Peter33
Established Members-
Posts
755 -
Joined
-
Last visited
-
Days Won
30
Peter33 last won the day on March 20 2021
Peter33 had the most liked content!
Profile Information
-
Gender
Male
-
Location
Germany
Recent Profile Visitors
The recent visitors block is disabled and is not being shown to other users.
Peter33's Achievements
Newbie (1/14)
48
Reputation
-
santosh250201 started following Peter33
-
Both, the Dell and the Lenovo Update Agents are prime examples of bad programming and usage of WMI. #1 - they are hogging the client CPU for several hours during each scan #2 - the automatic driver selection is awful. Instead of using the newest driver for the device, every matching driver will be installed. #3 - they require huge amounts of disk space on the server side which triples with SCCM (download source, WSUS content, Package source) #4 - you can't use the BIOS updates if your clients are Bitlocker enabled Overall it was one of the worst experiences fo my past SCCM years. Cleaing up the WSUS after getting rid of 3rd party patching has been a pain too.
-
Find Differences in Security Roles
Peter33 replied to rdr222's topic in System Center Configuration Manager (Current Branch)
There is always Powershell ... Import-Module -Name "$(split-path $Env:SMS_ADMIN_UI_PATH)\ConfigurationManager.psd1" $SiteCode = Get-PSDrive -PSProvider CMSITE Set-Location "$($SiteCode.Name):" #################################### $server = 'sccm01' # MECM Primary Server Name $role1 = 'Company Resource Access Manager' # Security Role Name $role2 = 'Compliance Settings Manager' # Security Role Name $DiffOnly = $false # change to $true to show differences only #################################### $ns = 'root\SMS\Site_'+$SiteCode function _getRoles{ Param( [parameter(position=0)] [string] $role ) $props = (Get-CMSecurityRole -Name $role -ErrorAction SilentlyContinue | Select *).Properties $rules = [System.Collections.Generic.List[psobject]]::new() $props.Operations | ForEach-Object { $ops = $_.GrantedOperations $typeId = $_.ObjectTypeID $BitMask = [convert]::ToString($($ops),2) $BitMaskReverse = ([regex]::Matches($BitMask,'.','RightToLeft') | ForEach {$_.value}) -join '' 0..($BitMaskReverse.Length - 1) | ForEach-Object{ if($BitMaskReverse.Substring($_, 1) -eq 1){ $BitFlag = [math]::Pow(2, $_) $result = Get-CimInstance -Namespace $ns -Query "SELECT * FROM SMS_AvailableOperation WHERE ObjectTypeID=$typeId and BitFlag=$BitFlag" -ComputerName $server $rules.AddRange(@([pscustomobject]@{TypeName = $result.ObjectTypeName; OperationName = $result.OperationName}) -as [psobject[]]) } } } return $rules } $r1 = _getRoles $role1 | Sort-Object -Property TypeName, OperationName $r2 = _getRoles $role2 | Sort-Object -Property TypeName, OperationName function _normalizeList{ Param( [parameter(position=0)] [System.Collections.Generic.List[psobject]] $list ) $tmp = @{} $list.TypeName | Get-Unique | ForEach-Object { $tn = $($_) $val = ($list | Where-Object {$_.TypeName -eq $tn}).OperationName -join ',' $tmp.Add($tn,$val) } return $tmp } $list1 = _normalizeList $r1 $list2 = _normalizeList $r2 $allkeys = $list1.Keys + $list2.Keys | Sort-Object | Get-Unique $final = [System.Collections.Generic.List[psobject]]::new() foreach($key in $allkeys){ if($list1[$key]){ $val1 = $list1[$key] } else{ $val1 = '' } if($list2[$key]){ $val2 = $list2[$key] } else{ $val2 = '' } if($DiffOnly -eq $false -or $val1 -ne $val2){ $final.AddRange(@([pscustomobject]@{TypeName = $key; $($role1) = $val1; $($role2) = $val2}) -as [psobject[]]) } } $final | Out-GridView -
Hello Jesse, i just put that idea into a tiny script because that is something i will be end up using too. So thank's for the idea. Just create a daily scheduled task that runs the script. ##################################################################################################################### $rserver = 'smtprelay.mydomain' # your smtp relay server $rport = '25' # your smtp relay server port $from = 'sccm@mydomain' # make sure to edit mydomain $to = 'my.name@mydomain' # your email address here $subject = "IIS Certificate of $env:COMPUTERNAME expires soon" $body = "The IIS certificate of $env:COMPUTERNAME is about to expire soon (xxx). Time to wake up mate." $ipport = '0.0.0.0:443' # modify if you need to $days = '30' # grace period before the script starts bothering you ###################################################################################################################### $warn = (Get-Date).AddDays($days) $cmd = [string]"& netsh http show sslcert ipport={0}" -f $ipport $certhash = (((Invoke-Expression $cmd | Where-Object {$_ -match 'Certificate Hash'}) -split ':')[1]).trim() $cert = Get-ChildItem Cert:\LocalMachine\My -ErrorAction SilentlyContinue | Where-Object {$_.Thumbprint -eq $certhash} $certexpire = $cert.NotAfter if($certexpire -le $warn){ $body = $body -replace 'xxx', $cert.NotAfter Send-MailMessage -SmtpServer $rserver -Port $rport -Subject $subject -From $from -To $to -Body $body } So long Peter
- 1 reply
-
- certificate
- ssl
-
(and 2 more)
Tagged with:
-
Hi Martinez, if you are running a Proxy server in your environment run these command on your Management Point in an admin cmd. netsh winhttp set proxy proxy.fqdn:port "<local>;*.fqdn" bitsadmin /util /setieproxy localsystem NO_PROXY bitsadmin /util /setieproxy localsystem proxy.fqdn:port "<local>;*.fqdn" iisreset I was struggeling with the same problem for a long time. The IIS server has some serious problems when the IEProxy for local system is configured with AUTODETECT. That can result in various errors in Config Manager. The settings above also fixed my installation errors for MDOP Bitlocker and Cache Server for delivery optimization. So long Peter
-
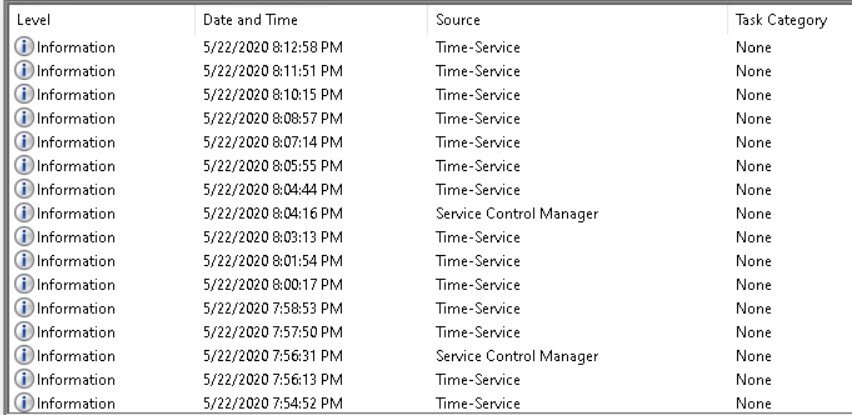
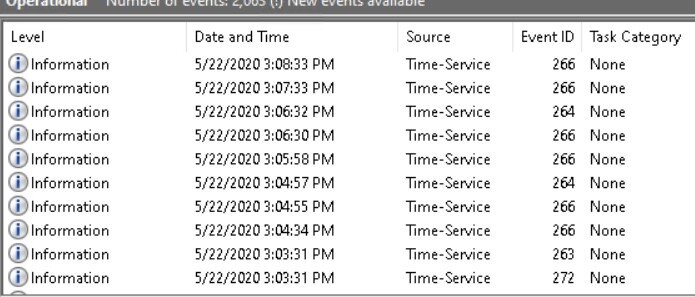
Hi fellow ConfigManager-Admins, after testing the Delivery Optimization option in Config Manager 19010/2002 for the last 2 month at one of our locations, i stumbled across this very strange and annoying behavior on our Windows 10 clients. As soon as you apply the setting to activate Delivery Optimization on the client the W32time service gets reconfigured to sync each and every minute with the configured time server. I'm not sure if that's the intended setting or just an oversight of the development team. The event log gets flooded with tons of entries and the domain controller bombarded with sync requests. Can someone verify this behavior? So long Peter
-
OSD ERROR
Peter33 replied to SHASHIDUBEY01's topic in System Center Configuration Manager (Current Branch)
Hello Shashi, you're very welcome and stay safe yourself too. So long Peter -
OSD ERROR
Peter33 replied to SHASHIDUBEY01's topic in System Center Configuration Manager (Current Branch)
Hello Shashi, Since you already have configured the PKI Option, you should not chose to activate self signed certs also. Especially if you are planning to use the Co-management option later on. This also goes for the CRL option if your CRL is not published to the Internet. The Configuration in your Screenshot covers only the Management Point configuration. You still need to configure the Web Server certificate and a client certificate for your PE boot images. Make sure that you follow Nialls instructions to the letter and you will be fine. -
OSD ERROR
Peter33 replied to SHASHIDUBEY01's topic in System Center Configuration Manager (Current Branch)
Make sure you have a valid certificate bound to your IIS default site for the Distribution Point. -
I was able to fix the problem by editing the installer script. Just added a session variable to avoid the proxy. https://social.technet.microsoft.com/Forums/en-US/1ff999c3-f8d2-4dd2-bd17-df9fc79b8ec2/1910-setting-up-mbam-issues?forum=ConfigMgrCBGeneral function Get-CertificateFromSqlServer { param( [Parameter(Mandatory=$true)] [string]$sqlServer ) $option = New-PSSessionOption -ProxyAccessType NoProxyServer ### added fix for WinRm error [array]$encodedCerts = Invoke-Command -ComputerName $sqlServer -ScriptBlock { Get-ChildItem -Path Cert:\LocalMachine\My | Where-Object { ($_.FriendlyName -eq "ConfigMgr SQL Server Identification Certificate") -and ($_.NotBefore -lt (Get-Date)) -and ($_.NotAfter -gt (Get-Date)) } | ForEach-Object { $bytes = $_.Export("cert"); [Convert]::ToBase64String($bytes) } } -SessionOption $option ### added fix for WinRm error
-
You have to narrow it down to a single value result by filtering. WQL is not flexible enough to get you there. Try a powershell global condition like this. (Get-WmiObject -Namespace root\cimv2 -Class win32_networkadapterconfiguration -Filter "ipenabled='true'" | Where-Object {$_.DefaultIPGateway -like '*.*.*.*'} | select -First 1).DefaultIPGateway
- 1 reply
-
- mandatory profiles
- wondows 10
-
(and 36 more)
Tagged with:
- mandatory profiles
- wondows 10
- cb1910
- sccm
- cross-forest
- multi-domain
- sccm
- cmg
- azure
- sup
- client
- sccm
- dp
- office 365 updates
- query or collection in sccm
- gpo
- sccm cb
- database
- sccm cmdlets
- sccm client
- powershell
- wmi
- sccm
- client settings
- console
- dell
- 7212
- imaging
- osd
- defaultuser0
- configmgr
- sccm
- admin tools
- current branch
- manageengine
- patch connect plus
- configuration manager
- non microsoft updates
-
Make sure that your Firewall allows inbound remote management on the DP as well outbound on the MP. Also make sure that your MP computer account is a member of the local admin group on the DP.
- 1 reply
-
- mandatory profiles
- wondows 10
-
(and 36 more)
Tagged with:
- mandatory profiles
- wondows 10
- cb1910
- sccm
- cross-forest
- multi-domain
- sccm
- cmg
- azure
- sup
- client
- sccm
- dp
- office 365 updates
- query or collection in sccm
- gpo
- sccm cb
- database
- sccm cmdlets
- sccm client
- powershell
- wmi
- sccm
- client settings
- console
- dell
- 7212
- imaging
- osd
- defaultuser0
- configmgr
- sccm
- admin tools
- current branch
- manageengine
- patch connect plus
- configuration manager
- non microsoft updates
-
This command should work .. WFLASH2x64.exe xxxxxxx.ROM /bb /rsmb /ign /quiet /sccm The Problem is that you actually need a shutdown and not a resboot, which is not supported in SCCM. There is a workaround with a delayed restart command but its not very pretty or reliable. Also the kernel mode driver is using outdated and supported SHA1 signatures. The whole ThinkCentre BIOS update routine is pretty much crap ? There is also a problem with HVCI and those outdated signatures, which might cause blue screens under Windows 10 wen you have HVCI avtivated. After all i switched to the UEFI driver updates from https://www.catalog.update.microsoft.com/Search.aspx?q=thinkcentre%20firmware . Problem there is, they are not updated as often as they would be needed to. But they are easy to install and just require a plain old restart. Cheers Peter
- 1 reply
-
- mandatory profiles
- wondows 10
-
(and 36 more)
Tagged with:
- mandatory profiles
- wondows 10
- cb1910
- sccm
- cross-forest
- multi-domain
- sccm
- cmg
- azure
- sup
- client
- sccm
- dp
- office 365 updates
- query or collection in sccm
- gpo
- sccm cb
- database
- sccm cmdlets
- sccm client
- powershell
- wmi
- sccm
- client settings
- console
- dell
- 7212
- imaging
- osd
- defaultuser0
- configmgr
- sccm
- admin tools
- current branch
- manageengine
- patch connect plus
- configuration manager
- non microsoft updates
-
(Get-CMApplication -Name 'AppName').DateCreated or even better (Get-CMApplication -Name 'AppName').DateLastModified