-
Posts
9255 -
Joined
-
Last visited
-
Days Won
371
Everything posted by anyweb
-
what version of the sccm client are you using ?
- 5 replies
-
- feature update
- sccm
-
(and 3 more)
Tagged with:
-
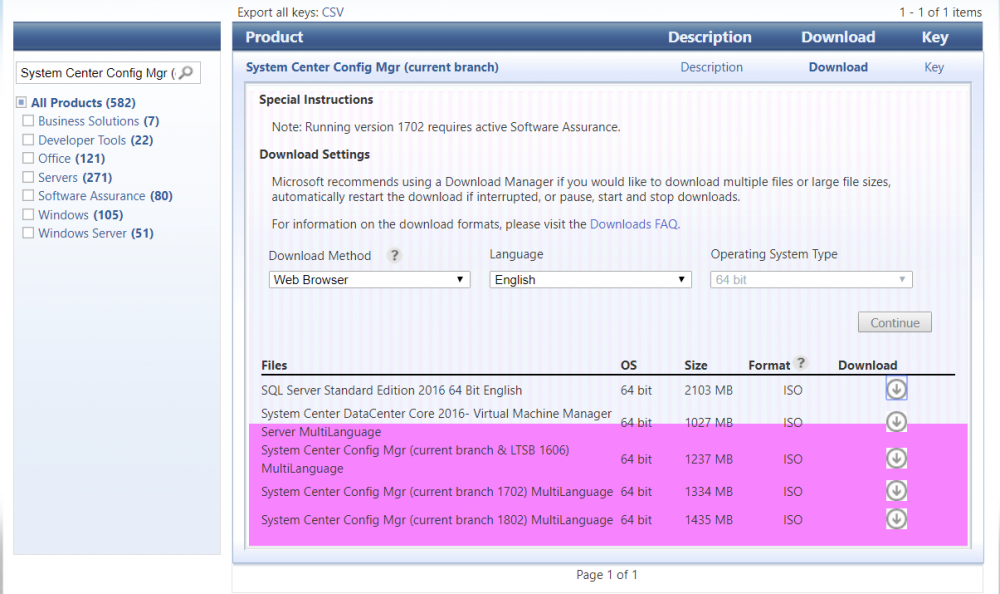
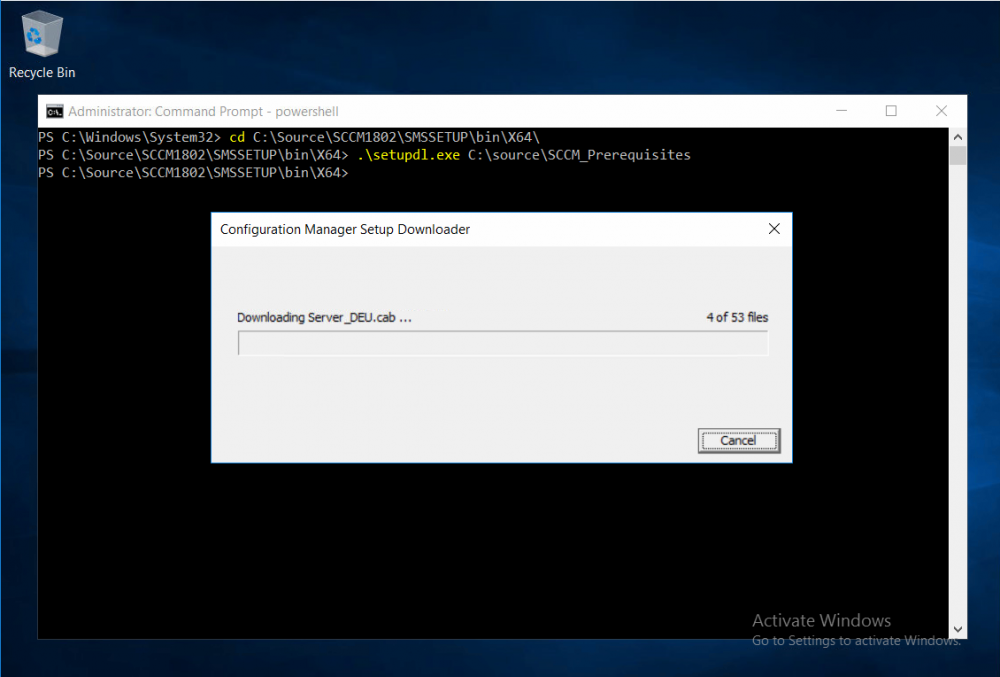
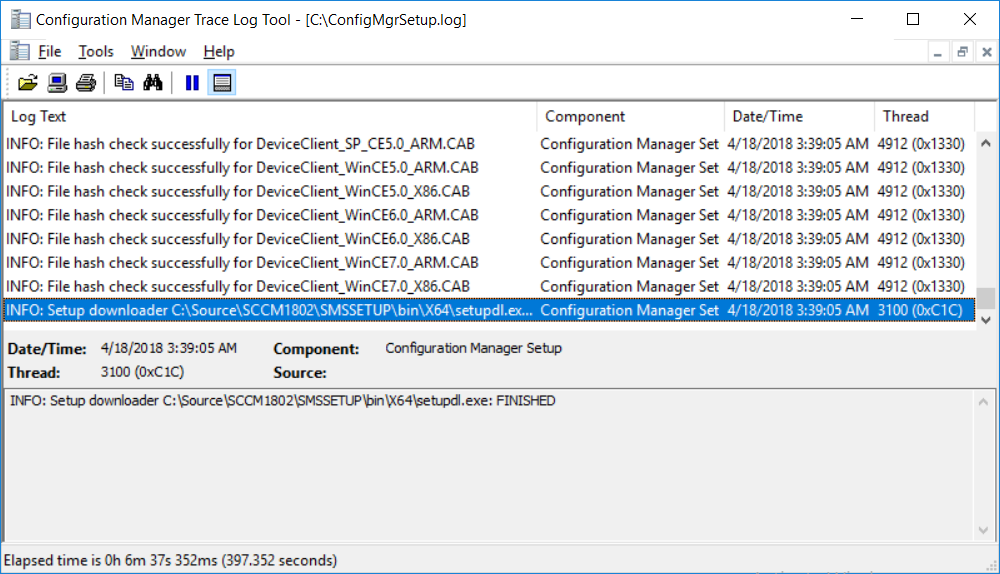
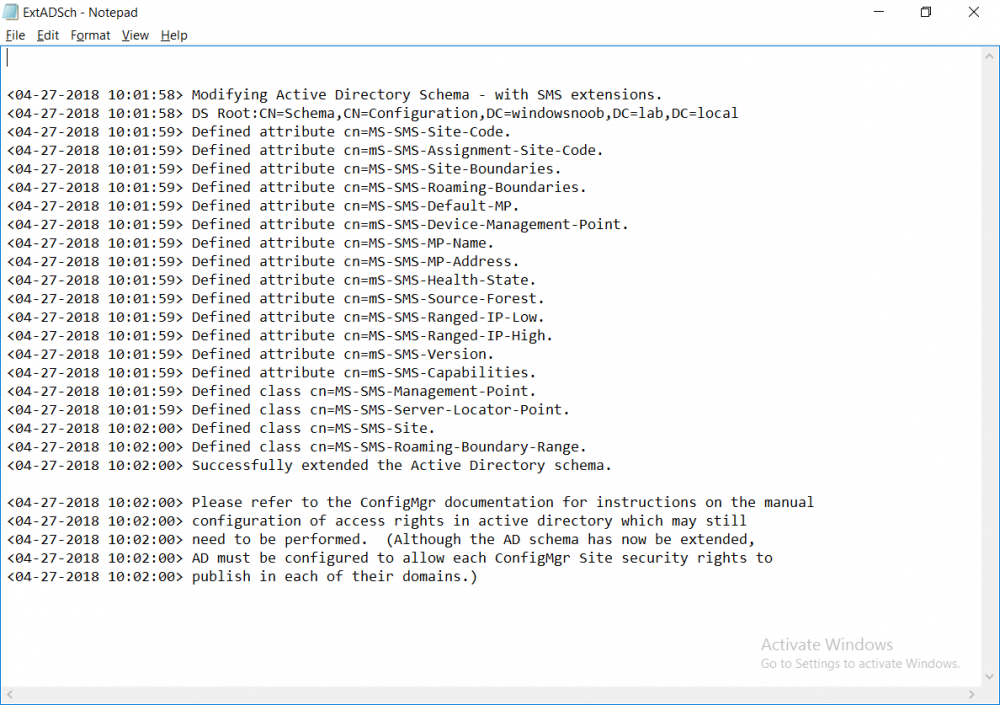
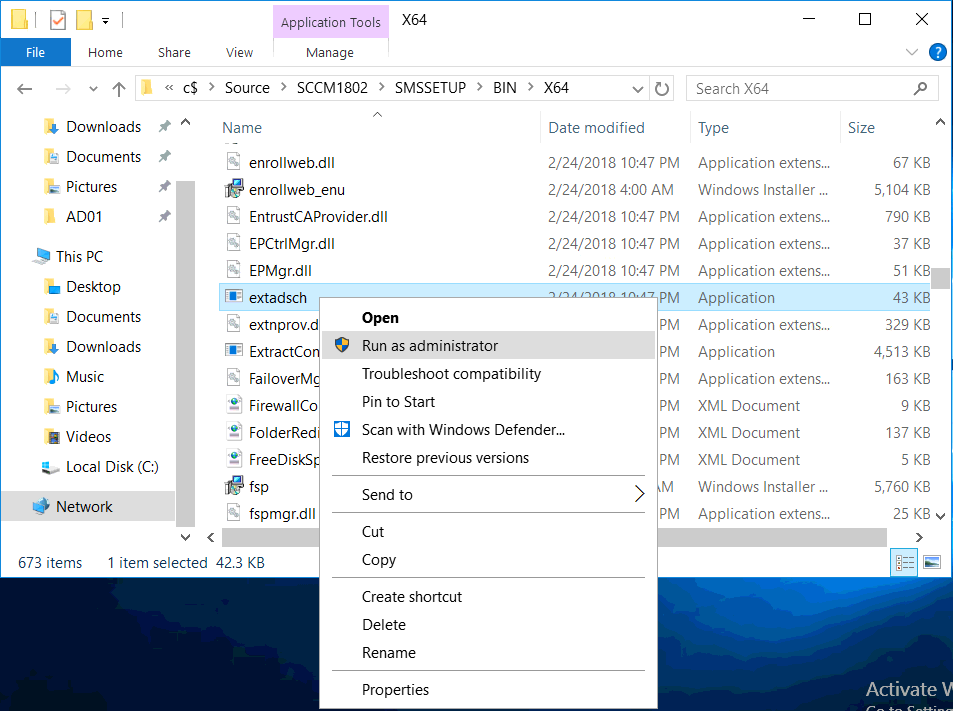
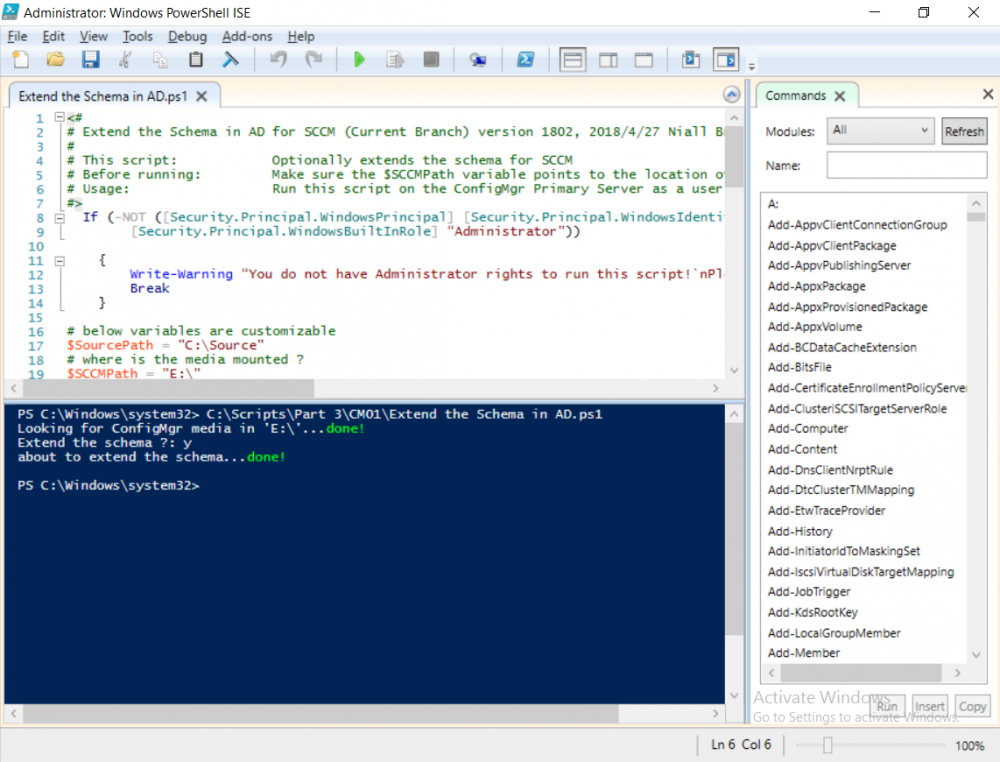
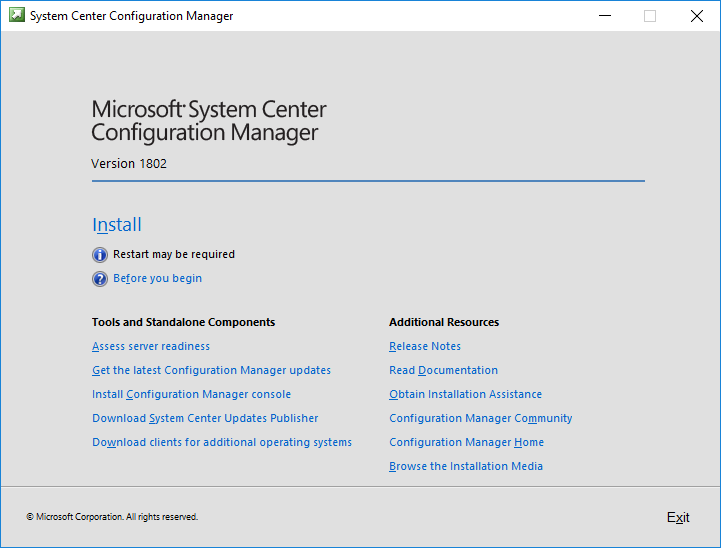
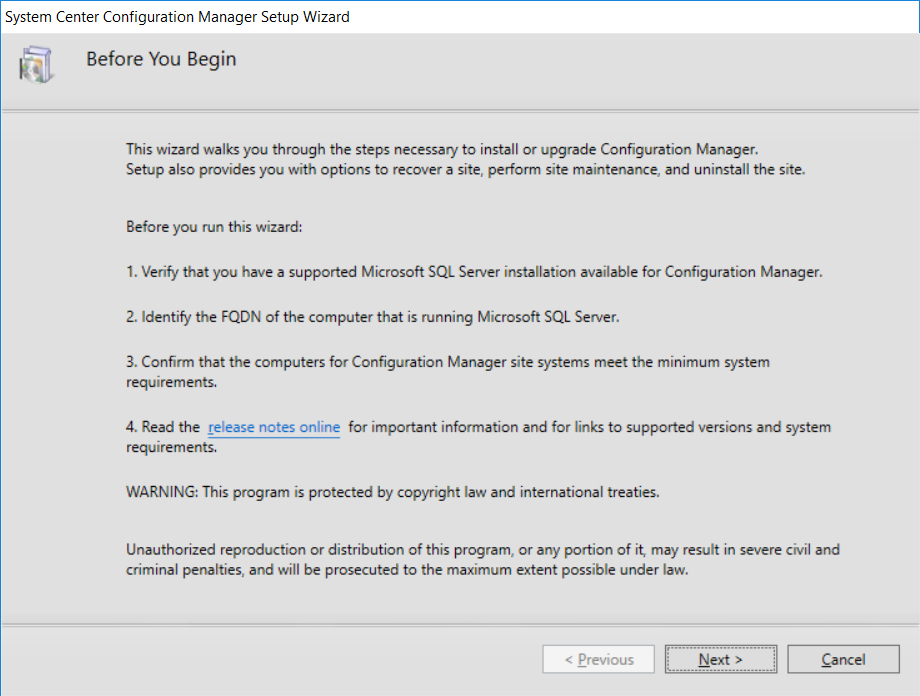
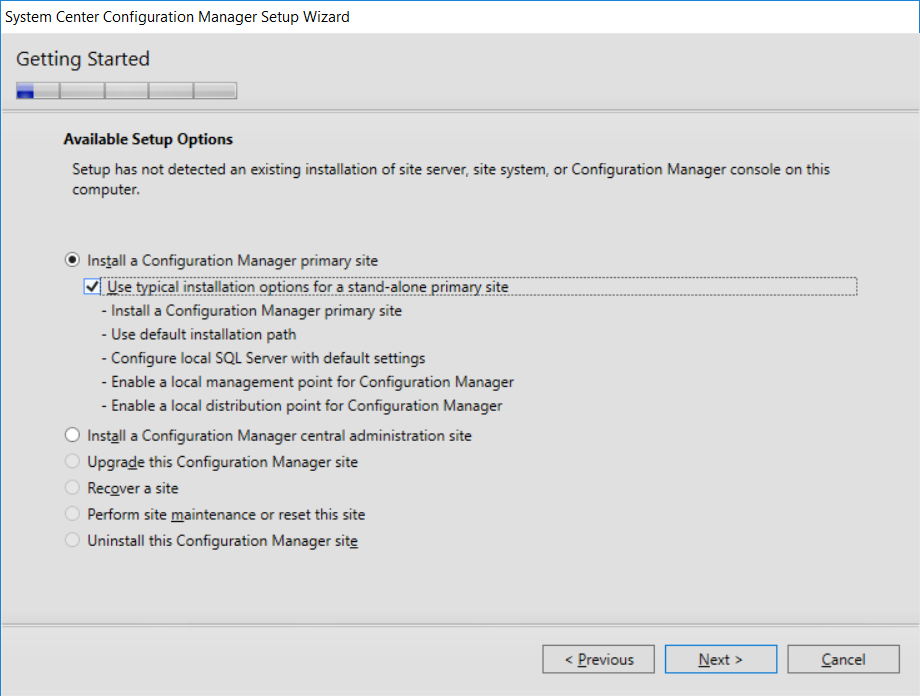
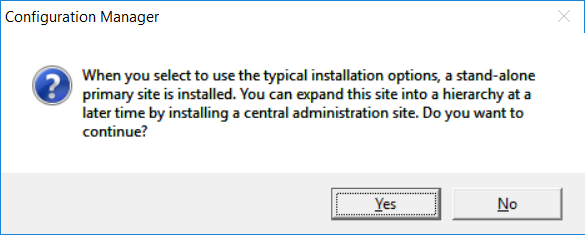
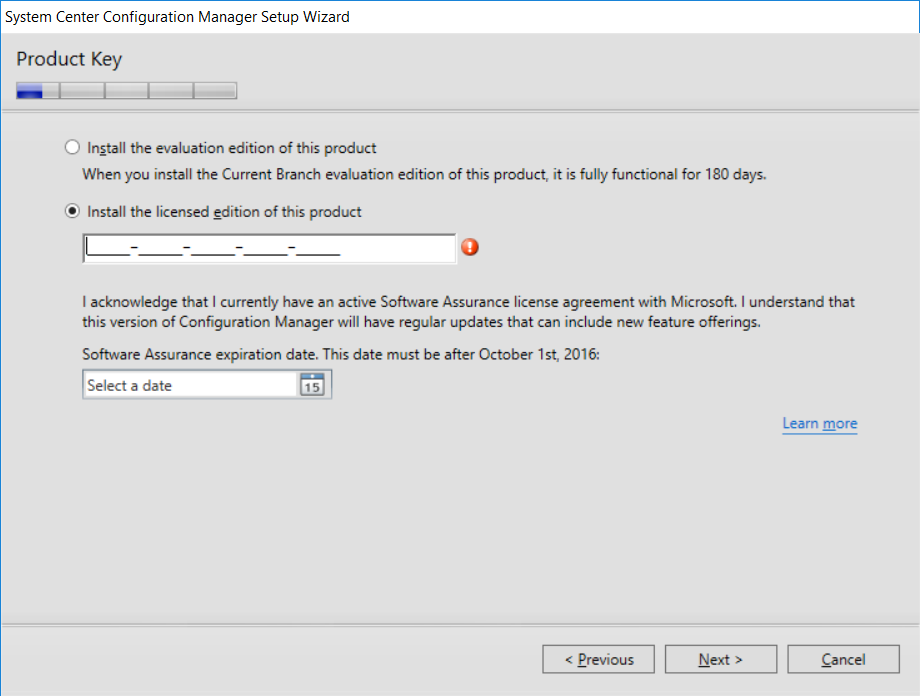
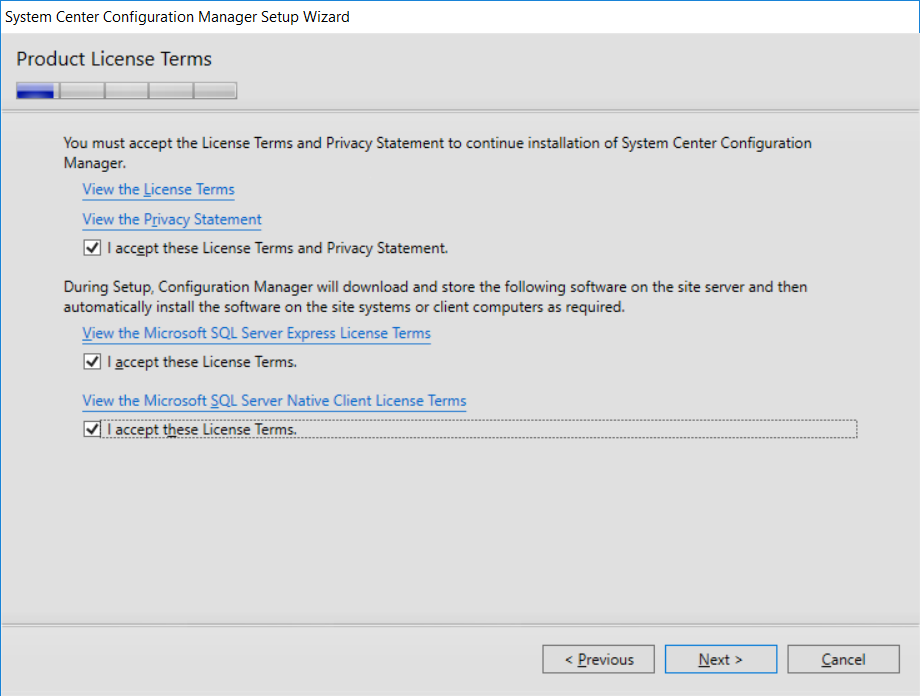
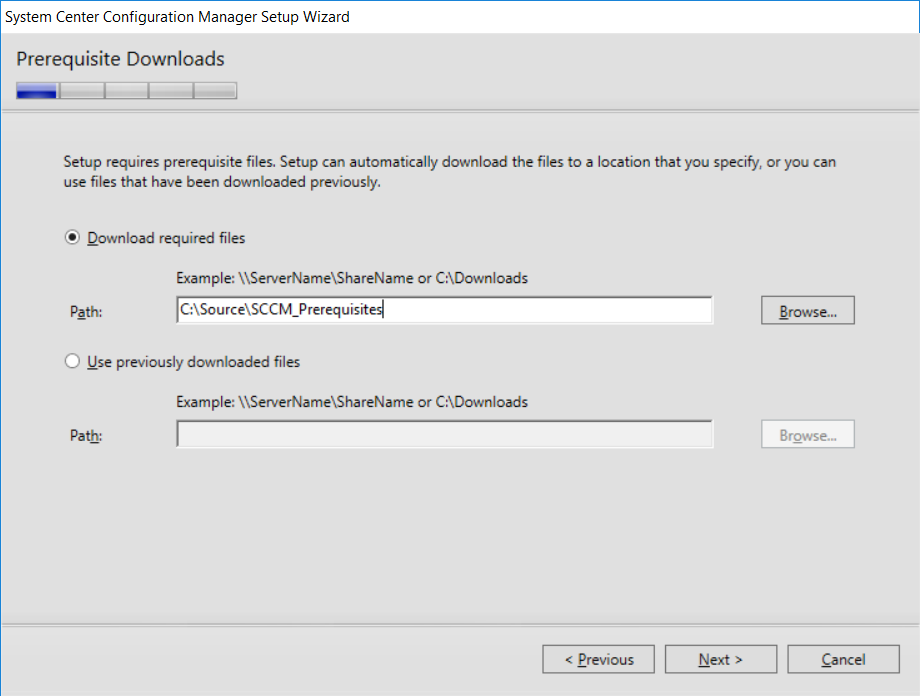
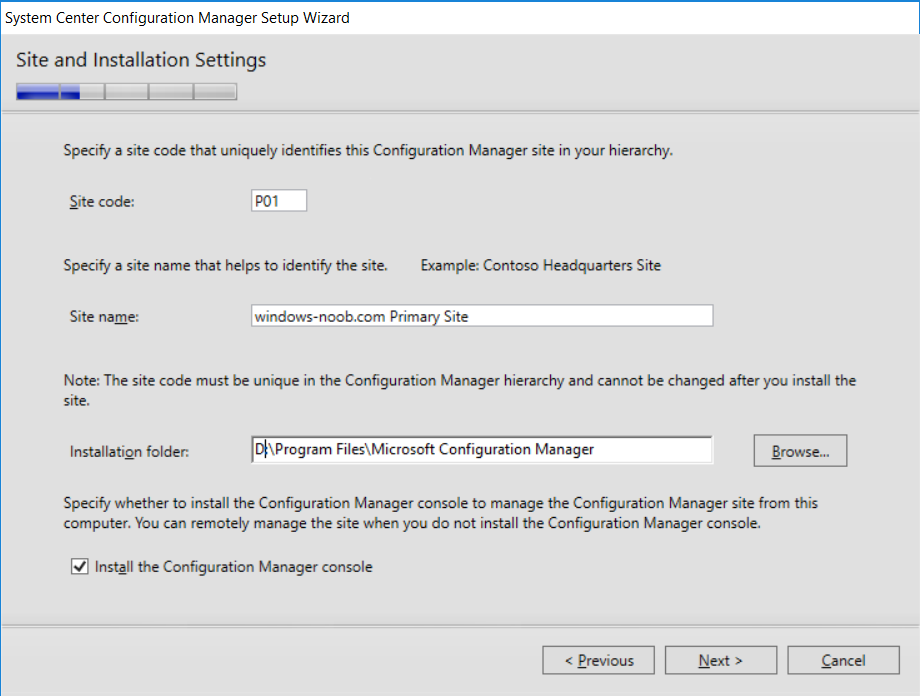
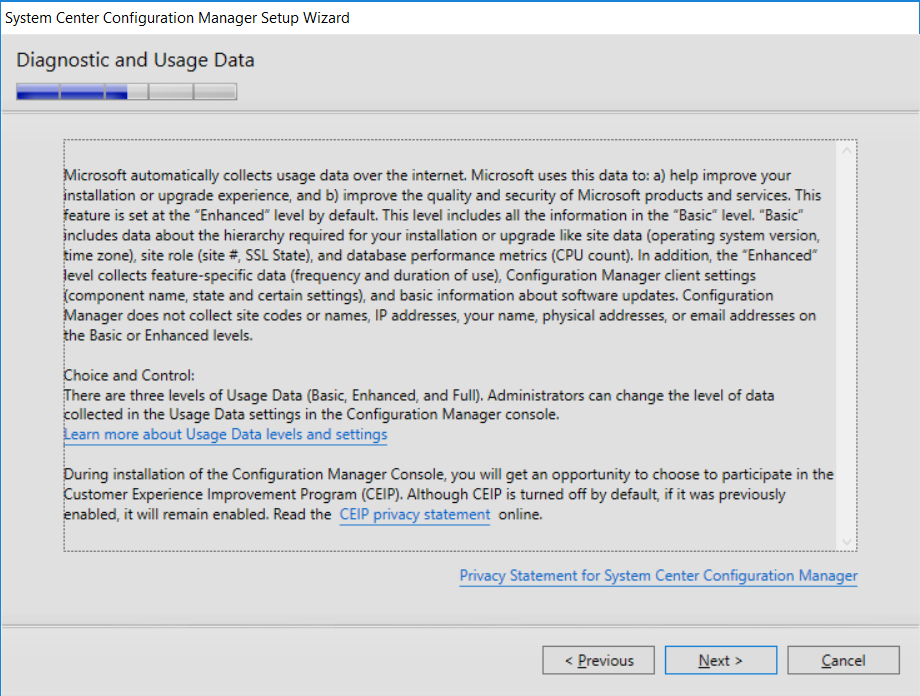
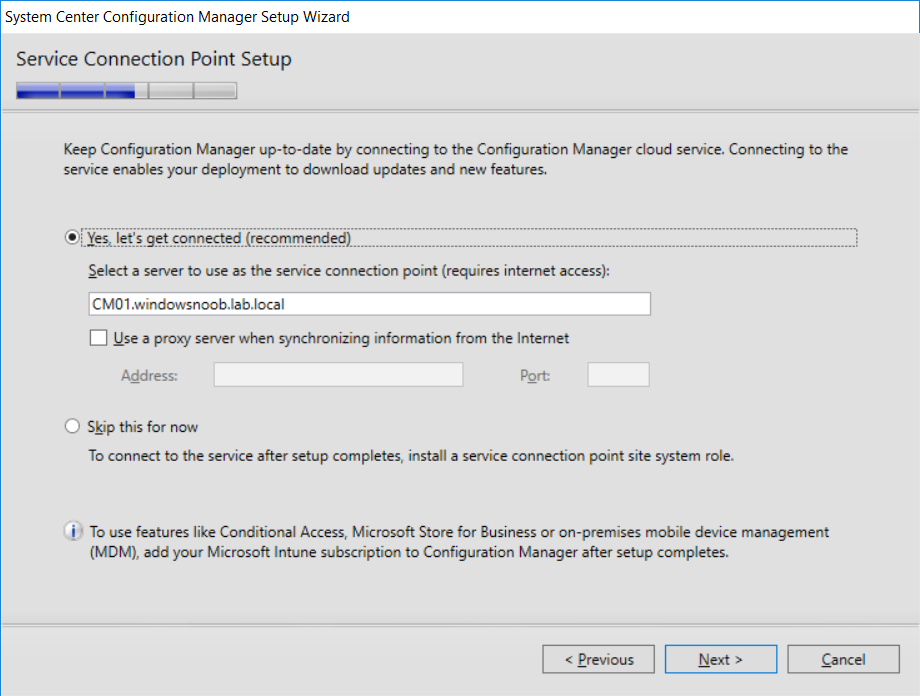
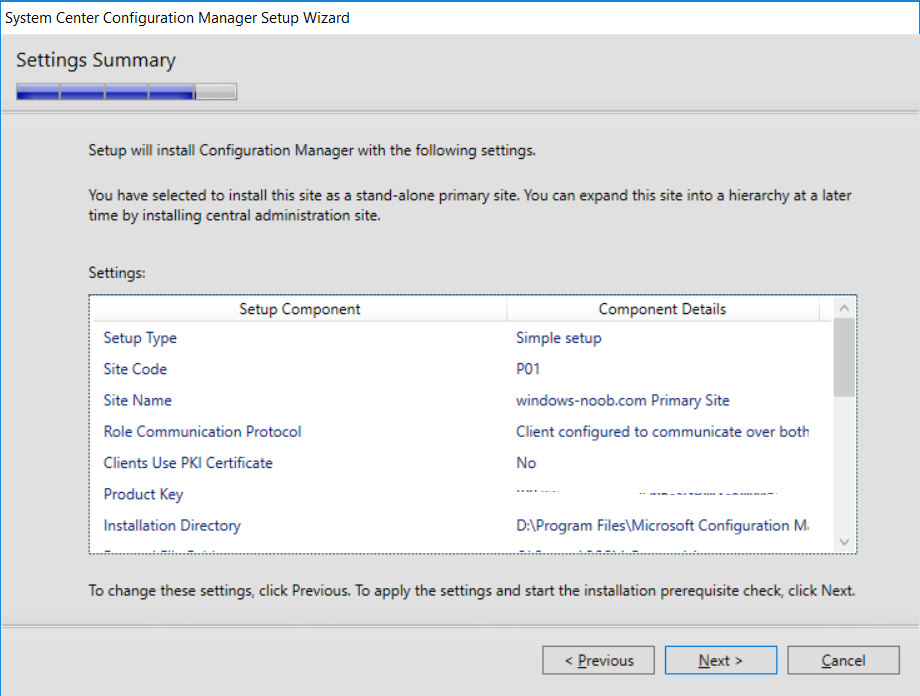
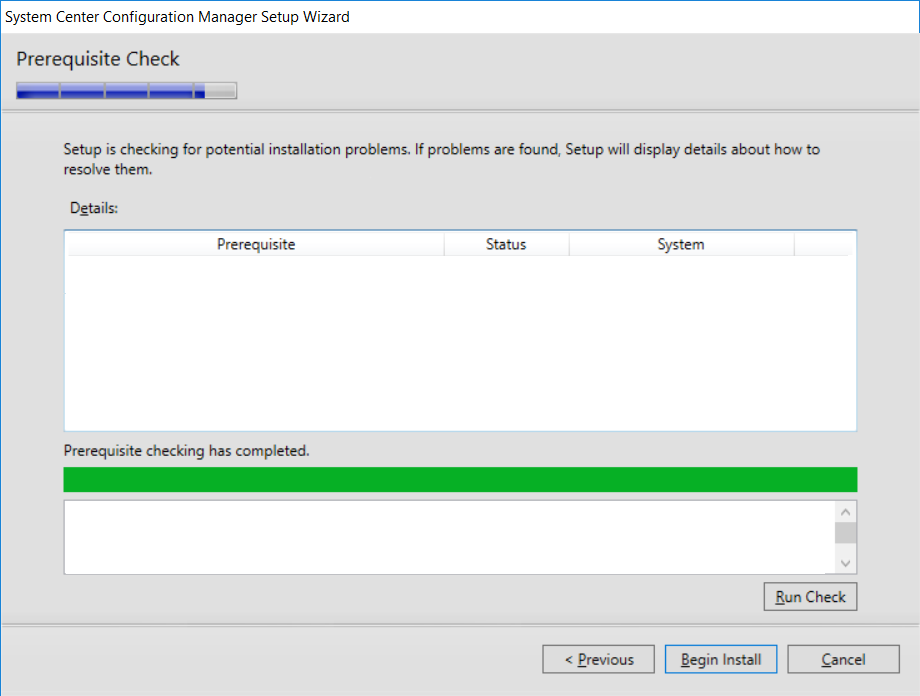
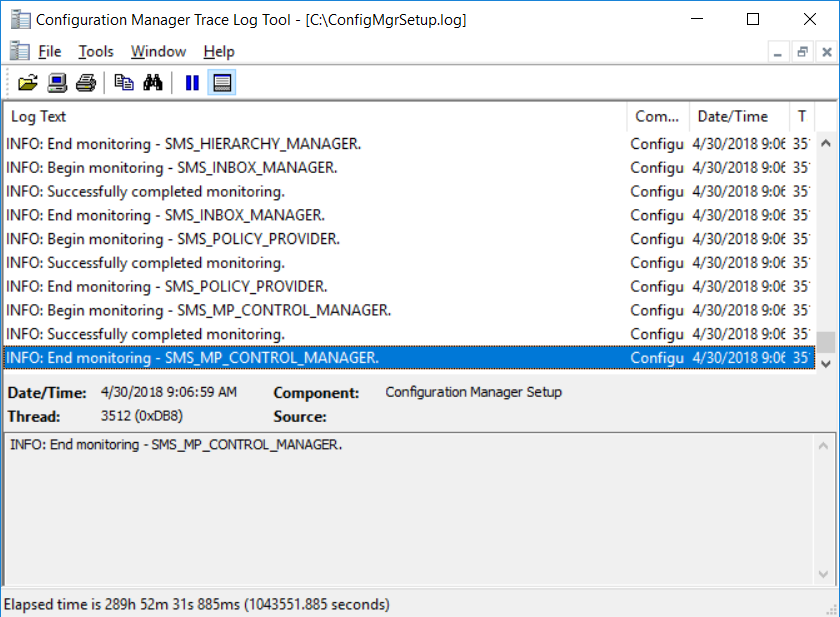
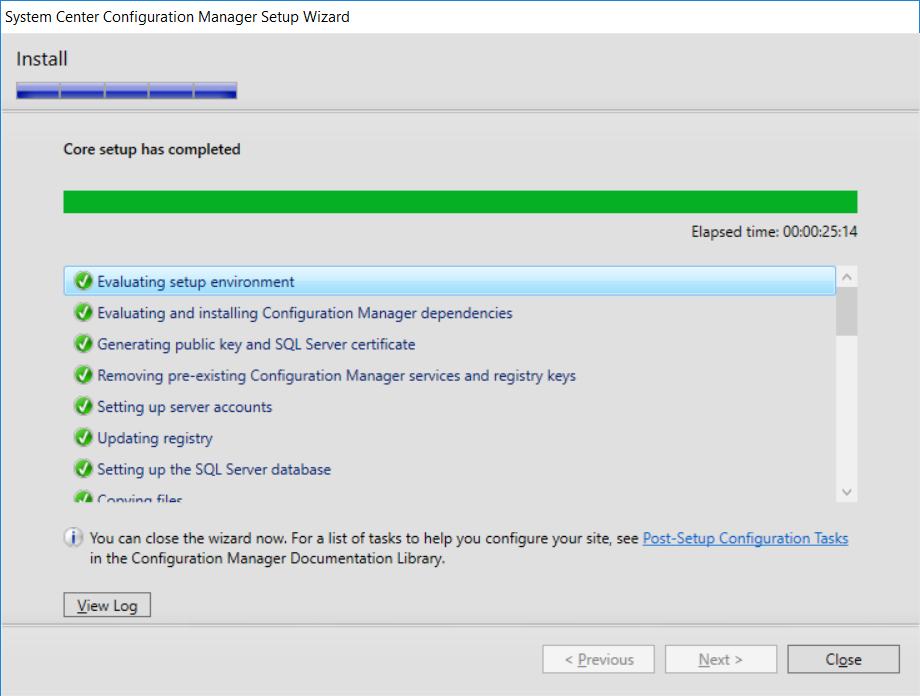
This multi-part guide will show you how to install the latest baseline version of Configuration Manager from Microsoft. The latest available baseline version is System Center Configuration Manager (Current Branch) version 1802 as of March 29th 2018. How can I install System Center Configuration Manager (Current Branch) version 1802 on Windows Server 2016 with SQL Server 2017 – Part 1 How can I install System Center Configuration Manager (Current Branch) version 1802 on Windows Server 2016 with SQL Server 2017 – Part 2 How can I install System Center Configuration Manager (Current Branch) version 1802 on Windows Server 2016 with SQL Server 2017 – Part 3 How can I install System Center Configuration Manager (Current Branch) version 1802 on Windows Server 2016 with SQL Server 2017 – Part 4 You can use this multi-part guide to get a hierarchy up and running on Windows Server 2016 using SQL Server 2017. The concept behind this is to guide you through all the steps necessary to get a working Configuration Manager Primary site installed using manual methods or automating it by using PowerShell. This gives you the power to automate the bits that you want to automate, while allowing you to manually do other tasks when needed. You decide which path to take. PowerShell knowledge is desired and dare I say required if you are in any way serious about Configuration Manager. I will show you how to do most steps via two methods shown below, it’s up to you to choose which method suits you best but I highly recommend automating everything that you can (if possible), using PowerShell. Method #1 – Do it manually Method #2 – Automate it with PowerShell In Part 1, you configured Active Directory Domain Services (ADDS) on AD01, then joined the Configuration Manager primary server (CM01) to the newly created domain. You then created users, usergroups and OU's in Active Directory and created the System Management Container. Finally you delegated permission to the Configuration Manager server to the System Management container. In Part 2, you configured Windows Server 2016 roles and features on the Configuration Manager primary server (CM01) and then you downloaded and installed Windows ADK 1709. Next you installed SQL Server 2017 CU5 with SQL Server Management Studio (SSMS) and Reporting Services before installing the WSUS role which uses SQL to store the SUSDB instead of the Windows Internal Database (WID). In this Part, you will download and extract the ConfigMgr content, you'll download the ConfigMgr prerequisites and then you'll extend the Active Directory schema before installing System Center Configuration Manager (Current Branch) version 1802. Step 1. Download and extract the ConfigMgr content Before installing System Center Configuration Manager version 1802 you'll need to download the content as it is a baseline version. You can download baseline versions of the ConfigMgr media from Microsoft's Volume licensing Service Center (VLSC) site for use in production or from MSDN (or the Microsoft Evaluation site) for use in a lab. The VLSC download can be found be searching for Config and then selecting System Center Config Mgr (current branch and LTSB) as shown below. Once you've downloaded the ISO, mount it using Windows File Explorer and copy the contents to somewhere useful like C:\Source\SCCM1802 on the Configuration Manager server. Step 2. Download the ConfigMgr Prerequisites Note: Perform the following on the Configuration Manager server (CM01) as a Local Administrator You can download the prerequisites during ConfigMgr setup or in advance. As you'll probably want to install more than one copy of ConfigMgr (one lab, one production) it's nice to have the prerequisites downloaded in advance. Method #1 – Do it manually To do that, open an administrative PowerShell command prompt and navigate to the following folder: C:\Source\SCCM1802\smssetup\bin\X64 Run the following line .\SetupDL.exe C:\Source\SCCM_Prerequisites Once the process is complete you can open C:\ConfigMgrSetup.log with CMTrace (or notepad) to verify the status of the download. Note: You can find the CMTrace executable in the SMSSetup Tools folder in the location that you extracted the ConfigMgr media, eg: C:\Source\SCCM1802\SMSSETUP\TOOLS. Method #2 – Automate it with PowerShell To automate the download of the prerequisites simply follow the instructions and run the Install SCCM Current Branch version 1802.ps1 Powershell script in Step 4 or use the Download SCCM prerequisite files.ps1. Step 3. Extend the Schema Note: Perform the following on the Domain controller server (AD01) as Administrator. You do not have to extend the Active Directory schema if it was already extended for Configuration Manager previously. Method #1 – Do it manually To do that, on the Active Directory domain controller (AD01), open Windows File Explorer and browse to the network path of the ConfigMgr server where you've copied the SCCM source, eg: \\cm01\c$\Source\SCCM1802\SMSSETUP\BIN\X64 In that folder, locate extadsch.exe and right click, choose Run as Administrator. After the schema has been extended for SCCM, you can open C:\ExtAdsch.log on the root of C:\ on the server you are performing this on, and review the success or failure of that action. Method #2 – Automate it with PowerShell To automate extending the schema, use the Extend the Schema in AD.ps1 PowerShell script. Run the script on the CM01 server using credentials that have the ability to extend the schema. Step 4. Install SCCM Current Branch (version 1802) Note: Perform the following on the ConfigMgr server (CM01) as Administrator. Method #1 – Do it manually To do that, on the Configuration Manager server (CM01), open Windows File Explorer and browse to the network path of the ConfigMgr server where you've copied the SCCM source, eg: C:\Source\SCCM1802\ In that folder, double click on splash.hta. The Installer appears, click on Install. At the Before You Begin screen click Next. In the Available Setup Options screen, place a checkbox in "Use typical Installation options for a stand alone primary site" When prompted if you want to continue click Yes. On the Product Key screen enter your Key (or choose the eval option), and set the Software Assurance Date (optional) On the Product License Terms screen, select the 3 available options and click Next. On the Prerequisite Downloads screen, select the first option and specify C:\Source\SCCM_Prerequisites as the folder to download the prerequisite files. Click Next to start the download. On the Site and Installation Settings screen, enter your chosen site code (eg: P01), your site name and the path where you want to install ConfigMgr. On the Diagnostics and Usage data screen, click Next. On the Service Connection Point Setup screen, enter your choices and click Next. On the Settings Summary, review your choices and when happy with them click Next. On the Prerequisite Check screen click Begin Install when ready. During the installation, click on View Log (opens C:\ConfigmgrSetup.log) to review the installation progress using CMTrace and when the installation is done, click Close. Method #2 – Automate it with PowerShell To automate the installation of ConfigMgr 1802 (including all the previous steps above), simply run the Install SCCM Current Branch version 1802.ps1 PowerShell script. Run the script on the CM01 server and when prompted to extend the schema, enter your choice (yes or no) and if you choose to extend the schema, provide suitable credentials when prompted. Once done with the schema extension, the installation will continue (as shown below). and once installed you can launch the console. Success ! Summary In this 3 part guide you used quite a bit of PowerShell to automate pretty much most of Installing System Center Configuration Manager Current Branch (version 1802), including installing and configuring SQL Server 2017 on Windows Server 2016. Doing it with PowerShell means you can safely say that you've got a handle on Automation using PowerShell. I hope you learned a lot from doing it this way, and until next time, adios ! Downloads The scripts used in this guide are available for download here. Unzip to C:\Scripts on both servers. The scripts are placed in the corresponding folder (Part 1, Part 2 etc) and sorted into which server you should run the script on (AD01 or CM01). Scripts.zip
- 19 replies
-
- powershell
- current branch
-
(and 2 more)
Tagged with:
-
good question which I (and Justin) answered on the facebook group here https://www.facebook.com/groups/windowsnoob/
- 7 replies
-
- sccm
- current branch
-
(and 2 more)
Tagged with:
-

How can I add a new driver to an existing Driver Package
anyweb replied to sccmmidi's question in Deploy software, applications and drivers
the issue with this is as soon as you add new content to an existing package, you need to update it to your distribution points, (otherwise your clients won't get the new drivers...) and when you do that, any live task sequence that references that package will fail on that package until the content is distributed, so, if you can time it so that you know no one will be using the task sequence, then sure you can use the existing driver package and simply update the content source with the new drivers, and then update the package to your dp's, if however you cannot guarantee down time for the task sequences, then your best option is to create a v2 of the same driver package but with the new content, then distribute that to all your dp's and once done, replace the reference in your task sequence with the v2 version of the driver package -
do you want to replace the current VPN gateway address with a new one or check for both ? are you using multiple VPNs ? If multiple then you'll need to edit line 300 to include nested If statements as described here
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
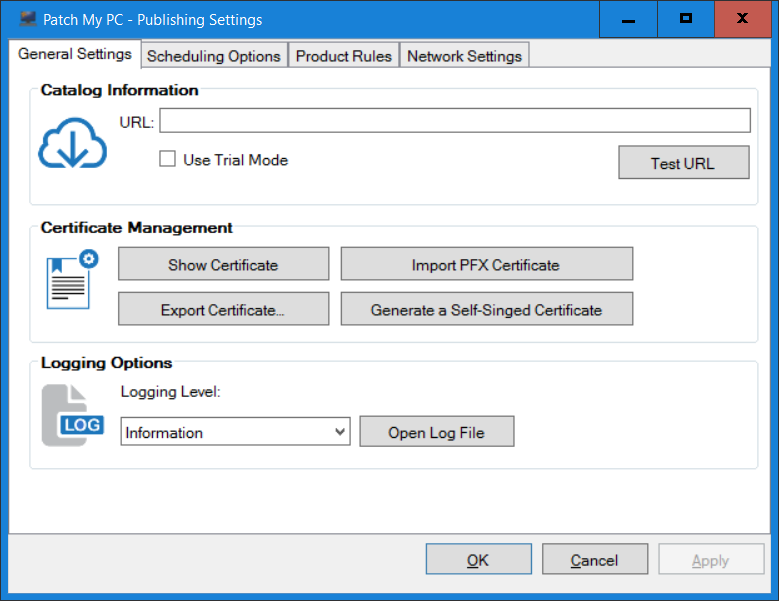
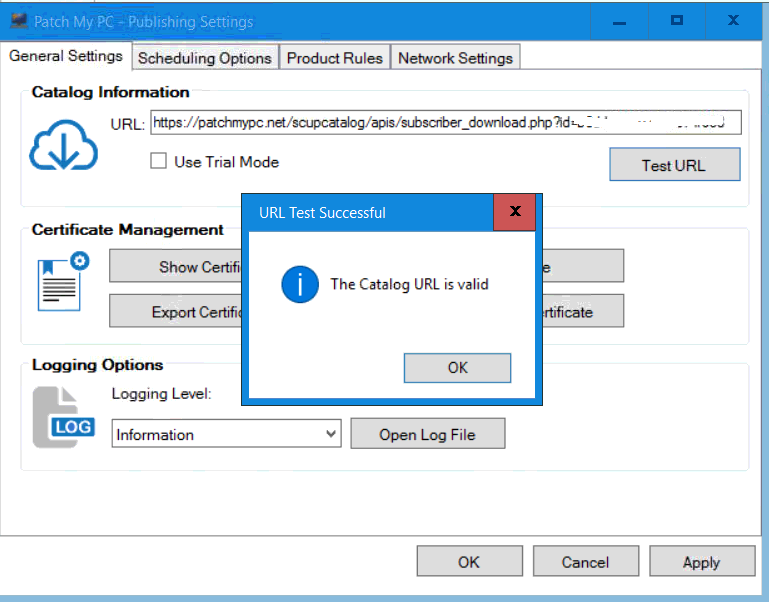
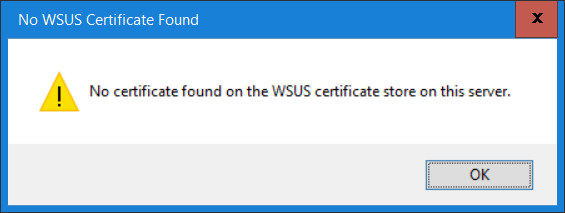
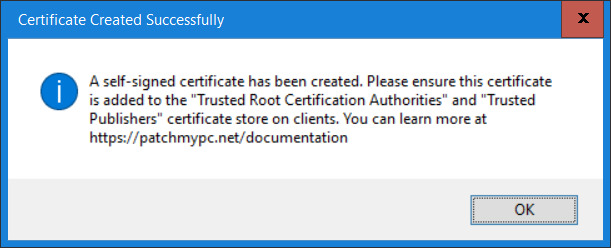
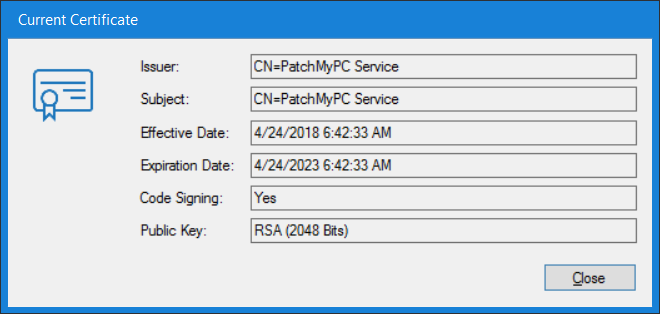
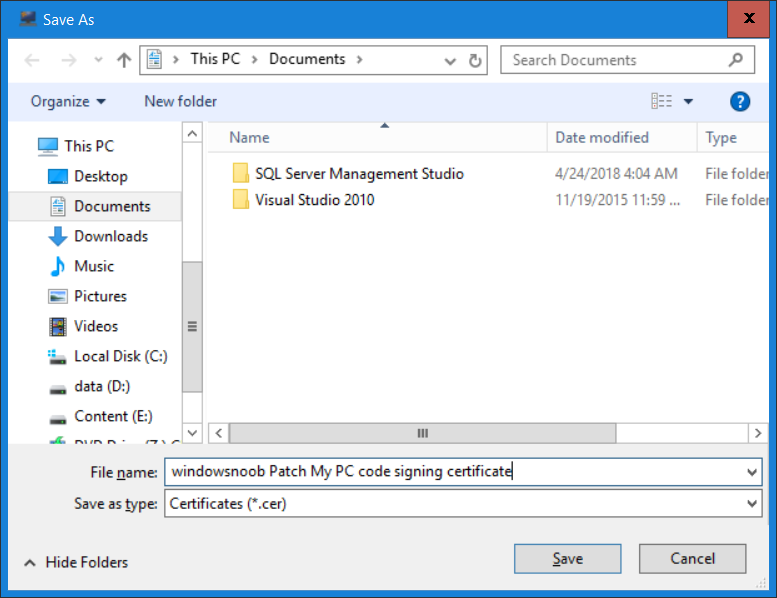
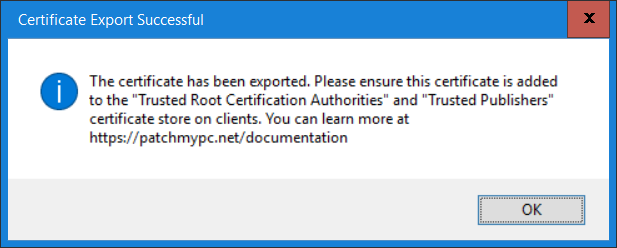
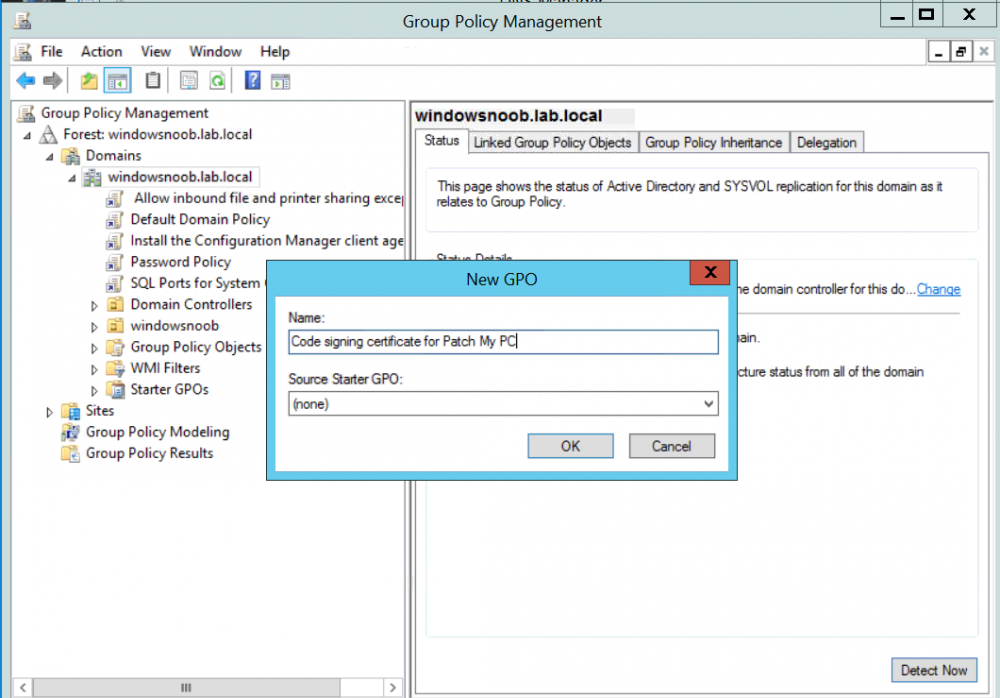
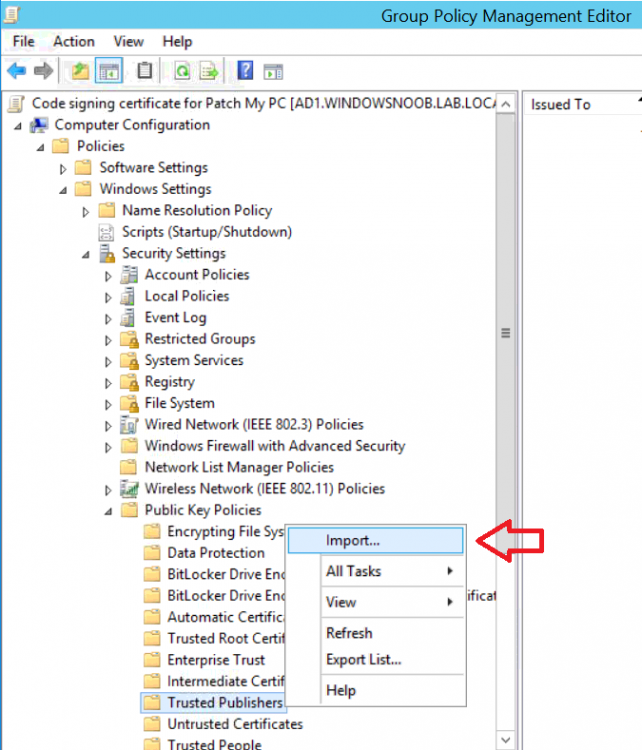
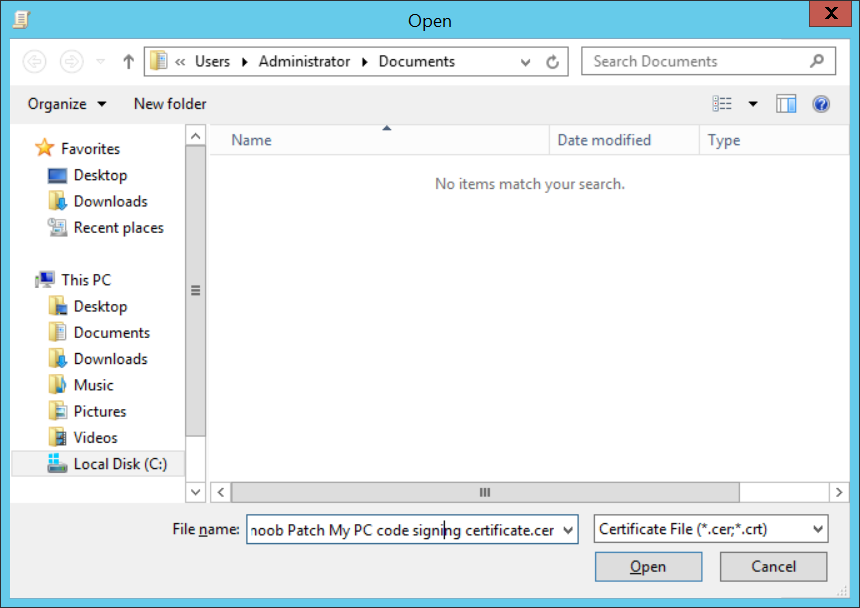
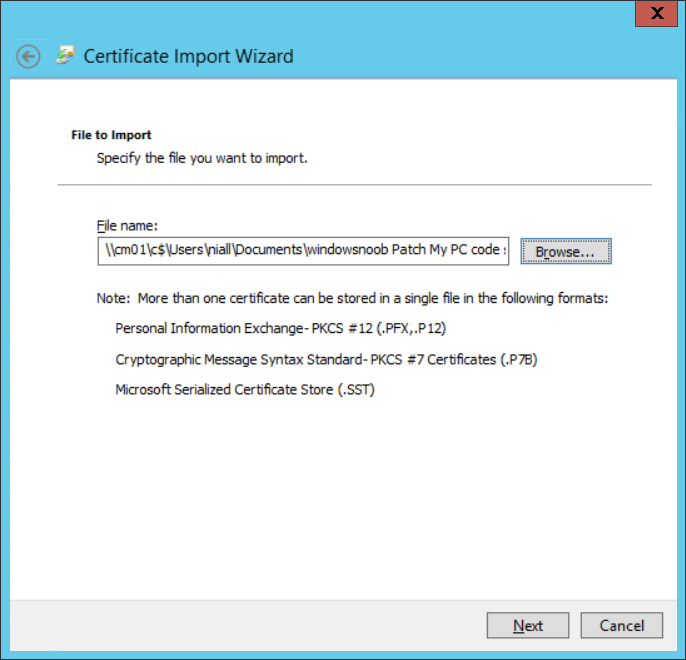
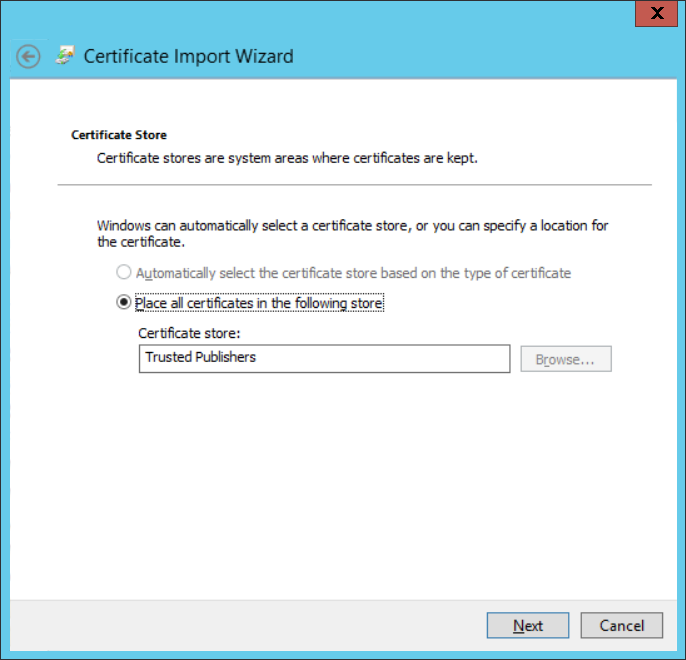
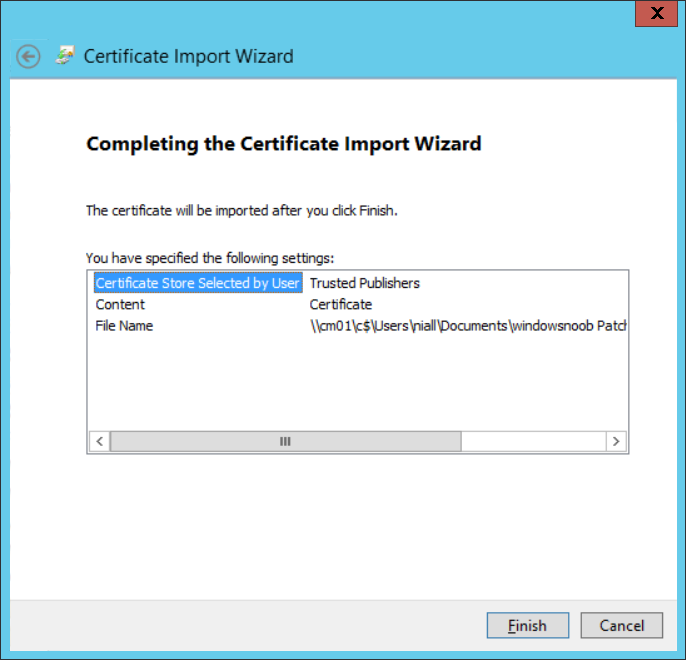
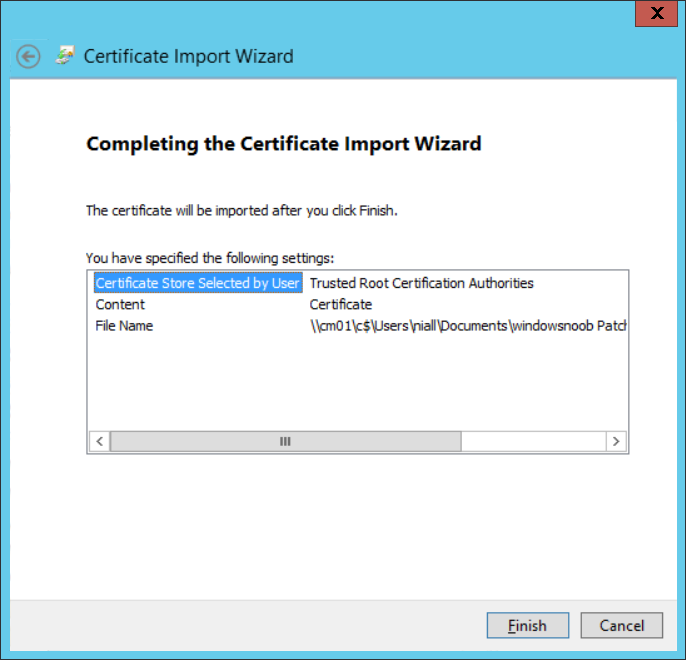
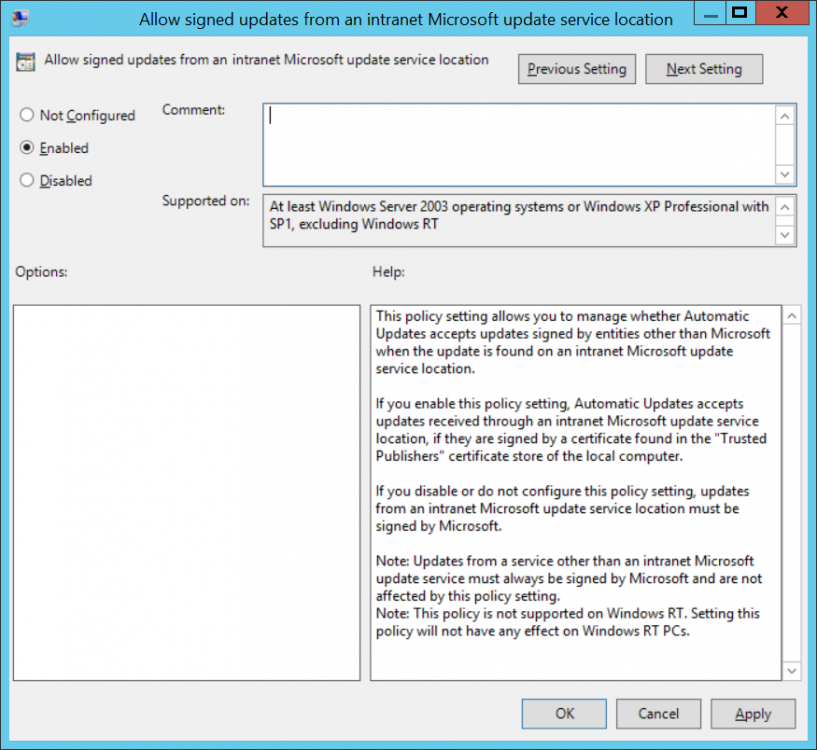
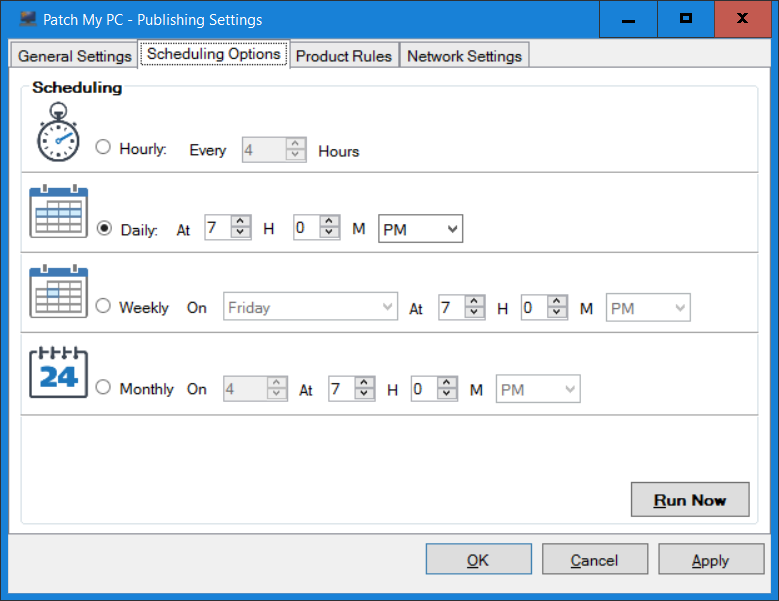
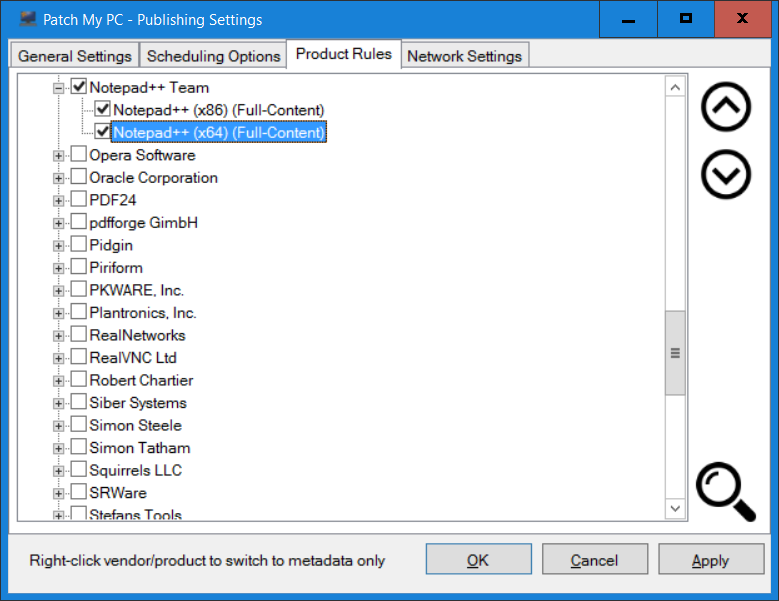
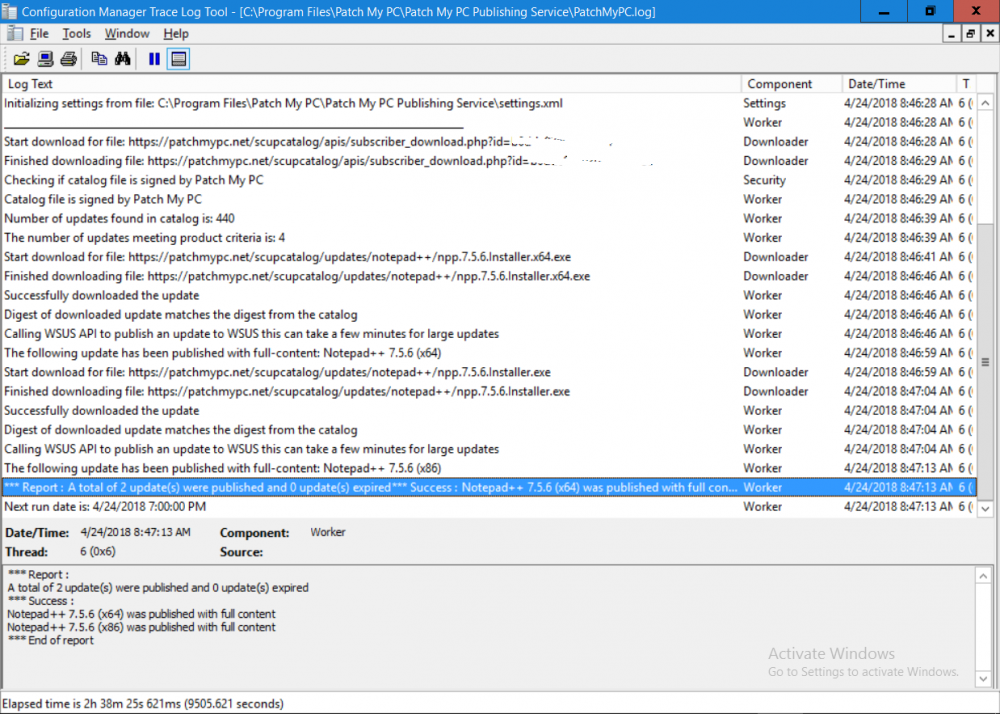
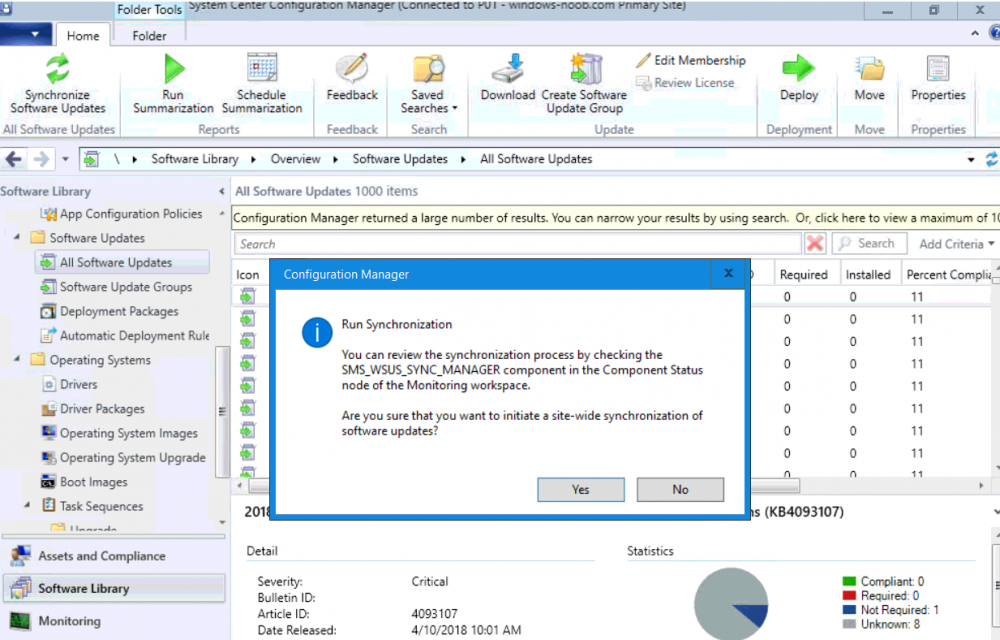
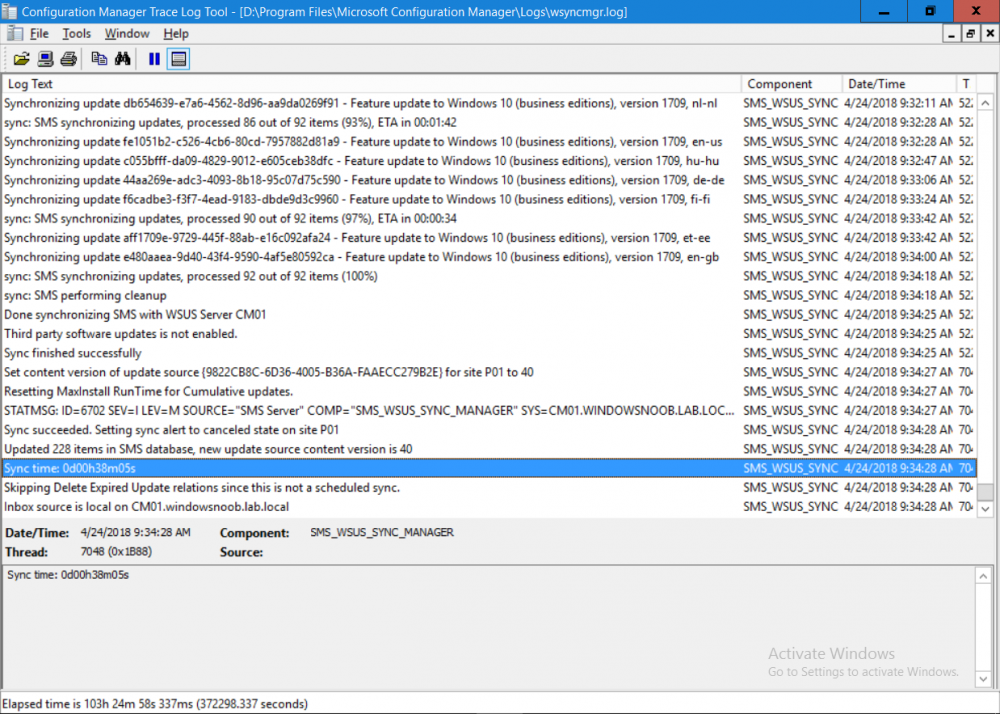
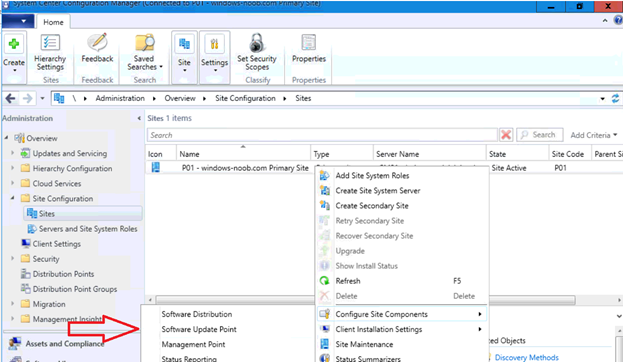
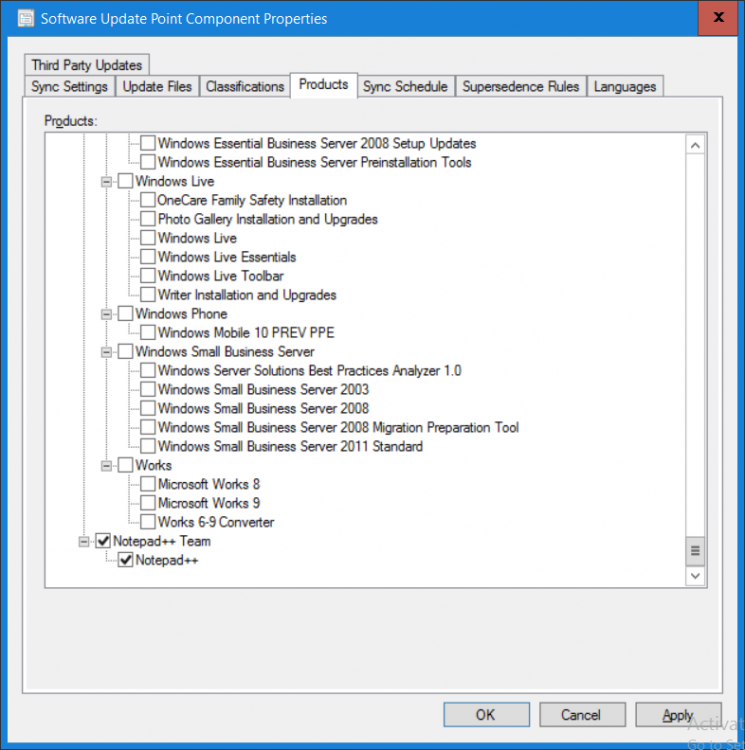
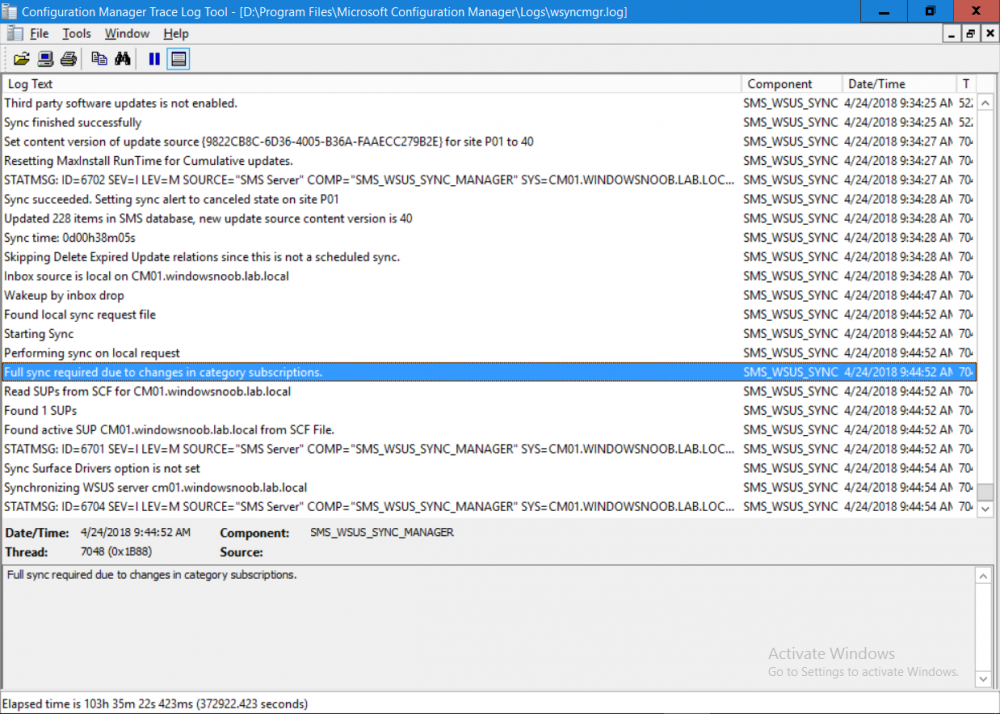
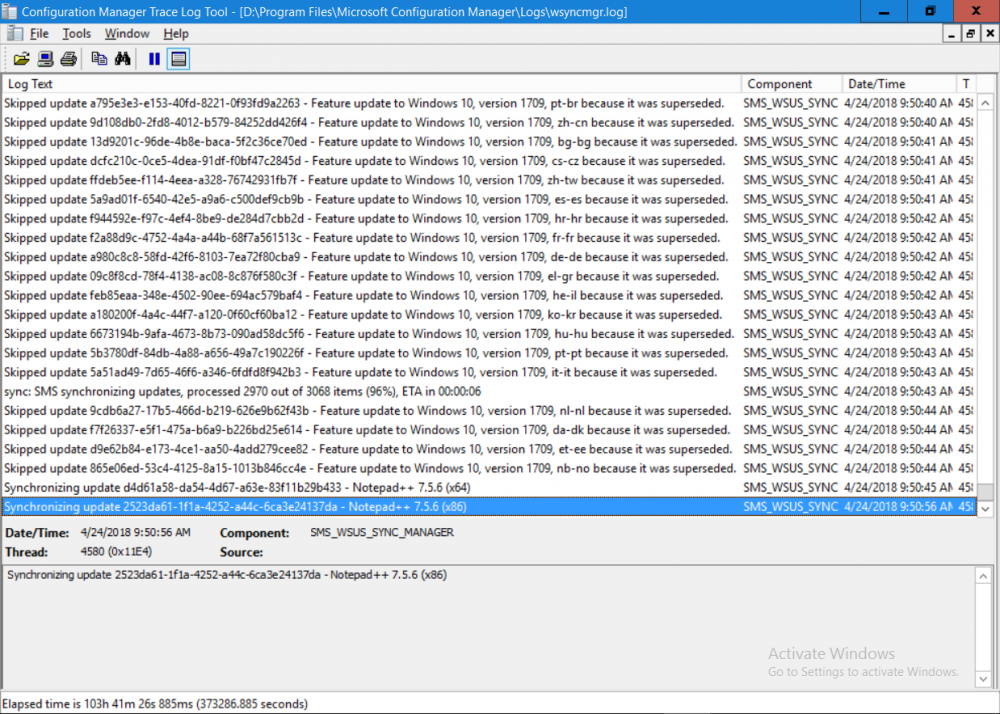
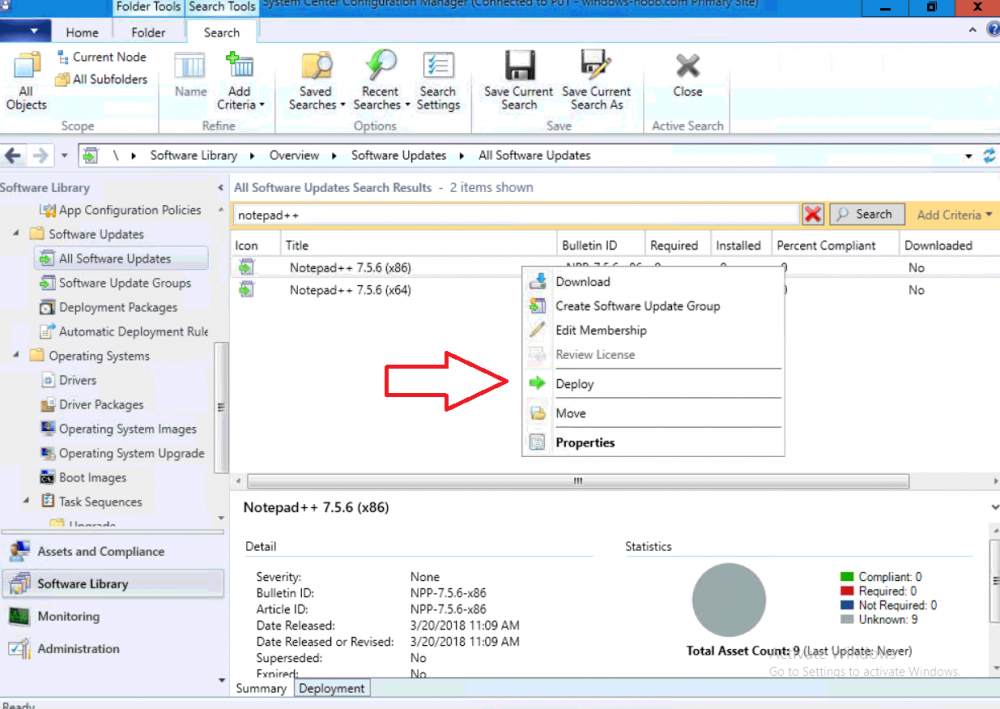
Introduction Security is a bigger focus today than ever before, and rightly so. As part of that focus ongoing patching is a requirement, both of the operating system (quality updates and feature updates) and the application layer too. Microsoft provides updates for their supported operating systems and applications that can be downloaded manually or automatically on the client via Microsoft Update, or deployed using on premise infrastructures like WSUS or SCCM or even via cloud based technology such as Microsoft Intune and Windows Update for Business. But what about on-premise patching of 3rd party applications (applications that come from vendors other than Microsoft), those vendors usually provide their own patches to help secure their products, but because they are 3rd party, they are not natively trusted by WSUS. Getting those patches into WSUS requires some outside help and there are several companies offering applications to help you with that task, one of which is called Patch My PC. Patch My PC is recommended because it’s lean, easy to use and competitively priced and it was developed by former Premier Field Engineers at Microsoft. Step 1. Download the Patch My PC Publishing Service Setup file Note: This guide was completed using SCCM version 1802 (Current Branch) running on Server 2016. To install that version of SCCM yourself, follow this link. Download the Patch My PC Publishing Service Setup file (MSI format) from the link below: https://patchmypc.net/publishing-service-download You should install it on the computer hosting your Software Update Point. Note: The MSI only supports WSUS 4.0 (Windows Server 2012 & 2016). Once the software is installed you can choose to launch it, the Settings UI appears. Step 2. Adding the catalog URL in the service After installing the software, you need to enter your individual catalog URL (if you are subscribed to the service) or enable trial mode to test the software. To do this, paste the unique download ID supplied in the email you received when you signed up for the service into the field provided. Click on Test URL to verify the catalog URL is correct. Using your unique catalog URL gives you access to all the supported applications in the catalog whereas when using the trial mode you only get access to a small subset (12) of those supported applications. Step 3. Creating a self-signed or importing a PFX based certificate In order to publish updates to WSUS, you need to setup a code-signing certificate. Certificates are used by the Patch My PC Publishing Service to sign the 3rd party updates so that WSUS can use them. There are two options available: · Self-signed certificate · PFX based certificate (3rd party or internal certificate authority) Note: Clicking on Show Certificate will show if any existing certificate is in place, for example if you’ve migrated from System Center Updates Publisher (SCUP). If like me you haven’t set this up yet, clicking on Show Certificate will not find any certificate in the WSUS certificate store. A self-signed certificate is the easiest way to get started with this tool and it’s free, however it does not provide security focused features such as revocation (cancellation of the certificate for all computers using CRL’s). For the purpose of this guide however, you’ll create a self-signed certificate using the tool. To create a self-signed certificate, click on the Generate a Self-Signed Certificate button in Certificate Management. Click OK to the Certificate Created Successfully message and then click on Show Certificate again, to see details about the newly created self-signed certificate. Step 4. Exporting the code-signing certificate In order for clients to install third-party updates, they must trust the code-signing certificate. To do this you can export the certificate and deploy it using group policy. Click on Export Certificate and give the .CER file a suitable name so you know what it is for. Click OK to the Certificate Export Successful popup. Step 5. Deploy the code signing certificate to clients using Group Policy On the domain controller, open Group Policy Management and create or edit an existing GPO. Edit the GPO settings and navigate to Computer Configuration, Policies, Windows Settings, Security Settings and select Public Key Policies. Right Click on Trusted Publishers and click on Import. In the wizard that appears, click Next and then browse to the location where you saved the code-signing certificate, select it and click on Open. The certificate will be displayed, click Next. Click Next again and click Finish to complete the wizard. Click OK to the Import was successful message. Note: If you used a self-signed certificate, you must also import the exported .CER file to the Trusted Root Certificate Authorities certificate store. Right-click on Trusted Root Certification Authorities and select Import, follow the same process as above to import the exported .CER file. Once done, click OK to the Import was successful message. Step 6. Enabling the group policy object for allowing third-party updates to be used on clients In order that clients will allow 3rd party updates to be installed, you need to configure the Allow signed updates from an intranet Microsoft update service location policy to Enabled. To do so, select the GPO created above and navigate to Computer Configuration, Administrative Templates, Windows Components, then choose Windows Update, select the Allow signed updates from an intranet Microsoft update service location policy and set it to Enabled as shown below. Step 7. Setting the schedule for the publishing service If you need to configure the Patch My PC tool scheduling service to check for updates, then click on the scheduling options tab, the default options are displayed and should be adequate. Step 8. Enabling the product you want to include for automatic publishing Next on the Product Rules tab, select the Product (or Products) that you want to include for automatic publishing. In this guide you will select Notepad++. You can scroll up and down to find the vendor, or use the search magnifying glass to search. Right clicking on a product will change from Full-Content to metadata, and this allows you to report on compliance information for a large number of updates prior to deciding if you need to patch computers with a particular 3rd party update. Once done, click on Apply. Step 9. Trigger the initial publishing of updates To trigger the initial publishing of updates available from selected vendors, click on the scheduling options tab and select Run Now. You’ll get a popup informing you to check the log. The Log in question (PatchMyPC.log) can be found in the General Settings tab by clicking on Open Log File and is best viewed with CMTrace. As you can see below it’s found some updates for Notepad++. Step 10. Synchronize Software Updates in ConfigMgr In SCCM, select Software Library, Software Updates All Software Updates and click on Synchronize Software Updates. You can monitor the progress of that operation via the wsyncmgr.log available in the SCCM logs folder. And once the sync is complete you’ll see a line like Sync time:…. Step 11. Configure Products in ConfigMgr Once the sync is complete, select the Administration workspace, select site configuration, sites, right click on your site and configure site components, select Software Update Point as shown below. Next, select the Products you had previously selected in the Patch My PC tool. Click Apply and then OK. Next, trigger another Synchronize Software Updates in the SCCM console to synchronize the newly selected product(s). You’ll note that a full sync is required due to a change in categories. And you can see that NotePad++ updates are found And after a successful sync, they show up in the ConfigMgr console (refresh the console view), and can be deployed using whatever method you prefer, create an ADR (Automatic Deployment Rule) or Software Update or Software Update Group. Summary When using Patch My PC and System Center Configuration Manager (Current Branch), it’s never been easier to patch your computers with applicable 3rd party patches.
- 7 replies
-
- sccm
- current branch
-
(and 2 more)
Tagged with:
-
no worries by the way i've a new version of this guide below, part 3 coming soon How can I install System Center Configuration Manager (Current Branch) version 1802 on Windows Server 2016 with SQL Server 2017 – Part 1 How can I install System Center Configuration Manager (Current Branch) version 1802 on Windows Server 2016 with SQL Server 2017 – Part 2
-
ok so why the differences here if they are all on the same server, the FQDN's don't look right $SDKServer="mysccm2016.local" $RoleCommunicationProtocol="HTTPorHTTPS" $ClientsUsePKICertificate="0" $PrerequisiteComp="1" $PrerequisitePath="D:\Downloads" $ManagementPoint="mysccm2016.local" $ManagementPointProtocol="HTTP" $DistributionPoint="mysccm2016.local" $DistributionPointProtocol="HTTP" $DistributionPointInstallIIS="0" $AdminConsole="1" $JoinCEIP="0" $SQLServerName="MySCCM2016.MY2016DC.LOCAL" so in your example, i think you should change all those above to "MySCCM2016.MY2016DC.LOCAL" and try again
-
i've informed Microsoft PG, let's see what they say
-
i see the same thing i'll try with another driver_package to verify...
-
what error do you get ?
-
can you check if your slow clients are by any chance stuck in provisioning mode ? if they are the below key will be set to true Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\CCM\CcmExec\ProvisioningMode
- 5 replies
-
- software centre
- 1702
-
(and 1 more)
Tagged with:
-
check your custom client settings, it's likely that someone has configured them and deployed them to different collections, with different software center settings, also, on the machines where software center is slow to populate have you seen any other issues, do the logs look ok (c:\windows\ccm\logs)
- 5 replies
-
- software centre
- 1702
-
(and 1 more)
Tagged with:
-

windows defender through ADR
anyweb replied to Nshrouf's topic in System Center Configuration Manager (Current Branch)
the error means - Pre install scan failed Source: System Center Configuration Manager ----- start reading this https://support.microsoft.com/en-us/help/3090184/how-to-troubleshoot-software-update-scan-failures-in-system-center-201 -

windows defender through ADR
anyweb replied to Nshrouf's topic in System Center Configuration Manager (Current Branch)
could you possibly include some details of how you've configured your ADR settings, and what version of SCCM you are testing on, your screenshot isn't showing... -

Surface pro 4 does not PXE boot
anyweb replied to jack_SCCM's question in Deploying Operating Systems
you can add hardware mac addresses in SCCM 1606 or later via Administration, select Site Configuration select Sites, then click Hierarchy Settings and add your mac addresses- 29 replies
-
- Surface
- Surface pro
-
(and 5 more)
Tagged with:
-
Think containers are just for developers? Think again. Containers have recently gained massive industry adoption and many IT pros are now being asked to support this new disruptive technology. Are you in the know? Join us on April 24th for a very special webinar with the co-creator of Hyper-V, Microsoft’s very own Ben Armstrong. Andy Syrewicze from Altaro will be moderating this AMA-styled webinar with Ben to answer all your burning questions about containers in the Microsoft ecosystem. The discussion will include: Industry adoption of containers Container and micro-services examples Best practices for deployment The future of containers This webinar is a rare chance to ask your technology questions directly to Ben Armstrong drawing on special insights from the inner workings of Microsoft and over 20 years of experience working with operating systems and virtualization. It’s an opportunity you cannot miss! We look forward to seeing you there! sign up here
-
they should be as it's released to the slow ring - if you do have any issues post them here and we'll see what we can do
- 56 replies
-
- current branch
- sccm
-
(and 1 more)
Tagged with:
-
Hi, I first want to say thank you, for all of your articles they are wonderful and spot on. thanks i appreciate it ! Is there a reason to run this as "run another program first" versus the 1st thing in the task sequence? yes the reason we run another program first is because we don't want to 'start' the task sequence unless we are ready to do so, and therefore it's chained to the wrapper, i.e. the wrapper must exit with a code of 0 (no error) in order for the task sequence to start, also task sequences run as SYSTEM (not user) account, and this requires that the user is logged on and interacts (to defer)
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
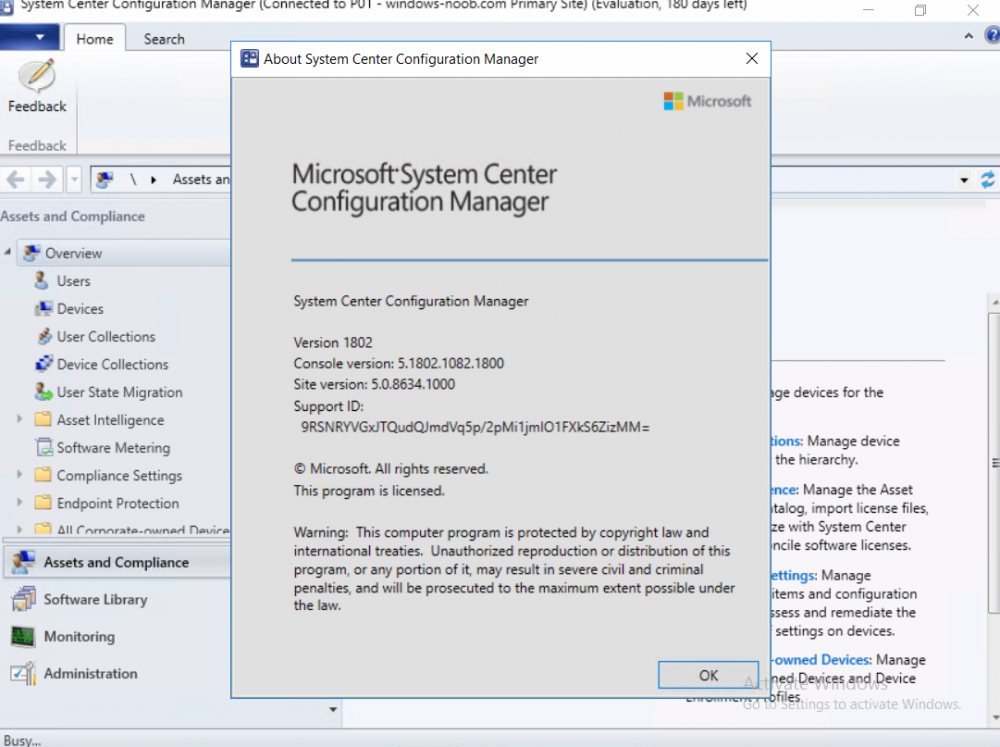
Introduction Microsoft recently release System Center Configuration Manager (Current Branch) version 1802. You can read the official announcement here and for a detailed list of what’s new, please see the following blog post. I blogged about how you can do the upgrade from start to finish here. If you want to get started with learning about System Center Configuration Manager (Current Branch) version 1802 you can follow my multi-part guide here, or even try labs for yourself using the 1802 eval media available at Microsoft’s eval site. The eval media is locked down to 180 days so it’s not suitable for use in Production. You can download the eval media from here. After signing up you can download the EXE and extract it. Click on Splash.hta to to start the installation wizard. Note that you’ll need the prerequisites installed and SQL server setup. You can follow my multi-part guide to help you with that. Once installed it will appear like so. Note: Do not confuse this media with the Baseline version media on VLSC. VLSC does not yet offer the production ready 1802 baseline version media at time of writing. Recommended reading How can I install System Center Configuration Manager (Current Branch) version 1802 on Windows Server 2016 with SQL Server 2017 – Part 1 How can I install System Center Configuration Manager (Current Branch) version 1802 on Windows Server 2016 with SQL Server 2017 – Part 2 Download eval version of System Center Configuration Manager and Endpoint Protection (current branch – version 1802) What are Baseline versions in System Center Configuration Manager (Current Branch)