-
Posts
9254 -
Joined
-
Last visited
-
Days Won
369
Everything posted by anyweb
-
Just wanted to follow up and let you know I have had great success utilizing your script.. the error checking is superb.. thank you for the work and troubleshooting you have done to vet your script.. you are a life saver!! great to hear it ! and thanks for the kind words @Jerzystransfer
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-

Configuring BitLocker in Intune - Part 2. Automating Encryption
anyweb replied to anyweb's topic in Microsoft Intune
sure post your updated code here -
why are you still using and even considering moving SCCM 2012 SP2 into Azure ? this version of ConfigMgr is out of mainstream support and is on extended support currently. https://support.microsoft.com/en-us/lifecycle/search/1060 if you want to use ConfigMgr in Azure then you'll need to be on a Current Branch release see - https://docs.microsoft.com/en-us/configmgr/core/understand/configuration-manager-on-azure
-
can you give some details of what you were doing here exactly and what type of drive D:\ is ?
-
you also need to remove any encryption on those devices before implementing BitLocker.
-

IP Helper question
anyweb replied to twidener's topic in System Center Configuration Manager (Current Branch)
iphelpers should point to where you intend to PXE boot from, so from the local (nearest) distribution point hosting a WDS role -
it's trying to copy a file (CM_site.mdf), not a folder. is the file in the source and target location ?
- 14 replies
-
- mandatory profiles
- wondows 10
-
(and 36 more)
Tagged with:
- mandatory profiles
- wondows 10
- cb1910
- sccm
- cross-forest
- multi-domain
- sccm
- cmg
- azure
- sup
- client
- sccm
- dp
- office 365 updates
- query or collection in sccm
- gpo
- sccm cb
- database
- sccm cmdlets
- sccm client
- powershell
- wmi
- sccm
- client settings
- console
- dell
- 7212
- imaging
- osd
- defaultuser0
- configmgr
- sccm
- admin tools
- current branch
- manageengine
- patch connect plus
- configuration manager
- non microsoft updates
-
are you failing with the same errors as before ?
- 14 replies
-
- mandatory profiles
- wondows 10
-
(and 36 more)
Tagged with:
- mandatory profiles
- wondows 10
- cb1910
- sccm
- cross-forest
- multi-domain
- sccm
- cmg
- azure
- sup
- client
- sccm
- dp
- office 365 updates
- query or collection in sccm
- gpo
- sccm cb
- database
- sccm cmdlets
- sccm client
- powershell
- wmi
- sccm
- client settings
- console
- dell
- 7212
- imaging
- osd
- defaultuser0
- configmgr
- sccm
- admin tools
- current branch
- manageengine
- patch connect plus
- configuration manager
- non microsoft updates
-
well you cannot have two different disk encryption methods at the same time so if you want to move to BitLocker (good choice) then you'll first need to completely remove whatever encryption that McAfee has put in place. Once that is done and the McAfee agent is removed you can enforce BitLocker easily with Configuration Manager, check out my blog post here for guidance. https://www.niallbrady.com/2019/11/13/want-to-learn-about-mbam-integrated-with-microsoft-endpoint-manager-configuration-manager/
-
normally you should use service accounts, but in your case, your sccm login is probably what you need, try it...
- 14 replies
-
- mandatory profiles
- wondows 10
-
(and 36 more)
Tagged with:
- mandatory profiles
- wondows 10
- cb1910
- sccm
- cross-forest
- multi-domain
- sccm
- cmg
- azure
- sup
- client
- sccm
- dp
- office 365 updates
- query or collection in sccm
- gpo
- sccm cb
- database
- sccm cmdlets
- sccm client
- powershell
- wmi
- sccm
- client settings
- console
- dell
- 7212
- imaging
- osd
- defaultuser0
- configmgr
- sccm
- admin tools
- current branch
- manageengine
- patch connect plus
- configuration manager
- non microsoft updates
-
what account was used before with the database mentioned ?
- 14 replies
-
- mandatory profiles
- wondows 10
-
(and 36 more)
Tagged with:
- mandatory profiles
- wondows 10
- cb1910
- sccm
- cross-forest
- multi-domain
- sccm
- cmg
- azure
- sup
- client
- sccm
- dp
- office 365 updates
- query or collection in sccm
- gpo
- sccm cb
- database
- sccm cmdlets
- sccm client
- powershell
- wmi
- sccm
- client settings
- console
- dell
- 7212
- imaging
- osd
- defaultuser0
- configmgr
- sccm
- admin tools
- current branch
- manageengine
- patch connect plus
- configuration manager
- non microsoft updates
-
look in SQL under logins, see what logins are there, add your account as SQL SysAdmin if you are not sure what to do
- 14 replies
-
- mandatory profiles
- wondows 10
-
(and 36 more)
Tagged with:
- mandatory profiles
- wondows 10
- cb1910
- sccm
- cross-forest
- multi-domain
- sccm
- cmg
- azure
- sup
- client
- sccm
- dp
- office 365 updates
- query or collection in sccm
- gpo
- sccm cb
- database
- sccm cmdlets
- sccm client
- powershell
- wmi
- sccm
- client settings
- console
- dell
- 7212
- imaging
- osd
- defaultuser0
- configmgr
- sccm
- admin tools
- current branch
- manageengine
- patch connect plus
- configuration manager
- non microsoft updates
-
check the username/password specified in sql, that's where it's failing, see below snippet... ERROR: Failed to restore databases. $$<Configuration Manager Setup><12-13-2019 14:41:31.500+00><thread=3800 (0xED8)> *** [28000][18456][Microsoft][SQL Server Native Client 11.0][SQL Server]Login failed for user 'sitename\user'. cheers niall
- 14 replies
-
- mandatory profiles
- wondows 10
-
(and 36 more)
Tagged with:
- mandatory profiles
- wondows 10
- cb1910
- sccm
- cross-forest
- multi-domain
- sccm
- cmg
- azure
- sup
- client
- sccm
- dp
- office 365 updates
- query or collection in sccm
- gpo
- sccm cb
- database
- sccm cmdlets
- sccm client
- powershell
- wmi
- sccm
- client settings
- console
- dell
- 7212
- imaging
- osd
- defaultuser0
- configmgr
- sccm
- admin tools
- current branch
- manageengine
- patch connect plus
- configuration manager
- non microsoft updates
-
thanks for sharing, please do let me know how you get on with this.
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
hiya i didn't see that problem (see part 2 of my videos here) https://www.niallbrady.com/2019/12/10/learn-about-mbam-integration-in-microsoft-endpoint-configuration-manager-version-1910-part-2-configure-portals/ however i have one lab with the cert issue you reported on technet and your workaround didn't work for me, fyi cheers niall
-
thanks! yes you could check for the ip range that your network cables use (as opposed to wireless), and detect based on that, all networks are different so you'll have to customize it somehow to suit your environment cheers niall
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
thanks for the thanks,. first thing though, is your 1910 lab in HTTPS mode ? if not you cannot use MBAM integration, it must be in HTTPS mode. if you need help with https mode see the following links, i converted one of my labs from http to https yesterday using these guides, it's not that hard if you pay attention to the guides: *to learn how to setup PKI and convert MEM CM from HTTP to HTTPS see https://windows-noob.com/forums/topic/16252-how-can-i-configure-pki-in-a-lab-on-windows-server-2016-part-1/ and then once complete, do this https://windows-noob.com/forums/topic/16300-how-can-i-configure-system-center-configuration-manager-in-https-mode-pki-part-1/
-
thanks Harley, i'll update it shortly ! as regards Part 8, it's on my ever growing to-do list, thanks for reminding me
- 24 replies
-
This Holiday Season, Altaro is helping you out with your Holiday Shopping: they’re giving you the chance to WIN fantastic gifts that you can give to your loved ones! It’s no secret that Holiday shopping can be stressful and very time-consuming. So this year, whether you need a present for your partner, your children, your parents and in-laws, or your friends… Altaro’s got your back. Enter and share it on socials for a chance to WIN one of the Grand Prizes: a Holy Stone GPS FPV RC Drone HS100, an All-Access MasterClass pass, Lomography Lomo’Instant San Sebastian, an Echo Plus (Smart Home Hub), a Wii Console & Mario Kart for Wii, 2x Netflix Gift Cards of $100 each, and a JBL Clip Portable Waterproof Speaker. And guess what? For any eligible subscription they give you a guaranteed Amazon voucher! So, if you are a Hyper-V or VMware user, download Altaro’s VM Backup and follow the instructions you will find over here to WIN these exciting prizes! Good luck & Happy Holidays!
-

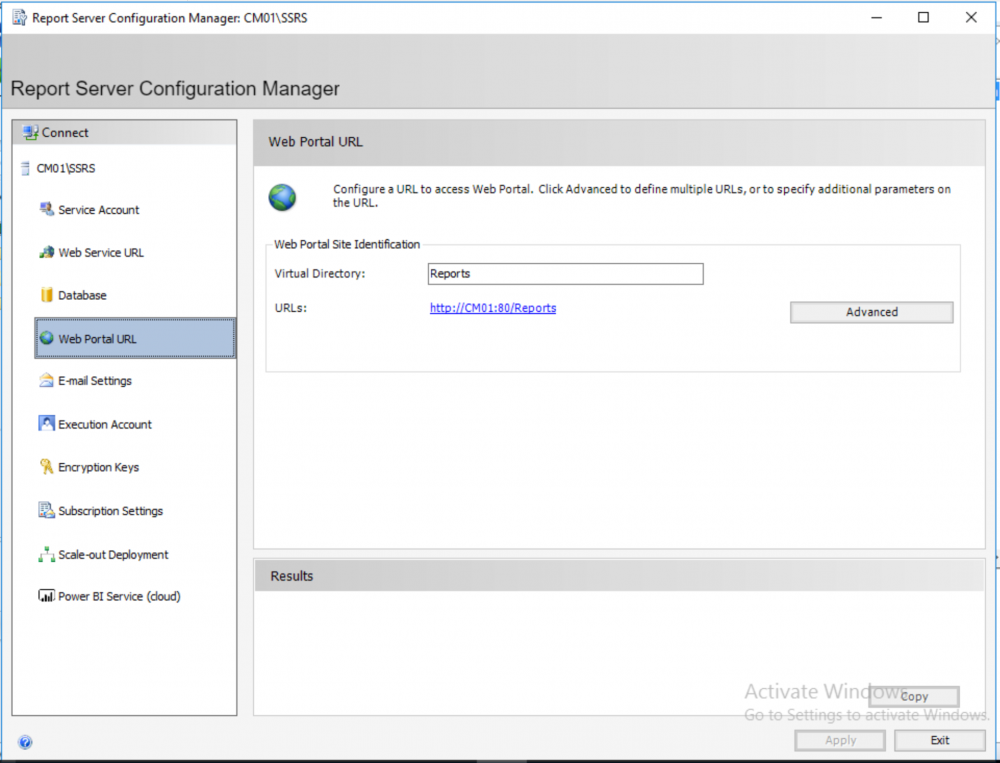
SCCM OSD Application upgrade
anyweb replied to Kevin79's question in Deploy software, applications and drivers
yes of course it's possible, and you've already figured it out




.thumb.png.78beb3234f9a981e2bc8eb4419509516.png)