-
Posts
9257 -
Joined
-
Last visited
-
Days Won
371
Everything posted by anyweb
-
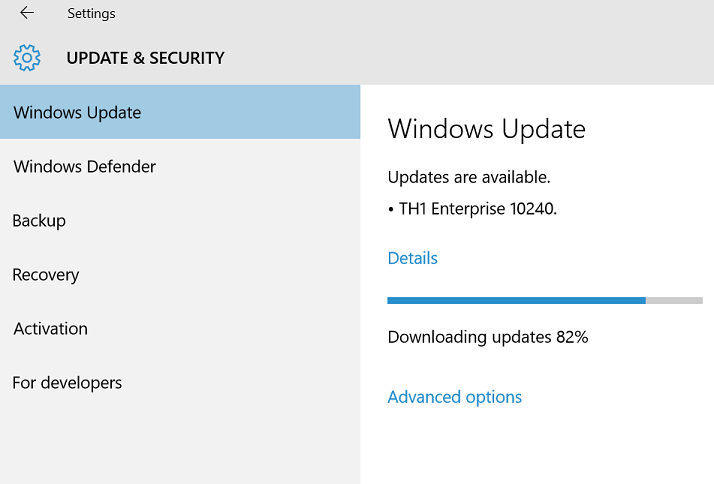
Yet another build of Windows 10, this time 10240 is available, and it's a TH build meaning threshold or 'very near to RTM'. and after the update is complete you get a new OOBE requiring you to accept the license terms, review the new apps like Microsoft EDGE and then accept the settings changes, once you login, the Watermark is gone, you can review the Windows version using winver in a cmd prompt. This build feels complete, even The Verge claims it might be the RTM release. You can read about the release here. http://blogs.windows.com/bloggingwindows/2015/07/15/build-10240-now-available-for-windows-insiders-in-fast-and-slow-rings/
-

OSD Windows 7x64 and UEFI partitioning
anyweb replied to jrgonzalez_nyc's topic in Configuration Manager 2012
my advice with UEFI is use UEFI designed os's for UEFI deployments and that would be Windows 8 and onwards, I've done Windows 7 deployments in UEFI mode and they are patchy at best, for example on lenovo's they work as long as CSM mode is enabled but Secure boot must be disabled as it's not Windows 7 aware, rather than struggle with Windows 7 and UEFI, why not just go for Windows 10 in UEFI mode ? -

OSD Windows 7x64 and UEFI partitioning
anyweb replied to jrgonzalez_nyc's topic in Configuration Manager 2012
yup, and if you look at your log it looks ok <![LOG[successfully completed the action (Partition Disk 0 - UEFI) with the exit win32 code 0]LOG]!><time="12:55:10.084+420" date="07-13-2015" component="TSManager" context="" type="1" thread="560" file="instruction.cxx:830"> so... what happens after this ? are you sure it's failing at this point, can you press f8 when it's failing and verify that you are capturing the log from x:\windows\temp\smstslog\smsts.log -

OSD Windows 7x64 and UEFI partitioning
anyweb replied to jrgonzalez_nyc's topic in Configuration Manager 2012
well the disks are in legacy non-gpt mode so i think that's causing issues, are you starting the task sequence in windows or via PXE ? -

OSD Windows 7x64 and UEFI partitioning
anyweb replied to jrgonzalez_nyc's topic in Configuration Manager 2012
are you starting this in Windows ? and is the system in UEFI mode or LEGACY mode prior to running the task sequence ? -
your hta is not showing as it's running as system and therefore hidden from the user (you) try running it with serviceUI.exe from the mdt 2013 toolkit and it will work just fine (in Windows) to find out how to use serviceUI.exe see this post
-

Introducing the windows-noob.com FrontEnd HTA ver 1.0
anyweb replied to anyweb's question in Frontends, HTA's and Web Services
yup i'll do that -
Microsoft have released yet another new Windows 10 build prior to the release of the OS on July 29th. Here's the press release below: "We have a new build for PCs we’re releasing today to Windows Insiders in the Fast ring – Build 10166. Just like the 3 builds we released last week, this build is all about bug fixing and fit-and-finish. Be sure to keep using the Windows Feedback app to send us feedback on any problems you’re hitting to help us make sure Windows 10 is awesome when we release it on July 29th! We also have something for you to try out if you live in the Seattle area. With Windows 10, we are giving people the ability to purchase paid Wi-Fi through the Windows Store via the Microsoft Wi-Fi app. You will know when you can purchase Wi-Fi when you see “Buy Wi-Fi from Windows Store” in your list of networks when clicking on the network icon on the lower right in the Taskbar. The Microsoft Wi-Fi app provides the choice to pay with a Credit or Debit Card, a Microsoft Gift Card, or PayPal and it helps keep your information secure since it uses the Windows Store payment system. Completing the purchase is simple as there is no need to enter additional personal or payment information if you’ve already registered in Windows Store. Right now, we’re testing this experience out in Seattle but it’ll soon open up to the rest of the U.S. We also have a corresponding Windows 10 SDK preview release with this build. The Building Apps for Windows blog will go into details on the change log. As always, you can download the latest Windows SDK and mobile emulator from the Windows 10 Developer Tools page. For those of you on older builds – now is definitely the time to upgrade to the most current build. Grab 10166 from Windows Update today or build 10162 ISOs from the Windows Insider Program website. Thank you to all of our Windows Insiders who have given us terrific feedback and helped us shape Windows 10. We’re getting close to release now and the whole team here is working hard and incredibly excited!" via > http://blogs.windows.com/bloggingwindows/2015/07/09/announcing-windows-10-insider-preview-build-10166/
-

Introducing the windows-noob.com FrontEnd HTA ver 1.0
anyweb replied to anyweb's question in Frontends, HTA's and Web Services
i havent tested it with Technical Preview 2 but if i do so i'll let you know, you should really look at the latest version of this frontend and it's here. CM12 in a Lab - The CM12 UEFI BitLocker FrontEnd HTA - Part 2. Installation CM12 in a Lab - The CM12 UEFI BitLocker Frontend HTA - Part 1. The features. -

Introducing the windows-noob.com FrontEnd HTA ver 1.0
anyweb replied to anyweb's question in Frontends, HTA's and Web Services
which versions do you mean, please be specific -

Deploying apps via UDI - Issues!
anyweb replied to MorsePacific's topic in Configuration Manager 2012
logs logs logs, i know it's frustrating to have these issues but without logs what can we do, please attach zipped copies of your SMSTS*.log and app*.log -

How to make the .wim of Windows 7 for Pre installed software.
anyweb replied to niyaz Ahmed's question in Windows Deployment Services
use mdt 2013 to create your master image, (reference image) Johan and Mikael have many example blog posts about doing this, heres a sample. http://deploymentresearch.com/Research/Post/357/Building-reference-images-like-a-boss -
have you tried redistributing the image to the distribution point ?
-

0x80070002 For OSD deployment after 2012 R2 SP1 upgrade
anyweb replied to wing5wong's topic in Configuration Manager 2012
how about posting the smsts.log file so we can take a look -

Can't create capture media - error code 0x8001010e
anyweb replied to nhottinger's topic in Configuration Manager 2012
have you tried doing this on a computer with antivirus disabled ? -

SCCM 2012 R2 and MBAM 2.5 Integration Hw Inventory Problem
anyweb replied to JazYO.o's question in How do I ?
why are you running mofcomp on it, have you seen the instructions here ?\ https://technet.microsoft.com/en-us/library/dn656927.aspx and https://technet.microsoft.com/en-us/library/dn645321.aspx these are two SEPARATE mof files, and that's important, one you append to your mof file in <CMInstallLocation>\Inboxes\clifiles.src\hinv\ and the other you import to your clients via default client settings, so, have you done that ? -
yes of course, but how you build that windows 7 vm is what you have to decide, do it manually (not a good idea), do it automated using MDT 2013 (recommended) or use Configuration Manager 2012 to build it, (recommeded provided that you have that infrastructure in place)
-

How to make the .wim of Windows 7 for Pre installed software.
anyweb replied to niyaz Ahmed's question in Windows Deployment Services (WDS)
you should use MDT, but if you insist on using WDS itself, then read this -
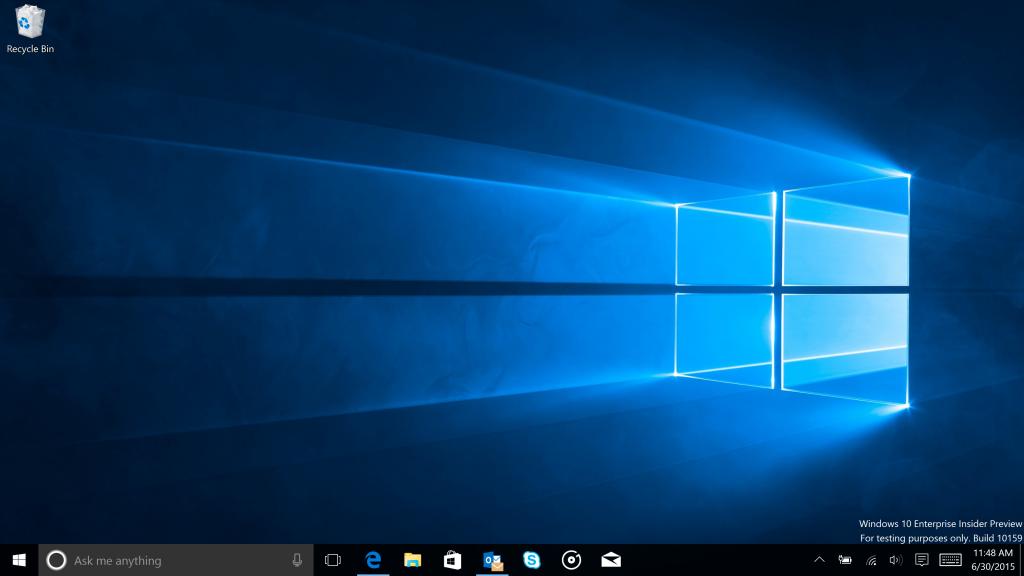
Just when I got my build 10158 Upgrade and New Computer scenario task sequences done, Microsoft releases..... build 10159 ! The new build has 300 bug fixes since build 10158 and a new wallpaper too (that one where they spent half a trillion US dollars on making the video which turned into a BMP), well ok, it wasn't quite that expensive, but it was a nice result :-) I nearly forgot, the blog post announcing the new build is right here http://blogs.windows.com/bloggingwindows/2015/06/30/whoa-another-pc-build/ get it, install it, deploy it, use it ! Windows 10 ftw :-)