-
Posts
9218 -
Joined
-
Last visited
-
Days Won
367
Everything posted by anyweb
-
We can all recognize that Microsoft licensing is not only complex, but can change at any given moment across hundreds of different products. Implementing an effective software management program is important to keep on top of these changes, avoid audits, and help save your organization tens of thousands of dollars annually by providing clear data visibility to reclaim under-utilized software licenses. Many organizations rely on manual processes and programs like Excel to track software assets with limited visibility to software usage – a time consuming and error-prone process that produces inaccurate and incomplete data. Others try to leverage Software Metering and Inventory Data within Microsoft Configuration Manager to gain insight into their assets. While a step in the right direction, this also does not provide a complete or accurate picture to optimize spend and reduce risks. Attempting to cleanse and manually normalize the raw inventory data from Configuration Manager while trying to keep up with the Microsoft Licensing rules for each product that could change at any given moment can be extremely time consuming. So how do you gain control of your Microsoft licensing? Cireson believes managing Microsoft software licensing doesn’t have to be expensive or complicated. This is why they recently released True Software Asset Management for Microsoft Licensing, a beautiful and simple solution that natively integrates with Microsoft Configuration Manager to leverage your existing investment. True Software Asset Management helps with every stage of the SAM journey, from importing and managing your asset data, to data normalization with the Global Content Library, and finally providing the ability to truly manage compliance and optimize spend with visibility to your calculated license position leveraging the License Calculation Engine. With the data you need at your fingertips, everyone in the organization can make informed decisions for Enterprise Agreement renewals, contract negotiations, as well as license reclamation and redistribution as needed. Benefits include: Automatically calculate your Microsoft license position Ensure compliance Optimize spend Normalize software data with the powerful Global Content Library Identify opportunities to reclaim under-utilized licenses Provide visibility to excess licenses Prepare for upcoming Enterprise Agreement renewals Understand license position for improved contract negotiations Leverage product use rights to reduce consumption Connect Microsoft Configuration Manager to bring in device data How True Software Asset Management can help solve Microsoft licensing challenges across your organization. No matter your job function, True Software Asset Management puts the data you need at your fingertips to reduce costs and ensure compliance of your Microsoft license estate. Take a look at some common challenges solved by role. SAM Manager Automatically calculate Microsoft license compliance Eliminate time intensive and manual product license calculations Optimize spend with an accurate, complete picture of your Microsoft license data Reduce errors from manually maintaining license entitlement data Procurement Manager Improve contract negotiations with accurate Microsoft license data Reduce spend on renewals and under-utilized applications Make informed purchase decisions with better visibility into license data Insert bullets from website IT Management Ongoing visibility to under-utilized, non-compliant and excess licenses Prepare audit defense Reduce costs of unbudgeted true-ups Forecast software needs and create annual budgets with accurate Microsoft license data Leverage your existing SCCM investment with direct integration into True SAM IT Administrator Reduce time to manage, maintain, and support your SAM solution Automatically track credentials and network access for Server applications Gain accurate, real-time reporting Schedule data import with preconfigured connectors to SCCM, Active Directory, Office 365, or CSV files Get started with a free demo today or take True SAM for a spin in the online demo lab.
-
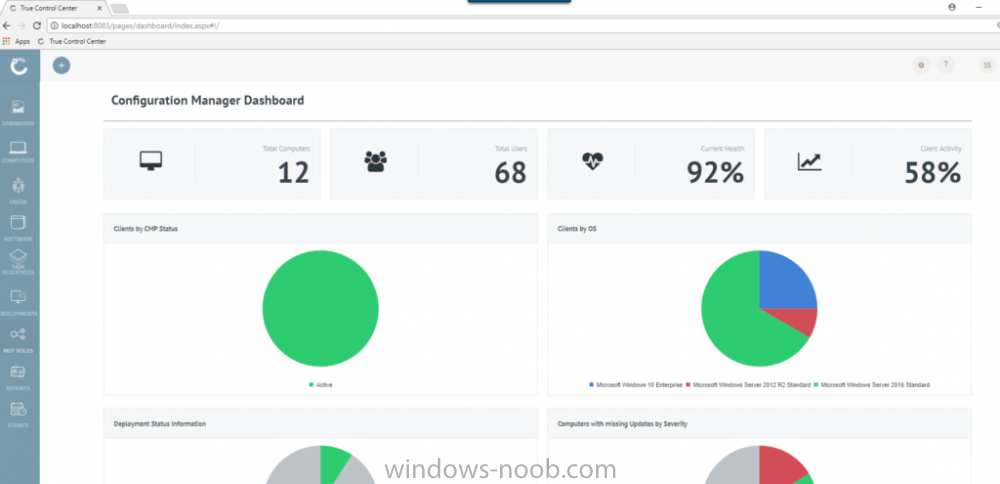
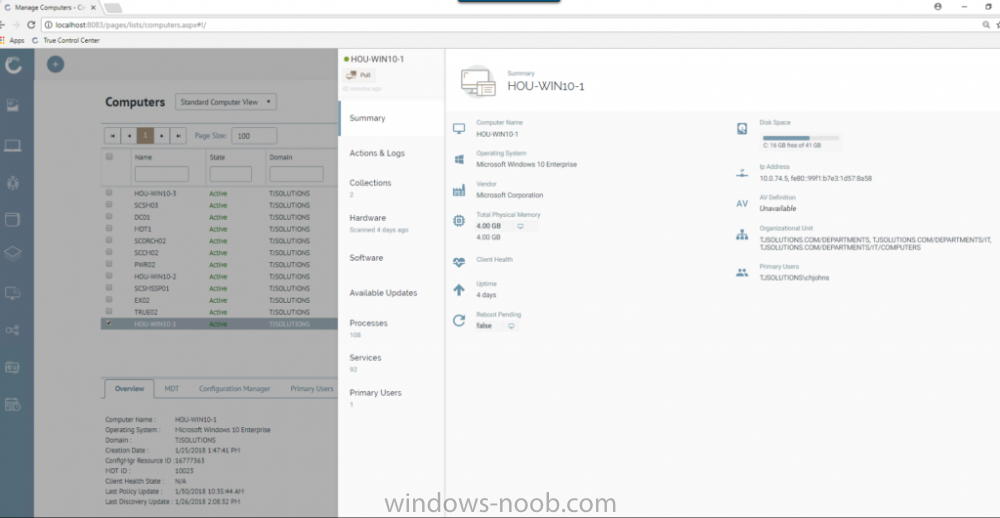
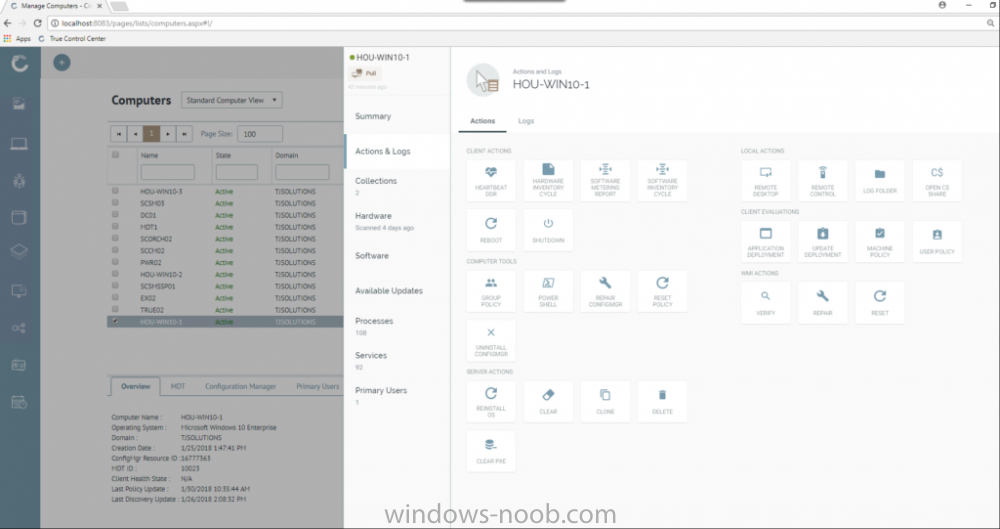
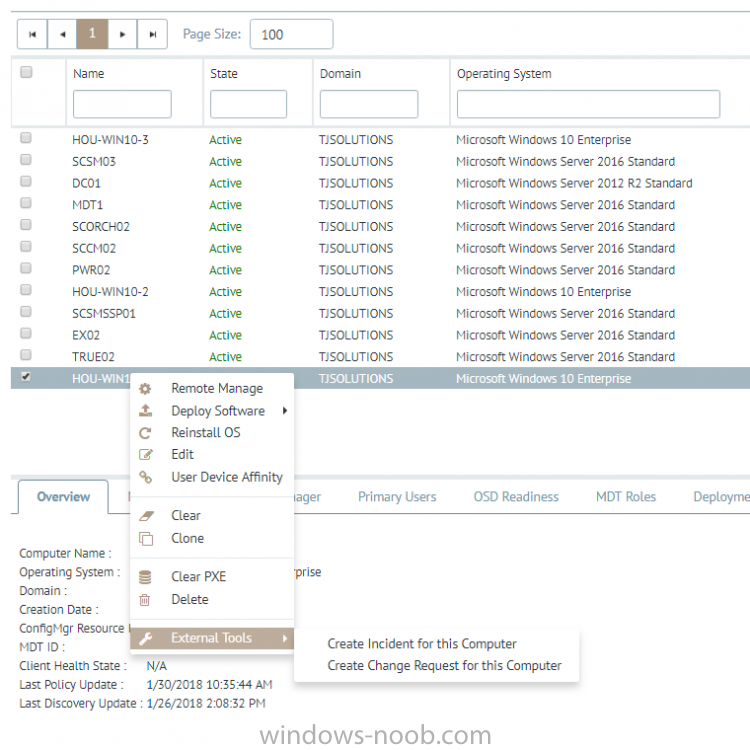
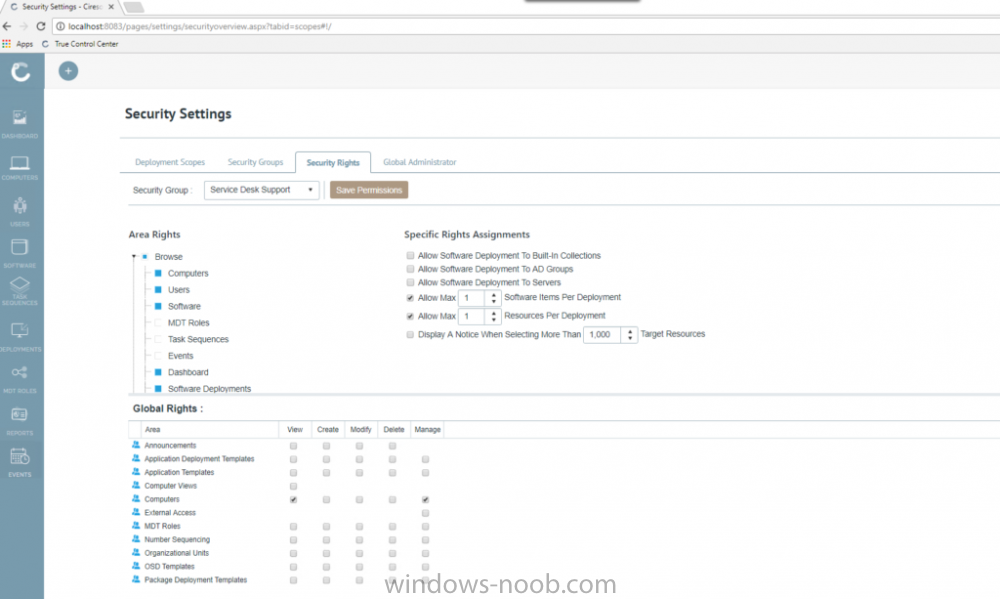
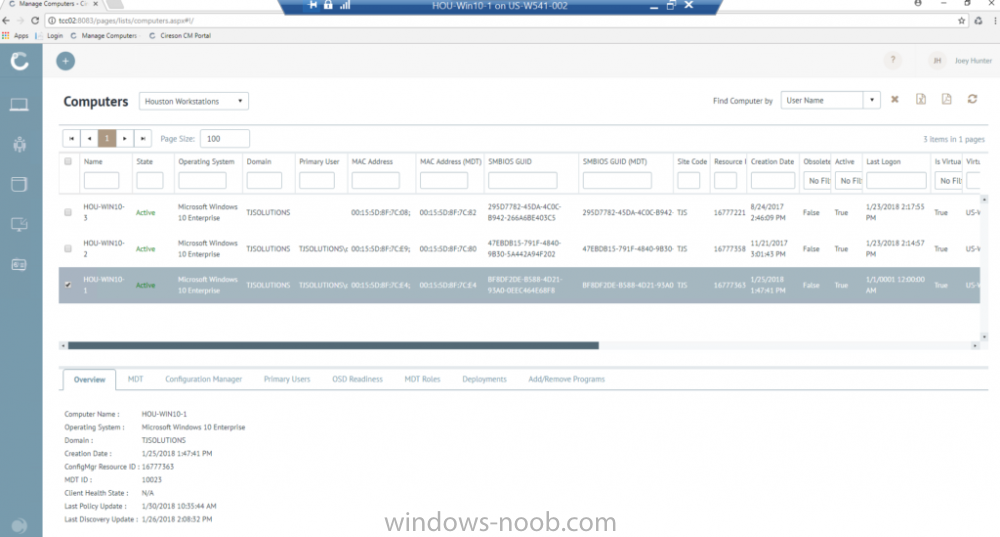
I've previously blogged about Cireson's venture into SCCM management with their excellent ConfigMgr Portal. I'm happy to report that they havn't stopped there, they've listened to feedback and built upon that product to release a new product called Cireson True Control Center and below is a blog from Billy Wilson @ Cireson. Do yourself a favor and check it out ! I know I will ! cheers niall “With great power, comes great responsibility.” I heard that in a movie once. This is a quote that Microsoft System Center Configuration Manager Admins know all too well. Configuration Manager has a lot of power to manage a company’s servers and workstations from a central point. Gone are the days of carrying around discs to put an OS or application on a workstation or server. Also having to deal with multiple versions of multiple Operating Systems at multiple patch levels (if any). Then being told by the boss right before budget time, “Go forth and view the land and tell me everything we have, where it is, and who is using it.” With my Console, I can send out standardized images and applications from the comfort of my ergonomic chair and pull information from any of several hundred reports. That’s the great power. The great responsibility comes from the fact that if I am not paying attention, I can literally bring down every server, workstation, ATM, and/or slot machine (many ATMs and slots use Windows…fun fact) in my company from that same comfortable ergonomic chair. Its happened with SCCM before. There are career-ending horror stories (Google it). So, SCCM Admins must be on the ball and careful as the ultimate accountability for any mishaps with the system lies exclusively with them. So, when the Service Desk Manager comes by and asks if we can deploy the Configuration Manager Console to his or her team because they need to get response times down and don’t want to wait for me to deploy an app or get them info on a computer, I understand where they are coming from. I was there once. However, there’s no way I am giving out that Console willingly. Setting up RBAC so that a Service Desk person doesn’t re-image the Domain Controllers isn’t a lot of fun. And if anything goes wrong, do they hammer the Service Desk person? No, they don’t. The torches and pitchforks are all aimed at…. Giving the console out to anybody who isn’t a trained Configuration Manager Admin keeps people like me awake at night. But the need is still valid and Cireson has answered the call with True Control Center. True Control Center (or TCC) is a web-based Portal that SCCM Admins can provide to other levels of IT so that they can utilize the power and utility of Configuration Manager (and then some) to make their day-to-day lives more productive. However, the Admin has the ability to easily limit and target that power and utility so that these Analysts can do only what the need to, only to the users and computers they should access, keeping the rest of the company safe and allowing the Admins to sleep better. Here are some of the key benefits and features of the True Control Center. Web Based True Control Center is a web-based Portal that is easily installed, configured, and hosted. No more deployment of the Configuration Manager Console. Access from anywhere in the company using Windows authentication. Power and Utility with Remote Manage Information can be at your fingertips. You can give your Analysts the ability to access computer data such as: Current health status Network information Uptime Hardware information Installed Applications Installed & available Software Updates Currently running processes Current status of services Status of Software and Task Sequence deployments Primary User information (if you are utilizing UDA) They can access user data such as: Active Directory information Primary Device information Status of User-based Software Deployments You can also provide access to any or all of the hundreds of out-of-the-box ConfigMgr SSRS Reports that you find relevant to the Analysts’ job responsibilities and, if that isn’t enough, export the results of views directly to Excel or PDF! And that’s just information. You can also provide Analysts the access to perform the following functions on computers remotely: Deploy Applications, Software, and Task Sequences Initiate Config Man Client actions such as Heartbeat DDR, get client policy updates and hardware and software inventory cycles Reboot or shut down Create a PowerShell remote session RDP or initiate a Config Man Remote Control session Repair or uninstall the ConfigMan client or WMI Clear or clone app deployments Add or remove computers from Collections Terminate processes or stop and start Windows services Add or remove Primary Users Add and configure MDT roles Create and manage Applications, Software, or Task Sequences Add, pre-register, or import computers into Config Man For End Users, you can give Analysts the capability to: Initiate user-based application deployments Reset or unlock their AD accounts and passwords Manage their primary devices Integrated Not only does True Control Center integrate with Configuration Manager but it can also integrate with MDT. You also have the ability to link to External Tools so that you can initiate action on other systems and pass in data, such as creating an Incident or Change Request for a computer. Peace of Mind As a Configuration Manager Administrator, True Control Center will give you the ability to provide the power and utility with mitigated risk. Access to the data and actions above are easily scoped to Analyst role via Active Director group membership. You have the power to limit what computers, users, and software that a group of Analysts can even see in their Portal using any criteria that makes sense for your organization. You can make it so that there is no possible way the someone could accidentally push and application or OS to a server or collection. The result for an Analyst group such as Service Desk could be… You can also provide Analysts templates so that they do not have to remember what settings go with which deployments. There are even templates for adding Applications and Task Sequences to Config Man through the Portal as well. We help you take the guess work out and keep the amount of training required for an Analyst to use the Portal to a minimum. Easy training and offloading tasks will help you be more productive in your day as well and that is money. The fact of the matter is… the Configuration Manager Console was designed for Admins, not Analysts. Being able to offer a safe, intuitive, and easily accessible alternative will allow you to make your Service Desk Manager’s day and maybe your average work day, a bit more peaceful. Get started with a free demo today or take True SAM for a spin in the online demo lab.
-
- sccm
- true control center
-
(and 1 more)
Tagged with:
-
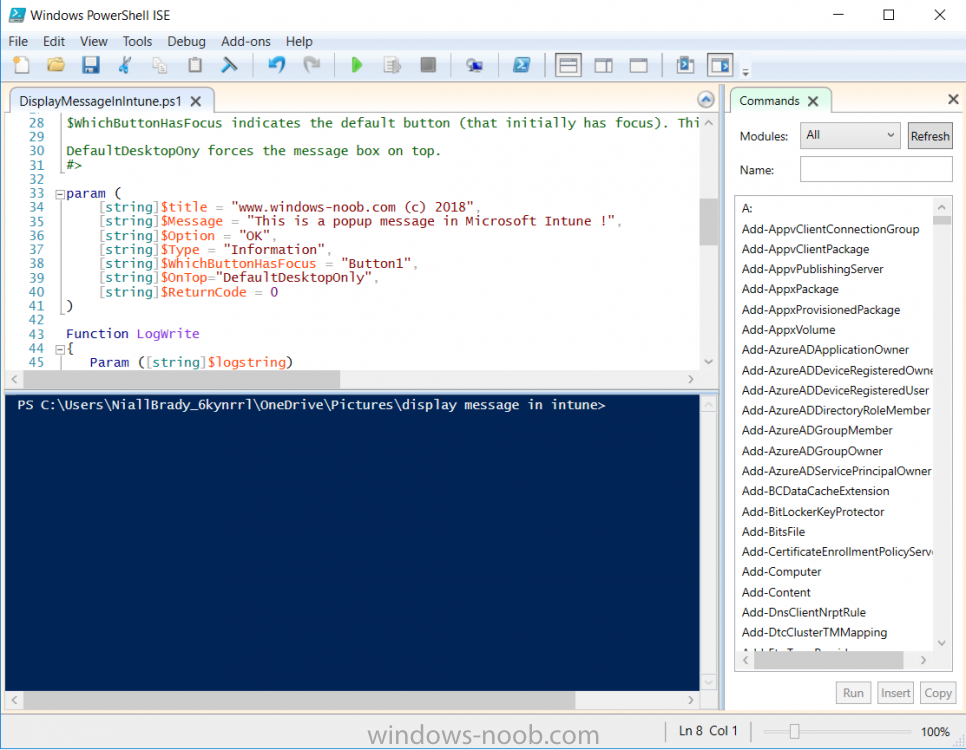
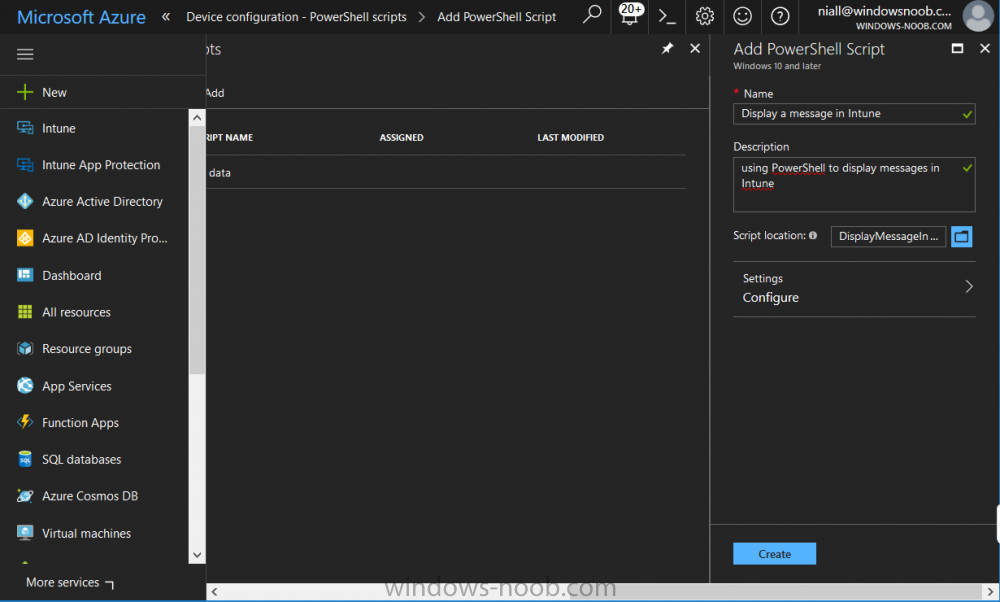
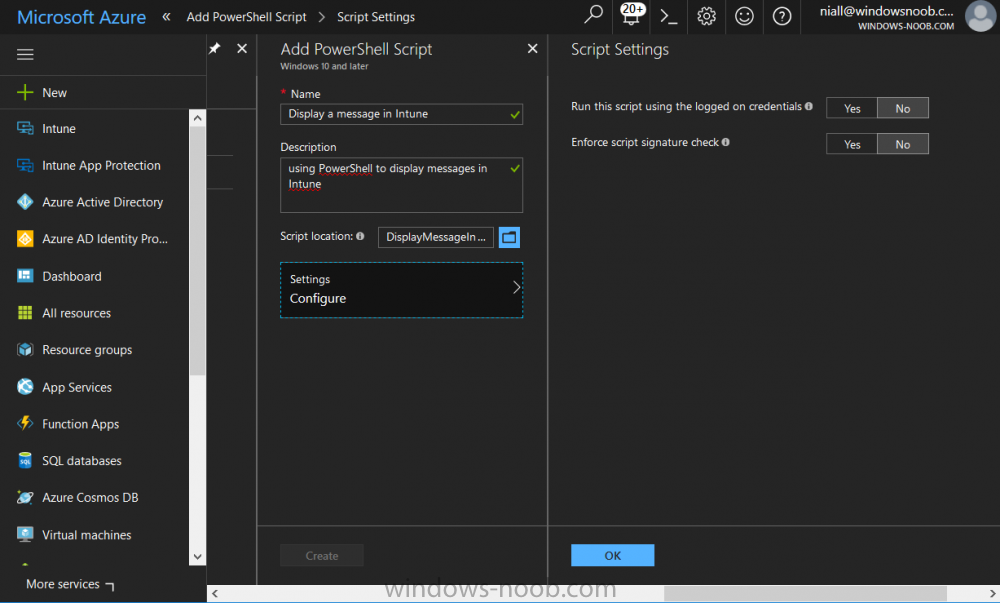
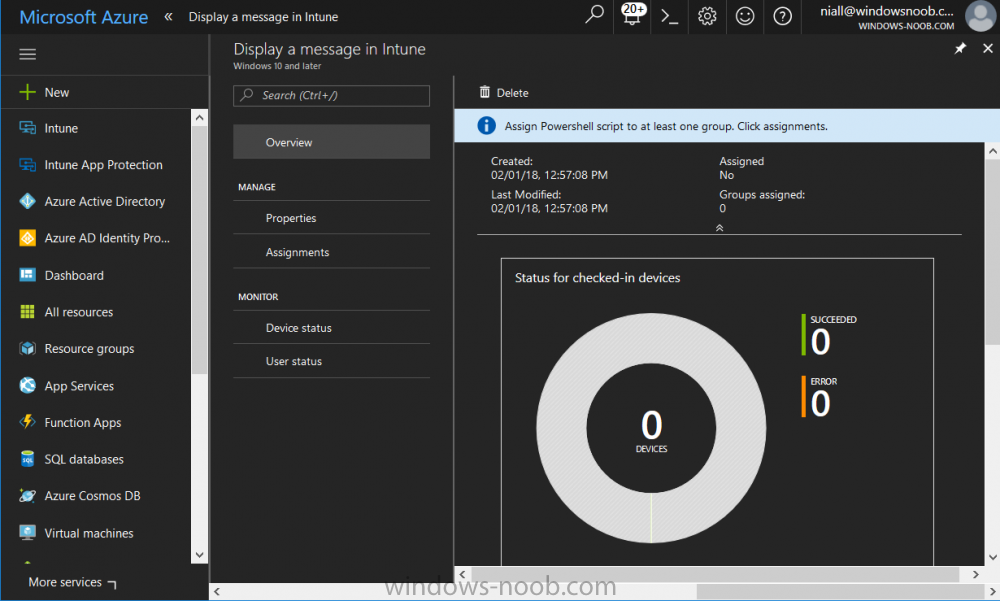
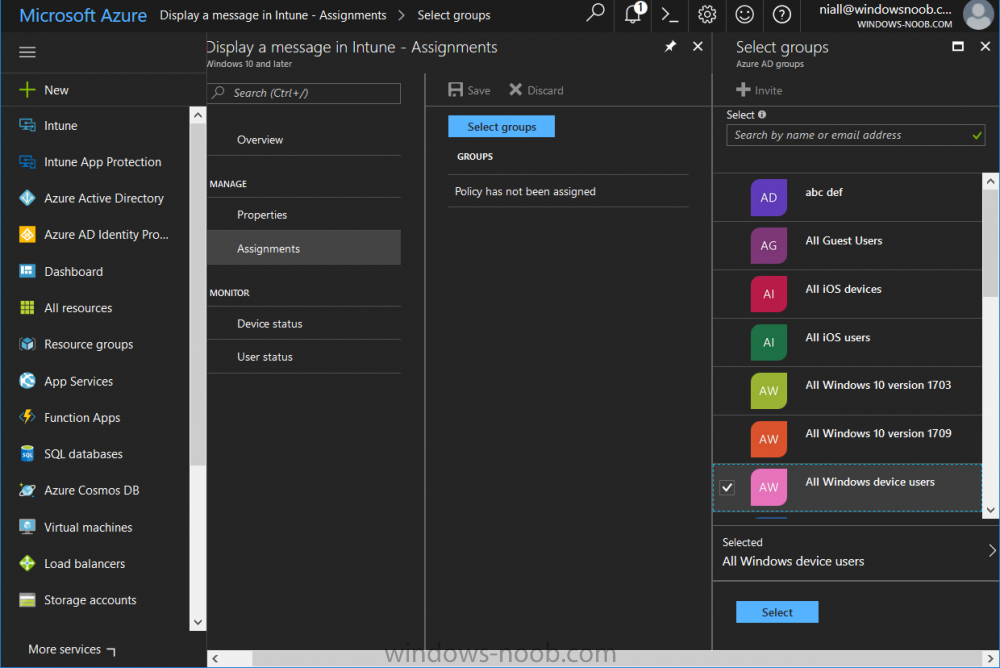
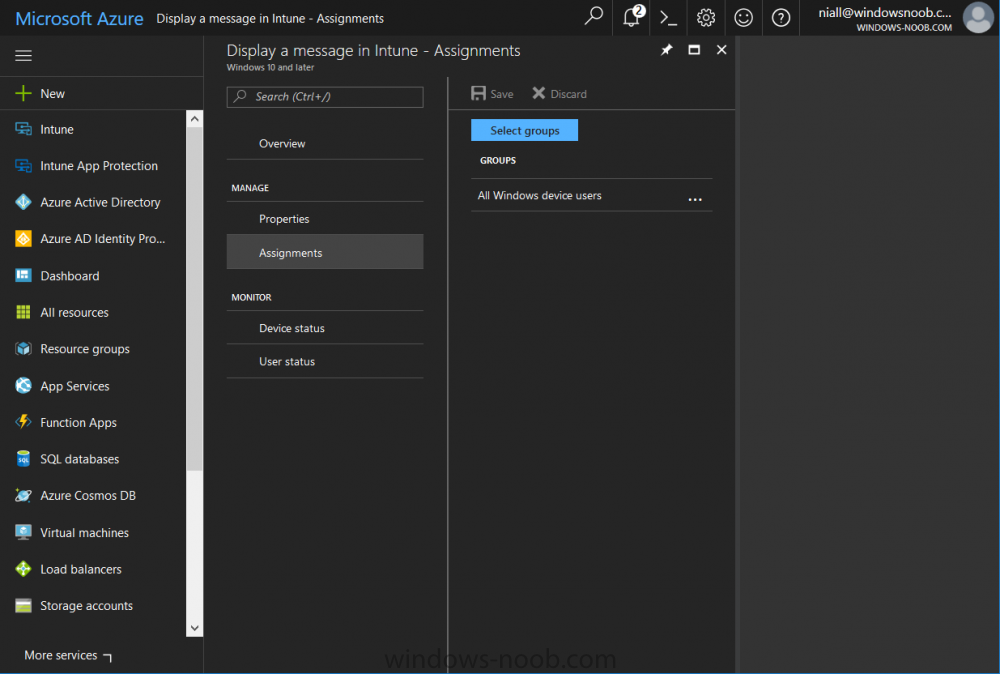
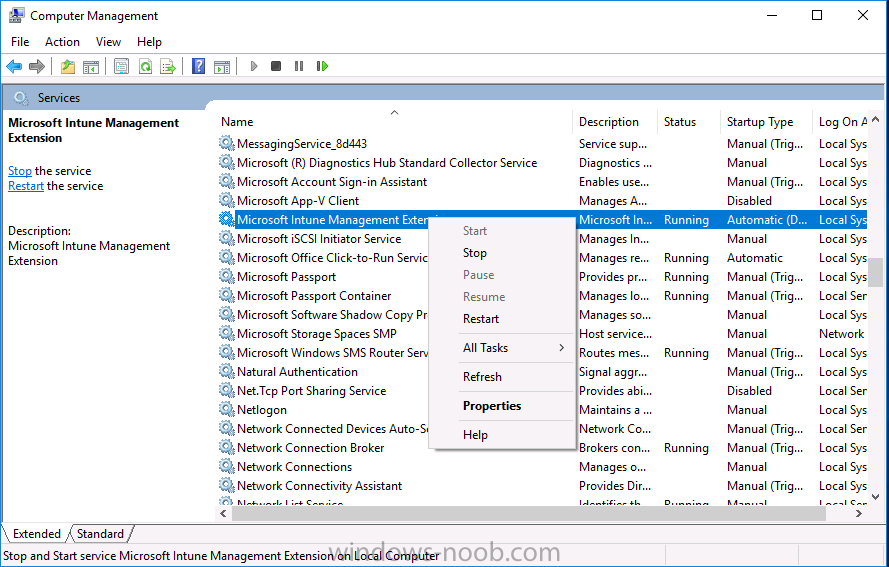
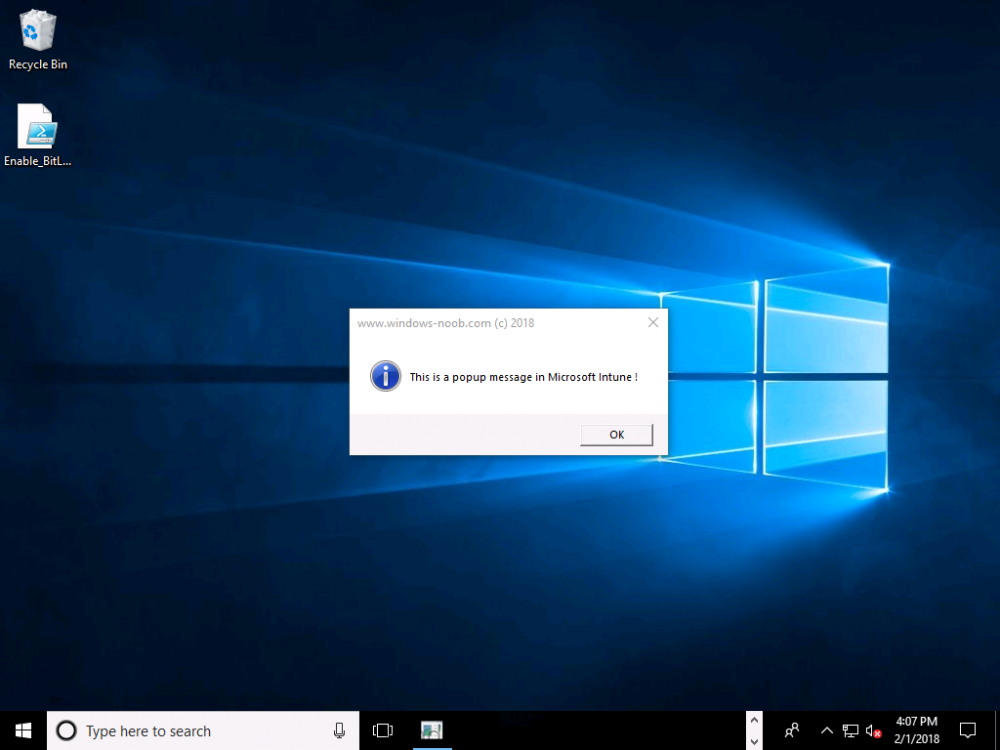
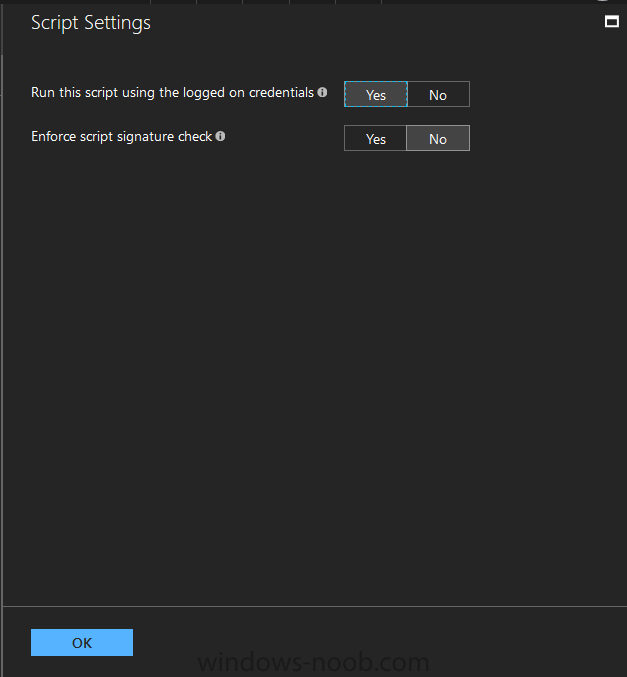
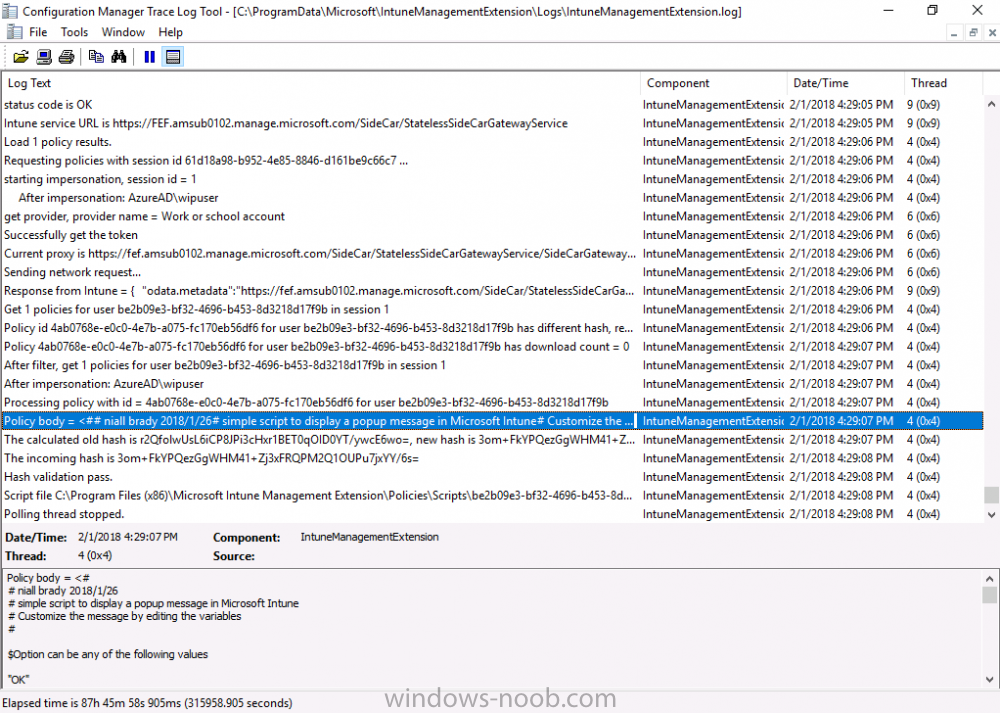
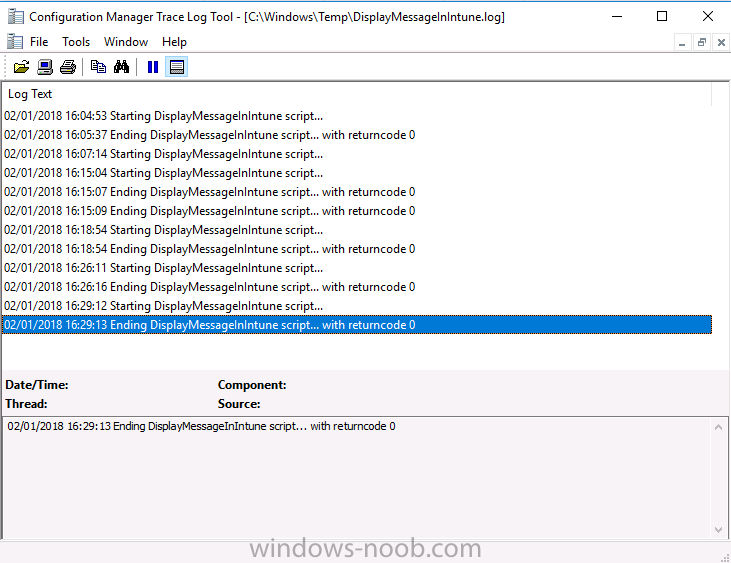
Introduction Occasionally you want to inform users about something, such as the need to update or install software, and the easiest way to do that is with some sort of a popup notification. The ability to do that in Microsoft Intune is not currently available in the product although it is a Uservoice item in progress. In the meantime however, if you need to send a notification to users of Windows devices in Microsoft Intune, it's possible using PowerShell and here's how to do it. The idea here is that you can customize the PowerShell script to deliver the message you want (and if necessary take possible actions, however you need to add your custom code to the script and it must not exceed 200KB). the screenshots below are taken on a Windows 10 version 1709 device enrolled into Intune, the device is logged on as a user with normal permissions (not an Administrator) and this was configured with Windows AutoPilot. Note: The Intune management extension which is used to run the PowerShell script has the following prerequisites: Devices must be joined to Azure AD Devices must run Windows 10, version 1607 or later Step 1. Download the script Download the DisplayMessageInIntune.ps1 script. DisplayMessageInIntune.zip Step 2. Edit the script in ISE Launch PowerShell ISE and open the extracted downloaded script. Scroll down to the following values. The values are currently set as PowerShell Parameters with the hope that the current functionality in Microsoft Intune will support Params with PowerShell scripts in the future (I've requested this ability as a DCR to Microsoft directly). If this ability does come to Intune then I will blog an update to this post explaining how to make it dynamic. When you've changed the message title and message body, you might also want to change the Type and Option available to the user, below are the values you can configure. $Option can be any of the following values "OK" "OKCancel" "AbortRetryIgnore" "YesNoCancel" "YesNo" "RetryCancel" $Type can be any of the following values "Asterisk" "Error" "Exclamation" "Hand" "Information" "None" "Question" "Stop" "Warning " Finally after line 69 you can add any additional code you want, for example to check what key was pressed etc. Step 3. Upload the script to Microsoft Intune In the Intune service in Azure select Device Configuration and click on PowerShell Scripts. In PowerShell scripts, click on Add. Enter the following values: Name: "Display a message in Intune" Description: "Using PowerShell to messages in Intune" Script location: DisplayMessageInIntune.ps1 Next click on Settings, Configure to see the options available, Change the first option so that the script runs with the same permissions as the logged on user. Click OK when done and then click on Create to create the PowerShell script in Intune. Next click on Assignments to assign the PowerShell script to a Group of Users. To do that, click on Select Groups and then select a Group of Users that you'd like to assign this to. Next click on Save to save this group. Step 4. Review what happens on a Windows device On a Windows device, logon using the credentials of a user that is in the selected group that you assigned the PowerShell script to. Tip: You can restart the Microsoft Intune Management Extension service (as a user account with Administrator permissions) rather than wait one hour for that extension service to run the PowerShell script. Note: Your users don't need to do the service restart, this is just so you get instant gratification and can review the end-result. After the policy is received the message popup is displayed on top of all windows. result ! Troubleshooting You can review 2 logs files, one is the log file for Microsoft Intune Management Extension: C:\ProgramData\Microsoft\IntuneManagementExtension\Logs\IntuneManagementExtension.log and the other is generated by the PowerShell script itself: C:\Windows\Temp\DisplayMessageInIntune.log Note: If you want to display the message to a user in SYSTEM context then download serviceUI.exe from the MDT toolkit and launch powershell with that exe, like so... and create a Win32 App instead of using a PowerShell script option. ServiceUI.exe -process:explorer.exe %SYSTEMROOT%\System32\WindowsPowerShell\v1.0\powershell.exe -NoProfile -WindowStyle Hidden -ExecutionPolicy Bypass -File DisplayMessageInIntune.ps1 Recommended reading https://docs.microsoft.com/en-us/intune/intune-management-extension https://oliverkieselbach.com/2017/11/29/deep-dive-microsoft-intune-management-extension-powershell-scripts/ https://www.petervanderwoude.nl/post/combining-the-powers-of-the-intune-management-extension-and-chocolatey/
-

UPGRADE SEQUENCE 1709 WINDOWS 10
anyweb replied to kcumbie8's question in Deploying Windows 10, Windows 8.1, Windows 7 and more...
interesting and thanks for sharing but we found out the issue, it's related to DMA as described in these links, so a GPP will solve it for now https://blogs.technet.microsoft.com/secguide/2018/01/18/issue-with-bitlockerdma-setting-in-windows-10-fall-creators-update-v1709/ https://support.microsoft.com/en-gb/help/4057300/devices-not-working-before-log-on-a-computer-running-windows-10-1709 -

Configuring BitLocker in Intune - Part 2. Automating Encryption
anyweb replied to anyweb's topic in Microsoft Intune
ok got it and replied -

Configuring BitLocker in Intune - Part 2. Automating Encryption
anyweb replied to anyweb's topic in Microsoft Intune
no email received ! who did you send it to ? -

Configuring BitLocker in Intune - Part 2. Automating Encryption
anyweb replied to anyweb's topic in Microsoft Intune
can you do a teamviewer session with me so i can troubleshoot it ? -

Configuring BitLocker in Intune - Part 2. Automating Encryption
anyweb replied to anyweb's topic in Microsoft Intune
it worked for me ! and according to your log it worked for you too, how did you test it exactly ? I tested using a windows autopilot enrolled device that had regular user permissions (not local admin) did you modify the script in any way ? -

Preparing for 1710 upgrade
anyweb replied to simulacra75's topic in System Center Configuration Manager (Current Branch)
it wont be overwritten, it'll still be there, but you won't be able to service it in the console, instead you can use dism to add remove drivers etc to it. -
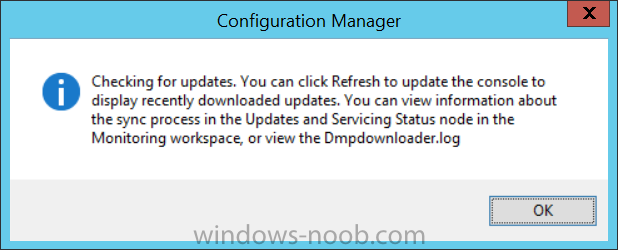
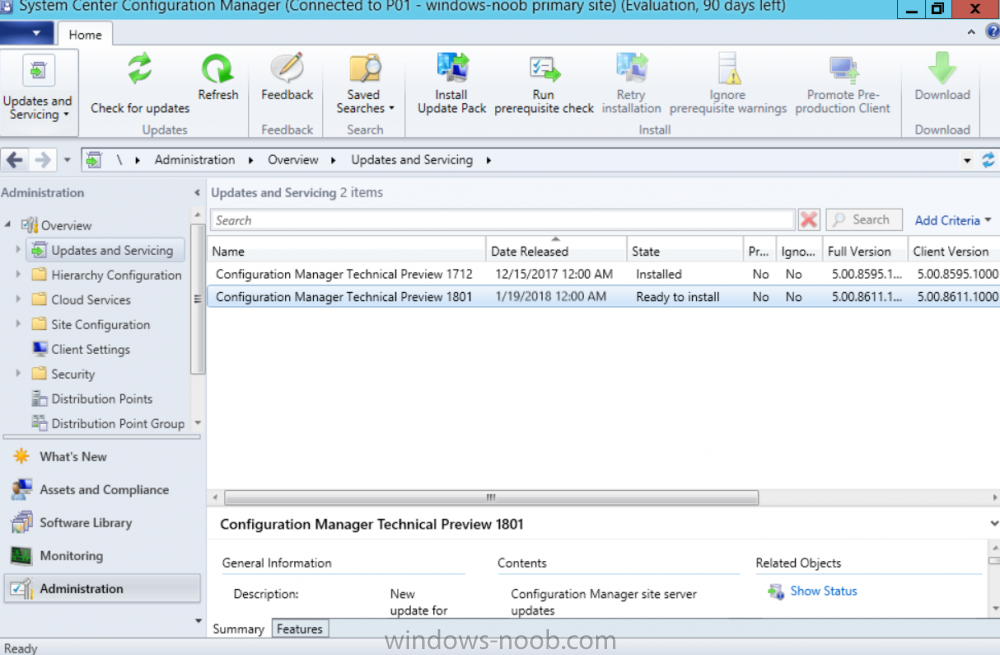
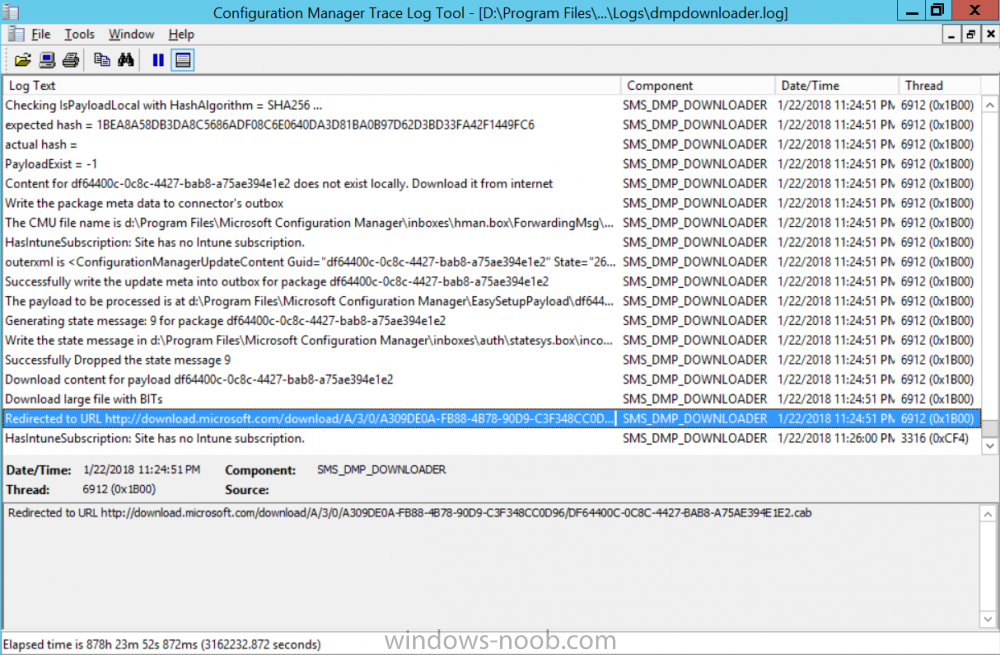
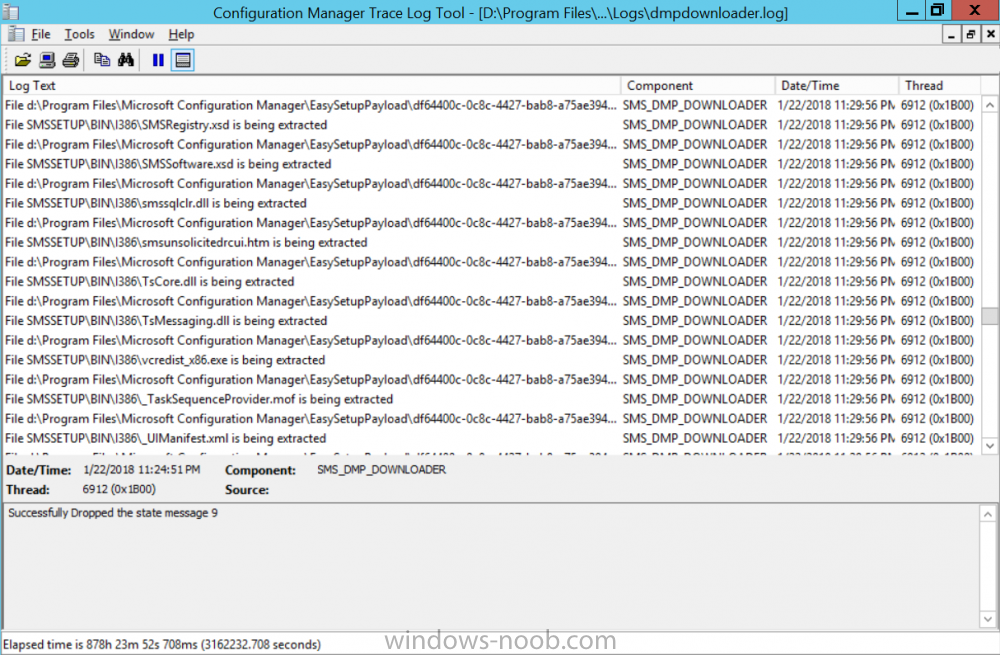
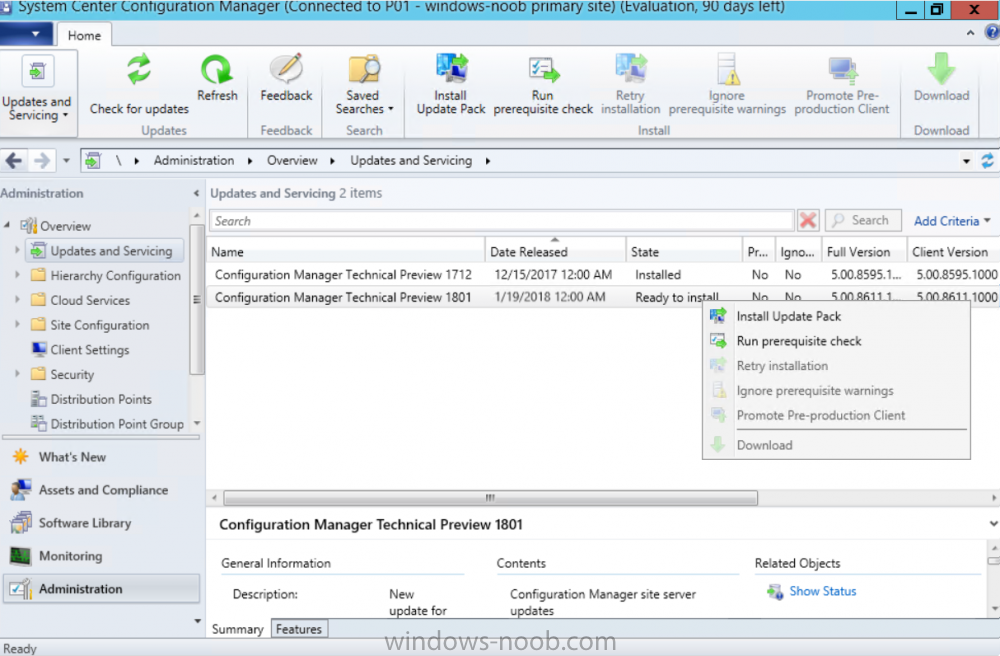
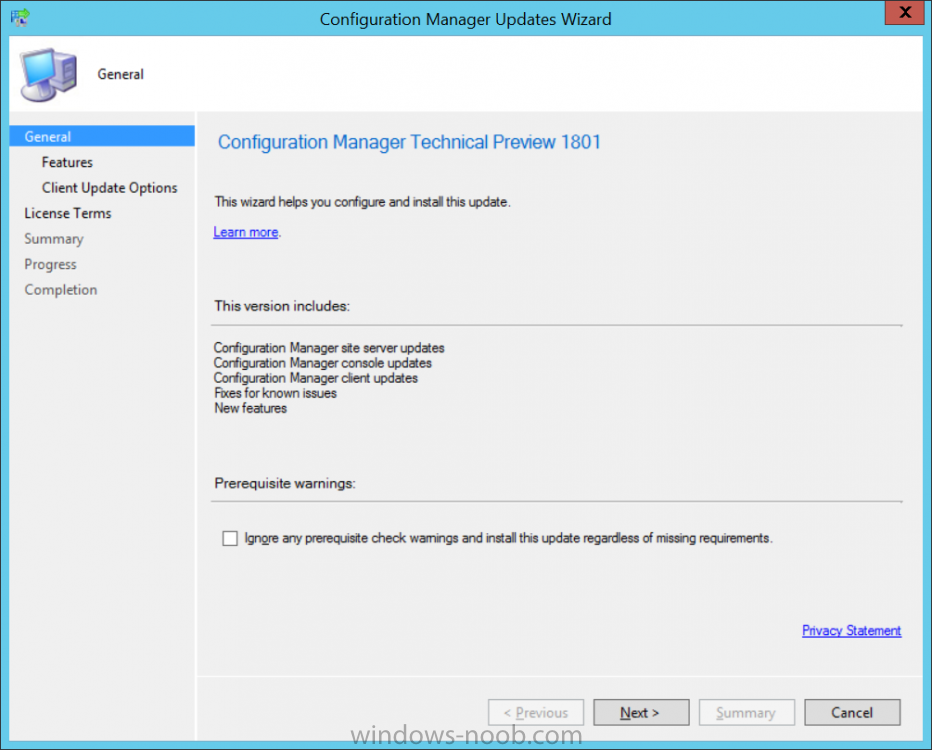
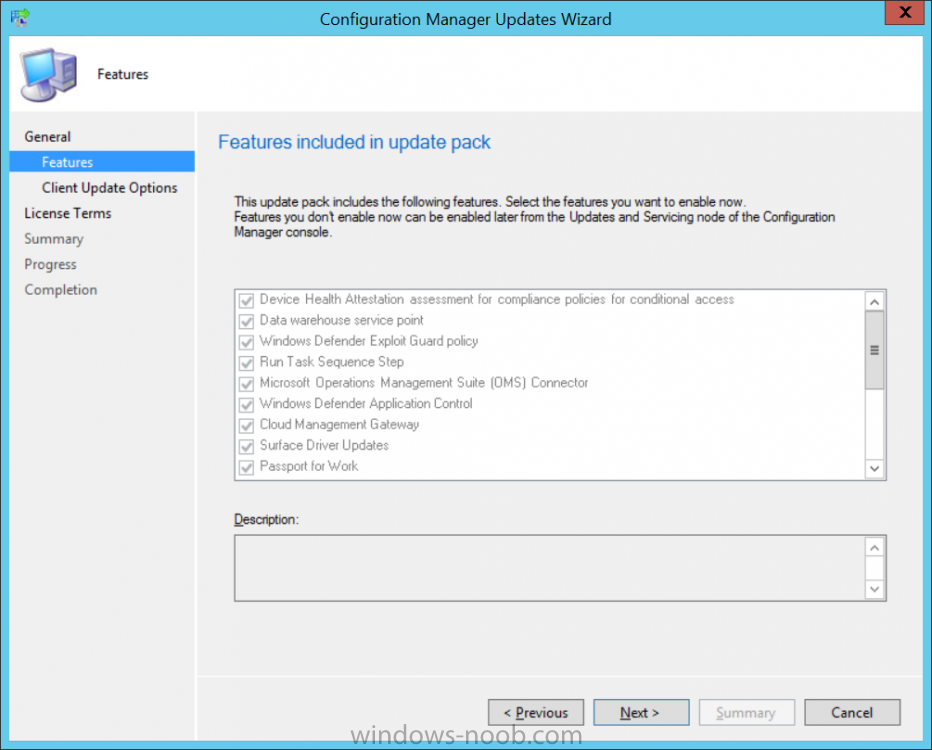
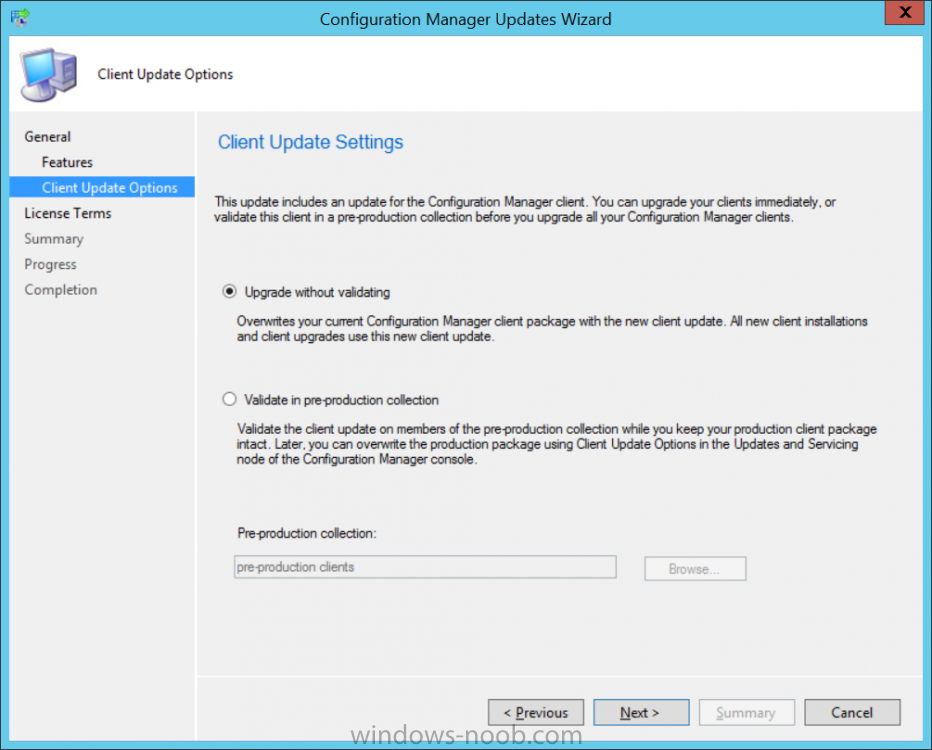
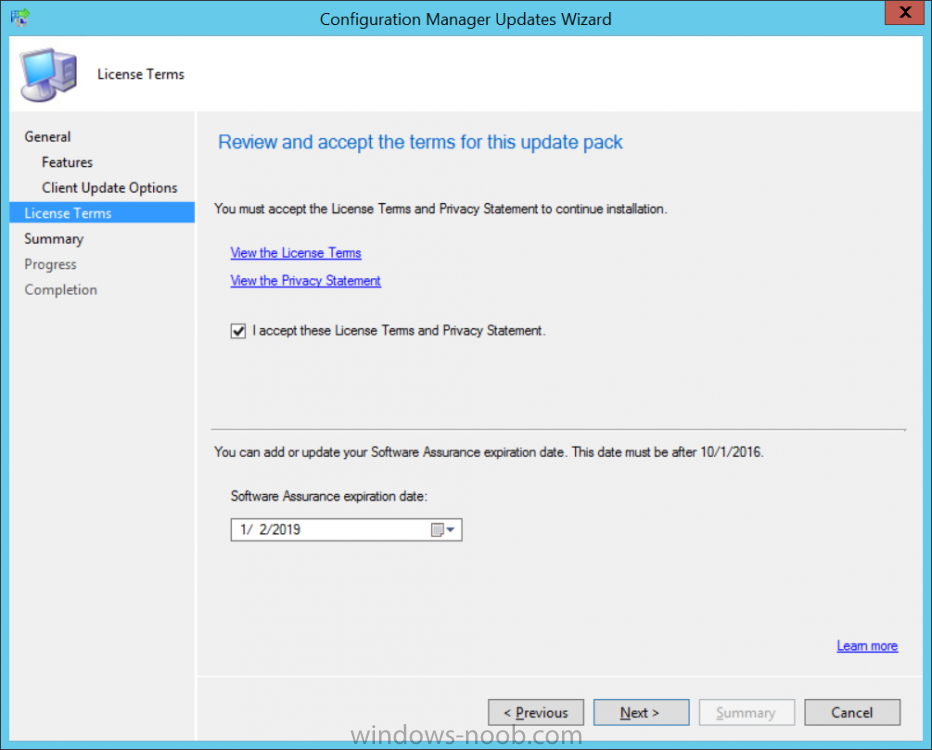
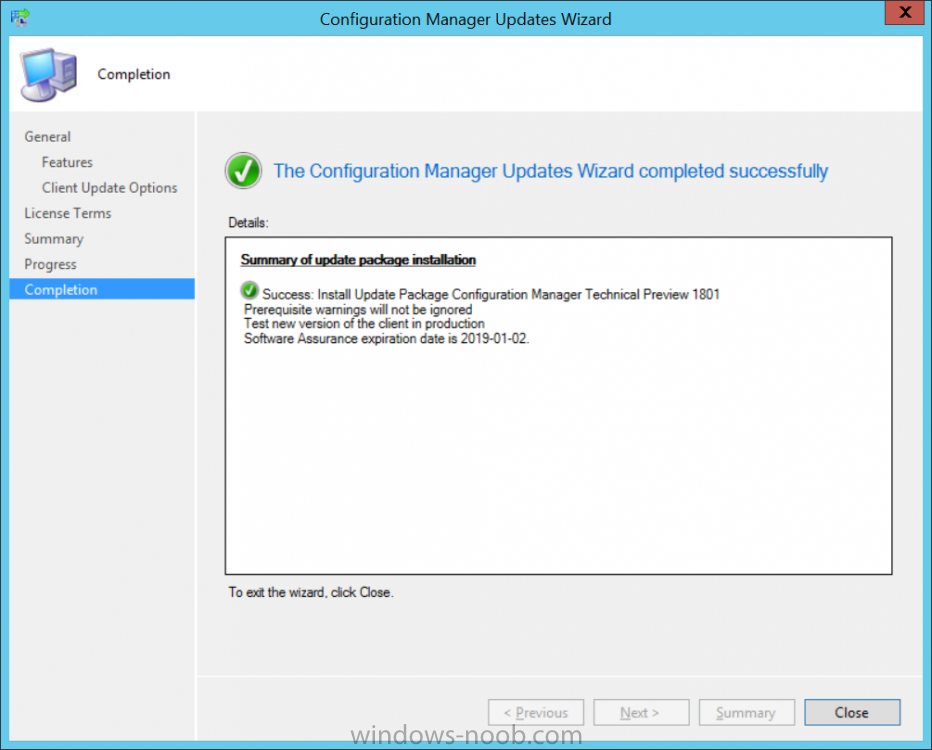
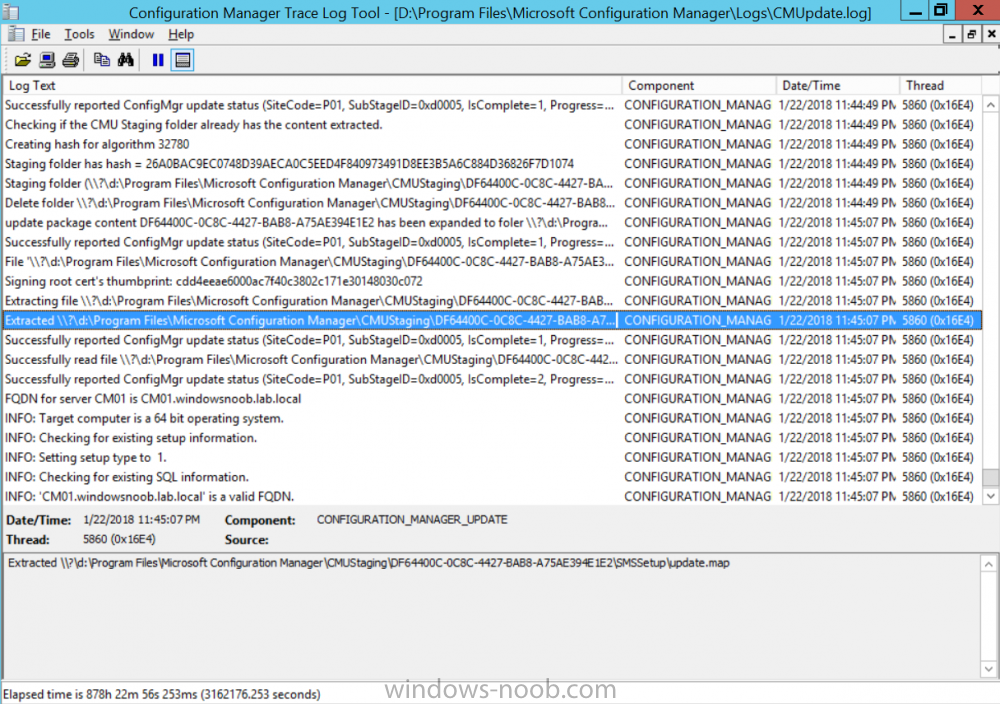
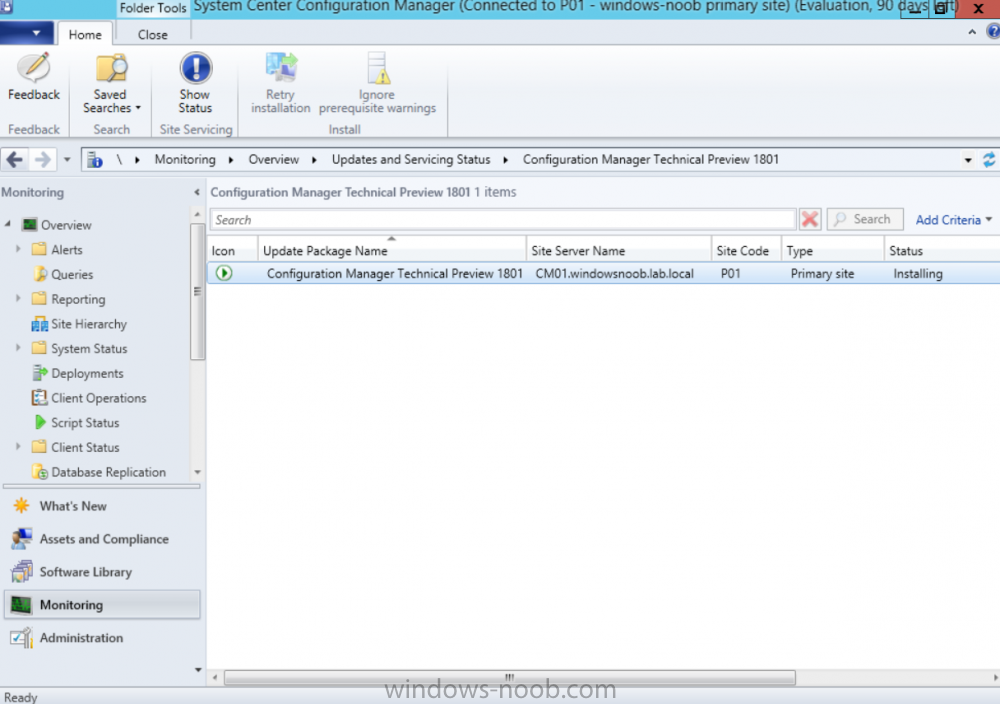
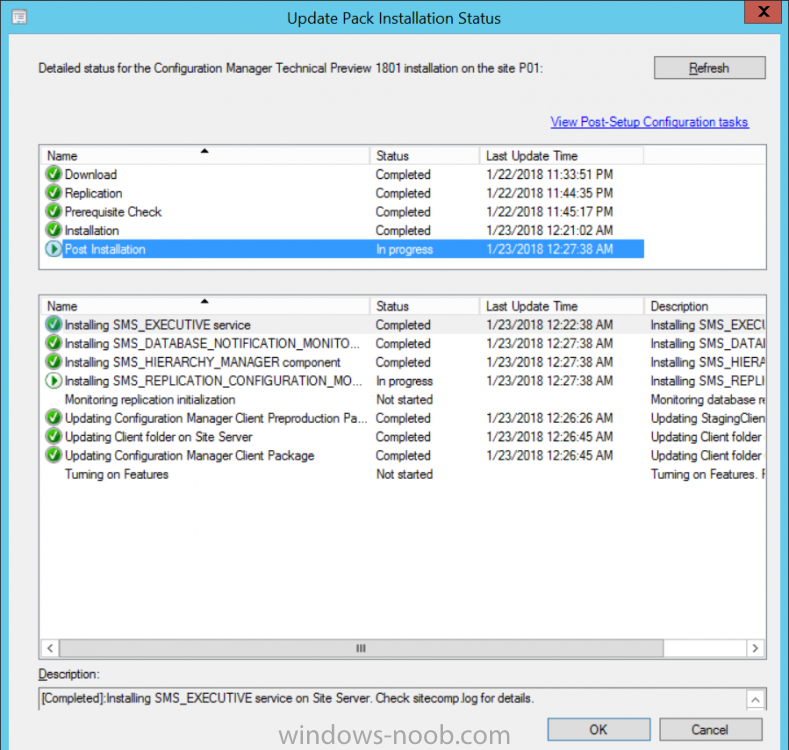
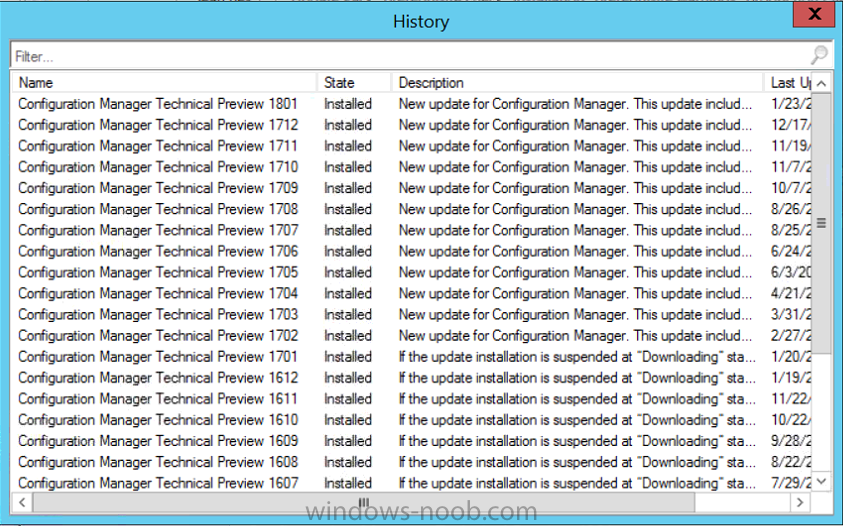
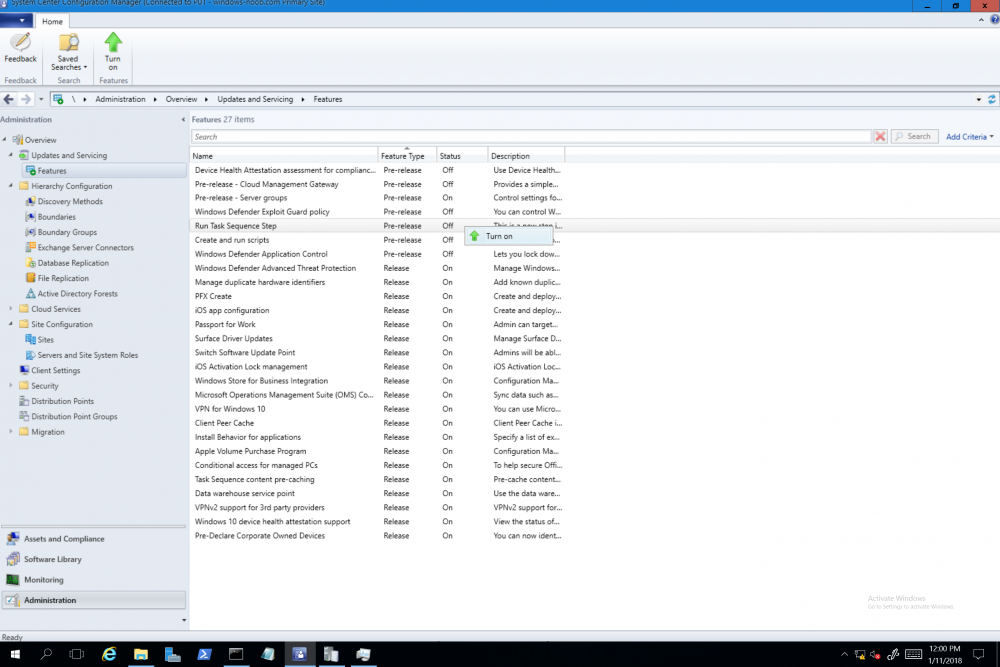
Introduction Microsoft have released the latest Technical Preview release of System Center Configuration Manager namely System Center Configuration Manager Technical Preview 1801. There are two main versions (of Configuration Manager) available: System Center Configuration Manager (Current Branch) System Center Configuration Manager (Technical Preview) System Center Configuration Manager (Current Branch) is designed for use in production, for managing anything from small to very large Enterprises whereas System Center Configuration Manager (Technical Preview) is for lab environments only and is limited to 10 clients. The Technical Preview releases are released monthly, and contain the latest and greatest features being trialed in the product, and usually these new features are the result of feedback from uservoice. Current Branch releases on the other hand are released only a few times per year and contain stable, tested features that are mature enough to release into production environments. System Center Configuration Manager Technical Preview 1801 is now available. This release offers the following new features: Run Scripts – You can now import and run signed scripts and monitor the script results. Moving Distribution Points between sites – You can now move an eligible distribution point from one primary site to another primary site or from under a secondary site to a primary site . For information about requirements for moving a distribution point see “Reassign Distribution Point”. Improvements to client settings for Software Center – Client settings for Software Center now has a customize button where you can preview your customizations before deploying them to machines. You can also hide unapproved applications in Software Center. New settings for Windows Defender Application Guard – For Windows 10 version 1709 and later devices, there are two new host interaction settings for Windows Defender Application Guard. Websites can be given access to the host’s virtual graphics processor and files downloaded inside the container can be persisted on the host. Co-management reporting – You can now view a dashboard with information about co-management in your environment. Phased Deployments – You can use phased deployments to automate a coordinated, sequenced rollout of software without creating multiple deployments. Support for hardware inventory strings greater than 255 characters in length – For newly added classes, you can specify string lengths greater than 255 characters for hardware inventory properties that are not keys. This release also includes the following improvements based on your feedback from UserVoice: Improvements to Automatic Deployment Rule evaluation schedule – You can now schedule Automatic Deployment Rule evaluation to be offset from a base day. Update 1801 for Technical Preview Branch is available in the Configuration Manager Technical Preview console. For new installations please use the recently updated 1711 baseline version of Configuration Manager Technical Preview Branch available on TechNet Evaluation Center. We would love to hear your thoughts about the latest Technical Preview! We’re now enabling Configuration Manager feedback through the Feedback Hub app built-in to Windows 10. When you Add new feedback be sure to select the Enterprise Management category and then choose from one of the following subcategories: Configuration Manager Client Configuration Manager Console Configuration Manager OS Deployment Configuration Manager Server Installing this release So how do you get Technical Preview installed ? There are two methods: Upgrade from a previous installation of Technical Preview (as shown in this guide). Do a clean install of Technical Preview 1703 (the latest TP baseline) by using the following guide and replace the base version in that guide with the TP1703 release and then upgrade. Upgrading to this release Once you have a Technical Preview release installed, in the Configuration Manager console browse to Administration, Overview, Updates and Servicing as shown below. Click on Check for Updates (in the ribbon) Next, click on the OK button. After refreshing the console, you can see the update is available, then start downloading, and once it is downloaded the state will change to Ready to Install. As instructed, if you want more details about what’s happening, you can read the DMPDownloader.log available in <drvletter>:\Program Files\Microsoft Configuration Manager\Logs, you can use CMTrace to do so. Once downloaded, the content will be extracted to the EasySetupFolder. Installing the update Right click the update and choose Install update pack. A wizard appears. Click Next. the Features included in the update pack will be listed. Select your client update settings and click Next accept the EULA and configure the software assurance expiration date and click through to the completion Monitoring the Upgrade At this point you should monitor the CMUpdate.log available in <drvletter>:\Program Files\Microsoft Configuration Manager\Logs, you can use CMTrace to do so. This log will detail the installation of the update pack. You should also pay attention to the following log files present in the root of C:\. CompMgrProv.Log ConfigMgrPrereq.log ConfigMgrSetup.log and after refreshing the console, the state of the update pack will change to Installing. Clicking on Show Status will give you detailed info about the state the Installation is in, it is broken down into 5 distinct phases in the top pane: Download Replication Prerequisite Check Installation Post Installation Selecting a phase will highlight what state the update is in, including what (if any) problems it has. And after a while it should progress through to the Post Installation phase, And after refreshing the console you’ll be informed that a new version is available namely version 5.1802.1050.1000. and after a while the new console is installed. After Installing this version, you can check your Upgrade history by navigating to the Updates and Servicing node, and clicking on History in the ribbon. Recommended reading Capabilities in Technical Preview 1801 for System Center Configuration Manager – https://docs.microsoft.com/en-us/sccm/core/get-started/capabilities-in-technical-preview-1712 Update 1801 for Configuration Manager Technical Preview Branch – Available Now! – https://cloudblogs.microsoft.com/enterprisemobility/2018/01/22/update-1801-for-configuration-manager-technical-preview-branch-available-now/
-
You may have already seen Part 2 of this series where you can automate BitLocker encryption in Intune using supplied MSI's, which contain logging, reboot prompt and other features. I've put together this video to show you how you can test the PowerShell scripts contained within the two MSI's here. This allows you to test the scripts outside of Intune, and when you are happy with the results you can re-package them and deploy the MSI via Intune. The video shows you how to use Psexec to start a process (in this example it's CMD.EXE) as SYSTEM. psexec.exe /s /i cmd.exe After starting the cmd prompt as SYSTEM, you can launch powershell. Next, browse to the folder where the scripts are, by default it's C:\Program Files (x86)\BitLockerTrigger and launch Enable_BitLocker.ps1. After the TriggerBitlocker msi is installed by Intune on a Windows AutoPilot enrolled device, the PowerShell script will run via the Scheduled Task as SYSTEM, so this method of testing is a valid way to verify any changes you add to the PowerShell script before repackaging it as an MSI. To see the video click below, have a look and happy troubleshooting. cheers niall
-

Configuring BitLocker in Intune - Part 2. Automating Encryption
anyweb replied to anyweb's topic in Microsoft Intune
it's working now, and i've added the updated USER msi to the original blogpost, please download and test, it works fine for me you can see a video of how to test it yourself outside of Intune, here cheers niall -
Introduction Yesterday I needed to deploy a new Windows 10 version 1709 Virtual Machine using Windows AutoPilot, with a user that did not have Administrative permissions on that Virtual Machine, so I created the profile in Windows AutoPilot in the Microsoft Store for Business and reset my virtual machine. After working my way through the Windows AutoPilot OOBE (out of box experience) screens, I was presented with a “Something went wrong” error shown below. This error can occur just after entering your password and should be the point where the device is setup and auto enrolled into MDM (if you have that option enabled and have Azure AD Premium). I decided to document the things I needed to check in order to resolve the issue to help others with the same problem. Thanks go to Per Larsen for pointing me in the right direction. Step 1. Check that the user has the correct license requirements For Auto-enrollment into MDM you need an Azure Ad Premium license, so I wanted to verify that the user in question was licensed appropriately. To do so, open https://portal.azure.com and open the Intune service, click on Users and select the username you wish to verify. The username used for this blog post was wipuser@windowsnoob.com. Next, click on Licenses in the left column. The Licenses available to the user are shown on the right blade along with a count of Enabled services. To drill down further, click on the Enterprise Mobility + Security E5 license. Details of the services enabled within that license are shown. So based on the above, you can see that the user is licensed for Azure AD Premium and Intune A direct so this is not a licensing issue. Step 2. Check the Device limit setting in Azure AD Note: Azure AD maximum devices controls Azure AD device registration, not MDM enrollment. Azure AD registration and MDM enrollment are two separate features controlled by two separate products. Not every MDM enrollment requires Azure AD registration and vice-versa. That said Windows AutoPilot does require Azure AD join, so it's a good idea to verify this setting prior to continuing your troubleshooting. You can set a limit on the number of devices users can enroll, to verify the current setting open the Azure Active Directory service and click on Devices then click on Device Settings. Look at the value stored in Maximum number of devices per user. The value is 20 which is an adequate number of devices that the user can have in Azure. Step 3. Check the number of devices the user has already enrolled Next, you should verify the number of devices the user in question has enrolled already. To do so, in the Intune service click on Users, select the username and then click on Devices. As you can see the user has already enrolled one device, and it’s well below the 20 max limit so you can determine that is not the issue. Step 4. Check if the user is in scope for MDM Next, verify that the user is actually in scope for MDM. To do so, in Azure Active Directory click on Mobility (MDM and MAM), select Microsoft Intune. In this example you can see that the MDM scope is set to Some, and that includes the following User Group All Windows Device Users. So next you need to verify that the user is in that User Group. And to do that in the Intune service click on Groups, then All Groups, select the group in question and search or locate your user in that group. And the user is present in the group so that is not the issue. Step 5. Check if the user is in scope for Azure AD Join To verify that the user can join devices into Azure AD, open the Azure Active Directory service and click on Devices then click on Device Settings. Look at the value stored in Users may join devices to Azure AD, it can be one of the following three options All Selected None In this example it is Selected and the User Group in question can be viewed by clicking on 1 member selected. The user group in this example is called Allowed Azure Ad Join. By clicking on the user group and then clicking on Members you can see what users are in that user group. From the above you can see that the user is NOT in this user group. To resolve the ‘something went wrong’ error, click on +Add members and select the user in question, then click on Try again on the Windows device. Step 6. Check for Enrollment restrictions In the Intune service click on Device Enrollment, then enrollment Restrictions and look at the settings for Device Limit Restrictions. In this case it's 15 which is more than the user has listed under their Devices. You can also review the Device Type restrictions however the Windows operating system is not listed as of 2017/1/16. Summary Sometimes when things go wrong and you get a message that tells you what the problem is, requires you to do some digging and verification in order to resolve. There may be other things that can generate the above error, if so let me know and I’ll add them.
-

Configuring BitLocker in Intune - Part 2. Automating Encryption
anyweb replied to anyweb's topic in Microsoft Intune
hi Nielsvd I'll have to test it in my lab and come back to you, so that's what i'll do now... -

Configuring BitLocker in Intune - Part 2. Automating Encryption
anyweb replied to anyweb's topic in Microsoft Intune
hi Nielsvd I created two msi's did you use the user based msi ? -
please re-download the main scripts and tell me is it working as designed
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
thanks for checking, i've now updated the main script with the fix
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
yup that's it ! mystery solved If objSysInfo.RebootRequired = "False" then i've rewritten it, it's a boolean operator, please try this code instead If objSysInfo.RebootRequired = False then does it work ? checkreboot.vbs
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
if you want to host the SUP on the standalone server then you'll still need to install WSUS, otherwise if you host the SUP role elsewhere or if you don't intend to manage software updates you are ok The software update point is required on the central administration site and on the primary sites in order to enable software updates compliance assessment and to deploy software updates to clients. The software update point is optional on secondary sites. The software update point site system role must be created on a server that has WSUS installed. The software update point interacts with the WSUS services to configure the software update settings and to request synchronization of software updates metadata. When you have a Configuration Manager hierarchy, install and configure the software update point on the central administration site first, then on child primary sites, and then optionally, on secondary sites. When you have a stand-alone primary site, not a central administration site, install and configure the software update point on the primary site first, and then optionally, on secondary sites. Some settings are only available when you configure the software update point on a top-level site. There are different options that you must consider depending on where you installed the software update point. via > https://docs.microsoft.com/en-us/sccm/sum/get-started/install-a-software-update-point