-
Posts
9249 -
Joined
-
Last visited
-
Days Won
369
Everything posted by anyweb
-
hi, this morning I performed a site upgrade (security update to version 4.2.4) which completed successfully (according to the upgrade process), except, it didn't. As a result, new users could not join, and people could not reply to posts or edit posts or start new posts, this affected users throughout Europe, Middle-East and Africa, but was resolved a few hours ago so US users probably didn't notice. I apologize for any inconvenience caused by this downtime, on the plus side, all blog posts (and other posts) were still readable during this time thanks to @hybrid (Peter) for fixing the problem this evening, cheers niall
-
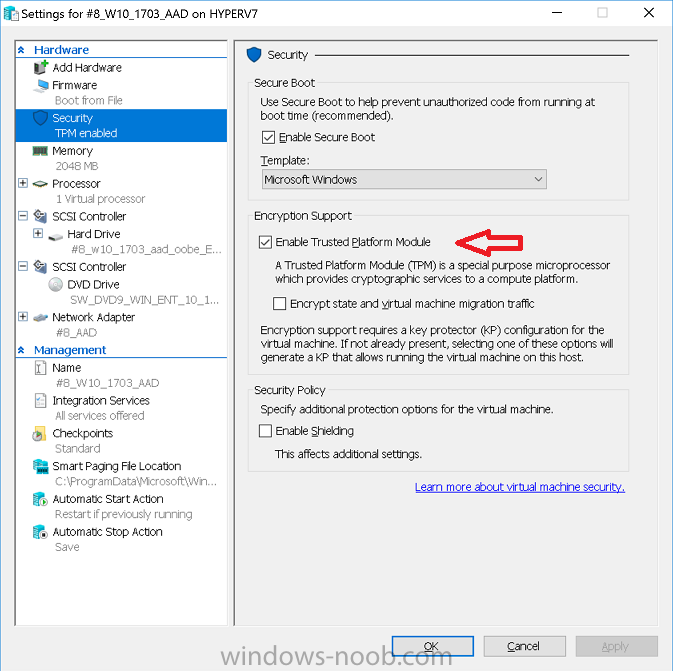
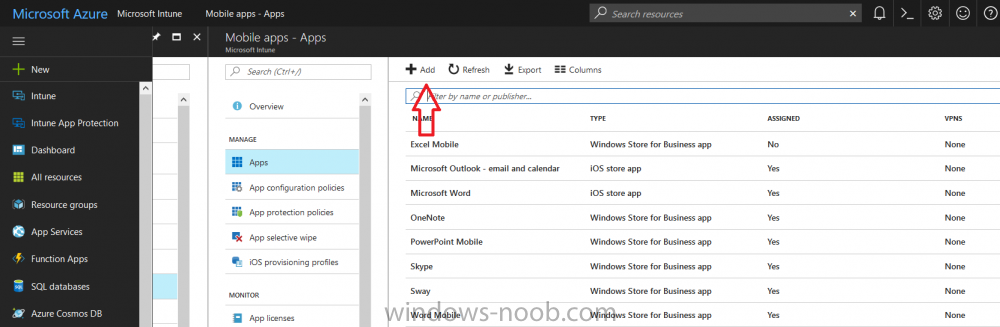
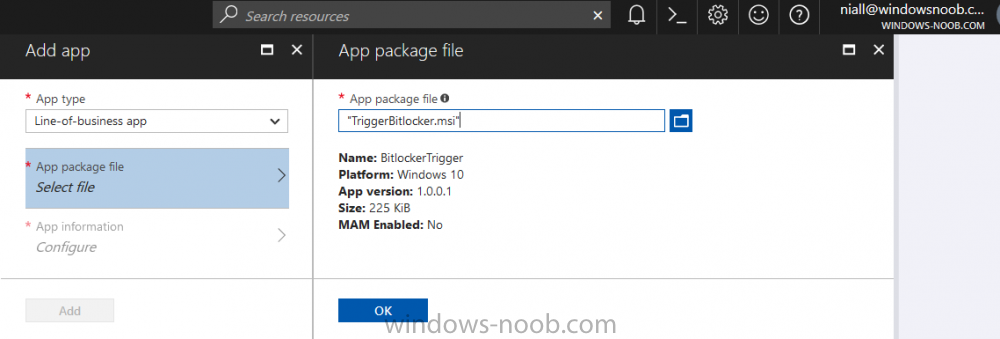
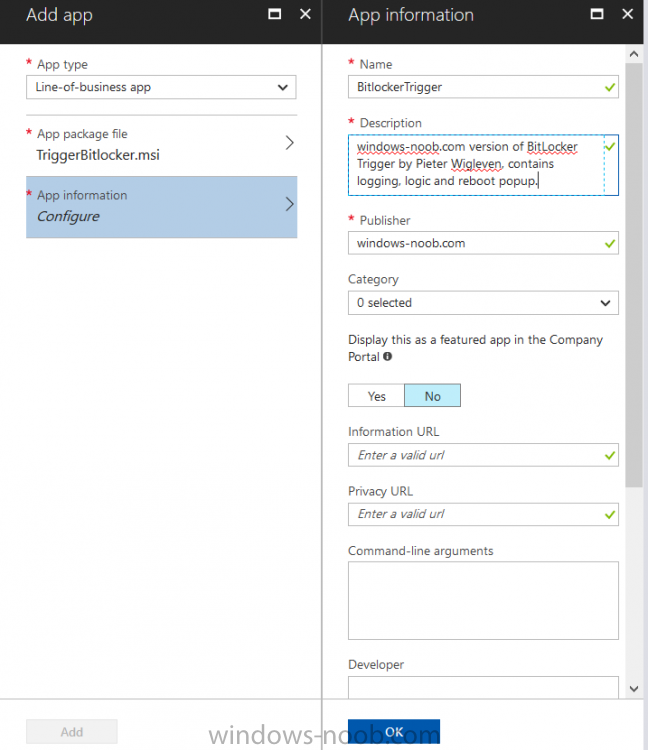
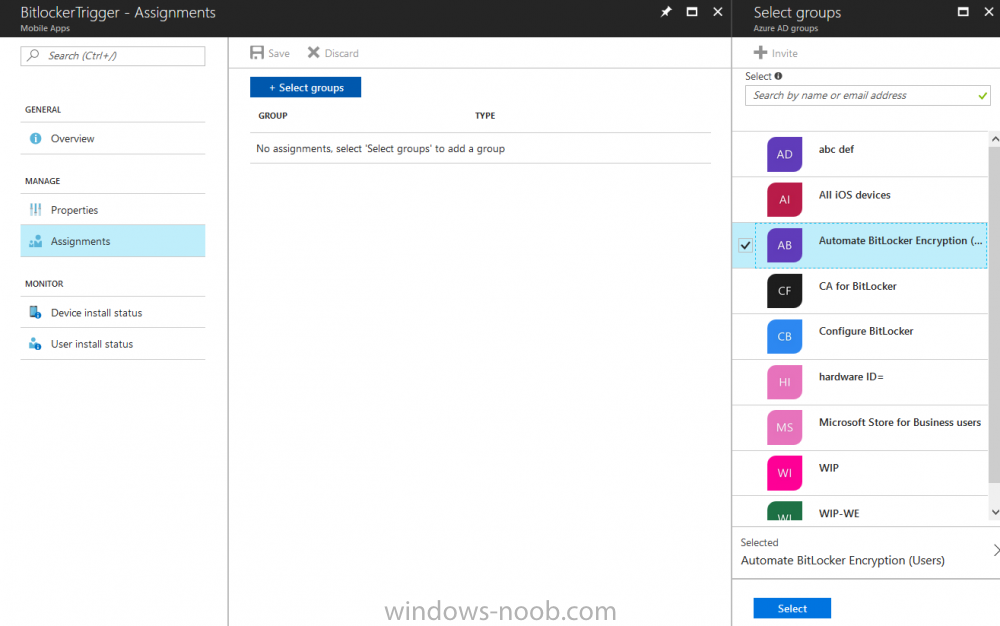
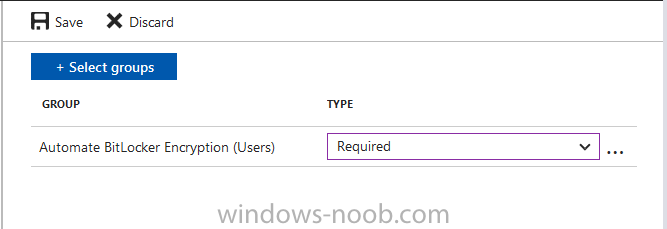
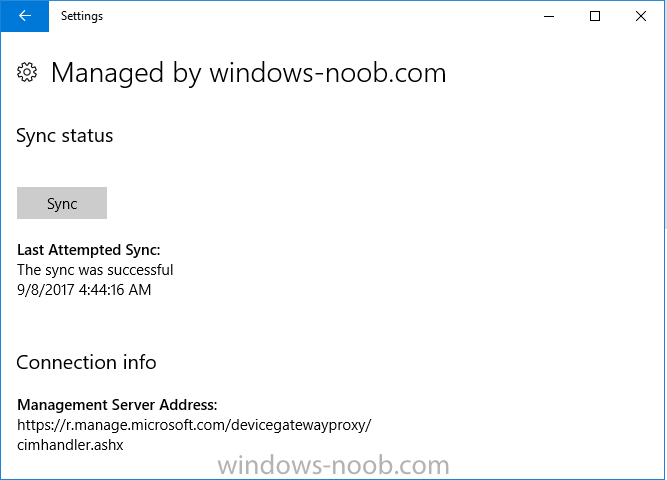
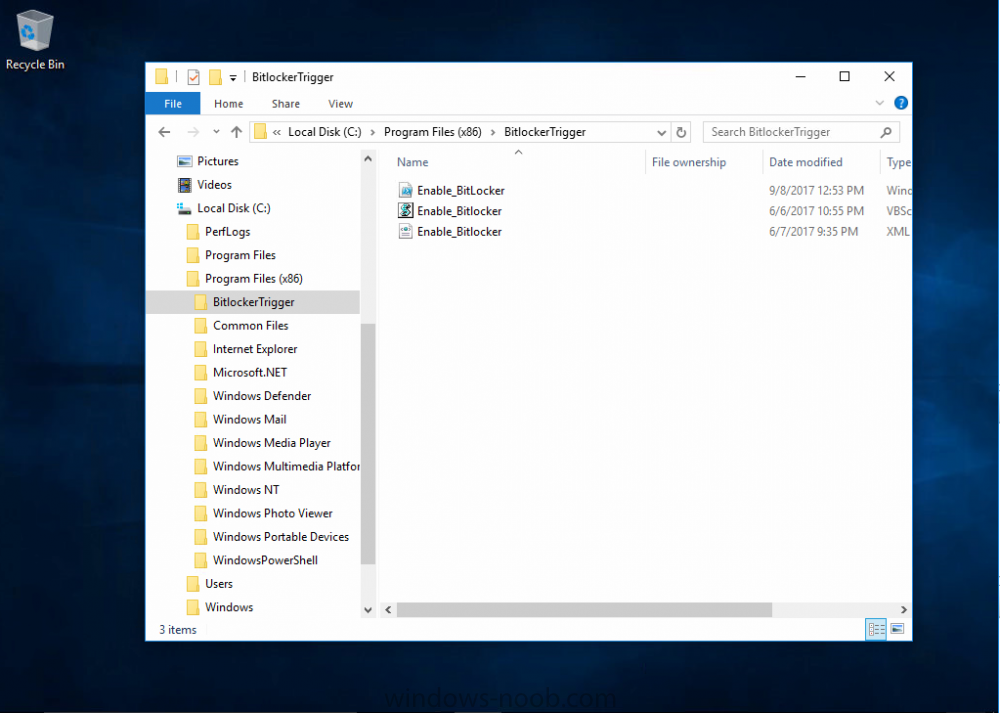
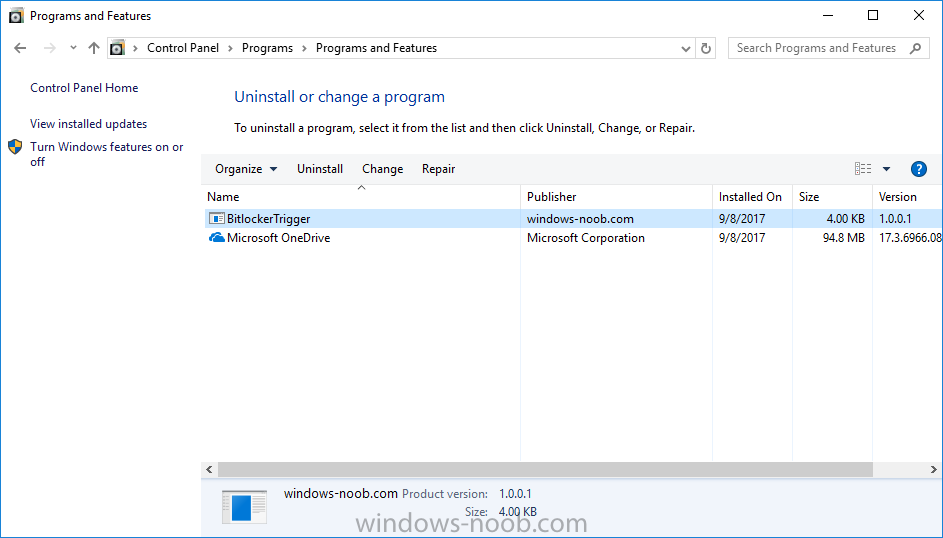
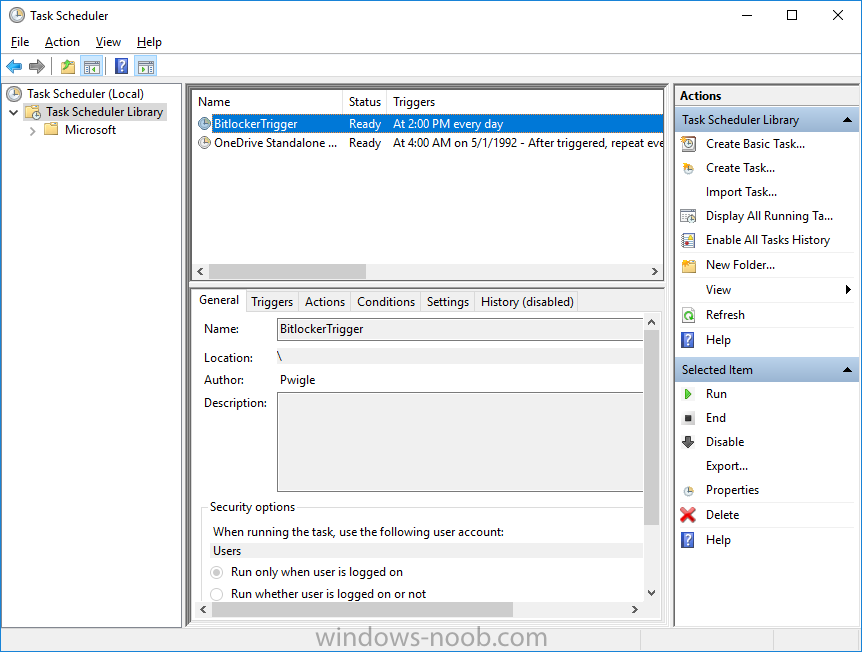
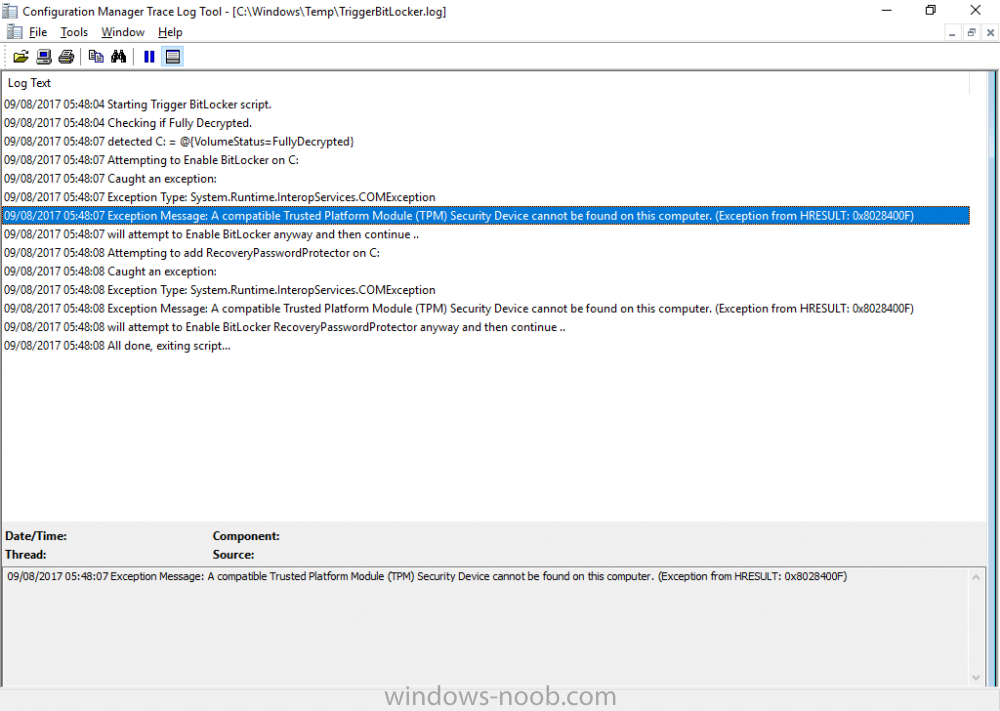
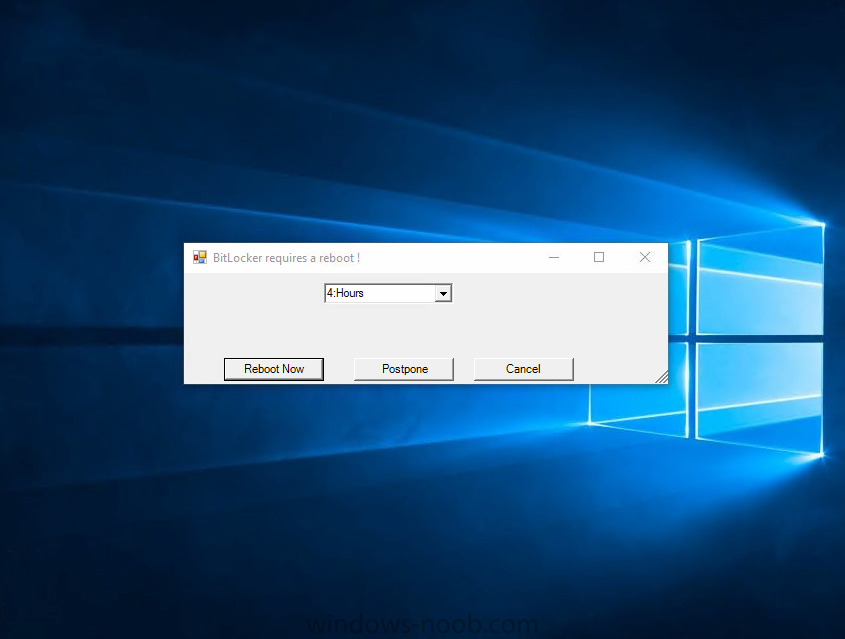
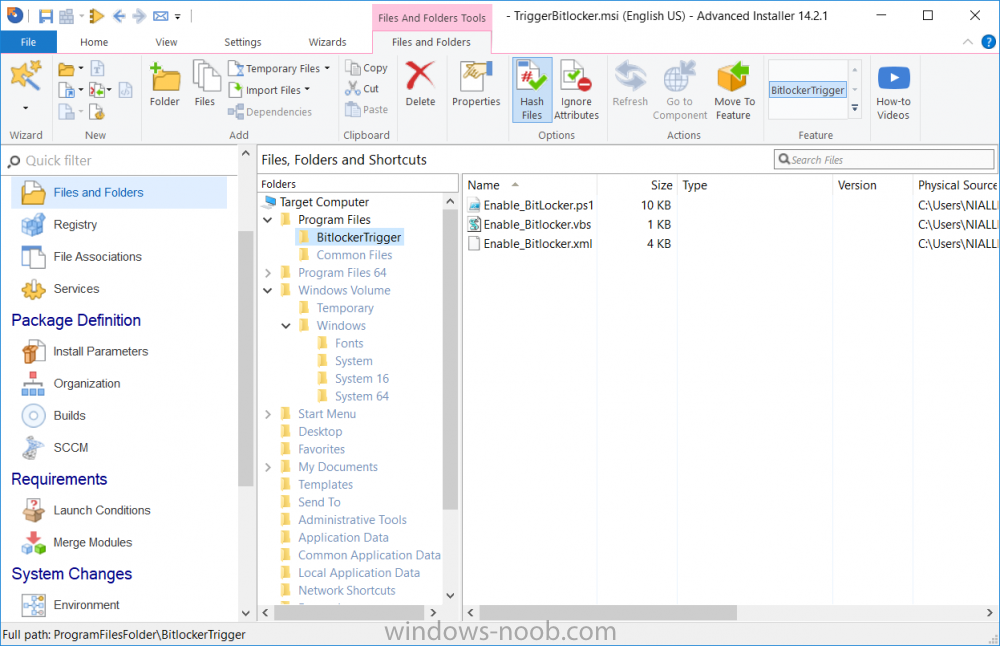
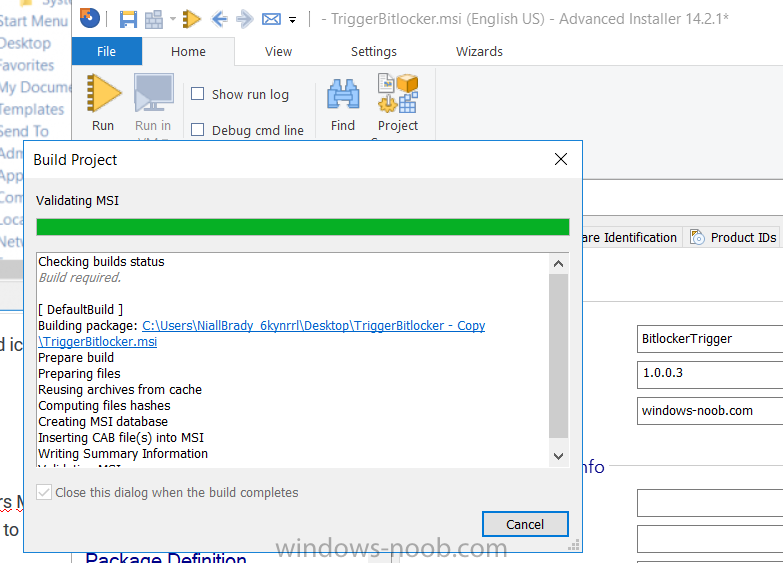
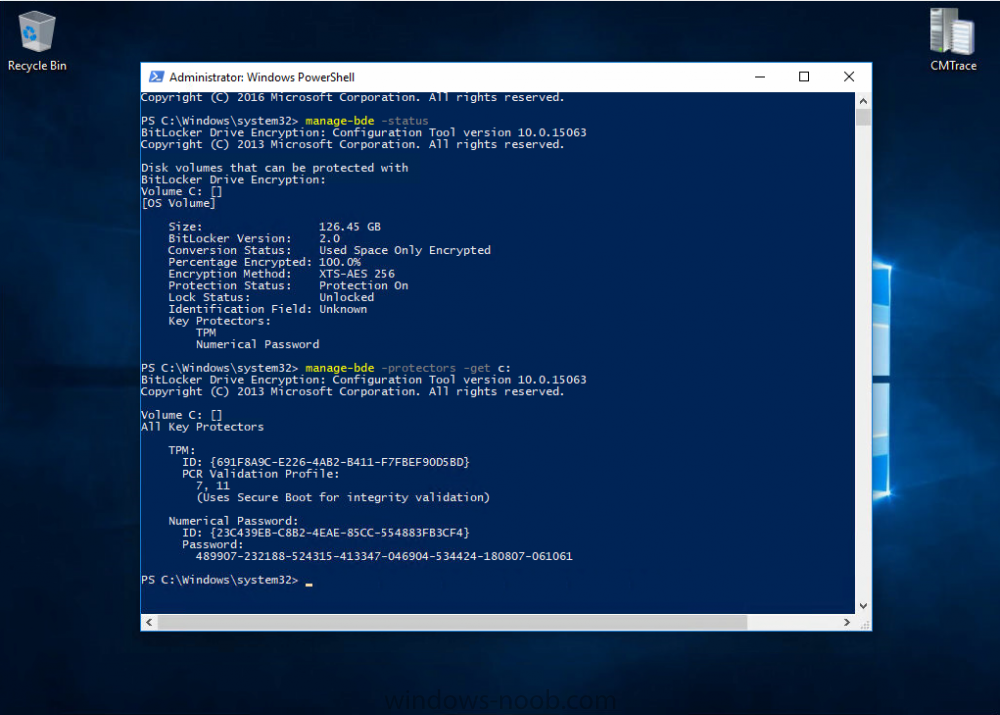
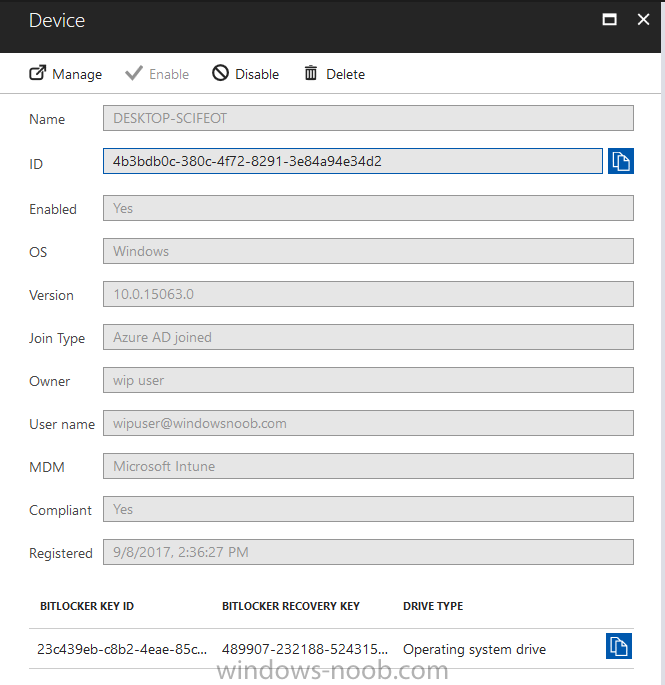
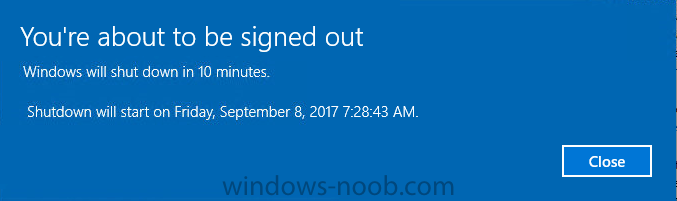
Introduction In Part 1 I showed you how you can configure BitLocker on Windows 10 devices using Microsoft Intune, but that method relies on the end user actually clicking on the notification in Windows and then continuing through the wizard until completion. In this post I'll show you how you can automate that part of the process, using an MSI that is based upon an MSI that was originally created by Pieter WigLeven. That MSI creates a scheduled task to run daily until the drive is encrypted. Pieter's solution was great but lacked some key features that I wanted such as logging (so that you can view errors which may occur during the encryption phase), logic and a user facing reboot prompt. Therefore, I decided to rewrite the PowerShell script included in the MSI and then re-package it for your benefit. Note: I'd recommend you test this solution in a lab environment, I used Windows 10 version 1703 Hyper-v based virtual machines (Generation 2) with a Virtual TPM enabled. Also to note, this MSI (and Pieters) does not check for the existance of a third party encryption tool, if you want that functionality then you'll need to modify the PowerShell script accordingly and then repackage it as described in Step 5. Enabling a Virtual TPM If you use Hyper-v VM's without a Virtual TPM enabled then the PowerShell script will exit logging errors and will not start the encryption. You can enable the Virtual TPM in the Security settings of your virtual machine (shown in the screenshot below) by placing a check mark in Enable Trusted Platform Module. Step 1. Download the MSI Note: In this guide I've used the windows-noob.com version of the MSI. I've modified the MSI as described in Step 5 and made it available in the Downloads section of this Guide, it includes new features such as Detailed logging Logic to check if encryption was enabled Reboot notification for end users Automatically remove the scheduled task once encryption is enabled You can get the the windows-noob.com version of the MSI in the Downloads section of this guide (scroll down....) or you can get the original MSI from Pieter. Keep in mind that if you are doing Azure AD join, that the user is automatically an Administrator, if however you are using Windows Autopilot then the user will not be an Administrator. The windows-noob.com version of the tool is based on the user being an Administrator. Step 2. Add the MSI as a LOB app in Intune Now that you have the MSI available, it's time to upload it into Intune. In the Intune service in Azure, select Mobile Apps, then Apps, then click on + Add to add an App. Select Line of Business app in the drop down, then select Select file and point it to the downloaded MSI file before clicking on OK. Next click on App Configuration and fill in some details about the application before clicking on OK finally click on Add. Step 3. Assign the app as Required to a User Group Next you will deploy the application (Assign) to a group of Users. In this guide I've created an Assigned User Group called Automate BitLocker Encryption (Users) which contains users that I want to target with this policy. Click on Assignment, then click on Select Groups, select the User Group you created previously and then click on Select. For Type, click on the dropdown and select Required and then click on Save. This will mean that any users in this User Group will be targeted by this required application and it will automatically download and run. Step 4. Verify the experience On a Windows 10 computer that is not yet BitLockered (and not encrypted by any third party encryption), Logon as a user that is a member of the above User Group. Keep in mind that they also need to have received the BitLocker Configuration created in Part 1 of this guide. That policy will set the BitLocker Configuration options (such as Encryption Algorithm), but it will not start encryption automatically. Trigger a Sync using the appropriate button. This will pull down the new policy and start the download and installation of the MSI which in turn will copy some files, and create a scheduled task. Once policy is received, you can see that the application is installed in Control Panel And three files are present in the File System at C:\Program Files (x86)\BitLockerTrigger. Note: The VBS kicks off the PowerShell script and the XML file is used in the creation of the Task Scheduler task. You can also check Task Scheduler to see the task is added, and that it is scheduled to run at 2pm. Tip: By default Windows Task Scheduler has the History tab disabled by default, to enable it you must start Task Scheduler as Administrator (Run as Administrator) and then click on Enable All Tasks History in the right pane. This will give you some details about the running task and whether it did run or not, but for more details about the task review the TriggerBitLocker.log file as described below. Running the Task You can wait until 2pm for the scheduled task to run or right click on the task and choose Run to run it now. after it has run, if everything was ok it will popup a reboot to the user, if things don't go according to plan use CMTrace.exe and navigate to C:\Windows\Temp and open the generated log file C:\Windows\Temp\TriggerBitLocker.log The log file should reveal any problems that occur. In the example below you can see what happens when you try to run the task on a computer without a TPM. The key takeaway here is that logging is now included with the MSI and the PowerShell logic will avoid popping up a reboot message to the end user in the event that it has not succeeded to enable Encryption. On a computer that meets the specifications (TPM), the PowerShell script enables encryption and the user will see the popup, they can delay for a few hours or accept the reality that they are getting Encrypted with BitLocker. and if they choose Reboot Now they'll see something like this After the reboot we can verify BitLocker encryption status and the recovery key is in Intune in Azure. job done ! Note: After successfully enabling BitLocker the script deletes the Scheduled Task so that it no longer re-runs. Step 5. (Optional) Edit the MSI with Advanced Installer If you'd like to update the MSI yourself, you can install the MSI on a vm, and pull the scripts from the folder shown above, then load it using Advanced Installer. Edit what you want in the package and edit the PowerShell script to suit your needs, once done copy the replacement scripts back into the MSI in the Files and Folders section below Once done, to build the package click on the Save icon in the ribbon. And use that compiled MSI in the guide above. Downloads Below is the windows-noob.com version of Pieters MSI, this version was compiled using Advanced Installer 14.2.1 (great product !) and contains improvements to the PowerShell script such as logic handling, logging to help with troubleshooting and a Reboot computer popup at the end of the script which only appears if encryption is enabled. windows-noob.com TriggerBitlocker.msi (version 1.0.0.2) - TriggerBitlocker.msi windows-noob.com TriggerBitLockerUser.msi (version 1.0.0.2TriggerBitlockerUser.msi Recommended reading Hardware independent automatic Bitlocker encryption using AAD/MDM https://blogs.technet.microsoft.com/home_is_where_i_lay_my_head/2017/06/07/hardware-independent-automatic-bitlocker-encryption-using-aadmdm/#comment-26696 Configuring BitLocker in Intune - Part 1. Configuring BitLocker https://www.windows-noob.com/forums/topic/15514-configuring-bitlocker-in-intune-part-1-configuring-bitlocker/ Download Advanced Installer http://www.advancedinstaller.com/download.html
-
if you've already extended the schema for ConfigMgr then you are good to go. to verify you can delete everything in the system mangement container using adsiedit and restart the sms_executive component, it should repopulate the system management container, if not it's not working or delegated correctly
-
yes you can, those workgroup machines can be Azure AD joined (and enrolled into MDM with Intune) or they can be simply workgroup machines enrolled into MDM or they can be workgroup machines that use MAM-WE
-
what does your smspxe.log tell you ? attach it here
-
On Microsoft's blog, they announced that RS3 (Redstone 3) aka Fall Creators Update is coming October 17th 2017. "Create and play this holiday with the Windows 10 Fall Creators Update coming Oct. 17" It offers the following new features Windows Inking Windows Inking keeps getting better, letting you ink directly onto PDF’s, making it easier and faster to comment and share with others, improving on what you could do with pen and paper alone. Smart Ink applies artificial intelligence to inking automatically making the squares you draw more perfect, or turning boxes into a table for you with no extra work. And you know how sometimes you can’t find your keys, wallet, and phone, sometimes it’s hard to find your pen to do the inking. Windows Find my Pen fixes that in the Fall Creators Update. Photos and Videos We have reimagined our Photos Application to deliver remixed experiences for telling your stories with photos, videos, music, 3D, and even inking. OneDrive Files On-Demand You can save all of your creations in OneDrive Files On-Demand, accessing your cloud files like any of your other files on your PC, without using up your local storage space. Gaming The fuel that often inspires creativity is play. With the Fall Creators Update, we’ve updated Game Mode, which allows your games to use the full processing power of your device as if it was an Xbox game console, right from a new button on the Game bar. And to take advantage of this power, we have a fantastic lineup of Xbox Play Anywhere games coming including, Cuphead, Forza Motorsport 7, Super Lucky’s Tale and Middle-earth: Shadow of War. And, if you love these Xbox play anywhere games, coming on November 7 you can play them on the most powerful console on the planet, Xbox One X. Security While you create and play, our goal is to keep you safe and secure. With the Fall Creators Update, Windows Defender is smarter and defends better than ever before. With behind the scenes cloud intelligence that enables new defenses against ransomware and exploits. I can’t talk about security without talking about Windows 10 S. Introduced last May, Windows 10 S is specifically designed for simplicity and security, with significant breakthroughs in battery life and performance. It’s off to a great start, with some of our highest customer satisfaction results yet. This is the core of Fall Creators Update, it’s all about unleashing your creativity and having some fun while at the same time keeping you safe and secure. Accessibility I also want to share some exciting new technology that speaks to our mission at Microsoft to create products which are inclusive by design. With the Fall Creators Update, we are making Windows more accessible for those with Lou Gehrig’s disease, a progressive neurodegenerative disease that impacts the brain’s ability to control your muscles. The one muscle it doesn’t impact, are the eyes. A new feature Eye Control implements incredible eye tracking technology that lets you type, and operate a mouse just using your eyes, this is life changing technology for those with Lou Gehrig’s disease. This is real advancement in accessibility that we are introducing to the world with the Fall Creators Update. Windows Mixed Reality Lastly, with the Fall Creators Update, we are enabling you to immerse yourself in a new reality, the world of Windows Mixed Reality. By combining our physical and digital worlds, we believe mixed reality is the next step in the evolution of human computing. For the first time, we are talking about a mixed reality system that fully immerses you in the experience not limited to a mobile device screen size. One that is easy to setup, not requiring you to mount cameras around the room, just put the headset on your head, plug it into your PC and get started, leaving your hands free to interact with the mixed world. It’s available from a wide range of partners around the world, like Acer, ASUS, Dell, HP, and Lenovo with headsets starting as low as $299. I am thrilled to announce that Windows Mixed Reality headsets will start to become available on October 17 when the Fall Creators Update ships. And if you find yourself without a headset, we will also deliver mixed reality experiences through the PC. With Mixed Reality Viewer, you can see 3D objects – either from the Remix3D.com community or your own creation from Paint 3D – mixed into your actual surroundings through your PC’s camera – and snapped and shared – for powerful ways to tell your story.
-

Boot Media - Now fails at network settings
anyweb replied to LOKI's topic in Configuration Manager 2012
try this script it will help