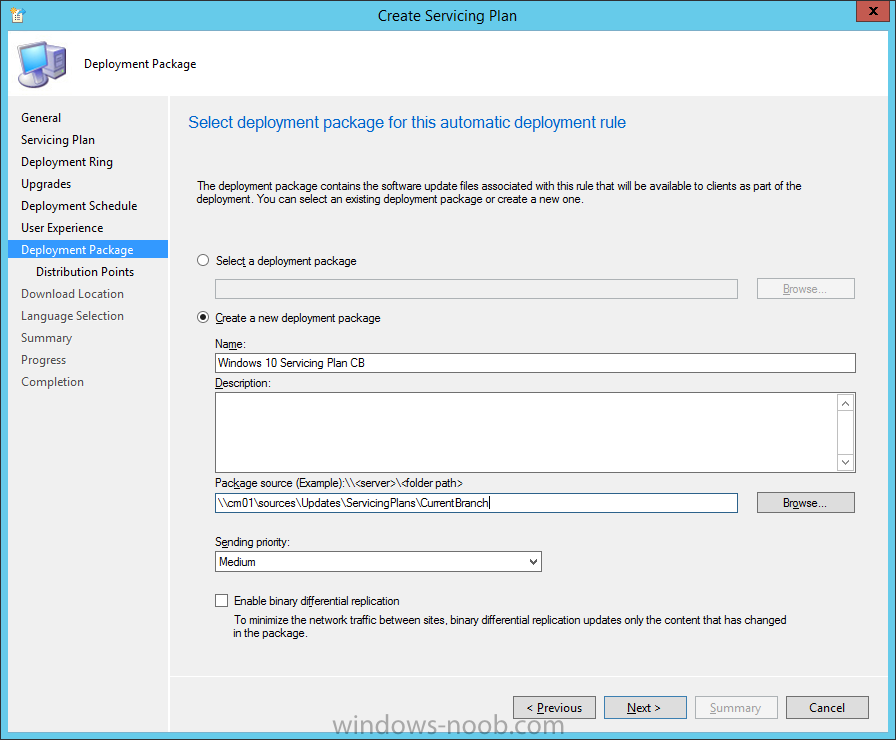
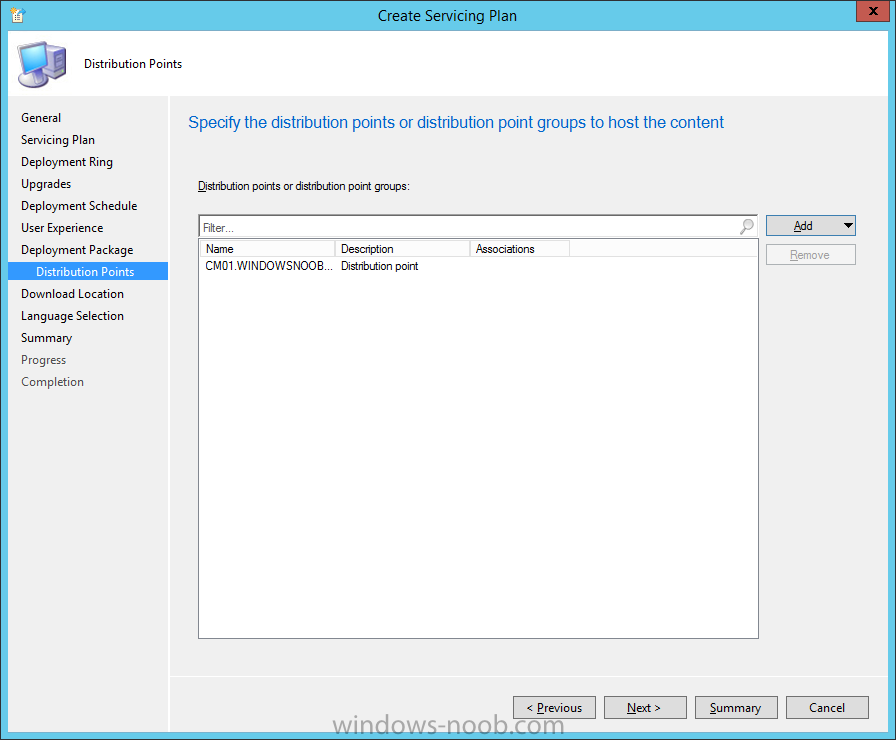
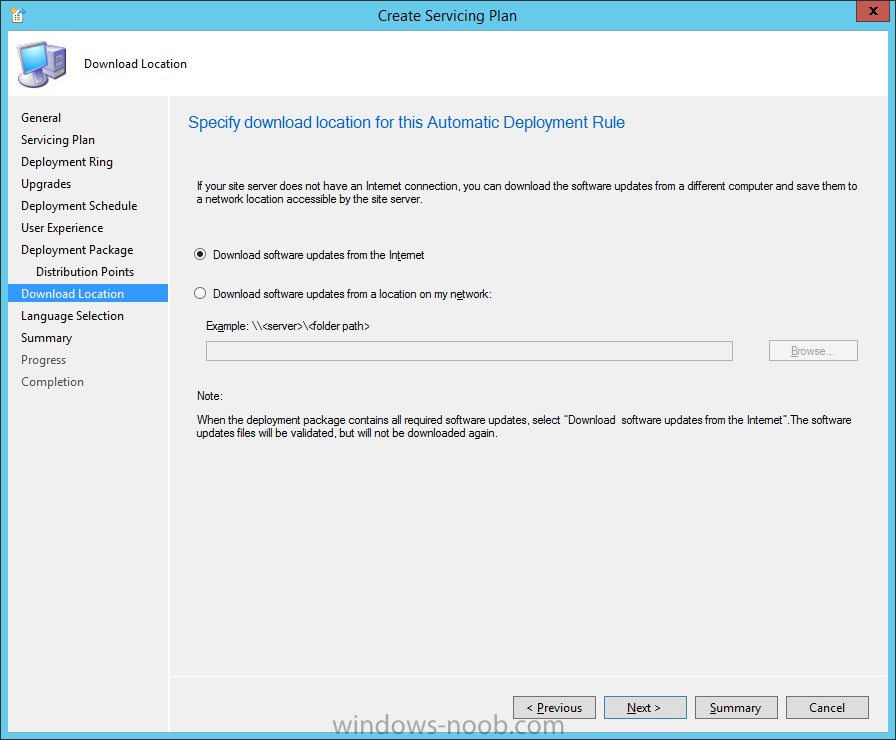
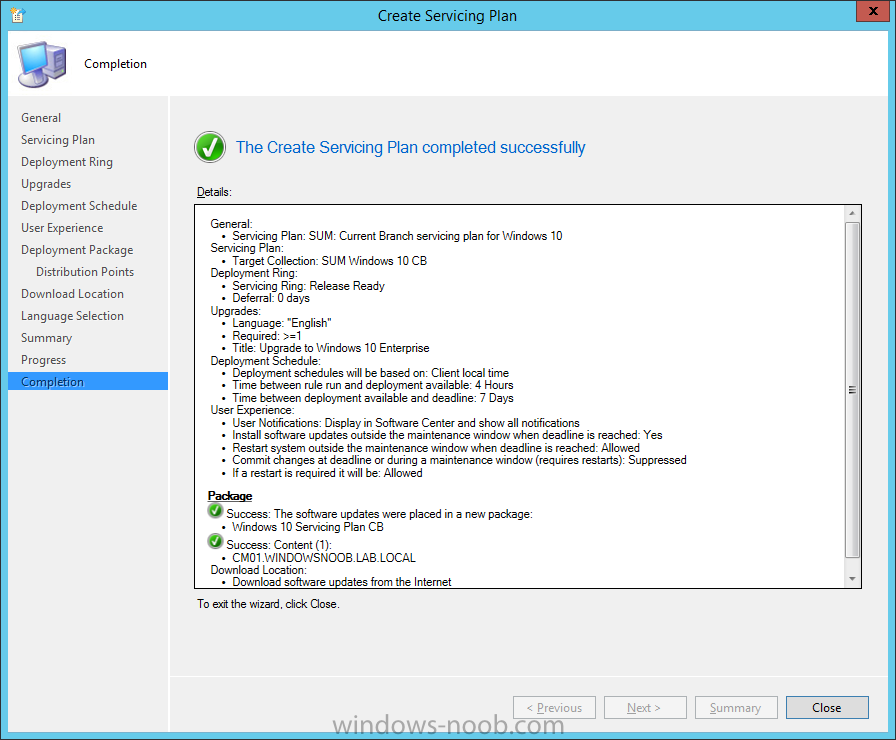
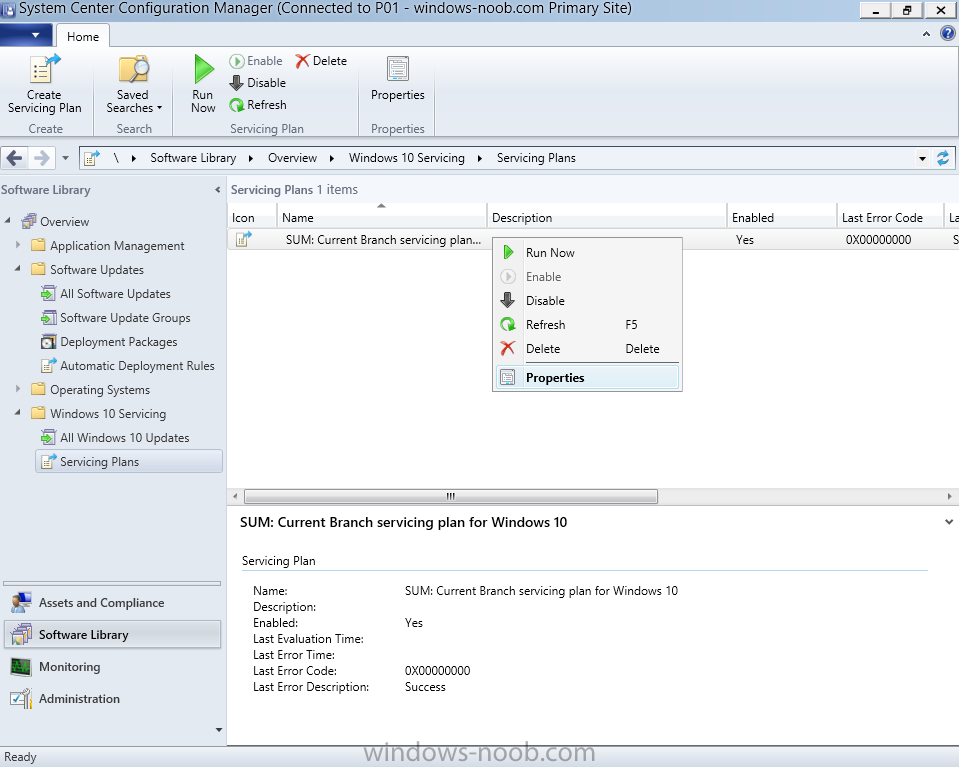
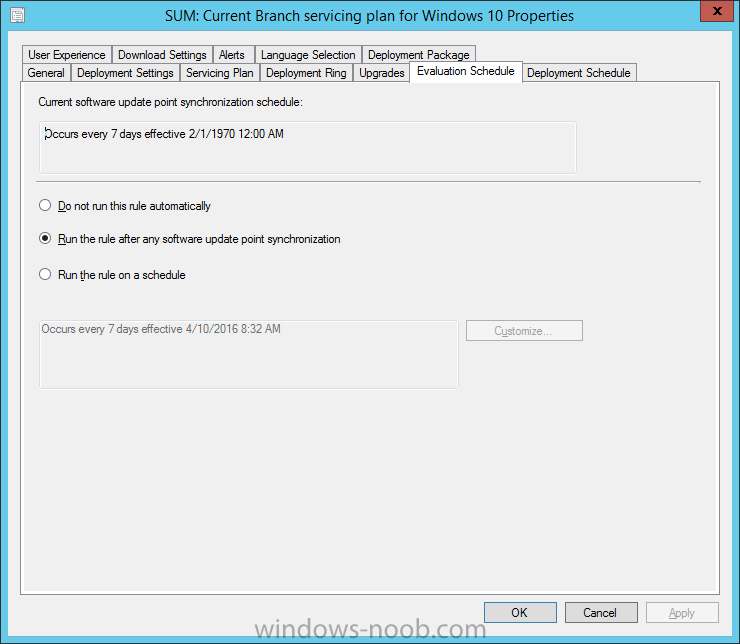
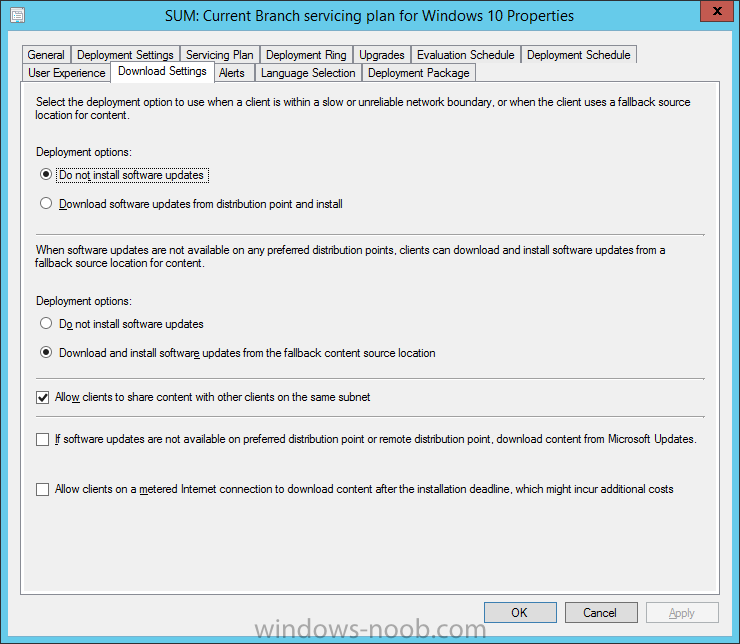
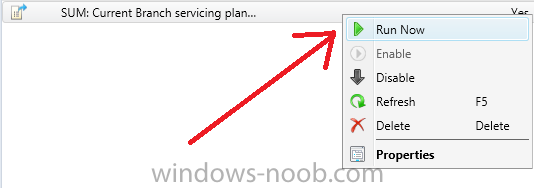
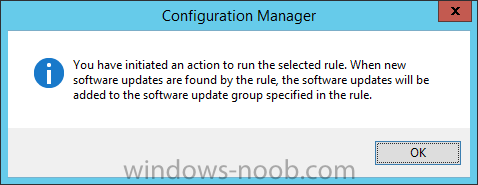
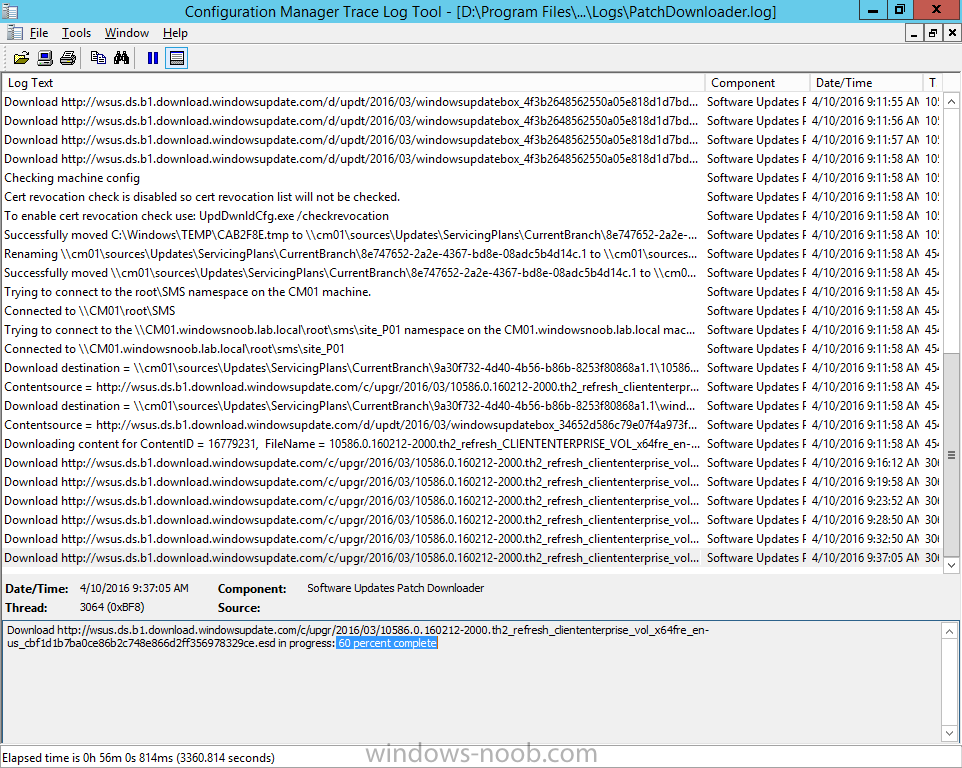
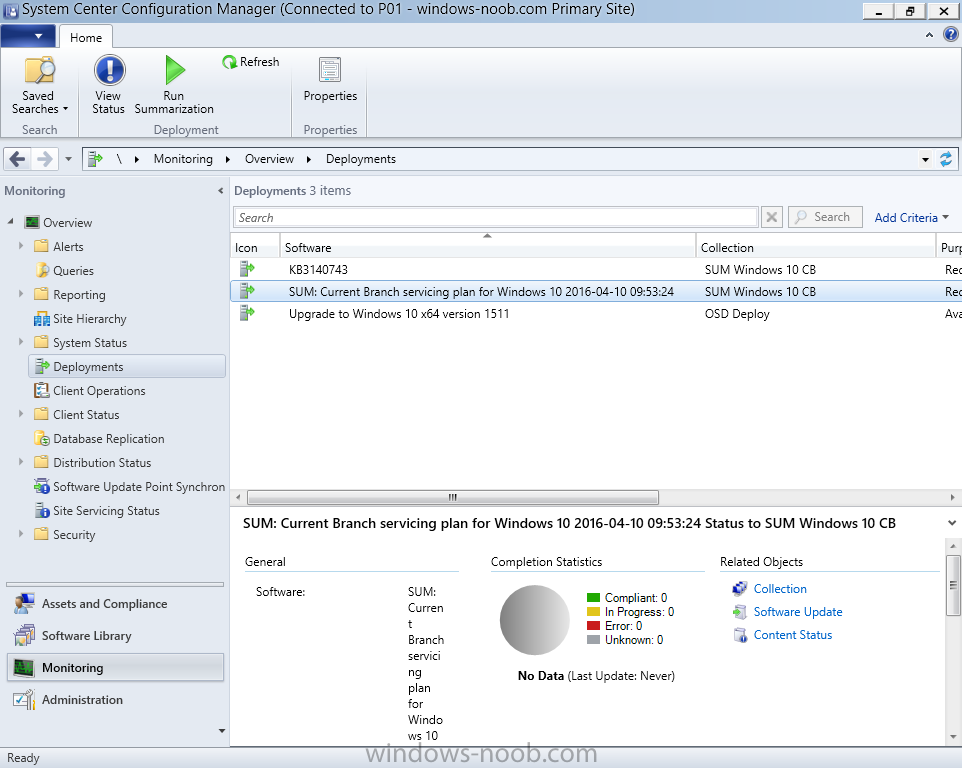
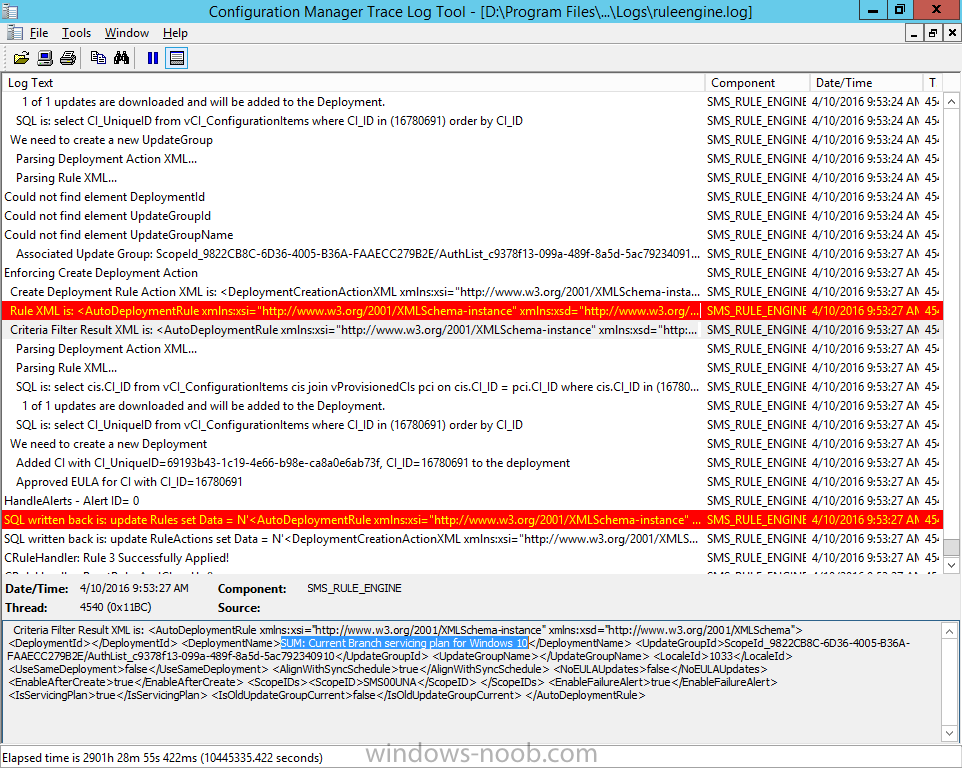
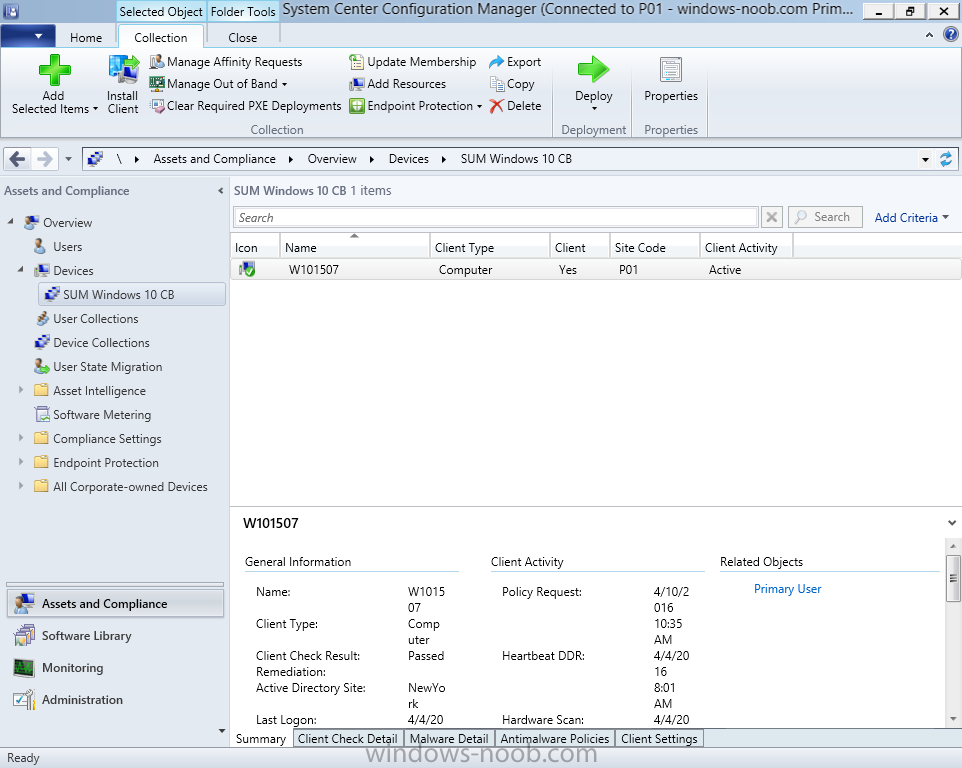
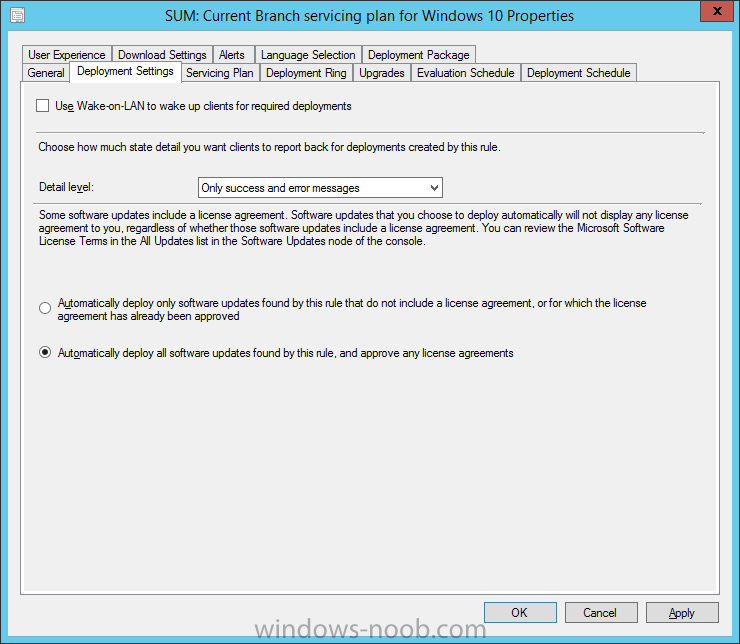
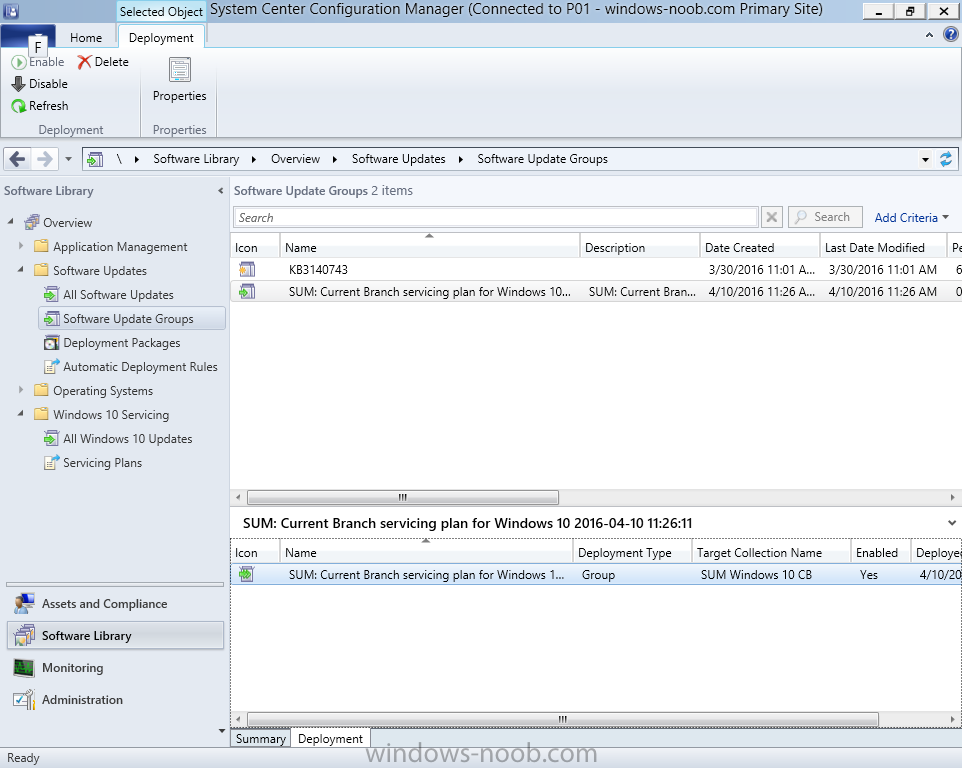
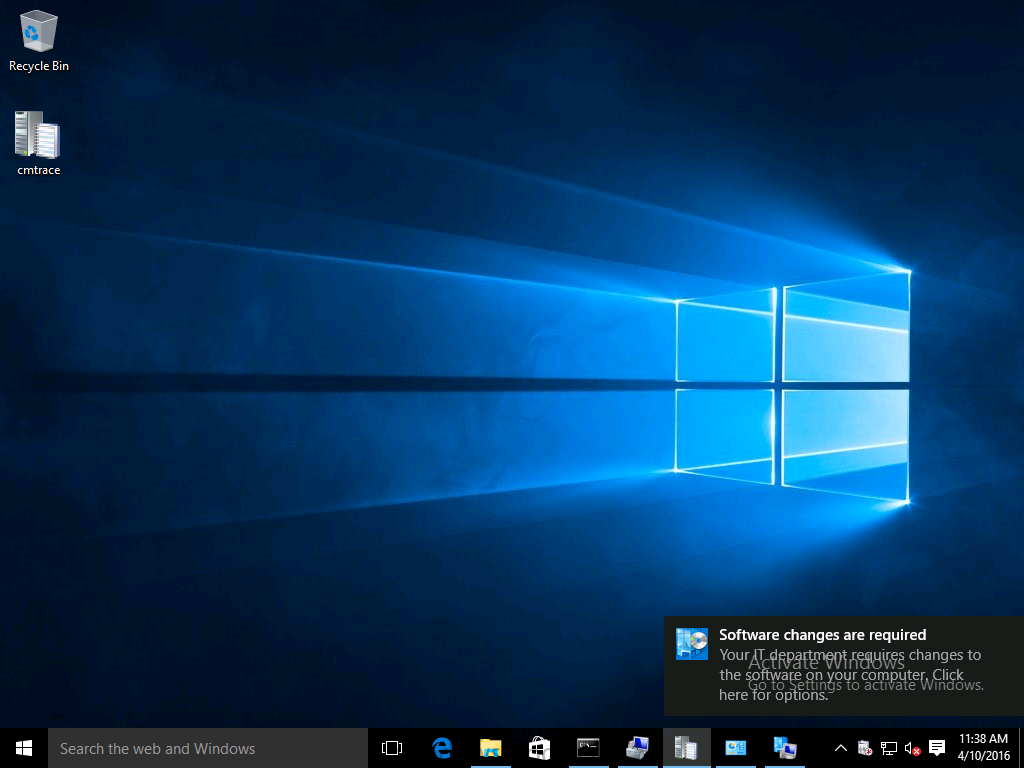
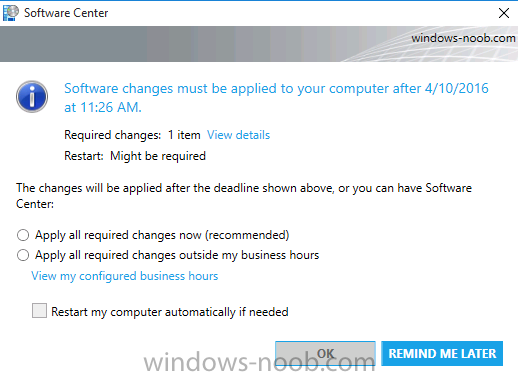
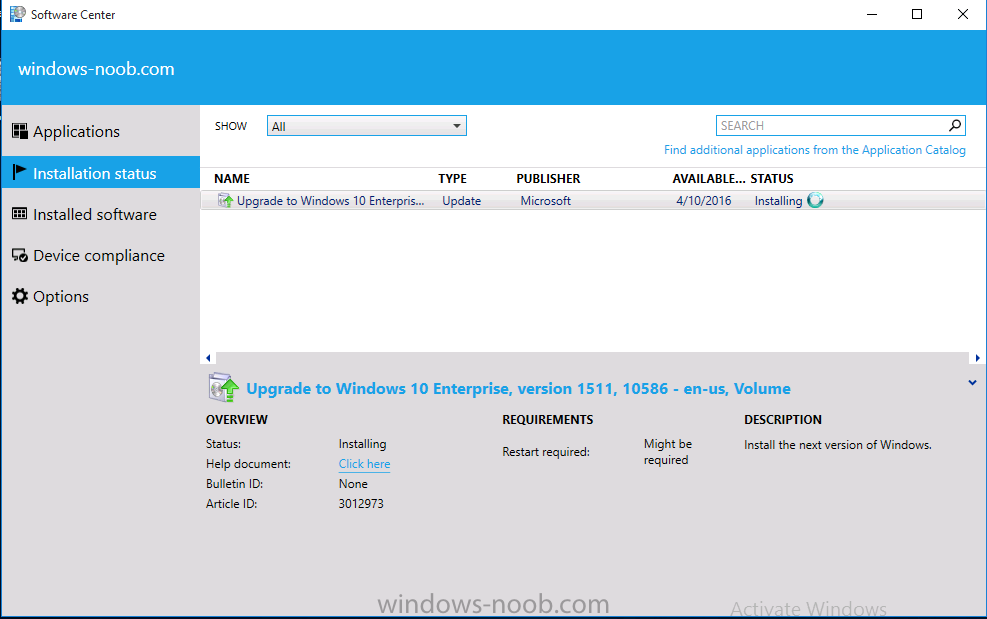
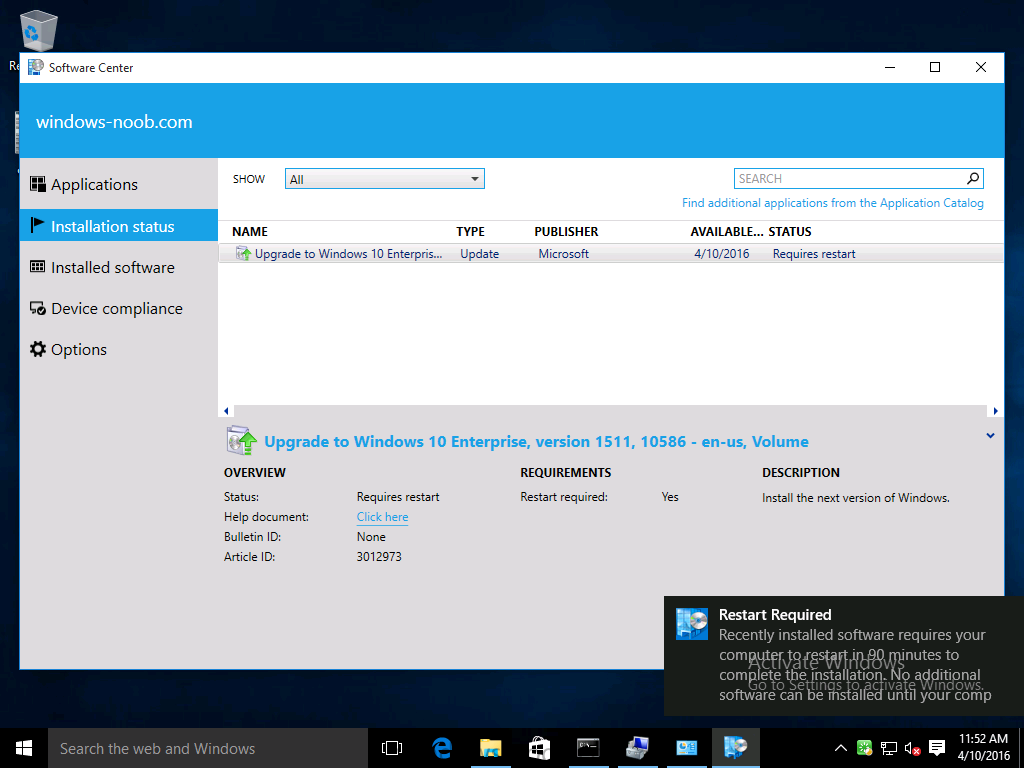
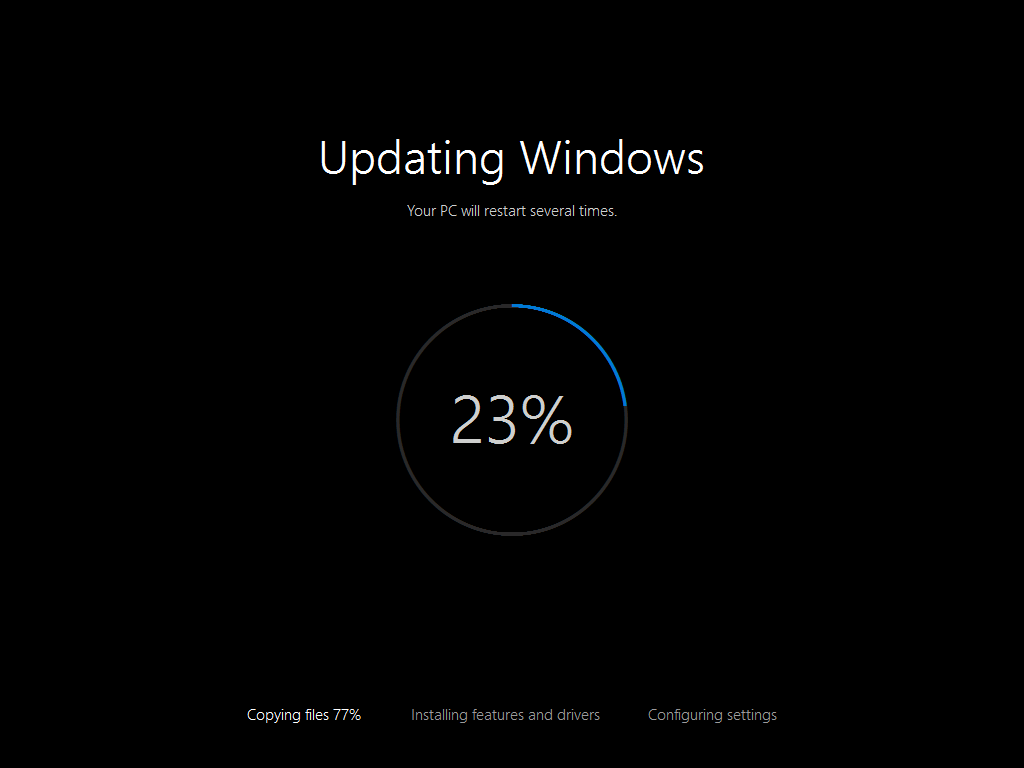
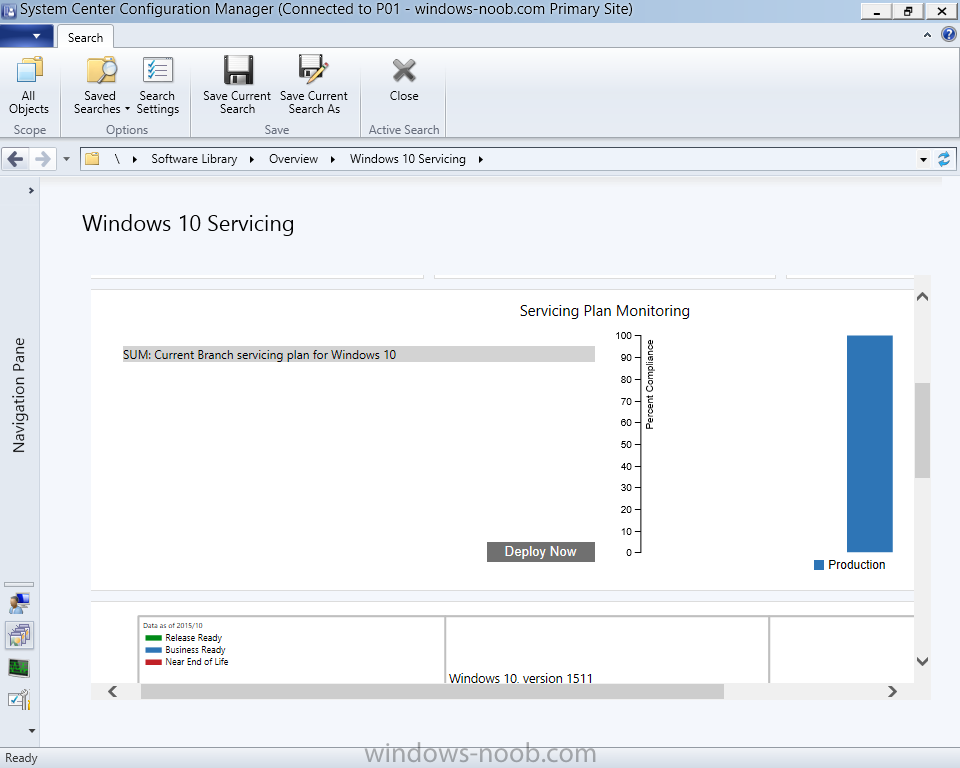
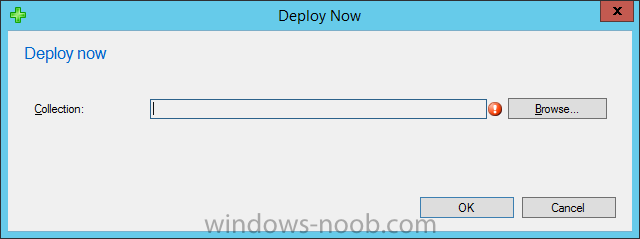
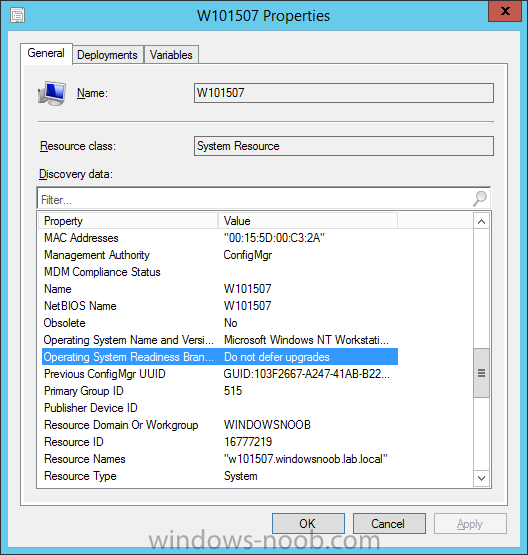
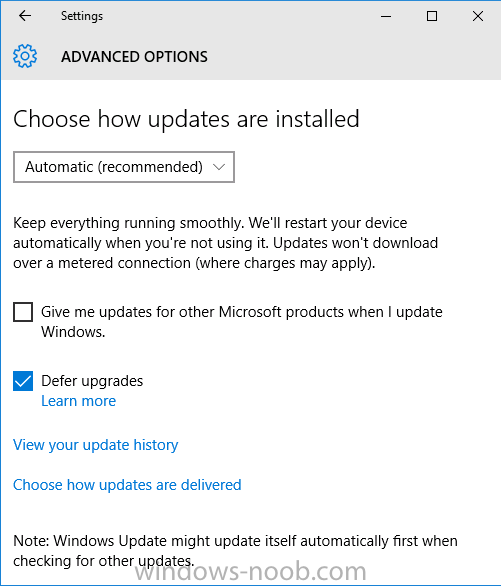
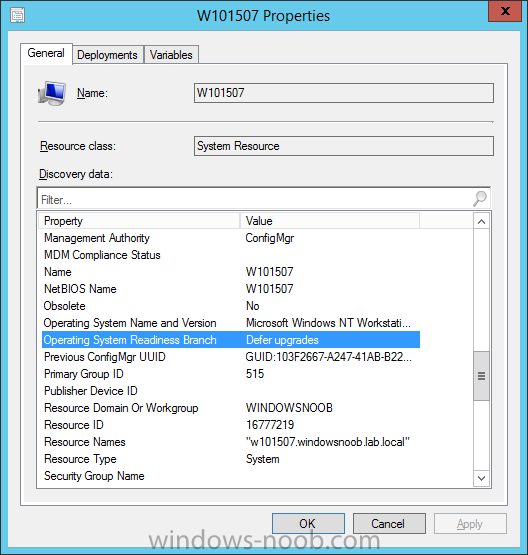
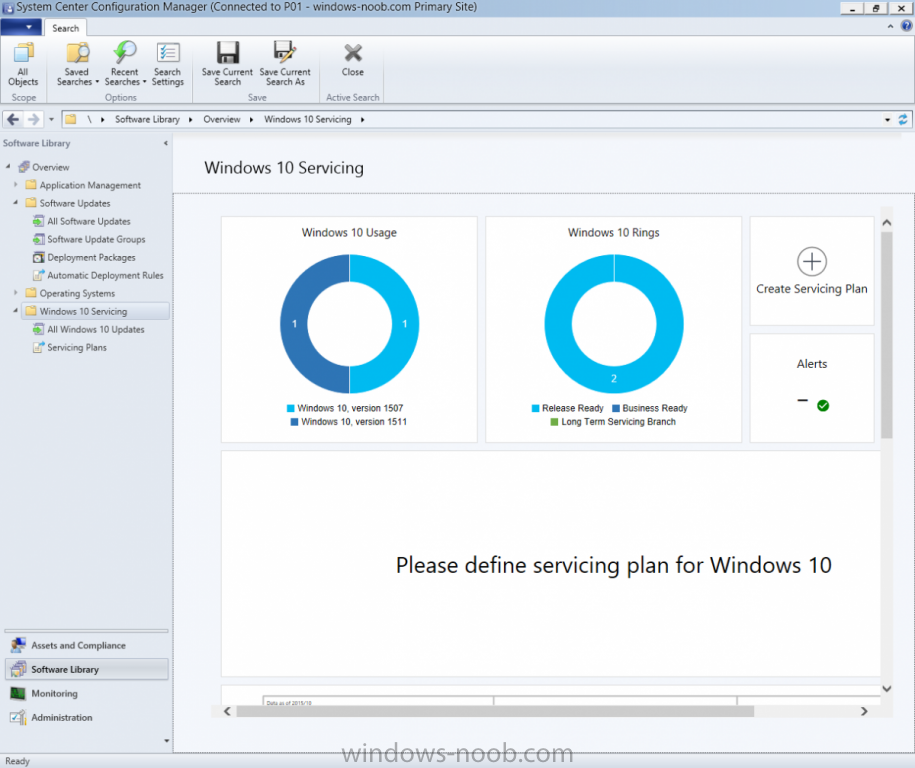
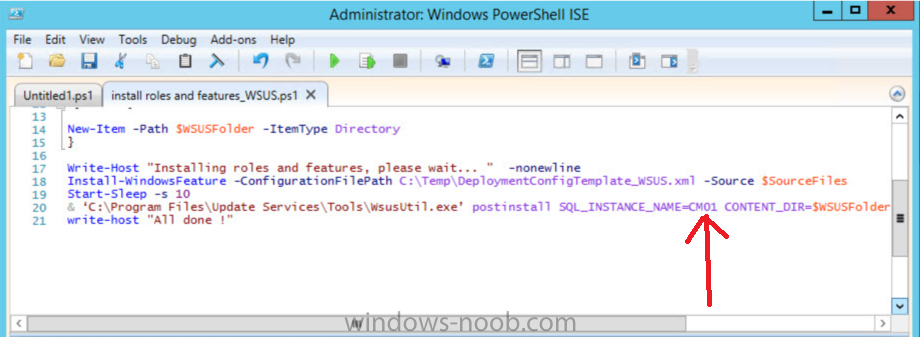
Introduction At the start of this series of step by step guides you installed System Center Configuration Manager (Current Branch), then you configured discovery methods. Next you configured boundaries to get an understanding of how automatic site assignment and content location works. After that you learned how to update ConfigMgr with new features and fixes using a new ability called Updates and Servicing and you learned how to configure ConfigMgr to use Updates and Servicing in one of these two modes: Online mode Offline mode To prepare your environment for Windows 10 servicing (this guide) you learned how to setup Software Updates using an automated method (via a PowerShell script) or manually using the ConfigMgr console. Next you used a PowerShell script to prepare some device collections, then you configured client settings for your enterprise and finally you'll deployed the ConfigMgr client agent using the software updates method which is the least intensive method of deploying the Configuration Manager client agent. As System Center Configuration Manager (current branch) is being delivered as a service now, version 1602 was made available (March 11th, 2016) and you used Updates and Servicing to do an in-place upgrade to that version as explained here. Next you learned about how to use the Upgrade task sequence to upgrade your Windows 7, Windows 8 (and 8.1) and even your Windows 10 devices to a later build of Windows 10. In this guide you'll take a look at the new Windows 10 servicing features in ConfigMgr (Current Branch). A short introduction to Windows 10 servicing Windows 10 servicing is a broad category (discussed at length here on Technet) which includes different options for applying updates and upgrades to Windows 10 devices using a variety of different methods available. In this guide we are primarily interested in looking at Windows 10 servicing options within ConfigMgr (Current Branch) so that will be the focus. In a nutshell there are three Windows 10 servicing options we need to consider: Current Branch Current Branch for Business Long Term Servicing Branch Each branch has its' own properties. If you are using Current Branch, then updates and upgrades are made available as soon as they are released from Microsoft and the key benefits are that it makes new features available to users as soon as possible. Current Branch for Business allows more time (4 to 8 months depending on your Defer Updates and Upgrades preferences) to 'wait and see' how those updates (and upgrades) can impact your environment. The key benefit here is it provides additional time to test new feature upgrades before deployment which is useful in a business scenario. Long Term Servicing Branch is aimed at low-change configurations (Operational Technology for example) where changing functionality can impact production. This is all neatly explained in the following table from Technet. Note: Make sure to read the following post so that you understand the implications of enabling CBB using various methods (registry or gpo). Familiarizing yourself with the Windows 10 servicing dashboard Note: All screenshots taken here were from System Center Configuration Manager version 1602 (Current Branch). As ConfigMgr (Current Branch) is evolving at a fast rate based on UserVoice and production development it is very likely that abilities and even UI elements shown here will change in later versions of the product. In order to populate information on the dashboard and test Windows 10 Servicing, this lab already contains two Windows 10 computers, one is version 1507 and the other is version 1511. In the ConfigMgr console select Software Library and expand Windows 10 Servicing. A dashboard similar to the below screenshot should appear. The first thing you'll notice in the tiles displayed are the two doughnuts which contain visual clues about the versions and branches of Windows 10 in your organization. Note: You will notice similar colors used throughout the tiles in the dashboard, however they don't necessarily match up between different tiles. This behavior will more than likely change in a later release of ConfigMgr (a bug has been raised and Microsoft is working on it). Windows 10 Usage Within the first tile is a doughnut called Windows 10 Usage. This tile should give you an estimate of the different Windows 10 build versions encountered by ConfigMgr in your organization. If you have any Windows 10 Insider Preview versions, they'll be listed as Other. Windows 10 Rings Within the second tile is a doughnut called Windows 10 Rings. This tile is used to give you an overview of the Windows 10 Branches in use and their readiness state, however instead of referring to those branches as explained in the table above, they have alias's. The following Table should clear that up: Release Ready : Current Branch Business Ready : Current Branch for Business Long Term Servicing Branch : Long Term Servicing Branch In addition to the two doughnuts in the first two tiles you have another two tiles which allow you to Create Servicing plan and monitor Alerts along with a big tile reminding you to Please define servicing plan for Windows 10. Note: Creating a servicing plan directly from within the dashboard will create a basic servicing plan which only prompts you for name, collection, deployment package, and readiness state (along with associated limitations for the last two). All other values will be default. If you want custom options, create the servicing plan directly from the ConfigMgr console. Windows 10 Build To see more information you either need a large resolution monitor or simply scroll down to reveal the Windows 10 Build tile which is a graph that plots out the versions of Windows 10, their readiness state and an approximate EOL. What you can see from the above is that Windows 10 version 1507 is classified as Business Ready (Current Branch for Business) from the date it was released, and from approximately March 2016 Windows 10 version 1511 takes over that spot (while Windows 10 1507 heads into EOL). In fact, Windows 10 version 1511 was declared Current Branch for Business on the 8th of April 2016. Ok so now that you've seen the dashboard, let's get on with the business of creating a servicing plan. Step 1. Synchronize Software Updates Before you create your servicing plan, make sure that the data you are using is up to date. To do that you need to synchronize with Microsoft Update. To perform a sync do as follows: In the ConfigMgr console select the Software Library workspace, select Software Updates, right click on All Software Updates and choose Synchronize Software Updates. Answer Yes to the popup. Using CMTrace, monitor the sync progress in <ConfigMgr Installation Path>\Logs\Wsyncmgr.log. Look for the Sync succeeded. Setting sync alert to canceled state on site <your_site_code> text in the log file to notify you of a successful sync. Step 2. Creating a servicing plan Servicing plans are akin to Automatic Deployment Rules (ADR) in Software Updates in that they can automatically download, and deploy updates to a collection based on the settings you define in the rule. Servicing plans however allow you to define what Windows 10 branches are in user in your environment and then monitor them in the servicing dashboard. From version 1602 onward, servicing plans are also tied so that you can manage the behavior for high-risk deployments. Note: Servicing plans are designed to upgrade Windows 10 versions from one build to another build only. They are not designed for upgrading Windows 7 or Windows 8.1 to Windows 10. If you need to upgrade your Windows 7 or Windows 8.1 computers to Windows 10 use the Upgrade Task Sequence instead. In this example you will create a servicing plan for Windows 10 Current Branch (this is because at the time of writing there were no upgrades available for Current Branch for Business). In the ConfigMgr console select Software Library and expand Windows 10 Servicing. Select Servicing Plans and in the ribbon click on Create Servicing Plan. When the wizard appears, give the Servicing Plan a suitable name like SUM: Servicing Plan for Windows 10 (The SUM prefix allows you to clearly see that the deployment is for software updates in the monitoring console later.) Next, point it to your target collection, this collection should contain Windows 10 computers that are suitable for this servicing plan (i.e. Current Branch as defined by not setting the Defer Upgrades setting). Note: In production you'd want to create a hierarchy of test collections prior to releasing upgrades to the masses, this is in order to verify that your critical applications are not affected by the upgrade. How you populate those collections is up to you. Next you get to choose which Deployment Ring you'd like to use. The Deployment Ring refers to the Windows readiness state that applies to this servicing plan, and once again you get to choose between Release Ready (Current Branch) or Business Ready (Current Branch for Business). Depending on which state you choose, you will see different results in the console, so it's a good idea to use the Preview button on the Upgrades screen particularly when moving the days (to wait) slider. This servicing plan is aimed at Current Branch computers so select the first option. Note: Even though Windows 10 version 1511 was declared as Current Branch for Business (CBB) on April 8th, 2016, that information has not yet trickled down to ConfigMgr as of 2016/4/10 therefore if you select the Business Ready deployment ring and 0 days, you will not see any suitable upgrades listed. On the Upgrades screen select the three checkboxes and set the search criteria to Language=English Required=>=1 Title= Upgrade to Windows 10 Enterprise Note: Make sure to select the right version (SKU) of Windows 10 for your deployment, if your clients are running Windows 10 Enterprise, then you should select the Enterprise version of the upgrade. Next, click on the Preview button, this will show what updates the wizard found that match your criteria For the Deployment Schedule screen set the Software Available Time to be at least 4 hours after the rule has run in order for the actual software update deployment packages to reach the destination distribution points. In a slow wan, increase that time. For Installation Deadline, the deadline is the displayed deadline time plus a random amount of time up to 2 hours, this is to reduce the load generated by all computers in the collection downloading the updates at the same time. On the User Experience screen, for User Notifications select Display in Software Center and show all notifications. For Deadline behavior, place a checkmark in Software Update Installation and System Restarts. On the Deployment Package screen choose Create a new deployment package and fill in the details as appropriate Next add the Distribution Points you want the package distributed to select where to download the content from and click through to the completion screen. Step 3. Review additional servicing plan properties Now that the servicing plan is created, highlight it in the console, right click and choose Properties. Select the Evaluation Schedule tab, as you can see by default it's set to run after every SUP sync, if you want to change that behavior modify it here. You can also review the Download Settings for the client in the Download Settings tab. In Deployment Settings set the amount of detail to Only success and error messages Step 4. Run the servicing plan and monitor Now everything is in place, you could sit back and wait for things to happen or kick off a test run. To trigger the servicing plan into running you need to initiate a SUP sync (as specified by the Evaluation Schedule), or right click on the Servicing Plan and choose Run Now. click OK to the message Using CMTrace, monitor the download progress in <ConfigMgr Installation Path>\Logs\PatchDownloader.log. If you are connecting to the console using terminal services check C:\Users\<username>\AppData\Local\Temp\2\PatchDownloader.log. You can even determine how much of the download is remaining based on the percent complete value as shown in this screenshot below: Note: Each Upgrade selected for download contains two architectures (X86 and X64) and their associated files. It is currently not possible to decide which Architecture to download. Using CMTrace, you can review the servicing plan progress in <ConfigMgr Installation Path>\Logs\RuleEngine.log After the download has completed successfully the Servicing Plan will be deployed (and the content distributed to the distribution points) and then show up in the ConfigMgr console in the Monitoring workspace, under Deployments. You can also review Software Update Groups where the servicing plan will be listed along with its' Deployment. Step 5. Review the Upgrade process on your Windows 10 devices Note: Ensure that one or more applicable Windows devices are in the collection used when creating the servicing plan. Also note that if you are just testing the servicing plan, and you used the settings above that it may take up to 4 hours to show up on the client, adjust the servicing plan as necessary and choose Run Now again to re-deploy it with the new settings.. Now everything is in place for the Windows 10 servicing to begin. For this section you can review what happens on a Windows 10 version 1507 client. The first thing the client will see is a familiar notification in the systray informing the user that Software Changes are required. clicking on that shows you these options and before long it starts downloading and then installing the Upgrade as the Servicing Plan was configured for all notifications, the user will be notified of the pending restart at which time Windows will get updated after everything is complete, log in to Windows to see this... note the new version after the upgrade ? Job done! After confirming the success of the upgrade methodology, you can hop back to the ConfigMgr console and review the Windows 10 Servicing Dashboard. Notice the Deploy Now button, that allows you to further deploy the same Servicing Plan to more collections. Note: Occasionally Microsoft re-releases the Windows 10 upgrade media to the VLSC and Windows Update with newer versions of the media (for example adding Cumulative Updates to the media), and when they do so they currently expire the available media, meaning that new content has to be downloaded and evaluated by your servicing plans. This behavior may change in the future but for now, be aware of it. until next time, adios ! Summary Upgrading Windows 10 devices to a later release of Windows 10 is made easier with servicing plans defined at a schedule that suits you. While servicing plans won't take care of earlier versions of Windows such as Windows 7 or Windows 8.1, you can upgrade those devices with the upgrade task sequence method instead. Client side language packs are important to keep in mind as Servicing Plans do not deal with languages on the client side (if any are installed). Also, servicing plans cannot handle drivers or pre and post setup upgrade steps, for that use the upgrade task sequence method instead. A significant amount of functionality has improved and changed between the ConfigMgr 1511 and ConfigMgr 1602 Current Branch releases based on feedback from UserVoice and connect.microsoft.com. I strongly expect the next release of ConfigMgr will be even more fine tuned and feature rich particularly in the area of Windows 10 servicing. Related Reading Plan for Windows 10 deployment - https://technet.microsoft.com/itpro/windows/plan/index Windows 10 servicing options for updates and upgrades - https://technet.microsoft.com/itpro/windows/manage/introduction-to-windows-10-servicing Manage Windows as a service using System Center Configuration Manager - https://technet.microsoft.com/en-us/library/mt627931.aspx Windows 10 1511 is now a Current Branch for Business (CBB) release - http://blogs.technet.com/b/windowsitpro/archive/2016/04/08/windows-10-1511-is-now-a-current-branch-for-business-cbb-release.aspx Windows 10 release information - https://technet.microsoft.com/en-us/windows/mt679505.aspx?ocid=wc-ext-aka Downloads You can download a Microsoft Word copy of this guide here dated 2016/04/10 How can I use servicing plans in System Center Configuration Manager (Current Branch) to upgrade Windows 10 devices.zip
-
Microsoft has announced that Windows 10 version 1511 has been officially declared as Current Branch for Business. Michael Niehaus stated:- "each new Windows 10 feature update is initially considered a Current Branch (CB) release, to be used by organizations for initial pilot deployments. The feature update will later be declared as Current Branch for Business (CBB), once we have received feedback and confirmation from organizations, OEMs, and partners, confirming that the feature update is ready for broad deployment." So what does that mean for those of us who are actively deploying Windows 10 in the Enterprise already ? Not a whole lot as long as you are running Windows 10 version 1511 already. For devices already running Windows 10 version 1511, deployed before the CBB declaration, no action is required other than standard monthly servicing. With the installation of the March cumulative update (KB3140768) or any later cumulative update, the device is already running the equivalent of what was declared as CBB. What about those of us who have Windows 10 1507 devices deployed in the Enterprise ? I've highlighted some points in bold below:- For devices being serviced using Windows Update for Business and configured to “Defer upgrades,” Windows 10 1511 will begin to deploy as soon as the updated media has been published. (Note that the deferral policies that specify an additional number of months to defer the feature update are not supported for devices running Windows 10 1507.) For devices being serviced using Windows Server Updates Services, the updates to the existing Windows 10 1511 feature updates will need to be re-approved once the new updated media is received (unless you have an automatic update rule configured for the “Upgrades” category). For those using the System Center Configuration Manager Windows 10 servicing plans to keep Windows 10 devices up to date, the updated media will be detected as “business ready,” causing servicing plans based on that “business ready” designation to begin to be evaluated. For devices that will be upgraded using System Center Configuration Manager or Microsoft Deployment Toolkit task sequences, you may want to switch to the latest media (downloaded from the Volume Licensing Service Center) instead of the current Windows 10 1511 media. Alternatively, you can inject the March cumulative update (KB3140768) into your existing media. (a guide for the upgrade task sequence along with injecting updates is here) Microsoft has also updated the Release Information page available at http://aka.ms/win10releaseinfo to reflect the updated status of Windows 10 1511. cheers niall
-
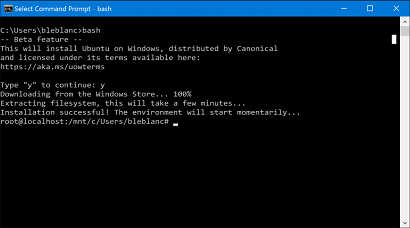
Gabe Aul announced that there's a new insider preview available on the fast ring, and here’s what’s new in Build 14316 Run native Bash on Ubuntu on Windows: In this build, you can natively run Bash in Windows as announced last week at Build 2016. To do this, you first need to turn on Developer Mode via Settings > Update & security > For developers. Then search for “Windows Features” and choose “Turn Windows features on or off” and enable Windows Subsystem for Linux (Beta). To get Bash installed, open Command Prompt and type “bash”. For more details, see this blog post. to see a guide explaining what to do see here > https://msdn.microsoft.com/en-us/commandline/wsl/install_guide# and for more info about this release see the original blog post here > https://blogs.windows.com/windowsexperience/2016/04/06/announcing-windows-10-insider-preview-build-14316/
-

PS script for registry edit - works manually, not through SCCM
anyweb replied to Kops's topic in Configuration Manager 2012
here's a way around it https://www.windows-noob.com/forums/topic/7772-how-can-i-change-a-hkcu-setting-within-windows-during-an-osd-deployment/ -
pause the computer after scanstate to see what is working (or not working)
-
Microsoft is reaching out to Linux developers in a way that the company never has before. "The Bash shell is coming to Windows. Yes, the real Bash is coming to Windows," said Microsoft's Kevin Gallo on stage at today's Build 2016 keynote. The announcement received an uproarious applause from the crowd. The new functionality will be enabled as part of this summer's Anniversary Update to Windows 10. "This is not a VM. This is not cross-compiled tools. This is native," he said. "We've partnered with Canonical to offer this great experience, which you'll be able to download right from the Windows Store." Third-party tools have enabled this sort of thing for years, but a direct partnership between Microsoft and Canonical should offer even more flexibility and convenience for developers who prefer using these binaries and tools. for the full story read more @ the Verge
-

Unable to Pause Task Sequence using .HTA
anyweb replied to Config_Mgr_noob's topic in Configuration Manager 2012
where is the warning.hta file placed ? try hard coding the path to it eg: C:\Windows\temp\warning.hta -
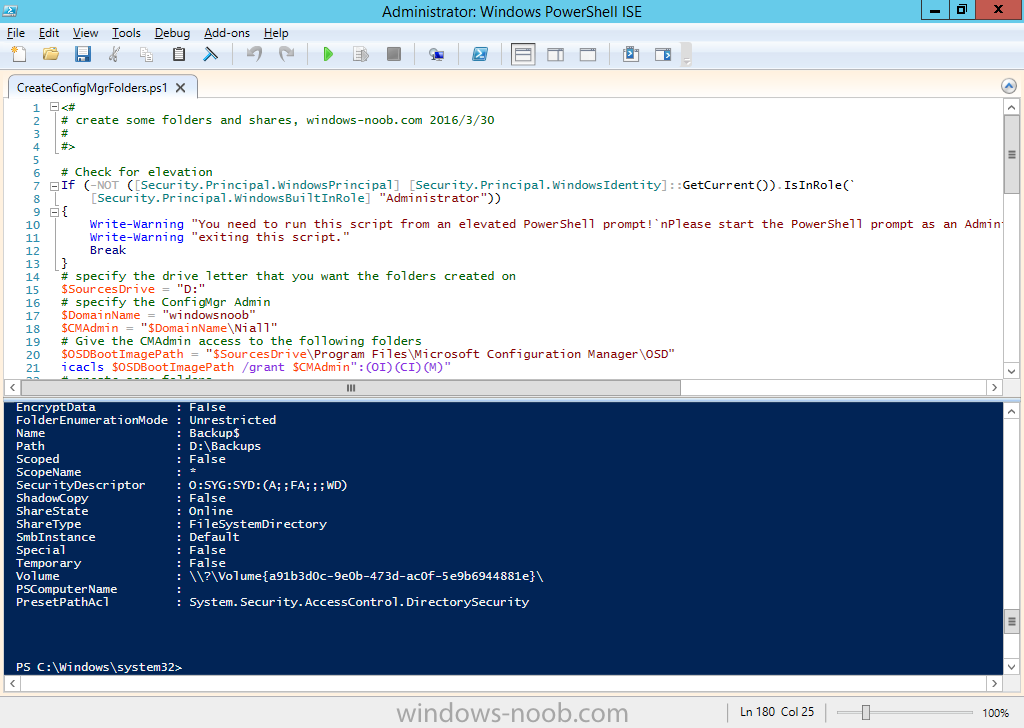
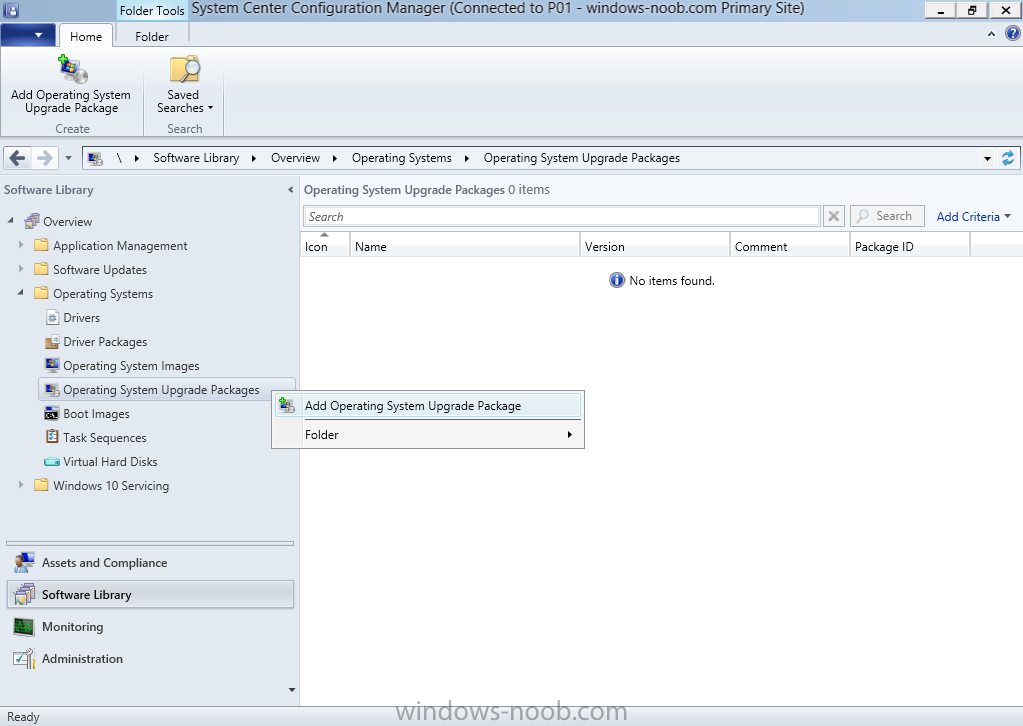
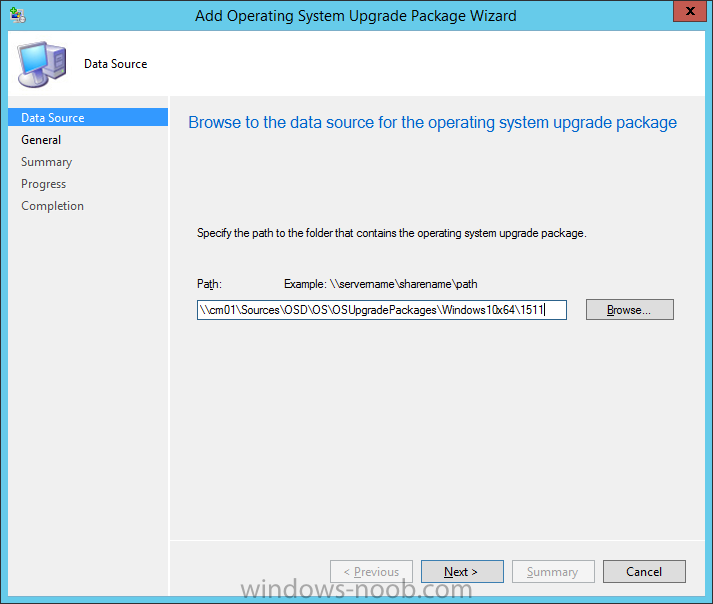
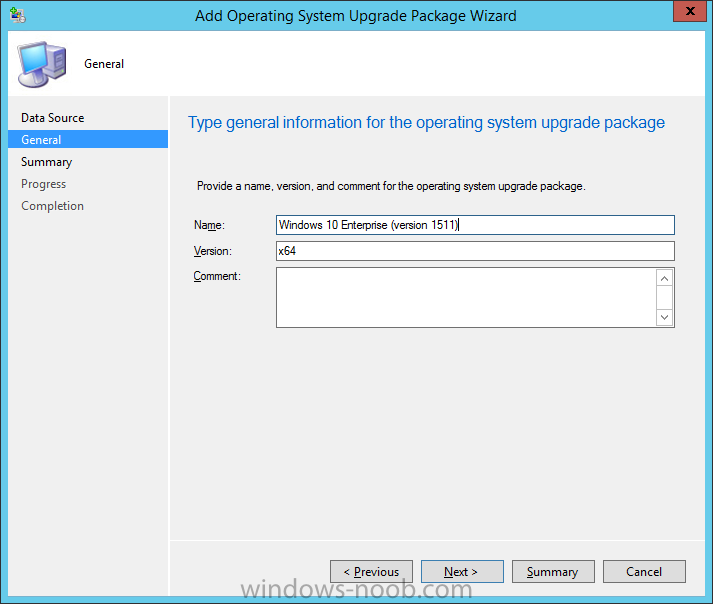
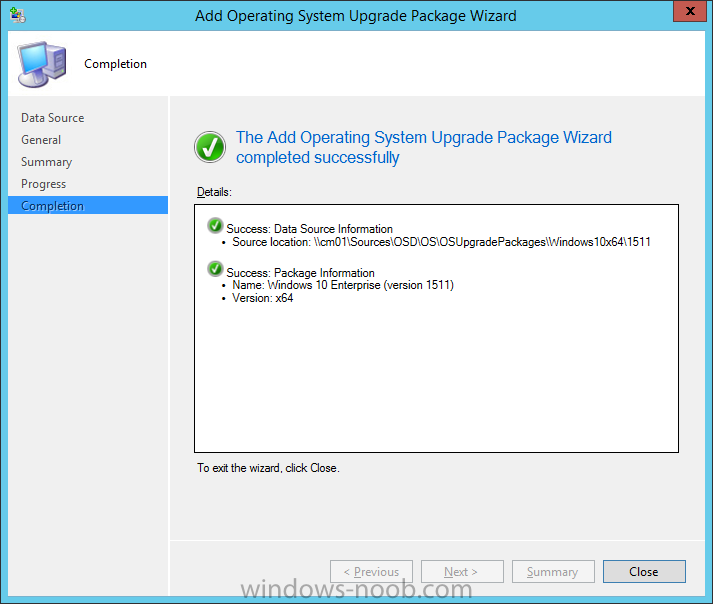
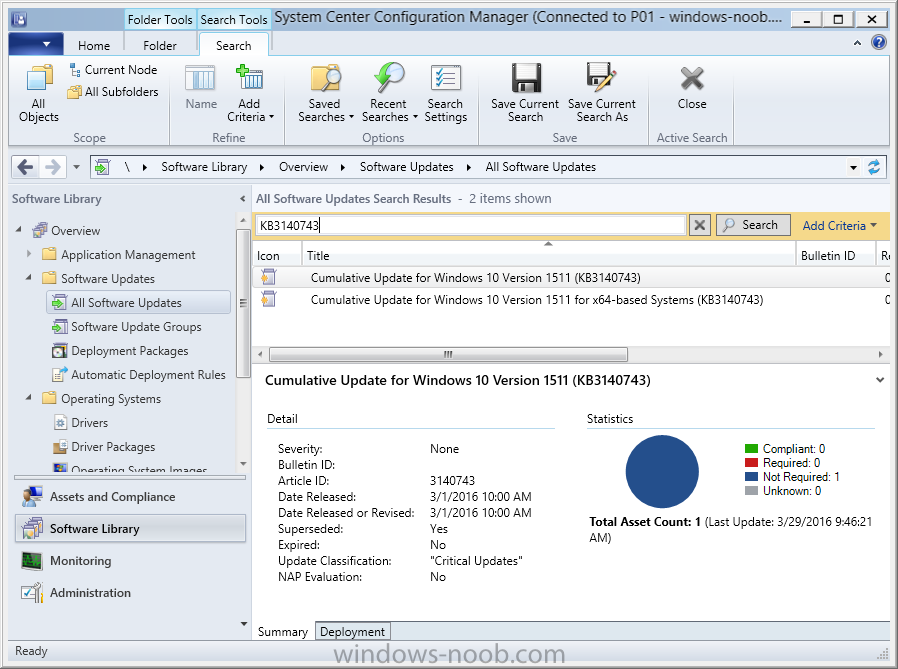
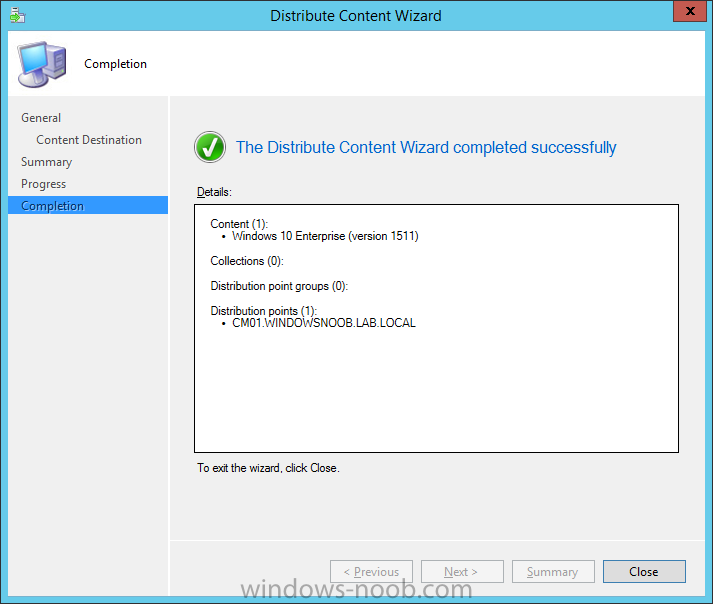
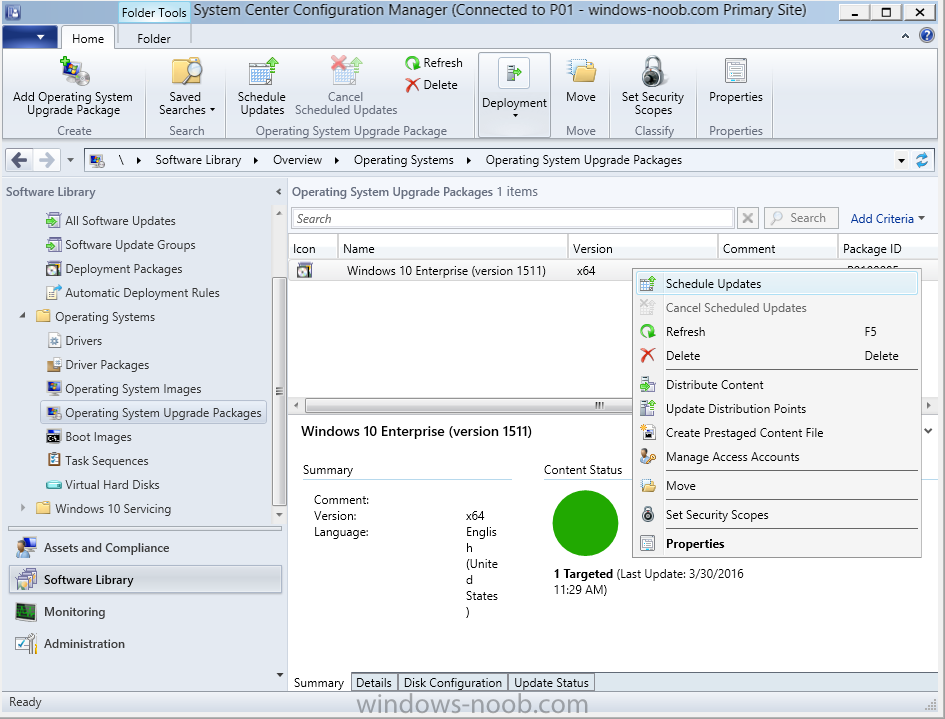
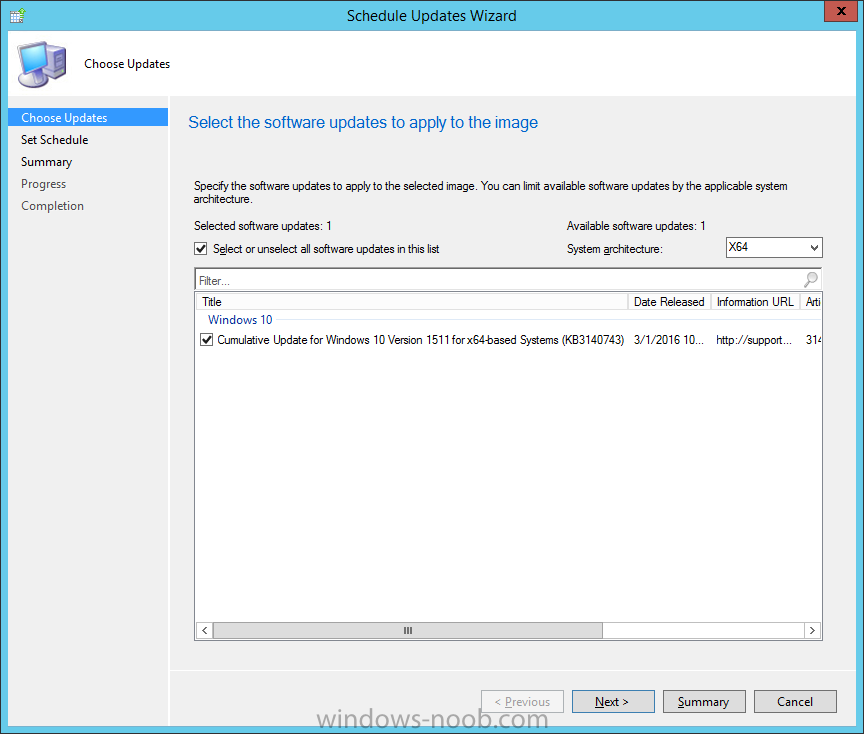
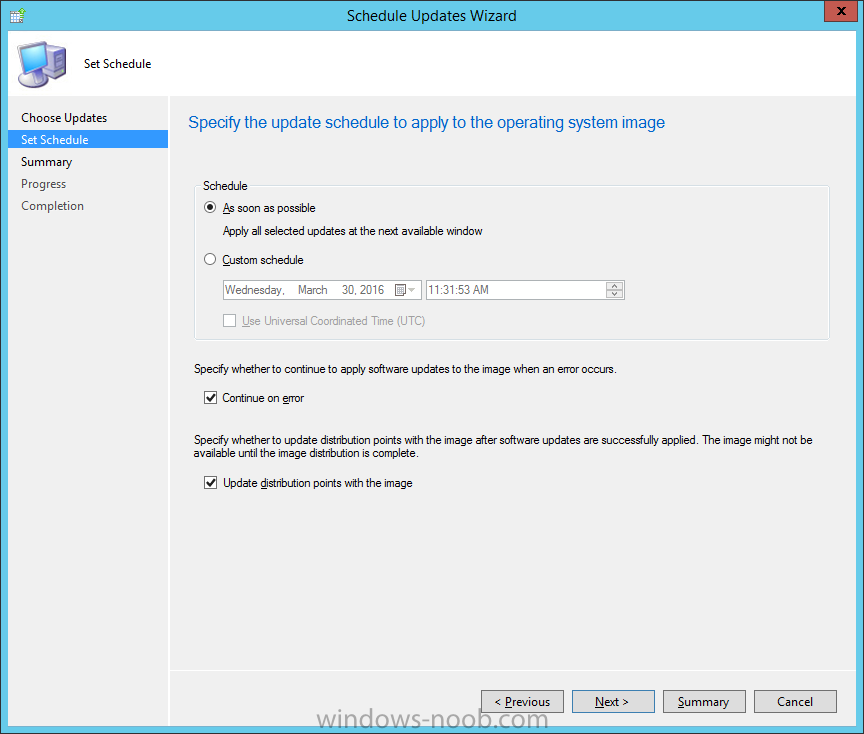
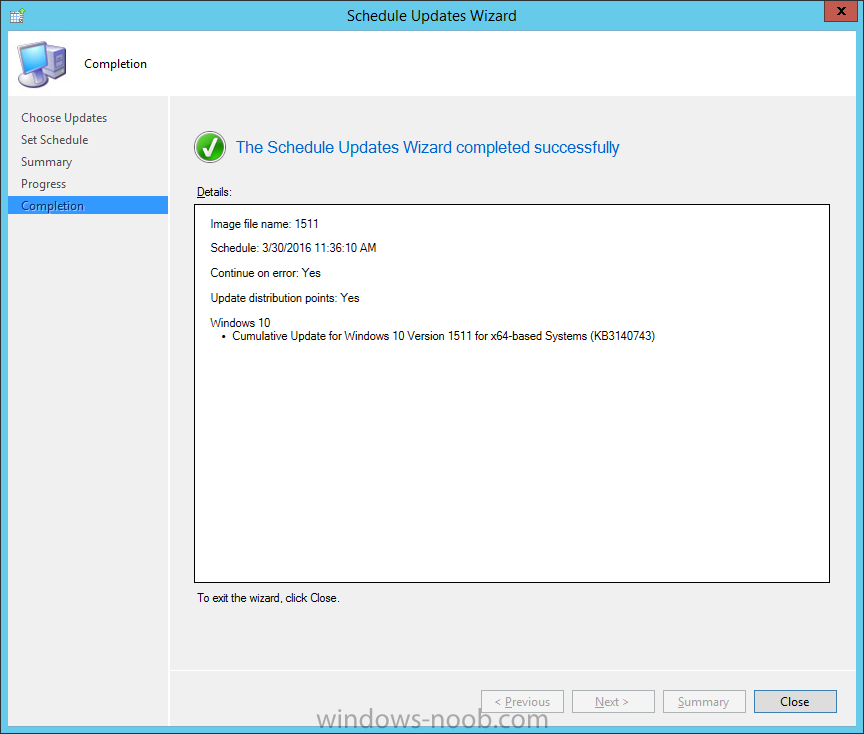
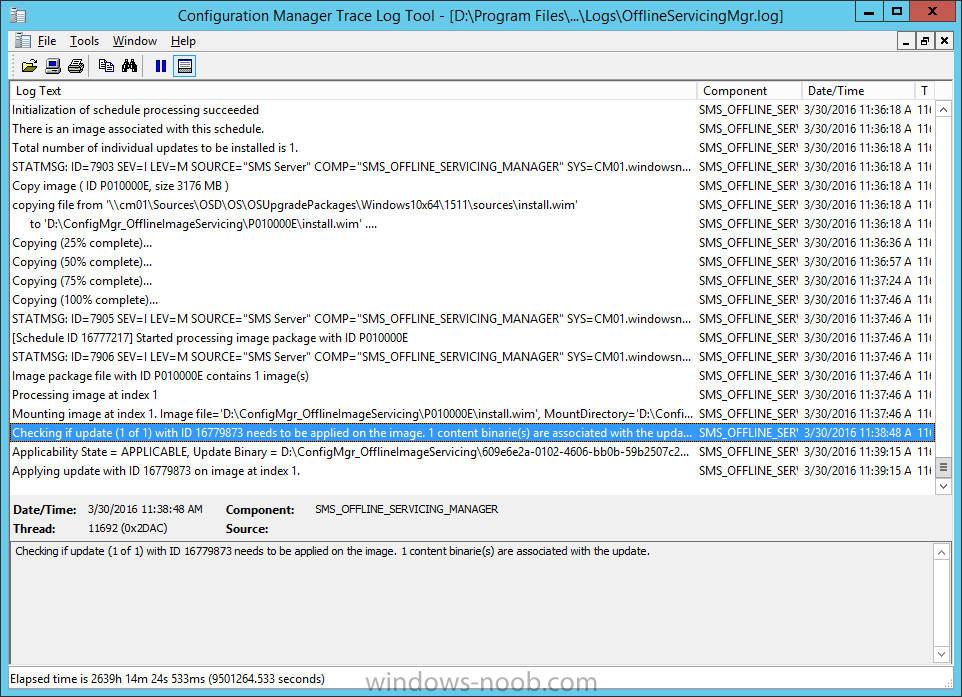
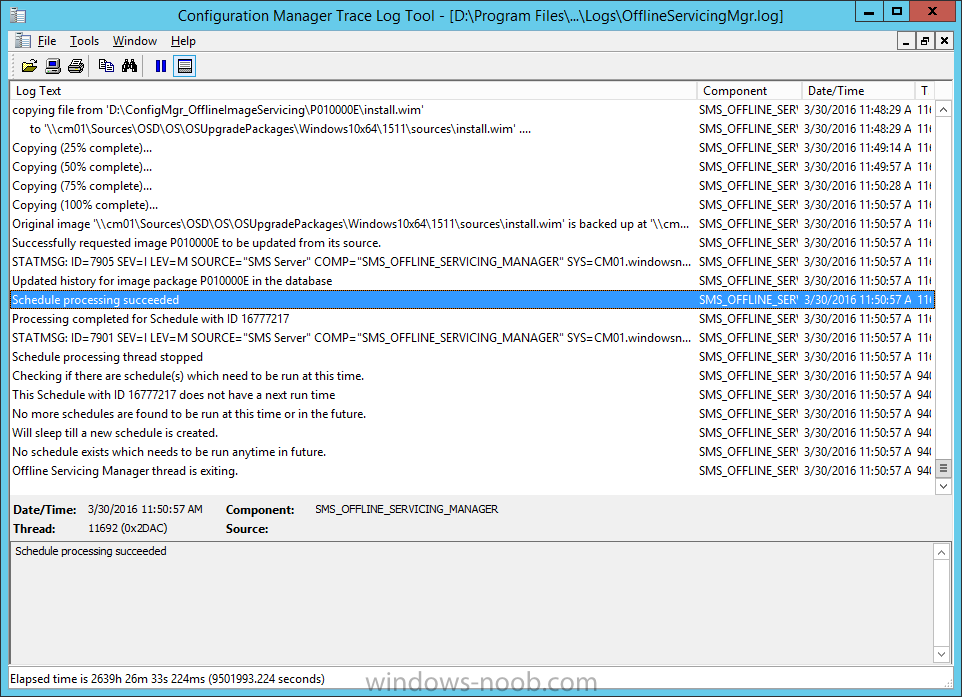
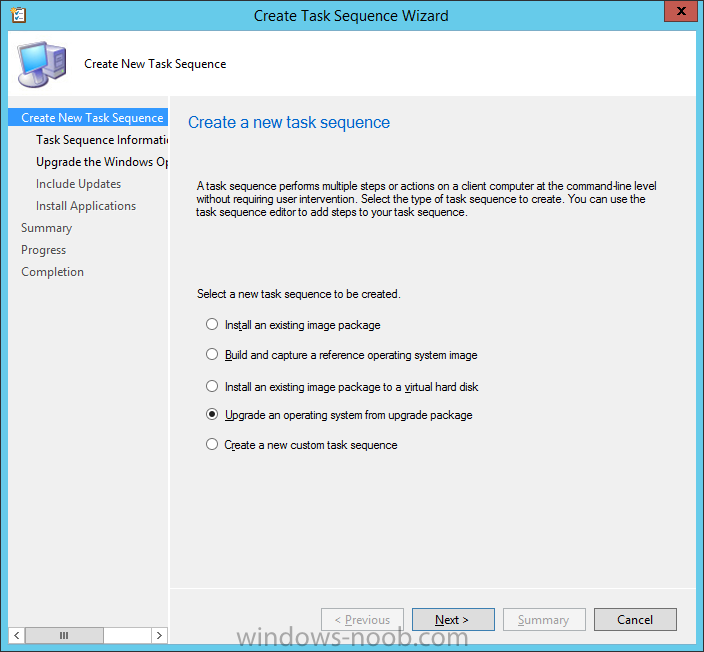
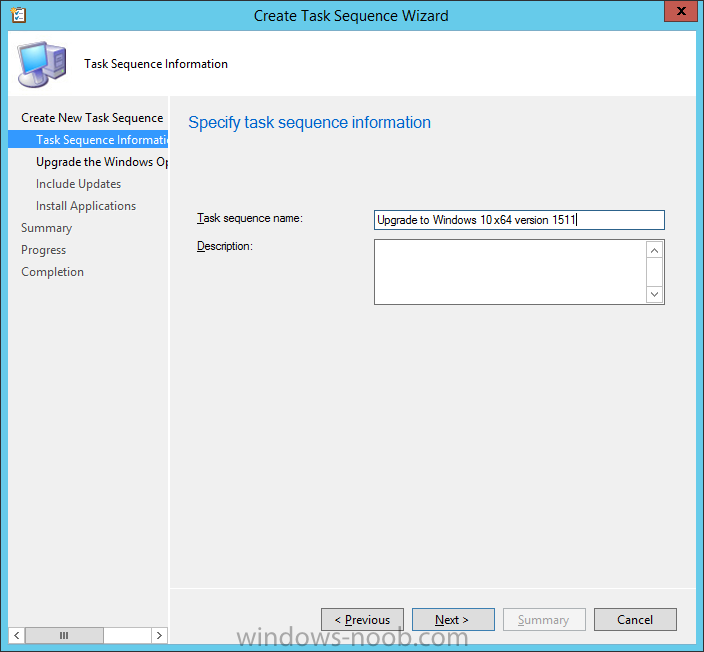
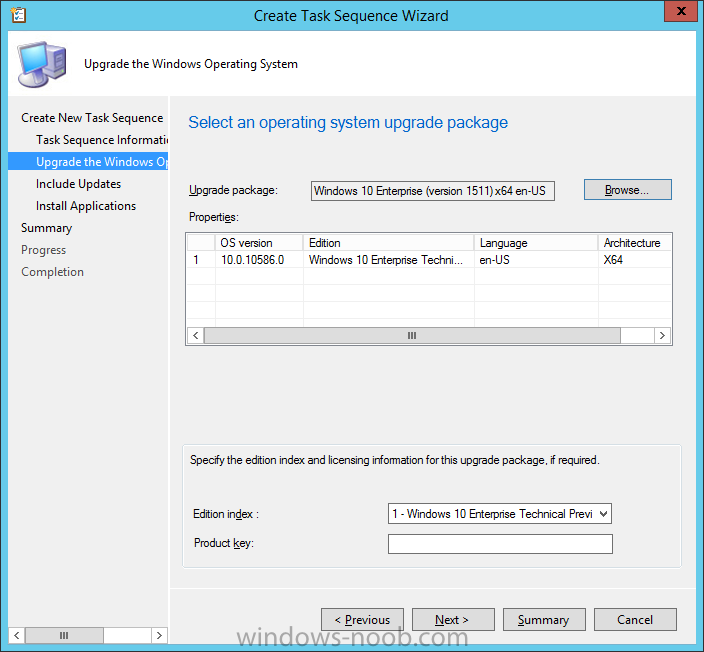
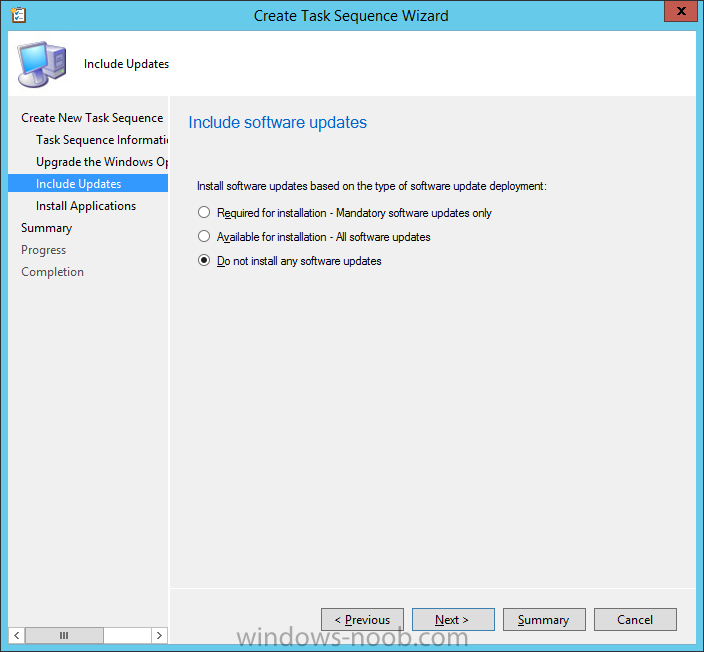
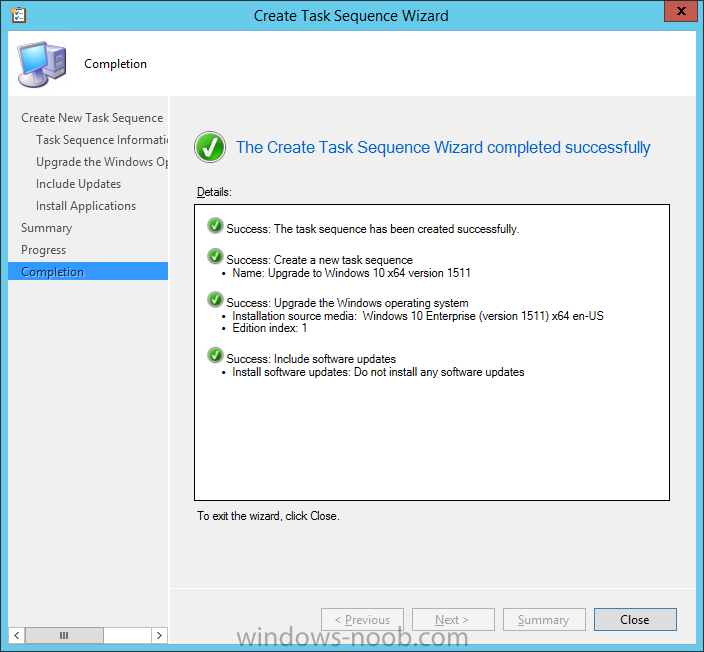
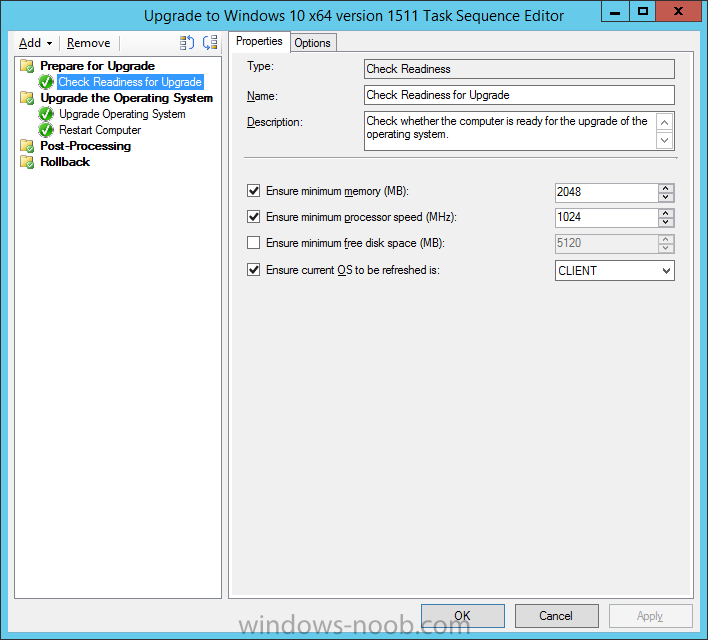
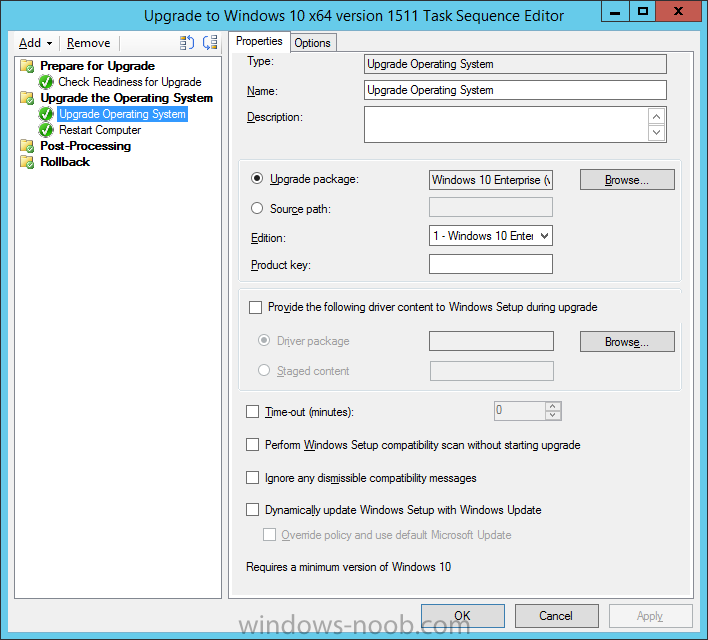
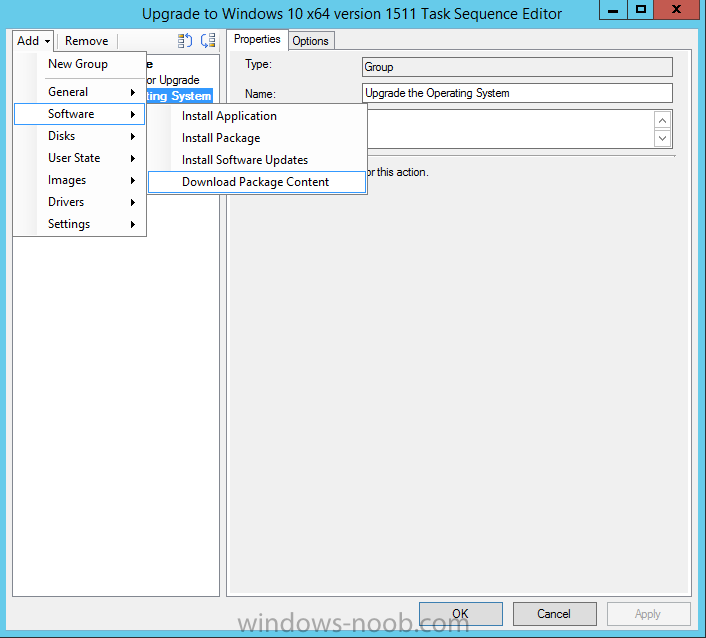
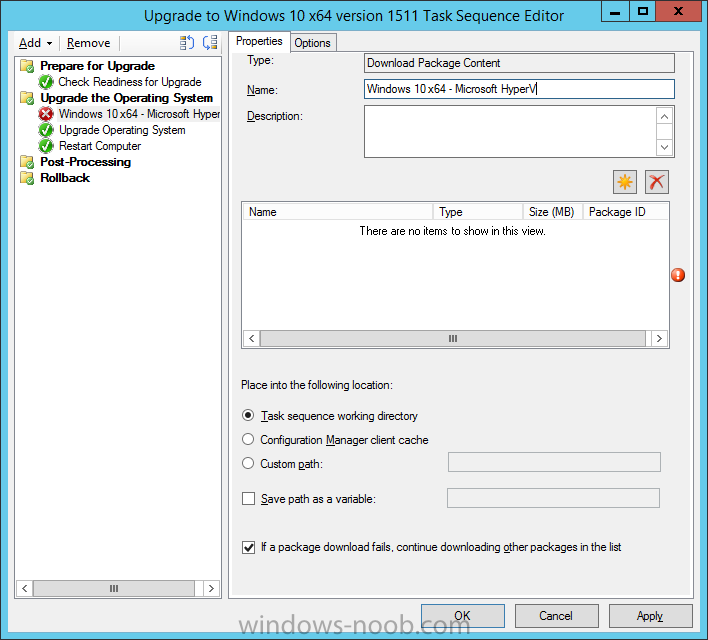
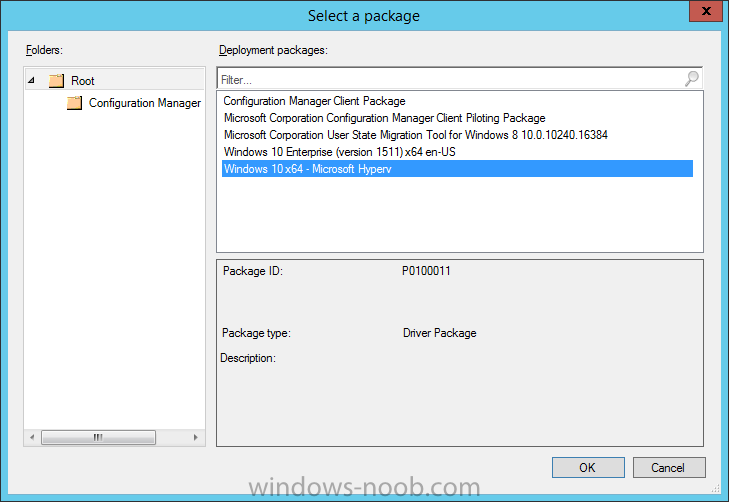
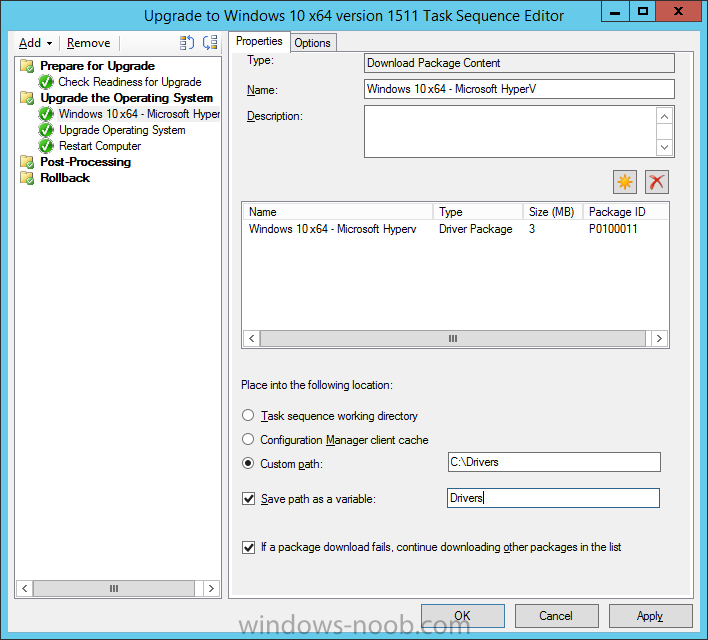
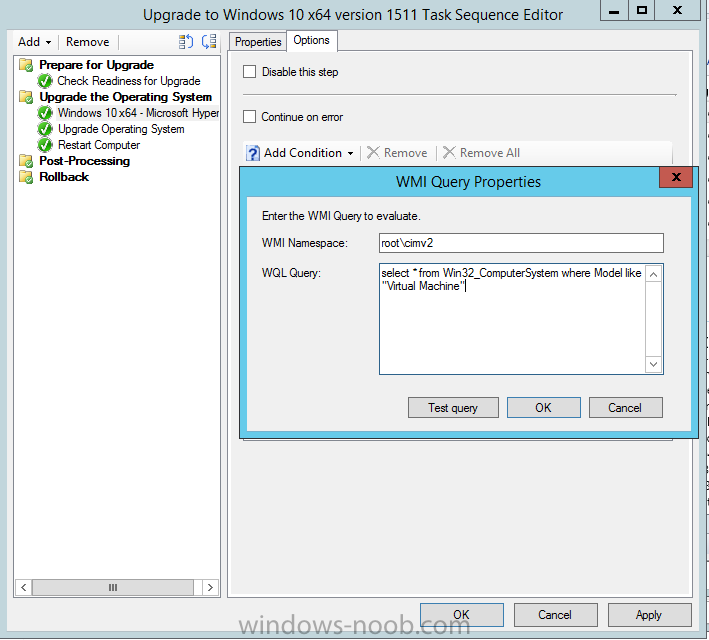
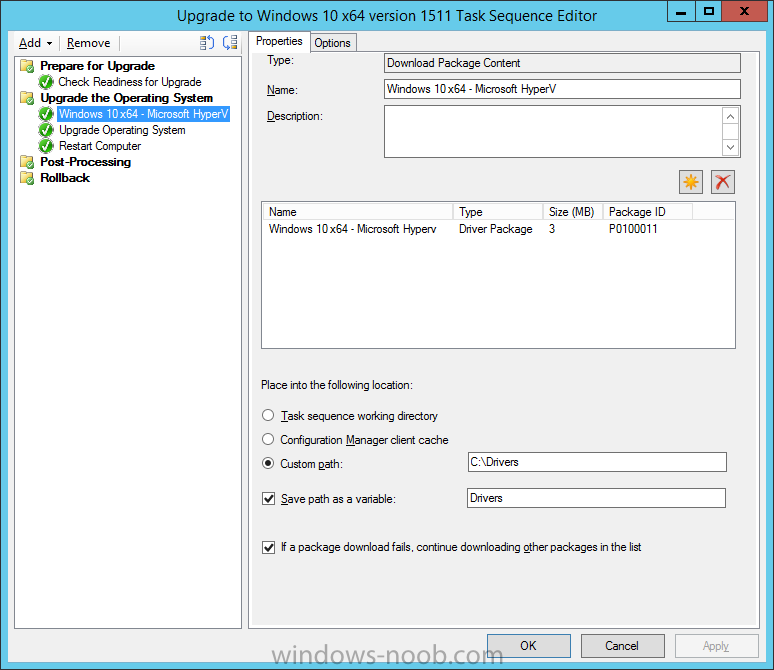
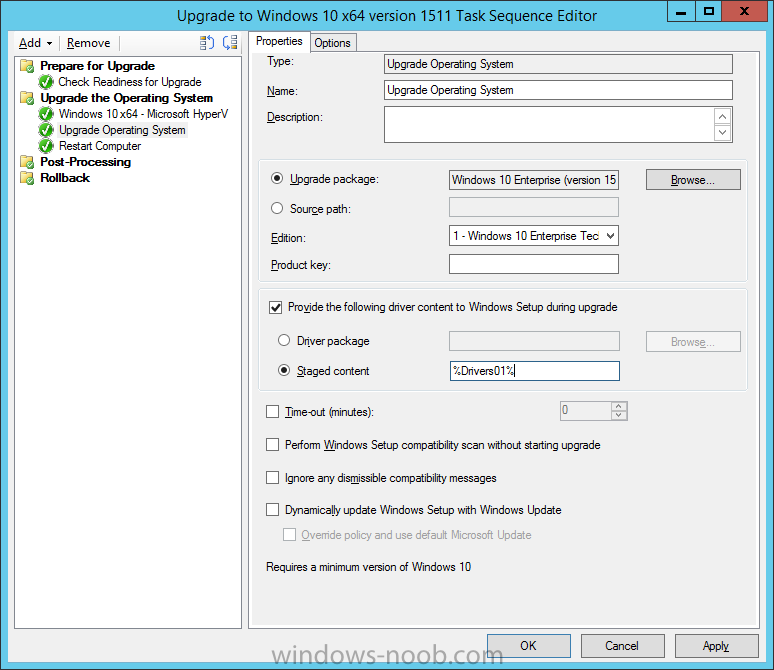
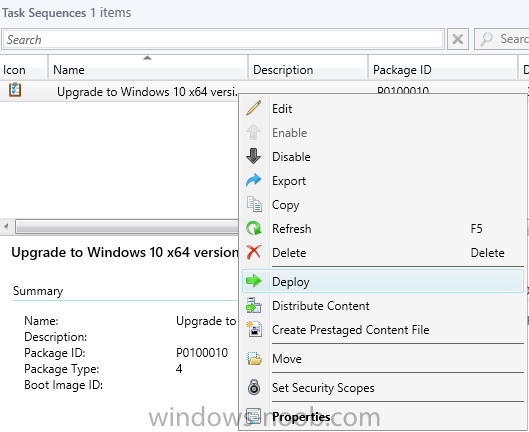
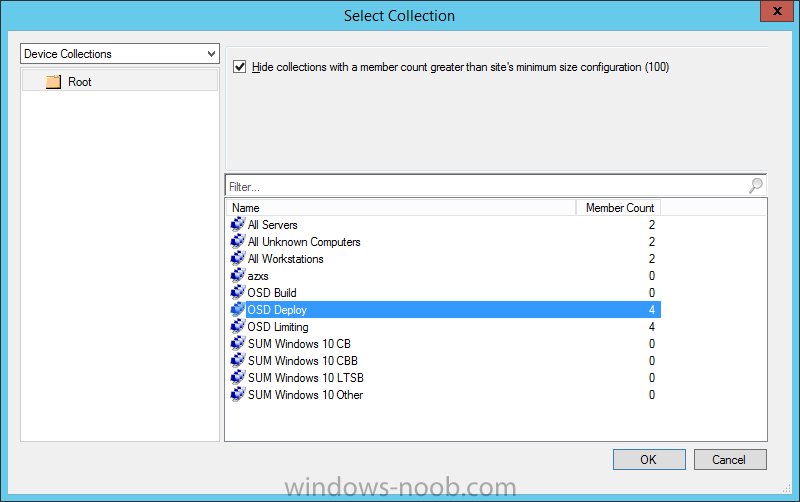
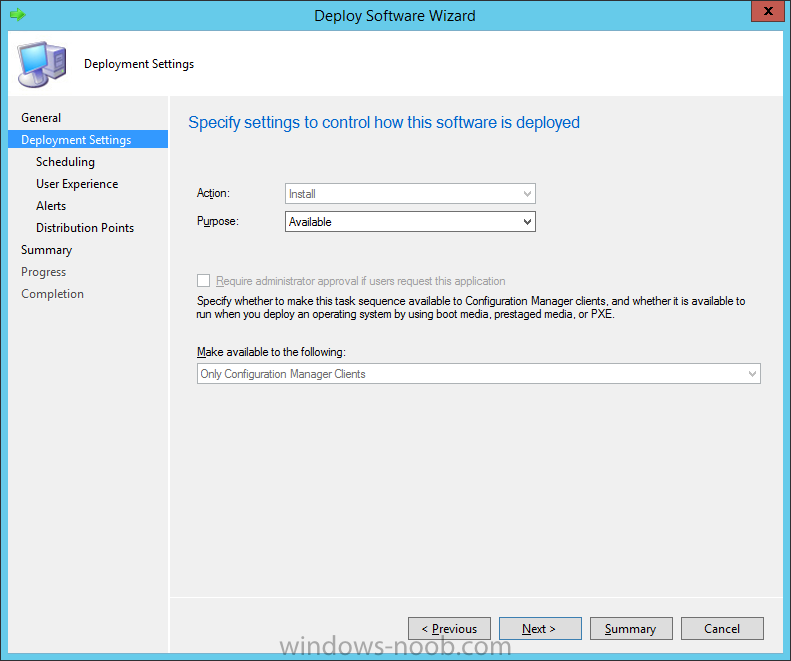
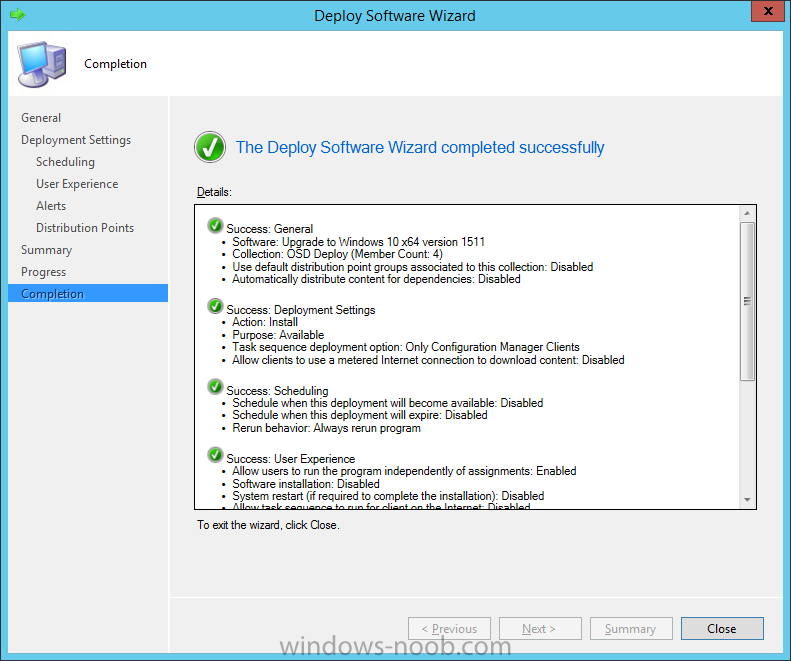
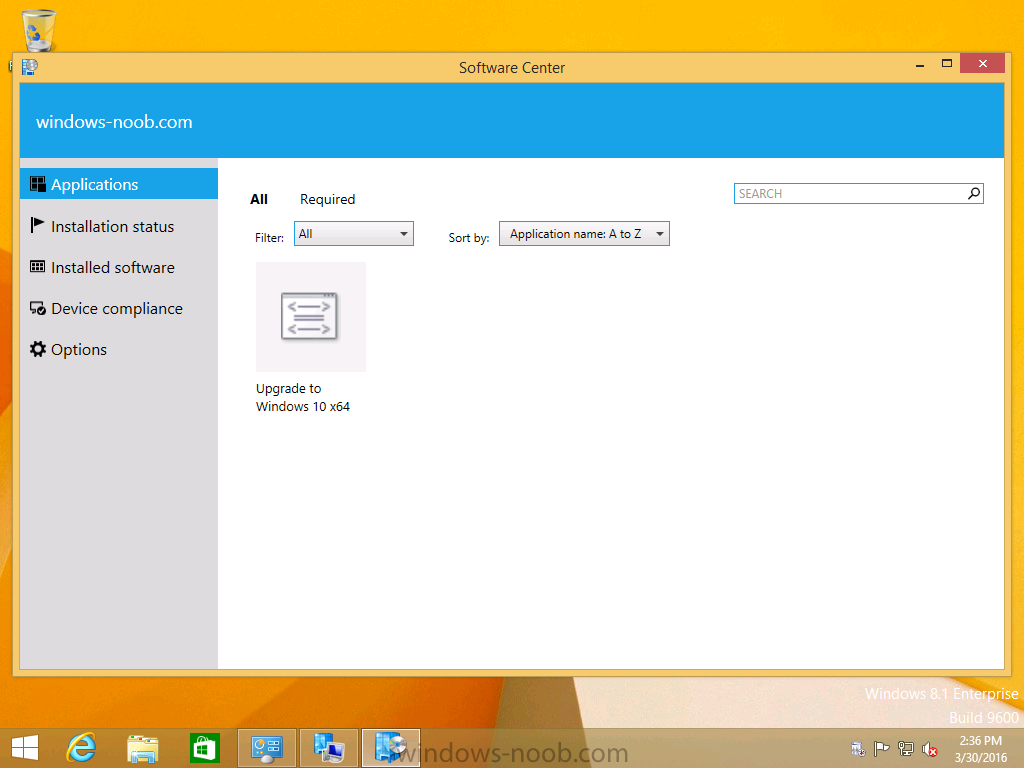
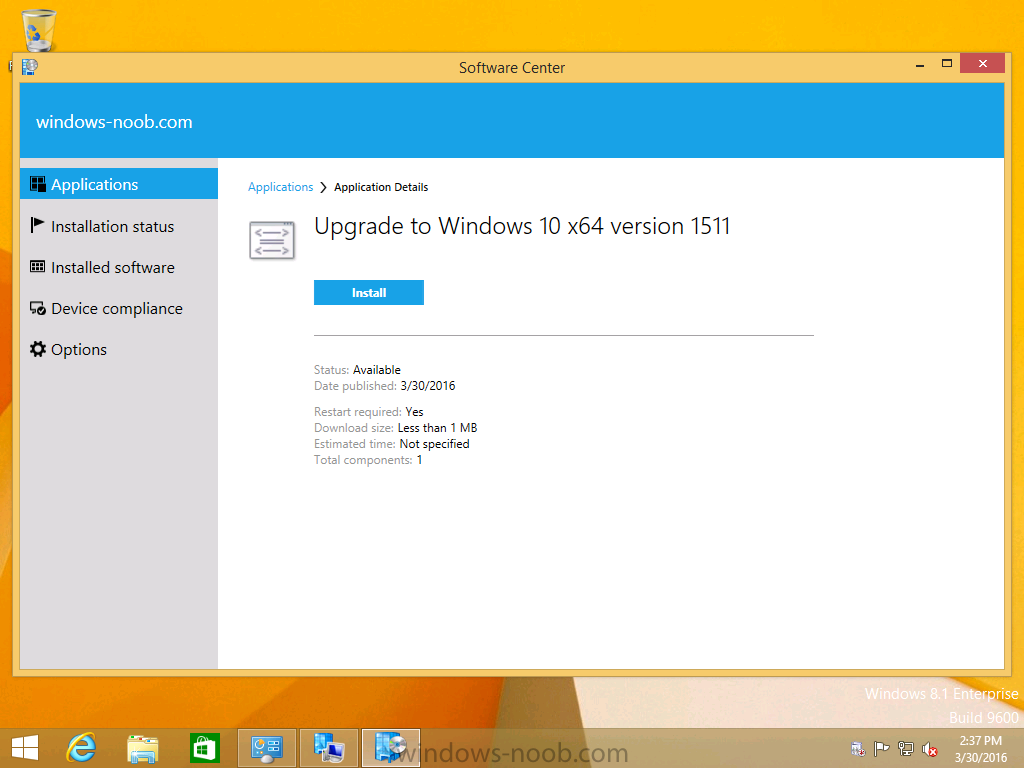
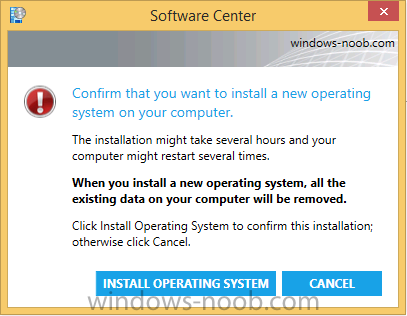
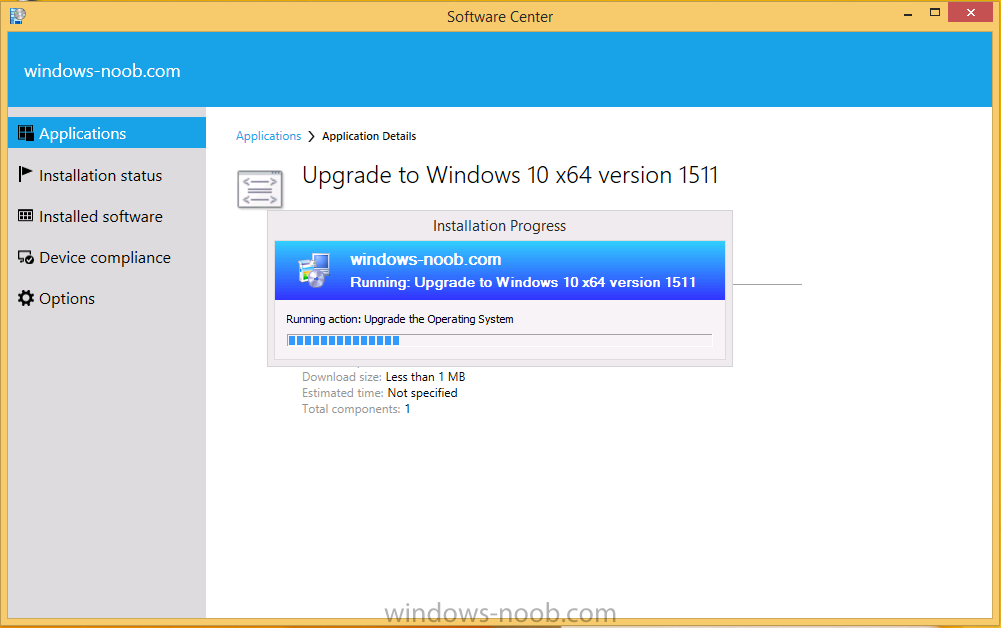
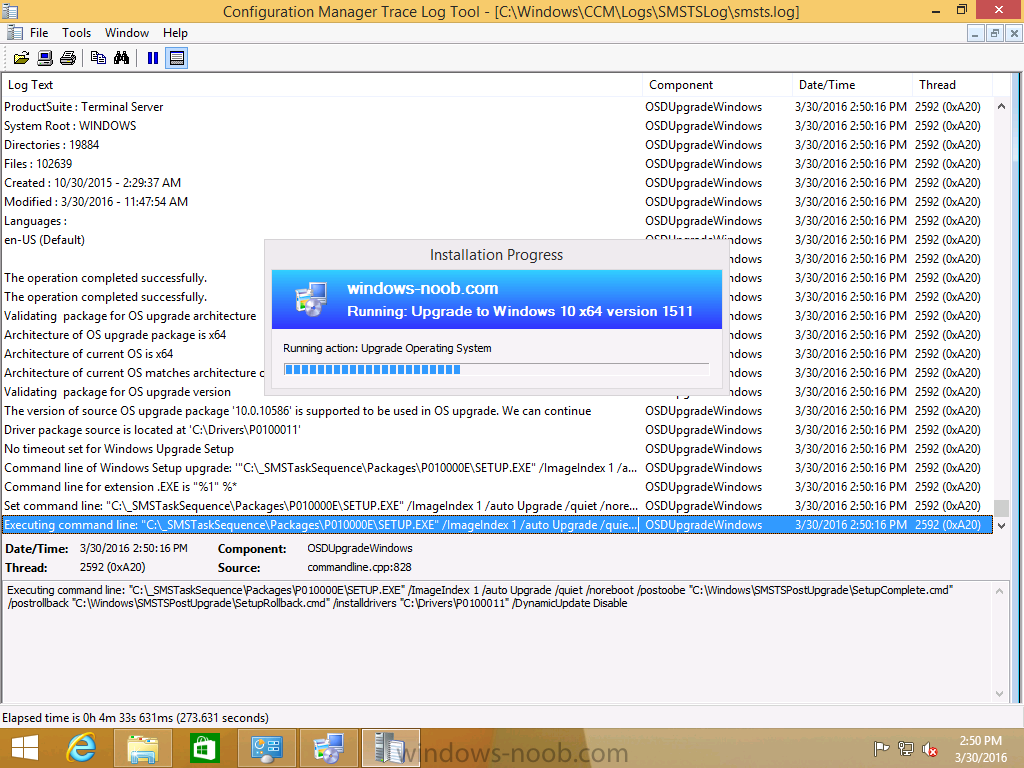
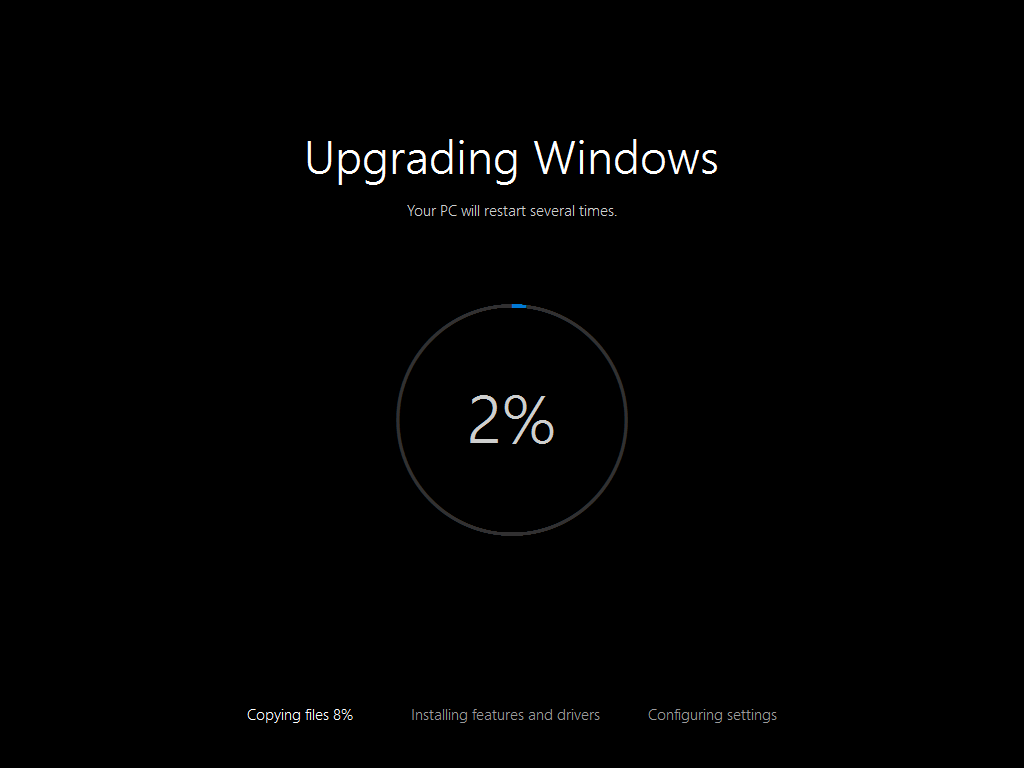
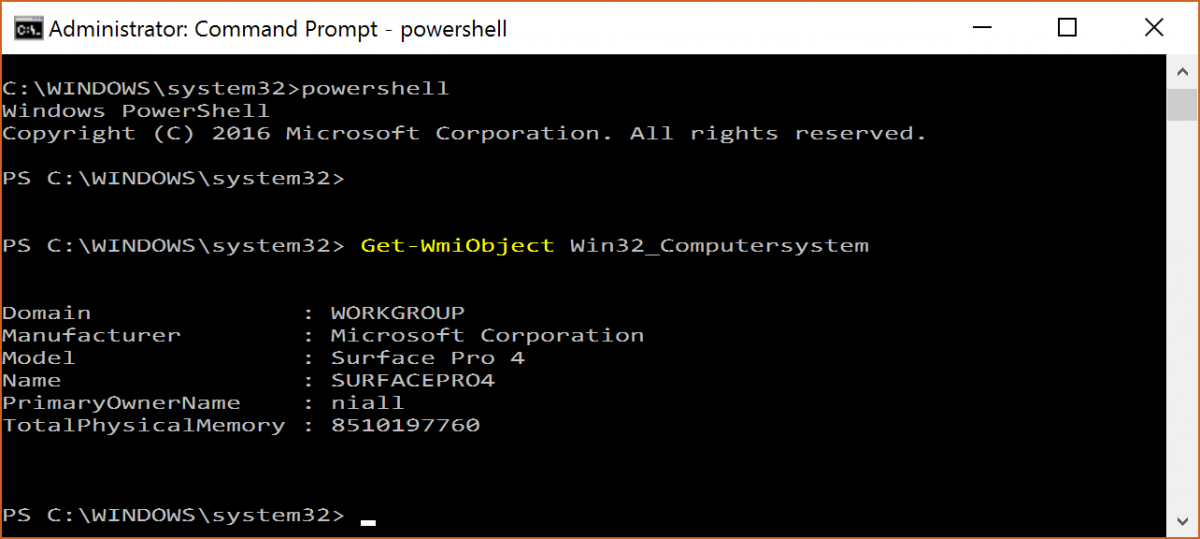
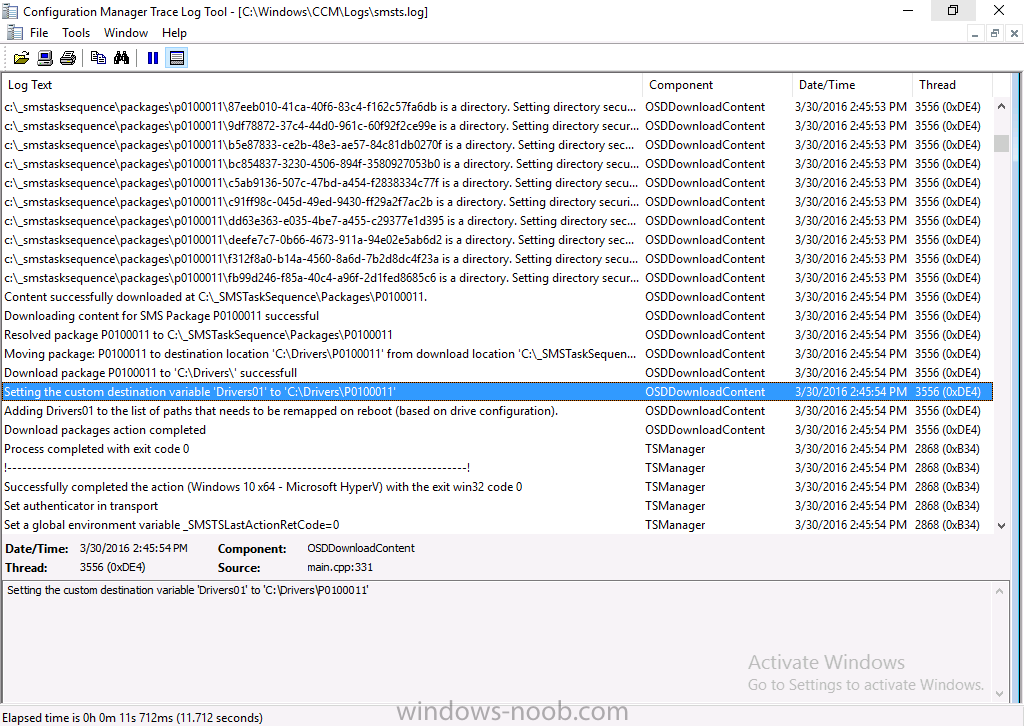
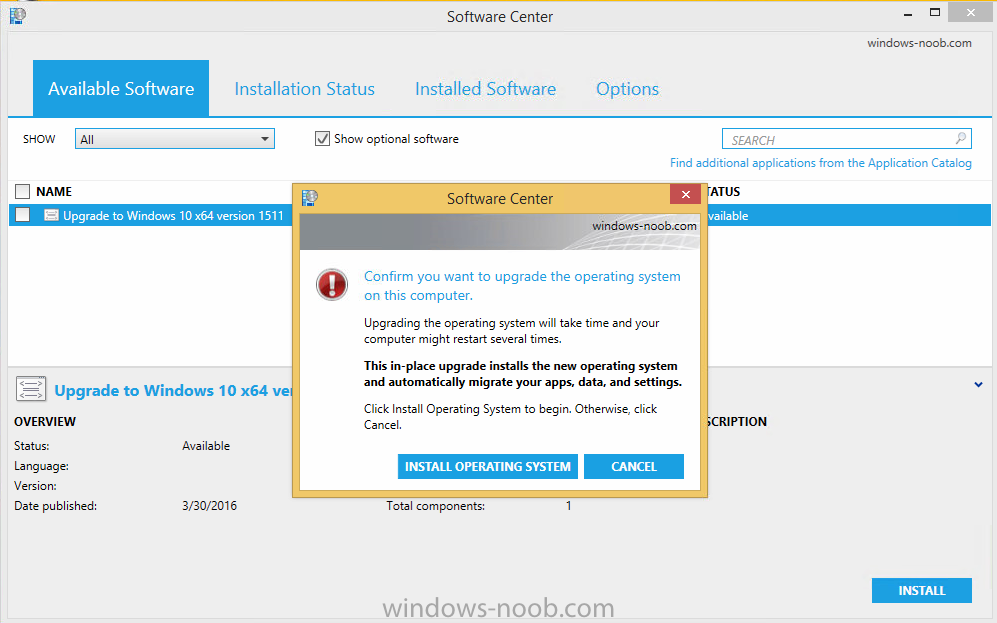
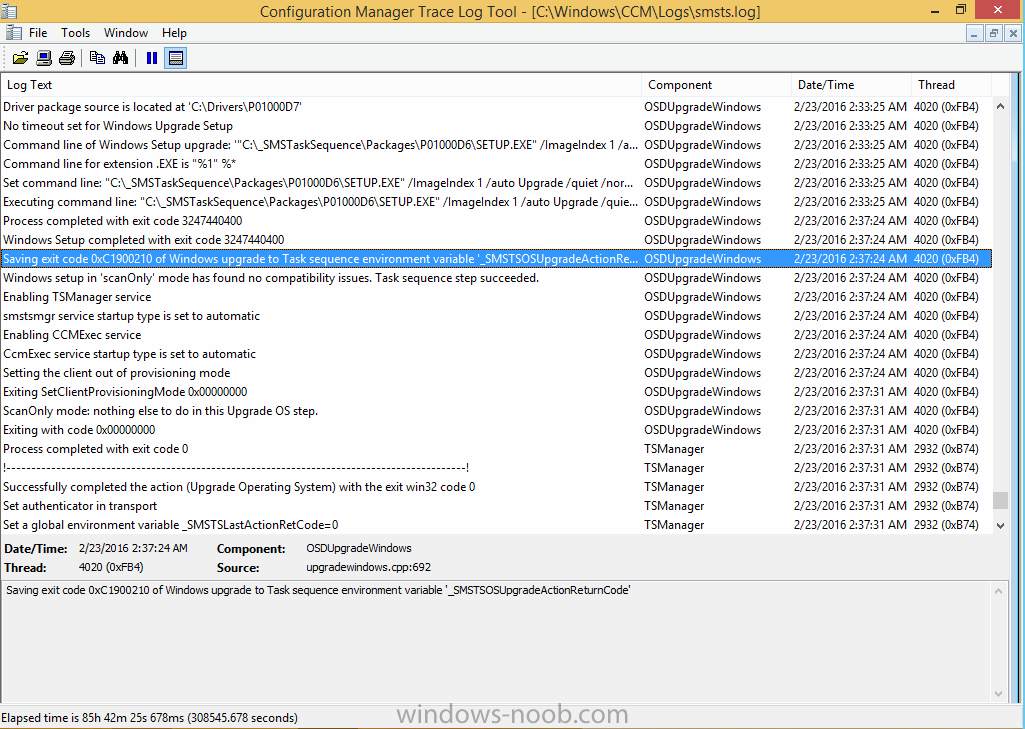
Introduction At the start of this series of step by step guides you installed System Center Configuration Manager (Current Branch), then you configured discovery methods. Next you configured boundaries to get an understanding of how automatic site assignment and content location works. After that you learned how to update ConfigMgr with new features and fixes using a new ability called Updates and Servicing and you learned how to configure ConfigMgr to use Updates and Servicing in one of these two modes: Online mode Offline mode To prepare your environment for Windows 10 servicing (coming in a later guide) you learned how to setup Software Updates using an automated method (via a PowerShell script) or manually using the ConfigMgr console. Next you used a PowerShell script to prepare some device collections, then you configured client settings for your enterprise and finally you'll deployed the ConfigMgr client agent using the software updates method which is the least intensive method of deploying the Configuration Manager client agent. As System Center Configuration Manager (current branch) is being delivered as a service now, version 1602 was made available (March 11th, 2016) and you used Updates and Servicing to do an in-place upgrade to that version as explained here. The Upgrade Task Sequence In this guide you will learn about the Upgrade Task Sequence which is now built-in to System Center Configuration Manager (current branch). This new type of task sequence was initially offered as a download from Microsoft for System Center 2012 R2 SP1 Configuration Manager however that version lacked certain abilities (such as installing drivers). The Upgrade task sequence allows you to upgrade your Windows 7, Windows 8, Windows 8.1 computers (and even Windows 10) to the latest and greatest version of Windows 10. This is a new method of upgrading the operating system and it leaves the users files and settings intact. The System Center Configuration Manager (current branch) Upgrade Task Sequence can even handle drivers in the task sequence which is definitely a useful feature. Note: In this Lab I've already upgraded the ADK version from 1507 to 1511, for details about how you can do that review Brandon's post here. In addition these boot wims are patched with KB3143760 and you can use Keith's PowerShell script to do it easily. Step 1. Create some ConfigMgr folders We need some folders created to store things that OSD requires (such as the operating system upgrade package) so let's use a PowerShell script to create them. Note: This script creates several custom folders used for OSD, many are not applicable to the Upgrade Task Sequence but I'm including them as they will be used later as part of this series. The script is available at the end of this post in the Downloads section. To use it simply edit any variables you deem necessary (such as domain, users and sources drive) and save your changes. Open the edited script in PowerShell ISE by starting it as Administrator and run the script by pressing on the green triangle. Some of the created folders are shown below. Step 2. Copy the Windows 10 media Before you get started with the upgrade task sequence you'll need a copy of Windows 10 media which you can download from MSDN or your Microsoft Volume License site. In this guide I'll use the latest version currently available and that is Windows 10 x64 version 1511. Once you've located a copy of this media copy the extracted contents of it to the following path (which was created by the PowerShell script above). \\cm01\Sources\OSD\OS\OSUpgradePackages\Windows10x64\1511 as shown below Step 3. Add Windows 10 as an operating system upgrade package To add Windows 10 version 1511 as an operating system upgrade package do as follows. In the Configuration Manager console, click Software Library and expand Operating Systems then click Operating System upgrade packages. Right click on Operating System upgrade packages and choose Add Operating System upgrade package. When the wizard appears fill in the path to the media and click on next fill in some details about the Windows 10 image, and include the version as you'll need to re-do this process every 6 months or so. continue through the wizard until completion. Note: To make the image available on the network, distribute it to your distribution points by right-clicking and choose Distribute Content. Step 4. Optionally add software updates to the Windows 10 upgrade package Cumulative updates are released for Windows 10 regularly, and the latest available cumulative update for Windows 10 version 1511 at the time of writing is KB3140743. To make this update available for servicing search for it in Software Updates as shown below. I won't go into too many details of making the update available but in a nutshell what i did was as follows: Synchronize Software Updates create folder structure to store update package (\\cm01\sources\updates\windows10) create a Software Update Group from the matching architecture (x64) Cumulative Update above and deploy it to the SUM Windows 10 CB collection While the above worked for me, all you should have to do is: Synchronize Software Updates Select one or more updates and download them Once done, right click on the Windows 10 upgrade package and choose Schedule Updates after a few moments you should see any updates you've made available and you can select the update you wish to apply or deselect any you don't want applied Next, select a schedule that applies to your environment remembering that distribution of the patched wim can consume network resources so perhaps a custom schedule during off-business hours would be useful and click next through completion. At this point you can monitor the OfflineServicingMgr.log file available in <ConfigMgr Installation Path>\Logs by opening it in CMTrace to get details of the actual patching of the wim file. After some time it will check all available updates that you made available to see if they are applicable or not, each update will have an Applicability State which can be listed as any of the following:- NOT_REQUIRED INSTALLED APPLICABLE APPLICABILITY_CHECK_NOT_SUPPORTED The Schedule Updates process will then commit those changes, you should verify that all is well in the OfflineServicingMgr.log file before continuing with this guide. Note: In addition to committing the changes the process then creates a backup copy of the original WIM file (with a file extension of .bak). The path to the backup file is included in the log. Below is a sample: Original image '\\cm01\Sources\OSD\OS\OSUpgradePackages\Windows10x64\1511\sources\install.wim' is backed up at '\\cm01\Sources\OSD\OS\OSUpgradePackages\Windows10x64\1511\sources\install.wim.bak' To verify that the Schedule Updates process was successful look for a line which states Schedule processing succeeded, this notifies you that all is done with the patching of the WIM file. Step 5. Create a task sequence to upgrade an operating system Now we are ready to create the actual task sequence, to do so in the ConfigMgr console do as follows: Click Software Library and expand Operating Systems, click Task Sequences. Right click and choose Create Task Sequence to start the Create Task Sequence Wizard. When the wizard appears select Upgrade an operating system from upgrade package from the list of available options as shown below: Give the task sequence a suitable name like Upgrade to Windows 10 x64 version 1511 On the Select an Operating system upgrade package step click on browse and select the Operating System Upgrade Package added (and patched) earlier, enter a product key if necessary for your version of Windows choose your software update options add any applications you want installed and continue through to completion Once created, right click on the task sequence and choose edit, observe the Check readiness for upgrade step and next review the Upgrade Operating System step, note all the options it provides If you choose the option to Perform windows setup compatability scan without starting upgrade then the task sequence will use a /Compat {IgnoreWarning | ScanOnly option with Windows setup and set a task sequence read-only variable called set a variable called _SMSTSOSUpgradeActionReturnCode with the error Windows setup error code as shown in the example below: This could be useful if you create a PowerShell script to parse the errors and log them somewhere for example in order to determine if a collection of computers is really ready for Windows 10, the downside is they have to go through the download of the operating system which takes time and disk space before actually running this step. Step 6. Add drivers to the task sequence Note: This post will not cover importing drivers into ConfigMgr, if you want to do that please refer to this post (step 2 and onwards) for a PowerShell script and manual methods to add drivers to ConfigMgr. To add driver support in the Upgrade Task Sequence for models you intend to upgrade, do as follows: In the Upgrade Operating System group add a new step called Download Package Content And give it a suitable name such as Windows 10 x64 - Microsoft HyperV depending on the hardware model you intend to support, Click on the yellow starburst and select a previously created driver package applicable to this model In the Place into the following location section choose the following: Custom Path = C:\Drivers Save path as variable = Drivers On the options tab select Add Condition, choose WMI Query and enter a query to look for your chosen hardware To identify what the model of any computer is use Powershell with the following command Get-WmiObject Win32_Computersystem Apply the changes and repeat the above process for each and every model you intend to support Next select the Upgrade Operating System step and place a checkmark in Provide the following content to Windows Setup during Upgrade and then select Staged Content and enter the following variable %Drivers01% Step 7. Deploy the task sequence At this point you are ready to start testing the task sequence. Right click it and choose Deploy, this task sequence must run within Windows so whatever collection you use should be created with that in mind... for collection choose OSD Deploy and for purpose choose Available (required is really only for the brave..., give users choice !) continue through the wizard until completion Step 8. Review it in action Note: In Progress/screenshots coming shortly, please check back for updates ! After policy is received you'll see the following in Software Center click on it for more details and click on Install to start the Upgrade Task Sequence, notice the popup and the text contained within, if you are using the 'default' software center (old style) you'll see a different popup text shown below Note: I've raised a UserVoice on this point to allow us to change the text in the popup or hide it and the task sequence from software center, you can review that here and vote too ! click on Install Operating System to start the upgrade, and off it goes.... Use CMTrace to monitor the deployment live, the log file you need to review is in C:\Windows\CCM\Logs\SMSTSLOG\smsts.log below you can see where it uses the %Drivers01% variable here's the upgrade step... and off it goes with the actual Upgrade to Windows 10 and after some time, it's completed ! Summary Microsoft continue to innovate, in System Center Configuration Manager Current Branch (version 1602) you can not only Upgrade your workstations to Windows 10 but you can ensure that they are patched with the latest available updates and installed with all applicable drivers. Related Reading A deeper look at the Upgrade task sequence in System Center Configuration Manager (Current Branch) Resolve Windows 10 upgrade errors How can I deal with languages in the Upgrade Task sequence using System Center Configuration Manager (Current Branch) Create a task sequence to upgrade an operating system in System Center Configuration Manager - https://technet.microsoft.com/en-us/library/mt613172.aspx Task sequence steps in System Center Configuration Manager - https://technet.microsoft.com/en-us/library/mt629396.aspx Manage operating system upgrade packages with System Center Configuration Manager - https://technet.microsoft.com/library/mt627916%28technet.10%29.aspx Technical details of the Windows 10 Upgrade process - https://www.sepago.com/blog/2016/05/18/windows-10-deployment-in-place-upgrade Windows 10 upgrade failure codes - https://support.microsoft.com/en-us/kb/3107983 Downloads You can download a Microsoft Word copy of this guide here dated 2016/03/31 How can I use the Upgrade Task Sequence in System Center Configuration Manager (current branch).zip You can download the PowerShell script used above here. CreateConfigMgrFolders.zip
-
you should avoid joining the virtual machine (please use virtual machines for this) to the domain at all costs, once you join a domain things happen in a computer, and group policies get applied, this will make troubleshooting problems later very difficult, can't you deploy the software during the deploy task sequence instead ?
-

Using SCCM 2012R2 how do you upgrade Windows 10?
anyweb replied to brink668's topic in Configuration Manager 2012
the only way to do that via SCCM 2012 R2SPCU3 is to use the Upgrade Task Sequence available here to upgrade Windows 10 using Software Update Management you need to upgrade to 1511 (and then 1602) -
I assume they went this path because it's a natural progression from the Intune console extensions we had with CM12, and this method also allows telemetry transfer to Microsoft so that they can improve the product going forward. As regards the 1602 option i've added a clarification of same, when i posted this article there were no updates available for Configuration Manager Current Branch.
-

Surface pro 4 does not PXE boot
anyweb replied to jack_SCCM's question in Deploying Operating Systems
boot the sp4 into windows, run a full windows update on it, then shutdown windows. Try pxe booting again, does it work ?- 29 replies
-
- Surface
- Surface pro
-
(and 5 more)
Tagged with: