-
Posts
9254 -
Joined
-
Last visited
-
Days Won
369
Everything posted by anyweb
-
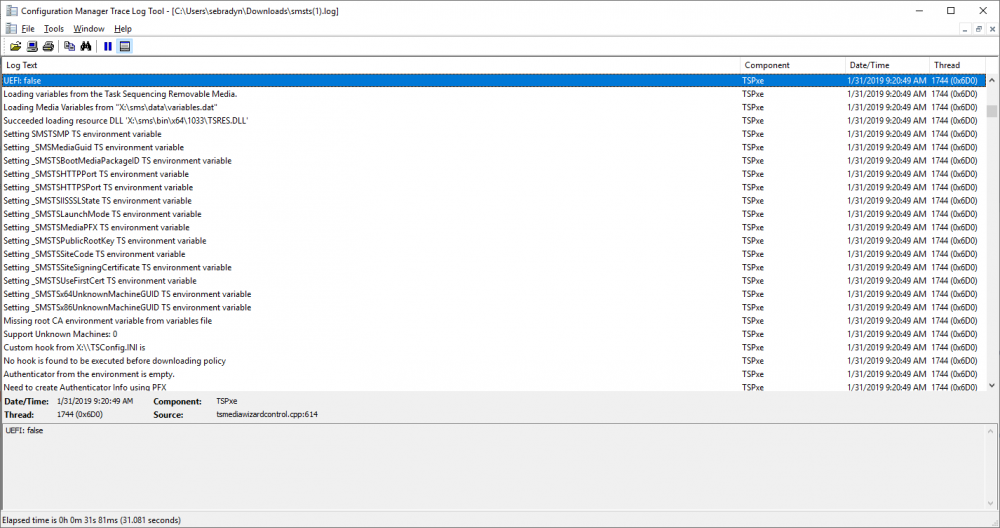
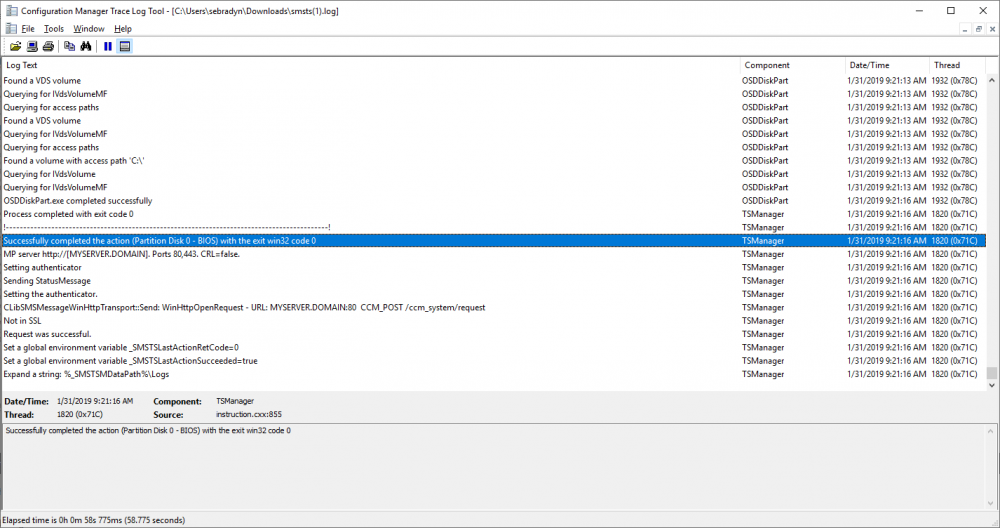
hi can you post the logs from C:\Programdata\ so i can take a look ?
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-

AD integrated bitlocker
anyweb replied to Kevin79's topic in System Center Configuration Manager (Current Branch)
technically i'm sure it's possible but you'd have to script something to make the call to AD and then pull the relevant data. -
best of luck with it Thomas, i know it's complex to setup, but once you have it all working in a lab it's worth it !
-
hi Thomas, i guess you missed the start of the blog post ? here it is again...I've also added a hard link to part 5 at the end of this blog post, thanks This series is comprised of different parts, listed below. Part 1 - Introduction and server setup Part 2 - Install and do initial configuration on the Standalone Offline Root CA Part 3 - Prepare the HTTP Web server for CDP and AIA Publication Part 4 - Post configuration on the Standalone Offline Root CA (this part) Part 5 - Installing the Enterprise Issuing CA Part 6 - Perform post installation tasks on the Issuing CA Part 7 - Install and configure the OCSP Responder role service Part 8 - Configure AutoEnroll and Verify PKI health
-
can you do a teamviewer session so i can take a look ?
- 19 replies
-
- powershell
- current branch
-
(and 2 more)
Tagged with:
-
can you post the error if you have it please
- 19 replies
-
- powershell
- current branch
-
(and 2 more)
Tagged with:
-
hi at the bottom of each post it links to the next in the series. Did you miss that ? fyi, all the Current Branch content I've written is listed here in chronological order https://www.windows-noob.com/forums/topic/13288-step-by-step-guides-system-center-configuration-manager-current-branch-and-technical-preview/ here are the 4 parts of this series How can I install System Center Configuration Manager (Current Branch) version 1802 on Windows Server 2016 with SQL Server 2017 – Part 1 How can I install System Center Configuration Manager (Current Branch) version 1802 on Windows Server 2016 with SQL Server 2017 – Part 2 How can I install System Center Configuration Manager (Current Branch) version 1802 on Windows Server 2016 with SQL Server 2017 – Part 3 How can I install System Center Configuration Manager (Current Branch) version 1802 on Windows Server 2016 with SQL Server 2017 – Part 4 I will edit the posts to link to all 4 parts.
- 20 replies
-
- sql server 2017
- powershell
-
(and 3 more)
Tagged with:
-
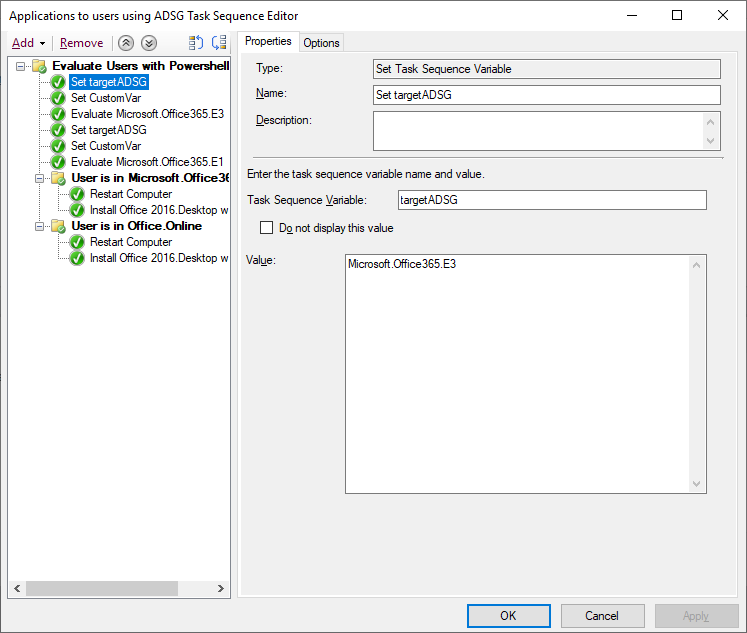
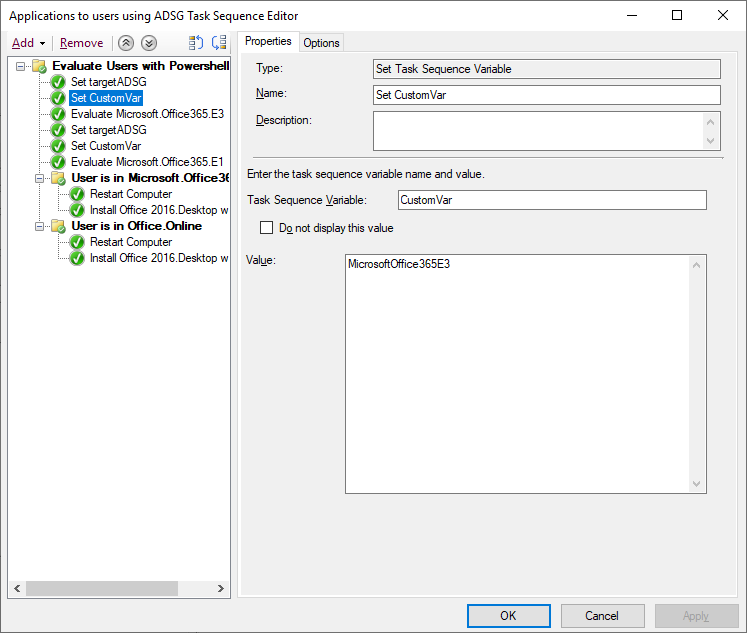
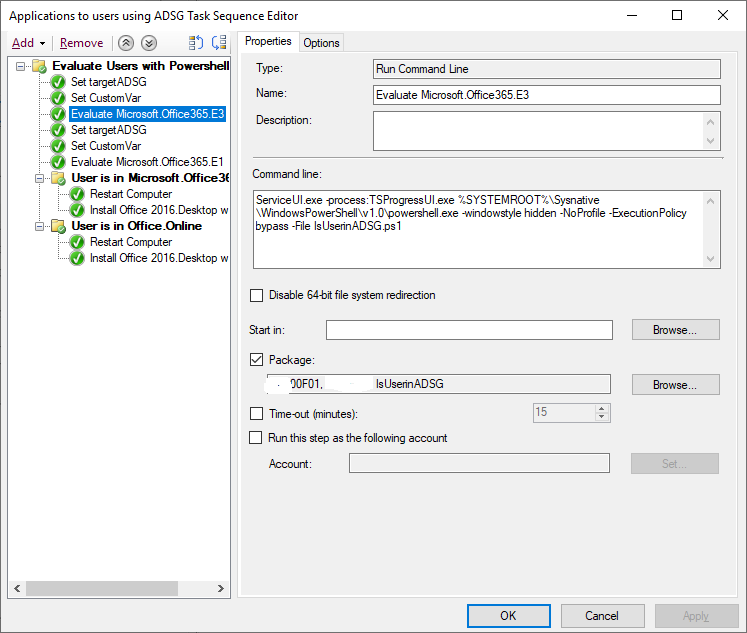
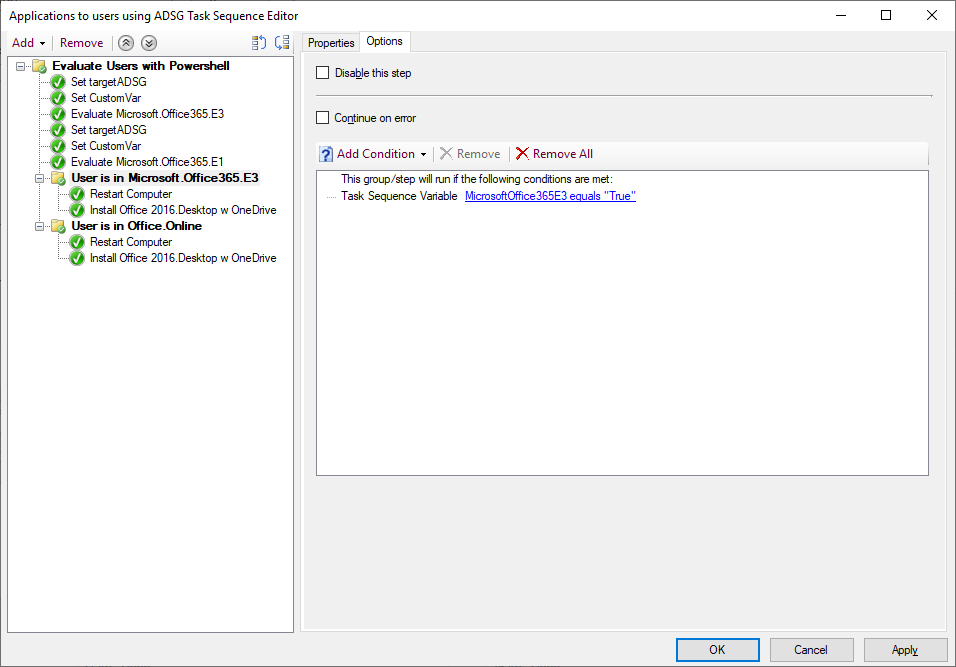
here's one way of doing it for users, you could easily modify the PowerShell script to take the two parameters so it's a one step process instead of 3, i just haven't had time yet to modify it. Note: You will need to define the TargetUser in the task sequence using whatever method you want as the script checks for that in the following line: $strName = $tsenv.Value("targetuser") Step 1. Set TargetADSG set the target Active Directory Security Group you want to test if the user is present in step 2. Set a custom variable for that Step 3. call the powershell script (uses ServiceUI.exe from the MDT Toolkit, use the correct architecture for the version of Windows you are deploying) ServiceUI.exe -process:TSProgressUI.exe %SYSTEMROOT%\Sysnative\WindowsPowerShell\v1.0\powershell.exe -windowstyle hidden -NoProfile -ExecutionPolicy bypass -File IsUserinADSG.ps1 Step 4, Run the Group to install software if the CustomVar set earlier is true here's the powershell script I used IsUserinADSG.ps1
-
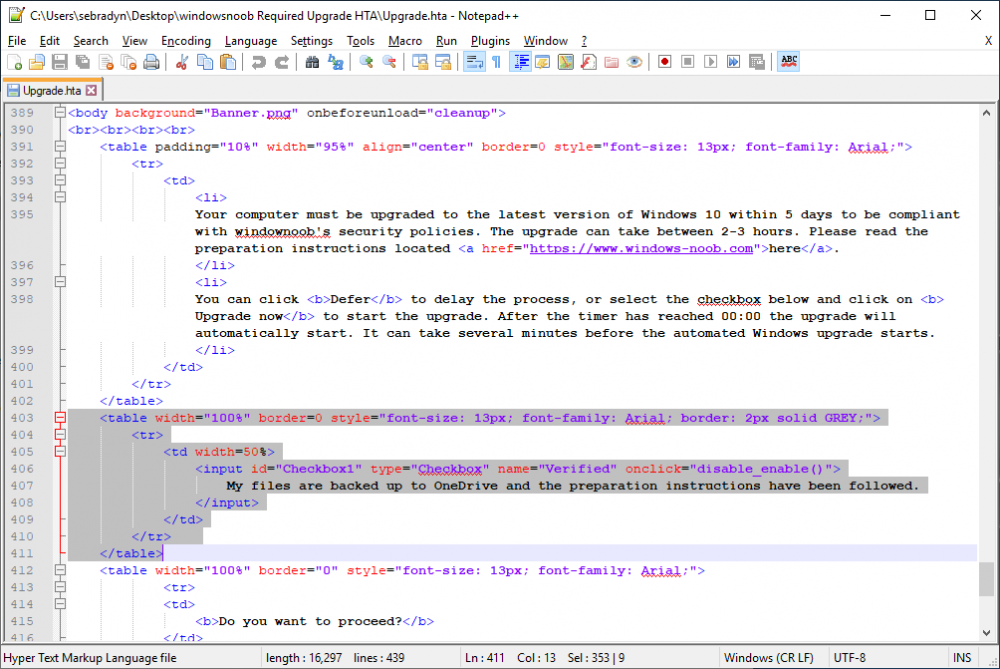
thanks ! you need to cut out this bit and then modify this function to ensure that Upgrade Now button is not disabled function disable_enable(){ if (document.getElementById("Checkbox1").checked == true) //alert('checked'); document.getElementsByName("run_vbscript_button").item(0).disabled = false; else //alert('not checked'); document.getElementsByName("run_vbscript_button").item(0).disabled = true; cheers niall
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
if you open the HTA using Notepad ++ and change the Language used to VBScript (VBS) or HTML in Notepad ++ you'll see it format the HTA nicely and it'll make more sense.
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with:
-
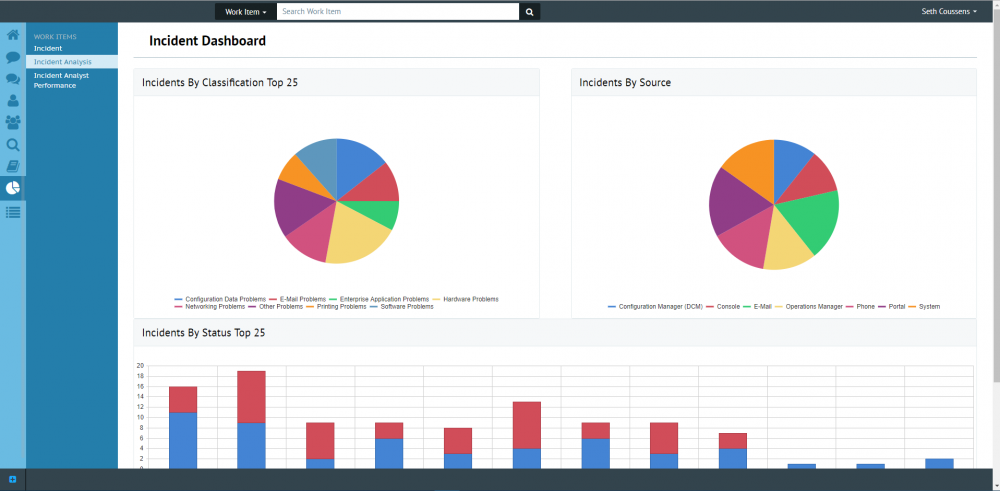
If you use System Center Service Manager (SCSM) then you really should check out the great Portals from Cireson. Cireson has today launched a new free Analyst Portal today for SCSM, offering web-based Incident Management. Check it out here: https://cireson.com/apps/analyst-portal-community/ Here’s the press release: https://cireson.com/press/cireson-releases-free-web-based-analyst-portal-community-app-in-further-commitment-to-microsoft-service-manager-community/
-
well spotted, except that one is remmed out hence the // so it doesn't do anything (it's a comment) cheers niall
- 242 replies
-
- 1702
- forced upgrade
-
(and 2 more)
Tagged with: