-
Posts
9257 -
Joined
-
Last visited
-
Days Won
371
Everything posted by anyweb
-

New sccm site showing warning
anyweb replied to lalajee's topic in System Center Configuration Manager (Current Branch)
follow this series of guides (replace 1902 with 2203) and you'll be fine... -

The task sequence error cannot be executed
anyweb replied to zhangyongcheng's topic in Configuration Manager 2012
you are welcome, 1. the official docs are the place to start https://docs.microsoft.com/en-us/mem/configmgr/ 2. as long as it's Current Branch, you can upgrade in increments via the console, to upgrade follow the advice from my old post here 3. I'm not sure what scripts you are referring to... -

The task sequence error cannot be executed
anyweb replied to zhangyongcheng's topic in Configuration Manager 2012
dns is needed by the client(s) and servers so that they can all communicate with each other, for example the clients need to send state messages to the Management Point, aside from this, a network (whether LAB or Production) should always have working DNS otherwise you'll have problems with pretty much everything -

The task sequence error cannot be executed
anyweb replied to zhangyongcheng's topic in Configuration Manager 2012
ok it looks very like a DNS issue to me verify that DNS is working before trying again, you can do simple ping tests to the servers in question from a cmd prompt, or tracert/nslookup tests. -
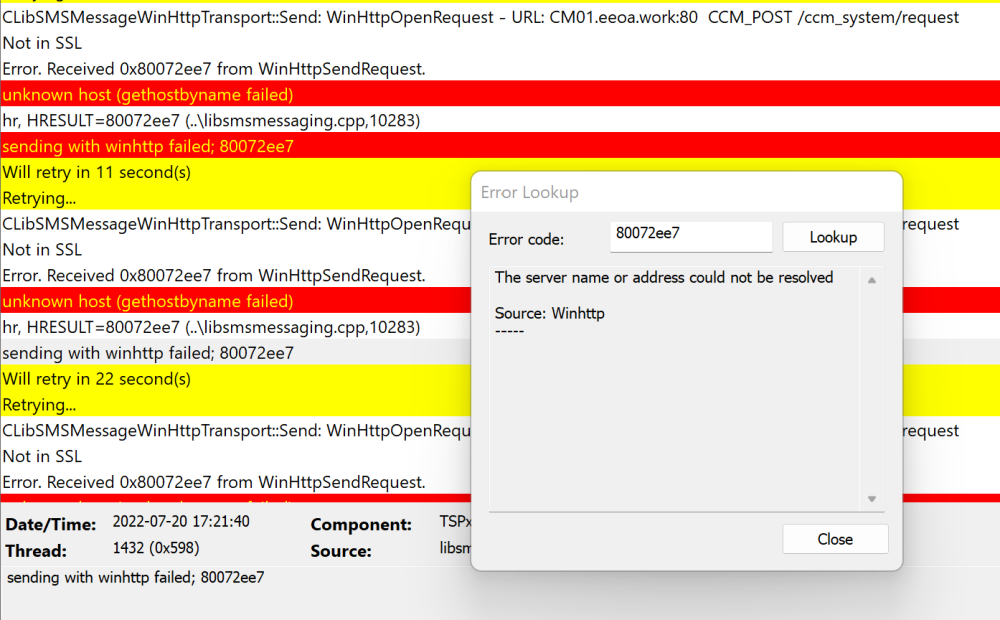
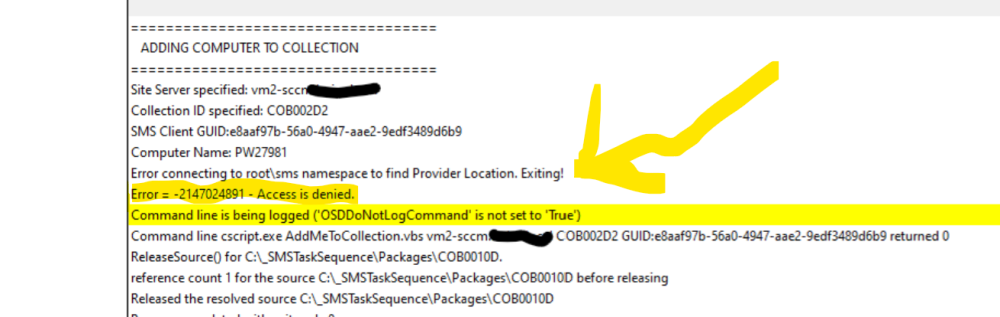
looking at your error, the actual problem is connecting to the root\sms namespace to find the provider location take a look at this see does it give you some pointers https://docs.microsoft.com/en-us/troubleshoot/windows-server/system-management-components/sms-administrator-console-connectivity-issue if it doesn't help try disabling the DCOM hardening. https://support.microsoft.com/en-us/topic/kb5004442-manage-changes-for-windows-dcom-server-security-feature-bypass-cve-2021-26414-f1400b52-c141-43d2-941e-37ed901c769c
-

Free report: Managing risks and costs at the edge
anyweb posted a topic in Official Forum Supporters
New research shows 50% of endpoints are at risk 600 CISOS, IT SecOps Directors, and Managers report that almost half of devices are vulnerable to attack because they are undetected by IT or have outdated operating systems. Thousands if not hundreds of thousands of devices at the edge need to work securely no matter where they are. But three significant factors are standing in the way: Device proliferation: 61% of respondents say distribution points have increased in the past 2 years and only 33% are confident they can reduce that sprawl. An expanding threat landscape: Only 39% of respondents believe their organizations are effective at preventing and detecting endpoint attacks. Rapid decentralization: 57% of IT professionals say that a remote workforce has made it difficult to deliver necessary security updates and patches to endpoints. So why is it that despite the average $4.3 million IT budget dedicated to endpoint protection ($31.50/endpoint) do only 34% of organizations have enough resources to minimize endpoint risk? The speed and scalability of their endpoint management solutions have everything to do with it. Get over 50 pages of peer insights in this year's Managing Risks and Costs at the Edge report from Ponemon Institute and Adaptiva. -

The task sequence error cannot be executed
anyweb replied to zhangyongcheng's topic in Configuration Manager 2012
can you please attach the entire smsts.log file here so we can see what is failing ? -
the last step it runs is installing some applications, Installing application 'Base Office 365 2019 v1902_SA_(Build 14131-20278)' does this app restart the computer unexpectedly ? after that it seems to have issues, i'm guessing your step occurs after this point ? can we see a screenshot of your task sequence with the step you are expecting to run ?
-

Admin console connectivity issues
anyweb replied to fj40ratt's topic in System Center Configuration Manager (Current Branch)
why not try disabling DCOM hardening, > https://support.microsoft.com/en-us/topic/kb5004442-manage-changes-for-windows-dcom-server-security-feature-bypass-cve-2021-26414-f1400b52-c141-43d2-941e-37ed901c769c. -
can this be related to versions of Microsoft Visual C++ installed ?
- 12 replies
-
- sccm
- config mngr
-
(and 1 more)
Tagged with:
-
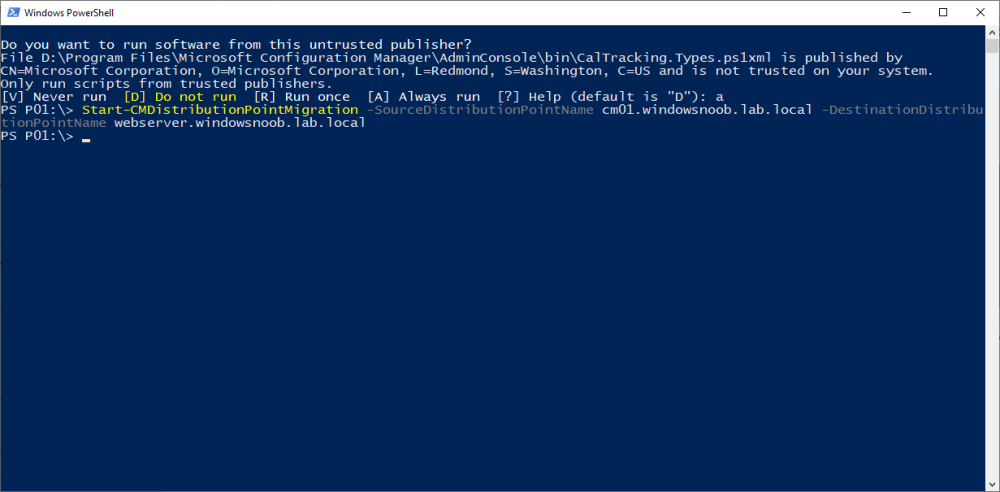
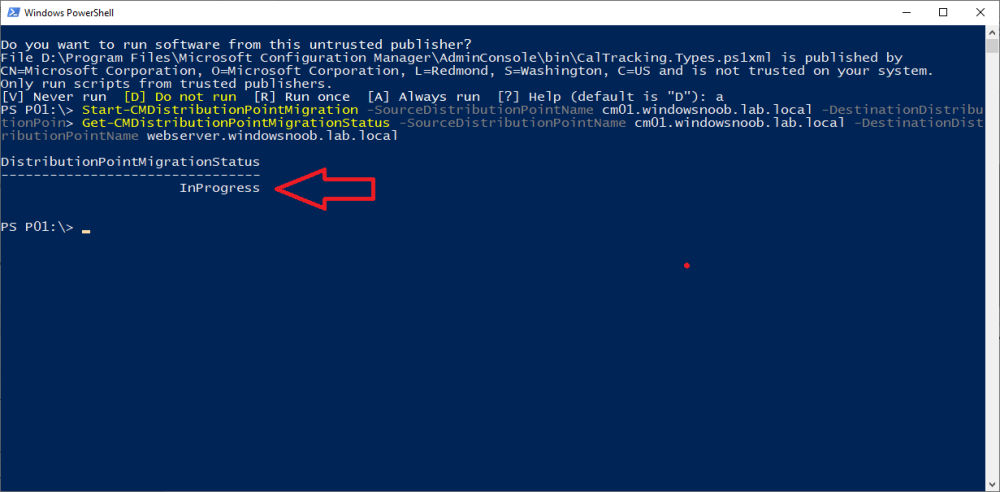
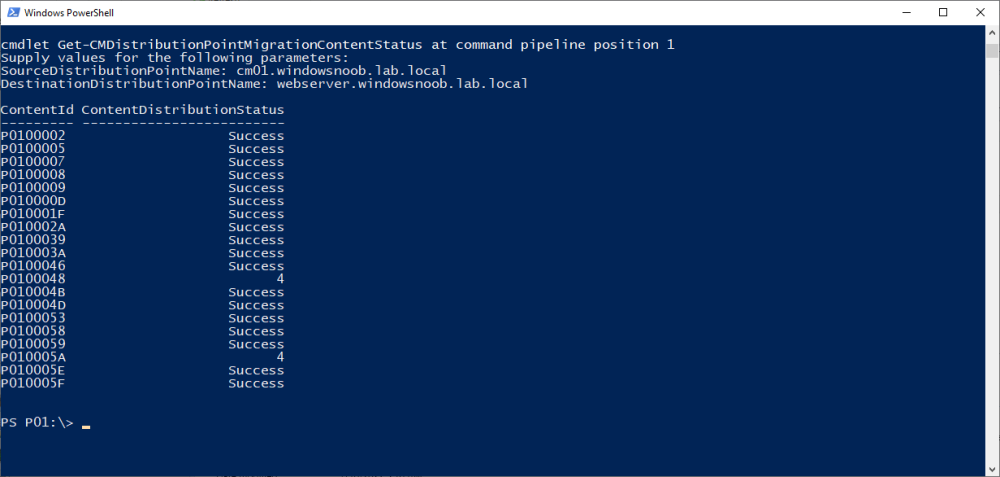
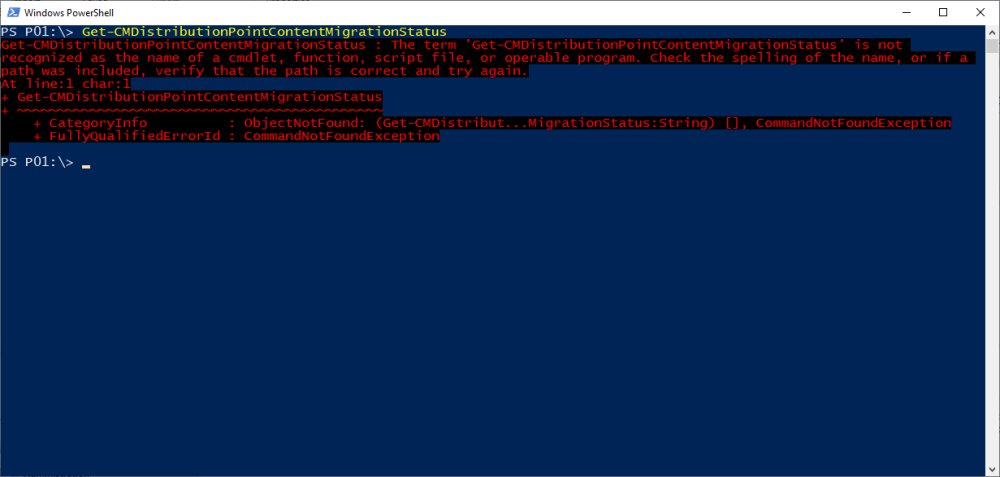
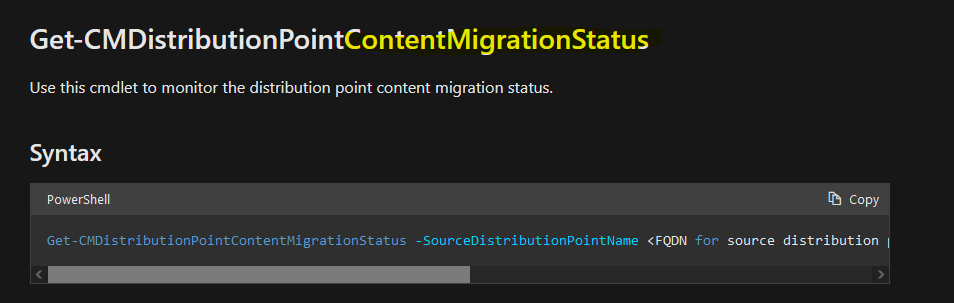
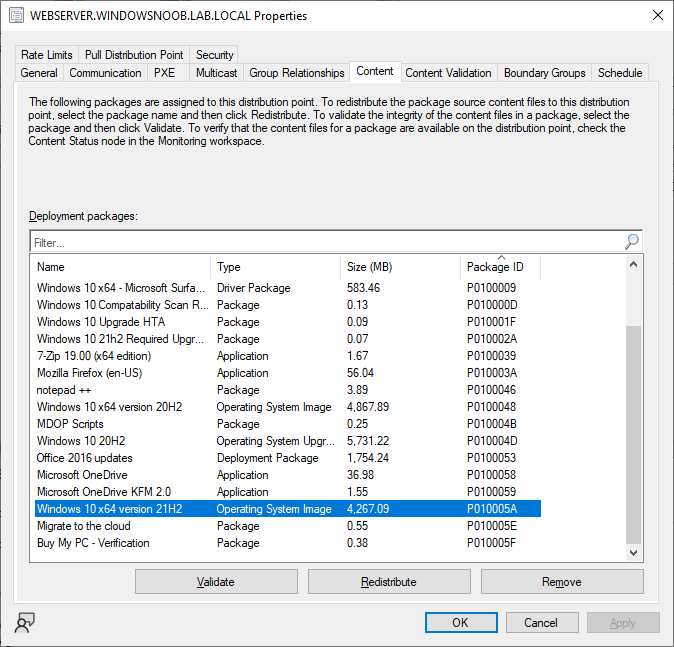
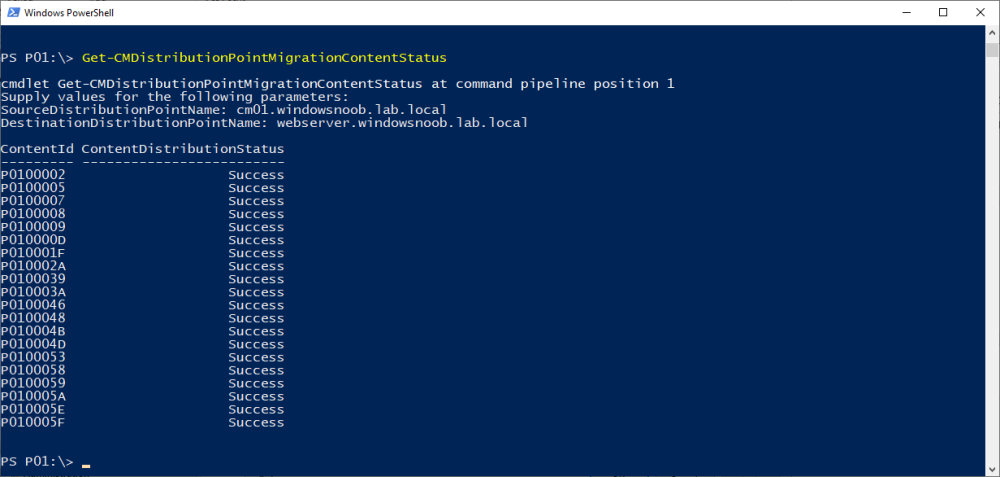
Introduction Microsoft released another Technical Preview release, this time 2207, and it has a new feature, Distribution point content migration. According to the official blog post this will come in handy when you need to migrate your distribution point content from one dp to another, in particular because of the first 2 points listed below. As I don't have either (1) or (2) I will test scenario (3). Step 1. Satisfy the prerequisites One of the prerequisites is that the user performing the migration has the "Copy to Distribution Point" permission enabled under the Distribution Point permissions. As my user account is a Full Administrator, that requirement is already met. The other requirements are listed below. If you want to deprecate the source distribution point, make sure that the source and destination distribution points have the same boundary group. The destination distribution point should be installed already and able to receive the content. Step 2. Migrate a distribution point using Powershell As the current solution does not work in the Console, we need to use Powershell to do the migration. On the Configuration Manager server, open a Powershell cmd prompt via the console, and try the following Start-CMDistributionPointMigration -SourceDistributionPointName <FQDN for source distribution point> -DestinationDistributionPointName <FQDN for destination distribution point> for example... Start-CMDistributionPointMigration -SourceDistributionPointName cm01.windowsnoob.lab.local -DestinationDistributionPointName webserver.windowsnoob.lab.local as shown here... The fact that it didn't error was a good start. Step 3. Monitor the migration using Powershell As the ability to monitor this via the console is not yet available, you'll need to once again monitor things using Powershell. The command this time is Get-CMDistributionPointMigrationStatus -SourceDistributionPointName <FQDN for source distribution point> -DestinationDistributionPointName <FQDN for destination distribution point> Let's give it a try. Get-CMDistributionPointMigrationStatus -SourceDistributionPointName cm01.windowsnoob.lab.local -DestinationDistributionPointName webserver.windowsnoob.lab.local The result should tell you if it's in progress, completed and so on. Step 4. Monitor the content being migrated The docs incorrectly listed the cmdlet as Get-CMDistributionPointContentMigrationStatus but that doesn't work, see below. Here is a screenshot of the docs... (as of 2022/07/10), I've informed them of the error, so I'm sure it'll be fixed soon Using the power of the TAB key, I figured out the correct command and here it is: Get-CMDistributionPointMigrationContentStatus I think that the status (4) means that it's still in progress but I've asked the Microsoft Product Group for comment. As you can see below the source DP lists this packageID as a large package so it will take more time to complete. and sure enough, after more minutes in transit, the status changes from 4 to Success So there you have it, content migration from one distribution point to another using Powershell built into ConfigMgr works very nicely indeed, is that cool or what ? Related reading https://techcommunity.microsoft.com/t5/configuration-manager-blog/configuration-manager-technical-preview-version-2207/ba-p/3567090 https://docs.microsoft.com/en-us/mem/configmgr/core/get-started/2022/technical-preview-2207 cheers niall
-
interesting, what version were they running prior to this ?
- 12 replies
-
- sccm
- config mngr
-
(and 1 more)
Tagged with:
-
great Nancy, what did you do exactly so others may learn
- 12 replies
-
- sccm
- config mngr
-
(and 1 more)
Tagged with:
-
and if you rdp to one of these machines and launch the console, does it work ?
- 12 replies
-
- sccm
- config mngr
-
(and 1 more)
Tagged with:
-
what does the SMSAdminUI.log tell you (on their pc) ?
- 12 replies
-
- sccm
- config mngr
-
(and 1 more)
Tagged with:
-

SCCM ADR - Windows Updates
anyweb replied to OwenL's topic in System Center Configuration Manager (Current Branch)
the ruleengine.log should give you some clues as to why it's taking time to do what you expect, take a look at this old blog post which will hopefully give you some ideas about going deeper with your troubleshooting -
have you looked at your SQL firewall ports on the primary, there are several errors connecting to it in the start of the log *** [08001][2][Microsoft][SQL Server Native Client 11.0]A network-related or instance-specific error has occurred while establishing a connection to SQL Server. Server is not found or not accessible. Check if instance name is correct and if SQL Server is configured to allow remote connections. For more information see SQL Server Books Online. *** Failed to connect to the SQL Server, connection type: SCCM02-SHA.company.LOCAL MASTER. ERROR: Failed to connect to SQL Server 'master' db.